Most of the malicious search ads we have seen have originated from Google, but threat actors are also abusing other search engines. Microsoft Bing is probably the second best target due to its close ties to the Windows ecosystem and Edge browser.
我们看到的大多数恶意搜索广告都来自谷歌,但威胁行为者也在滥用其他搜索引擎。Microsoft Bing可能是第二好的目标,因为它与Windows生态系统和Edge浏览器有着密切的联系。
In this blog post, we look at a very recent malvertising campaign impersonating the popular VPN software NordVPN. A malicious advertiser is capturing traffic from Bing searches and redirecting users to a decoy site that looks almost identical to the real one.
在这篇博文中,我们介绍了最近冒充流行的 VPN 软件 NordVPN 的恶意广告活动。恶意广告商正在捕获来自 Bing 搜索的流量,并将用户重定向到看起来与真实网站几乎相同的诱饵网站。
The threat actors went ever further by trying to digitally sign a malicious installer as if they were the official vendor. Victims will have the impression they are getting NordVPN as it is part of the package, but will also inadvertently install a Remote Access Trojan known as SecTopRAT on their computer.
威胁行为者更进一步,试图对恶意安装程序进行数字签名,就好像他们是官方供应商一样。受害者会给人的印象是他们正在获得 NordVPN,因为它是软件包的一部分,但也会无意中在他们的计算机上安装一个名为 SecTopRAT 的远程访问木马。
We have reported the malicious Bing ad to Microsoft, and other parts of the distribution infrastructure to their respective provider. We want to reiterate that NordVPN is a legitimate VPN provider and they are being impersonated by threat actors.
我们已将恶意必应广告报告给 Microsoft,并将分发基础结构的其他部分报告给各自的提供商。我们想重申,NordVPN 是合法的 VPN 提供商,他们正在被威胁行为者冒充。
Fraudulent Bing ad 欺诈性 Bing 广告
When searching for “nord vpn” via the Bing search engine, we identified a malicious ad that impersonates NordVPN. The ad itself looks suspicious because of the URL in the ad snippet. The domain name nordivpn[.]xyz was created one day ago (April 3, 2024). It was probably chosen as it looks quite similar to the official name and can deceive users who aren’t looking too closely.
通过必应搜索引擎搜索“nord vpn”时,我们发现了一个冒充 NordVPN 的恶意广告。由于广告代码段中的网址,广告本身看起来很可疑。域名nordivpn[.]xyz 是在一天前(2024 年 4 月 3 日)创建的。之所以选择它,可能是因为它看起来与官方名称非常相似,并且可以欺骗那些不太仔细的用户。
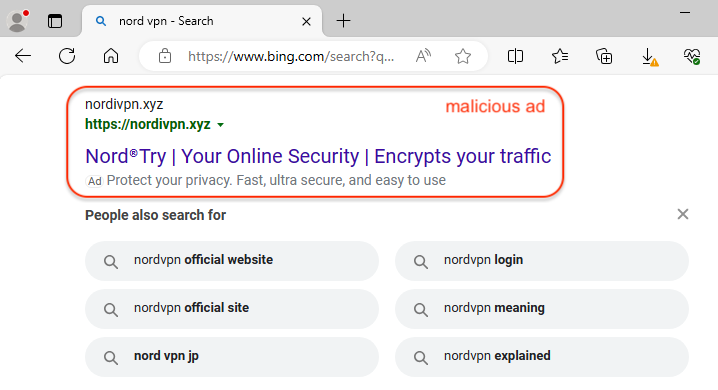
As we often see, the ad URL is simply used as a redirection mechanism to a fake website that is meant to look identical to the one being impersonated. This is true here as well, where we have a redirect to besthord-vpn[.]com (note again the spelling chosen with the ‘h‘ looking like an ‘n‘) which was created today, only a few hours ago.
正如我们经常看到的,广告 URL 只是用作指向虚假网站的重定向机制,该虚假网站看起来与被冒充的网站相同。这里也是如此,我们有一个重定向到 besthord-vpn[.]com(再次注意选择的拼写,其中“h”看起来像“n”),这是今天创建的,就在几个小时前。
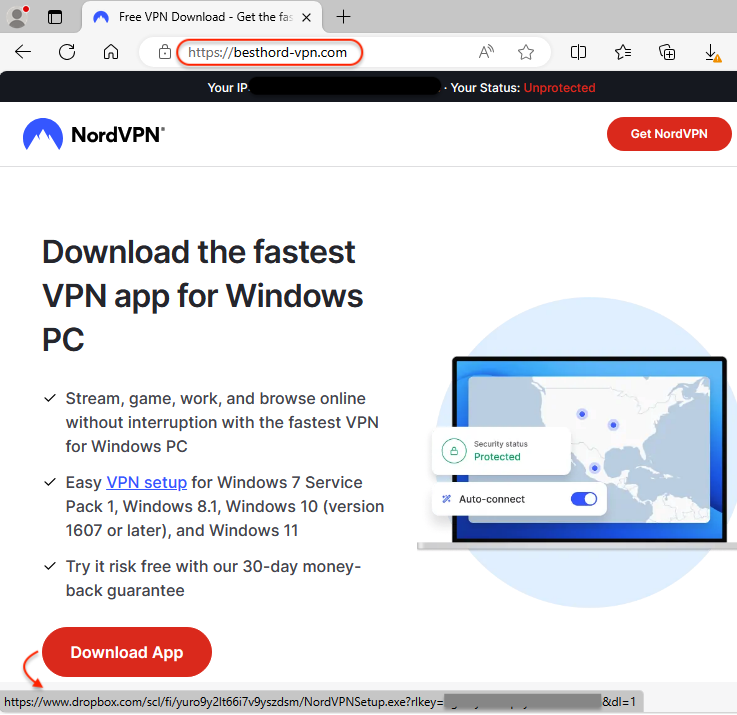
The website looks incredibly convincing, and victims will be tricked into downloading the app from there. Unlike the legitimate NordVPN that goes through a sign up process, here you can directly download the installer from Dropbox.
该网站看起来非常有说服力,受害者将被诱骗从那里下载该应用程序。与通过注册过程的合法NordVPN不同,您可以直接从Dropbox下载安装程序。
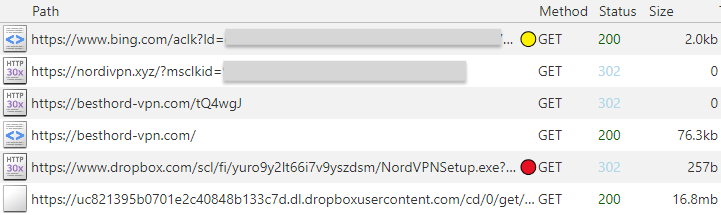
Here’s a summary of the traffic flow from the malicious ad to the download link:
以下是从恶意广告到下载链接的流量摘要:
Malware payload 恶意软件有效负载
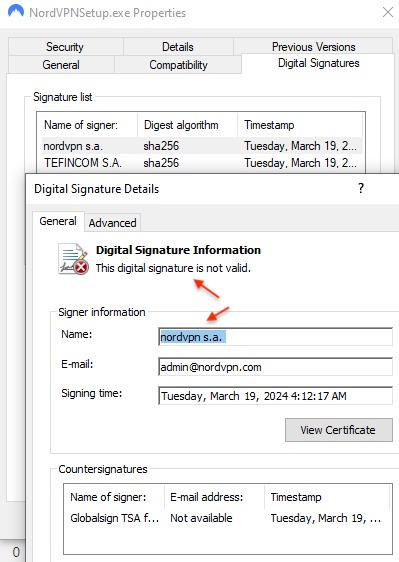
The downloaded file is called NordVPNSetup.exe and is digitally signed, as if it was from its official vendor; however, the signature is not valid.
下载的文件称为 NordVPNSetup.exe 并经过数字签名,就好像它来自其官方供应商一样;但是,签名无效。
The file contains both an installer for NordVPN and a malware payload. The installer for NordVPN is meant to give victims the illusion that they are actually installing a real file.
该文件包含 NordVPN 的安装程序和恶意软件有效负载。NordVPN的安装程序旨在让受害者产生一种错觉,即他们实际上正在安装一个真实的文件。
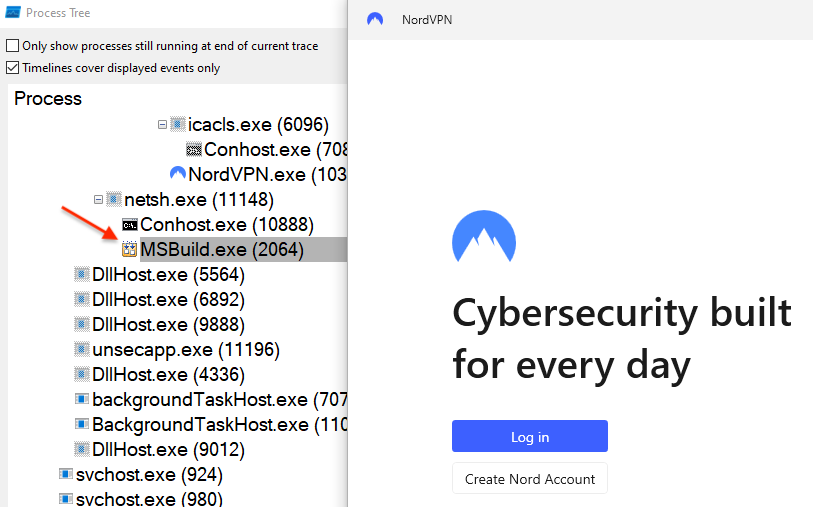
The payload is injected into MSBuild.exe and will connect to the malware author’s command and control server at 45.141.87[.]216 on port 15647.
有效负载被注入MSBuild.exe,并将连接到恶意软件作者的命令和控制服务器,地址为45.141.87[.]端口 15647 上的 216。
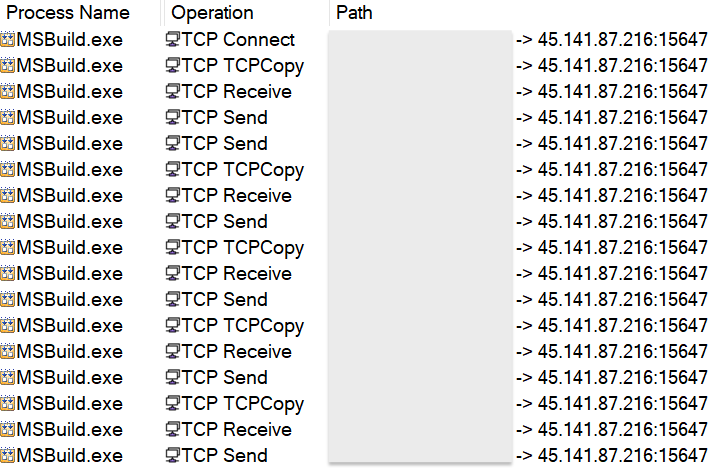
That network traffic is detected by Emerging Threats as Arechclient2 Backdoor, an alias for SecTopRAT.
该网络流量被 Emerging Threats 检测为 Arechclient2 后门,即 SecTopRAT 的别名。
Conclusion 结论
Malvertising continues to show how easy it is to surreptitiously install malware under the guise of popular software downloads. Threat actors are able to roll out infrastructure quickly and easily to bypass many content filters.
恶意广告继续表明,以流行的软件下载为幌子秘密安装恶意软件是多么容易。威胁参与者能够快速轻松地推出基础架构,以绕过许多内容过滤器。
ThreatDown customers who have DNS Filtering can proactively block online ads by enabling the rule for advertisements. This is a simple, and yet powerful way to prevent malvertising across an entire organization or in specific areas.
具有 DNS 过滤的 ThreatDown 客户可以通过启用广告规则来主动阻止在线广告。这是一种简单而有效的方法,可以防止整个组织或特定领域的恶意广告。
The malicious ad and related indictors have been reported as we work with industry partners to take down this campaign. Dropbox has already taken action to take down the malicious download.
在我们与行业合作伙伴合作取缔此活动时,已经报告了恶意广告和相关指标。Dropbox已经采取了行动来删除恶意下载。
Indicators of Compromise
入侵指标
Malicious domains 恶意域
nordivpn[.]xyz besthord-vpn[.]com
Fake NordVPN installer 假 NordVPN 安装程序
e9131d9413f1596b47e86e88dc5b4e4cc70a0a4ec2d39aa8f5a1a5698055adfc
SecTopRAT C2
45.141.87[.]216
原文始发于Jérôme Segura:Bing ad for NordVPN leads to SecTopRAT