MetaStealer is a popular piece of malware that came out in 2022, levering previous code base from RedLine. Stealers have become a very hot commodity in the criminal space, so much so that there is competition between various groups.
MetaStealer 是一种流行的恶意软件,于 2022 年问世,利用了 RedLine 以前的代码库。偷窃者已成为犯罪领域非常热门的商品,以至于各种团体之间存在竞争。
Threat actors have primarily used malspam as an infection vector to drop MetaStealer as well as cracked software via stolen YouTube accounts, but it was at least once previously seen in a malvertising campaign.
威胁行为者主要使用恶意垃圾邮件作为感染媒介,通过被盗的 YouTube 帐户丢弃 MetaStealer 以及破解软件,但至少在恶意广告活动中出现过一次。
In the past week, we observed some malicious ads that weren’t dropping FakeBat or PikaBot, but rather a different payload that we recognized as MetaStealer. Interestingly, in early December, the malware authors behind MetaStealer gave an interview and announced that they were about to release a new and improved version of their tool.
在过去的一周里,我们观察到一些恶意广告,这些广告并没有丢弃 FakeBat 或 PikaBot,而是丢弃了我们识别为 MetaStealer 的不同有效载荷。有趣的是,在 12 月初,MetaStealer 背后的恶意软件作者接受了采访,并宣布他们即将发布其工具的新改进版本。
Distribution 分配
We captured two different ads for Notepad++ and AnyDesk via Google searches:
我们通过谷歌搜索捕获了Notepad++和AnyDesk的两个不同的广告:
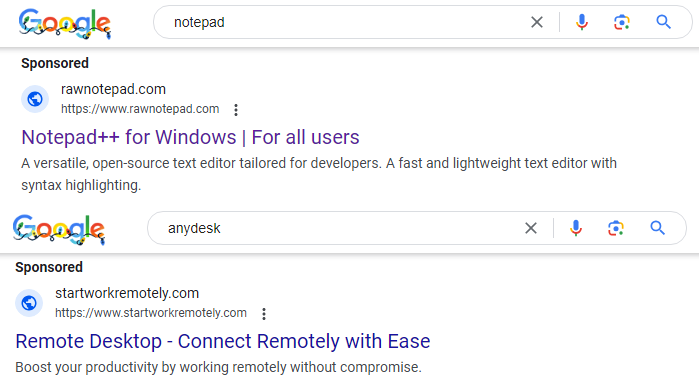
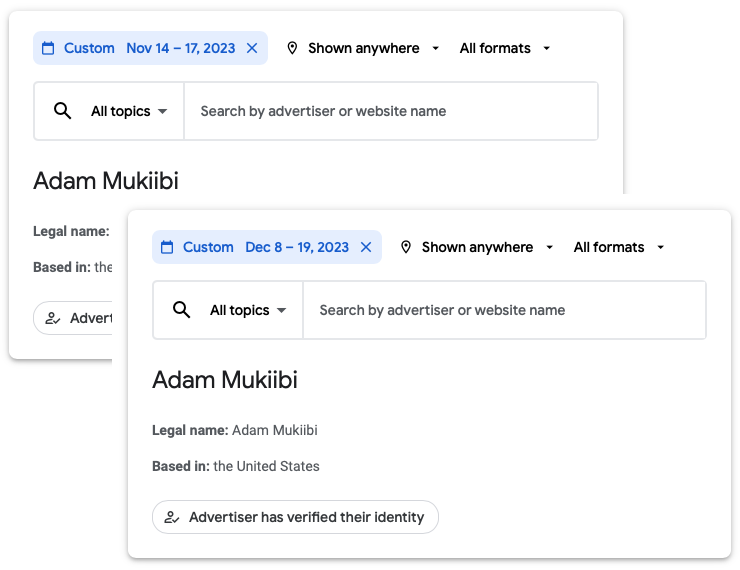
According to the Google Ads Transparency Center, one of the campaigns ran in November and December, during specific dates:
根据 Google Ads 透明度中心的数据,其中一个广告系列在 11 月和 12 月的特定日期投放:
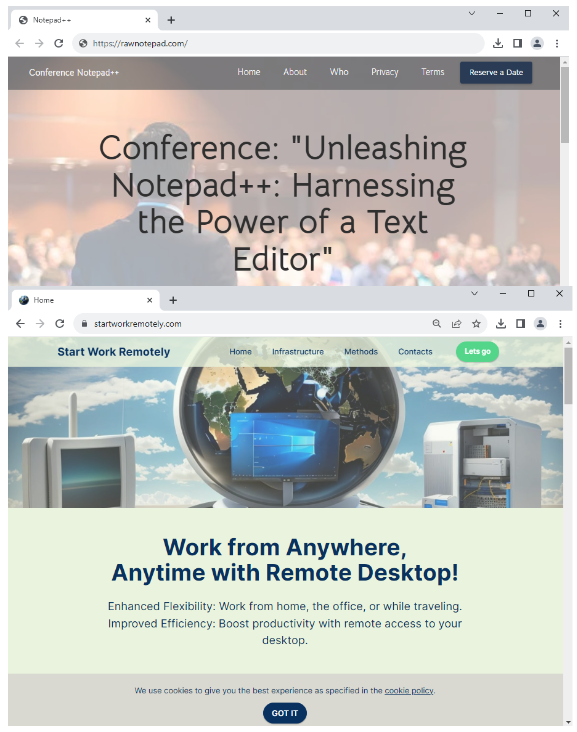
Two domains have been setup as both decoy and landing pages. If you were to browse to those sites directly, you would see content that looks like it was generated automatically. Note how the two pages have a similar template.
两个域已设置为诱饵和登录页面。如果您直接浏览这些网站,您会看到看起来像是自动生成的内容。请注意这两个页面如何具有相似的模板。
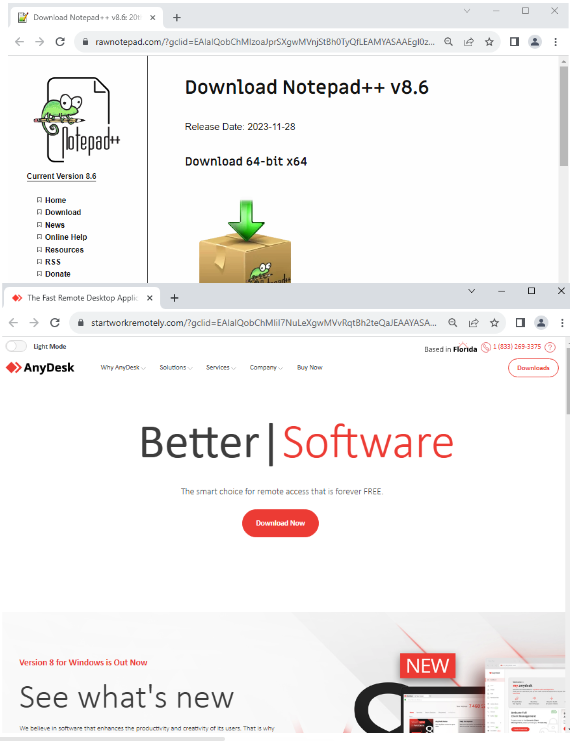
However, users that clicked on the ads and met the selection criteria will get a malicious landing page and a download link:
但是,点击广告并符合选择标准的用户将获得恶意着陆页和下载链接:
Payload 有效载荷
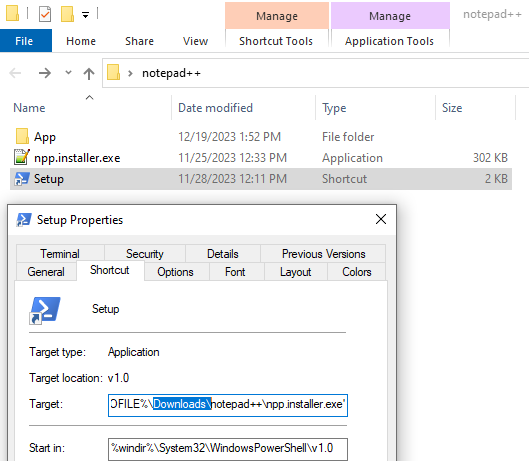
The November payload contained a shortcut launching PowerShell that used a hardcoded path to the Downloads folder (would fail if the file was extracted in another directory):
11 月有效负载包含启动 PowerShell 的快捷方式,该快捷方式使用指向 Downloads 文件夹的硬编码路径(如果文件被提取到另一个目录中,则会失败):
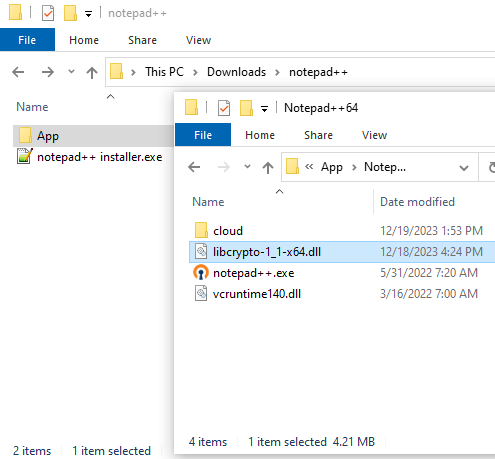
The December campaign got rid of the PowerShell and the malicious DLL was recompiled:
12 月的活动摆脱了 PowerShell,恶意 DLL 被重新编译:
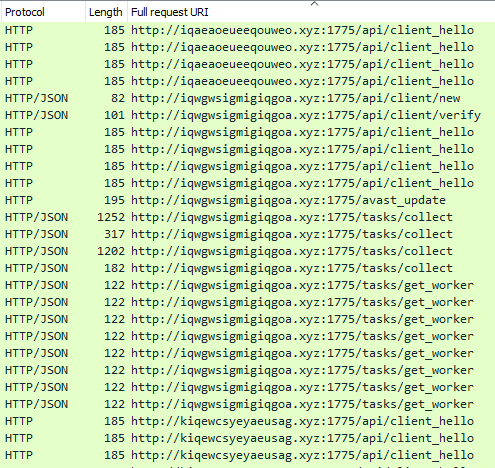
Based on network traffic activity alone, it appears that both payloads are still the MetaStealer from the 3.x branch:
仅根据网络流量活动,似乎两个有效负载仍然是 3.x 分支的 MetaStealer:
For an in-depth look at MetaStealer, check out this article by Russian Panda.
要深入了解 MetaStealer,请查看 Russian Panda 的这篇文章。
Conclusion 结论
The developers of MetaStealer are improving their product and we are likely to see more of their customers distributing it. Stealers can serve multiple purposes but tend to revolve around items that criminals can easily monetize. Crypto wallets are usually quite coveted, but so are credentials for various online services. And finally, stealers can also be used by initial access brokers, paving the path for ransomware actors.
MetaStealer的开发人员正在改进他们的产品,我们可能会看到更多的客户分发它。偷窃者可以有多种用途,但往往围绕着犯罪分子可以轻松获利的物品。加密钱包通常非常令人垂涎,但各种在线服务的凭据也是如此。最后,初始访问代理也可以使用窃取程序,为勒索软件行为者铺平道路。
We have reported the malicious ads to Google and have already blocked the infrastructure behind these campaigns.
我们已向 Google 报告了这些恶意广告,并已屏蔽了这些广告系列背后的基础架构。
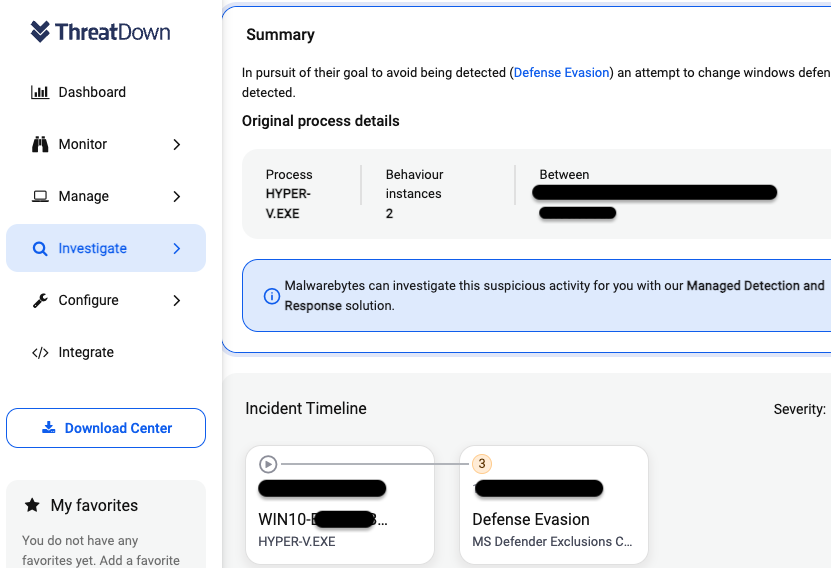
ThreatDown, powered by Malwarebytes, detects this threat as Trojan.MetaStealer.Generic. The Endpoint Detection and Response (EDR) can also see the process activity tied to this attack:
由 Malwarebytes 提供支持的 ThreatDown 将此威胁检测为 Trojan.MetaStealer.Generic。终结点检测和响应 (EDR) 还可以查看与此攻击相关的进程活动:

Additionally, the newly released Incident Timeline feature can alert you of an active intrusion attempt which our Managed Detection and Response team can assist you with.
此外,新发布的事件时间线功能可以提醒您主动入侵尝试,我们的托管检测和响应团队可以为您提供帮助。
Indicators of Compromise
入侵指标
Malicious domains 恶意域
rawnotepad[.]com startworkremotely[.]com
Payload URLs 有效负载 URL
rawnotepad[.]com/notepad++.zip startworkremotely[.]com/Anydesk.zip
Payload hashes 有效负载哈希
949c5ae4827a3b642132faf73275fb01c26e9dce151d6c5467d3014f208f77ca 99123063690e244f95b89d96759ec7dbc28d4079a56817f3152834047ab047eb c5597da40dee419696ef2b32cb937a11fcad40f4f79f9a80f6e326a94e81a90f
MetaStealer C2s
wgcuwcgociewewoo[.]xyz ockimqekmwecocug[.]xyz kiqewcsyeyaeusag[.]xyz cewgwsyookogmmki[.]xyz startworkremotely[.]com csyeywqwyikqaiim[.]xyz iqaeaoeueeqouweo[.]xyz mmswgeewswyyywqk[.]xyz accounts[.]google[.]com iqwgwsigmigiqgoa[.]xyz
