A new variant of Agent Tesla uses the uncommon compression format ZPAQ to steal information from approximately 40 web browsers and various email clients. But what exactly is this file compression format? What advantage does it provide to threat actors? And why it is assumed that the version of Agent Tesla is “new”?
Agent Tesla 的新变体使用不常见的压缩格式 ZPAQ 从大约 40 个 Web 浏览器和各种电子邮件客户端窃取信息。但是这个文件压缩格式到底是什么?它为威胁行为者提供了什么优势?为什么假设特斯拉特工的版本是“新”的?
ZPAQ compression format and what it hides
ZPAQ 压缩格式及其隐藏的内容
On November 1, 2023, researcher Xavier Mertens reported a phishing attempt on one of his honeypots. What’s noteworthy is that a threat actor used the ZPAQ archive and .wav file extension to infect the system with Agent Tesla.
2023 年 11 月 1 日,研究员 Xavier Mertens 报告了他的一个蜜罐遭到网络钓鱼尝试。值得注意的是,威胁行为者使用 ZPAQ 存档和 .wav 文件扩展名用 Agent Tesla 感染系统。
ZPAQ is a file compression format that offers a better compression ratio and journaling function compared to widely used formats like ZIP and RAR. That means that ZPAQ archives can be smaller, saving storage space and bandwidth when transferring files. However, ZPAQ has the biggest disadvantage: limited software support. There are GUI unpackers that support this format, for example, Peazip, but ZPAQ can be extracted primarily with a command-line tool that does not make it easy to work with, especially for users without technical expertise.
ZPAQ 是一种文件压缩格式,与广泛使用的格式(如 ZIP 和 RAR)相比,它提供了更好的压缩比和日记功能。这意味着 ZPAQ 存档可以更小,从而在传输文件时节省存储空间和带宽。然而,ZPAQ最大的缺点是:软件支持有限。有一些支持这种格式的 GUI 解包器,例如 Peazip,但 ZPAQ 可以主要使用命令行工具提取,该工具不容易使用,特别是对于没有技术专长的用户。
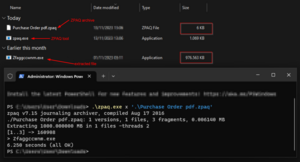
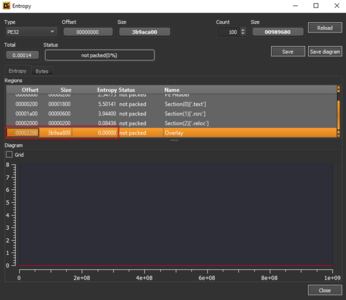
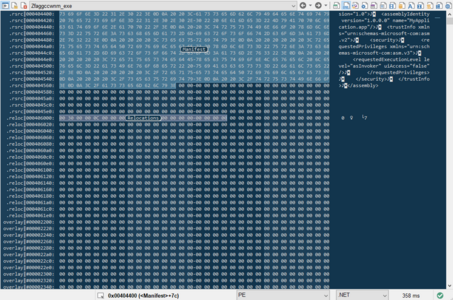
The initial file was found in an email called “Purchase Order pdf.zpaq”. As you can see from the file name, the threat actor is attempting to deceive us into believing that the archive contains a PDF file with important information. After using the command-line extraction tool ZPAQ it turns out that the 6KB archive suddenly “weighed” 1GB after extraction. After a deep look into the executable, it turned out that the file is a .NET executable with async methods and that is bloated with zero bytes. One of the indicators is 0 entropy in the overlay section. The analysis of the executable in a hex editor proved that 90% of the sample is filled with zero bytes.
初始文件是在名为“采购订单pdf.zpaq”的电子邮件中找到的。从文件名中可以看出,威胁行为者试图欺骗我们相信存档包含包含重要信息的 PDF 文件。使用命令行提取工具ZPAQ后,原来6KB的存档在提取后突然“重”了1GB。在深入研究可执行文件后,发现该文件是具有异步方法的 .NET 可执行文件,并且字节数为零。其中一个指标是叠加部分的 0 熵。在十六进制编辑器中对可执行文件的分析证明,90% 的样本填充了零字节。
Threat actors may prefer to use bloated executable files due to their significant advantage: the inability to upload such files to automatic scanning systems, Virus Total, sandboxes, etc. This technique allows them to bypass traditional security measures and increase the effectiveness of their attack.
威胁参与者可能更喜欢使用臃肿的可执行文件,因为它们具有显着优势:无法将此类文件上传到自动扫描系统、病毒总数、沙盒等。这种技术使他们能够绕过传统的安全措施并提高攻击的有效性。
Sounds like stolen data 听起来像是被盗数据
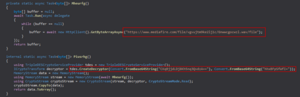
The main function of the unarchived .NET executable is to download a file with .wav extension and decrypt it (3DES algorithm).
未存档的.NET可执行文件的主要功能是下载扩展名为.wav的文件并对其进行解密(3DES算法)。
Waveform Audio File Format (shortened as .wav) is a popular audio file format standard. However, in that case, it is unrelated to audio, and the threat actor simply used this file extension to hide the presence of malicious content. One possible reason is covert communication: using commonly used file extensions disguises the traffic as normal, making it more difficult for network security solutions to detect and prevent malicious activity.
波形音频文件格式(缩写为 .wav)是一种流行的音频文件格式标准。但是,在这种情况下,它与音频无关,威胁参与者只是使用此文件扩展名来隐藏恶意内容的存在。一个可能的原因是隐蔽通信:使用常用的文件扩展名会将流量伪装成正常流量,使网络安全解决方案更难检测和防止恶意活动。
Telegram as C&C 电报作为C&C
Due to the widespread legal usage of Telegram, its traffic is often allowed through firewalls, making it a useful medium for covert communication. Unlike other messaging platforms, Telegram’s API does not require the installation of Telegram software on target devices. Its chat interface simplifies conversation.
由于 Telegram 的广泛合法使用,其流量通常允许通过防火墙,使其成为秘密通信的有用媒介。与其他消息传递平台不同,Telegram 的 API 不需要在目标设备上安装 Telegram 软件。它的聊天界面简化了对话。
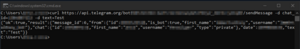
The Telegram API of the threat actor was found among the configuration data of the payload. Unfortunately, it was not possible to retrieve information about the Telegram bot malware because of authorization problems. It can indicate that the token has been already changed, removed, or expired at the moment of the analysis.
在有效负载的配置数据中发现了威胁参与者的 Telegram API。不幸的是,由于授权问题,无法检索有关 Telegram 机器人恶意软件的信息。它可以指示令牌在分析时已被更改、删除或过期。
Another Agent Tesla 另一位特工特斯拉
Agent Tesla is a .NET-based information stealer that emerged around 2014. Over time, it has undergone multiple updates, evolving in terms of both capabilities and evasion techniques. In this specific case, Agent Tesla was obfuscated with the .NET Reactor (my colleague Karsten has done an in depth analysis of this in a video – the link will open in a new window), and several rounds of de-obfuscation were necessary to make the code clearer. The analysis revealed that it possesses the following functions:
特斯拉特工是一个.2014 年左右出现的基于 NET 的信息窃取程序。随着时间的流逝,它经历了多次更新,在功能和规避技术方面都发生了变化。在这个特定案例中,Agent Tesla 被 .NET Reactor 混淆了(我的同事 Karsten 在视频中对此进行了深入分析 – 链接将在新窗口中打开),并且需要进行几轮反混淆以使代码更清晰。分析表明,它具有以下功能:
- targetting sensitive data of around 40 different web browsers
针对大约 40 个不同 Web 浏览器的敏感数据 - stealing credentials from popular email clients
从流行的电子邮件客户端窃取凭据 - screen logging 屏幕记录
- keylogging 键盘记录
- gathering system information
收集系统信息 - capturing sensitive data of VPN tools
捕获VPN工具的敏感数据
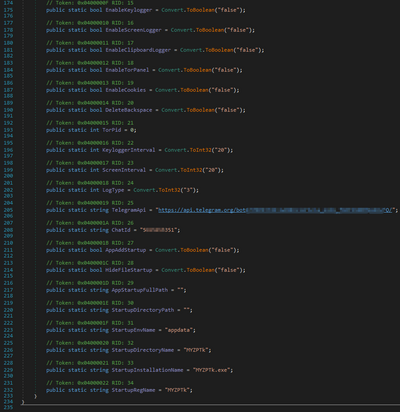
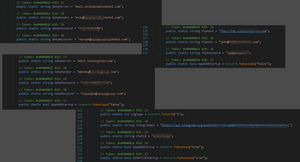
From a capabilities standpoint, it doesn’t offer anything significantly new. However, after analysis of similar samples, all of them have a similar .NET class with configuration data. The way to submit the stolen data, persistence variables, keylogger variable and etc. are kept in this class. Other samples had the same structure, but just different methods to deliver information to the threat actor
从功能的角度来看,它没有提供任何重大的新东西。但是,在分析了类似的示例后,它们都具有具有类似配置数据的 .NET 类。提交被盗数据的方式、持久性变量、键盘记录器变量等都保留在这个类中。其他样本具有相同的结构,但只是向威胁参与者传递信息的方法不同
The way to submit the stolen data, persistence variables, keylogger variable and etc. are kept in this class. Other samples had the same structure, but just different methods to deliver information to the threat actor. It was noticed that besides Telegram, the threat actor uses FTP and SMTP. And the list can be much bigger, because since 30.09.2023 more than 700 versions of this variant were observed on VirusTotal. As is customary in casses like this, the data being used is associated with compromised websites, the accerss credentials to which were likely acquired through an access broker who specializes in selling those types of accounts..
提交被盗数据的方式、持久性变量、键盘记录器变量等都保留在这个类中。其他样本具有相同的结构,但只是向威胁参与者传递信息的方法不同。人们注意到,除了 Telegram 之外,威胁行为者还使用 FTP 和 SMTP。而且列表可能要大得多,因为自 2023 年 9 月 30 日以来,在 VirusTotal 上观察到了该变体的 700 多个版本。按照惯例,使用的数据与受感染的网站相关联,这些网站的访问凭据可能是通过专门销售这些类型帐户的访问经纪人获得的。
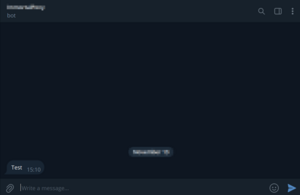
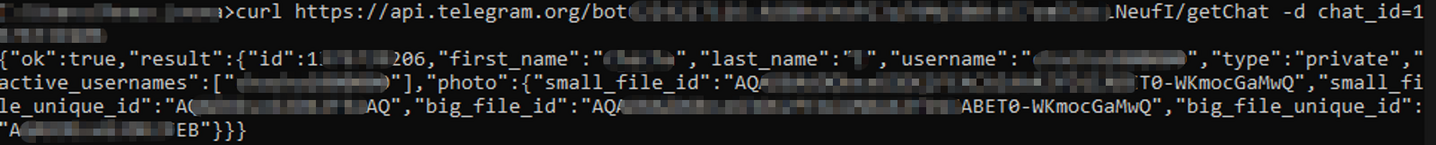
One of the TelegramAPIs from the oldest observed sample is still active. Here the information that was found about this communication channel:
来自最早的观测样本的 TelegramAPI 之一仍处于活动状态。以下是找到的有关此通信渠道的信息:
Takeaways 要点
The usage of the ZPAQ compression format raises more questions than answers. The assumptions here are that either threat actors target a specific group of people who have technical knowledge or use less widely known archive tools, or they are testing other techniques to spread malware faster and bypass security software. However, it is definitely a good example that even very specific archive formats or widely spread file extensions like .wav can be used for malicious purposes.
ZPAQ 压缩格式的使用引发的问题多于答案。这里的假设是,威胁行为者要么针对具有技术知识的特定人群或使用不太广为人知的存档工具,要么他们正在测试其他技术以更快地传播恶意软件并绕过安全软件。但是,这绝对是一个很好的例子,即使是非常具体的存档格式或广泛传播的文件扩展名(如 .wav)也可以用于恶意目的。
Like any other stealer, Agent Tesla can harm not only private individuals but also organizations. It has gained popularity among cybercriminals for many reasons including ease of use, versatility, affordability on the Dark Web, and so on. It is worth mentioning that cybersecurity professionals and organizations are constantly working on developing countermeasures and detection techniques to minimize its effects. To protect your devices, it is essential to have malware protection, maintain a high level of security awareness, and regularly update software.
像任何其他窃取者一样,特斯拉特工不仅可以伤害个人,还可以伤害组织。由于多种原因,它在网络犯罪分子中越来越受欢迎,包括易用性、多功能性、暗网上的可负担性等。值得一提的是,网络安全专业人员和组织一直在努力开发对策和检测技术,以尽量减少其影响。为了保护您的设备,必须具有恶意软件防护、保持高度的安全意识并定期更新软件。
Information for fellow researchers
为其他研究人员提供的信息
ZPAQ archive: ZPAQ存档:
1c33eef0d22dc54bb2a41af485070612cd4579529e31b63be2141c4be9183eb6 – Archive.Trojan-Downloader.AgentTesla.LG5F9Z
.wav file: .wav文件:
c2c466e178b39577912c9ce989cf8a975c574d5febe15ae11a91bbb985ca8d2e – MSIL.Malware.Injector.L8JTF6
c2c466e178b39577912c9ce989cf8a975c574d5febe15ae11a91bbb985ca8d2e – MSIL。恶意软件.Injector.L8JTF6
Agent Tesla: 特工特斯拉:
45dc4518fbf43bf4611446159f72cdbc37641707bb924bd2a52644a3af5bab76 – MSIL.Trojan-Stealer.AgentTesla.B
45dc4518fbf43bf4611446159f72cdbc37641707bb924bd2a52644a3af5bab76 – MSIL。Trojan-Stealer.AgentTesla.B
原文始发于Anna Lvova:New “Agent Tesla” Variant: Unusual “ZPAQ” Archive Format Delivers Malware
转载请注明:New “Agent Tesla” Variant: Unusual “ZPAQ” Archive Format Delivers Malware | CTF导航