
- Cisco Talos has recently observed an increase in activity conducted by 8Base, a ransomware group that uses a variant of the Phobos ransomware and other publicly available tools to facilitate their operations.
思科 Talos 最近观察到 8Base 的活动有所增加,8Base 是一个勒索软件组织,该组织使用 Phobos 勒索软件的变体和其他公开可用的工具来促进其操作。 - Most of the group’s Phobos variants are distributed by SmokeLoader, a backdoor trojan. This commodity loader typically drops or downloads additional payloads when deployed. In 8Base campaigns, however, it has the ransomware component embedded in its encrypted payloads, which is then decrypted and loaded into the SmokeLoader process’ memory.
该组织的大多数 Phobos 变体都是由后门木马 SmokeLoader 分发的。此商品加载程序通常在部署时删除或下载其他有效负载。然而,在 8Base 活动中,它在其加密的有效载荷中嵌入了勒索软件组件,然后将其解密并加载到 SmokeLoader 进程的内存中。 - 8Base’s Phobos ransomware payload contains an embedded configuration which we describe in this blog. Besides this embedded configuration, our analysis did not uncover any other significant differences between 8Base’s Phobos variant and other Phobos samples that have been observed in the wild since 2019.
8Base 的 Phobos 勒索软件有效载荷包含我们在本博客中描述的嵌入式配置。除了这种嵌入式配置之外,我们的分析没有发现 8Base 的火卫一变体与自 2019 年以来在野外观察到的其他火卫一样本之间的任何其他显着差异。 - Our analysis of Phobos’ configuration revealed a number of interesting capabilities, including a user access control (UAC) bypass technique and reporting victim infections to an external URL.
我们对火卫一配置的分析揭示了许多有趣的功能,包括用户访问控制(UAC)绕过技术和向外部URL报告受害者感染。 - Notably, in all samples of Phobos released since 2019 that we analyzed, the same RSA key protected the encryption key. This led us to conclude that attaining the associated private key could enable decryption of all these samples.
值得注意的是,在我们分析的自 2019 年以来发布的所有火卫一样本中,相同的 RSA 密钥保护了加密密钥。这使我们得出结论,获得相关的私钥可以解密所有这些样本。
SmokeLoader’s three stage process to deliver the Phobos payload
SmokeLoader 提供火卫一有效载荷的三阶段过程
We won’t use this space to provide a full overview of SmokeLoader (Malpedia has the basics), but we would like to show how reverse-engineers can reach the final payload. In this example, we’ll use the sample 518544e56e8ccee401ffa1b0a01a10ce23e49ec21ec441c6c7c3951b01c1b19c, but any recent 8base sample will have the same ransomware binary payload in the end. This process requires the execution of the malware in a controlled environment under a debugger like x32dbg.
我们不会利用这个空间来提供 SmokeLoader 的完整概述(Malpedia 有基础知识),但我们想展示逆向工程师如何达到最终有效载荷。在此示例中,我们将使用示例 518544e56e8ccee401ffa1b0a01a10ce23e49ec21ec441c6c7c3951b01c1b19c,但任何最近的 8base 示例最终都将具有相同的勒索软件二进制有效负载。此过程需要在调试器(如 x32dbg)下的受控环境中执行恶意软件。
SmokeLoader malware decrypts its payload in three stages. The first contains many random API calls to obfuscate the execution flow, while the other two involve shellcode stored in allocated memory. The final binary is exposed in the third stage, where a binary copy of the PE (Windows Portable Executable) data in that memory block gives the final payload in its original form.
SmokeLoader 恶意软件分三个阶段解密其有效载荷。第一个包含许多随机 API 调用来混淆执行流程,而另外两个涉及存储在分配的内存中的 shellcode。最终的二进制文件在第三阶段公开,其中该内存块中 PE(Windows 可移植可执行文件)数据的二进制副本以原始形式提供最终有效负载。
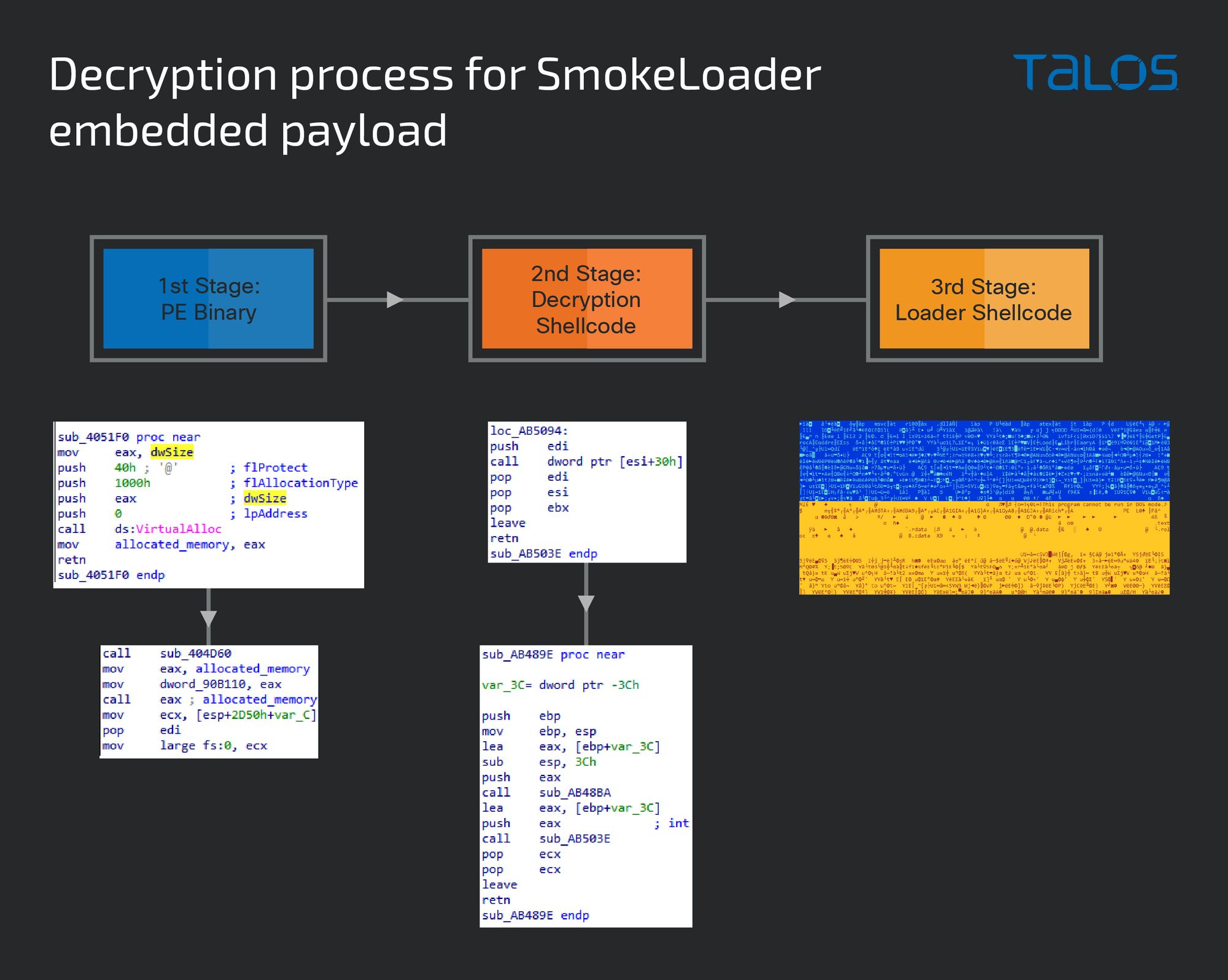
SmokeLoader 嵌入式有效负载的解密过程。
In the first stage, enabling a breakpoint at VirtualAlloc or VirtualProtect and checking its arguments should reveal the address where the next stage will be decrypted. This memory location will then be called at the end of the entry point (EP) function, as shown above.
在第一阶段,在 VirtualAlloc 或 VirtualProtect 处启用断点并检查其参数应显示下一阶段将解密的地址。然后,将在入口点 (EP) 函数的末尾调用此内存位置,如上所示。
On the second-stage shellcode, following the second call in the function called from the entry point leads to the call to the second allocated memory with the third stage. Once the third stage is reached, that memory area should contain the unpacked binary (PE) which can then be exported to a file and analyzed.
在第二阶段 shellcode 上,在从入口点调用的函数中进行第二次调用后,将导致对第三阶段的第二个分配内存的调用。一旦达到第三阶段,该内存区域应包含解压缩的二进制文件(PE),然后可以将其导出到文件并进行分析。
The final payload hash extracted by this method is 32a674b59c3f9a45efde48368b4de7e0e76c19e06b2f18afb6638d1a080b2eb3.
此方法提取的最终有效负载哈希值为 32a674b59c3f9a45efde48368b4de7e0e76c19e06b2f18afb6638d1a080b2eb3。
Overview of features included in the Phobos ransomware
Phobos 勒索软件中包含的功能概述
Our analysis of Phobos uncovered a number of features that enable operators of the ransomware to establish persistence in a targeted system, perform speedy encryption, and remove backups, amongst other capabilities. Phobos is a typical ransomware capable of encrypting files both in local drives as well as network shares. In our FY23 Q2 Talos Incident Response Quarterly Report, we detailed how the 8Base group used their Phobos variant after installing AnyDesk to enable remote access to the machine as well as perform credential dumping via LSASS. These stolen credentials were later used to elevate privileges, exfiltrate data and run the ransomware module.
我们对 Phobos 的分析发现了许多功能,这些功能使勒索软件的运营商能够在目标系统中建立持久性、执行快速加密和删除备份等功能。Phobos 是一种典型的勒索软件,能够加密本地驱动器和网络共享中的文件。在我们的 23 财年第二季度 Talos 事件响应季度报告中,我们详细介绍了 8Base 小组在安装 AnyDesk 后如何使用他们的 Phobos 变体来启用对机器的远程访问以及通过 LSASS 执行凭据转储。这些被盗的凭据后来被用于提升权限、泄露数据和运行勒索软件模块。
Talos has observed the following features present in the malware code:
Talos 观察到恶意软件代码中存在以下特征:
- Full encryption of files below 1.5MB and partial encryption of files above this threshold to improve the speed of encryption. Larger files will have smaller blocks of data encrypted throughout the file and a list of these blocks is saved in the metadata along with the key at the end of the file.
对1.5MB以下的文件进行完全加密,对超过此阈值的文件进行部分加密,以提高加密速度。较大的文件将在整个文件中加密较小的数据块,这些块的列表与文件末尾的密钥一起保存在元数据中。 - Capability to scan for network shares in the local network.
能够扫描本地网络中的网络共享。 - Persistence achieved via Startup folder and Run Registry key.
通过“启动”文件夹和“运行注册表项”实现持久性。 - Generation of target list of extensions and folders to encrypt.
生成要加密的扩展名和文件夹的目标列表。 - Process watchdog thread to kill processes that may hold target files open. This is done to improve the chances the important files will be encrypted.
进程监视器线程以终止可能使目标文件保持打开状态的进程。这样做是为了提高重要文件被加密的机会。 - Disable system recovery, backup and shadow copies and the Windows firewall.
禁用系统恢复、备份和卷影副本以及 Windows 防火墙。 - Embedded configuration with more than 70 options available. This configuration is encrypted with the same AES function used to encrypt files, but using a hardcoded key.
嵌入式配置,提供 70 多个选项。此配置使用用于加密文件的相同 AES 函数进行加密,但使用硬编码密钥。
Based on the analysis of this configuration data, we were able to uncover additional features present in the malware binary which can be enabled by setting specific options. These features have not been documented or have only been superficially mentioned in open source reporting to date:
根据对此配置数据的分析,我们能够发现恶意软件二进制文件中存在的其他功能,这些功能可以通过设置特定选项来启用。到目前为止,这些功能尚未被记录在案,或者只是在开源报告中被肤浅地提及:
- UAC bypass using a .NET profiler DLL loading vulnerability.
UAC 绕过使用 .NET 探查器 DLL 加载漏洞。 - The existence of a debugging file that enables additional features in the malware, illustrated in the following section.
存在一个调试文件,该文件在恶意软件中启用了其他功能,如下一节所示。 - List of blocklisted file extensions that point to names of other groups using the Phobos malware.
指向使用 Phobos 恶意软件的其他组名称的被阻止列表的文件扩展名列表。 - Dynamically imported API calls to avoid behavioral detection by security products.
动态导入API调用,避免安全产品行为检测。 - A hardcoded RSA key used to protect the per-file AES key used in the encryption.
硬编码的 RSA 密钥,用于保护加密中使用的每个文件 AES 密钥。 - Reporting of victim infection to an external URL.
向外部 URL 报告受害者感染情况。 - OS check for Cyrillic language to prevent the malware from running in unwanted environments.
操作系统检查西里尔语,以防止恶意软件在不需要的环境中运行。
We also examined the encryption methodology used by Phobos. Versions of Phobos released after 2019 use a custom implementation of AES-256 encryption, with a different random symmetric key used for each encrypted file, instead of using the Windows Crypto API like earlier variants. Once each file is encrypted, the key used in the encryption along with additional metadata is then encrypted using RSA-1024 with a hardcoded public key, and saved to the end of the file. This algorithm has been documented before, for example in this Malwarebytes post from 2019, and the process still remains the same.
我们还研究了火卫一使用的加密方法。2019 年之后发布的 Phobos 版本使用 AES-256 加密的自定义实现,每个加密文件使用不同的随机对称密钥,而不是像早期变体那样使用 Windows 加密 API。加密每个文件后,加密中使用的密钥以及其他元数据将使用 RSA-1024 和硬编码公钥进行加密,并保存到文件末尾。该算法之前已记录过,例如在 2019 年的 Malwarebytes 帖子中,该过程仍然保持不变。
This makes it extremely unlikely the files can be decrypted by brute force, as each file uses a different key, even though attempts at brute-forcing it have been made in the past. It implies, however, that once the private RSA key is known, any file encrypted by any Phobos variant since 2019 can reliably be decrypted. This fact is supported by an analysis of over a thousand unpacked Phobos samples available on VirusTotal since 2019, where the same public RSA key mentioned above is used.
这使得文件极不可能通过暴力破解,因为每个文件都使用不同的密钥,即使过去曾尝试过暴力破解。然而,这意味着,一旦知道了 RSA 私钥,自 2019 年以来由任何 Phobos 变体加密的任何文件都可以可靠地解密。自 2019 年以来,对 VirusTotal 上提供的一千多个未打包的火卫一样本的分析支持了这一事实,其中使用了上述相同的公共 RSA 密钥。

Talos 分析了自 2019 年以来所有火卫一变体中使用的 RSA 密钥。
Next, we are going to take a deeper look at the configuration file and some of the features it enables.
接下来,我们将更深入地了解配置文件及其启用的一些功能。
Decrypting the Phobos configuration file
解密 Phobos 配置文件
In order to understand how the configuration data is used in Phobos, we analyzed the malicious code in IDA Pro. This allowed us to interact with the configuration data using IDA Python and to decrypt all the configuration data at once. But first, we are going to look at how the configuration data looks in the binary. Once the file is loaded in IDA Pro, one of the first operations we observe being executed by the code is to check its payload and load it into memory:
为了了解配置数据在火卫一中的使用方式,我们分析了 IDA Pro 中的恶意代码。这使我们能够使用 IDA Python 与配置数据进行交互,并一次性解密所有配置数据。但首先,我们将看看配置数据在二进制文件中的样子。在 IDA Pro 中加载文件后,我们观察到代码执行的第一个操作是检查其有效负载并将其加载到内存中:

入口处的代码片段,在内存中设置了 Phobos 配置数据。
In the code above we see the malware initially checking the CRC32 hash of the data in the last section of the PE file. In the case of our sample, this section is named “.cdata” although different samples may use a variation of this name. We have observed samples using “.cdata” and “.sdata”.
在上面的代码中,我们看到恶意软件最初检查 PE 文件最后一部分中数据的 CRC32 哈希值。对于我们的示例,此部分被命名为“.cdata”,尽管不同的示例可能使用此名称的变体。我们观察到使用“.cdata”和“.sdata”的样本。
The data is then loaded into a heap-allocated memory and a structure with pointers to this data is saved to a global variable, named “payoad_struct_addr” in the image above. This structure will be used by the decryption function in order to load requested configuration entries later throughout the code. Each entry has a specific index which is passed as a parameter to the decryption function as we can see in the last code block.
然后,将数据加载到堆分配的内存中,并将带有指向此数据的指针的结构保存到全局变量中,如上图中名为“payoad_struct_addr”。解密函数将使用此结构,以便稍后在整个代码中加载请求的配置条目。每个条目都有一个特定的索引,该索引作为参数传递给解密函数,正如我们在最后一个代码块中看到的那样。
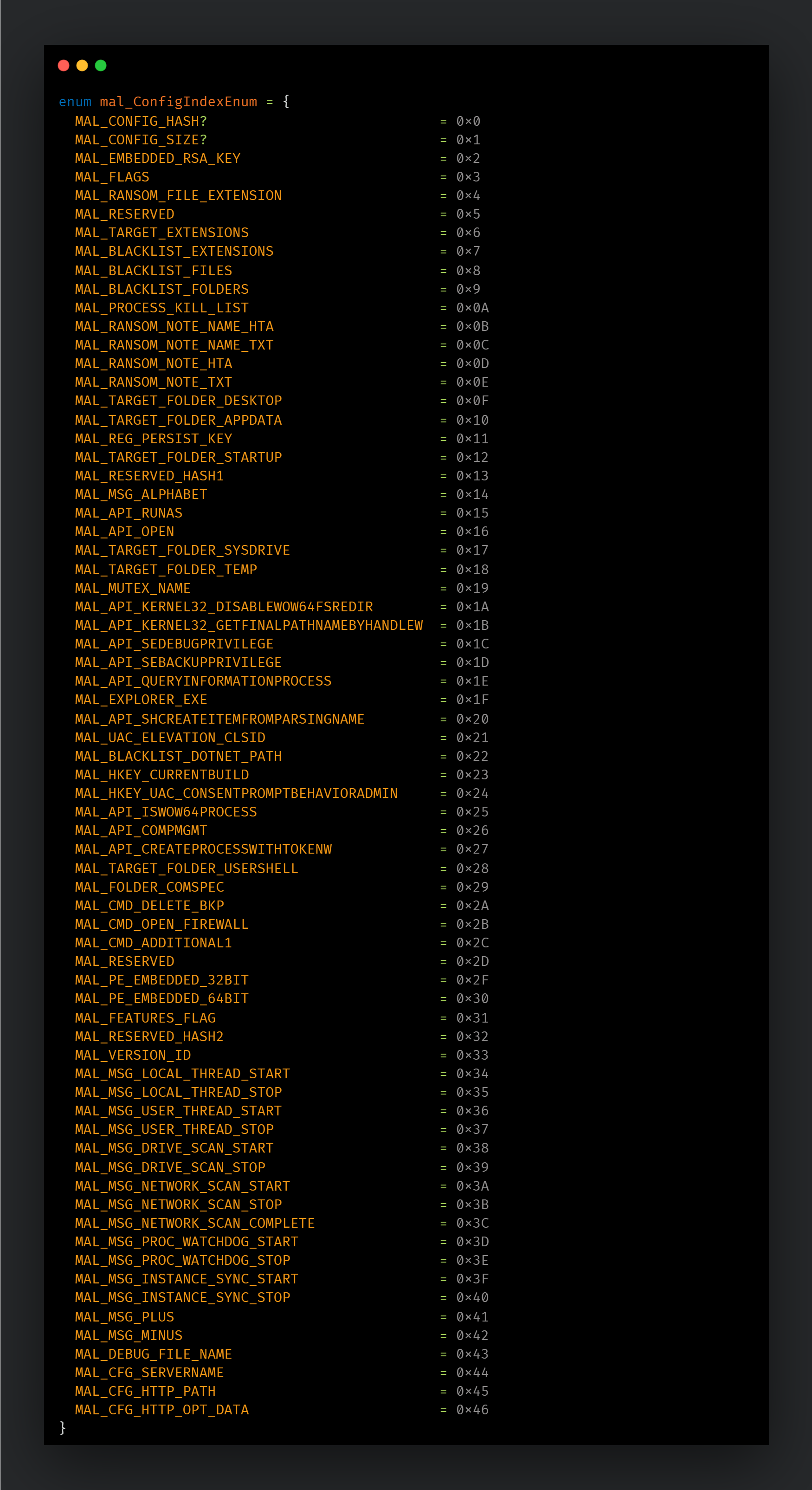
The structure used to handle the configuration data has 48 bytes and is defined as follows:
用于处理配置数据的结构有 48 个字节,定义如下:

存储指向配置数据的指针的结构。
The headers and the actual data are loaded in different buffers allocated in heap memory and pointers to these buffers are saved in the structure, as well as the number of entries in the configuration. The data is followed by a 16-byte AES key used to decrypt the configuration. This key is hardcoded in the binary.
标头和实际数据加载到堆内存中分配的不同缓冲区中,指向这些缓冲区的指针保存在结构中,以及配置中的条目数。数据后跟一个用于解密配置的 16 字节 AES 密钥。此密钥在二进制文件中进行硬编码。
The header contains information to find the encrypted data for each index in the configuration. The structure has 12 bytes and is defined as follows:
标头包含用于查找配置中每个索引的加密数据的信息。该结构有 12 个字节,定义如下:

配置数据中标头条目的结构。
The offset above is relative to the start of the encrypted data buffer starting at 0x00. The index also starts at 0x00 and each index is relatively static for the type of data it contains, which means that for a given index, every sample should have the same type of configuration data in them.
上面的偏移量相对于从 0x00 开始的加密数据缓冲区的开始。索引也从 0x00 开始,对于它所包含的数据类型,每个索引都是相对静态的,这意味着对于给定的索引,每个样本中都应该有相同类型的配置数据。
We have, however, observed that some samples show small changes in the content of their indexes. Since Phobos has been used by many groups in the past, these variations could indicate they are using a different builder or variant. In our analysis of the public samples available in VirusTotal, we found that around 88% of them have 64 configuration entries, while some have as little as 40 and as many as 72 entries.
然而,我们观察到一些样本的指数内容发生了微小的变化。由于火卫一过去曾被许多团体使用过,这些变化可能表明他们正在使用不同的构建器或变体。在我们对 VirusTotal 中可用的公共样本的分析中,我们发现其中大约 88% 的样本有 64 个配置条目,而有些只有 40 个,多达 72 个条目。
Based on our code analysis, we were also able to infer the existence of three additional options used for setting the reporting URL and custom message to be sent back to the attacker. These options were not observed in any sample we analyzed, but the code to handle them is present in all samples. A better look at this feature is shown later in this blog.
根据我们的代码分析,我们还能够推断出存在三个额外的选项,用于设置要发送回攻击者的报告 URL 和自定义消息。在我们分析的任何样本中都没有观察到这些选项,但处理它们的代码存在于所有样本中。本博客稍后将介绍此功能的更好内容。
The decryption function accepts two parameters: an index to the desired entry and a pointer to a buffer that’s used if the entry contains more than four bytes of data. Otherwise, the buffer parameter must be zero.
解密函数接受两个参数:指向所需条目的索引和指向缓冲区的指针,如果条目包含的数据超过四个字节,则使用该缓冲区。否则,buffer 参数必须为零。

解密函数显示对有效负载结构中存在的密钥的AES_Init和AES_Decrypt调用。
The code scans the header buffer for an entry matching the requested index. It then allocates enough memory to store the encrypted data and copies the data to that space, and calls the AES_Init function with the key present at “payload_struct_addr + 0x10”, which is hardcoded in the sample data section. The function AES_Decrypt is then called with the encrypted data and this AES object as a parameter.
该代码扫描标头缓冲区,以查找与请求的索引匹配的条目。然后,它分配足够的内存来存储加密数据并将数据复制到该空间,并使用位于“payload_struct_addr + 0x10”的密钥调用 AES_Init 函数,该密钥在示例数据部分中进行了硬编码。然后,使用加密数据和此 AES 对象作为参数调用函数 AES_Decrypt。
Automating the configuration decryption with IDA Pro
Once the decryption algorithm is understood, it is easy to automate the decryption of every entry in the configuration and output the details to a file. IDA Pro allows the use of Python to automate tasks inside the application, and we decided to use the Flare-Emu Python module to emulate the malware’s AES routines instead of re-implementing the code in Python.
Since the decryption function requires only two parameters and is therefore fairly independent, we decided to start the emulation from that point, creating a structure similar to what the malware does for the payload data:
eh=flare_emu.EmuHelper()
conf_struct=eh.allocEmuMem(0x30)
header_data=eh.allocEmuMem(header_size)
config_data=eh.allocEmuMem(config_size)
Then populating this structure with the appropriate values:
然后用适当的值填充此结构:
eh.writeEmuPtr(conf_struct,header_data)
eh.writeEmuPtr(conf_struct+4,config_entries)
eh.writeEmuPtr(conf_struct+8,config_data)
eh.writeEmuPtr(conf_struct+0xc,config_size)
eh.writeEmuMem(conf_struct+0x10,AES_Init_key_struct)
# load buffers
eh.writeEmuMem(header_data,eh.getEmuBytes(enc_data_start+0x8, header_size))
eh.writeEmuMem(config_data,eh.getEmuBytes(config_start,config_size))
# write addr of struct back to code
eh.writeEmuPtr(eh.analysisHelper.getNameAddr(CFG_STRUCT_NAME), conf_struct)
Once the structure is created, we can walk through each entry in the header and prepare the emulator stack and call the emulation starting at the decryption function:
创建结构后,我们可以遍历标头中的每个条目,并准备模拟器堆栈,并从解密函数开始调用仿真:
if entry_size<=4:
buffer=0
else:
buffer=eh.allocEmuMem(entry_enc_size)
myStack = [0xffffffff, entry_idx, buffer]
eh.emulateRange(eh.analysisHelper.getNameAddr(DECRYPT_FN), stack = myStack, skipCalls=False)
The resulting decrypted data will be present in the EAX register if it’s four bytes or less, or in the allocated buffer if larger. After our analysis of the samples found in the wild, we found the following types of configuration entries:
生成的解密数据将出现在 EAX 寄存器中(如果为四个字节或更少),或者如果更大,则出现在分配的缓冲区中。在对野外发现的样本进行分析后,我们发现了以下类型的配置条目:
UAC bypass technique UAC 旁路技术
To execute its main objective of encrypting as many files from the victim machine as possible, a ransomware needs to be executed with elevated privileges so it can access all files on disk as well as disable important system services which may hinder its objective. Elevating process privileges usually causes a warning to be displayed to the user and may prevent the malware from running. To bypass that message, many malicious programs use an UAC bypass or exploits to elevate its own process privileges.
为了实现其从受害机器加密尽可能多的文件的主要目标,勒索软件需要以提升的权限执行,以便它可以访问磁盘上的所有文件,并禁用可能阻碍其目标的重要系统服务。提升进程权限通常会导致向用户显示警告,并可能阻止恶意软件运行。为了绕过该消息,许多恶意程序使用 UAC 绕过或利用来提升自己的进程权限。
The Phobos binary contains code that performs UAC bypass using a vulnerability in the .Net Profiler DLL loading process while executing “compmgmt.msc”. This technique has been documented since at least 2017 but still works in the latest version of Windows 10.
Phobos 二进制文件包含代码,该代码在执行“compmgmt.msc”时利用 .Net Profiler DLL 加载过程中的漏洞执行 UAC 绕过。此技术至少自 2017 年以来就已记录在案,但在最新版本的 Windows 10 中仍然有效。
Note: Even though the malware contains code to bypass UAC and the exploit works when executed, this only happens once we force the execution to follow that specific code branch and is not being actively used by the malware. The code path leading to this specific function seems to be reachable only when specific parameters are present in the malware configuration. Since Phobos is generally distributed along other malware and only after the actors are able to extract all the information they need, it’s possible the UAC code is not used because it’s not needed at the point in time the actors decide to encrypt the files.
注意:即使恶意软件包含绕过 UAC 的代码,并且漏洞利用在执行时有效,但只有当我们强制执行遵循该特定代码分支并且恶意软件未主动使用时,才会发生这种情况。只有当恶意软件配置中存在特定参数时,才能访问指向此特定函数的代码路径。由于 Phobos 通常与其他恶意软件一起分发,并且只有在参与者能够提取他们需要的所有信息之后,才可能不使用 UAC 代码,因为在参与者决定加密文件的时间点不需要它。
In this method, a DLL is dropped to a user-writable folder and the environment variables are modified to make the .Net profiler load the file even in elevated processes. In the case of Phobos, the configuration file stores a small 2KB DLL file that only contains code to create a new process with the malicious binary. Both 32- and 64-bit files are embedded in the configuration.
在此方法中,将 DLL 拖放到用户可写的文件夹中,并修改环境变量,使 .Net 探查器即使在提升的进程中也能加载文件。在火卫一的情况下,配置文件存储一个 2KB 的小 DLL 文件,该文件仅包含使用恶意二进制文件创建新进程的代码。32 位和 64 位文件都嵌入在配置中。

用于从提升的进程启动恶意二进制文件的代码。
The DLL is written to the %TEMP% folder using the machine serial number as its name like this: C:\Users\User\AppData\Local\Temp\1E41F172.
DLL 使用计算机序列号作为其名称写入 %TEMP% 文件夹,如下所示:C:\Users\User\AppData\Local\Temp\1E41F172。
The DLLs embedded in the configuration data do not represent a complete PE, containing only the data up to the import table present right after the “CALL [EAX]” shown above. The PE file is extracted from the configuration and fixed in memory before it is written to disk. The path to the malware binary is written to the file right after the import table, and will be used by the code as one of the parameters to “CreateProcessW”. The section is then finalized until the section alignment with the bytes 0xBAADF00D:
嵌入在配置数据中的 DLL 并不表示完整的 PE,仅包含截至导入表的数据,该表紧跟在上面所示的“CALL [EAX]”之后。PE 文件从配置中提取并固定在内存中,然后再写入磁盘。恶意软件二进制文件的路径将紧跟在导入表之后写入文件,并由代码用作“CreateProcessW”的参数之一。然后完成该部分,直到该部分与字节对齐0xBAADF00D:

在内存中修复之前和之后的 64 位示例的比较视图。配置中的 PE 文件紧跟在导入表之后。
The code will then call ShCreateItemFromParsingName using “Elevation:Administrator!new:{3ad05575-8857-4850-9277-11b85bdb8e09}” as a parameter in order to create an elevated shell object which will later be used to initialize the .Net environment before executing the Computer Management tool via mmc.exe.
然后,代码将使用“Elevation:Administrator!new:{3ad05575-8857-4850-9277-11b85bdb8e09}”作为参数调用 ShCreateItemFromParsingName,以便创建提升的 shell 对象,该对象稍后将用于在通过 mmc.exe 执行计算机管理工具之前初始化 .Net 环境。
Once the exploit is successful, a new instance of the malware binary is started with high privileges:
一旦利用成功,就会以高权限启动恶意软件二进制文件的新实例:

显示具有高完整性和完全提升权限的新进程的进程信息。
The process tree is also worth noting, as it is not typical to have MMC.EXE starting unknown binaries, as shown in the example below:
进程树也值得注意,因为通常不会让 MMC.EXE 启动未知的二进制文件,如下面的示例所示:

进程树显示从 mmc.exe 启动的勒索软件进程。
Phobos’ hidden debug file feature
Phobos的隐藏调试文件功能
One of Phobos’ hidden abilities we found in the configuration data is support for a debug file which can be used to enable additional features in the binary. At the beginning of the code, Phobos checks for the presence of a file name at index 0x43 in the configuration. If the setting is present, it will then check if the file exists in the same folder and if it contains valid arguments:
我们在配置数据中发现的 Phobos 的隐藏功能之一是支持调试文件,该文件可用于启用二进制文件中的其他功能。在代码的开头,Phobos 会检查配置中索引0x43处是否存在文件名。如果存在该设置,它将检查文件是否存在于同一文件夹中,以及它是否包含有效参数:

Phobos 检查是否存在调试文件。
If the debug file exists, Phobos will parse each line to see if they contain valid commands and will create a structure containing the flags and string parameters found after the commands. In the 8Base campaign, the name of this file is “suppo” but other groups use different names for the debug file or don’t have one set up at all.
如果调试文件存在,Phobos 将解析每一行以查看它们是否包含有效的命令,并将创建一个包含命令后找到的标志和字符串参数的结构。在 8Base 活动中,此文件的名称为“suppo”,但其他组对调试文件使用不同的名称,或者根本没有设置。
Based on our code analysis, the following commands are available for debugging:
根据我们的代码分析,以下命令可用于调试:
- ‘C’ or ‘c’: Shows a console to print debug strings.
“C”或“c”:显示用于打印调试字符串的控制台。 - ‘L’: Outputs a log file name. This name will be prefixed by “e-” to indicate the process is running elevated. For a typical process tree with a low privilege malware running an elevated process, two files will be created: “filename” and “e-filename”.
“L”:输出日志文件名。此名称将以“e-”为前缀,以指示进程正在提升运行。对于运行提升进程的低权限恶意软件的典型进程树,将创建两个文件:“filename”和“e-filename”。 - ‘M’ or ‘m’: Does not run the encryption loop. This option disables the malicious actions and causes the malware to jump to the end of the code.
“M”或“m”:不运行加密循环。此选项禁用恶意操作,并导致恶意软件跳转到代码末尾。 - ‘n’: Sets a flag in the buffer.
‘n’:在缓冲区中设置标志。 - ‘e’: Accepts a string of values separated by ‘;’ and stores a pointer to the data in the buffer structure.
‘e’:接受以 ‘; 分隔的字符串值,并将指向数据的指针存储在缓冲区结构中。 - ‘s’: Sets a flag in the buffer.
‘s’:在缓冲区中设置标志。 - ‘x’: Sets a flag in the buffer.
‘x’:在缓冲区中设置标志。
While some of these commands can be derived from analysis of the code, Talos never found an actual sample of these debug files to compare with our analysis, so some of the commands are not yet completely understood.
虽然其中一些命令可以从代码分析中派生出来,但 Talos 从未找到这些调试文件的实际样本来与我们的分析进行比较,因此某些命令尚未完全理解。
When the options for showing the console are present in the debug file, this is what is output by the malware during typical execution:
当用于显示控制台的选项出现在调试文件中时,这是恶意软件在典型执行期间输出的内容:

Phobos 调试文件设置创建的调试控制台和日志文件。
In the example above, we have enabled the Console display (command ‘c’) and log file (command ‘L’) and we can see the messages printed to the console. It shows the victim identification (the string “[1E41F172-3483]”) as well as the build number “v2.9.1”. All the strings shown in the output are also present as settings in the configuration, which indicates these messages can be customized by the threat actors behind each campaign.
在上面的示例中,我们启用了控制台显示(命令“c”)和日志文件(命令“L”),我们可以看到打印到控制台的消息。它显示受害者身份(字符串“[1E41F172-3483]”)以及内部版本号“v2.9.1”。输出中显示的所有字符串也作为设置出现在配置中,这表明这些消息可以由每个活动背后的威胁参与者自定义。
Phobos’ infection reporting capabilities
火卫一的感染报告能力
While Phobos does not typically demonstrate reporting a new infection to the attacker, our analysis indicates the capability to do so is present in the code, hidden behind a configuration setting which enables this feature and the creation of a custom URL and message chosen by the attacker.
虽然 Phobos 通常不会向攻击者报告新的感染,但我们的分析表明,这样做的能力存在于代码中,隐藏在启用此功能的配置设置后面,并创建攻击者选择的自定义 URL 和消息。
The configuration setting with index “0x31” is a flag used throughout the code to check if various features are enabled or not. If the reporting capability is enabled, the malware will attempt to extract the server name, URI path and custom message from indexes 0x44, 0x45 and 0x46 respectively:
索引为“0x31”的配置设置是整个代码中使用的标志,用于检查是否启用了各种功能。如果启用了报告功能,恶意软件将尝试分别从索引 0x44、0x45 和 0x46中提取服务器名称、URI 路径和自定义消息:

Phobos 代码检查配置中是否存在报告 URL。
If these options are present, the malware will then attempt to communicate an alert of the infection back to the specified server. The custom message mentioned above is a string parameter which may contain the tag “<<ID>>” in its body. This tag will then be replaced by the victim ID before submitting the request. As shown in the example below, the original message extracted from the binary still has the tag and the parsed message with the victim ID is passed as parameter to the HTTP Post function:
如果存在这些选项,恶意软件将尝试将感染警报传回指定的服务器。上面提到的自定义消息是一个字符串参数,其正文中可能包含标签“<>”。然后,在提交请求之前,此标签将被受害者 ID 替换。如下例所示,从二进制文件中提取的原始消息仍然具有标记,并且带有受害者 ID 的解析消息将作为参数传递给 HTTP Post 函数:

在解析 ID 后显示 HTTP POST 请求的参数的代码摘录。
The request is sent with almost no headers, as seen in this example:
发送请求时几乎没有标头,如下例所示:

如果在配置中启用了 POST 请求,则将请求发送回攻击者。
It is worth noting, however, Talos has not seen any threat actor use this feature in any sample analyzed thus far.
然而,值得注意的是,到目前为止,Talos 尚未在分析的任何样本中看到任何威胁行为者使用此功能。
Analysis of code changes in Phobos binaries over time
分析 Phobos 二进制文件中随时间变化的代码变化
Since 8Base group is known to operate with characteristics similar to previous Phobos campaigns, we compared the code in an 8Base sample with previous Phobos variants and determined there are no differences between the code at the binary level at all. As we mentioned above, this 8Base sample, 32a674b59c3f9a45efde48368b4de7e0e76c19e06b2f18afb6638d1a080b2eb3, was extracted from a SmokeLoader binary deployed in a recent 8Base campaign seen between June and August 2023.
由于已知 8Base 组具有与以前的 Phobos 活动相似的特征,因此我们将 8Base 样本中的代码与以前的 Phobos 变体进行了比较,并确定二进制级别的代码之间根本没有差异。如上所述,这个 8Base 样本 32a674b59c3f9a45efde48368b4de7e0e76c19e06b2f18afb6638d1a080b2eb3 是从 2023 年 6 月至 8 月期间最近一次 8Base 活动中部署的 SmokeLoader 二进制文件中提取的。
In their February 2023 post about brute-forcing Phobos encryption, the Computer Emergency Response Team from Poland (Cert-PL) looked at sample 2704e269fb5cf9a02070a0ea07d82dc9d87f2cb95e60cb71d6c6d38b01869f66 which was first observed in VirusTotal in 2020. Their observations about how the encryption works had many similarities with the 8Base sample we analyzed, and our analysis revealed that there were no changes in the code at all, with 100% carryover of samples’ functions and basic blocks.
在 2023 年 2 月关于暴力破解 Phobos 加密的帖子中,来自波兰的计算机应急响应小组 (Cert-PL) 查看了样本 2704e269fb5cf9a02070a0ea07d82dc9d87f2cb95e60cb71d6c6d38b01869f66,该样本于 2020 年在 VirusTotal 中首次观察到。他们对加密工作原理的观察与我们分析的 8Base 样本有许多相似之处,我们的分析表明代码根本没有变化,样本的函数和基本块 100% 残留。
The only thing that changes between these two binaries is the configuration data in the last PE section:
这两个二进制文件之间唯一更改的是最后一个 PE 部分中的配置数据:
|
8Base 8基地 |
Phobos Cert PL 火卫一证书PL |
|
|
Configuration Entries 配置条目 |
64 |
64 |
|
Encryption key 加密密钥 |
0xea73000e61c749e5287a2407e44c8679 |
0x591abb0fe93e56e0d8c8fd2d6019f995 |
|
File extension (IDX 0x4) 文件扩展名 (IDX 0x4) |
.id[<>-3483].[[email protected]].8base |
.id[<>-2378].[[email protected]].Barak |
|
Debug file (IDX 0x43) 调试文件 (IDX 0x43) |
suppo 苏波 |
egvtethyr576.txt |
|
Extension Blocklist (IDX 0x7) |
8base;actin;DIKE;Acton;actor;Acuff;FILE;Acuna;fullz;MMXXII;6y8dghklp;SHTORM;NURRI;GHOST;FF6OM6;MNX;BACKJOHN;OWN;FS23;2QZ3;top;blackrock;CHCRBO;G-STARS;faust;unknown;STEEL;worry;WIN;duck;fopra;unique;acute;adage;make;Adair;MLF;magic;Adame;banhu;banjo;Banks;Banta;Barak;Caleb;Cales;Caley;calix;Calle;Calum;Calvo;deuce;Dever;devil;Devoe;Devon;Devos;dewar;eight;eject;eking;Elbie;elbow;elder;phobos;help;blend;bqux;com;mamba;KARLOS;DDoS;phoenix;PLUT;karma;bbc;CAPITAL;WALLET;LKS;tech;s1g2n3a4l;MURK;makop;ebaka;jook;LOGAN;FIASKO;GUCCI;decrypt;OOH;Non;grt;LIZARD;FLSCRYPT;SDK;2023;vhdv |
Barak;actin;Acton;actor;Acuff;Acuna;acute;adage;Adair;Adame;banhu;banjo;Banks;Banta;Barak;Caleb;Cales;Caley;calix;Calle;Calum;Calvo;deuce;Dever;devil;Devoe;Devon;Devos;dewar;eight;eject;eking;Elbie;elbow;elder;phobos;help;blend;bqux;com;mamba;KARLOS;DDoS;phoenix;PLUT;karma;bbc;CAPITAL;WALLET; |
The same holds true for other samples found since 2020. The differences in code start to appear when we compare the 8Base sample with Phobos variants created in 2019. We analyzed the sample fc4b14250db7f66107820ecc56026e6be3e8e0eb2d428719156cf1c53ae139c6 first seen in VirusTotal in August 2019. The current 8Base sample shares 89.6% of its code with the 2019 sample, according to our analysis.
自 2020 年以来发现的其他样本也是如此。当我们将 8Base 样本与 2019 年创建的 Phobos 变体进行比较时,代码的差异开始出现。我们分析了样本fc4b14250db7f66107820ecc56026e6be3e8e0eb2d428719156cf1c53ae139c6,该样本于2019年8月首次出现在VirusTotal。根据我们的分析,当前的 8Base 样本与 2019 年的样本共享 89.6% 的代码。
There are several functions present in the current 8Base sample that did not exist in 2019:
当前 8Base 示例中存在几个函数,这些函数在 2019 年不存在:

8Base 样本中存在但 2019 样本中没有的函数列表。
There is now support for debug files and infection report capabilities, which are not present in the old samples. This implies these features were added to Phobos source code at some point in 2019 or 2020, likely the last time the Phobos source code was updated.
现在支持调试文件和感染报告功能,这些功能在旧示例中不存在。这意味着这些功能是在 2019 年或 2020 年的某个时候添加到火卫一源代码中的,这可能是最后一次更新火卫一源代码。
Another sample that caught our attention was first described by Malwarebytes in 2019. The sample, a91491f45b851a07f91ba5a200967921bf796d38677786de51a4a8fe5ddeafd2, was first observed in the wild in May 2019. This sample is considerably different from other samples from the same time frame, only sharing 47.2% of their code.
另一个引起我们注意的样本是 Malwarebytes 在 2019 年首次描述的。样本为a91491f45b851a07f91ba5a200967921bf796d38677786de51a4a8fe5ddeafd2,于2019年5月首次在野外观察到。此示例与同一时间范围内的其他示例有很大不同,仅共享其代码的 47.2%。

8base 样本与 Malwarebytes 博客中的 2019 年样本相比.
The main difference we observed in this sample is the usage of Windows Crypto API instead of the custom cryptographic code from recent samples. Looking at the functions present in the 2019 sample, we can see the Crypto API imported by this sample:
在此示例中观察到的主要区别是使用 Windows 加密 API,而不是最近示例中的自定义加密代码。查看 2019 示例中存在的函数,我们可以看到此示例导入的加密 API:

Malwarebytes 分析的 2019 年示例中导入的函数列表。
We observed these APIs being used in some critical functions throughout the code. The code block below is related to the encryption/decryption function in 8Base, which uses the custom cryptographic library, versus the code in the 2019 sample which uses Windows Crypto API
我们观察到这些 API 在整个代码中的一些关键函数中使用。下面的代码块与 8Base 中的加密/解密函数相关,该函数使用自定义加密库,而 2019 示例中的代码使用 Windows 加密 API

8Base与旧版2019 Phobos样本的文件加密功能比较。
There are similar differences in the function used to decrypt the configuration file, which behaves in a related fashion but using different cryptographic APIs.
用于解密配置文件的函数也存在类似的差异,其行为方式相同,但使用不同的加密 API。
These changes observed in early samples support the assumption that Phobos went through a development phase in 2019 but has remained unchanged since then.
在早期样本中观察到的这些变化支持了火卫一在2019年经历了发展阶段的假设,但此后一直保持不变。
In our second post titled “Understanding the Phobos affiliate structure and activity “, we will have additional information on the data we found in the blocklist extensions and how this is mapped to different actor groups, as well as the behavior of such groups once they get into a victim’s network.
在我们的第二篇题为“ 了解火卫一附属结构和活动 ”,我们将提供有关我们在阻止列表扩展中发现的数据以及如何将其映射到不同参与者群体的更多信息,以及这些群体一旦进入受害者网络的行为。
Coverage 覆盖

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
思科安全终端(以前称为面向终端的AMP)非常适合防止执行本文中详述的恶意软件。 在此处免费试用安全终端。
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
思科安全网络设备 Web 扫描可防止访问恶意网站,并检测这些攻击中使用的恶意软件。
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
思科安全邮件(以前称为思科邮件安全)可以阻止威胁行为者在其活动期间发送的恶意电子邮件。您可以在此处免费试用 Secure Email。
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Firewall(以前称为下一代防火墙和 Firepower NGFW)设备(如 Threat Defense Virtual、Adaptive Security Appliance 和 Meraki MX)可以检测与此威胁相关的恶意活动。
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
思科安全恶意软件分析 (Threat Grid) 可识别恶意二进制文件,并在所有思科安全产品中构建保护。
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Umbrella 是思科的安全互联网网关 (SIG),可阻止用户连接到恶意域、IP 和 URL,无论用户是在公司网络上还是在公司网络外。在此处注册免费试用 Umbrella。
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
思科网络安全设备(以前称为网络安全设备)会自动阻止潜在危险站点,并在用户访问可疑站点之前对其进行测试。
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
可从 Firewall Management Center 获得与特定环境和威胁数据相关的其他保护。
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Cisco Duo 为用户提供多因素身份验证,以确保只有获得授权的用户才能访问您的网络。
ClamAV detections are available for this threat:
ClamAV 检测可用于此威胁:
Win.Packed.Zusy Win.Packed.Zusy(温.Packed.Zusy)
Win.Ransomware.8base
Win.Downloader.Generic Win.Downloader.通用
Win.Ransomware.Ulise Win.勒索软件.Ulise
IOCs 国际奥委会
Indicators of Compromise associated with this threat can be found here.
可以在此处找到与此威胁相关的入侵指标。
原文始发于Guilherme Venere:A deep dive into Phobos ransomware, recently deployed by 8Base group
转载请注明:A deep dive into Phobos ransomware, recently deployed by 8Base group | CTF导航