Bug in Honda, Nissan, Toyota Cars App Let Hackers Unlock & Start The Car Remotely

A critical vulnerability uncovered in Honda, Nissan, Infiniti, and Acura vehicle apps lets hackers and law enforcement agencies unlock the car remotely and start the vehicle with a laptop from anywhere in the world.
The critical bug exists in SiriusXM, a connected vehicle platform that offers services to services to Acura, BMW, Honda, Hyundai, Infiniti, Jaguar, Land Rover, Lexus, Nissan, Subaru, and Toyota.

During routine research, Sam Curry, a Web application security researcher, and his team found a critical vulnerability in the connected vehicle’s remote management service that has enrolled with SiriusXM mobile apps.
The research has not only highlighted how one vulnerability could have a physical effect on a huge number of cars but also how much personal data can be retrieved from a vehicle.
Investigation Towards Finding the Bug
A Domain “http://telematics(.)net” was found in this research and is associated with enrolling vehicles in the SiriusXM remote management functionality.
Further analysis of this domain reveals that a large number of references are pointed to the Nissan Car Connected App.
Later move ahead to log in to the app and inspect the HTTPS traffic from one of the Nissan car owners.
During the scan, researchers found that there was one HTTP request, in particular, that was interesting: the “exchangeToken” endpoint would return an authorization bearer dependent on the provided “customerId”.


In the above HTTPS request, a VIN” parameter was removed and still works, in another hand, the request gets failed if the other things “nissancust” prefix and “Cv-Tsp” header will be changed.
Pull the Customer Data Out
“Further analysis of one of the HTTP responses researchers saw the following format of a VIN number: vin:5FNRL6H82NB044273, This VIN format looked eerily similar to the “nissancust” prefix from the earlier HTTP request. What if we tried sending the VIN prefixed ID as the customerId?” The researcher said in his tweet.
Through passing the VPN prefixed ID as a customerID, researchers get a bearer Toke return along with “200 OK” response of the following:

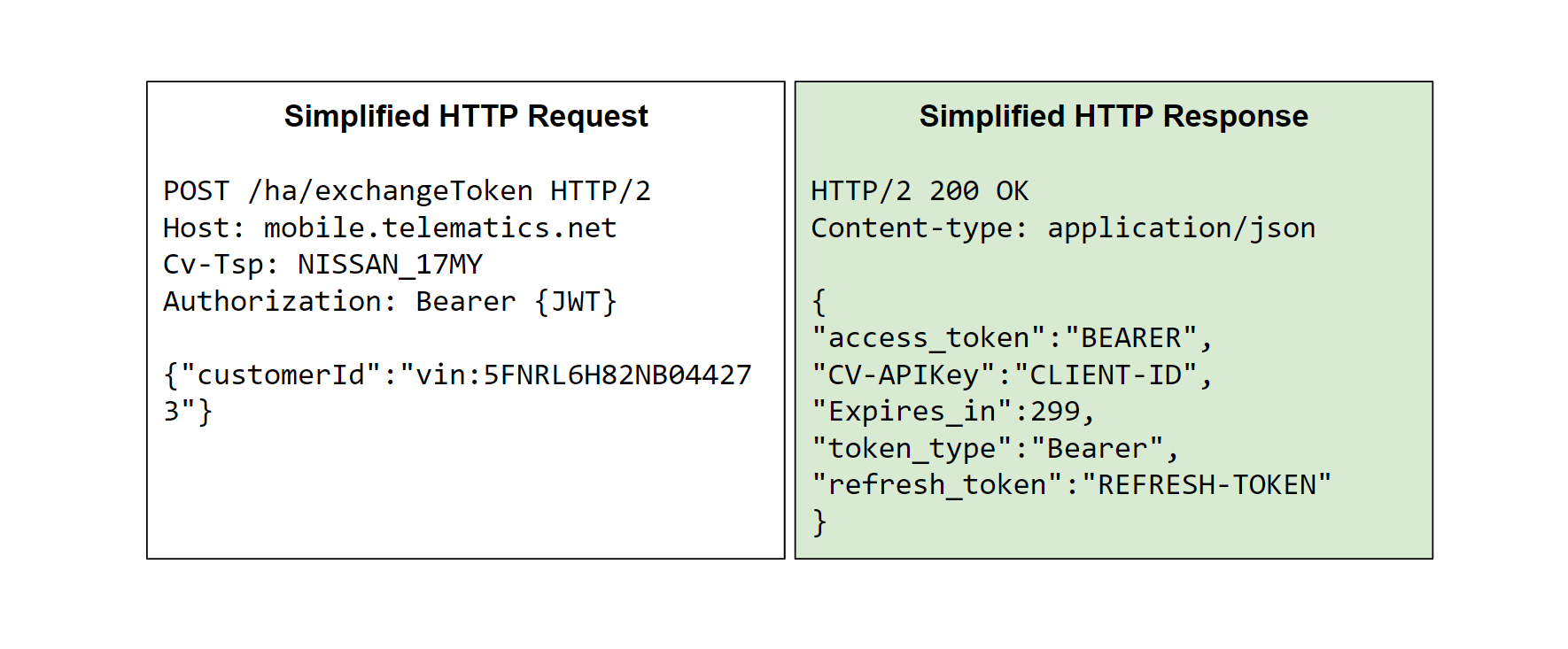
“This was exciting, we were generating some token and it was indexing the arbitrary VIN as the identifier. To make sure this wasn’t related to our session JWT, we completely dropped the Authorization parameter and it still worked!”
To fetch the user profile, researchers attempt to use the Authorization bearer in an HTTP request, in response, they have successfully retrieved the victim’s name, phone number, address, and car details.

By only having the VIN number, any attackers can fetch the customer details with the help of a python script and a continuous escalation lead researchers to find the HTTP request to run vehicle commands.
Eventually, at this point, attackers will access customer information and run vehicle commands to unlock the vehicle and start the car remotely.
Researchers have successfully tested this bug on Honda, Infiniti, and Acura vehicles in addition to Nissan vehicles and reported the issue to SiriusXM who fixed it immediately.
转载请注明:Bug in Honda, Nissan, Toyota Cars App Let Hackers Unlock & Start The Car Remotely | CTF导航
