
Long time no hear in terms of Evilginx updates. While I’m still working on the release of Evilginx Pro, I’ve decided to fix a few issues and add new features to the public version of Evilginx, in the meantime.
好久没有听到 Evilginx 更新的消息。虽然我仍在努力发布 Evilginx Pro,但同时我决定修复一些问题并为 Evilginx 的公共版本添加新功能。
First of all, I wanted to thank everyone for the great feedback and insightful discussions in the BREAKDEV RED community Discord. All of the reported issues and suggestions led to the improvement of Evilginx and this update is the fruit of such great community feedback.
首先,我要感谢大家在 BREAKDEV RED 社区 Discord 上的精彩反馈和有见地的讨论。所有报告的问题和建议都导致了 Evilginx 的改进,而这次更新是社区反馈的成果。
Additionally, I wanted to use this opportunity to thank everyone for sending their applications to access BREAKDEV RED. We’ve gathered an incredible number of security professionals (almost 850 at the time of writing) and every day I’m learning something new from you guys, which I’m super grateful for. Hell, I’ve even finally fully understood how to properly configure the SPF/DKIM/DMARC combo thanks to all the discussion on the subject.
此外,我想借此机会感谢大家发送他们的应用程序以访问 BREAKDEV RED。我们聚集了数量惊人的安全专业人员(在撰写本文时将近 850 人),每天我都在从你们那里学到新东西,我对此非常感激。见鬼,我什至终于完全理解了如何正确配置 SPF/DKIM/DMARC 组合,这要归功于关于该主题的所有讨论。
Vetting the applications takes a lot of time and before I open the registrations again, to the public, I’d like to automate the verification process a bit. Once I do this, requesting access to the community should be more accessible to everyone.
审查申请需要花费大量时间,在我再次向公众开放注册之前,我想将验证过程自动化一点。一旦我这样做了,每个人都应该更容易访问请求访问社区。
Allowing access only to red teamers with a clean conscience is still of utmost importance to me and it is the base for creating a friendly atmosphere, which fuels guilt-free information sharing.
只允许问心无愧的红队员进入对我来说仍然至关重要,这是创造友好氛围的基础,从而促进了无罪的信息共享。
This time I have something special for you. Never before have I had a request so popular that it was mentioned in 90% of all BREAKDEV RED application forms. Let it be known that your pleas have been heard.
这次我给你准备了一些特别的东西。我以前从未有过如此受欢迎的请求,以至于在所有 BREAKDEV RED 申请表中都有 90% 的请求被提及。让大家知道你的恳求已经被听到了。
Evilginx has an official integration with GoPhish by Jordan Wright from now on!
从现在开始,Evilginx 与 Jordan Wright 的 GoPhish 正式集成!
That’s right – you will finally be able to create phishing campaigns for sending emails with valid Evilginx lure URLs and enjoy all the benefits of GoPhish’s lovely UI, seeing which emails were opened, which lure URLs were clicked and which clicks resulted in successful session capture.
没错 – 您最终将能够创建网络钓鱼活动,以发送带有有效 Evilginx 诱饵 URL 的电子邮件,并享受 GoPhish 可爱的 UI 的所有好处,查看哪些电子邮件被打开,哪些诱饵 URL 被点击,哪些点击导致会话捕获成功。
Here is the full list of changes coming in Evilginx 3.3 together with a full guide on how to use all the new features.
以下是 Evilginx 3.3 中的完整更改列表,以及有关如何使用所有新功能的完整指南。
GoPhish Support GoPhish 支持
I’ve forked GoPhish and added the integration with Evilginx in the cleanest way possible. If you were using your custom version of GoPhish, merging Evilginx integration with your own fork should be relatively easy.
我已经分叉了GoPhish,并以最干净的方式添加了与Evilginx的集成。如果您使用的是自定义版本的 GoPhish,那么将 Evilginx 集成与您自己的分叉合并应该相对容易。
I have made the integration in such a way that Evilginx will be notifying GoPhish of the following events, which occur:
我以这样一种方式进行了集成,即 Evilginx 将通知 GoPhish 发生以下事件:
- A hidden image tracker is triggered when the email is opened. The tracker image is just a lure URL with specific parameters to let Evilginx know it should be used as a tracker.
打开电子邮件时,会触发隐藏的图像跟踪器。跟踪器图像只是一个带有特定参数的诱饵 URL,让 Evilginx 知道它应该用作跟踪器。 - A phishing link is clicked within the email message. The phishing link within the email message sent through GoPhish is just the lure URL with embedded parameters.
在电子邮件中单击网络钓鱼链接。通过GoPhish发送的电子邮件中的网络钓鱼链接只是带有嵌入参数的诱饵URL。 - The session is successfully captured with Evilginx. Once Evilginx gathers the credentials and logs the cookies, it will notify GoPhish that the data has been submitted.
使用 Evilginx 成功捕获会话。一旦Evilginx收集凭据并记录cookie,它将通知GoPhish数据已提交。
I’ve exposed additional API endpoints in GoPhish to make it possible to change the results status for every sent email.
我在 GoPhish 中公开了其他 API 端点,以便可以更改每封已发送电子邮件的结果状态。
Now, when you create a new campaign in GoPhish, you do not have a “Landing Page” to select. Instead, you will generate a lure URL in Evilginx and paste it into the “Evilginx Lure URL” text box.
现在,当您在GoPhish中创建新广告系列时,您没有可供选择的“登录页面”。相反,您将在 Evilginx 中生成一个诱饵 URL 并将其粘贴到“Evilginx 诱饵 URL”文本框中。
What’s more, GoPhish will automatically generate the encrypted custom parameters with personalized content, retrievable by Evilginx, for each embedded link. The personalized values embedded with every phishing link embedded within the generated email message are the following:
更重要的是,GoPhish将为每个嵌入式链接自动生成带有个性化内容的加密自定义参数,可由Evilginx检索。生成的电子邮件中嵌入的每个网络钓鱼链接中嵌入的个性化值如下:
- First Name (
fname)
名字 (fname) - Last Name (
lname)
姓氏 (lname) - Email (
email) 电子邮件 (email)
This is super useful as you can use the custom parameters further to customize the content on your phishing pages within your js_inject scripts.
这非常有用,因为您可以进一步使用自定义参数来自 js_inject 定义脚本中网络钓鱼页面上的内容。
Let’s say you wanted to pre-fill the email in the sign-in text box on the phishing page. Now you can just use the {email} placeholder within your injected script and you can be sure that GoPhish will deliver the right value for you. The same goes for {fname} and {lname}.
假设您想要在网络钓鱼页面上的登录文本框中预填充电子邮件。现在,您只需在注入的脚本中使用 {email} 占位符,就可以确定GoPhish将为您提供正确的值。 {fname} 和 {lname} 也是如此。
GoPhish will also embed the rid (Result ID) in the phishing link’s parameters, so that Evilginx will know for which result it should update the status.
GoPhish还将在网络钓鱼链接的参数中嵌入 rid (结果ID),以便Evilginx知道它应该更新哪个结果的状态。
You can monitor the status of your mailing campaigns and check email deliverability, straight from GoPhish, but Evilginx will be the only side storing the credentials and authentication cookies.
您可以直接从GoPhish监控邮件活动的状态并检查电子邮件的送达率,但Evilginx将是唯一存储凭据和身份验证cookie的一方。
How to set up GoPhish with Evilginx?
如何使用 Evilginx 设置 GoPhish?
First of all, you need to get GoPhish from my forked GoPhish repository. You can either grab clone the source code and build it yourself or you can grab the binaries from releases.
首先,您需要从我分叉的 GoPhish 存储库中获取 GoPhish。您可以获取克隆源代码并自己构建它,也可以从发布中获取二进制文件。
Deploy GoPhish on the external server. It doesn’t have to be the same server Evilginx is running on, but it will have to be reachable by your Evilginx instances. You can find out how to install GoPhish in its official documentation.
在外部服务器上部署GoPhish。它不必是运行 Evilginx 的同一台服务器,但必须可由您的 Evilginx 实例访问。您可以在其官方文档中找到如何安装GoPhish。
Once you have GoPhish running on a remote server and you also have Evilginx deployed and ready for action, you will need to tell Evilginx how it can communicate with your GoPhish server.
一旦您在远程服务器上运行了GoPhish,并且您还部署了Evilginx并准备好采取行动,您将需要告诉Evilginx它如何与您的GoPhish服务器进行通信。
Configuring Evilginx 配置 Evilginx
For this, you will need the Admin URL of your GoPhish instance and the API key. You can find the API key within the Account Settings in your GoPhish admin panel. To figure out the IP and port of your GoPhish instance, refer to the official documentation.
为此,您将需要 GoPhish 实例的管理员 URL 和 API 密钥。您可以在GoPhish管理面板的帐户设置中找到API密钥。要确定GoPhish实例的IP和端口,请参阅官方文档。
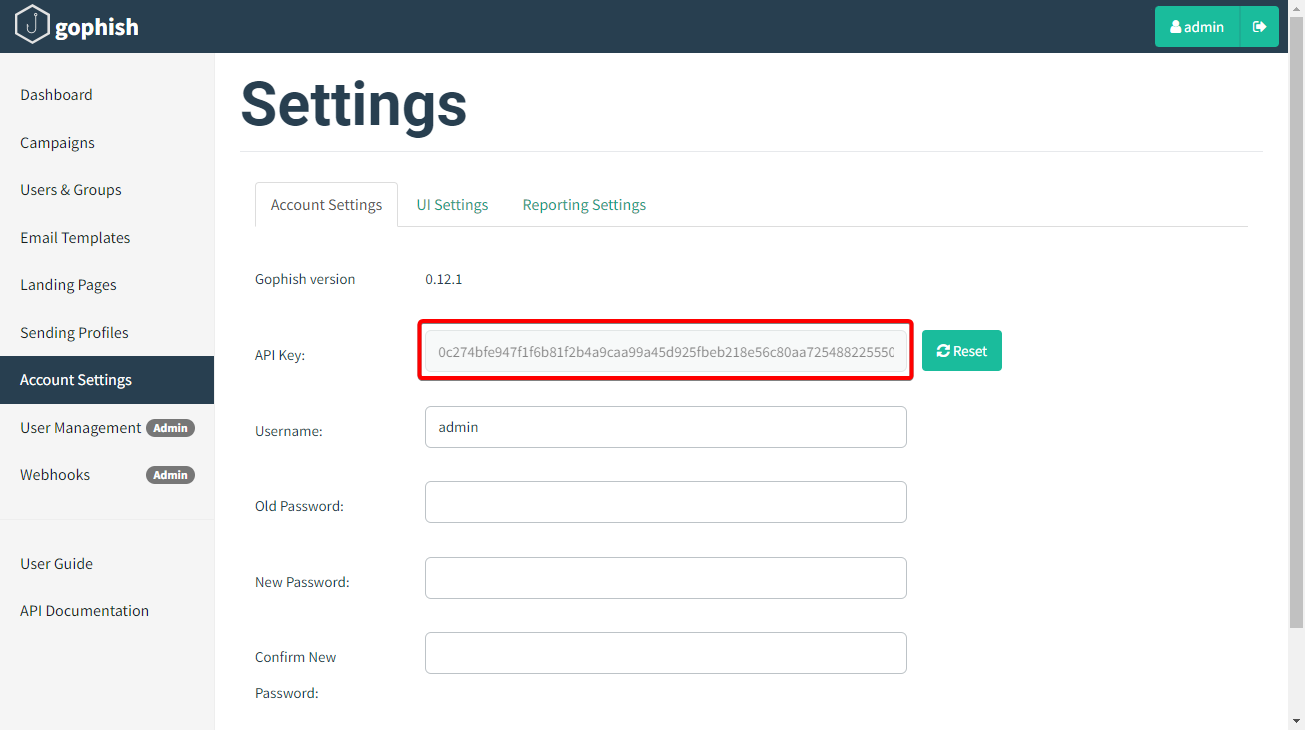
您可以在帐户设置中找到GoPhish API密钥
For example, if your GoPhish admin server is running on an IP 1.2.3.4 listening on port 3333, with TLS enabled, you can set it up as follows:
例如,如果您的GoPhish管理服务器在启用了TLS的IP 1.2.3.4 侦听端口 3333 上运行,则可以按如下方式进行设置:
config gophish admin_url https://1.2.3.4:3333
config gophish api_key c60e5bce24856c2c473c4560772If you do not use a valid TLS certificate for the exposed GoPhish instance, you may need to allow insecure TLS connections as well (such connections can be man-in-the-middled, so tread carefully):
如果您没有为公开的 GoPhish 实例使用有效的 TLS 证书,您可能还需要允许不安全的 TLS 连接(此类连接可以是中间人连接,因此请谨慎行事):
config gophish insecure trueOnce all this is configured, your Evilginx instance is ready to go. You can test if the communication with GoPhish works properly by issuing the command:
配置完所有这些后,您的 Evilginx 实例就可以使用了。您可以通过发出以下命令来测试与GoPhish的通信是否正常工作:
config gophish testConfiguring GoPhish 配置GoPhish
Here I am assuming you are familiar with how to use GoPhish. If not, feel free to check out the documentation on how to get started.
在这里,我假设您熟悉如何使用GoPhish。如果没有,请随时查看有关如何开始的文档。
Make sure GoPhish is running either in a tmux session or you set it up to run as a daemon. You can find more information on how to do it in this GitHub issue.
确保GoPhish在 tmux 会话中运行,或者将其设置为作为守护程序运行。您可以在此 GitHub 问题中找到有关如何执行此操作的更多信息。
Once you have everything properly set up, it is time to set up your Campaign. Create the new campaign and then select the Email Template, Sending Profile and the group of recipients. You may notice that instead of being asked for the Landing Page profile you need to provide the Evilginx Lure URL.
正确设置一切后,就可以设置广告系列了。创建新的市场活动,然后选择“电子邮件模板”、“发送配置文件”和收件人组。您可能会注意到,您需要提供 Evilginx 诱饵 URL,而不是被要求提供登录页面配置文件。
Open your Evilginx instance, create the lure and grab the lure URL you want to send out in your phishing campaign, using the command:
打开您的 Evilginx 实例,创建诱饵并获取要在网络钓鱼活动中发送的诱饵 URL,使用以下命令:
lures get-url <id>Copy this URL and paste it into the Evilginx Lure URL text field of the campaign creation panel.
复制此 URL 并将其粘贴到活动创建面板的 Evilginx Lure URL 文本字段中。
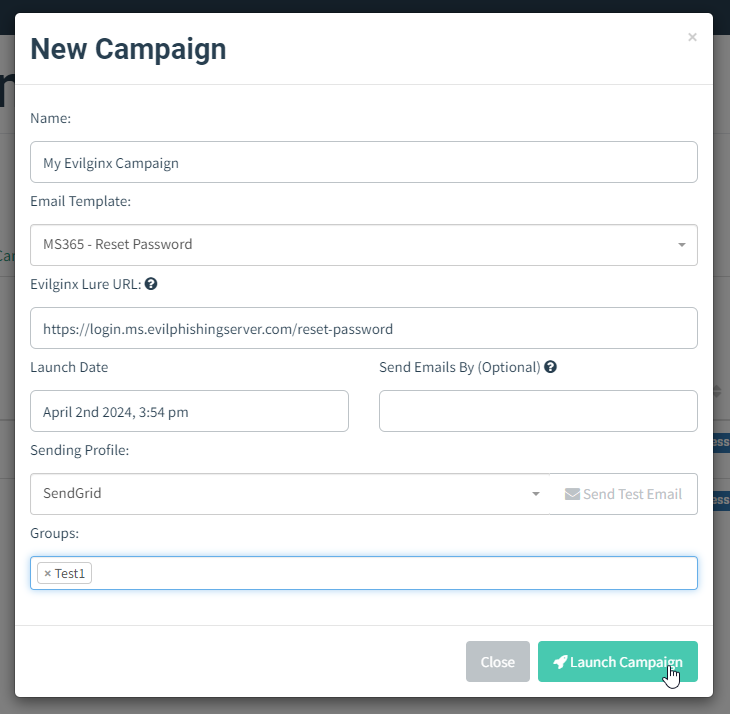
That’s it! You can now send out the campaign emails while enjoying the full overview of your campaign progress within the GoPhish UI.
就是这样!您现在可以发送活动电子邮件,同时在GoPhish UI中享受活动进度的完整概述。
Custom TLS Certificates 自定义 TLS 证书
Since the release of Evilginx 3.0, the tool has been using certmagic library for TLS certificate management with automated LetsEncrypt TLS certificate registration. Having to use only LetsEncrypt certificates is often not ideal as it may mark your phishing server, on an engagement, as suspicious.
自 Evilginx 3.0 发布以来,该工具一直使用 certmagic 库进行 TLS 证书管理,并自动注册 LetsEncrypt TLS 证书。必须仅使用 LetsEncrypt 证书通常并不理想,因为它可能会在参与时将您的网络钓鱼服务器标记为可疑。
Many people have requested support to use their own TLS certificates with Evilginx, including the wildcard certificates. This feature has finally been implemented.
许多人请求支持在 Evilginx 中使用他们自己的 TLS 证书,包括通配符证书。此功能终于实现了。
To add your own TLS certificates, first, create a new directory under ~/.evilginx/crt/sites/ with the name of your website or hostname. The name does not matter and it can be anything you choose.
要添加您自己的 TLS 证书,首先,请在 name with your website name or hostname 下 ~/.evilginx/crt/sites/ 创建一个新目录。名字并不重要,它可以是你选择的任何内容。
Evilginx will scan these directories looking for the public X509 certificate and the private key used to sign the certificate. The X509 certificate should have either the .pem or .crt extension, while the private key should have the .key extension.
Evilginx 将扫描这些目录,查找公共 X509 证书和用于签署证书的私钥。X509 证书应具有 .pem or .crt 扩展名,而私钥应具有 .key 扩展名。
For convenience, Evilginx will also recognize the keypair generated by CertBot, where the public certificate is named fullchain.pem and the private key is privkey.pem. You can copy both files into the same directory to add such a TLS certificate generated by CertBot.
为方便起见,Evilginx 还将识别 CertBot 生成的密钥对,其中公有证书被命名 fullchain.pem ,私钥为 privkey.pem 。您可以将这两个文件复制到同一目录中,以添加由 CertBot 生成的此类 TLS 证书。
Once you put your custom TLS certificates in the right place, don’t forget to disable automated LetsEncrypt certificate retrieval with:
将自定义 TLS 证书放在正确的位置后,不要忘记使用以下命令禁用自动 LetsEncrypt 证书检索:
config autocert offIMPORTANT! Make sure the private key files are not password-protected or otherwise Evilginx may fail to load them.
重要!确保私钥文件不受密码保护,否则 Evilginx 可能无法加载它们。
Example 1: 示例 1:
~/.evilginx/crt/sites/wildcard.domain.com/fullchain.pem
~/.evilginx/crt/sites/wildcard.domain.com/privkey.pemExample 2: 示例 2:
~/.evilginx/crt/sites/my_certificate/public.crt
~/.evilginx/crt/sites/my_certificate/private.keyCertMagic library will automatically add the TLS certificates to the managed pool and it will automatically respond with a valid TLS certificate.
CertMagic 库会自动将 TLS 证书添加到托管池,并自动使用有效的 TLS 证书进行响应。
HTTP Proxy IP Detection HTTP 代理 IP 检测
I know some of you use Caddy, Apache or Nginx as an additional proxy layer, sitting in front of the Evilginx instance. This created an issue for Evilginx to properly detect the origin IP address of incoming requests. Since all requests were proxied through a local web server, the origin IP would default to 127.0.0.1, completely ignoring the additional HTTP headers added by the proxies, with the correct origin IP addresses as values.
我知道你们中的一些人使用 Caddy、Apache 或 Nginx 作为额外的代理层,坐在 Evilginx 实例前面。这给 Evilginx 带来了一个问题,无法正确检测传入请求的源 IP 地址。由于所有请求都是通过本地 Web 服务器代理的,因此源 IP 将默认为 127.0.0.1 ,完全忽略代理添加的其他 HTTP 标头,并使用正确的源 IP 地址作为值。
Since this update, Evilginx will properly recognize the origin IP address of all proxied HTTP requests. The list of monitored HTTP headers is as follows:
自此更新以来,Evilginx 将正确识别所有代理 HTTP 请求的原始 IP 地址。受监控的 HTTP 标头列表如下:
X-Forwarded-For
X-Real-IP
X-Client-IP
Connecting-IP
True-Client-IP
Client-IPJSON support in force_post
force_post中的 JSON 支持
Thanks to @yudasm_ contribution, you can now enjoy injecting your custom POST parameters within body contents transmitted in JSON format.
多亏了@yudasm_的贡献,您现在可以享受在以 JSON 格式传输的正文内容中注入自定义 POST 参数的乐趣。
Check out Yehuda’s recent blog post on how he used this feature to evade FIDO2 authentication when phishing MS365 accounts.
查看 Yehuda 最近的博客文章,了解他在网络钓鱼 MS365 帐户时如何使用此功能来逃避 FIDO2 身份验证。
Fixed a bug used to detect Evilginx
修复了用于检测 Evilginx 的 bug
Keanu Nys reported an issue, in the BREAKDEV RED channel, where he found that one of the online URL scanners he used was able to open the phishing page by visiting the URL with just a hostname, without a valid lure URL path.
Keanu Nys 在 BREAKDEV RED 频道中报告了一个问题,他发现他使用的一个在线 URL 扫描器能够通过仅使用主机名访问 URL 来打开网络钓鱼页面,而没有有效的诱饵 URL 路径。
There was a bug in Evilginx, which would only enforce valid lure URLs for phishing hostnames, which were defined with session: true in the proxy_hosts section of the phishlet file.
Evilginx 中存在一个错误,它只会对网络钓鱼主机名强制执行有效的诱饵 URL,这些主机名在网络钓鱼文件 proxy_hosts 的部分中定义 session: true 。
Upon closer inspection, I’ve decided that the session parameter never made sense and it is now obsolete. Every proxy_hosts entry is treated as if session was set to true.
经过仔细检查,我决定该 session 参数从未有意义,现在已经过时了。每个 proxy_hosts 条目都被视为 session 设置为 true 。
Keanu wrote a great post-mortem post about the bug he found, so if you’re interested in learning more about it, you can find it here.
基努写了一篇关于他发现的错误的很棒的事后分析文章,所以如果你有兴趣了解更多关于它的信息,你可以在这里找到它。
Fixed the infinite redirection loop
修复无限重定向循环
Evilginx, since forever, had a very annoying bug, which would trigger the infinite redirection loop, whenever the lure URL path was set to be the same as the login path of the targeted website.
Evilginx,从永远以来,有一个非常烦人的错误,每当诱饵URL路径设置为与目标网站的登录路径相同时,它就会触发无限重定向循环。
This has now been fixed and Evilginx will also make an additional check to compare if the lure URL contains the valid phishing domain used by the landing phishing page.
此问题现已修复,Evilginx 还将进行额外检查,以比较诱饵 URL 是否包含登陆网络钓鱼页面使用的有效网络钓鱼域。
Added support for more TLDs
添加了对更多 TLD 的支持
Over the years, there have been multiple new TLDs launched for registering domains. Evilginx will try hard to detect all URLs in proxied packets and convert them either from phishing domains to original domains or from original domains to phishing domains.
多年来,已经推出了多个用于注册域名的新顶级域名。Evilginx 将努力检测代理数据包中的所有 URL,并将它们从网络钓鱼域转换为原始域或从原始域转换为网络钓鱼域。
To be more efficient, it relies on the detection of URLs ending with known TLDs. Some of the newer TLDs have not been supported and this update changes that.
为了提高效率,它依赖于检测以已知 TLD 结尾的 URL。一些较新的 TLD 不受支持,此更新对此进行了更改。
Here is the new list of all supported TLDs:
以下是所有受支持的 TLD 的新列表:
aero
arpa
art
biz
bot
cat
click
cloud
club
com
coop
edu
game
gov
inc
info
ink
int
jobs
live
lol
mil
mobi
museum
name
net
online
org
pro
root
shop
site
tech
tel
today
travel
vip
wiki
xyz
[all known 2 character TLDs]Changelog 更改日志
Here is the whole Evilginx 3.3 changelog with some additional changes and fixes I did not mention in this post:
以下是整个 Evilginx 3.3 更新日志,其中包含一些我在这篇文章中没有提及的其他更改和修复:
3.3.0
- Feature: Official GoPhish integration, using the fork: https://github.com/kgretzky/gophish
功能:官方GoPhish集成,使用分叉:https://github.com/kgretzky/gophish - Feature: Added support to load custom TLS certificates from a public certificate file and a private key file stored in
~/.evilginx/crt/sites/<hostname>/. Will loadfullchain.pemandprivkey.pempair or a combination of a.pem/.crt(public certificate) and a.key(private key) file. Make sure to run without-developerflag and disable autocert retrieval withconfig autocert off.
功能:添加了对从公有证书文件和存储在 中的~/.evilginx/crt/sites/<hostname>/私钥文件加载自定义 TLS 证书的支持。将加载fullchain.pem并privkey.pem配对或.pem组合 /.crt(公共证书)和(.key私钥)文件。确保在不-developer带标志的情况下运行,并使用config autocert off禁用 autocert 检索。 - Feature: Added ability to inject
force_postPOST parameters into JSON content body (by @yudasm_).
功能:添加了将 POST 参数注入force_postJSON 内容正文(按 @yudasm_ 年)的功能。 - Feature: Added ability to disable automated TLS certificate retrieval from LetsEncrypt with
config autocert <on/off>.
功能:添加了禁用 LetsEncrypt 自动config autocert <on/off>TLS 证书检索的功能。 - Feature: Evilginx will now properly recognize origin IP for requests coming from behind a reverse proxy (nginx/apache2/cloudflare/azure).
功能:Evilginx 现在可以正确识别来自反向代理 (nginx/apache2/cloudflare/azure) 后面的请求的源 IP。 - Fixed: Infinite redirection loop if the lure URL path was the same as the login path defined in the phishlet.
已修复:如果诱饵 URL 路径与网络钓鱼中定义的登录路径相同,则无限重定向循环。 - Fixed: Added support for exported cookies with names prefixed with
__Host-and__Secure-.
已修复:添加了对名称以__Host-和__Secure-为前缀的导出 Cookie 的支持。 - Fixed: Global
unauth_urlcan now be set to an empty string to have the server return403on unauthorized requests.
已修复:现在可以将全局unauth_url设置为空字符串,以使服务器返回403未经授权的请求。 - Fixed: Unauthorized redirects and blacklisting would be ignored for
proxy_hostswithsession: false(default) making it easy to detect evilginx by external scanners.
修复:未经授权的重定向和黑名单将被忽略proxy_hosts(session: false默认),以便通过外部扫描程序轻松检测 evilginx。 - Fixed: IP address
127.0.0.1is now ignored from being added to the IP blacklist.
修复:IP地址127.0.0.1现在被忽略,无法被添加到IP黑名单中。 - Fixed: Added support for more TLDs to use with phishing domains (e.g.
xyz,art,tech,wiki,lol& more)
已修复:添加了对更多顶级域名的支持,以用于网络钓鱼域(例如xyz,art,tech,wikilol,等) - Fixed: Credentials will now be captured also from intercepted requests.
已修复:现在也将从截获的请求中捕获凭据。
Conclusion 结论
I’m happy to have finally been able to include the most requested features, together with some quality-of-life improvements, before the Evilginx Pro release this year.
我很高兴终于能够在今年 Evilginx Pro 发布之前包含最需要的功能,以及一些生活质量改进。
Please let me know your feedback about the update, either on Twitter @mrgretzky or in BREAKDEV RED Discord.
请让我知道您对更新的反馈,无论是在 Twitter @mrgretzky 还是在 BREAKDEV RED Discord 中。
Looking forward to your opinion!
期待您的意见!
If you’re reading this before 3rd April 2024, you can still get a 30% discount for the Evilginx Mastery course, which I am constantly updating and you get access for a lifetime. Expect to see the GoPhish integration guide added sometime in the future.
如果您在 2024 年 4 月 3 日之前阅读本文,您仍然可以获得 Evilginx Mastery 课程的 30% 折扣,我不断更新该课程,您可以终生使用。预计在未来的某个时候会添加GoPhish集成指南。
Happy phishing! 快乐的网络钓鱼!
原文始发于Kuba Gretzky:Evilginx 3.3 – Go & Phish