ESET has collaborated with the Federal Police of Brazil in an attempt to disrupt the Grandoreiro botnet. ESET contributed to the project by providing technical analysis, statistical information, and known command and control (C&C) server domain names and IP addresses. Due to a design flaw in Grandoreiro’s network protocol, ESET researchers were also able to get a glimpse into the victimology.
ESET与巴西联邦警察合作,试图破坏Grandoreiro僵尸网络。ESET通过提供技术分析、统计信息以及已知的命令和控制(C&C)服务器域名和IP地址为该项目做出了贡献。由于Grandoreiro的网络协议存在设计缺陷,ESET研究人员也能够一瞥受害者。
ESET automated systems have processed tens of thousands of Grandoreiro samples. The domain generation algorithm (DGA) the malware has used since around October 2020 produces one main domain, and optionally several failsafe domains, per day. The DGA is the only way Grandoreiro knows how to report to a C&C server. Besides the current date, the DGA accepts static configuration as well – we have observed 105 such configurations as of this writing.
ESET自动化系统已经处理了数万个Grandoreiro样本。自2020年10月左右以来,恶意软件使用的域生成算法(DGA)每天生成一个主域,并可选地生成几个故障安全域。DGA是Grandoreiro知道如何向C&C服务器报告的唯一方式。除了当前日期,DGA还接受静态配置-截至撰写本文时,我们已经观察到105个此类配置。
Grandoreiro’s operators have abused cloud providers such as Azure and AWS to host their network infrastructure. ESET researchers provided data crucial to identifying the accounts responsible for setting up these servers. Further investigation performed by the Federal Police of Brazil led to the identification and arrest of the individuals in control of these servers. In this blogpost, we look at how we obtained the data to assist law enforcement to execute this disruption operation.
Grandoreiro的运营商滥用Azure和AWS等云提供商来托管其网络基础设施。ESET的研究人员提供了关键数据,以确定负责设置这些服务器的帐户。巴西联邦警察进行的进一步调查查明并逮捕了控制这些服务器的个人。在这篇博文中,我们将介绍我们如何获得数据,以协助执法部门执行这一破坏行动。
Background 背景
Grandoreiro is one of many Latin American banking trojans. It has been active since at least 2017 and ESET researchers have been closely tracking it ever since. Grandoreiro targets Brazil and Mexico, and since 2019 Spain as well (see Figure 1). While Spain was the most targeted country between 2020 and 2022, in 2023 we observed a clear switch of focus towards Mexico and Argentina, the latter being new to Grandoreiro.
Grandoreiro是众多拉丁美洲银行业特洛伊木马之一。它至少从2017年开始活跃,ESET研究人员从那时起就一直在密切跟踪它。Grandoreiro的目标是巴西和墨西哥,自2019年以来也是西班牙(见图1)。虽然西班牙是2020年至2022年期间最受关注的国家,但在2023年,我们观察到重点明显转向墨西哥和阿根廷,后者是Grandoreiro的新成员。
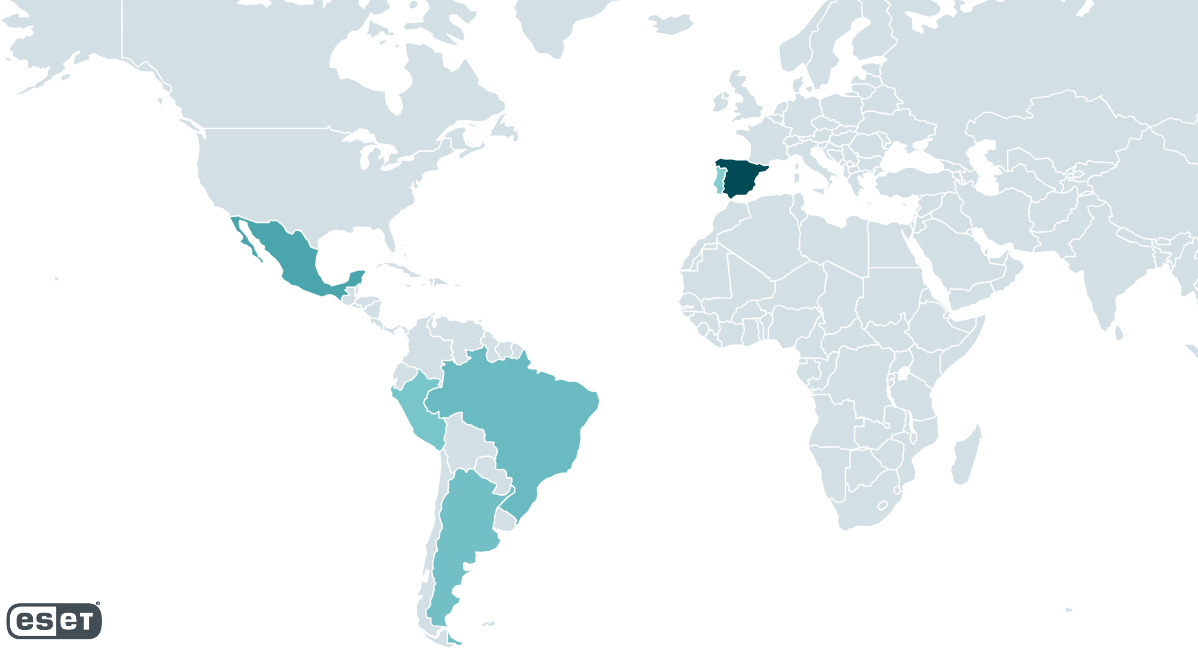
图1. Grandoreiro检测率(2020年1月以来的数据)
Functionality-wise, Grandoreiro hasn’t changed very much since our last blogpost in 2020. We offer a brief overview of the malware in this section and dive into the few changes, mainly new DGA logic, later.
功能方面,Grandoreiro自2020年我们的上一篇博客以来没有太大变化。我们在本节中简要概述了恶意软件,并在稍后深入了解一些变化,主要是新的DGA逻辑。
When a Latin American banking trojan successfully compromises a machine, it usually issues an HTTP GET request to a remote server, sending some basic information about the compromised machine. While older Grandoreiro builds implemented this feature, over time, the developers decided to drop it.
当拉丁美洲银行特洛伊木马成功危害计算机时,它通常会向远程服务器发出HTTP GET请求,发送有关受危害计算机的一些基本信息。虽然较旧的Grandoreiro版本实现了此功能,但随着时间的推移,开发人员决定放弃它。
Grandoreiro periodically monitors the foreground window to find one that belongs to a web browser process. When such a window is found and its name matches any string from a hardcoded list of bank-related strings, then and only then the malware initiates communication with its C&C server, sending requests at least once a second until terminated.
Grandoreiro定期监视前台窗口,以查找属于Web浏览器进程的窗口。当发现这样的窗口并且其名称与银行相关字符串的硬编码列表中的任何字符串匹配时,然后且仅在此时,恶意软件才会启动与其C&C服务器的通信,每秒至少发送一次请求,直到终止。
The operator has to interact manually with the compromised machine in order to steal a victim’s money. The malware allows:
操作员必须手动与受感染的机器进行交互,以窃取受害者的钱。该恶意软件允许:
- blocking the screen of the victim,
挡住了受害者的屏幕 - logging keystrokes, 伐木工人,
- simulating mouse and keyboard activity,
模拟鼠标和键盘活动, - sharing the victim’s screen, and
分享受害者的屏幕, - displaying fake pop-up windows.
显示假的弹出窗口
Grandoreiro undergoes rapid and constant development. Occasionally, we even saw several new builds a week, making it difficult to keep track. To demonstrate, in February 2022, Grandoreiro’s operators added a version identifier to the binaries. In Figure 2 we show how quickly the version identifier changed. On average, it was a new version every four days between February 2022 and June 2022. In the month-long gap between May 24th, 2022 and June 22nd, 2022 we continued to see new samples with progressing PE compilation times, but they lacked the version identifier. On June 27th, 2022 the version identifier changed to V37 and we haven’t seen it change since then, leaving us to conclude that this feature was dropped.
Grandoreiro经历了快速和不断的发展。偶尔,我们甚至一周看到几个新的构建,这使得跟踪变得困难。为了证明这一点,2022年2月,Grandoreiro的操作员在二进制文件中添加了一个版本标识符。在图2中,我们展示了版本标识符的变化速度。从2022年2月到2022年6月,平均每四天就有一个新版本。在2022年5月24日 th 和2022年6月22日 nd 之间长达一个月的间隙中,我们继续看到PE编译时间不断增加的新样本,但它们缺乏版本标识符。在2022年6月27日 th ,版本标识符更改为V37,从那以后我们没有看到它发生变化,让我们得出结论,该功能已被删除。
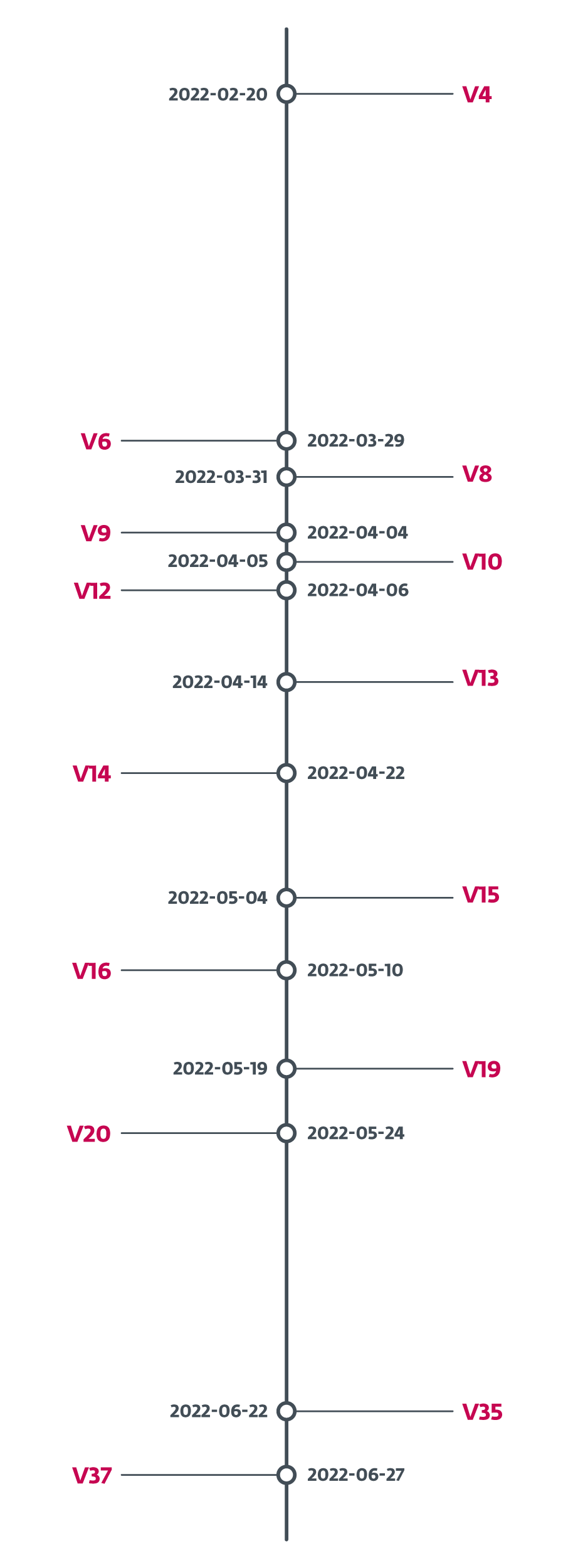
图2. Grandoreiro 2022年2月至6月期间的版本历史
Latin American banking trojans share a lot of commonalities. Grandoreiro is similar to other Latin American banking trojans mainly by the obvious core functionality and in bundling its downloaders within MSI installers. In the past, we have observed a few cases where its downloaders were shared with Mekotio and Vadokrist, though not in the last two years. The Grandoreiro banking trojan’s main distinction from the other families had been its unique binary padding mechanism that massively engorges the final executable (described in our blogpost in 2020). Over time, Grandoreiro’s operators added this anti-analysis technique to its downloaders as well. To our surprise, in Q3 2023, this feature was completely dropped from the banking trojan and downloader binaries and we haven’t observed it since.
拉丁美洲的银行木马有很多共同点。Grandoreiro与其他拉丁美洲银行木马类似,主要是通过明显的核心功能和在MSI安装程序中捆绑其下载程序。在过去,我们观察到一些情况下,它的下载器与Mekotio和Vadokrist共享,但不是在过去两年。Grandoreiro银行木马与其他家族的主要区别在于其独特的二进制填充机制,该机制会大量占用最终的可执行文件(在我们2020年的博客文章中描述)。随着时间的推移,Grandoreiro的运营商也将这种反分析技术添加到其下载程序中。令我们惊讶的是,在2023年第三季度,此功能完全从银行木马和下载器二进制文件中删除,此后我们再也没有观察到它。
Since February 2022, we have been tracking a second variant of Grandoreiro that differs significantly from the main one. We saw it, in small campaigns, in March, May, and June 2022. Based on the vast majority of its C&C server domains not resolving, its core features changing quite often, and its network protocol not functioning properly, we strongly believe it is a work in progress; hence we will focus on the main variant in this blogpost.
自2022年2月以来,我们一直在跟踪Grandoreiro的第二个变体,该变体与主要变体有很大不同。我们在2022年3月、5月和6月的小型活动中看到了这一点。基于其绝大多数C&C服务器域无法解析,其核心功能经常更改,其网络协议无法正常运行,我们坚信这是一项正在进行的工作;因此,我们将专注于这篇博文中的主要变体。
Grandoreiro long-term tracking
Grandoreiro长期跟踪
ESET systems designed for automated, long-term tracking of selected malware families have been monitoring Grandoreiro since the end of 2017, extracting version information, C&C servers, targets and, since the end of 2020, DGA configurations.
自2017年底以来,ESET系统一直在监控Grandoreiro,提取版本信息,C&C服务器,目标,并自2020年底以来,DGA配置。
DGA tracking DGA跟踪
The DGA configuration is hardcoded in the Grandoreiro binary. Each configuration can be referred to by a string we call dga_id. Using different configurations for the DGA yields different domains. We dive deeper into the DGA mechanism later in the text.
DGA配置在Grandoreiro二进制文件中进行硬编码。每个配置都可以通过一个我们称为dga_id的字符串来引用。对DGA使用不同的配置会产生不同的域。我们将在本文后面更深入地探讨DGA机制。
ESET has extracted a total of 105 different dga_ids from the Grandoreiro samples known to us. 79 of these configurations at least once generated a domain that resolved to an active C&C server IP address during the course of our tracking.
ESET已经从我们已知的Grandoreiro样本中提取了总共105个不同的dga_id。在我们的跟踪过程中,这些配置中至少有79个生成了一个解析为活动C&C服务器IP地址的域。
The generated domains are registered via No-IP’s Dynamic DNS service (DDNS). Grandoreiro’s operators abuse the service to frequently change their domains to correspond with the DGA and to change IP addresses at will. The vast majority of the IP addresses these domains resolve to are provided by cloud providers, mainly AWS and Azure. Table 1 illustrates some statistics about IP addresses used for Grandoreiro C&C servers.
生成的域名通过No-IP的动态DNS服务(DDNS)注册。Grandoreiro的运营商滥用这项服务,频繁地改变他们的域名以符合DGA,并随意改变IP地址。这些域名解析的绝大多数IP地址都是由云提供商提供的,主要是AWS和Azure。表1说明了Grandoreiro C&C服务器使用的IP地址的一些统计信息。
Table 1. Statistical information about Grandoreiro C&C IP addresses since we started our tracking
表1.自我们开始跟踪以来有关Grandoreiro C&C IP地址的统计信息
| Information 信息 | Average 平均 | Minimum 最小 | Maximum 最大 |
| Number of new C&C IP addresses per day 每天新增C&C IP地址数量 |
3 | 1 | 34 |
| Number of active C&C IP addresses per day 每天活动的C&C IP地址数 |
13 | 1 | 27 |
| Lifespan of C&C IP address (in days) C&C IP地址的寿命(天) |
5 | 1 | 425 |
Very soon after we began to track the generated domains and their associated IP addresses, we started to notice that many domains generated by DGAs with different configurations resolve to the same IP address (as illustrated in Figure 3). This means that on a given day, victims compromised by Grandoreiro samples with different dga_id all connected to the same C&C server. This phenomenon was no coincidence – we observed it almost on a daily basis during our tracking.
在我们开始跟踪生成的域及其关联的IP地址后不久,我们开始注意到,具有不同配置的DGA生成的许多域解析为相同的IP地址(如图3所示)。这意味着,在某一天,受害者被具有不同dga_id的Grandoreiro样本入侵,所有受害者都连接到同一个C&C服务器。这种现象并非巧合-我们在跟踪过程中几乎每天都能观察到。
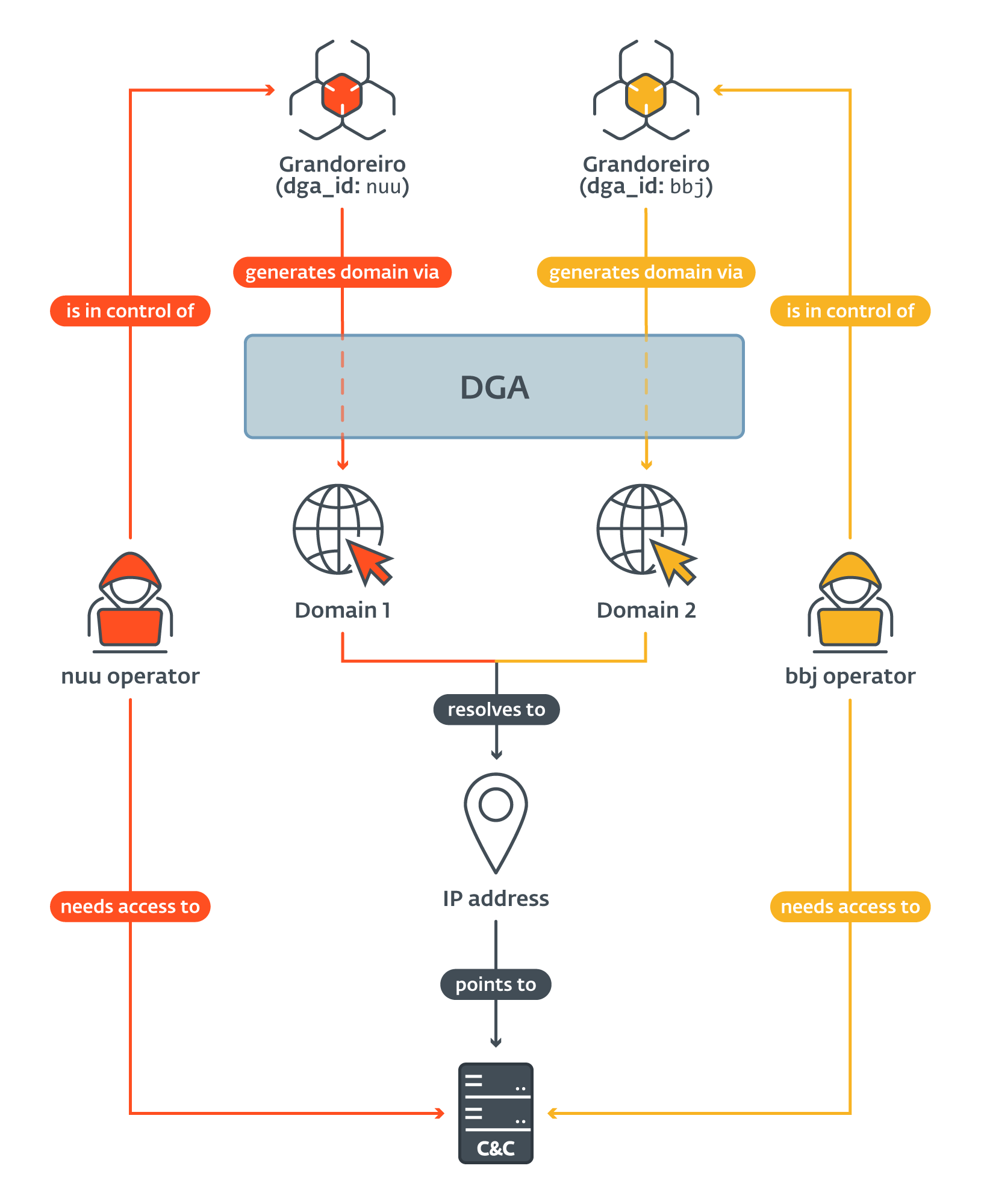
图3.两种不同Grandoreiro DGA配置中IP重叠的示意图
On much rarer occasions, we have also observed an IP address being reused by a different dga_id a few days later. Only this time, the parameters Grandoreiro used to establish a connection (explained later in the text) changed as well. This means that, in the meantime, the C&C server side must have been reinstalled or reconfigured.
在更罕见的情况下,我们还观察到IP地址在几天后被不同的dga_id重用。只是这一次,Grandoreiro用于建立连接的参数(稍后在本文中解释)也发生了变化。这意味着,在此期间,C&C服务器端必须重新安装或重新配置。
Our initial assumption was that the dga_id is unique for each DGA configuration. This later proved to be incorrect – we have observed two sets of different configurations sharing the same dga_id. Table 2 shows both of them, “jjk” and “gh”, where “jjk” and “jjk(2)” correspond to two different DGA configurations, same as “gh” and “gh(2)”.
我们最初的假设是dga_id对于每个DGA配置都是唯一的。这后来被证明是不正确的-我们已经观察到两组不同的配置共享相同的dga_id。表2显示了它们,“jjk”和“gh”,其中“jjk”和“jjk(2)”对应于两种不同的DGA配置,与“gh”和“gh(2)”相同。
Table 2 shows the clusters we were able to observe. All DGA configurations that shared at least one IP address are in the same cluster and their associated dga_ids are listed. Clusters that account for less than 1% of all victims are disregarded.
表2显示了我们能够观察到的集群。共享至少一个IP地址的所有DGA配置都在同一群集中,并且列出了其关联的dga_id。占所有受害者不到1%的群体被忽略。
Table 2. Grandoreiro DGA clusters
表2. Grandoreiro DGA团簇
|
Cluster ID 集群ID |
dga_id list dga_id列表 |
Cluster size 簇大小 |
% of all C&C servers 所有C&C服务器的百分比 |
% of all victims 占所有受害者的百分比 |
|
1 |
b, bbh, bbj, bbn, bhg, cfb, cm, cob, cwe, dee, dnv, dvg, dzr, E, eeo, eri, ess, fhg, fox, gh, gh(2), hjo, ika, jam, jjk, jjk(2), JKM, jpy, k, kcy, kWn, md7, md9, MRx, mtb, n, Nkk, nsw, nuu, occ, p, PCV, pif, rfg, rox3, s, sdd, sdg, sop, tkk, twr, tyj, u, ur4, vfg, vgy, vki, wtt, ykl, Z, zaf, zhf |
62 |
93.6% |
94% |
|
2 |
jl2, jly jl2,jly |
2 |
2.4% |
2.5% |
|
3 |
ibr |
1 |
0.8% |
1.6% |
|
4 |
JYY |
1 |
1.6% |
1.1% |
The biggest cluster contains 78% of all active dga_ids. It is responsible for 93.6% of all C&C server IP addresses and 94% of all victims we’ve seen. The only other cluster consisting of more than 1 dga_id is cluster 2.
最大的集群包含所有活动dga_id的78%。它占所有C&C服务器IP地址的93.6%,占我们见过的所有受害者的94%。另一个包含1个以上dga_id的集群是集群2。
Some sources claim that Grandoreiro operates as malware-as-a-service (MaaS). The Grandoreiro C&C server backend does not allow simultaneous activity of more than one operator at once. Based on Table 2, the vast majority of DGA-produced IP addresses can be clustered together with no clear distribution pattern. Finally, considering the network protocol’s heavy bandwidth requirements (we dive into that at the end of the blogpost), we believe that the different C&C servers are used as a primitive load-balancing system and that it is more likely that Grandoreiro is operated by a single group or by a few groups closely cooperating with one another.
一些消息来源声称Grandoreiro作为恶意软件即服务(MaaS)运行。Grandoreiro C&C服务器后端不允许一个以上的操作员同时进行活动。根据表2,绝大多数DGA产生的IP地址可以聚集在一起,没有明确的分布模式。最后,考虑到网络协议的高带宽要求(我们在博客文章的最后深入讨论),我们认为不同的C&C服务器被用作原始的负载平衡系统,并且Grandoreiro更有可能由单个组或几个相互密切合作的组操作。
C&C tracking C&C跟踪
Grandoreiro’s implementation of its network protocol allowed ESET researchers to take a peek behind the curtain and get a glimpse of the victimology. Grandoreiro C&C servers give away information about the connected victims at the time of the initial request to each newly connected victim. That said, the data is biased by the number of requests, their intervals, and the validity of the data provided by the C&C servers.
Grandoreiro的网络协议的实现使ESET研究人员能够在幕后偷看并瞥见受害者。Grandoreiro C&C服务器在向每个新连接的受害者发出初始请求时给予有关连接的受害者的信息。也就是说,数据会受到请求数量、请求间隔以及C&C服务器提供的数据有效性的影响。
Each victim connected to the Grandoreiro C&C server is identified by a login_string – a string Grandoreiro constructs upon establishing the connection. Different builds use different formats and different formats contain different information. We summarize the information that can be obtained from the login_string in Table 3. The Occurrence column shows a percentage of all the formats we’ve seen that hold the corresponding kind of information.
连接到Grandoreiro C&C服务器的每个受害者都由login_string标识-Grandoreiro在建立连接时构造的字符串。不同的构建使用不同的格式,不同的格式包含不同的信息。我们在表3中总结了可以从login_string获得的信息。Occurrence列显示了我们见过的所有包含相应类型信息的格式的百分比。
Table 3. Overview of information that can be obtained from a Grandoreiro victim’s login_string
表3.可从Grandoreiro受害者的login_string中获得的信息概述
|
Information 信息 |
Occurrence 发生 |
Description 描述 |
|
Operating system 操作系统 |
100% |
OS of victim’s machine. |
|
Computer name 计算机名 |
100% |
Name of victim’s machine. |
|
Country 国家 |
100% |
Country that the Grandoreiro sample targets (hardcoded in the malware sample). |
|
Version 版本 |
100% |
Version (version_string) of the Grandoreiro sample. |
|
Bank codename 银行代号 |
92% |
Codename of the bank that triggered the C&C connection (assigned by Grandoreiro’s developers). |
|
Uptime |
25% |
Time (in hours) that the victim’s machine has been running. |
|
Screen resolution 屏幕分辨率 |
8% |
Screen resolution of the victim’s main monitor. |
|
Username 用户名 |
8% |
Username of the victim. |
Three of the fields deserve a closer explanation. Country is a string hardcoded in the Grandoreiro binary rather than information obtained via appropriate services. Therefore, it serves more like an intended country of the victim.
其中三个领域值得更深入的解释。国家是硬编码在Grandoreiro二进制中的字符串,而不是通过适当的服务获得的信息。因此,它更像是受害者的目的国。
Bank codename is a string Grandoreiro’s developers associated with a certain bank or other financial institution. The victim visited that bank’s website, which triggered the C&C connection.
银行代号是一个字符串Grandoreiro的开发商与某一银行或其他金融机构。受害者访问了该银行的网站,触发了C&C连接。
The version_string is a string identifying a specific Grandoreiro build. It is hardcoded in the malware and holds a string that identifies a specific build series, a version (which we already talked about in the introduction), and a timestamp. Table 4 illustrates the different formats and the information they hold. Notice that some of the timestamps contain only month and day, while others contain the year as well.
version_string是标识特定Grandoreiro构建的字符串。它被硬编码在恶意软件中,并保存一个字符串,用于标识特定的构建系列,版本(我们已经在介绍中讨论过)和时间戳。表4说明了不同的格式及其所包含的信息。请注意,有些时间戳只包含月和日,而其他时间戳也包含年。
Table 4. List of different version_string formats and their parsing
表4.不同的version_string格式及其解析列表
|
Version string 版本字符串 |
Build ID 构建ID |
Version 版本 |
Timestamp 时间戳 |
|
DANILO |
DANILO |
N/A |
N/A |
|
(V37)(P1X)1207 (V37)(P1X)1207 |
P1X |
V37 |
12/07 |
|
(MX)2006 (MX)2006年 |
MX |
N/A |
20/06 |
|
fox50.28102020 |
fox50 福克斯50 |
N/A |
28/10/2020 |
|
MADMX(RELOAD)EMAIL2607 MADMX(重新加载)EMAIL2607 |
MADMX(RELOAD)EMAIL MADMX(重新加载)电子邮件 |
N/A |
26/07 |
One may be tempted to say that the Build ID actually identifies the operator. However, we don’t think that is the case. The format of this string is very chaotic, sometimes it refers only to a month in which the binary probably was built (like (AGOSTO)2708). Additionally, we strongly believe that P1X refers to a console used by Grandoreiro operator(s) called PIXLOGGER.
人们可能会说,构建ID实际上标识了操作员。然而,我们认为情况并非如此。这个字符串的格式非常混乱,有时它只表示二进制文件可能构建的月份(如(AGOSTO)2708)。此外,我们坚信P1X是指Grandoreiro操作员使用的名为PIXLOGGER的控制台。
C&C server tracking – findings
C&C服务器跟踪-调查结果
In this section, we focus on what we’ve found by querying the C&C servers. All the statistical data listed in this section has been obtained directly from Grandoreiro C&C servers, not from ESET telemetry.
在本节中,我们将重点关注通过查询C&C服务器所发现的内容。本节中列出的所有统计数据均直接从Grandoreiro C&C服务器获得,而不是从ESET遥测获得。
Old samples are still active
旧样本仍然活跃
Each login_string we observed contains the version_string and the vast majority of those contain the timestamp information (see Table 3 and Table 4). While a lot of them contain only day and month, as seems to be the developer’s choice occassionally, the oldest communicating sample was timestamped 15/09/2020 – that is from the time this DGA was first introduced to Grandoreiro. The most recent sample was timestamped 12/23/2023.
我们观察到的每个login_string都包含version_string,其中绝大多数包含时间戳信息(参见表3和表4)。虽然它们中的许多只包含日期和月份,但这似乎是开发人员偶尔的选择,最古老的通信样本的时间戳是15/09/2020 -也就是从DGA首次引入Grandoreiro的时间开始。最近的样本时间戳为2023年12月23日。
Operating system distribution
操作系统发行
Since all of the login_string formats contain OS information, we can paint an accurate picture of what operating systems fell victim, as illustrated in Figure 4.
由于所有login_string格式都包含操作系统信息,因此我们可以准确地描绘出操作系统的受害者,如图4所示。
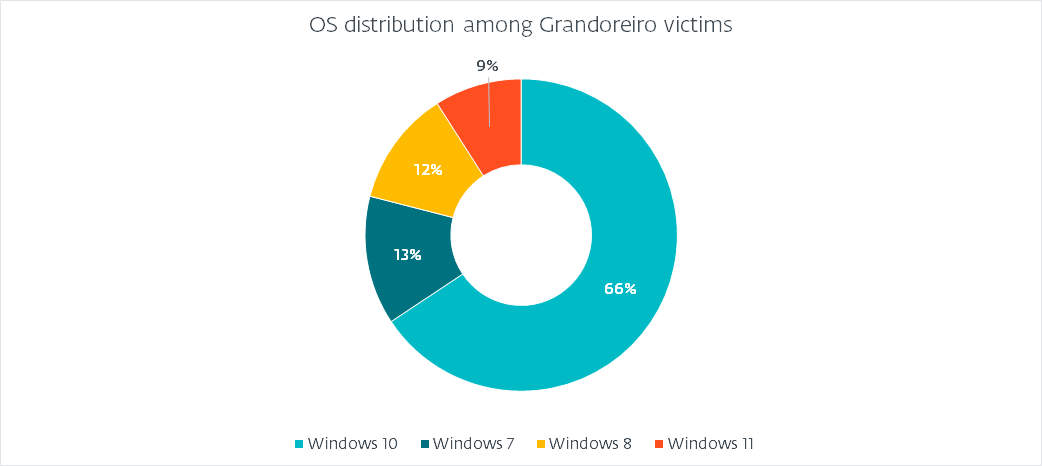
图4. Grandoreiro受害者的操作系统分布
(Intended) country distribution
(预定)国家分布
We already mentioned that Grandoreiro uses a hardcoded value instead of querying a service to obtain the country of the victim. Figure 5 shows the distribution that we have observed.
我们已经提到,Grandoreiro使用硬编码的值而不是查询服务来获取受害者的国家。图5显示了我们观察到的分布。
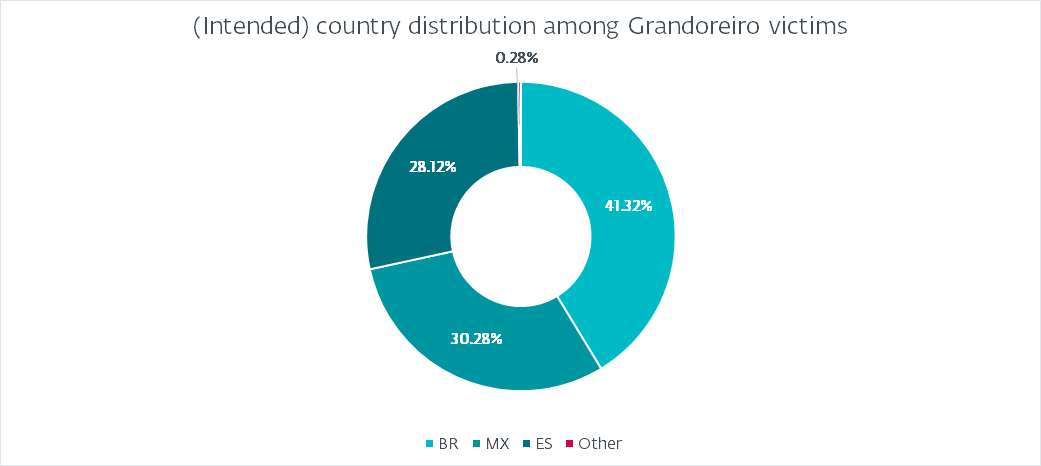
图5.在Grandoreiro受害者中分配(预定)国家代码
This distribution is to be expected of Grandoreiro. Interestingly, it does not correlate with the heatmap depicted in Figure 1. The most logical explanation is that the builds are not marked properly to resemble their intended targets. For example, the increase in attacks in Argentina is not reflected at all by the hardcoded marking. Brazil accounts for almost 41% of all victims, followed by Mexico with 30% and Spain with 28%. Argentina, Portugal, and Peru account for less than 1%. Interestingly, we have seen a few (fewer than 10) victims marked as PM (Saint Pierre and Miquelon), GR (Greece), or FR (France). We believe those are either typos or have other meanings rather than aiming at those countries.
这种分布是预期的Grandoreiro。有趣的是,它与图1中描绘的热图无关。最合乎逻辑的解释是,构建没有正确地标记以与其预期目标相似。例如,阿根廷境内袭击事件的增加根本没有反映在硬编码标识中。巴西占所有受害者的近41%,其次是墨西哥的30%和西班牙的28%。阿根廷、葡萄牙和秘鲁所占比例不到1%。有趣的是,我们看到一些(不到10个)受害者被标记为PM(圣皮埃尔和密克隆),GR(希腊)或FR(法国)。我们认为,这些要么是错别字,要么有其他含义,而不是针对这些国家。
Also note that while Grandoreiro added targets from many countries outside of Latin America as early as 2020, we have observed few to no campaigns targeting those countries and Figure 5 supports this.
另请注意,虽然Grandoreiro早在2020年就增加了拉丁美洲以外许多国家的目标,但我们观察到很少有针对这些国家的活动,图5支持这一点。
Number of victims 受害者人数
We have observed that the average number of victims connected in a day is 563. However, this number certainly contains duplicates, because if a victim stays connected for a long time, which we’ve observed is often the case, then the Grandoreiro C&C server will report it on multiple requests.
我们观察到,平均每天连接的受害者人数为563人。然而,这个数字肯定包含重复,因为如果受害者保持连接很长一段时间,我们已经观察到这种情况,那么Grandoreiro C&C服务器将在多个请求中报告它。
Trying to address this issue, we defined a unique victim as one with a unique set of identifying characteristics (like computer name, username, etc.) while omitting those that are subject to change (like uptime). With that, we ended up with 551 unique victims connected in a day on average.
为了解决这个问题,我们将唯一受害者定义为具有唯一识别特征集(如计算机名称,用户名等)的受害者。而忽略那些容易改变的(比如,这样,我们平均每天有551个不同的受害者。
Taking into account that we have observed victims who were connecting to the C&C servers constantly for over a year’s period, we calculated an average number of 114 new unique victims connecting to the C&C servers each day. We came to this number by disregarding unique victims that we have already observed before.
考虑到我们观察到的受害者在一年多的时间里不断连接到C&C服务器,我们计算出平均每天有114名新的独特受害者连接到C&C服务器。我们得出这个数字是因为忽略了我们之前观察到的独特受害者。
Grandoreiro internals Grandoreiro内部构件
Let us focus, in depth, on the two most crucial features of Grandoreiro: the DGA and the network protocol.
让我们深入关注Grandoreiro的两个最重要的特性:DGA和网络协议。
DGA
Grandoreiro’s operators have implemented several kinds of DGAs over the years, with the most recent one appearing in July 2020. While we noticed a few minor changes, the core of the algorithm hasn’t change since.
多年来,Grandoreiro的运营商已经实施了多种DGA,最近一次出现在2020年7月。虽然我们注意到了一些小的变化,但算法的核心从那以后就没有改变过。
The DGA utilizes a specific configuration that is hardcoded in the binary, stored as multiple strings. Figure 6 displays one such configuration (with dga_id “bbj”), reformatted in JSON for better readability.
DGA利用以二进制硬编码的特定配置,存储为多个字符串。图6显示了一个这样的配置(dga_id为“bbj”),为了更好的可读性,在JSON中重新格式化。
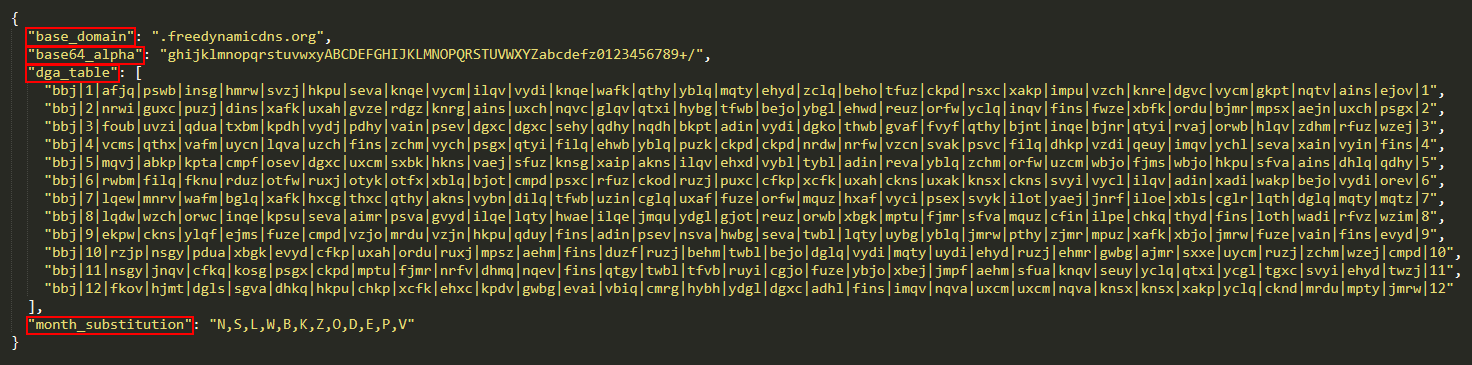
图6. Grandoreiro DGA配置,重新格式化为JSON
In the vast majority of cases, the base_domain field is freedynamicdns.org or zapto.org. As already mentioned, Grandoreiro utilizes No-IP for its domain registration. The base64_alpha field corresponds to the custom base64 alphabet the DGA uses. The month_substitution is used to substitute a month number for a character.
在绝大多数情况下,base_domain字段是freedynamicdns.org或zapto. org。如前所述,Grandoreiro使用No-IP进行域名注册。base64_alpha字段对应于DGA使用的自定义base64字母表。month_substitution用于将一个字符替换为一个月数。
The dga_table forms the main part of the configuration. It consists of 12 strings, each with 35 fields delimited by |. The first entry of each line is the dga_id. The second and last entry represent the month the line is intended for. The remaining 32 fields each represent a value for a different day of the month (leaving at least one field unused).
dga_table构成配置的主要部分。它由12个字符串组成,每个字符串有35个字段,|.每一行的第一个条目是dga_id。第二个和最后一个条目表示该行要用于的月份。剩下的32个字段分别表示一个月中不同日期的值(至少有一个字段未使用)。
The logic of the DGA is shown in Figure 7. The algorithm first selects the correct line and the correct entry from it, treating it as a four-byte key. It then formats the current date into a string and encrypts it with the key using a simple XOR. It then prepends the dga_id to the result, encodes the result using base64 with a custom alphabet, and then removes any = padding characters. The final result is the subdomain that, together with base_domain, is to be used as the C&C server for the current day. The part highlighted in red is a failsafe mechanism and we discuss it next.
DGA的逻辑如图7所示。该算法首先选择正确的行和正确的条目,将其视为四字节键。然后,它将当前日期格式化为一个字符串,并使用简单的XOR用密钥对其进行加密。然后将dga_id添加到结果中,使用base64和自定义字母表对结果进行编码,然后删除任何=填充字符。最后的结果是子域,与base_domain一起,将用作当天的C&C服务器。红色突出显示的部分是故障安全机制,我们接下来将讨论它。
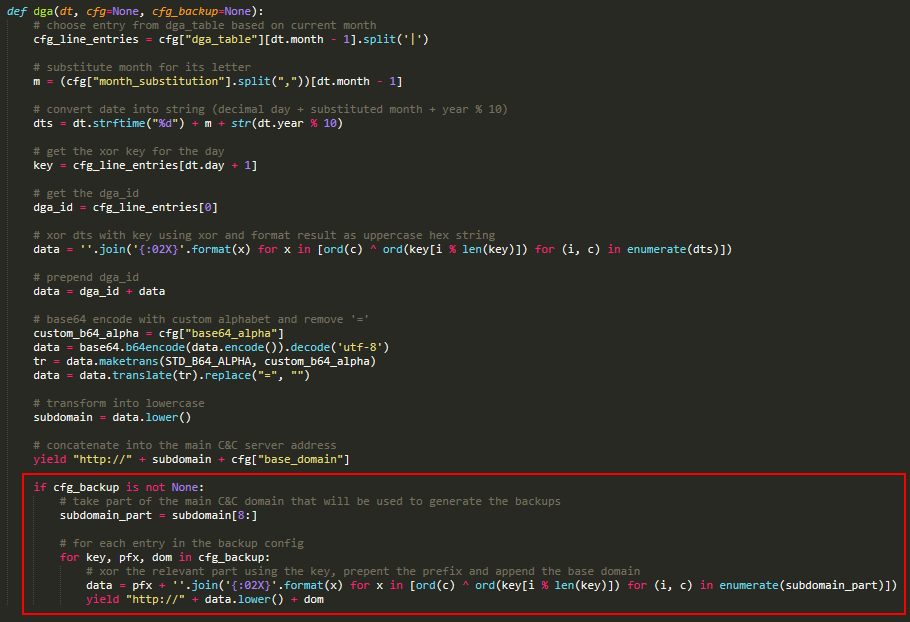
图7. Grandoreiro DGA计算在Python中重新实现
Grandoreiro has implemented, in some builds, a failsafe mechanism for when the main domain fails to resolve. This mechanism is not present in all builds and its logic has changed a few times, but the basic idea is illustrated in Figure 7. It uses a configuration that is constant in the samples we analyzed and can be generated by the simple code shown in Figure 8. Each entry consists of a key, a prefix, and a base domain.
Grandoreiro在某些构建中实现了一个故障安全机制,用于当主域无法解析时。这个机制并不存在于所有的构建中,它的逻辑也改变了几次,但基本思想如图7所示。它使用的配置在我们分析的示例中是恒定的,可以通过图8中所示的简单代码生成。每个条目由一个键、一个前缀和一个基本域组成。
The failsafe algorithm takes a part of the main C&C subdomain. It then iterates over all configuration entries, encrypts it using XOR and prepends a prefix, similar to the main algorithm part.
故障安全算法占C&C主子域的一部分。然后,它迭代所有配置条目,使用XOR对其进行加密,并添加前缀,类似于主算法部分。
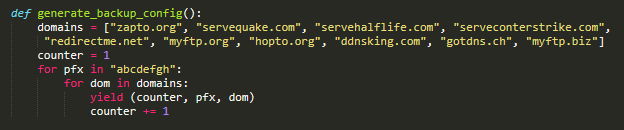
图8.在Python中重新实现的故障安全DGA配置生成器
Since September 2022, we have started to observe samples that utilize a slightly modified DGA. The algorithm remains almost identical, but rather than base64 encoding the subdomain in the final step, a hardcoded prefix is prepended to it. Based on our tracking, this method has become the dominant one since approximately July 2023.
自2022年9月起,我们开始观察使用经轻微修改的DGA的样本。该算法几乎保持相同,但在最后一步中不是对子域进行base64编码,而是在其前面添加硬编码前缀。根据我们的跟踪,自2023年7月以来,这种方法已成为主导方法。
Network protocol 网络协议
Grandoreiro utilizes RTC Portal, a set of Delphi components built on top of the RealThinClient SDK which is built on top of HTTP(S). The RTC Portal was discontinued in 2017 and its source code published on GitHub. Essentially, RTC Portal allows one or more Controls to remotely access one or more Hosts. Hosts and Controls are separated by a mediator component called Gateway.
Grandoreiro使用RTC Portal,这是一组构建在RealThinClient SDK之上的德尔菲组件,RealThinClient SDK构建在HTTP(S)之上。RTC Portal于2017年停止使用,其源代码发布在GitHub上。从本质上讲,RTC门户允许一个或多个控件远程访问一个或多个服务器。控制器和控件由称为网关的中介器组件分隔。
Grandoreiro operators use a console (acting as the Control) to connect to the C&C server (acting as Gateway) and to communicate with the compromised machines (acting as Hosts). To connect to Gateway, three parameters are required: a secret key, the key length, and a login.
Grandoreiro操作员使用控制台(作为控制)连接到C&C服务器(作为网关),并与受感染的机器进行通信(作为网关)。要连接到Gateway,需要三个参数:密钥、密钥长度和登录名。
The secret key is used to encrypt the initial request sent to the server. Therefore, the server also needs to know the secret key so as to decrypt the initial client request.
密钥用于加密发送到服务器的初始请求。因此,服务器还需要知道密钥,以便解密初始客户端请求。
The key length determines the length of the keys to encrypt the traffic, established during the handshake. The traffic is encrypted using a custom stream cipher. Two different keys are established – one for inbound and one for outbound traffic.
密钥长度确定在握手期间建立的用于加密流量的密钥的长度。流量使用自定义流密码进行加密。建立两个不同的密钥-一个用于入站流量,一个用于出站流量。
The login can be any string. The Gateway requires each connected component to have a unique login.
登录名可以是任何字符串。网关要求每个连接的组件具有唯一的登录名。
Grandoreiro uses two different combinations of secret key and key length values, always hardcoded in the binary, and we already discussed the login_string that is used as the login.
Grandoreiro使用两种不同的密钥和密钥长度值的组合,总是硬编码在二进制文件中,我们已经讨论过用作登录名的login_string。
The RTC documentation states that it can only handle a limited number of connections at once. Considering that each connected Host needs to send at least one request per second or else its connection is dropped, we believe that the reason Grandoreiro utilizes multiple C&C servers is an attempt not to overwhelm any one of them.
RTC文档指出,它一次只能处理有限数量的连接。考虑到每个连接的主机需要每秒发送至少一个请求,否则其连接将被丢弃,我们认为Grandoreiro使用多个C&C服务器的原因是试图不压倒其中任何一个。
Conclusion 结论
In this blogpost, we have provided a peek behind the curtain of our long-term tracking of Grandoreiro that helped to make this disruption operation possible. We have described in depth how Grandoreiro’s DGA works, how many different configurations exist simultaneously, and how we were able to spot many IP address overlaps among them.
在这篇博文中,我们提供了一个我们长期跟踪Grandoreiro的幕后故事,这有助于实现这一中断操作。我们已经深入描述了Grandoreiro的DGA是如何工作的,同时存在多少不同的配置,以及我们如何能够发现它们之间的许多IP地址重叠。
We have also provided statistical information obtained from the C&C servers. This information provides an excellent overview of the victimology and targeting, while also allowing us to see the actual level of impact.
我们也提供了从C&C服务器获得的统计信息。这些信息提供了受害者和目标的极好概述,同时也使我们能够看到实际的影响程度。
The disruption operation led by the Federal Police of Brazil aimed at individuals who are believed to be high up in the Grandoreiro operation hierarchy. ESET will continue to track other Latin American banking trojans while closely monitoring for any Grandoreiro activity following this disruption operation.
巴西联邦警察领导的破坏行动针对的是据信在Grandoreiro行动等级制度中身居高位的个人。ESET将继续跟踪其他拉丁美洲银行特洛伊木马,同时密切监测此次中断操作后的任何Grandoreiro活动。
For any inquiries about our research published on WeLiveSecurity, please contact us at [email protected].
有关我们在WeLiveSecurity上发表的研究的任何疑问,请通过[email protected]与我们联系。
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
ESET Research提供私人APT情报报告和数据馈送。有关此服务的任何查询,请访问ESET威胁情报页面。
IoCs
Files 文件
|
SHA-1 |
Filename FileName文件 |
Detection |
Description |
|
FB32344292AB36080F2D040294F17D39F8B4F3A8 |
Notif.FEL.RHKVYIIPFVBCGQJPOQÃ.msi |
Win32/Spy.Grandoreiro.DB |
MSI downloader |
|
08C7453BD36DE1B9E0D921D45AEF6D393659FDF5 |
RYCB79H7B-7DVH76Y3-67DVHC6T20-CH377DFHVO-6264704.msi |
Win32/Spy.Grandoreiro.DB |
MSI downloader |
|
A99A72D323AB5911ADA7762FBC725665AE01FDF9 |
pcre.dll |
Win32/Spy.Grandoreiro.BM |
Grandoreiro |
|
4CDF7883C8A0A83EB381E935CD95A288505AA8B8 |
iconv.dll |
Win32/Spy.Grandoreiro.BM |
Grandoreiro (with binary padding) |
Network
|
IP |
Domain 域 |
Hosting provider Hosting提供者 |
First seen 第一眼 |
Details |
|
20.237.166[.]161 20237166 [] 161 |
DGA‑generated DGA—Generated产生 |
Azure |
2024‑01‑12 2024—01—12 |
C&C server. C & C服务器。 |
|
20.120.249[.]43 20120249 [] 43 |
DGA‑generated DGA—Generated产生 |
Azure |
2024‑01‑16 |
C&C server. C&C服务器。 |
|
52.161.154[.]239 52.161.154[.] 239 |
DGA‑generated DGA生成 |
Azure |
2024‑01‑18 |
C&C server. C&C服务器。 |
|
167.114.138[.]249 167.114.138[.] 249 |
DGA‑generated DGA生成 |
OVH |
2024‑01‑02 |
C&C server. C&C服务器。 |
|
66.70.160[.]251 66.70.160[.] 251 |
DGA‑generated DGA生成 |
OVH |
2024‑01‑05 |
C&C server. C&C服务器。 |
|
167.114.4[.]175 167.114.4[.] 175 |
DGA‑generated DGA生成 |
OVH |
2024‑01‑09 |
C&C server. C&C服务器。 |
|
18.215.238[.]53 18.215.238[.] 53 |
DGA‑generated DGA生成 |
AWS |
2024‑01‑03 |
C&C server. C&C服务器。 |
|
54.219.169[.]167 54.219.169 167 |
DGA‑generated DGA生成 |
AWS |
2024‑01‑09 |
C&C server. C&C服务器。 |
|
3.144.135[.]247 3.144.135[.] 247 |
DGA‑generated DGA生成 |
AWS |
2024‑01‑12 |
C&C server. C&C服务器。 |
|
77.246.96[.]204 77.246.96[.] 204 |
DGA‑generated DGA生成 |
VDSina |
2024‑01‑11 |
C&C server. C&C服务器。 |
|
185.228.72[.]38 185.228.72[.] 38 |
DGA‑generated DGA生成 |
Master da Web Web大师 |
2024‑01‑02 |
C&C server. C&C服务器。 |
|
62.84.100[.]225 62.84.100 225 |
N/A |
VDSina |
2024‑01‑18 |
Distribution server. |
|
20.151.89[.]252 20.151.89[.] 252 |
N/A |
Azure |
2024‑01‑10 |
Distribution server. |
MITRE ATT&CK techniques MITRE ATT&CK技术
This table was built using version 14 of the MITRE ATT&CK framework.
此表是使用MITRE ATT&CK框架版本14构建的。
|
Tactic 战术 |
ID |
Name 名称 |
Description 描述 |
|
Resource Development 资源开发 |
Develop Capabilities: Malware |
Grandoreiro developers develop their own custom downloaders. |
|
|
Initial Access 初始接入 |
Phishing 钓鱼 |
Grandoreiro spreads through phishing emails. |
|
|
Execution 执行 |
User Execution: Malicious File |
Grandoreiro pressures victims to manually execute the phishing attachment. |
|
|
Persistence 持久性 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
Grandoreiro uses the standard Autostart locations for persistence. |
|
|
Hijack Execution Flow: DLL Search Order Hijacking |
Grandoreiro is executed by compromising the DLL search order. |
||
|
Defense Evasion 防御规避 |
Deobfuscate/Decode Files or Information |
Grandoreiro is often distributed in password-protected ZIP archives. |
|
|
Obfuscated Files or Information: Binary Padding |
Grandoreiro EXEs used to have enlarged .rsrc sections with large BMP images. |
||
|
System Binary Proxy Execution: Msiexec |
Grandoreiro downloaders are bundled inside MSI installers. |
||
|
Modify Registry 修改注册表 |
Grandoreiro stores part of its configuration data in the Windows registry. |
||
|
Discovery 发现 |
Application Window Discovery |
Grandoreiro discovers online banking websites based on window names. |
|
|
Process Discovery 流程发现 |
Grandoreiro discovers security tools based on process names. |
||
|
Software Discovery: Security Software Discovery |
Grandoreiro detects the presence of banking protection products. |
||
|
System Information Discovery |
Grandoreiro collects information about the victim’s machine, such as %COMPUTERNAME% and operating system. |
||
|
Collection 收集 |
Input Capture: GUI Input Capture |
Grandoreiro can display fake pop-ups and capture text typed into them. |
|
|
Input Capture: Keylogging |
Grandoreiro is capable of capturing keystrokes. |
||
|
Email Collection: Local Email Collection |
Grandoreiro’s operators developed a tool to extract email addresses from Outlook. |
||
|
Command and Control 指挥和控制 |
Data Encoding: Non-Standard Encoding |
Grandoreiro uses RTC, which encrypts data with a custom stream cipher. |
|
|
Dynamic Resolution: Domain Generation Algorithms |
Grandoreiro relies solely on DGA to obtain C&C server addresses. |
||
|
Encrypted Channel: Symmetric Cryptography |
In RTC, encryption and decryption are done using the same key. |
||
|
Non-Standard Port 非标准端口 |
Grandoreiro often uses non-standard ports for distribution. |
||
|
Application Layer Protocol |
RTC is built on top of HTTP(S). |
||
|
Exfiltration 渗出 |
Exfiltration Over C2 Channel |
Grandoreiro exfiltrates data to its C&C server. |
|
|
Impact 影响 |
System Shutdown/Reboot 系统重启 |
Grandoreiro can force a system reboot. |
