Malware authors have long targeted the market for free, cracked apps available through torrent services: in recent years a variety of cryptominers, adware, browser hijackers and bundled software installers have all plied their warez this way, but a recent macOS malware first spotted by researchers at Kaspersky is currently running rampant through dozens of different cracked copies of popular software.
长期以来,恶意软件作者一直瞄准市场,通过洪流服务提供免费的破解应用程序:近年来,各种加密矿工、广告软件、浏览器劫持者和捆绑软件安装程序都以这种方式进行宣传,但卡巴斯基研究人员最近首次发现的一种 macOS 恶意软件目前正在通过数十种不同的流行软件破解副本猖獗。
Aside from the scale of the campaign, macOS.Bkdr.Activator is concerning because its objective appears to be to infect macOS users on a massive scale, potentially for the purpose of creating a macOS botnet or delivering other malware at scale. The software titles targeted also include a range of business-focused and productivity apps that could be attractive in workplace settings.
除了活动的规模之外,macOS.Bkdr.Activator 也令人担忧,因为它的目标似乎是大规模感染 macOS 用户,可能是为了创建 macOS 僵尸网络或大规模传播其他恶意软件。目标软件标题还包括一系列以业务为中心的生产力应用程序,这些应用程序在工作场所环境中可能很有吸引力。

What is macOS.Bkdr.Activator?
什么是 macOS.Bkdr.Activator?
Researchers first identified the campaign earlier in January and noted how its multi-stage delivery made use of some novel techniques.
研究人员在1月初首次确定了该活动,并注意到其多阶段交付如何利用一些新技术。
Initial delivery method is via a torrent link which serves a disk image containing two applications: An apparently ‘uncracked’ and unusable version of the targeted software title, and an ‘Activator’ app that patches the software to make it usable. Users are instructed to copy both items to the /Applications folder before launching the Activator program.
最初的交付方法是通过一个 torrent 链接,该链接提供包含两个应用程序的磁盘映像:一个明显“未破解”且无法使用的目标软件标题版本,以及一个“Activator”应用程序,用于修补软件以使其可用。在启动 Activator 程序之前,指示用户将这两个项目复制到文件夹中 /Applications 。
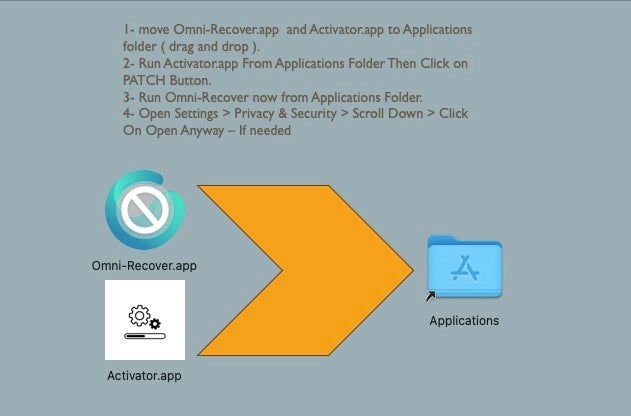
The Activator.app contains two malicious executables: a binary written in Swift named GUI located in the bundle’s MacOS folder, and a binary written in Objective-C named tool and stored in the Resources folder. The latter folder also contains a legitimate, signed installer for Python 3.9.
Activator.app 包含两个恶意可执行文件:一个用 Swift 编写的二进制文件,名为 GUI 位于捆绑包的 MacOS 文件夹中,另一个用 Objective-C 编写的二进制文件,命名 tool 并存储在 Resources 文件夹中。后一个文件夹还包含一个合法的、签名的 Python 3.9 安装程序。
On launching the Activator.app, victims are asked for an administrator password. This is used to turn off Gatekeeper settings via the spctl master-disable command and to allow apps sourced from ‘Anywhere’ to now run on the device.
启动 Activator.app 时,受害者会被要求输入管理员密码。这用于通过 spctl master-disable 命令关闭 Gatekeeper 设置,并允许来自“Anywhere”的应用程序现在在设备上运行。
Activator also checks for a Python install and, if absent, writes the Python package from its Resources folder to the /tmp directory.
Activator 还会检查 Python 安装,如果不存在,则将 Python 包从其 Resources 文件夹写入目录 /tmp 。
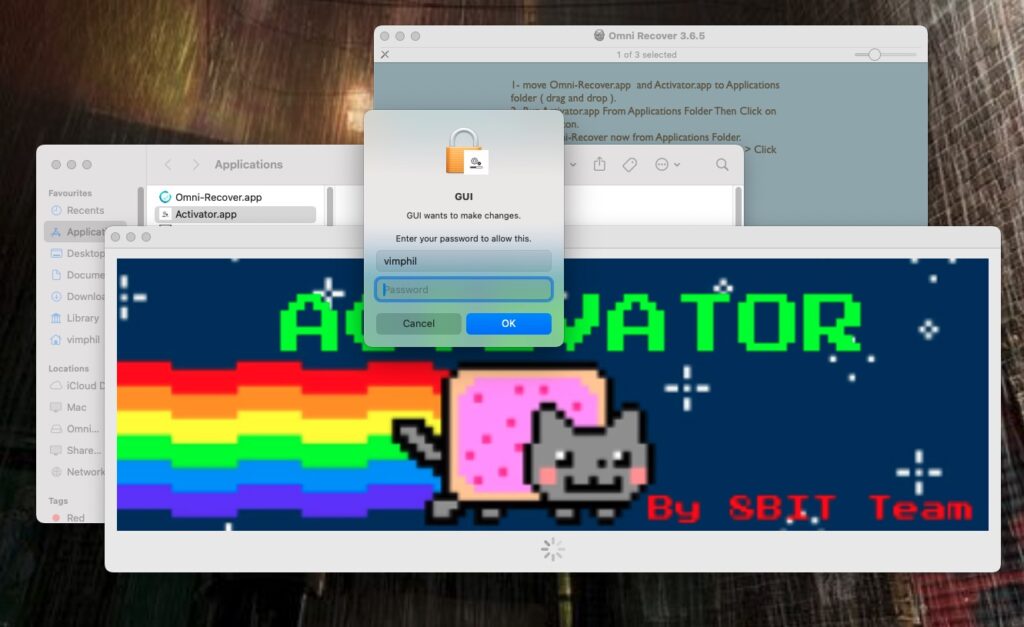
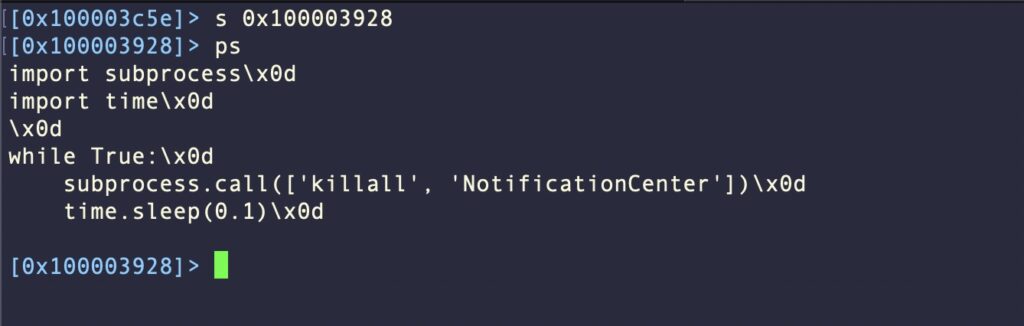
At this point the tool binary takes over, installs Python if required, and begins a series of malicious actions. The malware uses embedded Python code to kill the Notification Center. This is likely a means to bypass Apple’s attempt to alert users via Notifications when new persistence items like LaunchAgents are installed.
此时,二进制文件将接管,如果需要, tool 将安装 Python,并开始一系列恶意操作。该恶意软件使用嵌入式 Python 代码来杀死通知中心。这可能是绕过 Apple 在安装新的持久性项(如 LaunchAgents)时通过通知提醒用户的一种方法。
The Activator contains code to install a LaunchAgent at the following path, where the %@ variable is replaced with a UUID string generated at runtime.
Activator 包含用于在以下路径安装 LaunchAgent 的代码,其中 %@ 变量将替换为运行时生成的 UUID 字符串。
/Library/LaunchAgents/launched.%@.plist
#regex:
/Library/LaunchAgents/launched.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}\.plist
Prior to executing the Python script and installing the LaunchAgent, the tool binary attempts to retrieve a remote Python script. If the retrieval is successful, it then leverages the Apple defaults API to determine whether it has ran the same script before. Defaults allows programs to store preferences and other information that need to be maintained when the application isn’t running. While it is a standard macOS technology, it has rarely been leveraged by malware.
在执行 Python 脚本并安装 LaunchAgent 之前, tool 二进制文件会尝试检索远程 Python 脚本。如果检索成功,它将利用 Apple 默认 API 来确定它之前是否运行过相同的脚本。 Defaults 允许程序存储应用程序未运行时需要维护的首选项和其他信息。虽然它是一种标准的 macOS 技术,但它很少被恶意软件利用。
The Activator.app computes a hash of the script and saves it to the user defaults under the key lastExecutedScriptHash. If no hash has been previously saved or the stored hash is different, the retrived script is executed.
Activator.app 计算脚本的哈希值,并将其保存到用户默认值下的键 lastExecutedScriptHash 。如果之前未保存任何哈希值或存储的哈希值不同,则执行检索到的脚本。
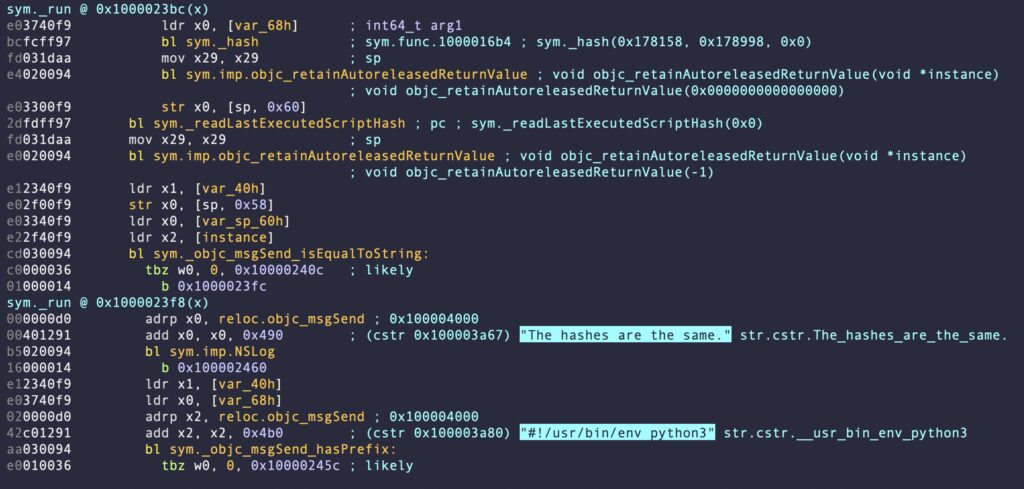
The application’s bundle identifier is “-.GUI”, so threat hunters may search the defaults database for signs of compromise with:
应用程序的捆绑标识符为“-.GUI“,因此威胁猎人可以在默认数据库中搜索以下入侵迹象:
defaults read "-.GUI"
macOS Torrents Infected with Backdoor Activator
感染了后门激活器的macOS种子
We have found several hundred unique Mach-O binaries on VirusTotal that are infected with macOS.Bkdr.Activator. Some have very low detection rates, and a few are currently not detected by any VirusTotal engines at all.
我们在 VirusTotal 上发现了数百个感染了 macOS.Bkdr.Activator 的独特 Mach-O 二进制文件。有些的检测率非常低,有些目前根本没有被任何 VirusTotal 引擎检测到。
Although the following list cannot be considered complete as new samples continue to be found, the malicious binaries we have discovered pertain to over 70 individual ‘cracked’ apps that have been hijacked for the Activator campaign.
尽管随着新样本的不断发现,以下列表不能被视为完整,但我们发现的恶意二进制文件与 70 多个单独的“破解”应用程序有关,这些应用程序已被 Activator 活动劫持。
Any of the following applications that have been sourced from a torrent site or anywhere other than their official distribution channels should be considered as a possible indicator of compromise and the host device inspected for signs of malware infection.
以下任何来自 torrent 站点或其官方分发渠道以外的任何地方的应用程序都应被视为可能的入侵指标,并检查主机设备是否有恶意软件感染的迹象。
| 4K Video Downloader 1.4.0 4K视频下载器 1.4.0 |
4K YouTube to MP3 Pro 5.1.0 4K YouTube 转 MP3 Pro 5.1.0 |
Aiseesoft Blu-ray Player Aiseesoft蓝光播放器 |
Alarm Clock Pro 15.6 闹钟专业版 15.6 |
| AnyMP4 iOS Cleaner 1.0.30 AnyMP4 iOS清洁器 1.0.30 |
Battery Indicator 2.17.0 电池指示灯 2.17.0 |
Bike 1.18.0 自行车 1.18.0 | Boxy SVG 4.21.1 四四方方的SVG 4.21.1 |
| Chain Timer 10.0 链式计时器 10.0 | Clipsy Clipboard Manager2.1 Clipsy 剪贴板管理器2.1 |
ColorWell 7.4.1 ColorWell 7.4.1 (英语) | Cookie 7.2.1 |
| Cover Desk 1.7 盖台 1.7 | DaisyDisk 4.26 (4.26) 菊花盘 4.26 (4.26) | DeliverExpress 2.7.11 交付快递 2.7.11 | Disk Xray 4.1.4 磁盘 X 射线 4.1.4 |
| Dropshare 5.45 直销份额 5.45 | Easy Data Transform 1.46.1 轻松转换数据 1.46.1 |
Eon Timer 2.9.11 Eon Timer 2.9.11 (英语) | Final Draft 12.0.10 最终草案 12.0.10 |
| Fix My iPhone 2.4.9 修复我的iPhone 2.4.9 |
FonePaw iOS Transfer 6.0.0 FonePaw iOS传输 6.0.0 |
FontLab 8.3.0.8766.0 Beta 字体实验室 8.3.0.8766.0 Beta |
Fork 2.38 叉子 2.38 |
| ForkLift 4.0.6 叉车 4.0.6 | getIRC – IRC Client 1.5 getIRC – IRC 客户端 1.5 |
Ghost Buster Pro 2.5.0 幽灵克星专业版 2.5.0 |
GrandTotal 8.2.2 总计 8.2.2 |
| Hides 5.9.2 隐藏 5.9.2 | HitPaw Video Converter 3.3.0 HitPaw视频转换器 3.3.0 |
Infuse Pro 7.6.6 注入专业版 7.6.6 | Invisible 2.8.0 隐形 2.8.0 |
| Iris 1.6.4 鸢尾花 1.6.4 | iShowUInstantAdvanced 1.4.19 | iTubeGo 7.4.0 Cracked iTubeGo 7.4.0破解版 | Keep It 2.3.7 保持它 2.3.7 |
| MacX DVD Ripper Pro 6.8.2 MacX DVD开膛手专业版 6.8.2 |
MacX MediaTrans 7.9 MacX 媒体传输 7.9 | Magic Battery 8.1.1 魔术电池 8.1.1 | Magic Disk Cleaner 2.6.0 魔盘清理器 2.6.0 |
| MarsEdit 5.1.2 火星编辑 5.1.2 | MetaImage 2.6.3 元映像 2.6.3 | Millumin 4 v4.18.d | Mission Control Plus 1.23 任务控制升级版 1.23 |
| Money Pro 2.10.4 金钱专业版 2.10.4 | MouseBoost Pro 3.3.5 MouseBoost 专业版 3.3.5 | NetWorker Pro 9.0.1 | Nisus Writer Express 4.4 尼苏斯作家快递 4.4 |
| Omni Toolbox 1.5.1 Omni工具箱 1.5.1 | OmniFocus Pro 4.0.3 OmniFocus 专业版 4.0.3 | OmniReader Pro 2.6.8 OmniReader 专业版 2.6.8 | Pastebot 2.4.6 粘贴机器人 2.4.6 |
| Perfectly Clear 4.6.0.2629 完美清除 4.6.0.2629 |
Privatus 7.0.2 私人 7.0.2 | QuickLinks 3.2 快速链接 3.2 | RAW Power 3.4.17 Cracked RAW Power 3.4.17 破解版 |
| Rhino-8 犀牛-8 | SimpleMind Pro 2.3.0 SimpleMind 专业版 2.3.0 | SiteSucker Pro 5.3.0 SiteSucker 专业版 5.3.0 | Soulver 3.10.0 灵魂 3.10.0 |
| SpamSieve 3.0.3 垃圾邮件筛 3.0.3 | Swinsian 3.0 斯温斯语 3.0 | SyncBird Pro 4.0.8 同步鸟专业版 4.0.8 | TechSmith Snagit 2023.2.6 |
| uDock 4.0.3 | Unclutter 2.2.6 整洁 2.2.6 | Valentina Studio Pro 13.7.0 瓦伦蒂娜工作室专业版 13.7.0 |
Web Confidential 5.4.3 网络机密 5.4.3 |
| WiFiSpoof 3.9.3 WiFi欺骗 3.9.3 | Xliff Editor 2.9.15 Xliff 编辑器 2.9.15 | xScope 4.7.0 xScope 4.7.0的 | zFuse Pro 1.7.36 zFuse 专业版 1.7.36 |
Further Stages 其他阶段
The Activator malware functions as a Stage 1 installer and downloader. The tool binary constructs a hardcoded domain name string and, according to Kaspersky researchers, retrieves TXT records for this domain from a DNS server. We were unable to confirm this in our tests, but the previous research suggests that the malware uses a novel technique of retrieving base64-encoded messages from the snippets contained in the DNS responses. These are then decrypted in-memory and were seen to contain a Python script which reached out to a further remote server to download the next stage.
Activator 恶意软件用作第 1 阶段安装程序和下载程序。该 tool 二进制文件构造了一个硬编码的域名字符串,根据卡巴斯基研究人员的说法,它从DNS服务器检索该域的TXT记录。我们无法在测试中证实这一点,但之前的研究表明,该恶意软件使用了一种新技术,从DNS响应中包含的代码段中检索base64编码的消息。然后,它们在内存中解密,并被视为包含一个 Python 脚本,该脚本连接到另一个远程服务器以下载下一阶段。
The content of these encrypted messages could change according to the operator’s whim, but in the observed case the final stage turned out to be a Python backdoor that allows the operator to execute arbitrary commands on the infected device. More details on this stage can be found here.
这些加密消息的内容可能会根据操作员的心血来潮而改变,但在观察到的情况下,最后阶段被证明是一个 Python 后门,允许操作员在受感染的设备上执行任意命令。有关此阶段的更多详细信息,请参见此处。
SentinelOne Detects macOS.Bkdr.Activator
SentinelOne 检测 macOS.Bkdr.Activator
The campaign is ongoing and we continue to track and identify new malicious samples. When the policy is set to ‘Protect’, the SentinelOne agent blocks execution of malicious samples. With the policy set to ‘Detect Only’, an alert is raised and the sample may be allowed to run for the purposes of observation.
该活动正在进行中,我们将继续跟踪和识别新的恶意样本。当策略设置为“保护”时,SentinelOne 代理会阻止恶意样本的执行。将策略设置为“仅检测”时,将引发警报,并可能允许运行示例以进行观察。
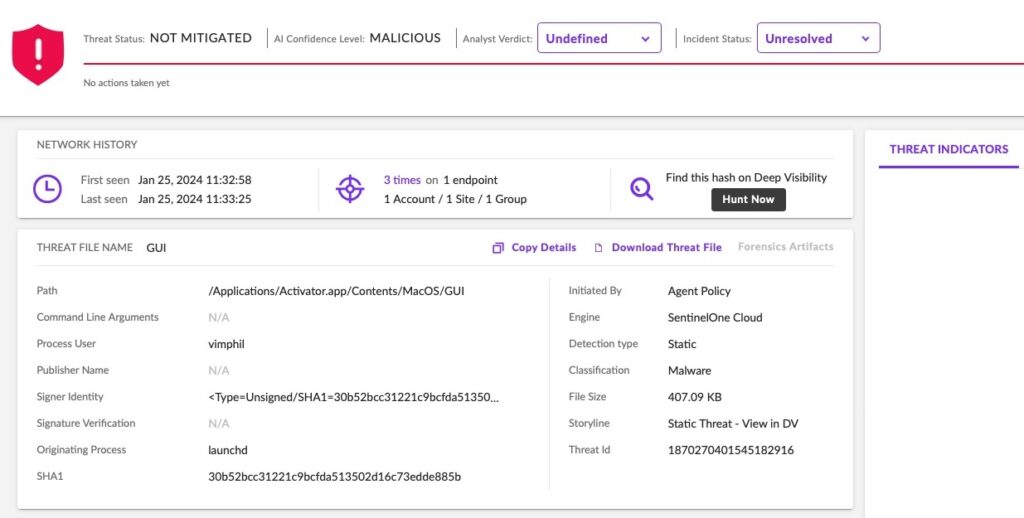
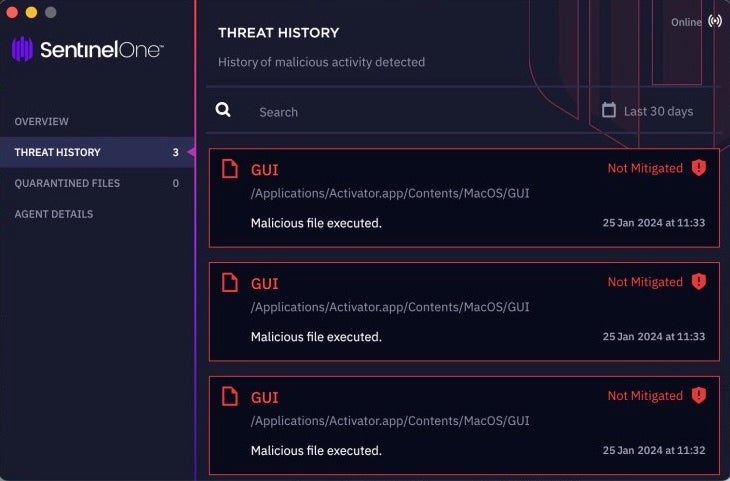
Indicators of Compromise
入侵指标
File Paths 文件路径
/tmp/python-3.9.6-macosx10.9.pkg
/Applications/Activator.app/Contents/MacOS/GUI
/应用程序/激活器.app/内容/MacOS/GUI
/Applications/Activator.app/Contents/Resources/tool
/应用程序/激活器:.app/内容/资源/工具
[~]/Library/LaunchAgents/launched.%@.plist
#regex:
/Library/LaunchAgents/launched.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}\.plist
SHA1 Mach-Os SHA1 马赫-OS
01223c67c44b9cb893576c624ceeb6971d7c8a64
02a38a5dd5dcff4354fab26601dd766c1d24293e
03c4a36c06c12e3420bd410a9600e09ddb4b4211
07da6661657d72a4d9fc14990bb57f46514318a9
08503aca7610a83aeb55d5cf68be16b221f677bf
14f6e7759541de4c31e6cdc5efd4059363b748a9
192fd322a6c4df2bb0e3d743dfe84d30c82512bd
1acaf1e08a03137827b9ef1972198cf9b52d0e15
1b434829544a5a63101e4d0e45ddb65ec840c841
21a5895c184b047c7b9aa7aa4f6451acbc8be826
21e6691d8466ecc6fbf25481cc33338ad47caf5c
25e12022e796d77f2496c3c2090febd048015a9f
28de5c653b938626b5c2663de07ec3affb61da7a
29f8c0f7f3a70ec114ac3cef2a47f0c285138fdb
2c6c43cf0655a2ed0d155ea12cfb100f1fc1f770
2c6d7642dd442d1e50985b938a4c5d827720b8b2
2e0159157a2443fe41abc1643d75cc923cda6896
2f26dc03de6ad3e8c7853588a96c524b5093d37e
315b793de51286b03fdedfd7bca1aa8885dfabb8
341e215d527c058d17c82ab34e4fc392a8d20575
343f788d605e9433aebc40edc3d1d621b11aef38
38d38f96558d3a476d9cf0b319299d069ae629e4
392377835b20d2faca7f40c5ea6959f8be0ca586
3a9a511b32753de5e3824abc91a1969bf12fbb47
3bac1bb68a996b0524d1082ec810d6af33061a50
429a81049145a7c03ec39e7d23a20a74d89d6dd9
4f2d4e69abf124edff096870271c4e1942ecef12
55d893acd26927a66583c200377f10baffc06347
5facd492d920ba088acb32d311ede7ae2190c7fd
5fd1f90079bfe29d519ab59380ab9d152e837b6d
61cf0c13d58bb03eaf8886e599132581f96a8585
65ca8d43bc622561d3b9b990873cb82ed2b7db6d
6bc6586134013472c5020e08648c946f5da859aa
719efeae3e91ba89222c8118ad76790cf996ae79
72c2469669b1aa50e0dc356dfc036a405ce26ef3
7966a3cdf552e698c6861849479cb25fb2fe22c7
7ebf2eba7be3535c6afd1195305f683a8d46f45a
8133447d1bfd6a704dbee353cecfa8105bdc324a
8c78b2b159894abf5dfaa08a4cd8b1b79aabe446
8d9f0539f82609de097c244d2c8182f7f240545f
8ecf86ee0eb436e30508b22bcda89585bf5a5613
9089265798cfd830240e1bb981df6e61aea49692
90ffd2f23d0c57c7b3becd52525d31aadcb142ba
92b476221f3b88de74e31aca92c44eb8ae8e1c6c
98e9bb5de5d8f487f84bca9276905a87a76d3bb4
9c75698e5ec05c3613510e866ef37673e1649536
a1bc32090d7a9599d14e5310ffd981727cec4d9a
a2a6948d39a3b1239d0e83792f3178c338aaefb6
编号:a2a6948d39a3b1239d0e83792f3178c338aaefb6
a3b9ea16b0d44e835d6458db44c018349f1cff3f
a5a28411bffe4efb72c99a63d234bffdd83bafef
A5A28411BFFE4EFB72C99A63D234BFFFD83BAFEF
a6fb4aaebd82681b5e5fac086cb4a41c7d64b718
b11d8ba52cef7fc9cd4b224a780bc2440afcfb82
货号:B11d8ba52cef7fc9cd4b224a780bc2440afcfb82
bc51a249ade7b619da3ad4d3593176381f114b01
c4e9f2bc657d32c9e642274c056b3d4a8e0bbb06
c74d70da36badfa1fb4914494d4e952fa56fdbb1
caadd51d6191966002986f5529ab3b60622f9a03
cd4d2e325fd4741bf7c1918e9f341a3bc0e2c45c
d326b6f10d91965282ba0eb0041f2bb3dc0c004b
d58823309eeed0a40287d1df22ce799a672483db
d5b4ba66b24becfce2944a0df7b5d36f2a617ebf
d73cb24b88bdeb29ea09a867d67006061f3d9464
db49f7b2ebb06eba1a821ed9a0050ca36a38d31e
dc64a04830d9209142c72937cd348d581afbad09
dcb8efd9817a46f79021afcad9ea67ef4c898ff6
def1ca81e74dad6bef7cd37d896d9521afd3e19e
e18c9dff96ba0b982cbfd1911db24f974db82cce
e439e6a35fe685b909e8656fed03b4c2ae8533cd
e591b784a7a6783580e8674ff1b263d5a6d91e86
e85cc29f9ea7c7cfcb31450cecaed85bc0201d32
e8613f03b1cbebb6c6fa42a65aef59ab547a8a59
eca71e86d45b43a558f1f05acd6fdbf48c79f097
ee90f40748c4bd0ba78abbf113a6251f39a5bbd5
f3f498574f91da8fc4a69e5ae35dbfcb058abb7b
fa08c5f4c6dbb5f32288ea05ed558ffcd273f181
