Last week I attended TROOPERS23 in Heidelberg.
Great event, great community, great talks! In the following I’ll summarize a couple of them which I found particularly interesting.
Jiska Classen & Alexander Heinrich: Attacking Ultra-Wideband: Security Analysis of UWB Applications in Smartphones
Jiska and Alexander have done quite some significant security research of radio technologies in the past, and they’re seasoned Troopers speakers. In this talk they covered some very cool recent work on ultra-wideband, which is also discussed here and here.
One of the (security) objectives of UWB is to provide precise distance measurements, which are then used in a variety of contexts, namely for passive keyless entry (PKES) to cars. Hence successful attacks against the distance measurement function of UWB can have severe implications for physical security. With a specific low-cost hardware setup (details see the first paper linked above) they managed to trick certain chips into incorrectly measuring the distance between the initiator and the responder of a measurement.


A newer class of attacks (called Mix-Down and Stretch-and-Advance attacks, see also 2nd link above) affects different chips:

They stressed several times that it doesn’t matter how secure some used crypto is once the underlying physical layer is already broken.
Conclusions, taken from their 2022 paper:

Axelle Apvrille: Stay fit. Hack a Jump Rope
Axelle had also spoken at Troopers before (in 2018, on smart toothbrushes), and this year she covered a smart … jump rope. For the security evaluation she focused on the app instead of other approaches involving hardware-based setups like sniffing the BLE communication (and she emphasized that generally this is her preferred approach):
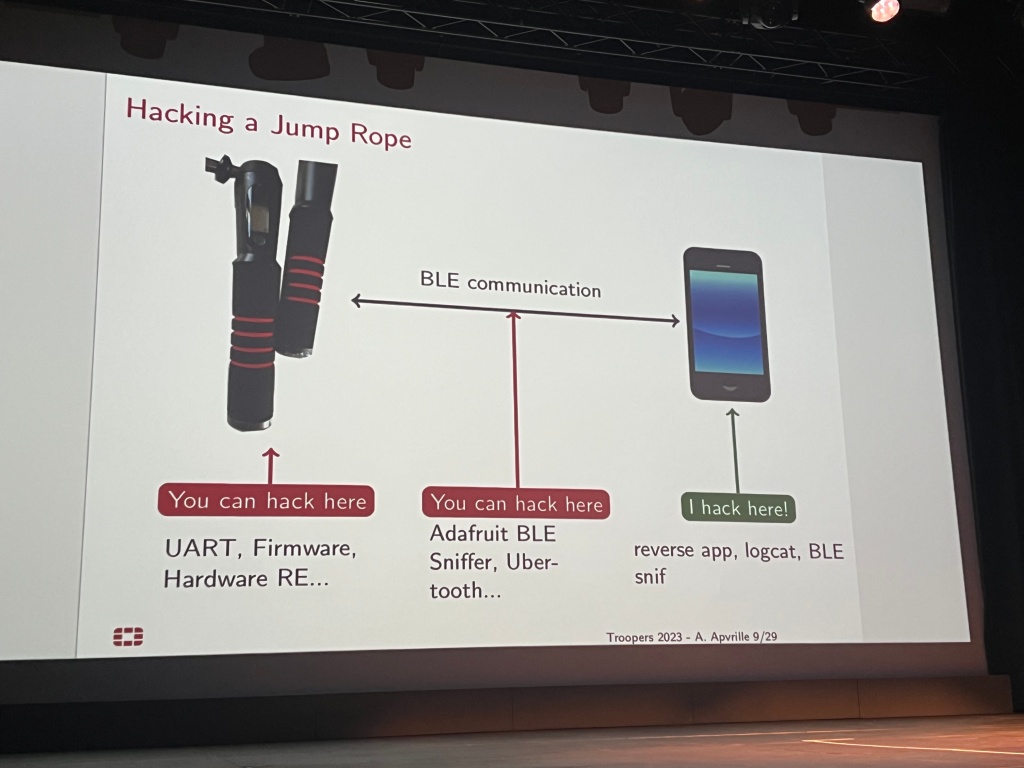
It turned out that the interaction between the device and the app generates log entries, so she performed a couple of jumps live on stage in order to generate some samples ;-), which allowed to further understand the device <-> app communication.


In the talk’s second half Axelle explained how she integrated the analyzed jump rope into the 2022 edition of Ph0wn, a CTF dedicated to smart devices, which she organizes.

Apparently Axelle had fun with the Troopers badge, too, and she wrote about this here (shout-out goes to Dennis for the related challenge).
Francisco Falcon: Vulnerabilities in the TPM 2.0 reference implementation code
Francisco spoke about two vulnerabilities which he had found in the TPM reference implementation (see also this blogpost). He started with this funny slide which nevertheless contains an important message (industry-wide implementation of code from a single – flawed – source, which actually reminded me of the 3GPP world. I did a bit telco of security research many years ago, and in the 3GPP world often code generators are used, based on parsing bulky 3GPP standards):

That message becomes clearer here:

He managed to identify an out-of-bounds write (CVE-2023-1017) and an out-of-bounds read (CVE-2023-1018).




A couple of aspects are of particular interest here:
- (large parts of) the communication to/from the TPM is encrypted. The vulnerabilities lie in the TPM-side code that actually parses the encrypted parameters (more specifically in the CryptParameterDecryption function). So pursuing certain security objectives (mainly confidentiality, and potentially integrity/authenticity) of the OS↔TPM communication leads to vulns that compromise the integrity of the secure entity (here: the TPM) itself.
- An OOB write of just 2 bytes may not seem like a very powerful primitive at first, but in 2022 two other Quarkslab folks had managed to obtain code execution on the Google Titan M chip with an OOB write of a single byte (see this TROOPERS22 talk, or this blogpost).
Here are the conclusions:


Francisco also gave the talk at Pass the SALT a couple of days later, and the video of that one is already published here.
Nils Weiss & Enrico Pozzobon: Fault Injection Attacks on Secure Automotive Bootloaders
Nils and Enrico are veteran Troopers speakers on automotive security topics. This year they spoke about EMFI attacks against bootloaders in ECUs. This was a spectacular talk, but following Nils’ request (see this thread) I will only publish details here later.
Stefan Schiller: Monitoring Solutions. Attacking IT Infrastructure at its Core
I couldn’t watch this one as it happened at the same time as the above automotive security talk, but I heard it was a great talk as well (continuing the tradition of the legend OSMOSIS talk from Troopers 2014). A write-up of Stefan‘s talk can be found here.
原文始发于:TROOPERS 23