原文始发于DMITRY KALININ:SoumniBot: the new Android banker’s unique techniques

The creators of widespread malware programs often employ various tools that hinder code detection and analysis, and Android malware is no exception. As an example of this, droppers, such as Badpack and Hqwar, designed for stealthily delivering Trojan bankers or spyware to smartphones, are very popular among malicious actors who attack mobile devices. That said, we recently discovered a new banker, SoumniBot, which targets Korean users and is notable for an unconventional approach to evading analysis and detection, namely obfuscation of the Android manifest.
广泛传播的恶意软件程序的创建者经常使用各种阻碍代码检测和分析的工具,Android 恶意软件也不例外。例如,Badpack 和 Hqwar 等滴管器旨在将特洛伊木马银行家或间谍软件秘密地运送到智能手机,在攻击移动设备的恶意行为者中非常受欢迎。也就是说,我们最近发现了一个新的银行家 SoumniBot,它以韩国用户为目标,以一种非常规的方法来逃避分析和检测,即混淆 Android 清单。
SoumniBot obfuscation: exploiting bugs in the Android manifest extraction and parsing procedure
SoumniBot 混淆:利用 Android 清单提取和解析过程中的错误
Any APK file is a ZIP archive with AndroidManifest.xml in the root folder. This file contains information about the declared components, permissions and other app data, and helps the operating system to retrieve information about various app entry points. Just like the operating system, the analyst starts by inspecting the manifest to find the entry points, which is where code analysis should start. This is likely what motivated the developers of SoumniBot to research the implementation of the manifest parsing and extracion routine, where they found several interesting opportunities to obfuscate APKs.
任何APK文件都是ZIP存档,AndroidManifest.xml在根文件夹中。此文件包含有关声明的组件、权限和其他应用数据的信息,并帮助操作系统检索有关各种应用入口点的信息。就像操作系统一样,分析师首先检查清单以查找入口点,这是代码分析应该开始的地方。这可能就是促使 SoumniBot 的开发人员研究清单解析和外延例程的实现的原因,他们在那里发现了几个混淆 APK 的有趣机会。
Technique 1: Invalid Compression method value
技术 1:压缩方法值无效
This is a relatively well-known technique used by various types of malware including SoumniBot and associated with the way manifests are unpacked. In libziparchive library, the standard unarchiving function permits only two Compression method values in the record header: 0x0000 (STORED, that is uncompressed) и 0x0008 (DEFLATED, that is compressed with deflate from the zlib library), or else it returns an error.
这是一种相对众所周知的技术,被各种类型的恶意软件(包括 SoumniBot)使用,并与清单的解压缩方式相关联。在 libziparchive 库中,标准取消存档函数只允许在记录标头中使用两个压缩方法值:0x0000(STORED,未压缩)и 0x0008(DEFLATED,使用 zlib 库中的 deflate 压缩),否则会返回错误。
Yet, instead of using this function, the developers of Android chose to implement an alternate scenario, where the value of the Compression method field is validated incorrectly.
然而,Android 的开发人员没有使用此函数,而是选择实现另一种方案,其中 Compression method 字段的值被错误地验证。
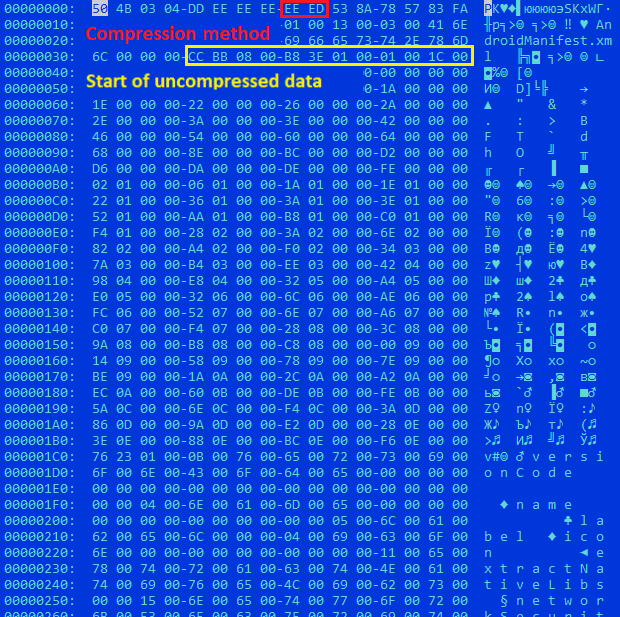
If the APK parser comes across any Compression method value but 0x0008 (DEFLATED) in the APK for the AndroidManifest.xml entry, it considers the data uncompressed. This allows app developers to put any value except 8 into Compression method and write uncompressed data. Although any unpacker that correctly implements compression method validation would consider a manifest like that invalid, the Android APK parser recognizes it correctly and allows the application to be installed. The image below illustrates the way the technique is executed in the file b456430b4ed0879271e6164a7c0e4f6e.
如果 APK 解析器在 AndroidManifest.xml 条目的 APK 中遇到任何压缩方法值,但0x0008 (DEFLATED),则认为数据已未压缩。这允许应用程序开发人员将除 8 以外的任何值放入压缩方法中并写入未压缩的数据。尽管任何正确实现压缩方法验证的解压缩器都会认为此类清单无效,但 Android APK 解析器会正确识别它并允许安装应用程序。下图说明了该技术在文件 b456430b4ed0879271e6164a7c0e4f6e 中的执行方式。
Technique 2: Invalid manifest size
技术 2:清单大小无效
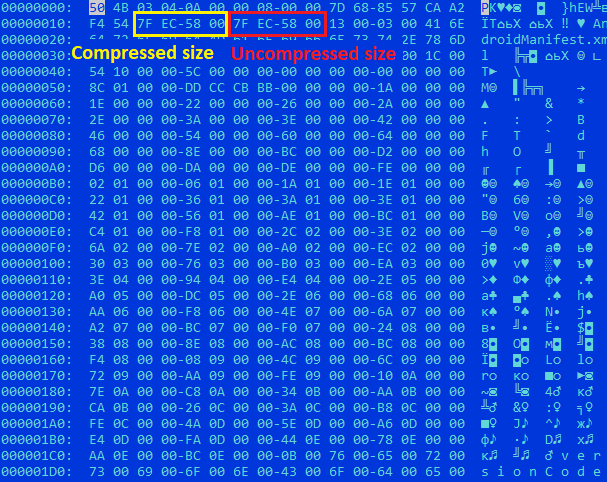
Let’s use the file 0318b7b906e9a34427bf6bbcf64b6fc8 as an example to review the essence of this technique. The header of AndroidManifest.xml entry inside the ZIP archive states the size of the manifest file. If the entry is stored uncompressed, it will be copied from the archive unchanged, even if its size is stated incorrectly. The manifest parser ignores any overlay, that is information following the payload that’s unrelated to the manifest. The malware takes advantage of this: the size of the archived manifest stated in it exceeds its actual size, which results in overlay, with some of the archive content being added to the unpacked manifest. Stricter manifest parsers wouldn’t be able to read a file like that, whereas the Android parser handles the invalid manifest without any errors.
我们以文件0318b7b906e9a34427bf6bbcf64b6fc8为例,回顾一下这种技术的本质。ZIP 存档中AndroidManifest.xml条目的标题声明清单文件的大小。如果条目未压缩存储,则即使其大小陈述不正确,也会原封不动地从存档中复制。清单分析器忽略任何覆盖,即有效负载后面与清单无关的信息。恶意软件利用了这一点:其中所述的存档清单的大小超过了其实际大小,这会导致覆盖,一些存档内容被添加到解压缩的清单中。更严格的清单解析器将无法读取这样的文件,而 Android 解析器可以处理无效的清单而不会出现任何错误。
Note that although live devices interpret these files as valid, apkanalyzer, Google’s own official utility for analyzing assembled APKs, cannot handle them. We have notified Google accordingly.
请注意,尽管实时设备将这些文件解释为有效,但 apkanalyzer(Google 自己用于分析组装的 APK 的官方实用程序)无法处理它们。我们已相应地通知了谷歌。
Technique 3: Long namespace names
技术 3:长命名空间名称
The SoumniBot malware family, for example the file fa8b1592c9cda268d8affb6bceb7a120, has used this technique as well. The manifest contains very long strings, used as the names of XML namespaces.
SoumniBot 恶意软件家族(例如文件 fa8b1592c9cda268d8affb6bceb7a120)也使用了这种技术。清单包含很长的字符串,用作 XML 命名空间的名称。
Manifests that contain strings like these become unreadable for both humans and programs, with the latter may not be able to allocate enough memory to process them. The manifest parser in the OS itself completely ignores namespaces, so the manifest is handled without errors.
包含此类字符串的清单对于人类和程序来说都是不可读的,后者可能无法分配足够的内存来处理它们。操作系统本身中的清单分析器完全忽略命名空间,因此可以毫无错误地处理清单。
What’s under the obfuscation: SoumniBot’s functionality
混淆之下的内容:SoumniBot 的功能
When started, the application requests a configuration with two parameters, mainsite и mqtt, from the server, whose address being a hardcoded constant.
启动时,应用程序会从服务器请求具有两个参数的配置,mainsite и mqtt,其地址是硬编码常量。
Both parameters are server addresses, which the malware needs for proper functioning. The mainsite server receives collected data, and mqtt provides MQTT messaging functionality for receiving commands. If the source server did not provide these parameters for some reason, the application will use the default addresses, also stored in the code.
这两个参数都是服务器地址,恶意软件需要这些地址才能正常运行。主站服务器接收采集到的数据,mqtt 提供 MQTT 消息传递功能,用于接收命令。如果源服务器由于某种原因未提供这些参数,则应用程序将使用默认地址,这些地址也存储在代码中。
After requesting the parameters, the application starts a malicious service. If it cannot start or stops for some reason, a new attempt is made every 16 minutes. When run for the first time, the Trojan hides the app icon to complicate removal, and then starts to upload data in the background from the victim’s device to mainsite every 15 seconds. The data includes the IP address, country deduced from that, contact and account lists, SMS and MMS messages, and the victim’s ID generated with the help of the trustdevice-android library. The Trojan also subscribes to messages from the MQTT server to receive the commands described below.
请求参数后,应用程序启动恶意服务。如果由于某种原因无法启动或停止,则每 16 分钟进行一次新的尝试。首次运行时,该木马会隐藏应用程序图标以使删除复杂化,然后开始每 15 秒在后台将数据从受害者的设备上传到主站点。数据包括 IP 地址、从中推断出的国家/地区、联系人和帐户列表、短信和彩信,以及借助 trustdevice-android 库生成的受害者 ID。该木马还订阅来自 MQTT 服务器的消息,以接收下述命令。
| # | Description | Parameters |
| 0 | Sends information about the infected device: phone number, carrier, etc., and the Trojan version, followed by all of the victim’s SMS messages, contacts, accounts, photos, videos and online banking digital certificates. 发送有关受感染设备的信息:电话号码、运营商等,以及木马版本,然后是受害者的所有短信、联系人、帐户、照片、视频和网上银行数字证书。 |
– |
| 1 | Sends the victim’s contact list. 发送受害者的联系人列表。 |
– |
| 2 | Deletes a contact on the victim’s device. 删除受害者设备上的联系人。 |
data: the name of the contact to delete data:要删除的联系人姓名 |
| 3 | Sends the victim’s SMS and MMS messages. 发送受害者的短信和彩信。 |
– |
| 4 | A debugging command likely to be replaced with sending call logs in a new version. 在新版本中,可能会替换为发送呼叫日志的调试命令。 |
– |
| 5 | Sends the victim’s photos and videos. 发送受害者的照片和视频。 |
– |
| 8 | Sends an SMS message. 发送 SMS 消息。 |
data: ID that the malware uses to receive a message to forward. The Trojan sends the ID to mainsite and gets message text in return. data:恶意软件用于接收要转发的消息的 ID。特洛伊木马将 ID 发送到主站点并获取消息文本作为回报。 |
| 24 | Sends a list of installed apps. 发送已安装应用的列表。 |
– |
| 30 | Adds a new contact on the device. 在设备上添加新联系人。 |
name: contact name; phoneNum: phone number 姓名:联系人姓名;phoneNum:电话号码 |
| 41 | Gets ringtone volume levels. 获取铃声音量级别。 |
– |
| 42 | Turns silent mode on or off. 打开或关闭静音模式。 |
data: a flag set to 1 to turn on silent mode and to 0 to turn it off data:设置为 1 以打开静默模式,设置为 0 以将其关闭的标志 |
| 99 | Sends a pong message in response to an MQTT ping request. 发送 pong 消息以响应 MQTT ping 请求。 |
– |
| 100 | Turns on debug mode. 打开调试模式。 |
– |
| 101 | Turns off debug mode. 关闭调试模式。 |
– |
The command with the number 0 is worth special mention. It searches, among other things, external storage media for .key and .der files that contain paths to /NPKI/yessign.
特别值得一提的是数字为 0 的命令。除其他事项外,它还在外部存储介质中搜索包含 /NPKI/yessign 路径的 .key 和 .der 文件。
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
public static List getAllBankingKeys(Context context) {
List list = new ArrayList();
Cursor cursor = context.getContentResolver().query(MediaStore.Files.getContentUri(“external”),
new String[]{“_id”, “mime_type”, “_size”, “date_modified”, “_data”},
“(_data LIKE \’%.key\’ OR _data LIKE \’%.der\’)”, null, null);
int index = cursor == null ? 0 : cursor.getColumnIndexOrThrow(“_data”);
if (cursor != null) {
while (cursor.moveToNext()) {
String s = cursor.getString(index);
If (!s.contains(“/NPKI/yessign”)) {
continue;
}
Logger.log(“path is:” + s);
list.add(s);
break;
}
cursor.close();
}
return list;
}
|
If the application finds files like that, it copies the directory where they are located into a ZIP archive and sends it to the C&C server. These files are digital certificates issued by Korean banks to their clients and used for signing in to online banking services or confirming banking transactions. This technique is quite uncommon for Android banking malware. Kaspersky security solutions detect SoumniBot despite its sophisticated obfuscation techniques, and assign to it the verdict of Trojan-Banker.AndroidOS.SoumniBot.
如果应用程序找到这样的文件,它会将它们所在的目录复制到 ZIP 存档中,并将其发送到 C&C 服务器。这些文件是韩国银行向其客户颁发的数字证书,用于登录网上银行服务或确认银行交易。这种技术在 Android 银行恶意软件中非常罕见。卡巴斯基安全解决方案可检测 SoumniBot,尽管其混淆技术很复杂,但会将其分配给 Trojan-Banker.AndroidOS.SoumniBot 的判定。
Conclusion 结论
Malware creators seek to maximize the number of devices they infect without being noticed. This motivates them to look for new ways of complicating detection. The developers of SoumniBot unfortunately succeeded due to insufficiently strict validations in the Android manifest parser code.
恶意软件创建者试图在不被注意的情况下最大限度地增加他们感染的设备数量。这促使他们寻找使检测复杂化的新方法。不幸的是,由于 Android 清单解析器代码中的验证不够严格,SoumniBot 的开发人员成功了。
We have detailed the techniques used by this Trojan, so that researchers around the world are aware of the tactics, which other types of malware might borrow in the future. Besides the unconventional obfuscation, SoumniBot is notable for stealing Korean online banking keys, which we rarely observe in Android bankers. This feature lets malicious actors empty unwitting victims’ wallets and circumvent authentication methods used by banks. To avoid becoming a victim of malware like that, we recommend using a reliable security solution on your smartphone to detect the Trojan and prevent it from being installed despite all its tricks.
我们详细介绍了该木马使用的技术,以便世界各地的研究人员了解其他类型的恶意软件将来可能会借用的策略。除了非常规的混淆之外,SoumniBot 还以窃取韩国网上银行密钥而闻名,我们在 Android 银行家中很少观察到这种情况。此功能允许恶意行为者清空不知情的受害者的钱包并规避银行使用的身份验证方法。为避免成为此类恶意软件的受害者,我们建议您在智能手机上使用可靠的安全解决方案来检测木马并防止其安装,尽管它有各种技巧。
Indicators of compromise
妥协指标
MD5
0318b7b906e9a34427bf6bbcf64b6fc8
00aa9900205771b8c9e7927153b77cf2
b456430b4ed0879271e6164a7c0e4f6e
fa8b1592c9cda268d8affb6bceb7a120
C&C
https[://]google.kt9[.]site
https[://]google.kt9[.]网站
https[://]dbdb.addea.workers[.]dev
https[://]dbdb.addea.workers[.]开发
转载请注明:SoumniBot: the new Android banker’s unique techniques | CTF导航