原文始发于RHINO:CVE-2022-25237: Bonitasoft Authorization Bypass and RCE
Vulnerability Overview
Bonita Web 2021.2 is affected by an authentication/authorization bypass vulnerability due to an overly broad filter pattern used in the API authorization filters.
By appending a crafted string to the API URL, users with no privileges can access privileged API endpoints. This can lead to remote code execution by abusing the privileged API actions to deploy malicious code onto the server.
Affected Product
Vendor: Bonitasoft
Product: Bonita Platform
Confirmed Vulnerable Version: < 2022.1-u0
Fixed Versions:
For community:
- 2022.1-u0 (7.14.0)
For subscription:
- 2022.1-u0 (7.14.0)
- 2021.2-u4 (7.13.4)
- 2021.1-0307 (7.12.11)
- 7.11.7
Vulnerable Versions: Official Docker image
What is Bonitasoft
Bonitasoft has 5M+ downloads from Dockerhub, it is a business automation platform allowing to more easily build, deploy and manage automation applications in business processes.
From the vendor’s website:
Bonita is an open-source and extensible platform for business process automation and optimization. Bonita Platform accelerates the development, go-to-production, and maintenance of automation projects. While allowing users to execute tasks that impact their business data, it also efficiently integrates with existing information systems and orchestrates heterogeneous systems, some of them being soft robots.
It provides deep visibility of process execution across the organization through its embedded end-user applications or the Living applications built by the project team to perfectly fit the business needs.
Technical Vulnerability Details
The web.xml file for a Tomcat Java application defines the routes within the application. It also can define how the authentication and authorization of routes in the application are handled. It is always one of the first places to look for potential authentication and authorization bypasses. Specifically, the “filters” defined in the web.xml can often be fruitful as they can determine what should or should not be filtered with authorization to access a particular route.
The following authorization filters specify an excludePattern parameter of “i18ntranslation” and then pass the parameter to 2 different filter classes: RestAPIAuthorizationFilter, TokenValidatorFilter.
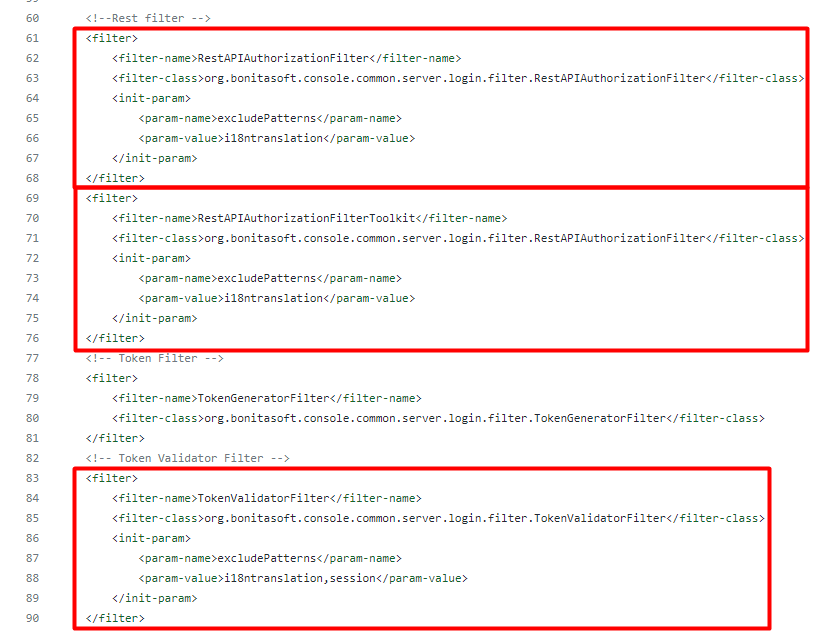
Taking a look at these filters they both extend the AbstractAuthorizationFilter, which contains the doFilter method. Inside the doFilter method. A check using the “sessionIsNotNeeded” function is used, which will continue the application flow if it returns true.
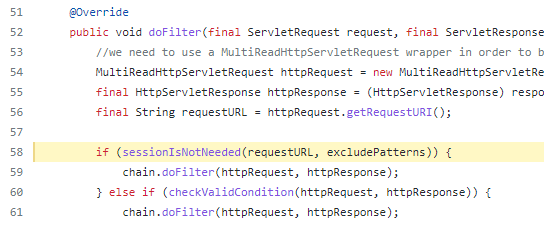
The sessionIsNotNeeded function shown below checks for excludePatterns in URLs. If the URL contains this pattern in the path then the authorization filter is bypassed allowing access to the resource.
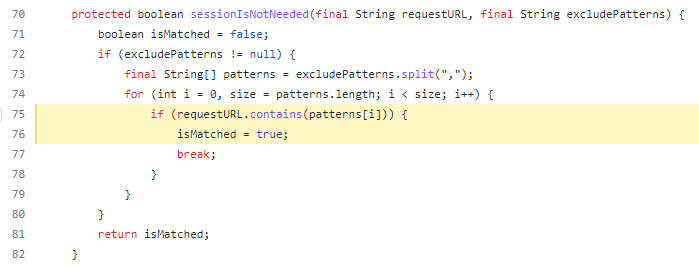
As we saw in the web.xml, the pattern which is passed in this parameter is “i18ntranslation” This means if this string is anywhere in the URL path, it will allow authorization/authentication to be bypassed for the API endpoints.
Two values were found that work to accomplish this. Simply appending either “/i18ntranslation/../” or “;i18ntranslation” to the API URL will allow authorization to be bypassed.
Caveat: Although this technically allows a full authentication bypass, its not able to be exploited without a valid user session. The user doesn’t need permissions, as long as they have a valid session token. In the case of a null session, the application will error out if it is unable to lookup values based on the session token, causing the bypass to fail.
Bonita Exploit Proof of Concept
To run the vulnerable version of Bonita, you can use the docker repository:
docker run –name CVE-2022-25237 -d -p 8080:8080 bonita:7.13.0
Log into http://localhost:8080/bonita and create a low privileged user in the “User” profile. We have published a PoC that achieves code execution on our CVE GitHub repository.

Conclusion
This is a good reminder that when using matching patterns and regular expressions to implement security controls it is important to always be as strict as possible with those patterns and thoroughly test them to look for unintended behavior.
We also want to thank the Bonitasoft team for working with us on getting this patched in a timely manner. As always, feel free to follow us on Twitter for more releases and blog posts: @RhinoSecurity, @daveysec
Disclosure Timeline
| 2/18/2022 | Reported to Bonitasoft |
| 2/21/2022 | Bonitsoft requested clarification on the PoC |
| 2/23/2022 | Rhino sent a corrected payload for the PoC |
| 3/14/2022 | Bonitasoft shares update on patching and a workaround for the vulnerability |
| 4/5/2022 | Bonitasoft confirm fixes have been released for community and subscription versions |
转载请注明:CVE-2022-25237: Bonitasoft Authorization Bypass and RCE | CTF导航