原文始发于leviathansecurity:TunnelVision (CVE-2024-3661): How Attackers Can Decloak Routing-Based VPNs For a Total VPN Leak
TunnelVision (CVE-2024-3661): How Attackers Can Decloak Routing-Based VPNs For a Total VPN Leak

Recently, we identified a novel network technique that bypasses VPN encapsulation. An attacker can use this technique to force a target user’s traffic off their VPN tunnel using built-in features of DHCP (Dynamic Host Configuration Protocol). The result of this is the user transmits packets that are never encrypted by a VPN, and an attacker can snoop their traffic. We are using the term decloaking to refer to this effect. Importantly, the VPN control channel is maintained so features such as kill switches are never tripped, and users continue to show as connected to a VPN in all the cases we’ve observed.
最近,我们发现了一种绕过VPN封装的新型网络技术。攻击者可以使用此技术,通过 DHCP(动态主机配置协议)的内置功能强制目标用户的流量离开其 VPN 隧道。其结果是用户传输从未被 VPN 加密的数据包,攻击者可以窥探他们的流量。我们使用术语“去隐身”来指代这种效果。重要的是,VPN控制通道得到了维护,因此终止开关等功能永远不会跳闸,并且在我们观察到的所有情况下,用户都会继续显示已连接到VPN。
We’ve spent extensive time exploring this capability and attempting to notify as many affected parties as possible. We also know it is our responsibility as security researchers to inform the security and privacy community, as well as the general public, about this threat. We also believe this technique may have been possible as far back as 2002 and could have already been discovered* and potentially used in the wild. For that reason, we believe it is critical for us to disclose publicly because notifying every VPN provider, operating system maintainer, self-hosted VPN admin, and VPN user is far beyond the capacity of our small research team.
我们花了大量时间探索此功能,并尝试通知尽可能多的受影响方。我们也知道,作为安全研究人员,我们有责任向安全和隐私社区以及公众通报这种威胁。我们还认为,这种技术可能早在 2002 年就已经实现,并且可能已经被发现*并可能在野外使用。出于这个原因,我们认为公开披露对我们来说至关重要,因为通知每个 VPN 提供商、操作系统维护者、自托管 VPN 管理员和 VPN 用户远远超出了我们小型研究团队的能力。
We’ve seen one mitigation for this technique, as well as identified a fix that exists on Linux-based operating systems. However, the mitigation offers a side channel that could be used for targeted denial-of-service censorship, as well as to de-anonymize the destination of traffic via traffic analysis. In some places in the world, the side-channel alone could lead to imprisonment or death for those who rely on VPNs for safety such as journalists or whistleblowers who are common targets of surveillance or spyware.
我们已经看到了此技术的一个缓解措施,并确定了基于 Linux 的操作系统上存在的修复程序。但是,该缓解措施提供了一个侧信道,可用于有针对性的拒绝服务审查,以及通过流量分析对流量目的地进行去匿名化处理。在世界上的一些地方,仅侧信道就可能导致那些依赖VPN安全的人入狱或死亡,例如记者或举报人,他们是监视或间谍软件的常见目标。
It is not feasible to fix the issue by simply removing support for the DHCP feature because this could break Internet connectivity in some legitimate cases. The strongest recommendation we have is for VPN providers to implement network namespaces on operating systems that support them, similar to the method described in WireGuard’s documentation. Network namespaces are a Linux feature that can segment interfaces and routing tables away from the local network’s control, and other operating system maintainers should consider whether namespaces are feasible to implement.
通过简单地删除对 DHCP 功能的支持来解决这个问题是不可行的,因为在某些合法情况下,这可能会中断 Internet 连接。我们最强烈的建议是 VPN 提供商在支持它们的操作系统上实现网络命名空间,类似于 WireGuard 文档中描述的方法。网络命名空间是 Linux 的一项功能,可以将接口和路由表分段为远离本地网络的控制,其他操作系统维护人员应考虑命名空间是否可行。
To help make this work accessible to as many people as possible, we are structuring this blog post to walk through the fundamentals of networking, VPN technology, and DHCP to fully explain the decloaking behavior. Advanced readers are welcome to jump straight to the proof-of-concept section.
为了帮助尽可能多的人访问这项工作,我们正在构建这篇博文,以介绍网络、VPN 技术和 DHCP 的基础知识,以充分解释去伪装行为。欢迎高级读者直接跳转到概念验证部分。
* UPDATE: The purpose of this research was to test this technique against modern VPN providers to determine their vulnerability and to notify the wider public of this issue. This is why we agreed with CISA to file a CVE when we disclosed to them and why we decided to name the vulnerability.
*更新:本研究的目的是针对现代VPN提供商测试此技术,以确定其漏洞并通知更广泛的公众此问题。这就是为什么我们同意 CISA 在向他们披露时提交 CVE,以及我们决定命名该漏洞的原因。
After publication, we have received details about prior research into combining routing table behavior with option 121. These researchers showed that at least some people were aware of DHCP option 121’s effect on VPNs going back to at least 2015. Despite this, the research did not lead to wide deployment of mitigations nor the general public awareness of the decloaking behavior.
发布后,我们收到了有关将路由表行为与选项 121 相结合的先前研究的详细信息。这些研究人员表明,至少有一些人意识到DHCP选项121对VPN的影响至少可以追溯到2015年。尽管如此,该研究并未导致缓解措施的广泛部署,也没有引起公众对隐身行为的普遍认识。
That said, we are grateful for the input of past researchers who explored the problem space. We will continue to credit our fellow security researchers who explored these issues.
也就是说,我们感谢过去探索问题空间的研究人员的投入。我们将继续感谢探索这些问题的安全研究人员。
Prior works referencing DHCP 121 route injection or VPN decloaking:
引用 DHCP 121 路由注入或 VPN 去隐身的先前工作:
-
2015 – Hardening OpenVPN for Def Con
2015 – 强化 OpenVPN for Def Con -
2016 – Samy Kamkar’s
2016 – 萨米·卡姆卡尔 -
2017 – Jomo’s Mastodon
2017 – 乔莫的乳齿象 -
2023 – Lowend talk thread
2023 – 低端谈话线程
Decloaking Primer: Low-level Networking
Decloaking Primer:低级网络
What is a network? 什么是网络?
A computer network is a group of computer devices that are connected to each other and can send and receive data to and from one another.
计算机网络是一组相互连接的计算机设备,可以相互发送和接收数据。
A basic example of this is to connect two laptops with an Ethernet cable to network them together. However, there’s more than meets the eye when it comes to low-level networking that’s hidden from the average user. The laptops are using a system of rules to talk to each other, which we call protocols. Each protocol has its own purpose and operates at what we call a layer.
一个基本的例子是用以太网电缆连接两台笔记本电脑,将它们联网在一起。然而,当涉及到对普通用户隐藏的低级网络时,还有更多的东西。笔记本电脑使用规则系统相互通信,我们称之为协议。每个协议都有自己的目的,并在我们所说的层上运行。
These layers are intended to solve different types of problems and are built such that they do not need to know what’s happening at a higher or lower layer. This is called encapsulation. For example, a user can trust that the layers lower than their browser (HTTP) are determining how to send electricity over a cable (Coax), knows who to talk to (Ethernet, IP), and ensure correct data delivery to the recipient server (TCP). This is like how someone writing a letter needs only to think about what they want to write or what the other person wrote. They do not need to care about how it got there.
这些层旨在解决不同类型的问题,并且构建时它们不需要知道更高或更低的层发生了什么。这称为封装。例如,用户可以相信低于其浏览器 (HTTP) 的层正在确定如何通过电缆 (Coax) 发送电力,知道与谁通信(以太网、IP),并确保将数据正确传送到接收服务器 (TCP)。这就像写信的人只需要考虑他们想写什么或另一个人写了什么。他们不需要关心它是如何到达那里的。
When we’re referring to layers in this blogpost, we are talking about the practical TCP/IP model, which is implemented on almost every device and network. We also decided to use the 5-layer variant of the model because it doesn’t combine the lower layers together; this is why there might be a discrepancy when viewing other TCP/IP model diagrams. When we’re referring to data that’s been packaged by all these layers, we generally refer to it as a packet.
当我们在这篇博文中提到层时,我们谈论的是实用的 TCP/IP 模型,该模型几乎在每个设备和网络上都实现了。我们还决定使用该模型的 5 层变体,因为它没有将下层组合在一起;这就是为什么在查看其他 TCP/IP 模型关系图时可能会存在差异的原因。当我们提到由所有这些层打包的数据时,我们通常将其称为数据包。
| Layer | Brief Description 快速描述 | Analogy | Protocols |
|---|---|---|---|
| Application Layer 应用层 | Determines the actual data that should be sent to a recipient. 确定应发送给收件人的实际数据。 |
Words on a page of a letter in the mail. 邮件中信件页面上的单词。 |
HTTP, DNS, HTTPS, DHCP HTTP、DNS、HTTPS、DHCP |
| Transport Layer 传输层 | Establishes end-to-end communication between a process on a host and a process on a recipient. 在主机上的进程和收件人的进程之间建立端到端通信。 |
A letter delivered to a specific apartment number. 寄往特定公寓号码的信件。 |
TCP, UDP TCP、UDP |
| Network Layer 网络层 | Sends traffic from a source system to a destination system across the internet. 通过 Internet 将流量从源系统发送到目标系统。 |
Delivering a letter to a single building in a city. 将一封信送到城市中的一栋建筑。 |
IP, ARP IP、ARP |
| Data Link Layer 数据链路层 | Controls traffic between systems on the same local network. 控制同一本地网络上系统之间的流量。 |
A post office truck taking mail from place to place or city to city. 邮局卡车将邮件从一个地方运送到另一个地方或从一个城市到另一个城市。 |
Ethernet |
| Physical | Determines how to encode data over a “physical medium” such as copper wire or radio waves (Wi-Fi). 确定如何通过“物理介质”(如铜线或无线电波 (Wi-Fi))对数据进行编码。 |
Physically writing the letter and placing it in an envelope. 亲自写信并将其放入信封中。 |
Fiber optic, Coax, Satellite, Microwave 光纤、同轴电缆、卫星、微波 |
What is a network interface?
什么是网络接口?
The most basic example of a network interface is a physical device such as a wireless or network card attached to a computer’s motherboard. These devices allow the computer to transmit bits of data over a physical medium (e.g., a copper wire, fiber optic cable, or radio frequency). They are a fundamental part of networking as they are what allows computers to talk to each other over a distance.
网络接口的最基本示例是物理设备,例如连接到计算机主板的无线或网卡。这些设备允许计算机通过物理介质(例如,铜线、光纤电缆或射频)传输数据位。它们是网络的基本组成部分,因为它们允许计算机远距离相互通信。
There are two types of network interfaces:
有两种类型的网络接口:
-
Physical Network Interfaces
物理网络接口 -
Virtual Network Interfaces
虚拟网络接口
Importantly, both types of interfaces are designed for encapsulation so they can be interacted with by higher layers in the same way.
重要的是,这两种类型的接口都是为封装而设计的,因此它们可以以相同的方式与更高层进行交互。
This is where Virtual Network Interfaces, a critical component of VPN clients and server, come in. Instead of using physical hardware, Virtual Network Interfaces create a file descriptor that can be read from or written to via software applications. Because file descriptors exist only in the memory of a host, Virtual Network Interfaces are especially useful for virtualized environments where traffic might never need to be transmitted over a physical medium.
这就是虚拟网络接口(VPN 客户端和服务器的关键组件)的用武之地。虚拟网络接口不使用物理硬件,而是创建一个文件描述符,可以通过软件应用程序读取或写入该描述符。由于文件描述符仅存在于主机的内存中,因此虚拟网络接口对于可能永远不需要通过物理介质传输流量的虚拟化环境特别有用。
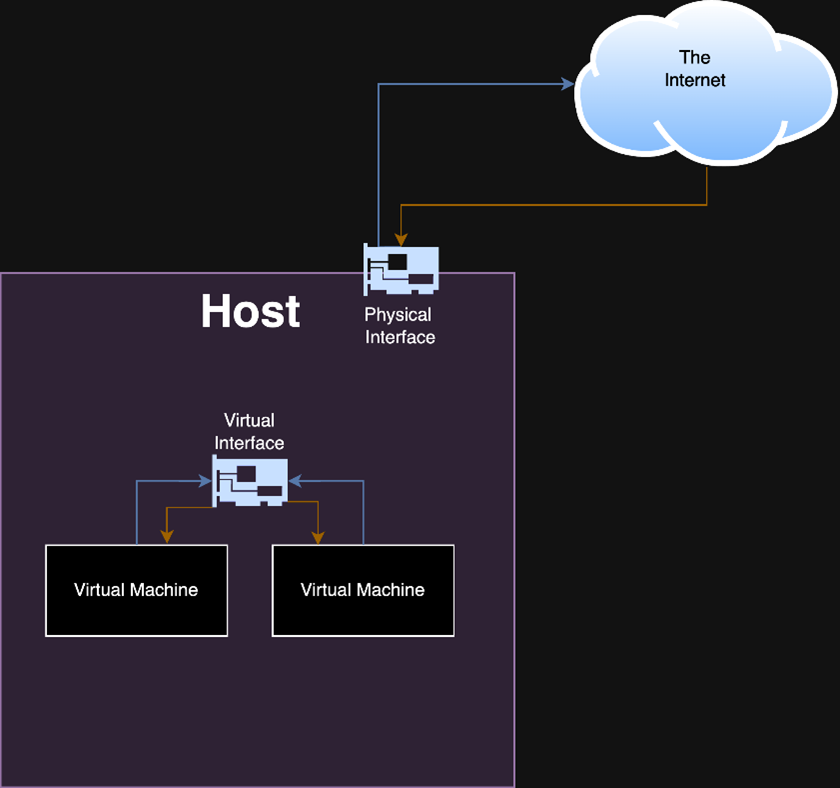
Figure 1: A simplified example of a virtual interface that is not backed by a physical interface. Traffic between virtual machines never leaves the host.
图 1:不受物理接口支持的虚拟接口的简化示例。虚拟机之间的流量永远不会离开主机。
However, there are use cases in which a user might want a virtual interface to be able to send traffic over a physical medium. For those cases, the virtual interface can also be backed by a physical network interface. Behind the scenes, the virtual interface forwards outbound traffic to a physical network interface.
但是,在某些情况下,用户可能希望虚拟接口能够通过物理介质发送流量。对于这些情况,虚拟接口也可以由物理网络接口提供支持。在后台,虚拟接口将出站流量转发到物理网络接口。
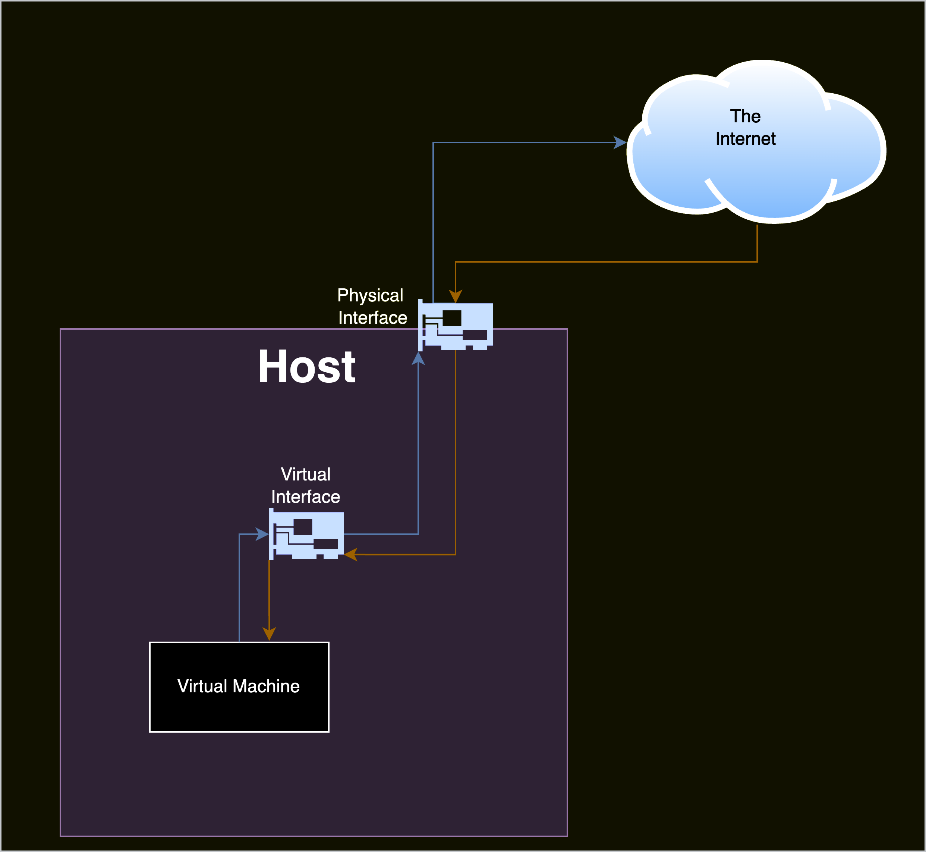
Figure 2: An example of a virtual interface that is backed by a physical interface.
图 2:由物理接口支持的虚拟接口示例。
What is a VPN? 什么是VPN?
A Virtual Private Network (VPN) allows users to create a tunnel for network traffic between their host device and a server on a different network. The resulting virtual network is not confined by geographic location while behaving identically to a physical network.
虚拟专用网络 (VPN) 允许用户为其主机设备与不同网络上的服务器之间的网络流量创建隧道。生成的虚拟网络不受地理位置的限制,同时与物理网络的行为相同。
To achieve this, VPN clients create a virtual network interface and use the underlying file descriptor to encrypt/decrypt traffic at a higher layer before sending it to a physical network interface.
为此,VPN 客户端会创建一个虚拟网络接口,并使用基础文件描述符在将流量发送到物理网络接口之前对更高层的流量进行加密/解密。
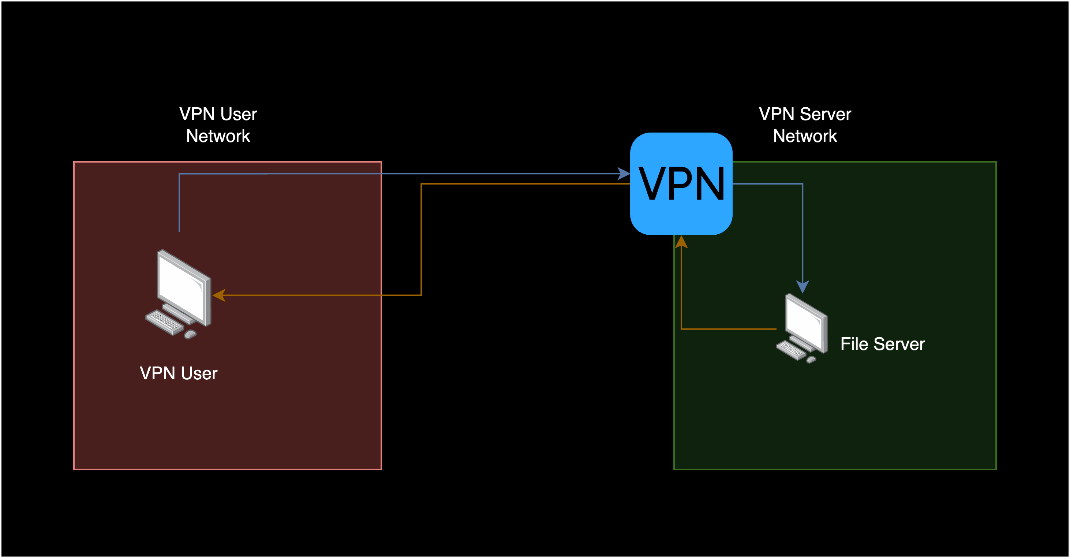
Figure 3: A simplified VPN setup where the VPN user is accessing a resource on a different network.
图 3:简化的 VPN 设置,其中 VPN 用户正在访问不同网络上的资源。
VPN use is designed to be as simple as possible for a user. Often, they do not need to do much besides log in and click a button to connect to their server.
VPN的使用旨在使用户尽可能简单。通常,除了登录并单击按钮连接到服务器之外,他们不需要做太多事情。
What a user does: 用户执行的操作:
-
Select the settings they want on the VPN Client
在 VPN 客户端上选择他们想要的设置 -
Click a button to connect
单击按钮进行连接 -
Log in (optional in some cases, depending on the client)
登录(在某些情况下是可选的,具体取决于客户端) -
Read the confirmation from the VPN they are connected
从他们连接的 VPN 中读取确认 -
Use remote resources from the VPN
使用来自 VPN 的远程资源
Importantly, VPNs actually increase the host’s attack surface because traffic from lower networking layers is send over the Internet. VPNs work by encapsulating lower layers inside of higher layers to create local area networks (LAN) over the Internet. LAN traffic is considered to be more privileged than traffic that is intended to be sent over the Internet. Attackers with LAN access have many more passive and active attack options than an attacker outside of the LAN. By creating a LAN over the Internet, VPNs extend the LAN attack surface to external attackers. Commonly, VPNs mitigate this attack surface by using compensating controls such as packet encryption.
重要的是,VPN实际上增加了主机的攻击面,因为来自较低网络层的流量是通过Internet发送的。VPN 的工作原理是将较低层封装在较高层中,以通过 Internet 创建局域网 (LAN)。LAN 流量被认为比打算通过 Internet 发送的流量更具特权。与局域网外的攻击者相比,具有LAN访问权限的攻击者具有更多的被动和主动攻击选项。通过通过 Internet 创建 LAN,VPN 将 LAN 攻击面扩展到外部攻击者。通常,VPN 通过使用补偿控制(如数据包加密)来缓解此攻击面。
This is an often-misunderstood fact about VPNs. The reason for encryption is not to increase the security of using the physical LAN, but rather to mitigate the added risk that VPNs introduce when they create a virtualized LAN over the Internet. VPNs do not secure you from local network attacks on the physical LAN despite common VPN marketing material and widely given advice.
这是关于VPN的一个经常被误解的事实。加密的原因不是为了提高使用物理LAN的安全性,而是为了减轻VPN在通过Internet创建虚拟化LAN时引入的额外风险。VPN并不能保护你免受物理LAN的本地网络攻击,尽管有常见的VPN营销材料和广泛的建议。
How do VPNs use virtual network interfaces?
VPN 如何使用虚拟网络接口?
The VPN client process creates an encrypted version of the packet it originally received from the file descriptor associated with its virtual network interface. It places this encrypted payload in the layer for its underlying VPN protocol, then uses that protocol to talk to the VPN server.
VPN 客户端进程创建最初从与其虚拟网络接口关联的文件描述符接收的数据包的加密版本。它将此加密有效负载放置在其底层 VPN 协议的层中,然后使用该协议与 VPN 服务器通信。
| Layer in TCP/IP TCP/IP 中的层 | Packet 1 (Before encrypted by VPN) 数据包 1(在 VPN 加密之前) |
Packet 2 (Encrypted by VPN) 数据包 2(由 VPN 加密) |
|---|---|---|
| Data Link Layer 数据链路层 | Ethernet: 以太网: Sender network card: [Physical interface MAC] 发送方网卡:[物理接口MAC] Dest. network card: [Router interface MAC] 网卡:[路由器接口MAC] |
Ethernet: 以太网: Source network card: [physical interface MAC] 源网卡:[物理接口MAC] Destination network card: [Router interface MAC] 目标网卡:[路由器接口MAC] |
| Network Layer 网络层 | IP: Source IP: 1.234.56.56.78 源IP: 1.234.56.56.78 Destination IP: 2.34.56.78 目标 IP:2.34.56.78 |
IP: Source IP: 1.234.56.78 源IP: 1.234.56.78 Destination IP: 99.87.65.43 目标 IP:99.87.65.43 |
| Transport Layer 传输层 | TCP: TCP: Sender port: 43555 发送端口:43555 Destination port: 80 目的端口:80 |
UDP: UDP: Sender port: 54232 发送端口:54232 Destination port: 1194 目的端口:1194 |
| Application Layer 应用层 | HTTP: 网址: GET google.com 获取 google.com |
OpenVPN Protocol: OpenVPN协议: Encrypted payload: 加密有效负载: Ethernet: 以太网: Sender network card: [virtual interface] 发送方网卡:[虚拟接口] Dest. network card: [server’s interface] 网卡:[服务器接口] IP (packet 1) IP(数据包 1) TCP (packet 1) TCP(数据包 1) HTTP (packet 1) HTTP(数据包 1) |
There’s quite a long process for how a VPN sends that packet to the VPN Server. We are including a more exhaustive list of steps in the Appendix for security researchers or developers who might need even more granular details.
VPN 如何将该数据包发送到 VPN 服务器有一个相当长的过程。我们在附录中为可能需要更详细细节的安全研究人员或开发人员提供了更详尽的步骤列表。
A simplified version of that process:
该过程的简化版本:
-
A VPN client establishes a “control channel” connection to a VPN server. If the VPN features a kill switch, then losing connection to this channel will result in a lockdown
VPN 客户端与 VPN 服务器建立“控制通道”连接。如果 VPN 具有终止开关,则失去与此频道的连接将导致锁定 -
The VPN client creates a virtual network interface
VPN 客户端创建虚拟网络接口 -
The VPN client optionally runs a startup script to configure the host. It may configure routing rules, the DNS server to use, host-based firewall rules, or other settings
VPN 客户端可以选择运行启动脚本来配置主机。它可以配置路由规则、要使用的 DNS 服务器、基于主机的防火墙规则或其他设置 -
A process on the host attempts to send network traffic to a destination (i.e., Internet browsing)
主机上的进程尝试将网络流量发送到目标(即 Internet 浏览) -
Routing rules select the VPN’s interface to send the traffic through
路由规则选择要发送流量的 VPN 接口 -
The VPN client receives and encrypts that traffic
VPN 客户端接收并加密该流量 -
The VPN client sends the encrypted traffic over a physically backed network interface to the VPN server
VPN 客户端通过物理支持的网络接口将加密流量发送到 VPN 服务器 -
The VPN server receives and decrypts that traffic from the VPN client
VPN 服务器接收和解密来自 VPN 客户端的流量 -
The VPN server forwards that traffic to the destination. If the destination is outbound, the VPN will send your traffic as though it is its own. This behavior is what VPN providers describe as “IP cloaking” or “IP hiding”
VPN 服务器将该流量转发到目标。如果目的地是出站,VPN 会像发送自己的流量一样发送您的流量。这种行为被VPN提供商描述为“IP隐藏”或“IP隐藏” -
The VPN server receives a reply from the destination, encrypts the response, and sends it to the VPN client
VPN 服务器接收来自目标的回复,对响应进行加密,并将其发送到 VPN 客户端 -
The VPN client decrypts the response, and the originating process finally receives the traffic
VPN 客户端解密响应,原始进程最终接收流量
It can be quite hard to understand fully since there are many steps involved. For that reason, we’ve made our own detailed diagram of a mental model we use for how a VPN client sends and receives information (Figure 4).
由于涉及许多步骤,因此很难完全理解。出于这个原因,我们制作了自己的心智模型的详细图表,用于 VPN 客户端如何发送和接收信息(图 4)。
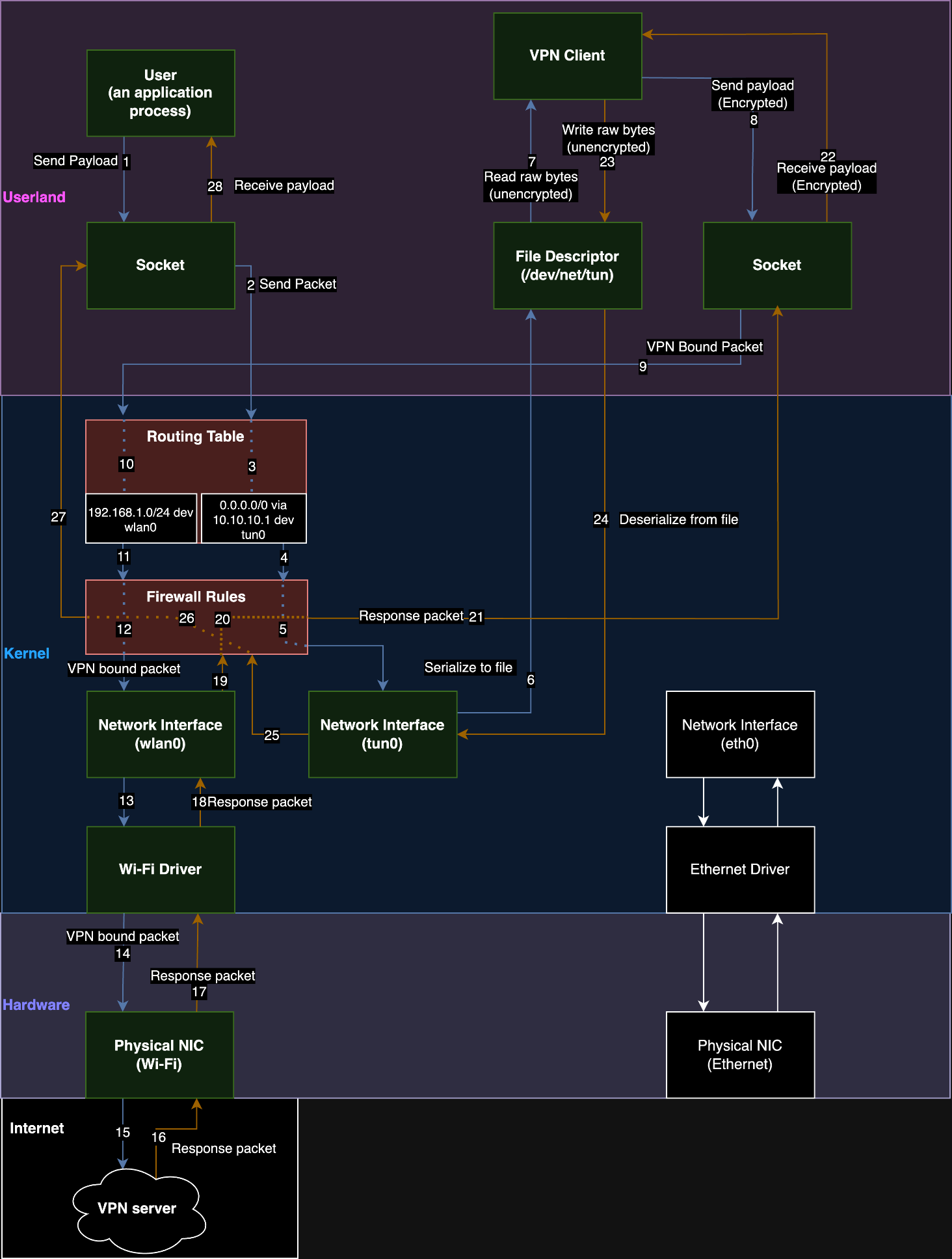
Figure 4: A dataflow diagram of a VPN on a Linux host.
图 4:Linux 主机上 VPN 的数据流图。
How do routing based VPNs configure a host?
基于路由的 VPN 如何配置主机?
Once a user connects to a VPN server, their VPN client process will configure the host’s settings to route traffic through the tunnel that it established. If all traffic* is routed through the VPN, we refer to it as a “full-tunnel VPN”. If there are user-defined exceptions for traffic, such as local network traffic, we refer to it as a “split-tunnel VPN”. The VPN client can also configure other settings on the host, such as the host’s firewall. Later, we’ll discuss a mitigation we observed using the host-based firewall.
用户连接到 VPN 服务器后,其 VPN 客户端进程将配置主机的设置,以通过其建立的隧道路由流量。如果所有流量*都通过 VPN 路由,我们将其称为“全隧道 VPN”。 如果存在用户定义的流量异常,例如本地网络流量,我们将其称为“拆分隧道 VPN”。VPN 客户端还可以在主机上配置其他设置,例如主机的防火墙。稍后,我们将讨论使用基于主机的防火墙观察到的缓解措施。
Commonly, these configuration changes are made by “up scripts” and “down scripts” when a connection is established or disconnected. The runtime process for a VPN client may also perform configuration changes, but this varies from vendor to vendor.
通常,这些配置更改是在建立或断开连接时由“向上脚本”和“向下脚本”进行的。VPN 客户端的运行时过程也可能执行配置更改,但这因供应商而异。
*Note: When we say, “all traffic”, we really mean “all traffic except the traffic necessary to keep the VPN in a working state.” For example, VPNs create an exception to their own previously configured routing rules. All traffic sent to the VPN servers IP address must be sent over a hardware backed interface instead of its own tunnel. Otherwise, it would break the hosts connection to the VPN server and the VPN client would be unable to send encrypted packets. In addition, there are other configuration exceptions made for DHCP traffic since the VPN must maintain its hosts IP address lease.
*注意:当我们说“所有流量”时,我们实际上是指“除保持VPN处于工作状态所需的流量之外的所有流量”。例如,VPN 会为自己之前配置的路由规则创建例外。发送到 VPN 服务器 IP 地址的所有流量都必须通过硬件支持的接口发送,而不是通过其自己的隧道发送。否则,它将断开主机与 VPN 服务器的连接,并且 VPN 客户端将无法发送加密数据包。此外,DHCP 流量还有其他配置例外,因为 VPN 必须维护其主机 IP 地址租约。
What are routes and routing tables?
什么是路由和路由表?
Routes are how we describe where to send traffic based on the destination. Routing tables are a collection of routes that are used by the network stack. Consider a network stack to just be all the code on an operating system that deals with sending and receiving data from a network.
路由是我们根据目的地描述将流量发送到何处的方式。路由表是网络堆栈使用的路由的集合。将网络堆栈视为操作系统上处理从网络发送和接收数据的所有代码。
A common route is sending all traffic (0.0.0.0/0 in Classless Inter-Domain Routing [CIDR] notation) to your router (192.168.1.1) over the physical network interface (eth0).
一种常见的路由是通过物理网络接口 ( ) 将所有流量( 0.0.0.0/0 采用无类别域间路由 [CIDR] 表示法)发送到路由器 ( 192.168.1.1 eth0 )。
An example of that rule in the table would be:
表中该规则的一个示例是:
0.0.0.0/0 via 192.168.1.1 dev eth0Another behavior of routing tables is that by default (in most network stacks) the most specific prefix length for the CIDR range has the highest priority. The prefix length for the range 192.168.1.1/32 is 32 and the prefix length for the range 0.0.0.0/0 is 0. The highest numerical value of a prefix length will take priority for routing selection (unless configured otherwise).
路由表的另一种行为是,默认情况下(在大多数网络堆栈中),CIDR 范围的最具体前缀长度具有最高优先级。范围 192.168.1.1/32 的前缀长度为 32 ,范围 0.0.0.0/0 的前缀长度为 0 。前缀长度的最高数值将优先于路由选择(除非另有配置)。
For example: 例如:
0.0.0.0/0 via 192.168.1.1 dev eth0
10.10.10.1/24 via 192.168.1.1 dev wifi1
10.10.10.2/32 via 192.168.1.2 dev eth0In this situation, if we sent traffic to 10.10.10.2, the most specific rule is the /32 rule and it would therefore be the rule the network stack uses despite matching the other two rules above it.
在这种情况下,如果我们将 10.10.10.2 流量发送到 ,最具体的规则是 /32 规则,因此它将是网络堆栈使用的规则,尽管它与上面的其他两个规则匹配。
Most full-tunnel VPNs use the least specific rule possible to capture all traffic. Note that the following example includes an exception route for the hypothetical VPN server address (12.34.56.78) as well.
大多数全隧道 VPN 使用尽可能不具体的规则来捕获所有流量。请注意,以下示例还包括假设的 VPN 服务器地址 ( 12.34.56.78 ) 的例外路由。
0.0.0.0/0 via 10.13.37.1 dev tun0
12.34.56.78/32 via 192.168.1.1 dev eth0Alternatively, providers may use two /1 rules to gain priority over the default route. It’s common in even non-adversarial environments for DHCP to set a default route to the physical gateway.
或者,提供商可以使用两个 /1 规则来获得默认路由的优先级。即使在非对抗性环境中,DHCP 也经常设置到物理网关的默认路由。
0.0.0.0/0 via 192.168.1.1 dev eth0
0.0.0.0/1 via 10.13.37.1 dev tun0
128.0.0.0/1 via 10.13.37.1 dev tun0
12.34.56.78/32 via 192.168.1.1 dev eth0What is DHCP? 什么是 DHCP?
DHCP was originally developed as a robust way to dynamically issue IP addresses to devices on a local network as opposed to manually addressing each device. All modern operating systems have their own DHCP client that will automatically request an IP address.
DHCP 最初是作为一种强大的方式开发的,用于向本地网络上的设备动态发出 IP 地址,而不是手动寻址每个设备。所有现代操作系统都有自己的DHCP客户端,该客户端将自动请求IP地址。
The main concept to understand is that DHCP provides a time-based lease for IP addresses, and it contains many additional features called options that allow you to adjust the configuration of devices remotely and dynamically. Some notable options include setting the default gateway that acts as the primary route to the Internet or DNS (Domain Name System) servers, which resolve domain names like “google.com” to an IP address.
要了解的主要概念是,DHCP 为 IP 地址提供基于时间的租约,并且它包含许多称为选项的附加功能,允许您远程和动态地调整设备的配置。一些值得注意的选项包括设置默认网关,该网关充当 Internet 或 DNS(域名系统)服务器的主要路由,后者将“google.com”等域名解析为 IP 地址。
A client who wants an IP address uses a broadcast to send a DHCPDISCOVER packet to the entire local subnet. Other hosts will ignore this, except for the server who will respond with a DHCPOFFER unicasted directly to the client to offer it a time-bound lease.
需要 IP 地址的客户端使用广播将 DHCPDISCOVER 数据包发送到整个本地子网。其他主机将忽略这一点,但服务器除外,服务器将使用直接向客户端单播的 DHCPOFFER 进行响应,以为其提供有时限的租约。
Alternatively, if a client knows who the DHCP server is, it has the option to unicast the DHCPDISCOVER to a DHCP server instead of broadcasting. Usually, this is used for renewing its lease.
或者,如果客户端知道 DHCP 服务器是谁,则可以选择将 DHCPDISCOVER 单播到 DHCP 服务器,而不是广播。通常,这用于续租。
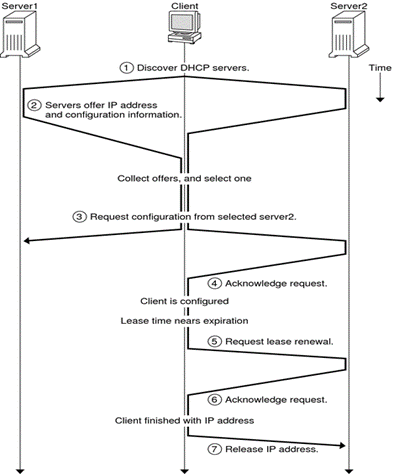
Figure 5: How a DHCP client obtains an IP address and then maintains its lease.
图 5:DHCP 客户端如何获取 IP 地址,然后维护其租约。
Source: https://docs.oracle.com/cd/E23824_01/html/821-1453/dhcp-overview-3.html
来源: https://docs.oracle.com/cd/E23824_01/html/821-1453/dhcp-overview-3.html
As seen in the above diagram, once a DHCP server makes an offer, the client can choose to accept or decline the offer. For example, if it receives multiple offers, it will choose the best one. The selection most often implemented by DHCP clients is “first come, first serve.” The servers that aren’t selected will be sent a DHCPDECLINE message from the client. Notably, the DHCPOFFER will include the options.
如上图所示,一旦DHCP服务器发出报价,客户端可以选择接受或拒绝报价。例如,如果它收到多个报价,它将选择最好的一个。DHCP 客户端最常实施的选择是“先到先得”。未选择的服务器将从客户端发送 DHCPDECLINE 消息。值得注意的是,DHCPOFFER 将包括这些选项。
What is DHCP option 121?
什么是 DHCP 选项 121?
In 1997, the DHCP RFC had option 33, which allowed network administrators to specify a static route to install into a client’s routing table. However, this used classful static routes, which fell out of favor over time as public IP space became limited. In 2002, RFC 3442 introduced option 121 classless static routes and obsoleted option 33 (which still should be supported, depending on who you ask). Option 121 also allows administrators to add static routes to a client’s routing table, but with classless ranges instead. There is no limit besides packet size to how many different routes can be installed at once.
1997 年,DHCP RFC 具有选项 33,它允许网络管理员指定要安装到客户端路由表中的静态路由。然而,这使用了经典的静态路由,随着时间的推移,随着公共 IP 空间的有限,这种路由不再受欢迎。2002 年,RFC 3442 引入了选项 121 无类别静态路由和过时的选项 33(仍然应该支持,具体取决于您询问的对象)。选项 121 还允许管理员将静态路由添加到客户端的路由表,但改为使用无类范围。除了数据包大小之外,一次可以安装多少个不同的路由没有限制。
An interesting quirk of DHCP option 121 is that the network interface device for the route it installs cannot be specified by the DHCP server. Below you can see a DHCPOFFER packet that was captured in Wireshark. It specifies the CIDR range and the router to use but has no interface device.
DHCP 选项 121 的一个有趣的怪癖是,DHCP 服务器无法指定其安装的路由的网络接口设备。您可以在下面看到在 Wireshark 中捕获的 DHCPOFFER 数据包。它指定 CIDR 范围和要使用的路由器,但没有接口设备。
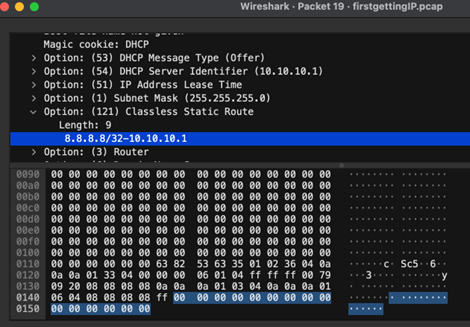
Figure 6: A DHCPOFFER packet that includes an option 121 route. The network interface is not specified by design.
图 6:包含选项 121 路由的 DHCPOFFER 数据包。网络接口不是由设计指定的。
Instead, the DHCP client will implicitly choose the network interface that the client is talking to the DHCP server on when installing its routing rules for this option.
相反,DHCP 客户端将在安装此选项的路由规则时隐式选择客户端与 DHCP 服务器通信的网络接口。
Decloaking Attacks 破坏攻击
Requirements for decloaking VPN traffic
取消隐藏 VPN 流量的要求
-
The targeted host must accept a DHCP lease from the attacker-controlled server
目标主机必须接受来自攻击者控制的服务器的 DHCP 租约 -
The targeted host’s DHCP client must implement DHCP option 121
目标主机的 DHCP 客户端必须实现 DHCP 选项 121
We want to stress that there are ways an attacker who is on the same network as a targeted user might be able to become their DHCP server:
我们想强调的是,与目标用户位于同一网络上的攻击者可以通过多种方式成为其 DHCP 服务器:
-
A rogue DHCP server using a DHCP starvation attack against the true DHCP, then responding to new clients. We have achieved this in lab environments and are working on a follow-up blog post.
一个流氓DHCP服务器,对真正的DHCP使用DHCP饥饿攻击,然后响应新客户端。我们已经在实验室环境中实现了这一点,并正在撰写后续博客文章。 -
A rogue DHCP server racing to respond to DHCPDISCOVER broadcasts to abuse DHCP clients’ common behavior where they implement first-offer lease selection.
一个流氓 DHCP 服务器竞相响应 DHCPDISCOVER 广播,以滥用 DHCP 客户端在实施首次报价租约选择时的常见行为。 -
ARP spoofing to intercept traffic between the true DHCP server and client, then waiting for a client to renew their lease.
ARP 欺骗以拦截真正的 DHCP 服务器和客户端之间的流量,然后等待客户端续订其租约。
Performing the attack 执行攻击
Our technique is to run a DHCP server on the same network as a targeted VPN user and to also set our DHCP configuration to use itself as a gateway. When the traffic hits our gateway, we use traffic forwarding rules on the DHCP server to pass traffic through to a legitimate gateway while we snoop on it.
我们的技术是与目标VPN用户在同一网络上运行DHCP服务器,并将DHCP配置设置为将自身用作网关。当流量到达我们的网关时,我们使用 DHCP 服务器上的流量转发规则将流量传递到合法网关,同时我们窥探它。
We use DHCP option 121 to set a route on the VPN user’s routing table. The route we set is arbitrary and we can also set multiple routes if needed. By pushing routes that are more specific than a /0 CIDR range that most VPNs use, we can make routing rules that have a higher priority than the routes for the virtual interface the VPN creates. We can set multiple /1 routes to recreate the 0.0.0.0/0 all traffic rule set by most VPNs.
我们使用 DHCP 选项 121 在 VPN 用户的路由表上设置路由。我们设置的路线是任意的,如果需要,我们也可以设置多条路线。通过推送比大多数 VPN 使用的 /0 CIDR 范围更具体的路由,我们可以使路由规则的优先级高于 VPN 创建的虚拟接口的路由。我们可以设置多个 /1 路由来重新创建大多数 VPN 设置 0.0.0.0/0 的所有流量规则。
Pushing a route also means that the network traffic will be sent over the same interface as the DHCP server instead of the virtual network interface. This is intended functionality that isn’t clearly stated in the RFC. Therefore, for the routes we push, it is never encrypted by the VPN’s virtual interface but instead transmitted by the network interface that is talking to the DHCP server. As an attacker, we can select which IP addresses go over the tunnel and which addresses go over the network interface talking to our DHCP server.
推送路由还意味着网络流量将通过与 DHCP 服务器相同的接口而不是虚拟网络接口发送。这是 RFC 中未明确说明的预期功能。因此,对于我们推送的路由,它永远不会由VPN的虚拟接口加密,而是由与DHCP服务器通信的网络接口传输。作为攻击者,我们可以选择哪些 IP 地址通过隧道,哪些地址通过网络接口与我们的 DHCP 服务器通信。

Figure 7: A malicious DHCP option 121 route that causes traffic to never be encrypted by the VPN process.
图 7:导致 VPN 进程永远不会加密流量的恶意 DHCP 选项 121 路由。
We now have traffic being transmitted outside the VPN’s encrypted tunnel. This technique can also be used against an already established VPN connection once the VPN user’s host needs to renew a lease from our DHCP server. We can artificially create that scenario by setting a short lease time in the DHCP lease, so the user updates their routing table more frequently. In addition, the VPN control channel is still intact because it already uses the physical interface for its communication. In our testing, the VPN always continued to report as connected, and the kill switch was never engaged to drop our VPN connection.
我们现在有流量在VPN的加密隧道之外传输。一旦VPN用户的主机需要从我们的DHCP服务器续订租约,这种技术也可以用于已经建立的VPN连接。我们可以通过在 DHCP 租约中设置较短的租约时间来人为地创建该方案,以便用户更频繁地更新其路由表。此外,VPN控制通道仍然完好无损,因为它已经使用物理接口进行通信。在我们的测试中,VPN 始终继续报告为已连接,并且从未使用终止开关来断开我们的 VPN 连接。
Proof of Concept 概念验证
-
Video proof of concept: 视频概念验证:
-
Lab Setup Code: 实验室设置代码:
-
DHCP Server image: DHCP 服务器映像:
The lab scenarios are built to represent:
实验室方案旨在表示:
-
An attacker compromises a DHCP server/access point
攻击者入侵 DHCP 服务器/接入点 -
A rogue administrator owns the infrastructure themselves and maliciously configures it
流氓管理员自己拥有基础架构并恶意配置它 -
An attacker sets up an evil twin wireless AP in a physical location such as a coffee shop or corporate office
攻击者在咖啡店或公司办公室等物理位置设置邪恶的孪生无线 AP -
One we release our tool, ArcaneTrickster, the lab can also be used to mimic an attacker who has an adjacent host on the network na dis otherwise not in a privileged network position
我们发布了我们的工具ArcaneTrickster,该实验室还可用于模拟在网络上拥有相邻主机的攻击者,否则不处于特权网络位置
Fixes 修复
Network Namespaces 网络命名空间
Using network namespaces on Linux can completely fix this behavior. However, in our experience, it is less commonly implemented.
在 Linux 上使用网络命名空间可以完全修复此行为。但是,根据我们的经验,它不太常被实施。
WireGuard’s documentation shows how it’s possible to use a namespace for all applications with traffic that should be using a VPN before sending it to another namespace that contains a physical interface. However, this appears to be Linux-specific functionality and it’s not clear if there is a solution for Windows, MacOS, or other operating systems with the same amount of robustness.
WireGuard 的文档展示了如何对所有应用程序使用命名空间,这些应用程序的流量应该使用 VPN,然后再将其发送到另一个包含物理接口的命名空间。但是,这似乎是特定于 Linux 的功能,目前尚不清楚是否有适用于 Windows、MacOS 或其他操作系统的解决方案具有相同的鲁棒性。
Mitigations 缓解措施
Firewall Rules 防火墙规则
We’ve observed VPN providers denying all inbound and outbound traffic to and from the physical interface via firewall rules. An exception was necessary for the DHCP and VPN server IPs because they are necessary to remain connected to the LAN and VPN server. Deep packet inspection could also allow only the DHCP and VPN protocols instead but would likely incur a performance penalty.
我们观察到 VPN 提供商通过防火墙规则拒绝进出物理接口的所有入站和出站流量。DHCP 和 VPN 服务器 IP 需要例外,因为它们必须保持与 LAN 和 VPN 服务器的连接。深度数据包检测也可能只允许 DHCP 和 VPN 协议,但可能会造成性能损失。
Problems with Firewall Rule Mitigations
防火墙规则缓解问题
Firewall mitigations create a selective denial of service for traffic using the DHCP route and introduce a side-channel. An attacker can use this side-channel to determine the destination of traffic. To determine the traffic’s destination, an attacker could perform traffic analysis on the volume of VPN encrypted traffic a user sends. The attacker would need a baseline volume of traffic where no malicious are installed. Then the attacker would need to modify the lease configuration to install routes that deny traffic and observe the difference in volume.
防火墙缓解措施会为使用 DHCP 路由的流量创建选择性拒绝服务,并引入侧信道。攻击者可以使用此侧信道来确定流量的目标。为了确定流量的目的地,攻击者可以对用户发送的 VPN 加密流量执行流量分析。攻击者需要未安装恶意流量的基线流量。然后,攻击者需要修改租约配置,以安装拒绝流量的路由并观察流量差异。
With enough samples, it would be possible to statistically prove whether the targeted user is sending traffic to a specific destination. For the average internet user, most internet traffic is already secured by TLS. Therefore, traffic intercepted by TunnelVision will mostly be unreadable except for the destination and protocols. This means that this side-channel has nearly the same impact and should be considered insufficient.
有了足够的样本,就可以从统计学上证明目标用户是否正在向特定目的地发送流量。对于普通互联网用户来说,大多数互联网流量已经受到TLS的保护。因此,除了目的地和协议之外,TunnelVision 截获的流量大多是不可读的。这意味着这个侧信道具有几乎相同的影响,应该被认为是不够的。
The side-channel is flexible in use:
侧通道使用灵活:
-
The traffic can be checked against a predefined list.
可以根据预定义的列表检查流量。 -
The traffic can be selectively denied as a censorship mechanism.
作为一种审查机制,可以有选择地拒绝流量。 -
The attacker can use IP space denial with binary search to determine all current connections in logarithmic time.
攻击者可以使用具有二进制搜索的 IP 空间拒绝来确定对数时间内的所有当前连接。
Ignore Option 121 忽略选项 121
Another possible mitigation is ignoring option 121 while the VPN is on. We noted that because Android does not implement support for DHCP option 121, it was uniquely unaffected. The downside is that option 121 exists for a reason, and ignoring these routes can break network connectivity (something that is frequently brought up as a reason to implement it on Android). If this mitigation is implemented, it must be mandatory because attackers could simply deny network access until the VPN or user re-enables option 121.
另一种可能的缓解措施是在 VPN 打开时忽略选项 121。我们注意到,由于 Android 未实现对 DHCP 选项 121 的支持,因此它唯一不受影响。缺点是选项 121 的存在是有原因的,忽略这些路由可能会破坏网络连接(这经常被提出作为在 Android 上实现它的原因)。如果实施了此缓解措施,则它必须是强制性的,因为攻击者可以简单地拒绝网络访问,直到 VPN 或用户重新启用选项 121。
Use a Hot Spot or VM
使用热点或 VM
Hot spots are temporary Wi-Fi networks controlled by a cellular device. They create a password-locked LAN with automatic network address translation. Because this network is completely controlled by the cellular device and requires a password, an attacker should not have local network access. A virtual machine would also work similarly as long as the VM’s network adapter is not in bridged mode.
热点是由蜂窝设备控制的临时 Wi-Fi 网络。他们创建一个具有自动网络地址转换功能的密码锁定局域网。由于此网络完全由手机网络设备控制,并且需要密码,因此攻击者不应具有本地网络访问权限。只要 VM 的网络适配器未处于桥接模式,虚拟机的工作方式也类似。
Do not use untrusted networks if you need absolute confidentiality of your traffic
如果您需要对流量进行绝对保密,请不要使用不受信任的网络
Industry Impact 行业影响
Is TunnelVision a vulnerability?
TunnelVision 是一个漏洞吗?
This is debatable. We’re calling it a technique because TunnelVision doesn’t rely on violating any security properties of the underlying technologies. From our perspective, TunnelVision is how DHCP, routing tables, and VPNs are intended to work.
这是值得商榷的。我们之所以称其为一种技术,是因为 TunnelVision 不依赖于违反底层技术的任何安全属性。从我们的角度来看,TunnelVision 是 DHCP、路由表和 VPN 的工作方式。
However, it contradicts VPN providers’ assurances that are commonly referenced in marketing materials; in our opinion, TunnelVision becomes a vulnerability when a VPN provider makes assurances that their product secures a customer from an attacker on an untrusted network. There’s a big difference between protecting your data in transit and protecting against all LAN attacks. VPNs were not designed to mitigate LAN attacks on the physical network and to promise otherwise is dangerous.
但是,它与营销材料中通常引用的VPN提供商的保证相矛盾;在我们看来,当VPN提供商保证其产品可以保护客户免受不受信任网络上的攻击者的攻击时,TunnelVision就会成为一个漏洞。保护传输中的数据和防止所有 LAN 攻击之间存在很大差异。VPN并非旨在减轻对物理网络的LAN攻击,并且承诺否则是危险的。
In our technique, we have not broken the VPN’s cryptographically secured protocol, and the VPN is still fully functional. An attacker is instead forcing a target user to not use their VPN tunnel. Regardless of whether we classify this as a technique, VPN users are affected when they rely on assurances that a VPN can secure them from attackers on their local network.
在我们的技术中,我们没有破坏VPN的加密安全协议,并且VPN仍然功能齐全。相反,攻击者会强制目标用户不使用其 VPN 隧道。无论我们是否将其归类为一种技术,当VPN用户依赖VPN可以保护他们免受本地网络攻击者的保证时,他们都会受到影响。
Affected Operating Systems
受影响的操作系统
In our testing, we observed that any operating system that implements a DHCP client according to its RFC specification and has support for DHCP option 121 routes is affected. This includes Windows, Linux, iOS, and MacOS. Notably, it does not affect Android as they do not have support for DHCP option 121.
在我们的测试中,我们观察到任何根据其 RFC 规范实现 DHCP 客户端并支持 DHCP 选项 121 路由的操作系统都会受到影响。这包括 Windows、Linux、iOS 和 MacOS。值得注意的是,它不会影响 Android,因为它们不支持 DHCP 选项 121。
Affected VPN Providers and VPN Protocols
受影响的 VPN 提供商和 VPN 协议
We found that VPNs that solely rely on routing rules to secure the host’s traffic are vulnerable. Those who are hosting their own VPN servers (e.g., system administrators) and are not hardening their VPN client configurations will likely be vulnerable as well. We have observed a mitigation from some VPN providers that drops traffic to non-VPN interfaces via firewall rules. It’s possible there are other methods that we did not encounter during testing to mitigate or fix this.
我们发现,仅依靠路由规则来保护主机流量的 VPN 容易受到攻击。那些托管自己的VPN服务器(例如,系统管理员)并且没有强化其VPN客户端配置的人也可能容易受到攻击。我们观察到一些 VPN 提供商通过防火墙规则将流量丢弃到非 VPN 接口的缓解措施。可能还有其他我们在测试过程中没有遇到过的方法来缓解或修复此问题。
As previously mentioned, we observed the same behavior on each operating system we tested, save one. Furthermore, the strength of the encryption algorithm a VPN uses makes no difference. TunnelVision’s effect is independent of the underlying VPN protocol (e.g., WireGuard, OpenVPN, or IPsec) because it reconfigures the operating system network stack the VPN relies on.
如前所述,我们在测试的每个操作系统上都观察到相同的行为,除了一个。此外,VPN使用的加密算法的强度没有区别。TunnelVision 的效果与底层 VPN 协议(例如 WireGuard、OpenVPN 或 IPsec)无关,因为它会重新配置 VPN 所依赖的操作系统网络堆栈。
Conclusion 结论
Call to Action 号召性用语
We have a limitation as a research team of two– there are simply too many VPNs on the market to test each one individually. The first approach we took was to notify companies via bug bounties or security disclosure email, but that quickly became unscalable. We’ve also engaged the EFF and CISA to help disclose as broadly as possible prior to publicly releasing this research. We thank them tremendously for their help. Our hope is that by publishing our work, we can reach more affected parties, especially because we believe the technique has been feasible since as early as 2002.
作为一个由两人组成的研究团队,我们有一个局限性——市场上的VPN太多了,无法单独测试每一个。我们采取的第一种方法是通过漏洞赏金或安全披露电子邮件通知公司,但这很快就变得无法扩展。我们还聘请了 EFF 和 CISA,在公开发布这项研究之前帮助尽可能广泛地披露。我们非常感谢他们的帮助。我们希望通过发表我们的工作,我们可以接触到更多受影响的各方,特别是因为我们相信该技术早在2002年就已经可行。
Although the public disclosure of this technique affects each party differently, ultimately there is a shared responsibility.
尽管这种技术的公开披露对各方的影响不同,但最终还是有共同的责任。
Users should be made aware of this technique and for sensitive traffic they should be warned against using untrusted networks. If they must use an untrusted network, they should use a VPN provider that has an effective mitigation against this technique. To determine if a provider has an effective mitigation or fix, our lab setup is available for testing and VPN providers themselves will be able to speak to the specifics of their existing mitigations in their documentation. If a VPN decloak does occur, most user data will not be visible to local network attackers assuming they are accessing websites with HTTPS, which has become increasingly common.
应让用户了解此技术,对于敏感流量,应警告他们不要使用不受信任的网络。如果他们必须使用不受信任的网络,他们应该使用能够有效缓解此技术的 VPN 提供商。为了确定提供商是否具有有效的缓解措施或修复措施,我们的实验室设置可用于测试,VPN 提供商本身将能够在其文档中讨论其现有缓解措施的细节。如果确实发生了 VPN 伪装,则假设本地网络攻击者使用 HTTPS 访问网站,大多数用户数据将不可见,这已经变得越来越普遍。
It is common for corporate VPNs to be used in areas such as coffee shops, hotels, or airports. Network administrators should inform employees that working from such places carries risks and should be avoided when possible. If such a policy is not practical, then administrators should advise using VPNs that enable the previously mentioned mitigations or fixes. Some alternatives would be to use a trusted hot spot and then connect to the VPN. Lastly, running the VPN inside of a VM that obtains a lease from a virtualized DHCP server would prevent the local networks DHCP server from installing routes altogether.
企业 VPN 通常用于咖啡店、酒店或机场等区域。网络管理员应告知员工,在这些地方工作存在风险,应尽可能避免。如果此类策略不切实际,则管理员应建议使用启用上述缓解措施或修复的 VPN。一些替代方法是使用受信任的热点,然后连接到 VPN。最后,在从虚拟化 DHCP 服务器获取租约的 VM 内运行 VPN 将阻止本地网络 DHCP 服务器完全安装路由。
Companies that control their own networks or have site-to-site VPNs should review the switches they use and enable features such as DHCP snooping and ARP protections. These layer 2 protections help prevent rogue DHCP servers but do not eliminate a rogue administrator scenario. In addition, implementing HTTPS or other protocols with encryption for internal resources will prevent data leakage from VPN users connecting from untrusted networks.
控制自己的网络或拥有站点到站点 VPN 的公司应检查他们使用的交换机,并启用 DHCP 监听和 ARP 保护等功能。 这些第 2 层保护有助于防止恶意 DHCP 服务器,但不能消除恶意管理员方案。此外,实施HTTPS或其他对内部资源进行加密的协议将防止从不受信任的网络连接的VPN用户的数据泄露。
VPN providers can add features to clients to configure firewall rules that drop outbound packets to network interfaces. However, such a setting will mean that a VPN user will be isolated from interacting with local network resources. If the VPN client is for Linux and is intended to be a full tunnel, using network namespaces for isolation. As such, VPN providers should publicly provide documentation about any mitigations or fixes they have for TunnelVision and warn their end users about TunnelVision’s existence. We also recommend reviewing their marketing material and cease marketing claims that VPNs protect customers on untrusted networks until it can be proven.
VPN 提供商可以向客户端添加功能,以配置将出站数据包丢弃到网络接口的防火墙规则。但是,这样的设置意味着 VPN 用户将与本地网络资源交互隔离。如果 VPN 客户端适用于 Linux 并且旨在成为完整隧道,请使用网络命名空间进行隔离。因此,VPN提供商应公开提供有关其针对TunnelVision的任何缓解措施或修复程序的文档,并警告其最终用户TunnelVision的存在。我们还建议您查看他们的营销材料,并停止营销声称 VPN 可以保护不受信任网络上的客户,直到可以证明这一点。
Operating system maintainers (outside of Linux) should determine whether adding or enhancing features related to network namespaces is feasible.
操作系统维护人员(Linux 之外)应确定添加或增强与网络命名空间相关的功能是否可行。
Upcoming Research 即将到来的研究
During the disclosure process, we encountered multiple cases in which the entities we disclosed to did not see this as a serious problem. They assumed that the prerequisite conditions included privileged positions or accounts, despite the only prerequisite being local network access. This assumption was partially fueled by our intentionally simplistic lab setup where we were the only DHCP server, and what we perceive as the entity’s lack of familiarity with low-level networking.
在披露过程中,我们遇到了多个案例,在这些案例中,我们披露的实体并不认为这是一个严重的问题。他们假设先决条件包括特权职位或帐户,尽管唯一的先决条件是本地网络访问。这一假设在一定程度上是由我们故意简化的实验室设置所推动的,我们是唯一的DHCP服务器,以及我们认为该实体对低级网络不熟悉的情况。
With this feedback, we decided to develop a robust adversarial infrastructure library to enable further LAN security research and demonstrate practical attacks. For example, we can demonstrate that it’s possible to consistently perform TunnelVision while simply being adjacent to the target host on the same LAN. We’re calling it “ArcaneTrickster” and plan on releasing it at a later date. However, we feature a demo in our videos, which are available in the proof of concept section.
根据这些反馈,我们决定开发一个强大的对抗性基础设施库,以实现进一步的局域网安全研究并演示实际攻击。例如,我们可以证明,只需在同一局域网上与目标主机相邻,就可以始终如一地执行 TunnelVision。我们称之为“ArcaneTrickster”,并计划在以后发布它。但是,我们在视频中提供了一个演示,可在概念验证部分找到。

Let Us Know 让我们知道
If you have questions or are interested in learning about how Leviathan Security Group can help you achieve your security goals, head over to our contact page and submit our short form.
如果您有任何疑问或有兴趣了解利维坦安全集团如何帮助您实现安全目标,请前往我们的联系页面并提交我们的简短表格。
Our team will reach out to you to schedule a time to learn more about your initiatives and priorities.
我们的团队将与您联系,安排时间详细了解您的计划和优先事项。
Credits 学分
Authors: 作者:
-
Lizzie Moratti 莉齐·莫拉蒂(Lizzie Moratti)
-
Dani Cronce 丹尼·克朗斯
Acknowledgements: 确认:
-
Sofia Aberegg 索菲亚·阿贝雷格
-
TC Johnson TC约翰逊
-
Brian Campbell 布莱恩·坎贝尔
-
Martin Bogomolni 马丁·博戈莫尔尼
-
Brad Haines 布拉德·海恩斯
-
Frank Heidt 弗兰克·海特
Special Thanks to: 特别鸣谢:
-
Electronic Frontier Foundation (EFF)
电子前沿基金会 (EFF) -
United States Cybersecurity Infrastructure and Security Agency (CISA)
美国网络安全基础设施和安全局 (CISA)
Appendix 附录
Prior research related to TunnelVision
与TunnelVision相关的先前研究
We found research related to DHCP leaking default routes over an incorrect interface as far back as 2015. However, it was implied that DHCP only pushed default routes and did not account for DHCP option 121.
早在 2015 年,我们就发现了与 DHCP 通过不正确的接口泄漏默认路由相关的研究。但是,这意味着 DHCP 仅推送默认路由,而不考虑 DHCP 选项 121。
In August 2023, a paper was published demonstrating that routing rules can be attacked in different ways to leak VPN traffic. The paper details two methods of leaking VPN traffic:
2023 年 8 月,发表了一篇论文,证明路由规则可以通过不同的方式受到攻击以泄露 VPN 流量。本文详细介绍了两种泄露VPN流量的方法:
-
Abusing non-RFC1918 IP ranges to leak traffic.
滥用非RFC1918 IP 范围泄漏流量。 -
DNS spoofing the VPN server’s domain name to trick the VPN client into adding a routing rule exception for an IP address.
DNS 欺骗 VPN 服务器的域名,诱骗 VPN 客户端为 IP 地址添加路由规则例外。
However, neither technique described in the August 2023 paper leveraged DHCP option 121 to push routes. Pushing routes through DHCP has a significantly higher impact from the same attacker vantage point (the ability to hand out IP leases for a non-RFC1918 range or spoofing DNS replies).
然而,2023 年 8 月论文中描述的两种技术都没有利用 DHCP 选项 121 来推送路由。从同一攻击者的角度来看,通过 DHCP 推送路由的影响要大得多(能够为非RFC1918范围分发 IP 租约或欺骗 DNS 回复)。
In-Depth Diagram Explanation
深入的图表解释
For posterity and because we haven’t encountered another diagram like ours (Figure 4), below are the steps from the diagram in as much detail as we could reasonably provide. We feel it could be useful to a future security researcher or a developer trying to understand the technology, so we are including it for their benefit.
为了子孙后代,因为我们没有遇到过像我们这样的其他图表(图 4),以下是图表中的步骤,尽可能详细地提供。我们认为它可能对未来的安全研究人员或试图了解该技术的开发人员有用,因此我们将其纳入其中是为了他们的利益。
-
An application process sends a payload to a socket it creates.
应用程序进程将有效负载发送到它创建的套接字。 -
The socket formats the payload into a packet and sends it to the routing table to determine which interface it should be sent through.
套接字将有效负载格式化为数据包,并将其发送到路由表,以确定应通过哪个接口发送有效负载。 -
The routing table determines that the packet should be sent through tun0.
路由表确定数据包应通过 tun0 发送。 -
The routing table sends the packet to the firewall.
路由表将数据包发送到防火墙。 -
The firewall rules allow the packet to continue to tun0.
防火墙规则允许数据包继续 tun0。 -
The network interface serializes the packet and writes it into a file descriptor at /dev/net/tun in userland.
网络接口序列化数据包,并将其写入用户空间中 /dev/net/tun 的文件描述符中。 -
The VPN client process reads the unencrypted raw bytes of the packet in the file descriptor.
VPN 客户端进程读取文件描述符中数据包的未加密原始字节。 -
The VPN process creates an encrypted payload and sends it to a socket the VPN made.
VPN 进程会创建一个加密的有效负载,并将其发送到 VPN 创建的套接字。 -
The socket formats the payload into a packet that is bound for the VPN’s server and sends it to the routing table to determine which interface it should be sent through.
套接字将有效负载格式化为绑定到 VPN 服务器的数据包,并将其发送到路由表以确定应通过哪个接口发送。 -
The routing table determines that the packet must be sent over the wlan0 interface.
路由表确定必须通过 wlan0 接口发送数据包。 -
The routing table sends the packet to the firewall.
路由表将数据包发送到防火墙。 -
The firewall rules determine that the outbound packet may continue using wlan0.
防火墙规则确定出站数据包可以继续使用 wlan0。 -
The network interface transfers the packet to its Wi-Fi driver.
网络接口将数据包传输到其 Wi-Fi 驱动程序。 -
The Wi-Fi driver sends the VPN-bound packet to the physical network interface card (NIC).
Wi-Fi 驱动程序将 VPN 绑定的数据包发送到物理网络接口卡 (NIC)。 -
The packet is sent across the internet to the VPN server.
数据包通过互联网发送到 VPN 服务器。 -
The VPN server sends a packet in response back to the physical NIC.
VPN 服务器将数据包发送回物理网卡。 -
The NIC sends the response packet to the Wi-Fi driver.
NIC 将响应数据包发送到 Wi-Fi 驱动程序。 -
The Wi-Fi driver delivers the response packet to wlan0.
Wi-Fi 驱动程序将响应数据包传送到 wlan0。 -
The response packet is sent to the firewall.
响应数据包将发送到防火墙。 -
The firewall rules allow the packet to continue.
防火墙规则允许数据包继续。 -
The packet is returned to the VPN socket.
数据包将返回到 VPN 套接字。 -
The socket receives the packet and sends the packet’s encrypted payload to the VPN client process.
套接字接收数据包并将数据包的加密有效负载发送到 VPN 客户端进程。 -
The VPN client process decrypts the payload and writes the unencrypted raw bytes of the response packet to the file descriptor.
VPN 客户端进程解密有效负载,并将响应数据包的未加密原始字节写入文件描述符。 -
The tun0 interface deserializes the bytes from the file descriptor and formats it into a packet.
tun0 接口反序列化文件描述符中的字节,并将其格式化为数据包。 -
The tun0 interface sends the packet to the firewall.
tun0 接口将数据包发送到防火墙。 -
The firewall rules allow the packet to continue.
防火墙规则允许数据包继续。 -
The packet is returned to the socket opened by the user’s application process.
数据包返回到用户的应用程序进程打开的套接字。 -
The payload from the packet is returned to the application process.
数据包中的有效负载将返回到应用程序进程。
转载请注明:TunnelVision (CVE-2024-3661): How Attackers Can Decloak Routing-Based VPNs For a Total VPN Leak | CTF导航