原文始发于 :EvilGophish’s Approach to Advanced Bot Detection with Cloudflare Turnstile
Introduction 介绍
Bots pose a significant threat to the integrity of phishing infrastructure, primarily by automating detection and countermeasures that can prematurely expose and neutralize simulated phishing campaigns. These automated agents can range from security scanners, which seek out and report phishing attempts, to malicious bots designed to flood systems with fake submissions, obscuring genuine interactions and skewing test results. For penetration testers and red team operators, the challenge is twofold: ensuring that our simulated phishing environments remain undetected for the duration of the test and maintaining the quality of data collected. By effectively mitigating bot interference, testers can ensure that their assessments accurately reflect how well an organization can withstand and respond to real-world phishing threats.
爬虫程序对网络钓鱼基础设施的完整性构成重大威胁,主要是通过自动检测和对策,这些措施可能会过早地暴露和消除模拟的网络钓鱼活动。这些自动化代理的范围可以从寻找和报告网络钓鱼尝试的安全扫描程序,到旨在用虚假提交淹没系统的恶意机器人,掩盖真实的交互并扭曲测试结果。对于渗透测试人员和红队操作员来说,挑战是双重的:确保我们的模拟网络钓鱼环境在测试期间不被发现,并保持收集的数据质量。通过有效缓解爬虫程序干扰,测试人员可以确保他们的评估准确反映组织抵御和响应现实世界网络钓鱼威胁的能力。
It is essential to have defense mechanisms in place to thwart off bots during your social engineering exercises. The previous way that EvilGophish would protect itself against bots was redirect rules and an IP address blacklist with Apache2 in front of the phishing infrastructure. You could define specific user agents, domain names, and IP addresses that would trigger an unauthorized request and redirect the client somewhere else away from the infrastructure. There is an obvious flaw with this methodology: everything is predefined. You cannot possibly prepare for every user agent that can potentially detect your infrastructure as phishing. The same goes for domain names and IP addresses. In comes Cloudflare Turnstile.
在您的社会工程练习中,必须建立防御机制来阻止机器人。EvilGophish 之前保护自己免受机器人攻击的方式是重定向规则和网络钓鱼基础设施前面带有 Apache2 的 IP 地址黑名单。您可以定义特定的用户代理、域名和 IP 地址,这些代理、域名和 IP 地址将触发未经授权的请求,并将客户端重定向到远离基础结构的其他位置。这种方法有一个明显的缺陷:一切都是预定义的。您不可能为每个可能将您的基础结构检测为网络钓鱼的用户代理做好准备。域名和 IP 地址也是如此。Cloudflare Turnstile 来了。
Defeating Bots with Cloudflare Turnstile
使用 Cloudflare Turnstile 击败机器人
In the digital domain, where bots constantly evolve to mimic human interactions more convincingly, distinguishing between genuine users and automated entities is increasingly challenging. Cloudflare Turnstile emerges as a sophisticated solution in this context, designed to seamlessly differentiate between human users and bots without compromising the user experience with intrusive challenges.
在数字领域,机器人不断进化以更令人信服地模仿人类交互,区分真实用户和自动化实体越来越具有挑战性。在这种情况下,Cloudflare Turnstile 是一种复杂的解决方案,旨在无缝区分人类用户和机器人,而不会因侵入性挑战而影响用户体验。
Invisible Verification 隐形验证
At its core, Cloudflare Turnstile leverages advanced behavior analysis and anomaly detection techniques. Unlike traditional CAPTCHA systems that require users to solve puzzles or identify images, Turnstile operates quietly in the background. It analyzes interaction patterns and browser environment characteristics to assess the likelihood of a visitor being human.
Cloudflare Turnstile 的核心是利用先进的行为分析和异常检测技术。与要求用户解决难题或识别图像的传统验证码系统不同,旋转门在后台安静运行。它分析交互模式和浏览器环境特征,以评估访问者是人类的可能性。
Behavioral Analysis 行为分析
Turnstile examines various aspects of user behavior, such as mouse movements, keystroke dynamics, and touch interactions. These subtle cues, which are challenging for bots to emulate convincingly, contribute to a risk score calculated for each visitor. By focusing on natural user interactions, Turnstile ensures that legitimate users are seldom, if ever, presented with a challenge.
Turnstile 检查用户行为的各个方面,例如鼠标移动、击键动态和触摸交互。这些微妙的线索对于机器人来说很难令人信服地模拟,有助于为每个访问者计算风险评分。通过专注于自然的用户交互,Turnstile 确保合法用户很少(如果有的话)面临挑战。
Adaptive Challenges 适应性挑战
When Turnstile encounters behavior that closely resembles bot activity, or when it can’t confidently distinguish a user as human, it may deploy lightweight, non-intrusive challenges as a secondary verification layer. These challenges are designed to be minimally disruptive, ensuring that even in cases where verification is required, user experience remains a top priority.
当 Turnstile 遇到与机器人活动非常相似的行为时,或者当它无法自信地将用户区分为人类时,它可能会部署轻量级、非侵入性质询作为辅助验证层。这些挑战旨在将破坏性降至最低,确保即使在需要验证的情况下,用户体验仍然是重中之重。
Continuous Learning 持续学习
Leveraging the power of machine learning, Turnstile continuously refines its detection algorithms based on new data. This adaptive approach ensures that Turnstile remains effective against evolving bot tactics. By analyzing vast datasets and identifying emerging patterns associated with automated behaviors, Cloudflare ensures that Turnstile’s detection mechanisms are always up-to-date.
利用机器学习的强大功能,Turnstile 根据新数据不断改进其检测算法。这种自适应方法确保 Turnstile 对不断发展的机器人策略保持有效。通过分析海量数据集并识别与自动化行为相关的新兴模式,Cloudflare 确保 Turnstile 的检测机制始终保持最新状态。
Privacy-centric Design 以隐私为中心的设计
In today’s digital landscape, user privacy is paramount. Turnstile is engineered with a strong emphasis on privacy, ensuring that personal data is protected. By focusing on behavioral patterns rather than personal information, Turnstile provides a verification method that respects user privacy while maintaining security.
在当今的数字环境中,用户隐私至关重要。旋转门的设计非常注重隐私,确保个人数据受到保护。通过关注行为模式而不是个人信息,Turnstile 提供了一种在维护安全的同时尊重用户隐私的验证方法。
Cloudflare Turnstile Conclusion
Cloudflare 旋转门 结论
Cloudflare Turnstile represents a significant advancement in the fight against bots, offering a user-friendly, privacy-conscious alternative to traditional CAPTCHAs. Its ability to operate invisibly, combined with the use of advanced behavioral analysis and adaptive challenges, ensures that bots are effectively thwarted while genuine users proceed unhindered. As phishing infrastructure becomes more sophisticated, tools like Turnstile are invaluable for maintaining the integrity of the infrastructure, ensuring that only real users can interact with it.
Cloudflare Turnstile 代表了对抗机器人的重大进步,为传统验证码提供了一种用户友好、注重隐私的替代方案。它能够隐身运行,结合先进的行为分析和适应性挑战,确保机器人被有效挫败,而真正的用户可以不受阻碍地进行。随着网络钓鱼基础设施变得越来越复杂,像 Turnstile 这样的工具对于维护基础设施的完整性非常宝贵,确保只有真正的用户才能与之交互。
EvilGophish Tutorial EvilGophish 教程
In order to provide this functionality, EvilGophish now comes with a HTTP server that listens locally on port 80 to process Cloudflare Turnstile challenge responses while the Evilginx proxy will proxy to this local server in order to carry out challenge response validation. A diagram of this infrastructure is shown below.
为了提供此功能,EvilGophish 现在附带了一个 HTTP 服务器,该服务器在端口 80 上本地侦听以处理 Cloudflare Turnstile 质询响应,而 Evilginx 代理将代理到该本地服务器以执行质询响应验证。此基础结构的示意图如下所示。

EvilGophish 基础设施布局
The first step is to create an account on Cloudflare, add a new site which will be your phishing domain, and retrieve the public/private keys.
第一步是在 Cloudflare 上创建一个帐户,添加一个新站点,该站点将成为您的网络钓鱼域,并检索公钥/私钥。
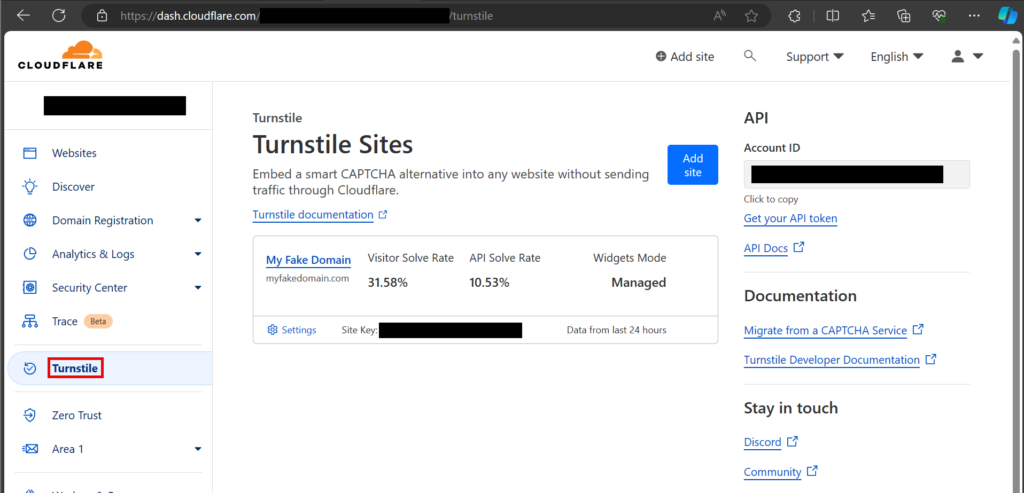
Once you have retrieved the public and private keys to validate Cloudflare Turnstile challenge responses, the next step is to create an HTML template for the Cloudflare Turnstile validation page. I have included a sample template in the EvilGophish repository which is shown below. I will not cover all of the template variables in-depth here as they are covered in the project’s README.md file.
检索公钥和私钥以验证 Cloudflare Turnstile 质询响应后,下一步是为 Cloudflare Turnstile 验证页面创建 HTML 模板。我在 EvilGophish 存储库中包含了一个示例模板,如下所示。我不会在这里深入介绍所有模板变量,因为它们在项目的 README.md 文件中都有介绍。
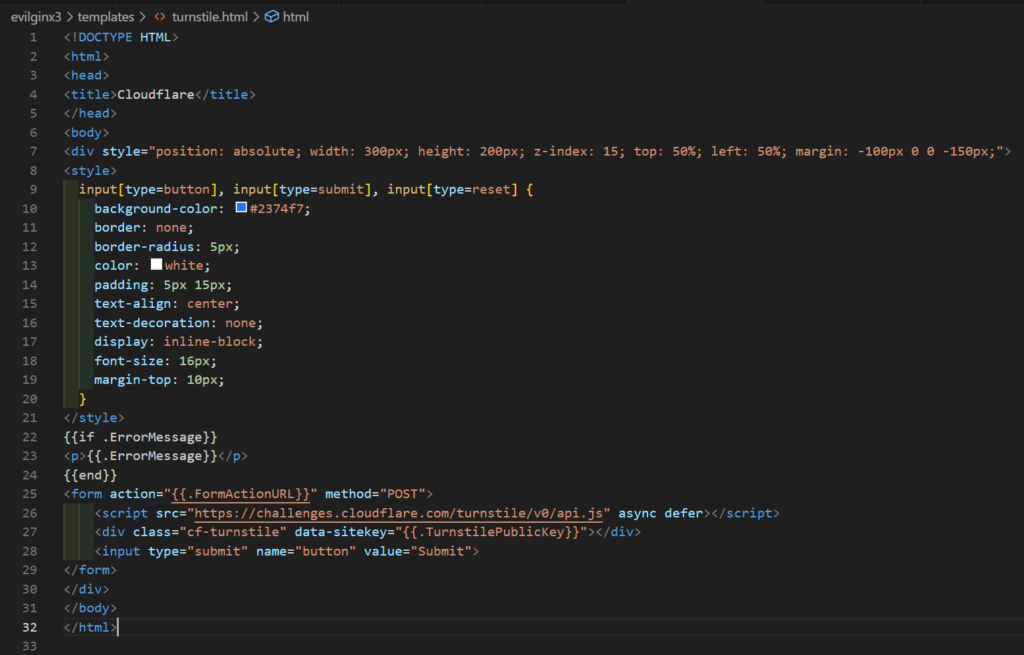
Cloudflare Turnstile Go HTML 模板示例
The use of Go HTML templates is to prevent static HTML code signatures in phishing infrastructure. It goes without saying that if you use the default template included in the project, you are likely going to get your infrastructure caught quickly. You are advised to change the template to include different code that has different styling and text. It also gives operators a lot of flexibility in how they would like to include this in their campaigns. You can make this fit together with your pretext by including logos that correspond with your phish, etc. There is also a template for forbidden responses that return a 403 code which is shown below.
使用 Go HTML 模板是为了防止网络钓鱼基础结构中的静态 HTML 代码签名。不言而喻,如果您使用项目中包含的默认模板,您可能会很快发现您的基础架构。建议您更改模板以包含具有不同样式和文本的不同代码。它还为运营商提供了很大的灵活性,他们希望如何将其包含在他们的活动中。您可以通过包含与您的网络钓鱼等相对应的徽标来使其与您的借口相吻合。还有一个用于返回 403 代码的禁止响应的模板,如下所示。
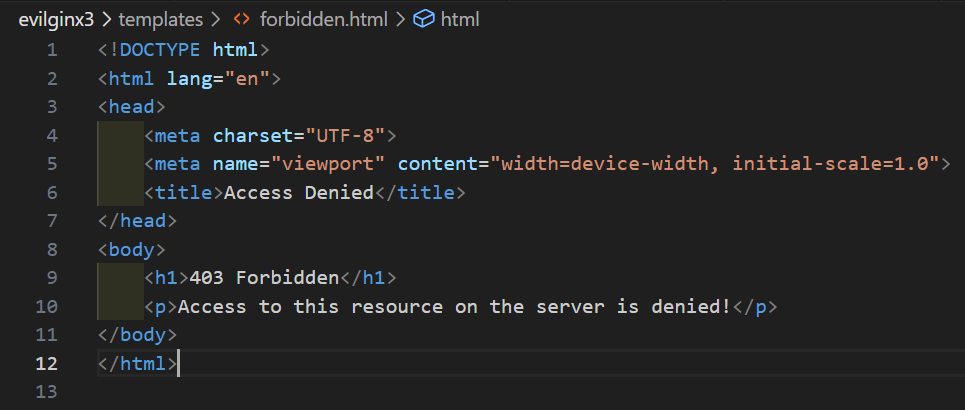
403 Forbidden Go HTML 模板示例
For all requests that do not have a valid session cookie from the Evilginx server (i.e. a request that doesn’t trigger the lure path), a 403 Forbidden response will be returned. A 403 Forbidden will also be returned if any errors occur during the Cloudflare Turnstile challenge response validation. This makes the infrastructure more malleable overall by being able to control this content as an operator. After you have your templates created and you are satisfied with them, you are ready to get going. The last step is to provide your Cloudflare Turnstile site keys to Evilginx and launch a campaign. I have included detailed instructions in the README.md of the project and have shown a similar command line below.
对于所有没有来自 Evilginx 服务器的有效会话 cookie 的请求(即未触发诱饵路径的请求),将返回 403 Forbidden 响应。如果在 Cloudflare Turnstile 质询响应验证期间发生任何错误,也将返回 403 Forbidden。这使得基础架构的整体延展性更强,因为它能够作为操作员控制这些内容。创建模板并对它们感到满意后,您就可以开始了。最后一步是向 Evilginx 提供您的 Cloudflare Turnstile 站点密钥并启动活动。我在项目 README.md 中包含了详细说明,并在下面显示了类似的命令行。
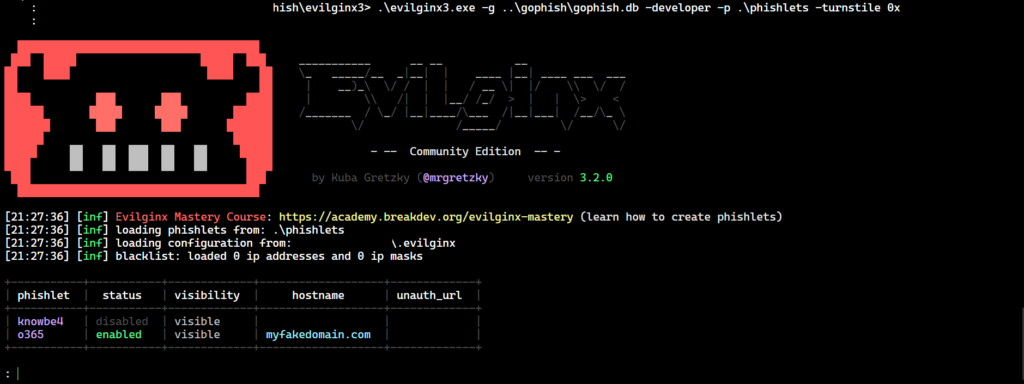
Evilginx 旋转门命令行标志
When you officially launch your campaign, you will see the HTML page you created for your template. I have shown the default template in action below.
当您正式启动广告系列时,您将看到您为模板创建的 HTML 页面。我在下面展示了默认模板。
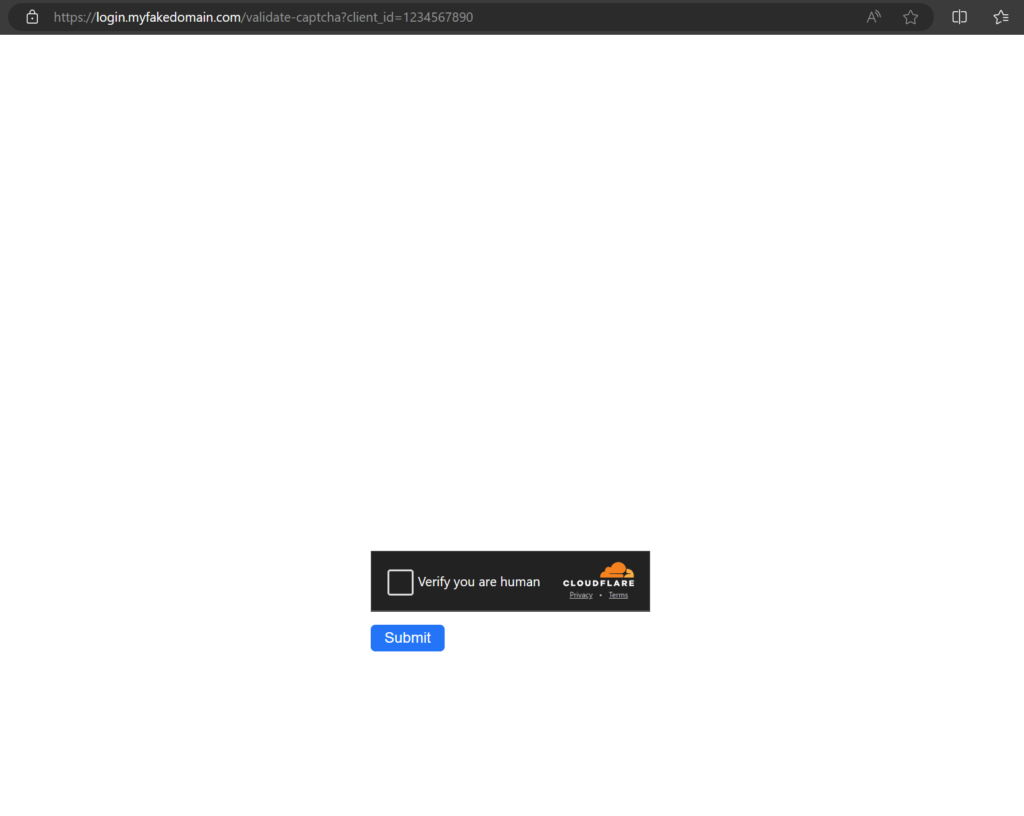
浏览器中的 Cloudflare Turnstile HTML 页面
Upon successfully completing a challenge, a victim will then be redirected to the Evilginx lure. If a client fails to complete the challenge, it will continue to display the Cloudflare Turnstile template page until a success occurs. If a success never happens, the same page will continue to be displayed and the client will never be granted access to the Evilginx lure. This forces the client to produce a successful challenge or access is never granted, hardening your phishing infrastructure against bots and other automated scanning software.
成功完成挑战后,受害者将被重定向到 Evilginx 诱饵。如果客户端未能完成质询,它将继续显示 Cloudflare Turnstile 模板页面,直到成功为止。如果从未成功,则将继续显示相同的页面,并且客户端将永远不会被授予对 Evilginx 诱饵的访问权限。这迫使客户端成功提出质询,否则永远不会授予访问权限,从而加强您的网络钓鱼基础设施免受机器人和其他自动扫描软件的攻击。
Conclusion 结论
The escalating sophistication of bots presents a formidable challenge in cybersecurity, particularly when ensuring the integrity of systems designed to simulate or test phishing vulnerabilities. Traditional defenses often fall short, either by impeding user experience with cumbersome challenges or failing to accurately distinguish between human and automated threats. Cloudflare Turnstile represents a paradigm shift in this ongoing battle, offering a solution that balances robust security with user convenience.
爬虫程序的复杂性不断升级,这给网络安全带来了巨大的挑战,尤其是在确保旨在模拟或测试网络钓鱼漏洞的系统的完整性时。传统的防御措施往往不足,要么通过繁琐的挑战阻碍用户体验,要么无法准确区分人为威胁和自动威胁。Cloudflare Turnstile 代表了这场持续战斗中的范式转变,它提供了一种平衡强大安全性和用户便利性的解决方案。
By leveraging advanced behavior analysis, adaptive challenges, and continuous learning from interaction data, Turnstile provides an effective shield against bots, ensuring that only genuine users can interact with critical infrastructure. Its invisible verification process minimizes disruptions, allowing legitimate users to proceed unhindered, while still offering the option of minimal, non-intrusive challenges when necessary. This dual approach ensures that security does not come at the expense of accessibility.
通过利用高级行为分析、自适应挑战和从交互数据中持续学习,Turnstile 提供了针对机器人的有效屏障,确保只有真正的用户才能与关键基础设施进行交互。其隐形验证过程最大限度地减少了中断,允许合法用户不受阻碍地进行,同时在必要时仍提供最小的、非侵入性的挑战选项。这种双重方法确保安全性不会以牺牲可访问性为代价。
For cybersecurity professionals and penetration testers/red team operators, integrating Cloudflare Turnstile into phishing infrastructure or similar testing environments underscores a commitment to cutting-edge security practices. It not only enhances the realism and effectiveness of simulations but also protects the integrity of these essential cybersecurity exercises. Turnstile’s ability to adapt to evolving threats, coupled with its privacy-conscious design, makes it an indispensable tool in the modern security toolkit.
对于网络安全专业人员和渗透测试人员/红队操作员来说,将 Cloudflare Turnstile 集成到网络钓鱼基础设施或类似的测试环境中,强调了对尖端安全实践的承诺。它不仅增强了模拟的真实性和有效性,而且还保护了这些基本网络安全练习的完整性。Turnstile 能够适应不断变化的威胁,加上其注重隐私的设计,使其成为现代安全工具包中不可或缺的工具。
转载请注明:EvilGophish’s Approach to Advanced Bot Detection with Cloudflare Turnstile | CTF导航