
Preamble 序言
When prioritizing detection engineering efforts, it’s essential to understand the most prevalent tactics, techniques, and procedures (TTPs) observed in the wild. This knowledge helps defenders make informed decisions about the most effective strategies to implement – especially where to focus engineering efforts and finite resources.
在确定检测工程工作的优先级时,必须了解在野外观察到的最流行的策略、技术和程序 (TTP)。这些知识有助于防御者就最有效的实施策略做出明智的决策,尤其是将工程工作和有限资源集中在何处。
To highlight these prevalent TTPs, we analyzed over 100,000 Windows malware samples extracted over several months from one of our dynamic malware analysis tools, Detonate. To generate this data and alerts, we leveraged Elastic Defend behavior (mapped to MITRE ATT&CK) and memory threat detection rules. It should be noted that this dataset is not exhaustive, it may not represent the entire spectrum of malware behavior, and specifically does not include long-term or interactive activity.
为了突出显示这些流行的 TTP,我们分析了几个月来从我们的动态恶意软件分析工具之一 Detonate 中提取的 100,000 多个 Windows 恶意软件样本。为了生成这些数据和警报,我们利用了 Elastic Defend 行为(映射到 MITRE ATT&CK)和内存威胁检测规则。应该注意的是,此数据集并非详尽无遗,它可能不代表恶意软件行为的全部范围,并且具体不包括长期或交互式活动。
Below an ES|QL query to summarize our dataset by file type:
低于 ES|QL 查询按文件类型汇总我们的数据集:
 Dataset by extension – 20 unique file types
Dataset by extension – 20 unique file types
按扩展名划分的数据集 – 20 种独特的文件类型
Tactics 策略
Beginning with tactics, we aggregated the alerts generated by this corpus of malware samples and organized them according to the counts of process.entity_id and alerts. As depicted in the image below, the most frequent tactics included defense evasion, privilege escalation, execution, and persistence. Certain tactics commonly linked with post-exploitation activities, such as lateral movement, provided an anticipated lower prevalence because these actions are commonly manually driven by the threat actor after the initial implant is established vs. being automated by the malware in our dataset.
从策略开始,我们汇总了该恶意软件样本语料库生成的警报,并根据警报的计数 process.entity_id 和警报进行组织。如下图所示,最常见的策略包括防御规避、权限升级、执行和持久性。某些通常与利用后活动相关的策略(例如横向移动)提供了预期的较低流行率,因为这些操作通常由威胁参与者在初始植入建立后手动驱动,而不是由我们数据集中的恶意软件自动驱动。

Tactics by volume 按数量划分的战术
In the following sections, we will delve into each tactic and the techniques and sub-techniques of each that exerted the most influence.
在以下各节中,我们将深入研究每种策略以及每种影响最大的技术和子技术。
Defense Evasion 防御规避
Defense Evasion involves methods employed by adversaries to avoid detection by security teams or capabilities. The foremost tactic detected was defense evasion, triggering 189 distinct detection rules (nearly 40% of our current Windows rules). The primary techniques noted are associated with code injection, defense tampering, masquerading, and system binary proxy execution.
防御规避涉及对手为避免安全团队或能力检测到而采用的方法。检测到的最重要的策略是防御规避,触发了 189 条不同的检测规则(占我们当前 Windows 规则的近 40%)。上述主要技术与代码注入、防御篡改、伪装和系统二进制代理执行有关。

Top observed defense evasion techniques
观察到的顶级防御规避技术
When we pivot by sub-techniques, it becomes evident that certain advanced techniques such as DLL side-loading and Parent PID Spoofing have become increasingly popular, even among non-targeted malwares. Both are frequently linked with code injection and masquerading.
当我们按子技术进行调整时,很明显,某些高级技术(例如DLL旁加载和父PID欺骗)变得越来越流行,即使在非目标恶意软件中也是如此。两者都经常与代码注入和伪装联系在一起。
Furthermore, system binary proxies Rundll32 and Regsvr32 remain highly abused, with a notable rise in the utilization of malicious MSI installers for malware delivery. The practice of masquerading as legitimate system binaries, whether through renaming or process hollowing, remains prevalent as well, serving as a means to evade user suspicion.
此外,系统二进制代理 Rundll32 仍然 Regsvr32 被高度滥用,恶意 MSI 安装程序用于恶意软件传递的利用显着增加。无论是通过重命名还是进程空心化,伪装成合法系统二进制文件的做法仍然很普遍,作为逃避用户怀疑的一种手段。

Top observed defense evasion sub-techniques
观察到的顶级防御规避子技术
Tampering with Windows Defender stands out as the most frequently observed defense evasion tactic, emphasizing the importance for defenders to acknowledge that adversaries will attempt to obscure their activities.
篡改 Windows Defender 是最常观察到的防御规避策略,强调了防御者承认对手会试图掩盖其活动的重要性。
Process Injection is prevalent across various malware families, whether they target legitimate system binaries remotely to blend in or employ self-injection (sometimes paired with DLL side-loading through a trusted binary). Furthermore, there is a noticeable uptick in the use of NTDLL unhooking to bypass security solutions reliant on user-mode APIs monitoring (Elastic Defend is not impacted).
进程注入在各种恶意软件系列中都很普遍,无论它们以合法系统二进制文件为目标进行远程混合还是采用自注入(有时通过受信任的二进制文件与DLL旁加载配对)。此外,使用 NTDLL 解钩来绕过依赖于用户模式 API 监控的安全解决方案的情况明显增加(Elastic Defend 不受影响)。

The most effective endpoint behavior rules for defense evasion
防御规避最有效的端点行为规则
From our shellcode alerts we can clearly see that self-injection is more prevalent than remote:
从我们的 shellcode 警报中,我们可以清楚地看到,自注入比远程注入更普遍:

Shellcode alerts volume by infection target type (local vs remote)
Shellcode 按感染目标类型(本地与远程)发出警报
Almost 50 unique vendors’ binaries abused for DLL side-loading, of which Microsoft is the top choice:
近 50 个独特的供应商二进制文件被滥用于 DLL 旁加载,其中 Microsoft 是首选:

DLL side-load by host process code signature subject name
按主机进程代码签名主题名称旁加载 DLL
Defense evasion comprises various techniques and sub-techniques necessitating comprehensive coverage due to their frequent occurrence. For instance, apart from memory threat protection, half of our rules are specifically tailored to address this tactic.
防御规避包括各种技术和子技术,由于它们经常发生,因此需要全面覆盖。例如,除了内存威胁防护之外,我们一半的规则都是专门为解决这种策略而量身定制的。
Privilege Escalation 权限提升
This tactic consists of techniques that adversaries use to gain greater permissions on a system or network. The most commonly used techniques relate to access token manipulation, execution through privileged system services, and bypassing User Account Control.
这种策略包括攻击者用来在系统或网络上获得更大权限的技术。最常用的技术涉及访问令牌操作、通过特权系统服务执行以及绕过用户帐户控制。

Privilege escalation techniques observed in the dataset
在数据集中观察到的权限提升技术
The most frequently observed sub-technique involved impersonation as the Trusted Installer service, which aligns closely with defense evasion and often precedes attempts to manipulate system-protected resources.
最常观察到的子技术涉及模拟为受信任的安装程序服务,它与防御规避密切相关,并且通常先于尝试操作受系统保护的资源。
Concerning User Account Control bypass, the primary method we observed was elevation by mimicking trusted directories, which is also related to DLL side-loading. Additionally, other methods like elevation via extended startupinfo (elevated parent PID spoofing) are increasingly prevalent among commodity malware.
关于用户帐户控制绕过,我们观察到的主要方法是通过模拟受信任目录来提升,这也与 DLL 旁加载有关。此外,其他方法(例如通过扩展的 startupinfo(提升父 PID 欺骗)进行提升)在商品恶意软件中越来越普遍。

Privilege escalation top observed sub-techniques
权限提升顶部观察到的子技术
As evident from the list below, there’s a notable rise in the use of vulnerable drivers (BYOVD) to manipulate protected objects and acquire kernel mode execution privileges.
从下面的列表中可以明显看出,使用易受攻击的驱动程序 (BYOVD) 来操作受保护对象和获取内核模式执行权限的情况显着增加。

The most effective endpoint behavior rules for privilege escalation
权限提升的最有效的终结点行为规则
Below, you’ll find a list of the most commonly exploited drivers triggered by our YARA rules:
下面,您将找到由我们的 YARA 规则触发的最常被利用的驱动程序列表:

Top triggered yara rules for vulnerable drivers detection
用于检测易受攻击的驱动程序的顶级触发 yara 规则
Execution 执行
Execution encompasses methods that lead to running adversary-controlled code on a local or remote system. These techniques are frequently combined with methods from other tactics to accomplish broader objectives, such as network reconnaissance or data theft.
执行包括导致在本地或远程系统上运行对手控制的代码的方法。这些技术经常与其他策略的方法相结合,以实现更广泛的目标,例如网络侦测或数据盗窃。
The most common techniques observed here involved Windows command and scripting languages, with the proxying of execution via the Windows Management Instrumentation (WMI) interface closely trailing behind.
此处观察到的最常见的技术涉及 Windows 命令和脚本语言,通过 Windows Management Instrumentation (WMI) 接口代理执行紧随其后。
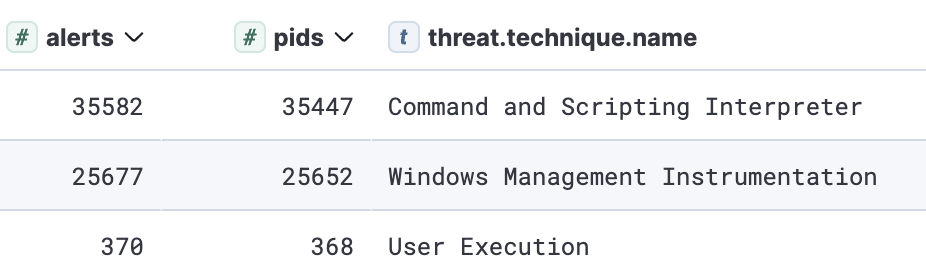 Execution techniques observed in our dataset
Execution techniques observed in our dataset
Powershell remains a preferred scripting language for malware execution chains, followed by Javascript and VBscript. Multi-stage malware delivery routinely involves a combination of two or more scripting languages.
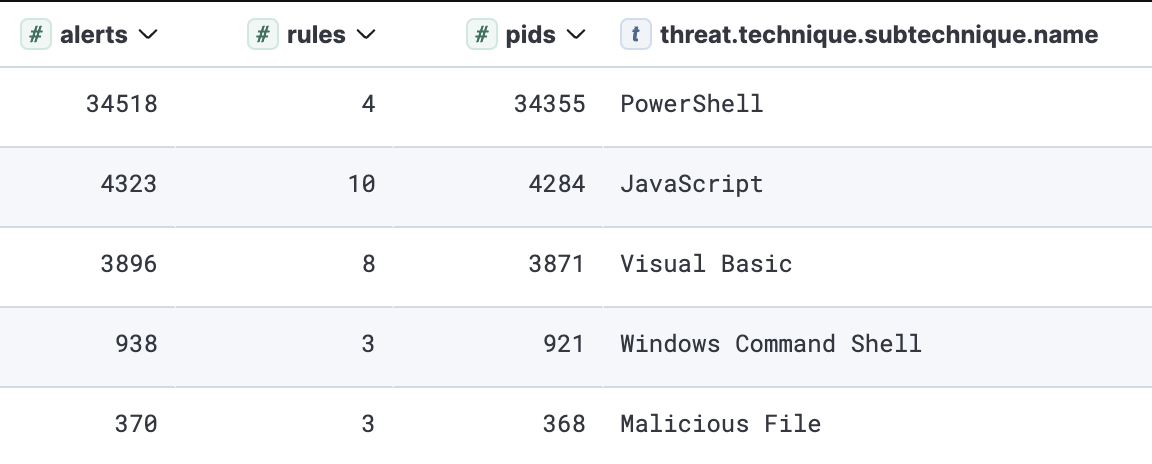 Execution top observed sub-techniques
Execution top observed sub-techniques
执行顶级观察子技术
Here is a list of the most frequently triggered endpoint behavior detections for this tactic:
以下是此策略最常触发的终结点行为检测列表:
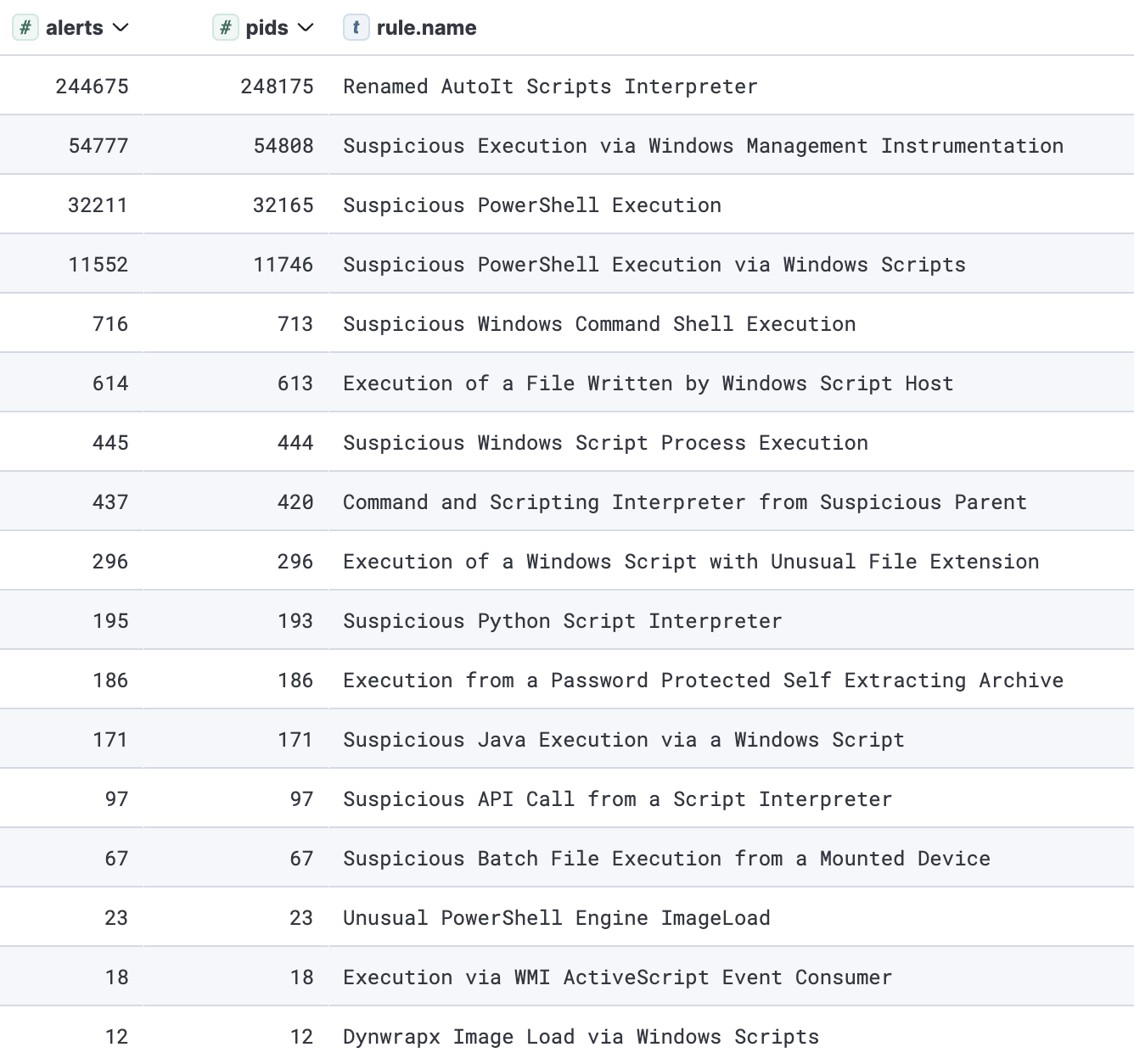 Frequently triggered execution detections
Frequently triggered execution detections
Windows’ default scripting languages remain the top preference for malware execution. However, there has been a slight uptick in the shift towards using other third-party scripting interpreters like Python, AutoIt, Java and Lua.
Persistence
It’s common for malware to install itself on an infected host. No surprises here: the most frequently observed persistence methods include scheduled tasks, the run key and startup folder, and Windows services (which typically require administrator privileges).
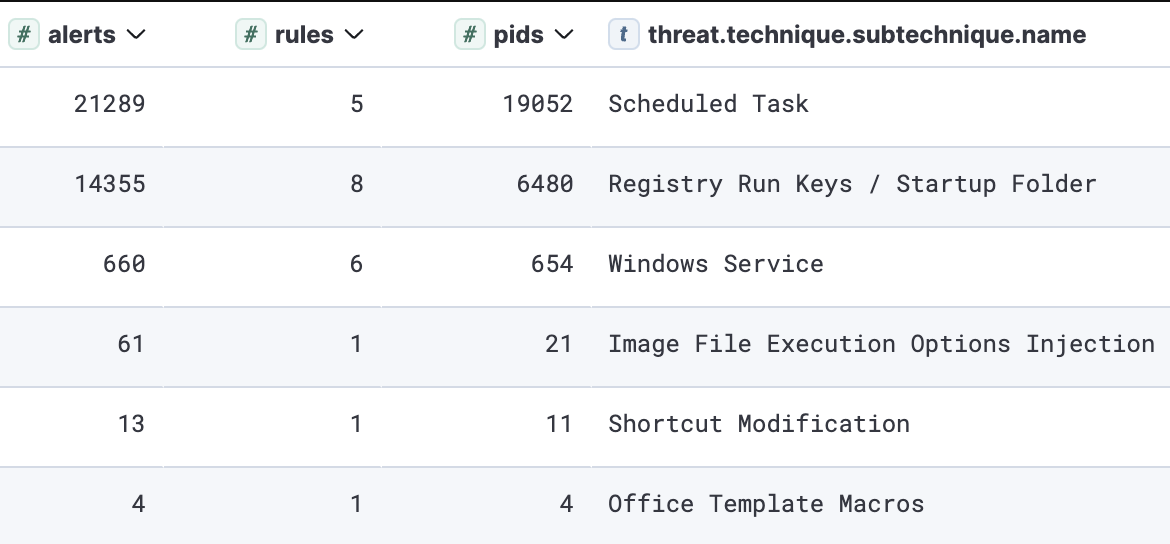 Top observed sub-techniques for persistence
Top observed sub-techniques for persistence
The top three persistence sub-techniques depicted in the list below are also commonly encountered in regular software installations. Therefore, it’s necessary to dissect them into multiple detections with additional suspicious signals to reduce false positives and enhance precision.
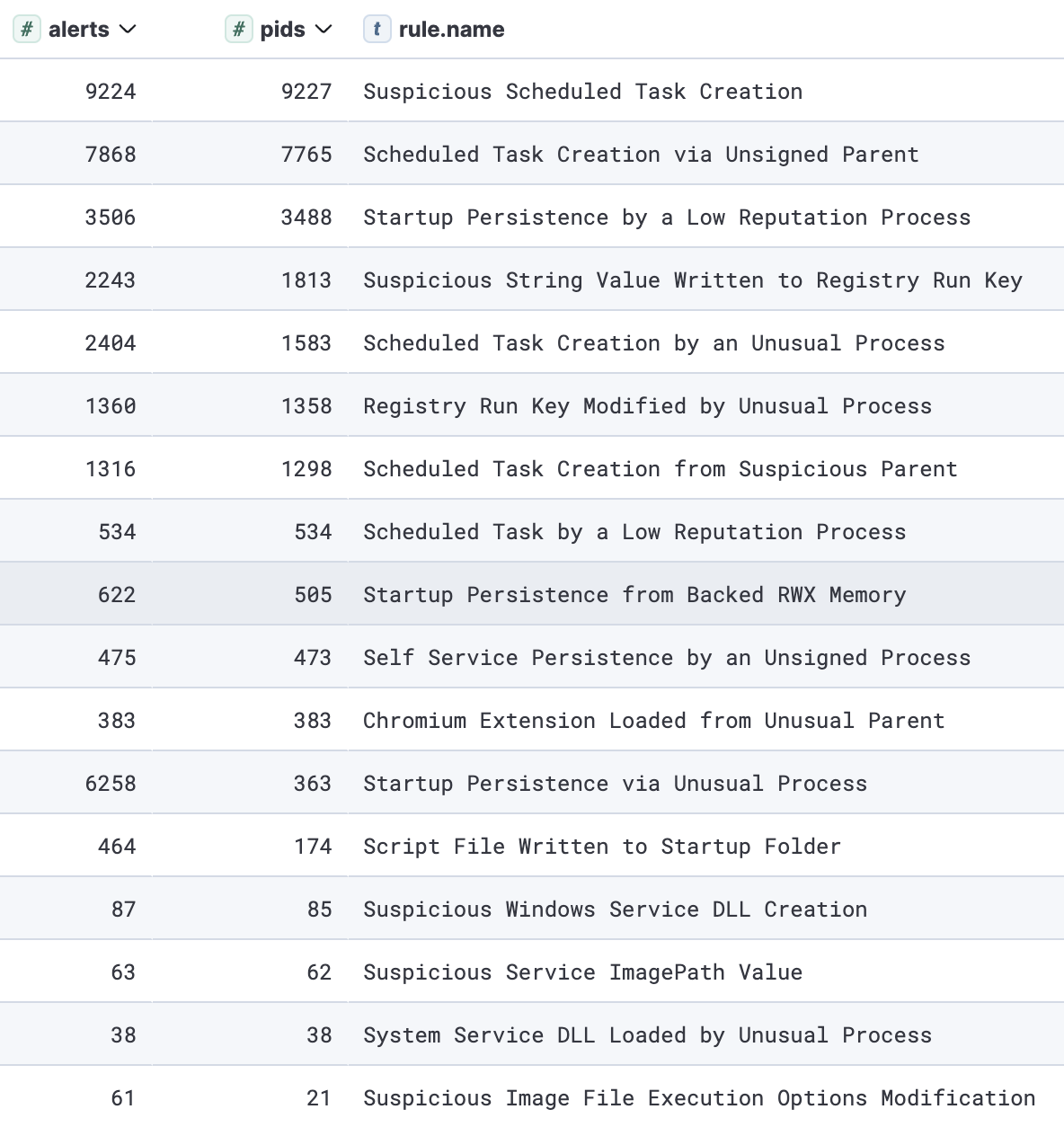 Top triggered alerts for persistence
Top triggered alerts for persistence
持久性最常触发的警报
Initial Access 初始访问
Considering the dataset’s composition, initial access was associated with primarily macro-enabled documents and Windows shortcut objects. Although a significant portion of the detonated samples also involved other formats, such as ISO/VHD containers with MSI installers extensively utilized for delivery, their genuine malicious behavior typically manifests in areas such as defense evasion and persistence.
考虑到数据集的组成,初始访问主要与启用宏的文档和 Windows 快捷方式对象相关联。尽管引爆样本的很大一部分还涉及其他格式,例如广泛用于交付的带有 MSI 安装程序的 ISO/VHD 容器,但它们真正的恶意行为通常表现在防御规避和持久性等领域。
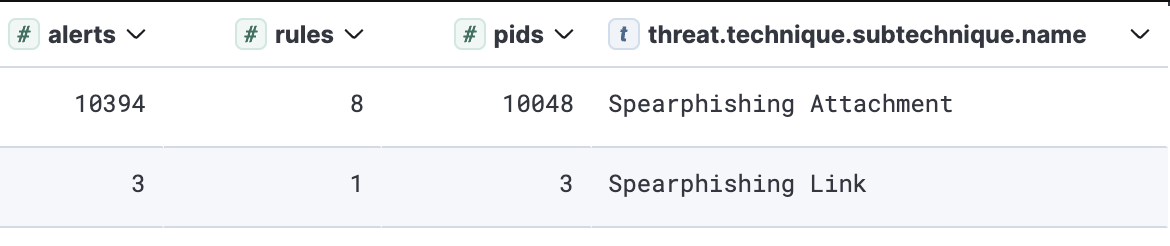 Top sub-techniques for initial access
Top sub-techniques for initial access
用于初始访问的顶级子技术
The most frequently abused Microsoft-signed binaries originating from malicious Microsoft Office documents align closely with execution and defense evasion tactics, command and scripting interpreters, and system binary proxy execution.
源自恶意 Microsoft Office 文档的最常被滥用的 Microsoft 签名二进制文件与执行和防御规避策略、命令和脚本解释器以及系统二进制代理执行密切相关。
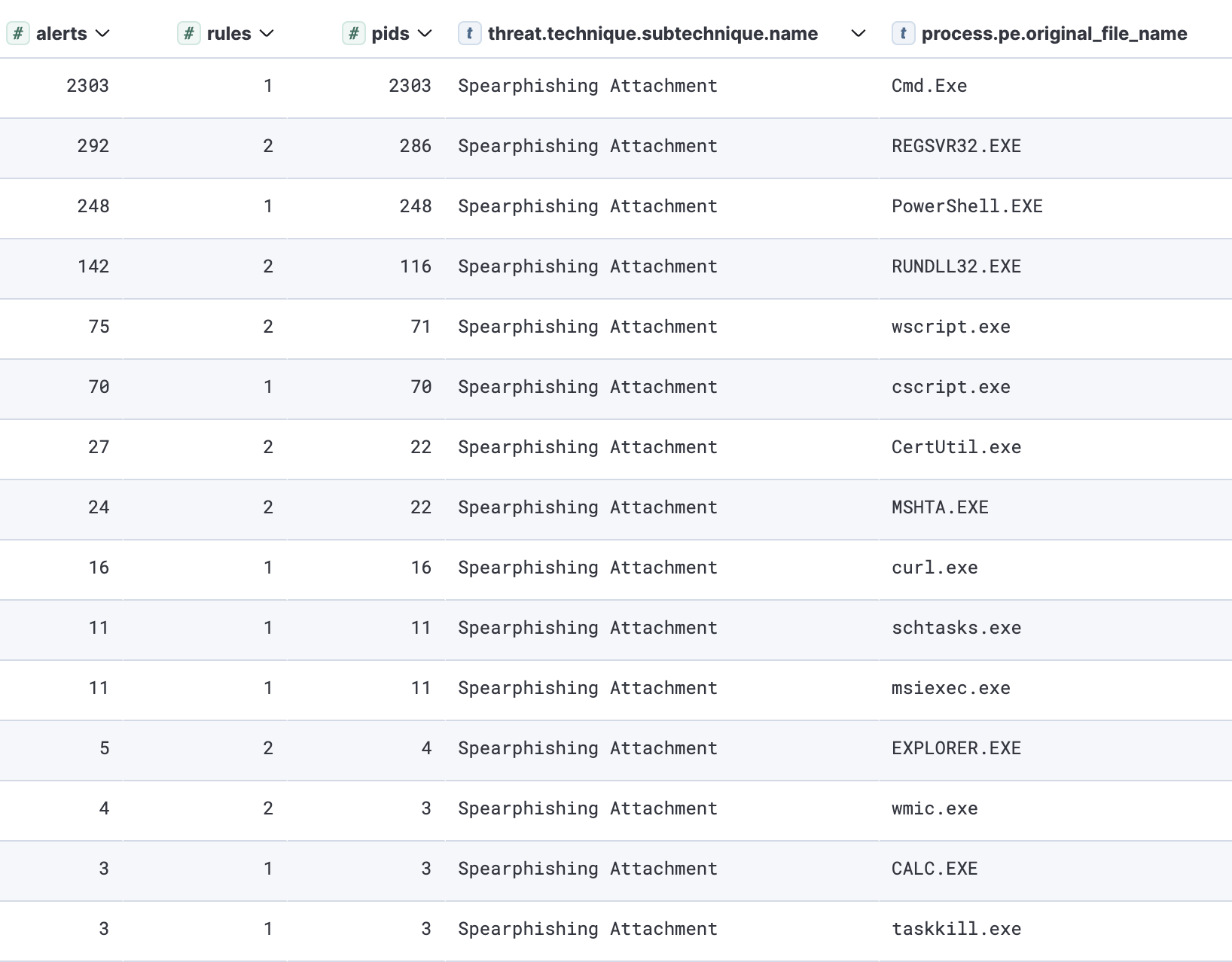 Top spawned child processes from malicious office documents
Top spawned child processes from malicious office documents
Here is a list of the most frequently triggered detections for initial access, regarding phishing attachments:
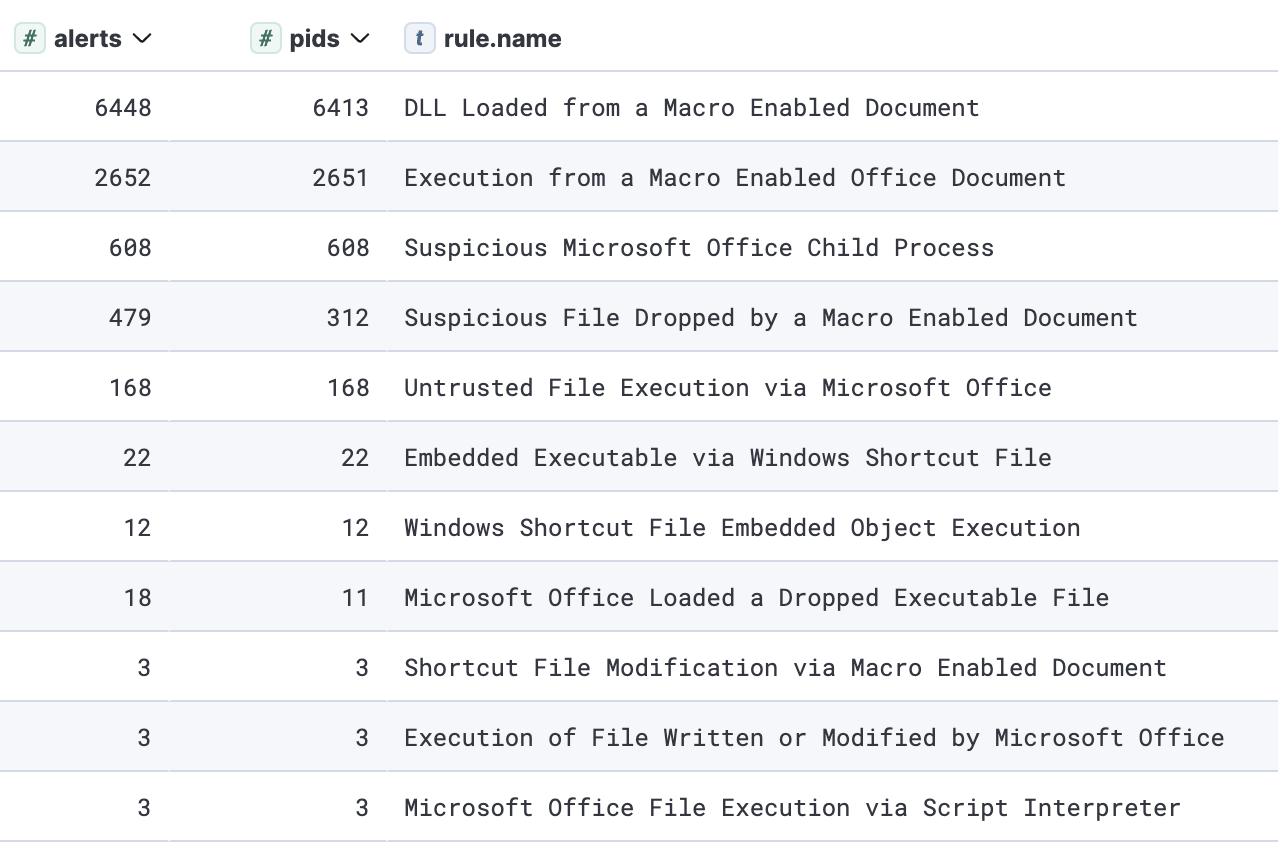 Top triggered rules for initial access via malicious attachments
Top triggered rules for initial access via malicious attachments
通过恶意附件进行初始访问的热门触发规则
Credential Access 凭据访问
Credential access in malware is frequently linked to information stealers. The most targeted credentials are typically associated with Windows Credential Manager and browser password stores. Domain and system-protected credentials require elevated privileges and are more likely a feature of a subsequent stage.
恶意软件中的凭据访问通常与信息窃取者有关。最有针对性的凭据通常与 Windows 凭据管理器和浏览器密码存储相关联。域和受系统保护的凭据需要提升的权限,并且更有可能是后续阶段的功能。
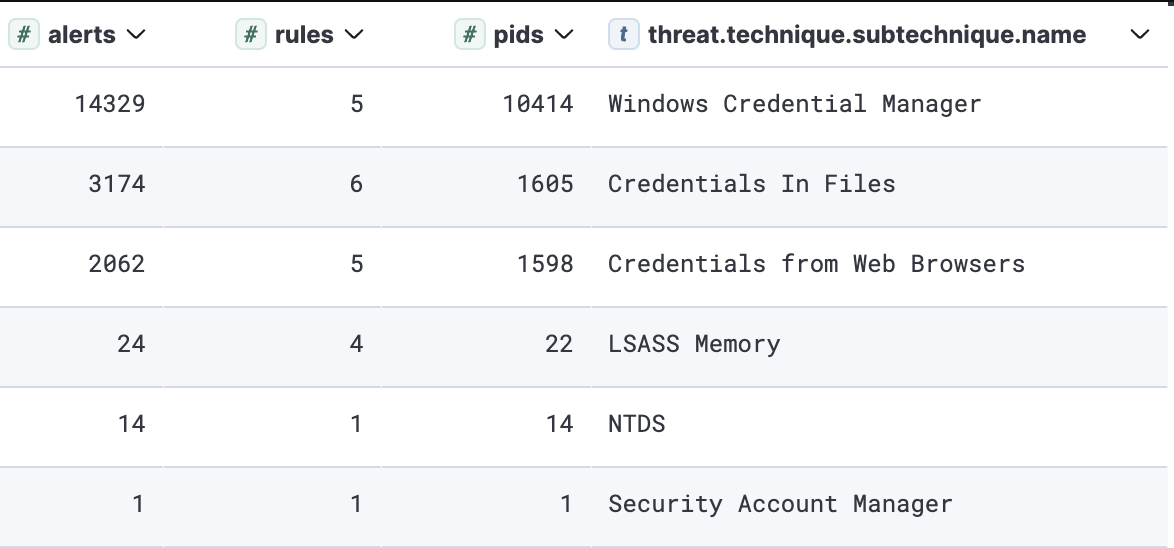 Top observed credential access sub-techniques
Top observed credential access sub-techniques
最常观察到的凭据访问子技术
Below a breakdown of the endpoint behavior detections that triggered the most on credentials access:
以下是触发凭据访问最多的终结点行为检测的细分:
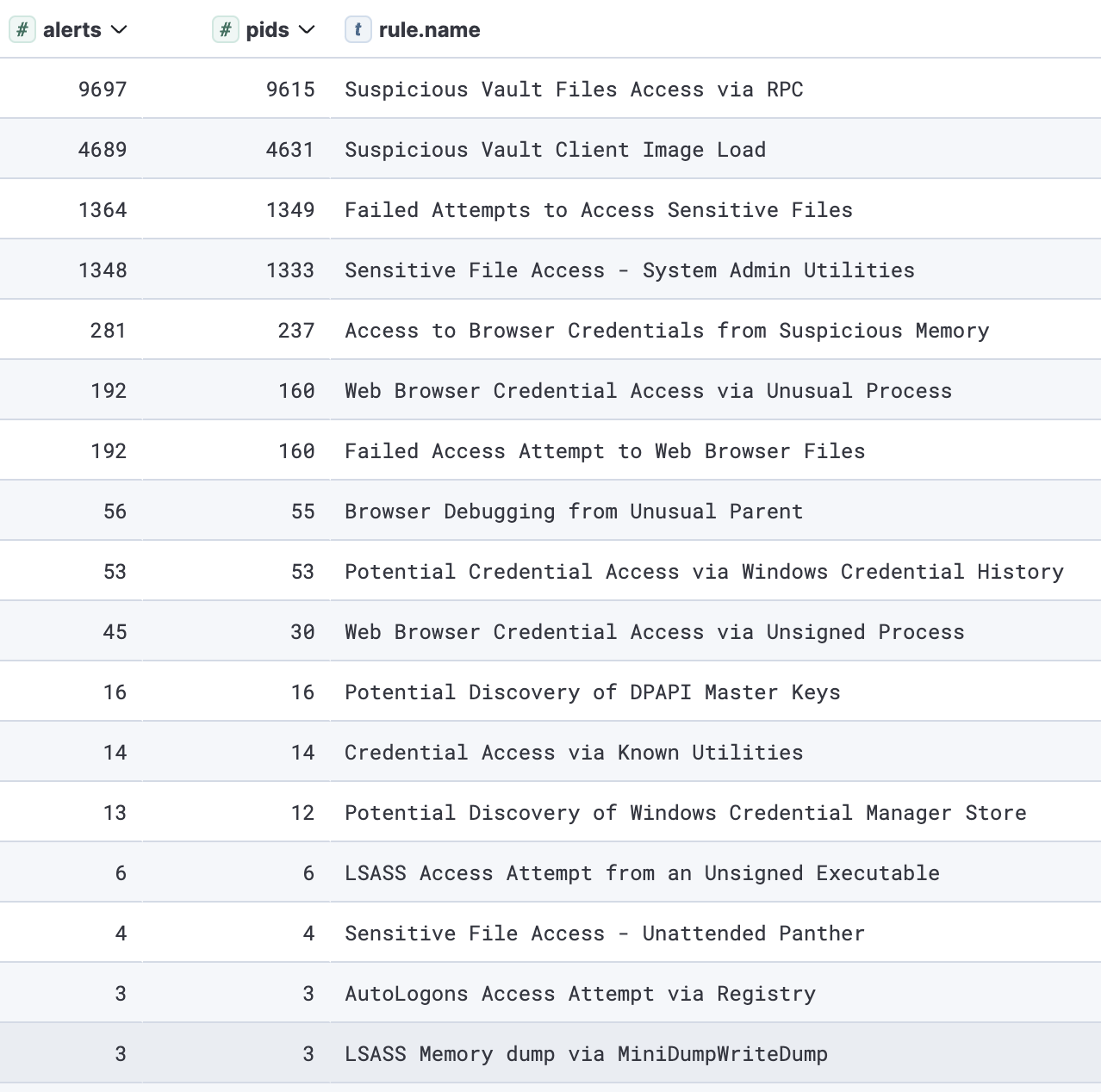 Frequently triggered credential access-related detection rules
Frequently triggered credential access-related detection rules
频繁触发的凭证访问相关检测规则
The majority of credentials access behaviors resemble typical file access events. Therefore, it’s essential to correlate and enrich them with additional signals to reduce false positives and enhance comprehension.
大多数凭据访问行为类似于典型的文件访问事件。因此,必须用额外的信号来关联和丰富它们,以减少误报并增强理解力。
Conclusion 结论
Even though this small dataset of about 100,000 malware samples represents only a fraction of the possible malware in the wild right now, we can still derive important insights from it about the most common TTPs using our behavioral detections. Those insights help us make decisions about detection engineering priorities, and defenders should make that part of their strategies.
尽管这个包含约 100,000 个恶意软件样本的小型数据集仅代表目前野外可能存在的恶意软件的一小部分,但我们仍然可以使用我们的行为检测从中获得有关最常见 TTP 的重要见解。这些见解有助于我们做出有关检测工程优先级的决策,防御者应将其作为其战略的一部分。
原文始发于hackthebox:Unveiling malware behavior trends