Research from Lab52 has uncovered a recent Turla campaign exhibiting novel tactics and a customized variant of the Kazuar trojan. This analysis offers technical insights into the campaign’s methodology and provides indicators of compromise (IOCs) to bolster defensive measures.
Lab52 的研究发现,最近的 Turla 活动展示了新颖的策略和 Kazuar 木马的定制变体。该分析提供了对该活动方法的技术见解,并提供了妥协指标(IOC)以加强防御措施。
Turla, a cyberespionage group with suspected links to the Russian FSB, is known for its precision targeting and persistent operational tempo. Active since at least 2004, Turla targets government entities, research institutions, embassies, and industries within the energy, telecommunications, and pharmaceutical sectors globally.
Turla 是一个涉嫌与俄罗斯联邦安全局有联系的网络间谍组织,以其精确的目标定位和持续的行动节奏而闻名。 Turla 至少自 2004 年起就开始活跃,其目标是全球范围内的政府实体、研究机构、大使馆以及能源、电信和制药领域的行业。
The campaign investigated demonstrates Turla’s focus on targeted attacks. Initial access likely occurs via prior infection, followed by the deployment of a malicious DLL disguised within legitimate-looking libraries (SkyTel, NVIDIA, etc.). This ‘Pelmeni Wrapper’ loads the next stage payload.
调查的活动表明 Turla 专注于有针对性的攻击。初始访问可能是通过先前的感染发生的,然后部署伪装在看似合法的库(SkyTel、NVIDIA 等)中的恶意 DLL。这个“Pelmeni Wrapper”装载下一阶段的有效载荷。
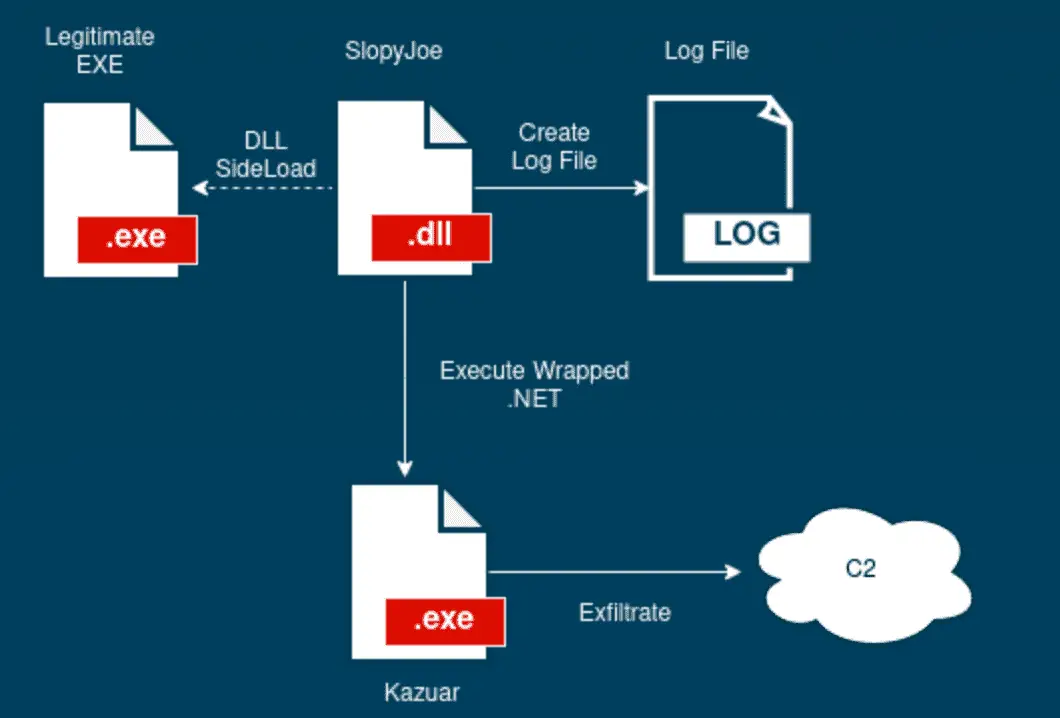
Infection chain 感染链
The Pelmeni Wrapper exhibits the following functionality:
水饺包装机具有以下功能:
- Operational Logging: Generates a hidden log file using randomized names and extensions for tracking campaign activity.
操作日志记录:使用随机名称和扩展名生成隐藏日志文件,以跟踪活动活动。 - Payload Delivery: Employs a custom decryption scheme leveraging a pseudorandom number generator to facilitate function loading and execution.
有效负载交付:采用自定义解密方案,利用伪随机数生成器来促进函数加载和执行。 - Execution Flow Redirection: Manipulates process threads and injects code to divert execution to a decrypted .NET assembly containing the core malware.
执行流重定向:操纵进程线程并注入代码以将执行转移到包含核心恶意软件的解密.NET 程序集。
The climax of Turla‘s elaborate scheme culminates with the activation of Kazuar, a multiplatform trojan horse that has been a staple in Turla’s arsenal since its discovery in 2017. Lab52’s analysis sheds light on subtle yet significant evolutions in Kazuar’s deployment, noting a new protocol for data exfiltration and variations in the logging directory – deviations that mark this sample’s uniqueness from its predecessors.
Turla 精心策划的计划随着 Kazuar 的激活而达到高潮,Kazuar 是一种多平台特洛伊木马,自 2017 年发现以来一直是 Turla 武器库中的主要内容。Lab52 的分析揭示了 Kazuar 部署中微妙但重大的演变,并指出了一种新协议用于数据泄露和日志目录中的变化——这些偏差标志着该样本与其前身的独特性。
The extracted .NET assembly is a modified Kazuar trojan. Key differences compared to previously analyzed versions include:
提取的 .NET 程序集是经过修改的 Kazuar 木马。与之前分析的版本相比,主要差异包括:
- Expanded Exfiltration Protocol: Support for socket-based exfiltration enhances the malware’s communication adaptability.
扩展的渗透协议:对基于套接字的渗透的支持增强了恶意软件的通信适应性。 - Modified Log Storage: A shift in log directory placement suggests customization for this campaign.
修改日志存储:日志目录位置的变化建议对此活动进行定制。
This research sheds light on Turla’s evolving tactics and their ongoing use of the Kazuar trojan. As APTs adapt, understanding their techniques remains critical for proactive defense. By integrating threat intelligence and remaining vigilant, organizations can mitigate the risks posed by this advanced threat actor.
这项研究揭示了 Turla 不断发展的策略以及他们对 Kazuar 木马的持续使用。随着 APT 的适应,了解其技术对于主动防御仍然至关重要。通过集成威胁情报并保持警惕,组织可以减轻这种高级威胁行为者带来的风险。
原文始发于 ·:Turla Leverages ‘Pelmeni Wrapper’ for Stealthy Kazuar Backdoor Delivery
转载请注明:Turla Leverages ‘Pelmeni Wrapper’ for Stealthy Kazuar Backdoor Delivery | CTF导航