Introduction 介绍
On February 19, 2023, ConnectWise published a security advisory for their ScreenConnect remote management tool. In the advisory, they describe two vulnerabilities, an authentication bypass with CVSS 10.0 and a path traversal with CVSS 8.4 (both currently without assigned CVE IDs). In this post we will dive into the technical details of the authentication bypass. You can view our POC here.
2023 年 2 月 19 日,ConnectWise 发布了针对其 ScreenConnect 远程管理工具的安全公告。在公告中,他们描述了两个漏洞,一个是 CVSS 10.0 的身份验证绕过漏洞,另一个是 CVSS 8.4 的路径遍历(两者目前都没有分配 CVE ID)。在这篇文章中,我们将深入探讨身份验证绕过的技术细节。您可以在此处查看我们的 POC。
Patch Diffing 补丁差异
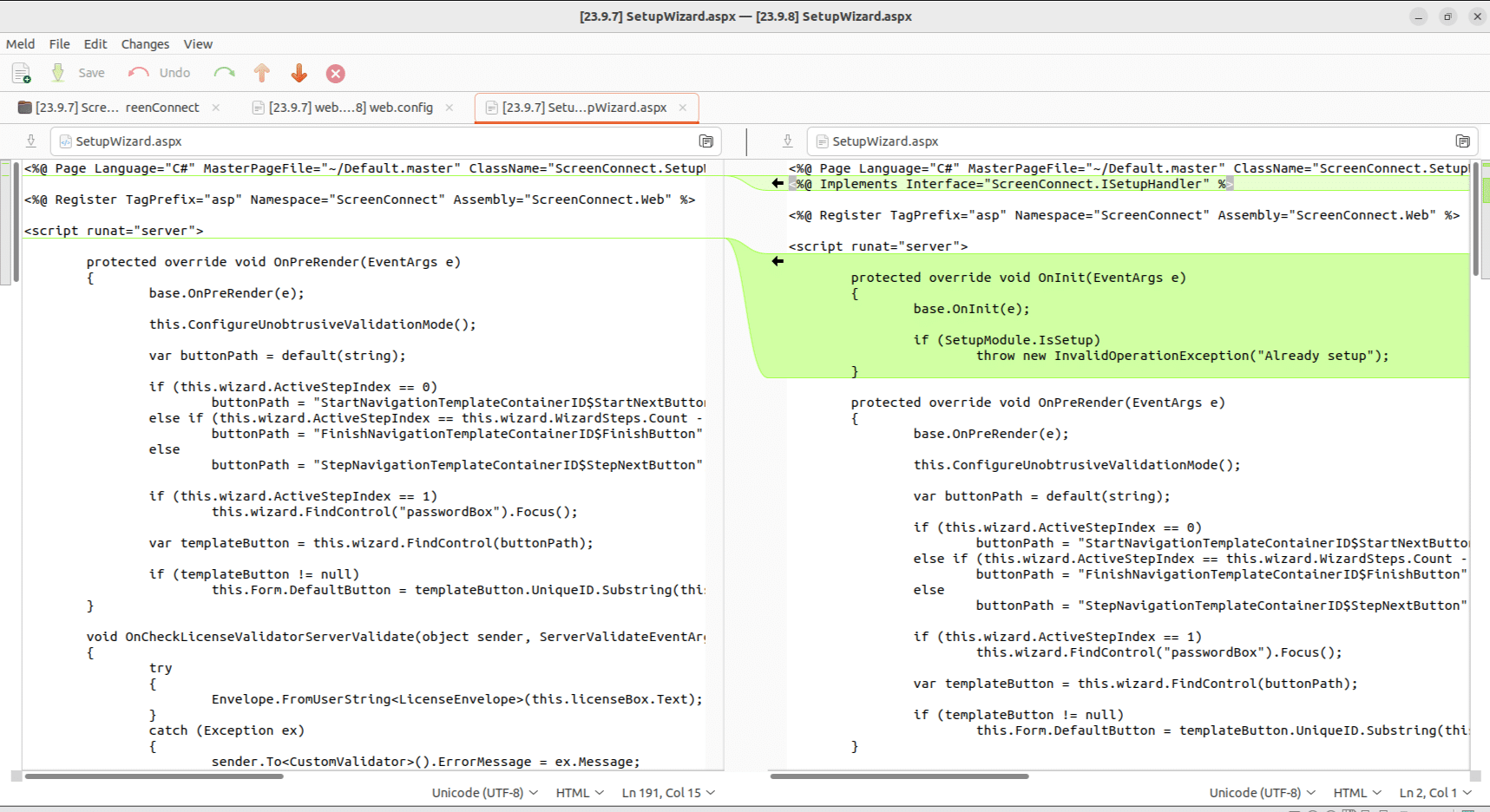
Comparing versions 23.9.7.8804 and 23.9.8.8811, we find a small update to SetupWizard.aspx. We see that a check was added to make sure that the initial application setup has not been completed if a user it trying to access the SetupWizard. The SetupWizard is responsible for creating an initial user and password, so it makes sense that this page should be locked down after an initial user has been created.
比较版本 23.9.7.8804 和 23.9.8.8811,我们发现 SetupWizard.aspx .我们看到添加了一个检查,以确保如果用户尝试访问 SetupWizard,则初始应用程序设置尚未完成。SetupWizard 负责创建初始用户和密码,因此在创建初始用户后锁定此页面是有道理的。
Figure 1. SetupWizard.aspx
图 1.SetupWizard.aspx
The Vulnerability 漏洞
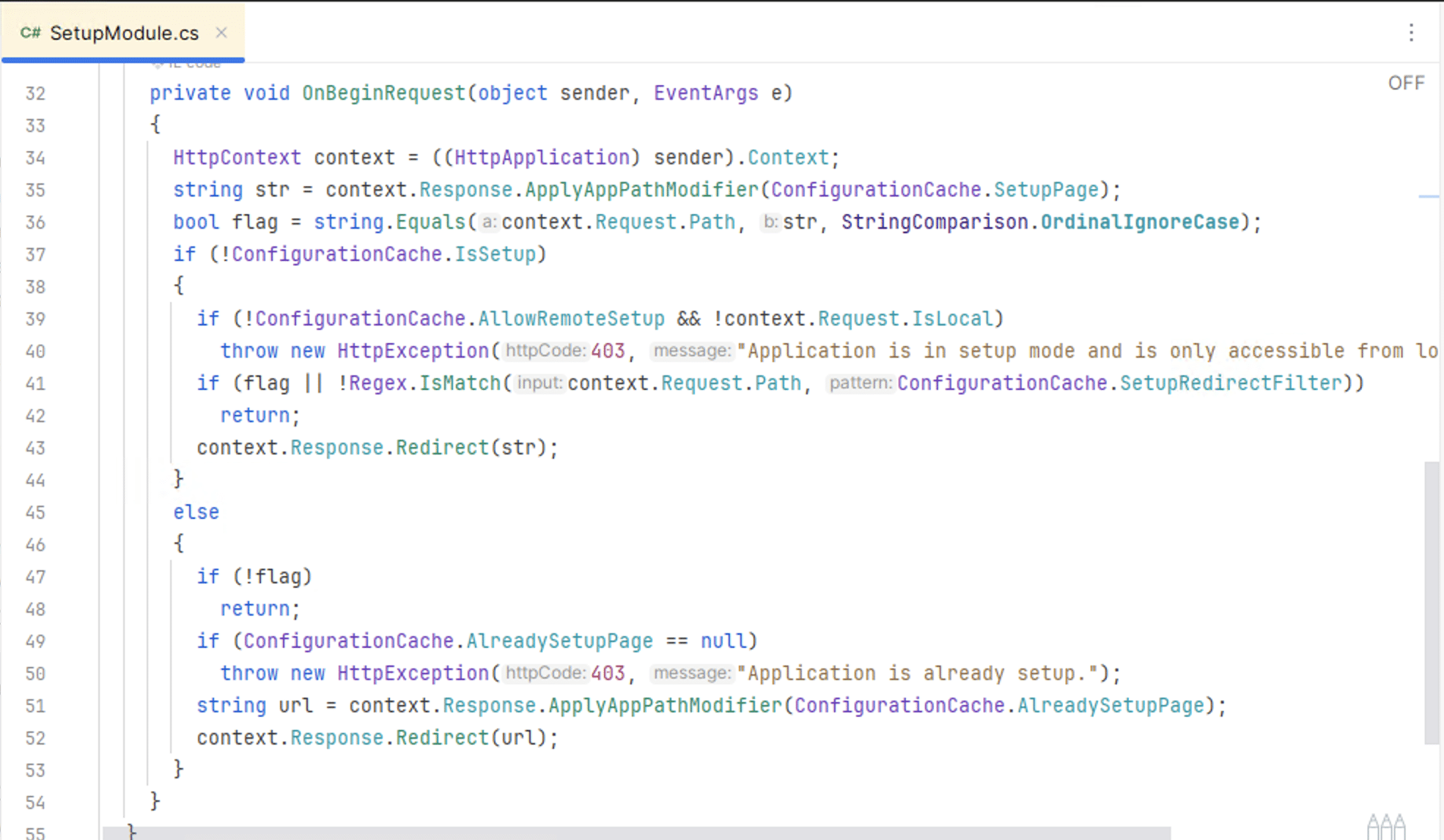
There is a HTTP request filter in SetupModule.cs that has two responsibilities:
有一个 HTTP 请求过滤器, SetupModule.cs 它有两个职责:
- If the application hasn’t been setup, redirect all requests to
SetupWizard.aspx
如果尚未设置应用程序,请将所有请求重定向到SetupWizard.aspx - If the application has been setup, deny any requests to
SetupWizard.aspxor redirect toAdministration.aspx
如果应用程序已设置,请拒绝任何请求SetupWizard.aspx或重定向到Administration.aspx
Figure 2. SetupModule.cs OnBeginRequest
图2.SetupModule.cs OnBeginRequest
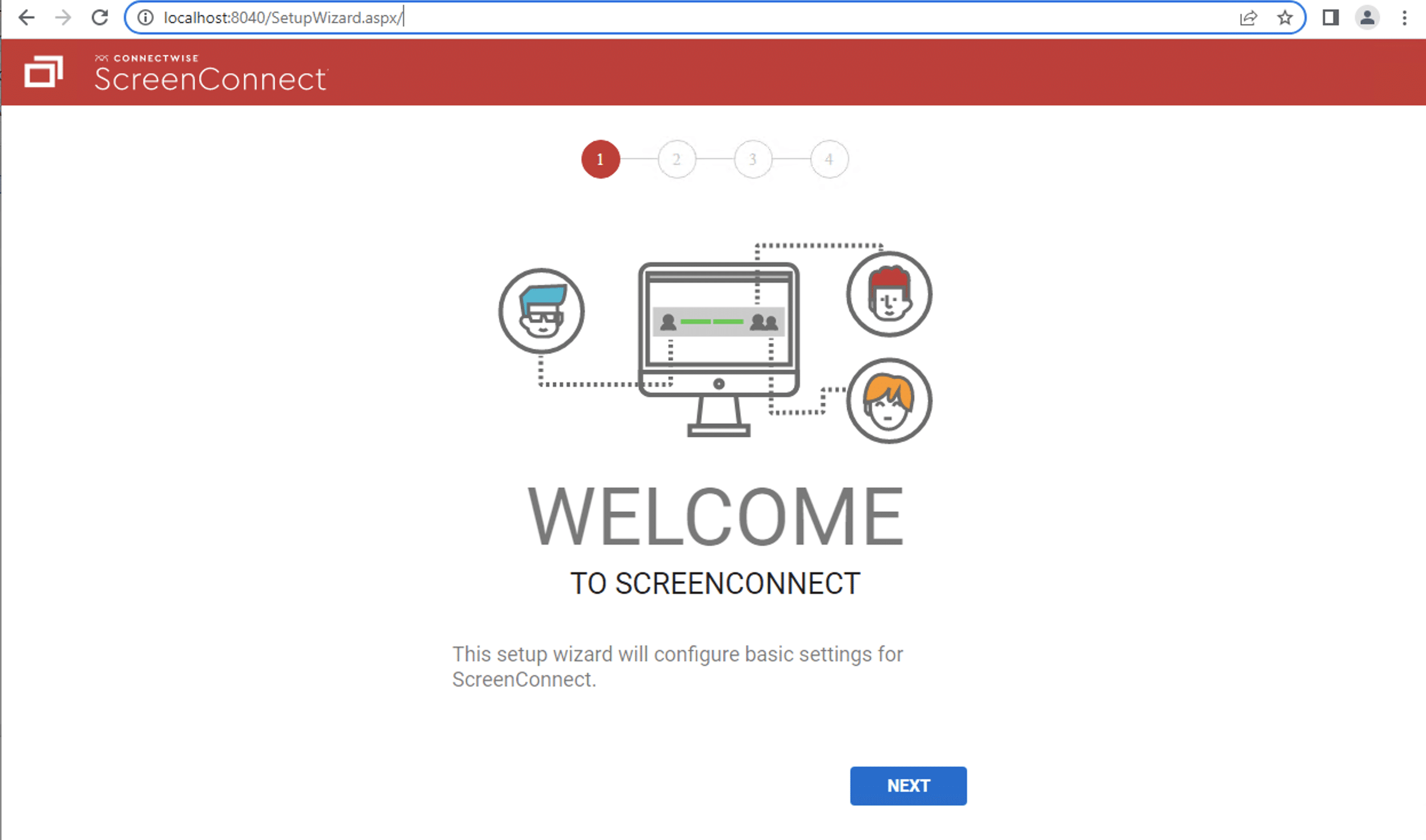
However, there is an issue with how this code checks if the request URL is SetupPage.aspx. The use of string.Equals checks for exact equality, so a URL like <app_url>/SetupWizard.aspx will match. However, there are other URLs that resolve to SetupWizard.aspx that don’t match. If we simply add a forward slash to the end of the URL (<app_url>/SetupWizard.aspx/) we get access to the setup wizard, even after the application is already setup.
但是,此代码检查请求 URL 是否为 SetupPage.aspx .使用 string.Equals 检查完全相等,因此 URL like <app_url>/SetupWizard.aspx 将匹配。但是,还有其他解析为 SetupWizard.aspx 不匹配的 URL。如果我们只是在 URL ( <app_url>/SetupWizard.aspx/ ) 的末尾添加一个正斜杠,我们就可以访问安装向导,即使在应用程序已经设置完毕之后也是如此。
Figure 3. SetupWizard.aspx
图3.SetupWizard.aspx
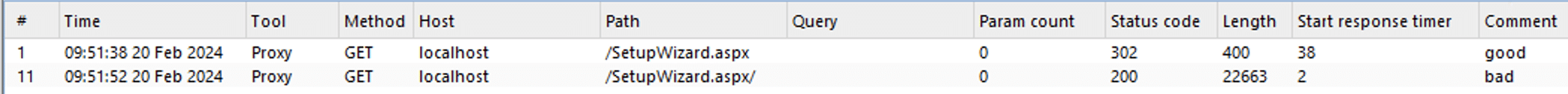
We can observe the differences in responses using Burp Suite. Notice the request path /SetupWizard.aspx responds with a 302, but the malicious path /SetupWizard.aspx/ responds with a 200.
我们可以使用 Burp Suite 观察响应的差异。请注意,请求路径 /SetupWizard.aspx 以 302 响应,但恶意路径 /SetupWizard.aspx/ 以 200 响应。
Indicators of Compromise
入侵指标
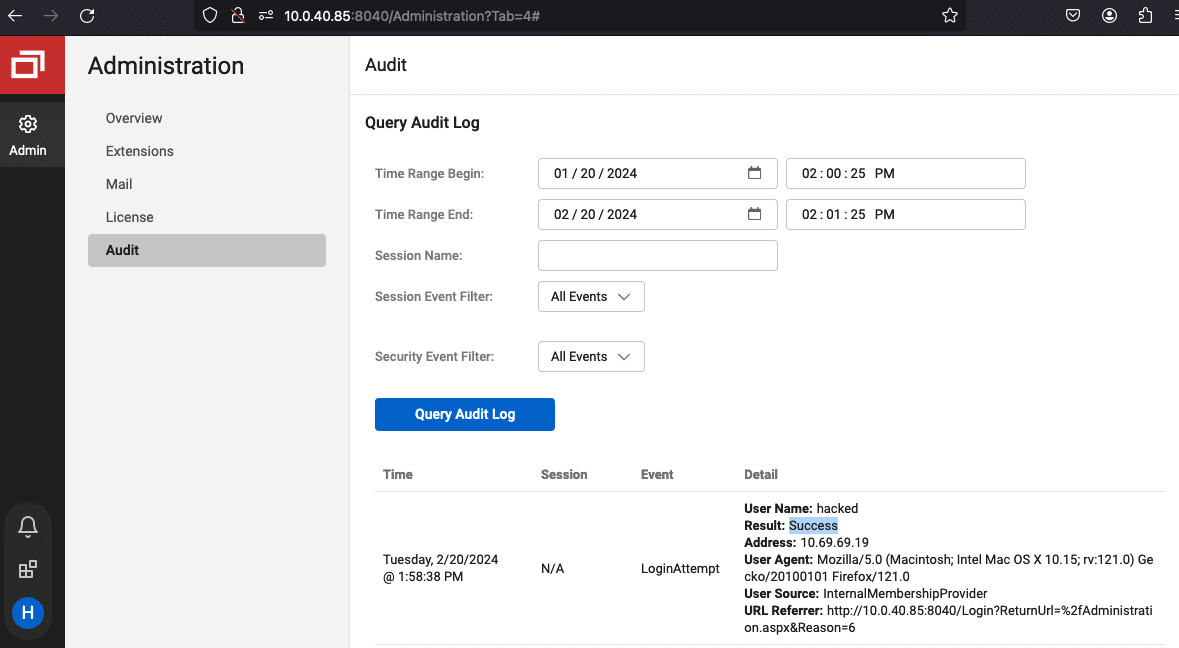
The application’s Admin -> Audit page displays a list of recent login attempts along with the IP address. You can check this page for any unrecognized users or IP addresses.
应用程序的“管理员>审核”页面显示最近登录尝试的列表以及 IP 地址。您可以检查此页面是否有任何无法识别的用户或 IP 地址。
As soon as we had sufficient information, we shared it with GreyNoise for which they developed a tag. Check out their tag here: https://viz.greynoise.io/tags/connectwise-screenconnect-auth-bypass-rce-attempt?days=1
一旦我们有足够的信息,我们就与GreyNoise共享,他们为此开发了一个标签。在这里查看他们的标签: https://viz.greynoise.io/tags/connectwise-screenconnect-auth-bypass-rce-attempt?days=1
Summary 总结
This vulnerability allows an attacker to create their own administrative user on the ScreenConnect server, giving them full control over the server. This vulnerability follows a theme of other recent vulnerabilities that allow attackers to reinitialize applications or create initial users after setup. See our recent writeup for a CVE-2024-0204 as an example.
此漏洞允许攻击者在 ScreenConnect 服务器上创建自己的管理用户,从而完全控制服务器。此漏洞遵循其他最近漏洞的主题,这些漏洞允许攻击者在设置后重新初始化应用程序或创建初始用户。请参阅我们最近针对 CVE-2024-0204 的文章作为示例。
Unfortunately, this vulnerability has not yet been assigned a CVE. Users of ConnectWise ScreenConnect should patch immediately to prevent attackers from leveraging this vulnerability.
遗憾的是,尚未为此漏洞分配 CVE。ConnectWise ScreenConnect 的用户应立即进行修补,以防止攻击者利用此漏洞。
NodeZero 节点零
Horizon3.ai clients and free-trial users alike can run a NodeZero operation to determine the exposure and exploitability of this issue.
Horizon3.ai 客户端和免费试用用户都可以运行 NodeZero 操作来确定此问题的暴露和可利用性。
Sign up for a free trial and quickly verify you’re not exploitable.
注册免费试用版并快速验证您不可利用。
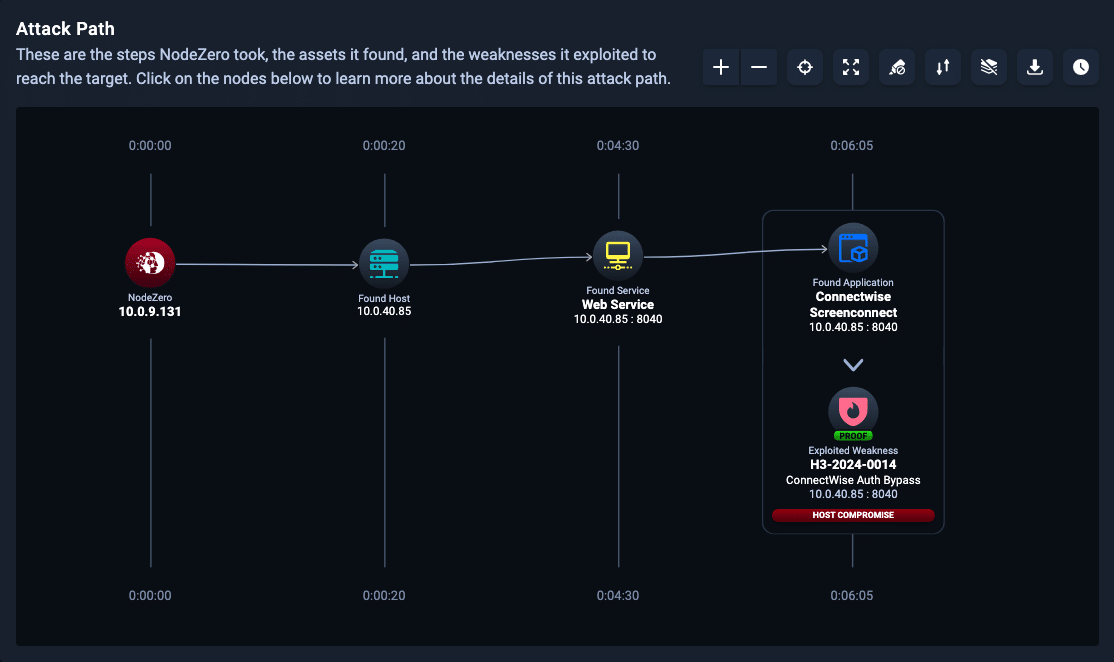
图5.NodeZero 攻击的利用路径
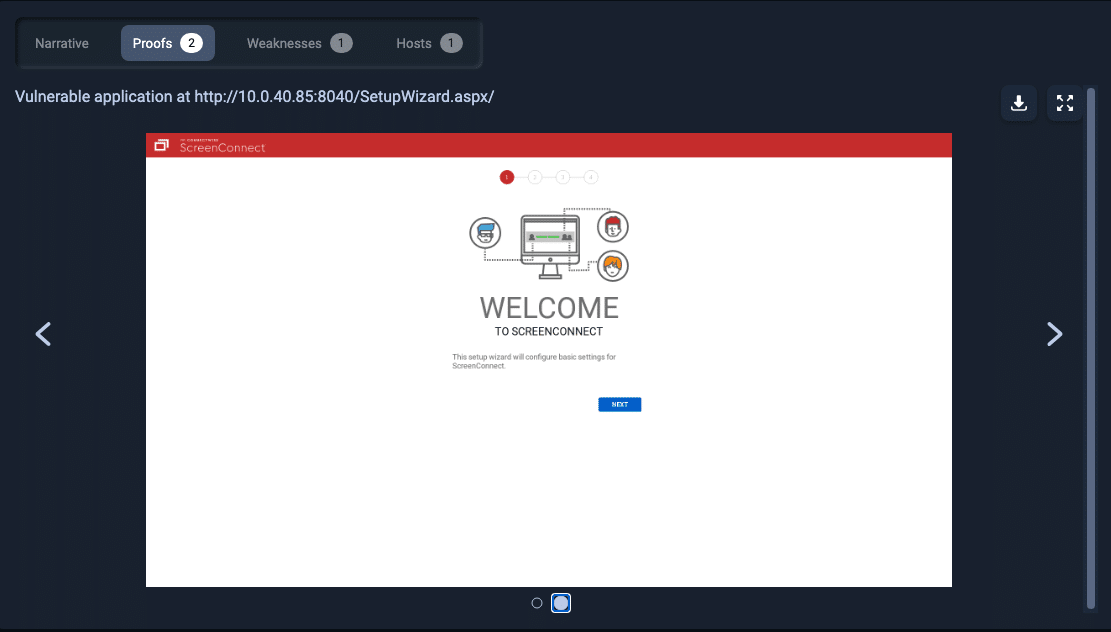
图6.访问SetupWizard.aspx页面的证明