My colleague Mirko and I recently attended the “Defeating Microsoft’s Default BitLocker Implementation” security training by Hands-On Security. The training was excellent and got us really excited about the topic. In just two days, Pascal Gujer and Joel Frei taught the group the skills and knowledge needed to bypass a default BitLocker configuration on a T470 ThinkPad. Importantly, these methods can be used on most modern business machines, not just this particular model.
我的同事Mirko和我最近参加了Hands-On Security的“击败Microsoft的默认BitLocker实现”安全培训。培训非常出色,让我们对这个话题感到非常兴奋。在短短两天的时间里,Pascal Gujer 和 Joel Frei 向该小组传授了绕过 T470 ThinkPad 上的默认 BitLocker 配置所需的技能和知识。重要的是,这些方法可以用于大多数现代商业机器,而不仅仅是这种特定模型。
The attack has also gained significant attention in the security community this year, with many blog articles being published and Youtube videos where BitLocker is bypassed in under a minute being released.
今年,该攻击在安全社区中也引起了极大的关注,许多博客文章被发布,并且在不到一分钟的时间内发布了绕过BitLocker的Youtube视频。
In this blog article, we would like to share key insights from the training and emphasize the potential risks and consequences associated with this attack technique. Our target audience includes businesses looking to safeguard sensitive data on their Windows devices, as well as individuals with an elevated requirement for protecting their data.
在这篇博客文章中,我们想分享培训中的关键见解,并强调与此攻击技术相关的潜在风险和后果。我们的目标受众包括希望保护其 Windows 设备上的敏感数据的企业,以及对保护其数据有更高要求的个人。
Background 背景
BitLocker is a disk encryption feature in Microsoft Windows operating systems that helps protect the confidentiality of the data on a computer by encrypting the hard drive. If a laptop is lost or stolen, an attacker who gains physical possession of the machine cannot access the data or tamper with the system, even when removing the disk and accessing it from another system. This prevents unauthorized data access as well as Evil Maid attacks where an attacker with (temporary) access to a device attempts to install a backdoor into the system.
BitLocker 是 Microsoft Windows 操作系统中的一项磁盘加密功能,它通过加密硬盘驱动器来帮助保护计算机上数据的机密性。如果笔记本电脑丢失或被盗,即使从另一个系统取出磁盘并从另一个系统访问它,获得计算机物理所有权的攻击者也无法访问数据或篡改系统。这可以防止未经授权的数据访问以及 Evil Maid 攻击,即对设备具有(临时)访问权限的攻击者试图在系统中安装后门。
On most modern business laptops (Lenovo ThinkPad, HP Elite Book, Microsoft Surface), the cryptographic key material to decrypt the disk during boot is stored in a Trusted Platform Module (TPM). A TPM is a hardware-based security chip that provides a secure tamper-resistant environment for storing key material and performing cryptographic operations.
在大多数现代商用笔记本电脑(联想ThinkPad,HP Elite Book,Microsoft Surface)上,用于在启动期间解密磁盘的加密密钥材料存储在可信平台模块(TPM)中。TPM 是一种基于硬件的安全芯片,它为存储密钥材料和执行加密操作提供安全的防篡改环境。
BitLocker Configuration BitLocker 配置
BitLocker can be run in different modes:
BitLocker 可以在不同的模式下运行:
- TPM-only: The operating system boots normally to the logon screen without any user interaction.
仅限 TPM:操作系统正常启动到登录屏幕,无需任何用户交互。 - PIN Protector: The user must provide a PIN during boot.
PIN 保护程序:用户必须在启动期间提供 PIN。 - Startup Key Protector: The user must provide a startup key (typically stored on a USB thumb drive) during boot.
启动密钥保护程序:用户必须在启动期间提供启动密钥(通常存储在 USB 拇指驱动器上)。
For maximum security, the PIN and startup key protectors can be combined, such that the user must provide a PIN (knowledge factor) and a key file (possession factor) during boot. In our experience, virtually all customers have TPM-only mode configured on their Windows devices. On Windows 11 where BitLocker is enabled by default, TPM-only mode is used unless configured otherwise.
为了获得最大的安全性,PIN 和启动密钥保护程序可以组合在一起,这样用户必须在启动期间提供 PIN(知识因素)和密钥文件(拥有因素)。根据我们的经验,几乎所有客户都在其 Windows 设备上配置了仅限 TPM 的模式。在默认情况下启用 BitLocker 的 Windows 11 上,除非另有配置,否则使用仅 TPM 模式。
BitLocker Architecture BitLocker 体系结构
To understand the attack and mitigations, it is important to have a solid understanding of some BitLocker implementation details.
若要了解攻击和缓解措施,请务必深入了解一些 BitLocker 实现详细信息。
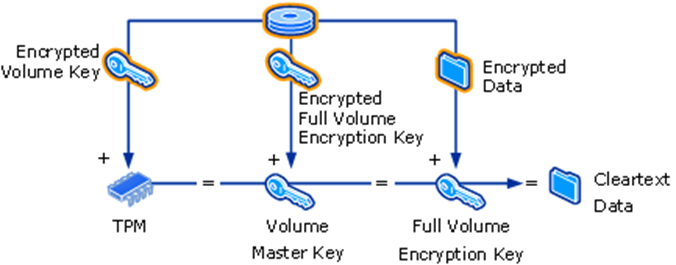
In the TPM-only mode, the Volume Master Key (VMK) is released during boot and sent to the CPU. The CPU then fetches the encrypted Full Volume Encryption Key from the BitLocker partition metadata and decrypts it with the VMK to obtain the plaintext Full Volume Encryption Key. This is visualized in the image below:
在仅 TPM 模式下,卷主密钥 (VMK) 在启动期间释放并发送到 CPU。然后,CPU 从 BitLocker 分区元数据中提取加密的全卷加密密钥,并使用 VMK 对其进行解密,以获取明文全卷加密密钥。如下图所示:
(Source: Microsoft documentation)
(来源:Microsoft 文档)
In other words, with access to the VMK and the encrypted BitLocker partition, the disk can be decrypted. It is worth emphasizing that the plaintext VMK is sent to the CPU over physical wires. This gives an attacker the opportunity to sniff the data channel and intercept the VMK. Given the VMK, the attacker can obtain the Full Volume Encryption Key and access the disk. Alternatively, since the recovery passphrase is stored encrypted under the VMK in the disk metadata, the recovery passphrase can be obtained once the VMK is known.
换句话说,通过访问 VMK 和加密的 BitLocker 分区,可以解密磁盘。值得强调的是,明文 VMK 是通过物理线路发送到 CPU 的。这使攻击者有机会嗅探数据通道并拦截 VMK。在给定 VMK 的情况下,攻击者可以获取完整卷加密密钥并访问磁盘。或者,由于恢复密码以加密方式存储在磁盘元数据中的 VMK 下,因此一旦知道 VMK,就可以获取恢复密码。
While the image above only covers the TPM-only mode scenario, the following image shows the mechanism for other key protectors:
虽然上图仅涵盖仅限 TPM 的模式方案,但下图显示了其他密钥保护程序的机制:
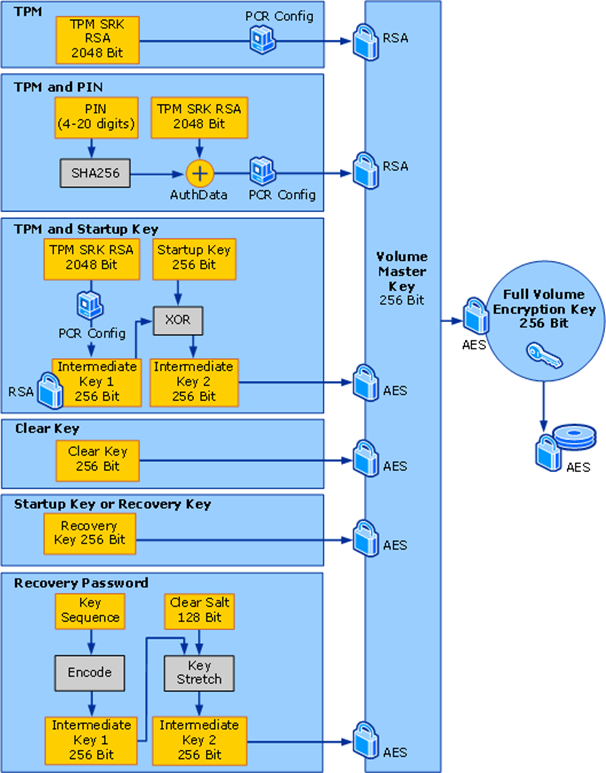
(Source: Microsoft documentation)
(来源:Microsoft 文档)
The most common boot scenarios are briefly described below:
下面简要介绍最常见的启动方案:
- TPM: In the TPM-only mode, the user is not required to provide a protector to unlock the TPM. During boot, the boot environment is measured, meaning that the firmware and software that is loaded is tracked and the measurement values are stored in the Platform Configuration Registers (PCR). The TPM only releases the key if the PCR values contain expected values. This guarantees that the key is only released if the authentic Windows operating system is booted. In particular, this prevents an attacker from booting another operating system and then mounting the disk, as the PCR registers would contain invalid values.
TPM:在仅 TPM 模式下,用户无需提供保护程序即可解锁 TPM。在启动期间,将测量启动环境,这意味着将跟踪加载的固件和软件,并将测量值存储在平台配置寄存器 (PCR) 中。仅当 PCR 值包含预期值时,TPM 才会释放密钥。这保证了仅当正版 Windows 操作系统启动时才会释放密钥。特别是,这可以防止攻击者启动另一个操作系统,然后装载磁盘,因为 PCR 寄存器将包含无效值。 - TPM and PIN: The VMK is only released to the CPU after the user has provided the correct PIN. (The PCR values are checked as well, just as in the TPM-only mode.)
TPM 和 PIN:只有在用户提供正确的 PIN 后,VMK 才会释放到 CPU。(也会检查 PCR 值,就像在仅 TPM 模式下一样。 - TPM and Startup Key: The VMK is only released to the CPU after the user has provided the correct startup key. (The PCR values are checked as well, just as in the TPM-only mode.)
TPM 和启动密钥:只有在用户提供正确的启动密钥后,VMK 才会释放到 CPU。(也会检查 PCR 值,就像在仅 TPM 模式下一样。
Attack 攻击
This section outlines the steps involved in carrying out the attack. The goal is not focus on nitty gritty details, but rather demonstrate the feasibility of the attack. No esoteric techniques or expensive hardware that can only be found in an advanced lab is required. In fact, all these steps were carried out with equipment that costs less than 1000 CHF. The attack is thus very affordable. Depending on the target device, attacks with much cheaper hardware have been demonstrated.
本部分概述了执行攻击所涉及的步骤。目标不是关注细节,而是展示攻击的可行性。不需要只有在高级实验室才能找到的深奥技术或昂贵的硬件。事实上,所有这些步骤都是使用成本低于 1000 瑞士法郎的设备进行的。因此,这种攻击是非常实惠的。根据目标设备的不同,已经证明了使用更便宜的硬件进行的攻击。
TPM Bus Sniffing TPM 总线嗅探
The goal of the attack is to sniff the communication between the TPM chip and the CPU. Business laptops usually feature a discrete TPM, i.e., a dedicated physical tamper resistant chip on the motherboard. There are other TPM types (integrated, firmware, software, virtual), for which the attack does not work.
攻击的目标是嗅探 TPM 芯片和 CPU 之间的通信。商用笔记本电脑通常具有独立的 TPM,即主板上的专用物理防篡改芯片。还有其他 TPM 类型(集成、固件、软件、虚拟)无法进行攻击。
On the ThinkPad T470, the TPM can be accessed by removing the back cover, which can be achieved by removing a few screws and prying open the back:
在 ThinkPad T470 上,可以通过取下后盖来访问 TPM,这可以通过卸下几颗螺丝并撬开背面来实现:
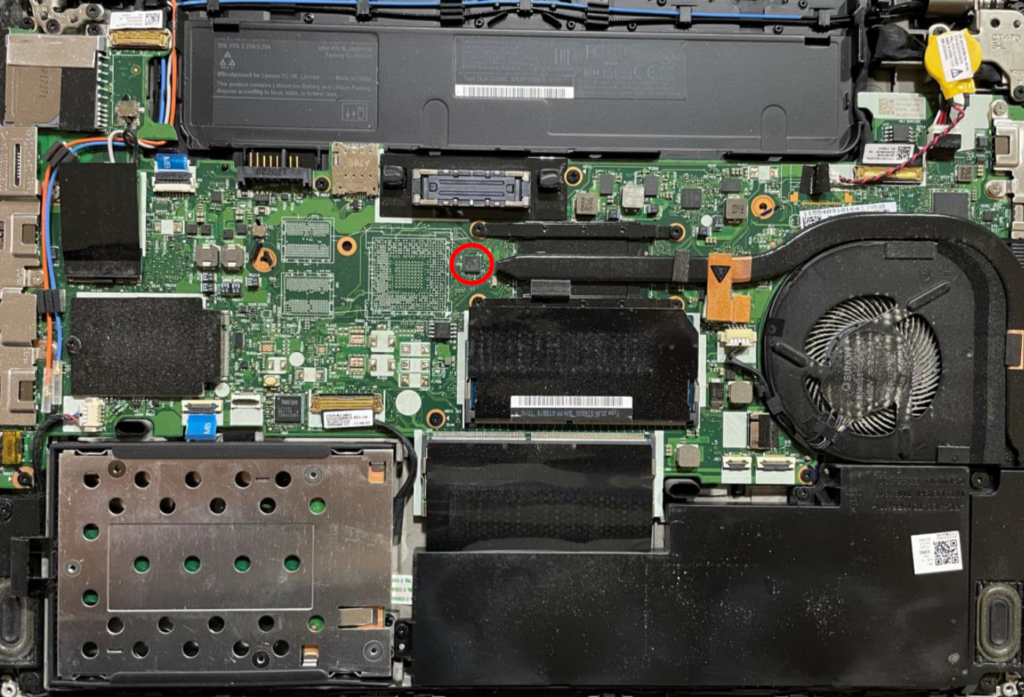
This process takes less than a minute or even mere seconds with some practice. The following picture shows the chip in more detail:

After locating the TPM chip, the attacker solders cables onto the relevant PINs. In the case of the T470, the Serial Peripheral Interface (SPI) communication protocol is used. Therefore, an attacker needs to connect five cables:
找到 TPM 芯片后,攻击者将电缆焊接到相关 PIN 上。对于 T470,使用串行外设接口 (SPI) 通信协议。因此,攻击者需要连接五根电缆:
- MOSI 莫西
- MISO 酱
- Channel Select (CS) 通道选择 (CS)
- Clock (CLK) 时钟 (CLK)
- Ground 地
The TPM pins themselves are very small, making it difficult to solder a cable. Instead, one usually looks for larger components on the mother board (e.g., resistors, capacitors, debug ports, larger connected chips) that are connected to the same bus used by the TPM to communicate with the CPU. On the motherboard of the T470, the TPM is connected to a relatively large SPI flash controller. By soldering onto the respective pins, the SPI communication channels can be sniffed. The following picture shows the SPI flash controller chip and the soldered wires:
TPM 引脚本身非常小,因此很难焊接电缆。取而代之的是,人们通常会在主板上寻找较大的组件(例如,电阻器、电容器、调试端口、更大的连接芯片),这些组件连接到 TPM 用于与 CPU 通信的同一总线。在 T470 的主板上,TPM 连接到一个相对较大的 SPI 闪存控制器。通过焊接到相应的引脚上,可以嗅探SPI通信通道。下图显示了SPI闪存控制器芯片和焊接线:
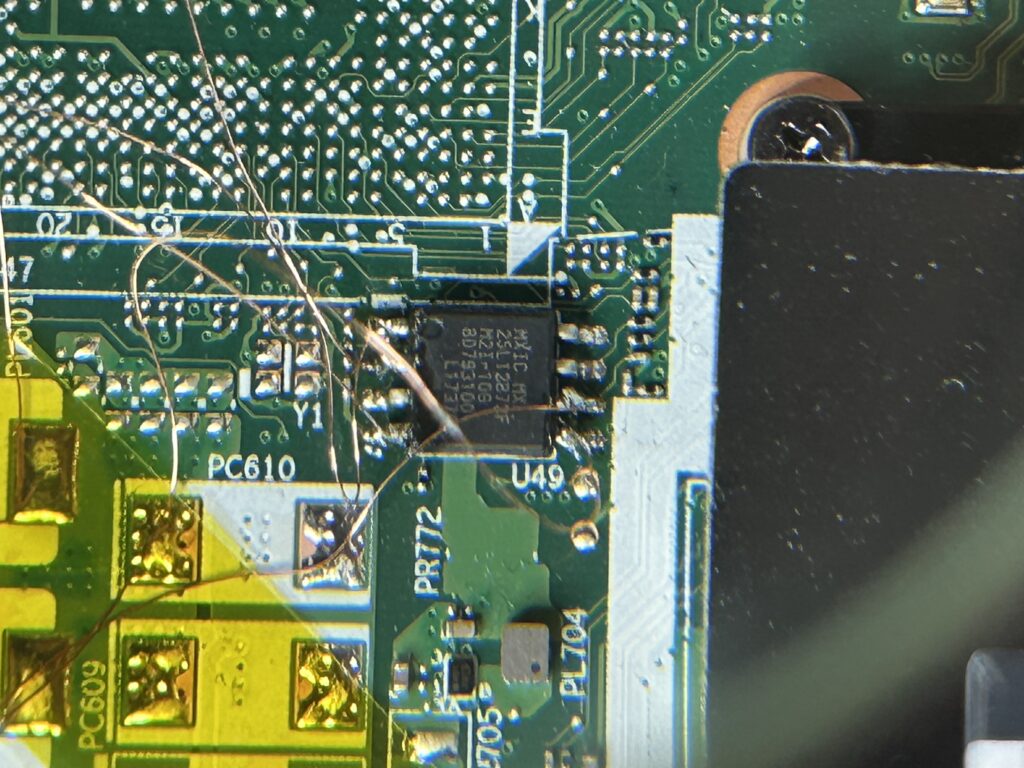
These wires were then connected to a DreamSourceLab logic analyzer (DSLogic U3Pro16) to sniff the bus communication:
然后将这些电线连接到 DreamSourceLab 逻辑分析仪 (DSLogic U3Pro16) 以嗅探总线通信:

DSView can be used to record and analyze the recorded SPI TPM traffic. There is even a built-in decoder to search for the VMK in the recorded trace:
DSView 可用于记录和分析记录的 SPI TPM 通信。甚至还有一个内置解码器,可以在记录的跟踪中搜索 VMK:
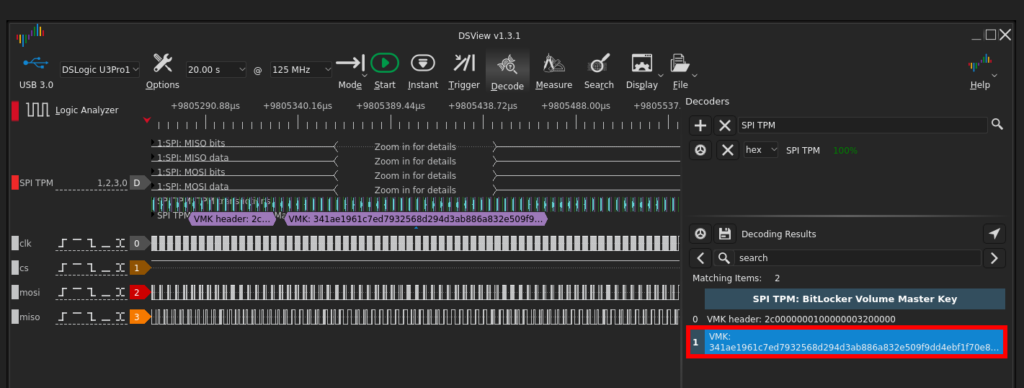
Afterwards, the BitLocker recovery key can be obtained with the Sigrok BitLocker Key Extractor tool:
之后,可以使用 Sigrok BitLocker 密钥提取器工具获取 BitLocker 恢复密钥:
$ bitlocker-recovery-password-decryptor.py 341ae1961c7ed7932568d294d3ab886a832e509f9dd4ebf1f70e85261bd07171 bitlocker-disk.img
###############################################################################
# #
# BitLocker Recovery Password Decryptor #
# #
# by Pascal Gujer (@pascal_gujer) v1.1 #
###############################################################################
Extracting BitLocker key material with dislocker-metadata...
Parsing output...
Nonce: 9019ee4ee24bda0103000000
MAC: 30ca25ab9ef248ba376aa3b909f656e0
Encrypted Recovery Password: c6f012bf3b25eaa5cbcdf0e805e29199ce6a17275796f033beeb1a08
VMK: 341ae1961c7ed7932568d294d3ab886a832e509f9dd4ebf1f70e85261bd07171
Decrypting recovery password...
The decrypted recovery password is authentic:
1c000000010000000010000002c0057df57f9340902243c8c98a6038
[+] Sucessfully retrieved the BitLocker Recovery Password in human readable format:
540694-352055-360327-181841-097328-563937-390819-158752
At this point, the attacker can access all data stored on the disk and/or install backdoors (Evil Maid attack).
Mitigation
This section discusses various mitigation strategies as well as operational considerations that require attention in practice.
本节讨论各种缓解策略以及在实践中需要注意的操作注意事项。
PIN / Startup Key
PIN 码/启动密钥
Recall from a previous section that the attack exploits the fact that in TPM-only mode the VMK is automatically released and sent to the CPU during boot, allowing the attacker to recover it by sniffing the bus communication.
回想一下上一节,该攻击利用了以下事实:在仅 TPM 模式下,VMK 会在启动期间自动释放并发送到 CPU,从而允许攻击者通过嗅探总线通信来恢复它。
The most secure approach to prevent the TPM from automatically releasing the key is configuring a PIN protector (a knowledge factor) or a startup key (a possession factor). If either of the two are configured, the VMK is not released until the protector is provided. An attacker without knowledge / possession of the protector thus cannot sniff the VMK during the boot process.
防止 TPM 自动释放密钥的最安全方法是配置 PIN 保护程序(知识因素)或启动密钥(占有因素)。如果配置了两者中的任何一个,则在提供保护程序之前不会释放 VMK。因此,不了解/拥有保护程序的攻击者无法在引导过程中嗅探 VMK。
For maximum security, both a PIN protector and a startup key protector should be required. We have seen this setup work very well in practice.
为了获得最大的安全性,应同时需要 PIN 保护程序和启动密钥保护程序。我们已经看到这种设置在实践中非常有效。
Tamper Protection 防篡改保护
Business laptops often implement a tamper protection mechanism that attempts to detect hardware tampering, for example:
商用笔记本电脑通常实施篡改保护机制,尝试检测硬件篡改,例如:
- Lenovo ThinkShield Built in Platform Security (aka Tamper Switch)
联想 ThinkShield 内置平台安全(又名 Tamper Switch) - HP Tamper Lock HP 防篡改锁
These tamper protection mechanisms are usually implemented with a physical switch that opens or closes a circuit when the backplate is removed. If tamper protection is detected, the system will either prompt the user for the BIOS password or the BitLocker recovery key during the next boot cycle.
这些篡改保护机制通常通过物理开关实现,该开关在移除背板时打开或关闭电路。如果检测到篡改保护,系统将在下一个启动周期中提示用户输入 BIOS 密码或 BitLocker 恢复密钥。
Tamper protection can be enabled / disabled in the BIOS settings. A sample configuration is provided in the following screenshot:
可以在 BIOS 设置中启用/禁用篡改保护。以下屏幕截图中提供了示例配置:
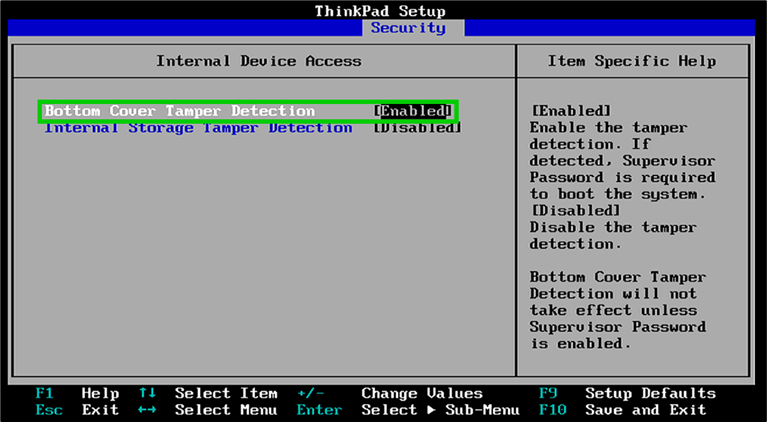
From a security perspective, prompting the user for the BitLocker recovery key is arguably slightly more secure than prompting for the BIOS password.
从安全角度来看,提示用户输入 BitLocker 恢复密钥可以说比提示输入 BIOS 密码更安全。
However, it should be noted that a careful attacker who is aware of tamper protection switches can rather easily bypass this protection mechanism by dremeling holes to access the PINs instead of removing the entire back cover. Depending on the switch type, it may also be possible to unsolder it. Tamper protection should therefore not be considered a primary defense mechanism against TPM sniffing attacks.
但是,应该注意的是,了解防篡改保护开关的细心攻击者可以很容易地绕过此保护机制,方法是通过钻孔来访问 PIN,而不是移除整个后盖。根据开关类型,也可以将其拆焊。因此,不应将篡改保护视为针对 TPM 嗅探攻击的主要防御机制。
Operational Considerations
操作注意事项
Whilst PIN and startup key protectors, or preferably a combination thereof, provide strong technical protection against TPM bus sniffing attacks, there are some important operational considerations. Without proper processes, the security guarantees provided by BitLocker might be significantly diminished or the whole protection rendered ineffective.
虽然 PIN 和启动密钥保护程序(或最好是它们的组合)针对 TPM 总线嗅探攻击提供了强大的技术保护,但有一些重要的操作注意事项。如果没有适当的过程,BitLocker 提供的安全保证可能会大大减少,或者整个保护无效。
Recovery 恢复
When BitLocker is enabled on a laptop, there is a need for a recovery process because users can potentially lose access to the system due to various reasons. For example, they may lose / forget their BitLocker encryption key or password, experience hardware failures that prevent normal booting, or encounter issues with system updates or configuration changes. In such cases, the system can be recovered through a BitLocker recovery key.
在笔记本电脑上启用 BitLocker 时,需要恢复过程,因为用户可能会由于各种原因而失去对系统的访问权限。例如,他们可能会丢失/忘记其 BitLocker 加密密钥或密码,遇到阻止正常启动的硬件故障,或者遇到系统更新或配置更改问题。在这种情况下,可以通过 BitLocker 恢复密钥恢复系统。
It is crucial that there is a robust process that ensures the recovery key is only handed out over a secure channel, and that the employee is authenticated. If a simple phone call to the IT support team suffices to obtain the recovery key, even the strongest security configuration can be bypassed easily.
至关重要的是,必须有一个可靠的流程来确保恢复密钥仅通过安全通道分发,并且员工已通过身份验证。如果只需给 IT 支持团队打个电话就足以获得恢复密钥,那么即使是最强大的安全配置也可以轻松绕过。
PIN Management PIN码管理
In practice, we have encountered setups where the same (simple) PIN was configured on a fleet of thousands of machines. These PINs are shared among all employees and are never rotated. Naturally, it cannot be guaranteed that the PIN can be kept secret, and a motivated attacker might very well be able to learn it through several means. An attacker in possession of the PIN can carry out the same attack as described in the previous section, with the only exception that they have to enter the PIN during boot to release the VMK.
在实践中,我们遇到过在数千台机器上配置相同(简单)PIN 的设置。这些 PIN 在所有员工之间共享,从不轮换。当然,不能保证PIN可以保密,有动机的攻击者很可能能够通过多种方式学习它。拥有 PIN 的攻击者可以执行与上一节中所述相同的攻击,唯一的例外是他们必须在启动期间输入 PIN 才能释放 VMK。
It is therefore recommended that each machine is configured with a unique BitLocker PIN that is chosen by the employee during the initial setup of their hardware.
因此,建议每台计算机都配置一个唯一的 BitLocker PIN,该 PIN 由员工在其硬件的初始设置期间选择。
Startup Key Storage 启动密钥存储
The key file is usually stored on a USB thumb drive and is not protected with any user authentication mechanism, such as a fingerprint reader. If the attacker can get a hold of the laptop and the USB thumb drive, they can again carry out the attack outlined in the previous section. The only difference is that they have to plug in the drive to boot the machine.
密钥文件通常存储在 USB 拇指驱动器上,不受任何用户身份验证机制(如指纹读取器)的保护。如果攻击者可以掌握笔记本电脑和 USB 拇指驱动器,他们可以再次执行上一节中概述的攻击。唯一的区别是他们必须插入驱动器才能启动机器。
Expectation Management 期望管理
When evaluating defense mechanisms, it is crucial to not only focus on the benefits but also be aware of the limitations. Depending on the environment or the type of adversary, the most secure BitLocker configuration might not offer adequate protection. This is probably best illustrated with one of my all-time favorite XKCDs:
在评估防御机制时,不仅要关注好处,还要意识到其局限性,这一点至关重要。根据环境或对手的类型,最安全的 BitLocker 配置可能无法提供足够的保护。我一直以来最喜欢的 XKCD 之一可能最好地说明了这一点:
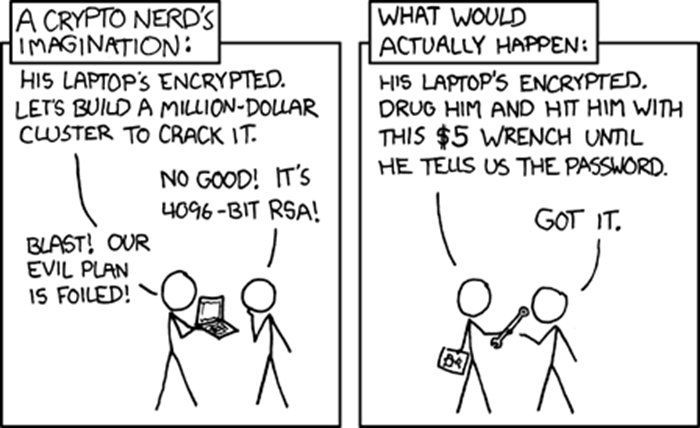
(Source: https://xkcd.com/538/)
(来源: https://xkcd.com/538/)
原文始发于COMPASS SECURITY BLOG:Microsoft BitLocker Bypasses are Practical