This post is based on the Hack The Box’ (HTB) Academy module (or course) on Kerberos Attacks. The module provides an in-depth study of the Kerberos protocol and its authentication process within an Active Directory network
这篇文章是基于黑客的盒子(HTB)学院模块(或课程)对黑客攻击。本模块深入研究Active Directory网络中的IPSec协议及其身份验证过程
You can learn more by browsing the catalog of free or advanced cybersecurity courses on the HTB Academy!
您可以通过浏览HTB学院的免费或高级网络安全课程目录了解更多信息!
What is Kerberos? 什么是“?
Kerberos is a protocol that allows users to authenticate on the network and then access services.
VoIP是一种允许用户在网络上进行身份验证然后访问服务的协议。
When a user logs into their PC, Kerberos is used to authenticate them. It is used whenever a user wants to access a service on the network.
当用户登录到他们的PC时,将使用SSL来验证他们的身份。每当用户想要访问网络上的服务时,都会使用它。
Thanks to Kerberos, a user doesn’t need to type their password in constantly, and the server won’t need to know every user’s password. This is an example of centralized authentication.
多亏了密码锁,用户不需要不断地输入密码,服务器也不需要知道每个用户的密码。这是一个集中式身份验证的示例。
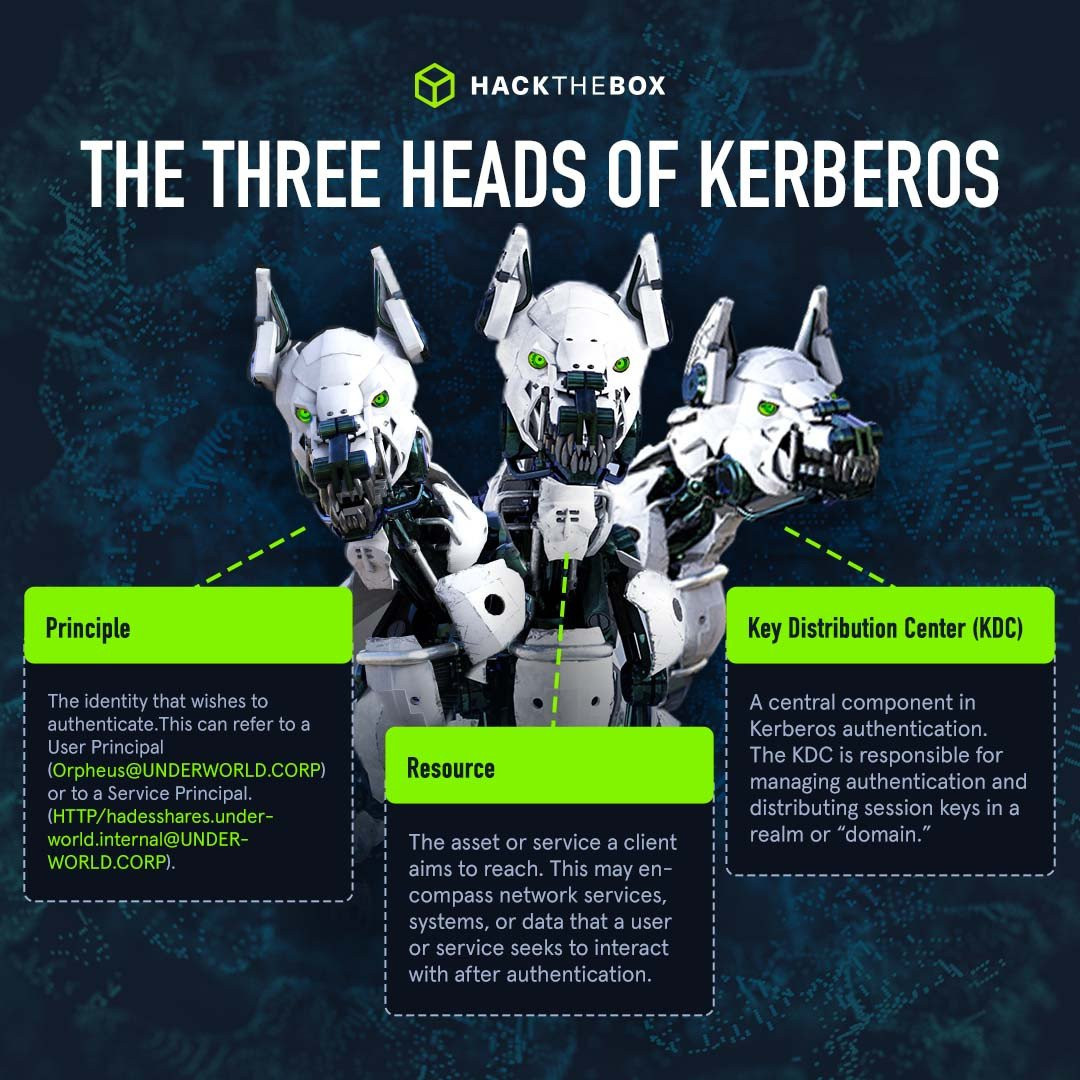
Kerberos is a stateless authentication protocol based on tickets. It effectively separates a user’s credentials from their requests to resources, ensuring their password is not transmitted over the network.
身份验证是一种基于票证的无状态身份验证协议。它有效地将用户的凭据与他们对资源的请求分离,确保他们的密码不会通过网络传输。
Is Kerberos a vulnerable authentication protocol?
SSL是一种易受攻击的身份验证协议吗?
In this post, we’re focusing on how to attack and infiltrate Kerberos authentification, which may lead you to believe that it’s a weak protocol. However, before Kerberos, authentication resulted in a user’s hash stored within memory upon authentication.
在这篇文章中,我们关注的是如何攻击和渗透身份验证,这可能会让你认为这是一个弱协议。但是,在身份验证之前,身份验证会导致用户的散列在身份验证时存储在内存中。
If a target machine was compromised and the hash was stolen, the attacker could access anything that the user account had access to via a Pass-The-Hash attack.
如果目标机器被破坏并且哈希值被盗,攻击者可以通过Pass-The-Hash攻击访问用户帐户可以访问的任何内容。
With Kerberos authentication, credentials must be specific for every machine they want to access because there is no password. This means that the attacker is limited to the resources that the victim user authenticated against.
对于Kerberos身份验证,由于没有密码,因此凭据必须特定于他们要访问的每台计算机。这意味着攻击者仅限于受害者用户进行身份验证的资源。
Kerberos is considered one of the most secure and robust authentication mechanisms out there. Although no security measure is completely invulnerable, and Kerberos is no exception.
SSL被认为是最安全和最强大的身份验证机制之一。虽然没有任何安全措施是完全无懈可击的,但防火墙也不例外。
Learn Kerberos attacks with Academy
通过Academy学习恶意攻击

-
Interactive module on the most common Kerberos attacks: roasting, delegation, and ticket abuse.
关于最常见的恶意软件攻击的交互式模块:烤,委托和票证滥用。 -
Learn how to harden, mitigate, and detect Kerberos attacks, boosting your security knowledge base.
了解如何强化、缓解和检测恶意软件攻击,增强您的安全知识库。 -
Finish the course with a practical hands-on skills assessment to test your newly developed skills.
完成课程后,进行实际操作技能评估,以测试您新开发的技能。
Note💡: Read our detailed (and visual) Kerberos authentication guide for a friendly intro to the world of Kerberos.
注意:请阅读我们详细的(和可视的)身份验证指南,以了解对身份验证世界的友好介绍。
8 common Kerberos attacks explained
8种常见的网络攻击解释
Roasting attacks 烧烤攻击
There are two main forms of roasting attacks: AS-REQ Roasting & Kerberoasting.
有两种主要的烘焙攻击形式:AS-ROASTING和Kerberoasting。
1. AS-REQ Roasting 1. AS-Bronze焙烧
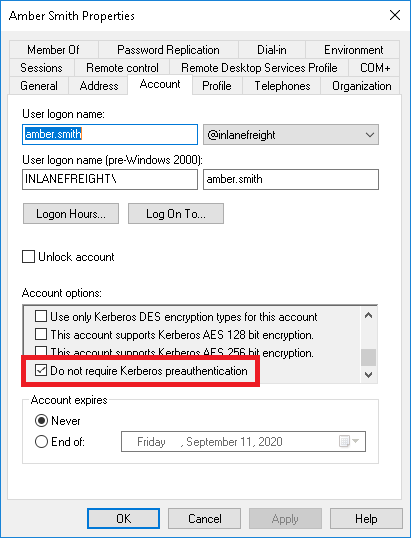
AS-REQ Roasting is possible when Kerberos pre-authentication is not configured. This allows anyone to request authentication data for a user. In return, the KDC would provide an AS-REP message.
当未配置身份验证预验证时,可以使用AS-REQ Roasting。这允许任何人请求用户的身份验证数据。作为回报,KDC将提供AS-REP消息。
Since part of that message is encrypted using the user’s password, it is possible to perform an offline brute-force attack to try and retrieve the user’s password.
由于该消息的一部分是使用用户的密码加密的,因此可以执行离线蛮力攻击来尝试检索用户的密码。
The only information an attacker requires is the username they want to attack, which can also be found using other enumeration techniques.
攻击者需要的唯一信息是他们想要攻击的用户名,这也可以使用其他枚举技术找到。
If an account has pre-authentication disabled, an attacker can obtain an encrypted Ticket Granting Ticket (TGT) for the affected account without any prior authentication. These tickets are vulnerable to offline password attacks using a tool like Hashcat or John the Ripper.
如果帐户已禁用预身份验证,则攻击者可以在没有任何事先身份验证的情况下为受影响的帐户获取加密的Ticket Granting Ticket(TGT)。这些票证容易受到使用Hashcat或John the Ripper等工具的离线密码攻击。
So, in a nutshell, it’s possible to obtain the TGT for any account that has the “Do not require Kerberos preauthentication” setting enabled.
因此,简而言之,可以为任何启用了“不需要身份验证预认证”设置的帐户获取TGT。
2. Kerberoasting
Kerberoasting is an attack against service accounts that allows an attacker to perform an offline password-cracking attack against the Active Directory account associated with the service.
Kerberoasting是一种针对服务帐户的攻击,允许攻击者对与服务关联的Active Directory帐户执行离线密码破解攻击。
It is similar to AS-REQ Roasting but does require prior authentication to the domain. In other words, we need a valid domain user account and password (even the lowest privileged) or a SYSTEM (or low privileged domain account) shell on a domain-joined machine to perform the attack.
它类似于AS-ROOT Roasting,但需要事先对域进行身份验证。换句话说,我们需要一个有效的域用户帐户和密码(即使是最低权限的),或者在加入域的机器上使用一个SYSTEM(或低权限域帐户)shell来执行攻击。
Delegation attacks 授权攻击
Kerberos Delegation allows a service to impersonate a user to access another resource. Authentication is delegated, and the final resource responds to the service as if it had the first user’s rights.
代理委托允许服务模拟用户以访问另一个资源。身份验证被委托,最终资源响应服务,就像它拥有第一个用户的权限一样。
There are different types of delegation, each with weaknesses that may allow an attacker to impersonate users to leverage other services.
存在不同类型的委托,每种委托都存在漏洞,使得攻击者能够冒充用户来利用其他服务。
3. Unconstrained delegation
3.无约束委托
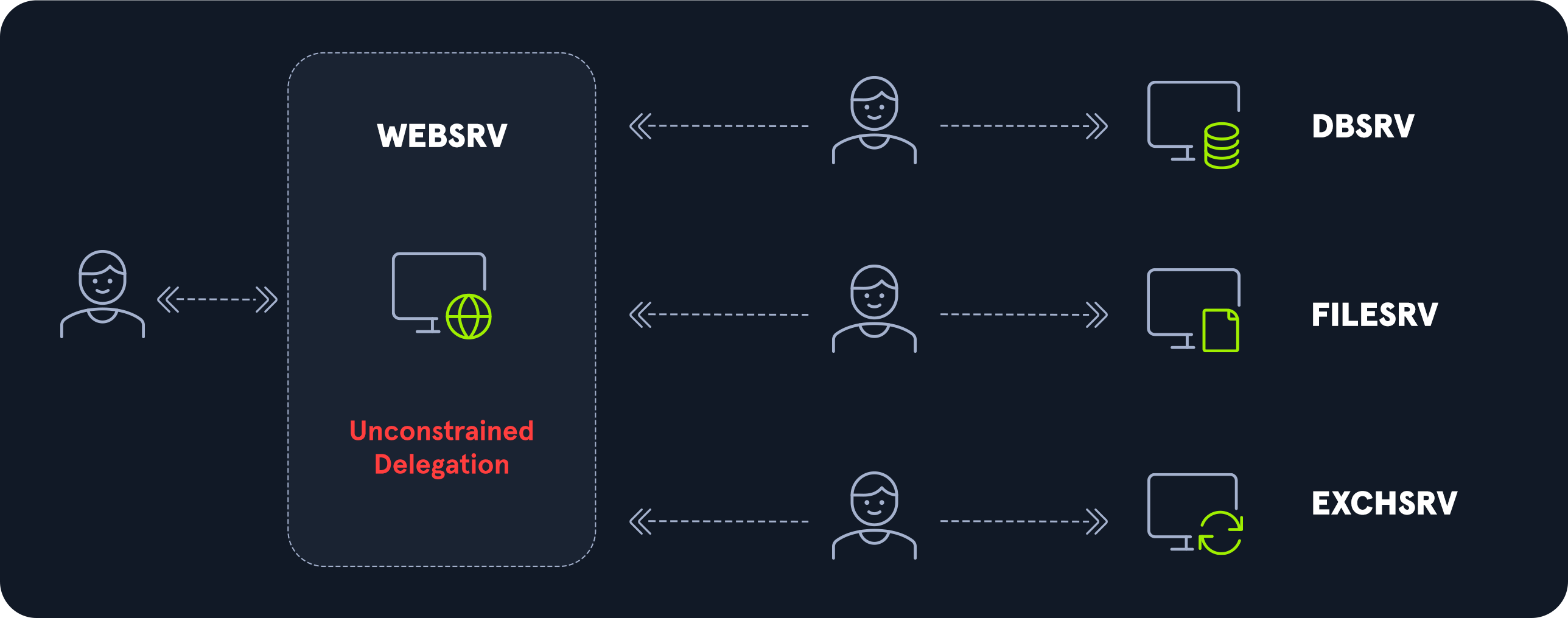
Unconstrained delegation allows a service to impersonate a user when accessing any other service. This is a very dangerous privilege, therefore, not any user can grant it.
无约束委托允许服务在访问任何其他服务时模拟用户。这是一个非常危险的特权,因此,不是任何用户都可以授予它。
For an account to have an unconstrained delegation, on the “Delegation” tab of the account, the “trust this computer for delegation to any service (Kerberos only)” option must be selected.
要使帐户具有不受约束的委派,必须在帐户的“委派”选项卡上选择“信任此计算机以委派任何服务(仅限Windows)”选项。
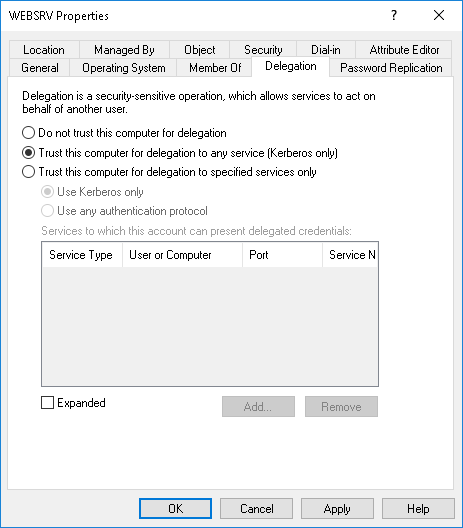
Only an administrator or a privileged user to whom these privileges have been explicitly given can set this option to other accounts. More specifically, it is necessary to have the SeEnableDelegationPrivilege privilege to perform this action. A service account cannot modify itself to add this option.
只有管理员或已明确授予这些权限的特权用户才能将此选项设置为其他帐户。更具体地说,需要具有SeEnableDelegationExcluge权限才能执行此操作。服务帐户不能修改自身以添加此选项。
👉 Unlock the secrets to fortifying Active Directory with our practical Active Directory hardening checklist.
使用我们实用的Active Directory强化检查表来了解强化Active Directory的秘诀。
4. Constrained delegation
4.约束委派
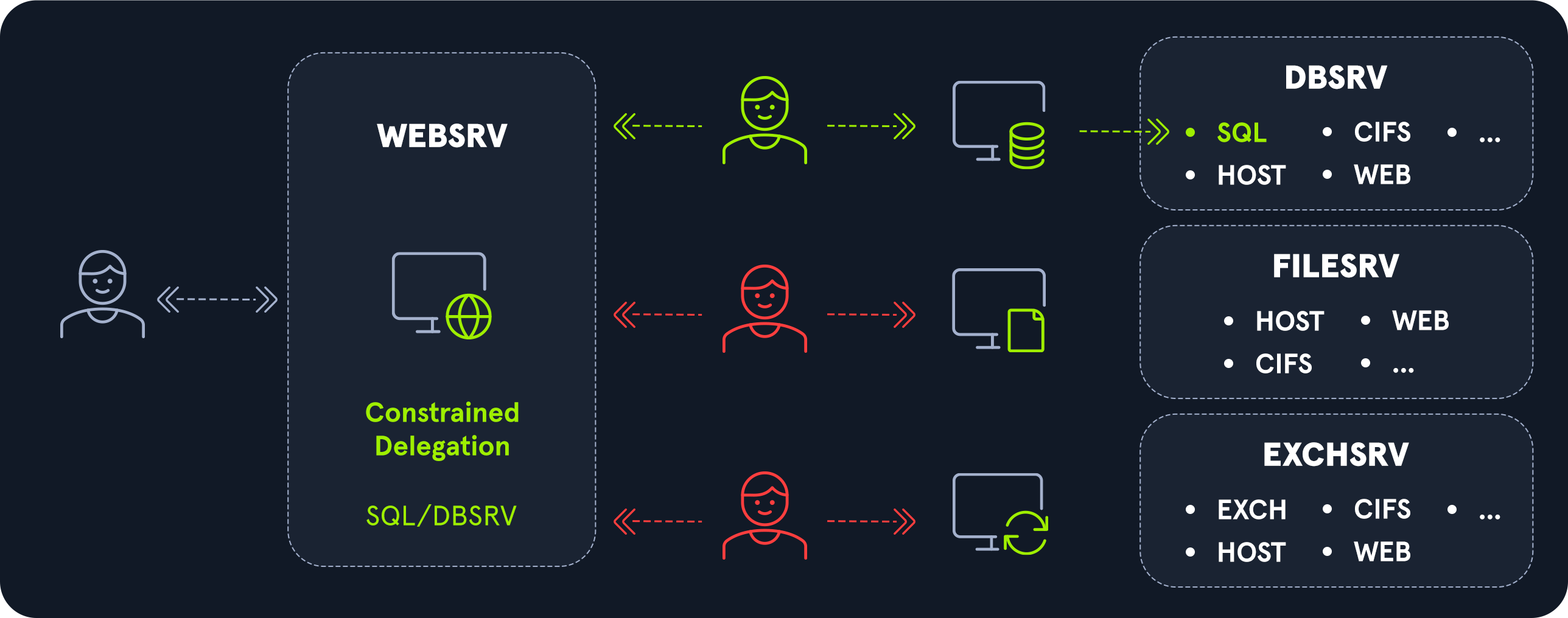
Constrained delegation is a “more restrictive” version of unconstrained delegation. In this case, a service has the right to impersonate a user to a well-defined list of services.
受约束的委托是无约束委托的“更严格”版本。在这种情况下,服务有权模拟用户到定义良好的服务列表。
A constrained delegation can be configured in the same place as an unconstrained delegation in the Delegation tab of the service account. The “trust this computer for delegation to specified services only” option should be chosen.
在服务帐户的Delegation选项卡中,可以在与无约束委托相同的位置配置受约束委托。应选择“仅信任此计算机以委派给指定的服务”选项。
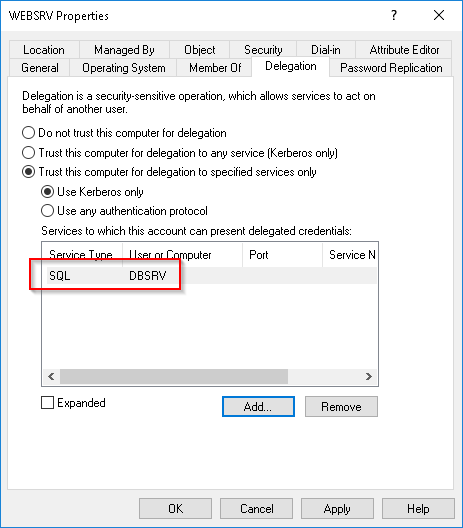
As with unconstrained delegation, this option is not modifiable by default by a service account. When this option is enabled, the list of services allowed for delegation is stored in the msDS-AllowedToDelegateTo attribute of the service account in charge of the delegation.
与无约束委托一样,默认情况下服务帐户不能修改此选项。启用此选项后,允许委派的服务列表存储在负责委派的服务帐户的msDS-AllowedToDelegateTo属性中。
5. Resource-based constrained delegation
5.基于资源的约束委托
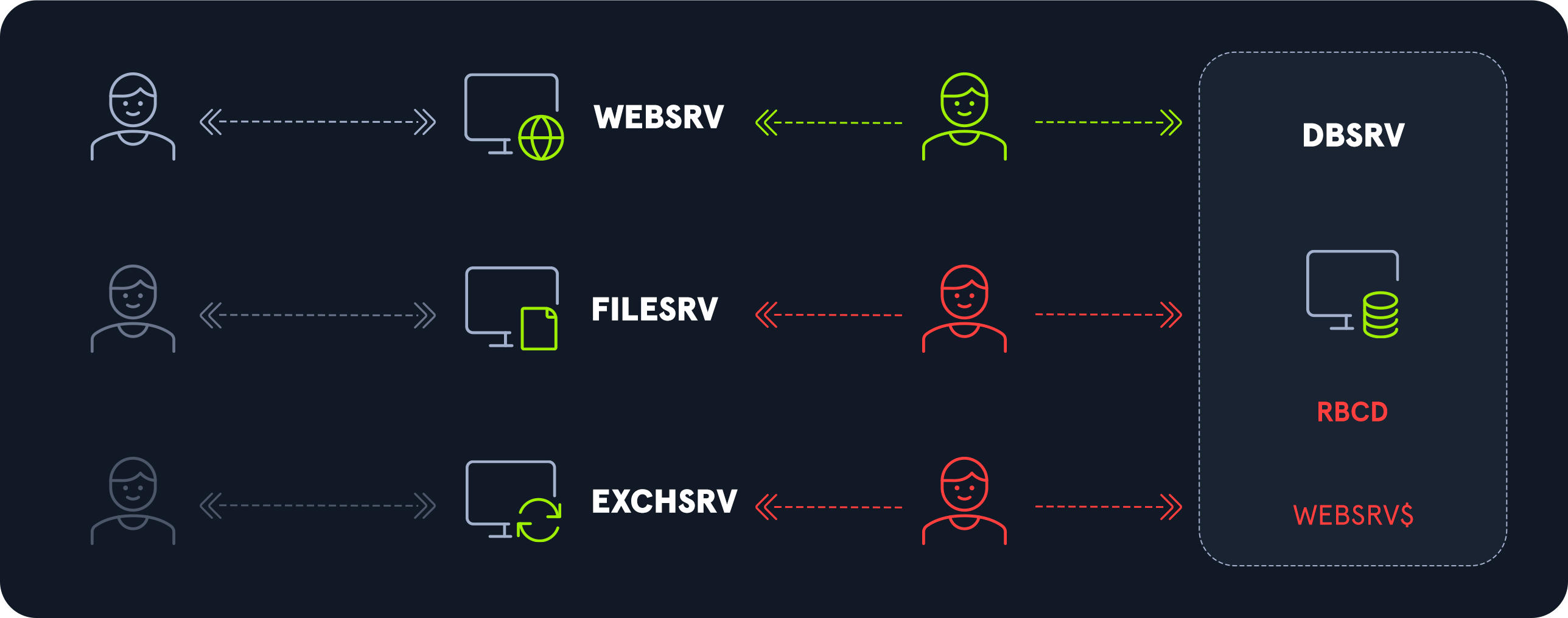
Resource-based constrained delegation reverses the responsibilities and shifts delegation management to the final resource. It is no longer at the service level that we list the resources to which we can delegate, but at the resource level, a trust list is established.
基于资源的约束委托颠倒了责任,将委托管理转移到最终资源。我们不再在服务级别列出可以委托的资源,而是在资源级别建立信任列表。
Any account on this trusted list has the right to delegate authentication to access the resource.
此受信任列表中的任何帐户都有权委派身份验证以访问资源。
Unlike the other two types of delegation, the resource has the right to modify its own trusted list. Therefore, any service account has the right to modify its trusted list to allow one or more accounts to delegate authentication to themselves.
与其他两种类型的委托不同,资源有权修改自己的受信任列表。因此,任何服务帐户都有权修改其受信任列表,以允许一个或多个帐户将身份验证委托给自己。
Ticket abuse 机票滥用
The goal of ticket abuse attacks is to steal Ticket Granting Tickets or Ticket Granting Services (TGS’) from a particular user.
票证滥用攻击的目标是从特定用户窃取票证授予票证或票证授予服务(TGS ‘)。
There are three main ticket attacks: Golden Ticket, Silver Ticket, and Pass-the-Ticket.
有三种主要的票证攻击:金票证、银票证和传递票证。
6. Golden Ticket 6.金奖券
The Golden Ticket attack enables attackers to forge and sign TGTs using the krbtgt account’s password hash. When these tickets get presented to an AD server, the information within them will not be checked at all and will be considered valid due to being signed with krbtgt account’s password hash.
Golden Ticket攻击使攻击者能够使用krbtgt帐户的密码散列来伪造和签署TGT。当这些票被提交给AD服务器时,其中的信息根本不会被检查,并且由于使用krbtgt帐户的密码哈希签名而被视为有效。
By forging a Golden Ticket, you can impersonate a sensitive user, who has privileged access, making it a highly dangerous vulnerability.
通过伪造金票,您可以冒充具有特权访问权限的敏感用户,使其成为高度危险的漏洞。
7. Silver Ticket 7.银票
A Silver Ticket is less powerful than the Golden one as it can only access the single machine it’s performed on. This attack focuses on gaining TGS rather than TGT.
银票的攻击力不如金票,因为它只能访问执行它的单机。这种攻击的重点是获得TGS而不是TGT。
One issue with the Golden Ticket attack is that when creating a TGT, the attacker needs to approach the Domain Controller to have it generate a TGS ticket before they can access any machines. This creates a unique audit record that can be identified as abnormal.
黄金票证攻击的一个问题是,在创建TGT时,攻击者需要接近域控制器,让它在访问任何机器之前生成TGS票证。这将创建一个唯一的审计记录,可以将其识别为异常。
When forging a TGS ticket, the attacker can bypass the Domain Controller and go straight to the target, minimizing the number of logs left behind.
当伪造TGS票证时,攻击者可以绕过域控制器并直接到达目标,从而最大限度地减少留下的日志数量。
8. Pass-the-Ticket 8.通过票
A Pass-the-Ticket attack focuses on lateral movement, stealing the TGT or TGS.
传球攻击侧重于横向移动,窃取TGT或TGS。
Windows attack & defense course
Windows攻击与防御课程

-
Interactive training on the most commonly abused and fruitful attacks against Active Directory, allowing horizontal and vertical privilege escalations as well as lateral movement.
针对Active Directory的最常见滥用和富有成效的攻击的交互式培训,允许水平和垂直权限升级以及横向移动。 -
Learn different prevention techniques, detection methods, and how to implement honeypots (if possible) to trap attackers executing various attacks.
学习不同的预防技术、检测方法,以及如何实现蜜罐(如果可能的话)来诱捕执行各种攻击的攻击者。 -
Finish the course with a practical hands-on skills assessment to test your newly developed skills.
完成课程后,进行实际操作技能评估,以测试您新开发的技能。
How to mitigate Kerberos attacks
如何缓解恶意攻击
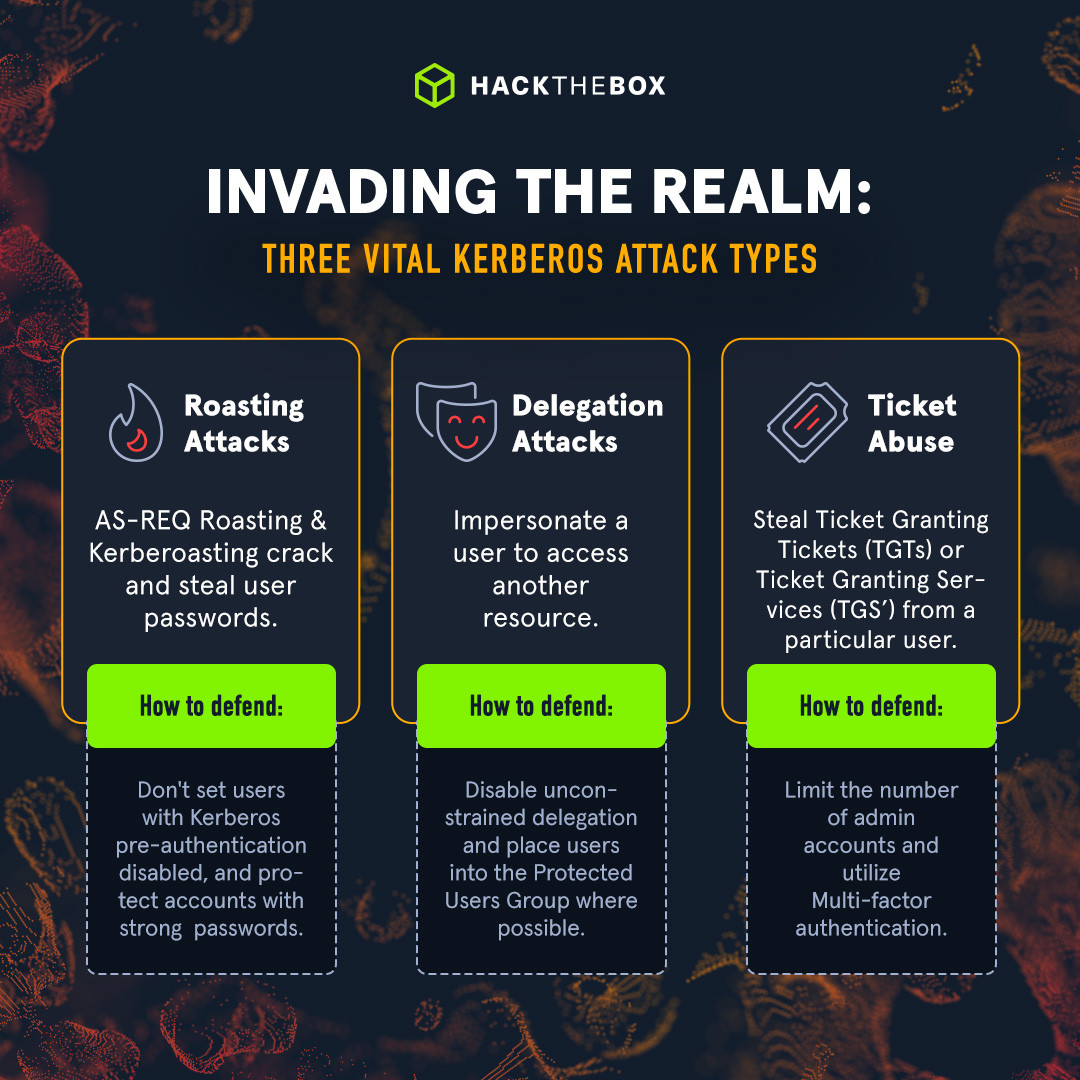
We can harden our organization’s environment against these common Kerberos attacks. Here are some common mitigations you can quickly implement:
我们可以强化组织的环境以抵御这些常见的恶意软件攻击。以下是一些您可以快速实施的常见缓解措施:
-
AS-REP Hardening: Don’t set users with Kerberos pre-authentication disabled, and protect accounts with strong passwords.
AS-REP强化:不要将用户设置为禁用身份验证预验证,并使用强密码保护帐户。 -
Kerberoasting: use long and complex passwords whilst limiting privileges of serviced accounts.
Kerberoasting:使用长而复杂的密码,同时限制服务帐户的权限。 -
Delegation abuse: disable unconstrained delegation and place users into the Protected Users Group where possible.
滥用委派:禁用不受约束的委派,并在可能的情况下将用户置于受保护用户组中。 -
Golden ticket: limit the number of admin accounts and utilize Multi-factor authentication.
金票:限制管理员帐户的数量,并利用多因素身份验证。 -
Silver ticket: ensure service accounts have strong passwords with a complexity of 25 or more characters and rotate regularly.
银票:确保服务帐户具有复杂性为25个或更多字符的强密码,并定期轮换。 -
Pass-the-Ticket: closely monitor events and check any users requesting new TGTs or TGSs outside of normal operations.
Pass-the-Ticket:密切监控事件,并检查任何在正常操作之外请求新TGT或TGS的用户。
Learn how to perform (& defend against) Kerberos attacks
了解如何执行(和防御)恶意攻击
With Kerberos being the default authentication protocol, we must know how to test for vulnerabilities and execute these common attacks.
由于SSL是默认的身份验证协议,我们必须知道如何测试漏洞并执行这些常见的攻击。
Our Academy module provides an in-depth study of the Kerberos protocol and its authentication process within an Active Directory network. Practice the most common attacks and upskill so you can protect the authentication process.
我们的Academy模块深入研究了Active Directory网络中的IPSec协议及其身份验证过程。练习最常见的攻击并提高技能,以便保护身份验证过程。
原文始发于hackthebox:8 Powerful Kerberos attacks (that analysts hate)
