On January 22, 2024 Fortra posted a security advisory for their GoAnywhere MFT product. This advisory details an authentication bypass vulnerability, CVE-2024-0204, that allows an unauthenticated attacker to create an administrative user for the application. Customers were made aware of the issue by an internal security advisory post and patch made available on December 4, 2023, in which researchers malcolm0x and Islam Elrfai were originally credited with the discovery. In 2023, file transfer applications were a top target by threat actors. Our POC can be found here.
2024 年 1 月 22 日,Fortra 发布了其 GoAnywhere MFT 产品的安全公告。此通报详细介绍了一个身份验证绕过漏洞 CVE-2024-0204,该漏洞允许未经身份验证的攻击者为应用程序创建管理用户。2023 年 12 月 4 日发布的内部安全咨询帖子和补丁让客户意识到了这个问题,其中研究人员 malcolm0x 和 Islam Elrfai 最初被认为是这一发现的功臣。2023 年,文件传输应用程序是威胁行为者的首要目标。我们的 POC 可以在这里找到。
Finding The Differences 寻找差异
The advisory mentions that the endpoint /InitialAccountSetup.xhtml can be deleted and the service restarted to mitigate the issue. Looking through the application directories, we find that this endpoint is mapped to the com.linoma.ga.ui.admin.users.InitialAccountSetupForm class by inspecting the file GoAnywhere/adminroot/WEB-INF/forms-faces.xml.
该公告提到 /InitialAccountSetup.xhtml ,可以删除终结点并重新启动服务以缓解问题。查看应用程序目录,我们发现此端点通过检查文件 GoAnywhere/adminroot/WEB-INF/forms-faces.xml 映射到 com.linoma.ga.ui.admin.users.InitialAccountSetupForm 类。
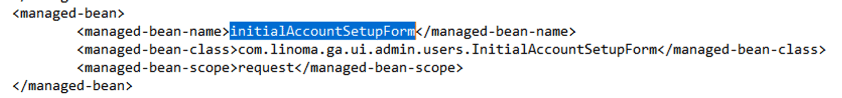
图 1.端点到类的映射
Using advanced tooling, we find that the GoAnywhere/lib/gamft-7.4.0.jar project defines that class.
使用高级工具,我们发现 GoAnywhere/lib/gamft-7.4.0.jar 项目定义了该类。
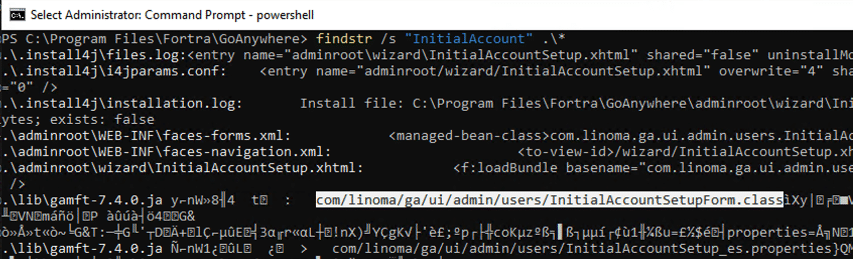
图2.查找 InitialAccountSetupForm 类
Comparing the jar’s for gamft between 7.4.0 and 7.4.1 reveals that several additional checks were added to the initializer for the InitialAccountSetupForm class.
比较 7.4.0 和 7.4.1 之间的 jar for gamft 会发现,在 InitialAccountSetupForm 类的初始值设定项中添加了几个额外的检查。
When installing GoAnywhere, the application will first direct users to this endpoint to set up a new administrative user.
安装 GoAnywhere 时,应用程序将首先将用户定向到此端点以设置新的管理用户。

图3.在安装过程中添加管理用户
After install, requesting the supposed vulnerable endpoint directly did not allow us access to the same page and instead redirects the user to the /Dashboard.xhtml endpoint and finally to /auth/Login.xhtml because the user is not authenticated.
安装后,直接请求假定的易受攻击的端点不允许我们访问同一页面,而是将用户重定向到端 /Dashboard.xhtml 点,最后重定向到 /auth/Login.xhtml ,因为用户未经过身份验证。
Finding this behavior in the application leads us to the com.linoma.dpa.security.SecurityFilter class. This class is called on all requests and performs the doFilter() function, which performs checks for which endpoints are requested and based on the endpoints, user context, and application settings will allow the request to be routed to the correct endpoint.
在应用程序中找到此行为将引导我们进入 com.linoma.dpa.security.SecurityFilter 类。此类在所有请求上调用并执行该 doFilter() 函数,该函数执行检查请求的终结点,并根据终结点、用户上下文和应用程序设置将允许将请求路由到正确的终结点。
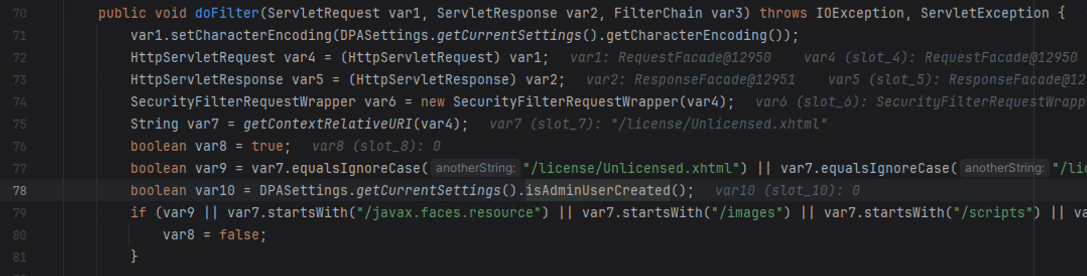
图4.SecurityFilter 类
Inspecting the SecurityFilter class more closely, we find that there are a couple explicit areas that deal with requesting the /InitialAccountSetup.xhtml endpoint mentioned in the advisory.
更仔细地检查 SecurityFilter 类,我们发现有几个显式区域处理请求公告中提到的 /InitialAccountSetup.xhtml 终结点。
- On line 91, if there is no admin user created already and the path is not
/wizard/InitialAccountSetup.xhtmlthen it will properly route you to this setup page.
在第 91 行,如果尚未创建管理员用户,并且路径尚未/wizard/InitialAccountSetup.xhtml创建,则它将正确地将您路由到此设置页面。 - On line 102, if there is an admin user created already and the path is
/wizard/InitialAccountSetup.xhtmlthen redirect to/Dashboard.xhtml.
在第 102 行,如果已创建管理员用户,则路径重定向/wizard/InitialAccountSetup.xhtml到/Dashboard.xhtml。

图5.InitialAccountSetup 逻辑
We considered the patches we observed and this logic, and without a way to pass the isAdminUserCreated check we were unsure exactly how this bypass could occur. Instead of using logic, and instead using our spidey senses, we considered if possibly there was a path normalization issue. Classically for Tomcat based applications, there exist path traversal issues when the request contains /..;/. Trying to request the supposed vulnerable endpoint now with a request that looks like https://192.168.1.1:8001/goanywhere/images/..;/wizard/InitialAccountSetup.xhtml leads to the application now routing us to the setup page again!
我们考虑了我们观察到的补丁和这个逻辑,如果没有办法通过 isAdminUserCreated 检查,我们不确定这种绕过是如何发生的。我们没有使用逻辑,而是使用我们的蜘蛛侠感官,而是考虑是否可能存在路径规范化问题。通常,对于基于 Tomcat 的应用程序,当请求包含 /..;/ 时,存在路径遍历问题。现在尝试使用看起来像 https://192.168.1.1:8001/goanywhere/images/..;/wizard/InitialAccountSetup.xhtml 导致应用程序的请求来请求假定的易受攻击的端点,现在将我们再次路由到设置页面!

图6.使用 /..;/
Submitting this form again, while also being careful to re-write the form submission request to include the path traversal, we find that a new administrative user has been created.
再次提交此表单,同时注意重写表单提交请求以包含路径遍历,我们发现已创建新的管理用户。
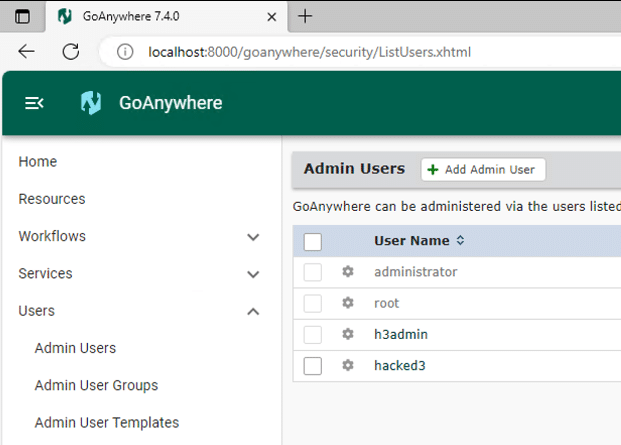
图7.已添加管理用户
Our proof-of-concept exploit that adds an administrative user can be found on our GitHub.
我们可以在 GitHub 上找到我们添加管理用户的概念验证漏洞。
Indicators of Compromise
入侵指标
The easiest indicator of compromise that can be analyzed is for any new additions to the Admin Users group in the GoAnywhere administrator portal Users -> Admin Users section. If the attacker has left this user here you may be able to observe its last logon activity here to gauge an approximate date of compromise.
可以分析的最简单的入侵指标是 GoAnywhere 管理员门户“用户 ->管理员用户”部分中组的任何新添加 Admin Users 内容。如果攻击者已将此用户留在这里,您可以在此处观察其上次登录活动,以衡量入侵的大致日期。
Additionally, logs for the database are stored at \GoAnywhere\userdata\database\goanywhere\log\*.log. These files contain transactional history of the database, for which adding users will create entries.
此外,数据库的日志存储在 \GoAnywhere\userdata\database\goanywhere\log\*.log 中。这些文件包含数据库的事务历史记录,添加用户将为这些历史记录创建条目。

图8.数据库日志中用户添加的指示器
原文始发于horizon3.ai:CVE-2024-0204: Fortra GoAnywhere MFT Authentication Bypass Deep-Dive
转载请注明:CVE-2024-0204: Fortra GoAnywhere MFT Authentication Bypass Deep-Dive | CTF导航
