Cybersecurity researchers have disclosed a now-patched security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the underlying operating system.
网络安全研究人员在Microsoft Windows和Apple macOS的Opera Web浏览器中披露了一个现已修补的安全漏洞,该漏洞可用于在底层操作系统上执行任何文件。
The remote code execution vulnerability has been codenamed MyFlaw by the Guardio Labs research team owing to the fact that it takes advantage of a feature called My Flow that makes it possible to sync messages and files between mobile and desktop devices.
Guardio Labs 研究团队将远程代码执行漏洞代号为 MyFlaw,因为它利用了名为 My Flow 的功能,可以在移动和桌面设备之间同步消息和文件。
“This is achieved through a controlled browser extension, effectively bypassing the browser’s sandbox and the entire browser process,” the company said in a statement shared with The Hacker News.
“这是通过受控的浏览器扩展来实现的,有效地绕过了浏览器的沙盒和整个浏览器进程,”该公司在与The Hacker News分享的一份声明中表示。
The issue impacts both the Opera browser and Opera GX. Following responsible disclosure on November 17, 2023, it was addressed as part of updates shipped on November 22, 2023.
该问题会影响 Opera 浏览器和 Opera GX。在 2023 年 11 月 17 日负责任地披露后,它已作为 2023 年 11 月 22 日发布的更新的一部分得到解决。
My Flow features a chat-like interface to exchange notes and files, the latter of which can be opened via a web interface, meaning a file can be executed outside of the browser’s security boundaries.
My Flow 具有类似聊天的界面来交换笔记和文件,后者可以通过 Web 界面打开,这意味着文件可以在浏览器的安全边界之外执行。
It is pre-installed in the browser and facilitated by means of a built-in (or internal) browser extension called “Opera Touch Background,” which is responsible for communicating with its mobile counterpart.
它预装在浏览器中,并通过称为“Opera Touch Background”的内置(或内部)浏览器扩展进行便利,该扩展程序负责与移动对应物进行通信。
This also means that the extension comes with its own manifest file specifying all the required permissions and its behavior, including a property known as externally_connectable that declares which other web pages and extensions can connect to it.
这也意味着扩展带有自己的清单文件,指定所有必需的权限及其行为,包括一个称为 externally_connectable 的属性,该属性声明哪些其他网页和扩展可以连接到它。
In the case of Opera, the domains that can talk to the extension should match the patterns “*.flow.opera.com” and “.flow.op-test.net” – both controlled by the browser vendor itself.
就 Opera 而言,可以与扩展程序通信的域应与模式“*.flow.opera.com”和“.flow.op-test.net”匹配——两者都由浏览器供应商本身控制。
“This exposes the messaging API to any page that matches the URL patterns you specify,” Google notes in its documentation. “The URL pattern must contain at least a second-level domain.”
“这会将消息传递 API 暴露给与您指定的 URL 模式匹配的任何页面,”谷歌在其文档中指出。“URL 模式必须至少包含二级域。”
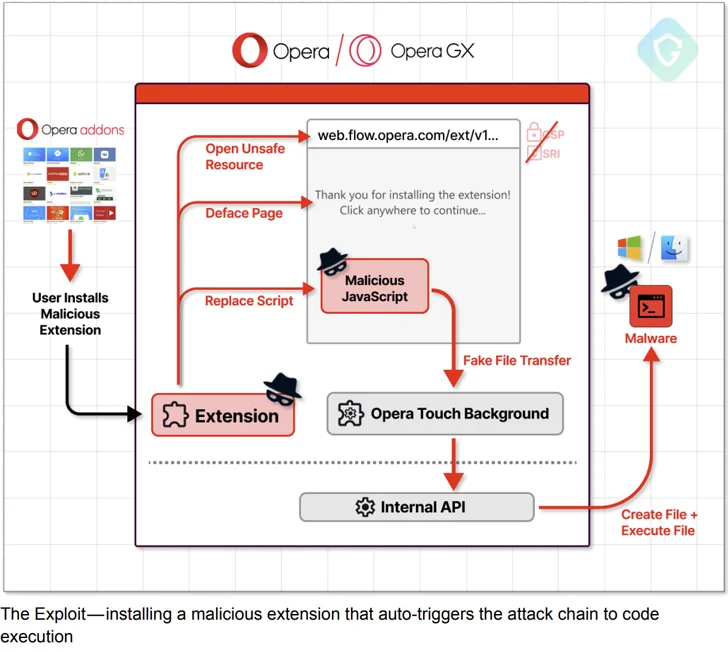
Guardio Labs said it was able to unearth a “long-forgotten” version of the My Flow landing page hosted on the domain “web.flow.opera.com” using the urlscan.io website scanner tool.
Guardio Labs 表示,它能够使用 urlscan.io 网站扫描工具挖掘出托管在域“web.flow.opera.com”上的“被遗忘已久”的 My Flow 登录页面版本。
“The page itself looks quite the same as the current one in production, but changes lie under the hood: Not only that it lacks the [content security policy] meta tag, but it also holds a script tag calling for a JavaScript file without any integrity check,” the company said.
“该页面本身看起来与当前生产中的页面完全相同,但变化隐藏在引擎盖下:它不仅缺少[内容安全策略]元标记,而且还包含一个脚本标签,调用JavaScript文件,没有任何完整性检查,”该公司表示。
“This is exactly what an attacker needs – an unsafe, forgotten, vulnerable to code injection asset, and most importantly, has access to (very) high permission native browser API.”
“这正是攻击者所需要的——一种不安全的、被遗忘的、容易受到代码注入攻击的资产,最重要的是,可以访问(非常)高权限的原生浏览器API。”
The attack chain then hinges, creating a specially crafted extension that masquerades as a mobile device to pair with the victim’s computer and transmit an encrypted malicious payload via the modified JavaScript file to the host for subsequent execution by prompting the user to click anywhere on the screen.
然后,攻击链会铰接,创建一个特制的扩展程序,该扩展程序伪装成移动设备,与受害者的计算机配对,并通过修改后的 JavaScript 文件将加密的恶意负载传输到主机,以便通过提示用户单击屏幕上的任意位置进行后续执行。
The findings highlight the increasing complexity of browser-based attacks and the different vectors that can be exploited by threat actors to their advantage.
这些发现凸显了基于浏览器的攻击的复杂性日益增加,以及威胁行为者可以利用的不同媒介来谋取利益。
“Despite operating in sandboxed environments, extensions can be powerful tools for hackers, enabling them to steal information and breach browser security boundaries,” the company told The Hacker News.
“尽管在沙盒环境中运行,但扩展程序可以成为黑客的强大工具,使他们能够窃取信息并破坏浏览器安全边界,”该公司告诉The Hacker News。
“This underscores the need for internal design changes at Opera and improvements in Chromium’s infrastructure. For instance, disabling third-party extension permissions on dedicated production domains, similar to Chrome’s web store, is recommended but has not yet been implemented by Opera.”
“这凸显了Opera内部设计变更和Chromium基础设施改进的必要性。例如,建议在专用生产域上禁用第三方扩展权限,类似于 Chrome 的网上商店,但 Opera 尚未实施。
When reached for comment, Opera said it moved quickly to close the security hole and implement a fix on the server side and that it’s taking steps to prevent such issues from happening again.
当被要求发表评论时,Opera表示,它迅速采取行动,关闭了安全漏洞,并在服务器端实施了修复,并且正在采取措施防止此类问题再次发生。
“Our current structure uses an HTML standard, and is the safest option that does not break key functionality,” the company said. “After Guardio alerted us to this vulnerability, we removed the cause of these issues and we are making sure that similar problems will not appear in the future.”
“我们目前的结构使用HTML标准,是最安全的选择,不会破坏关键功能,”该公司表示。“在Guardio提醒我们注意此漏洞后,我们消除了这些问题的原因,并确保将来不会出现类似的问题。
“We would like to thank Guardio Labs for their work on uncovering and immediately alerting us to this vulnerability. This collaboration demonstrates how we work together with security experts and researchers around the world to complement our own efforts at maintaining and improving the security of our products and ensuring our users have a safe online experience.”
“我们要感谢 Guardio Labs 在发现并立即提醒我们注意此漏洞方面所做的工作。此次合作展示了我们如何与世界各地的安全专家和研究人员合作,以补充我们自己在维护和提高产品安全性方面所做的努力,并确保我们的用户拥有安全的在线体验。
原文始发于the hacker news:Opera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows
转载请注明:Opera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows | CTF导航