Last year, we documented malware distribution campaigns both via malvertising and compromised sites delivering Atomic Stealer (AMOS) onto Mac users. This stealer has proven to be quite popular in the criminal underground and its developers have been adding new features to justify its hefty $3000/month rental fee.
去年,我们记录了恶意软件分发活动,包括通过恶意广告和受感染的网站向 Mac 用户提供 Atomic Stealer (AMOS)。事实证明,这个窃贼在地下犯罪中非常受欢迎,其开发人员一直在添加新功能,以证明其每月 3000 美元的高额租金是合理的。
It looks like Atomic Stealer was updated around mid to late December 2023, where its developers introduced payload encryption in an effort to bypass detection rules. Some samples from crack websites made their way to VirusTotal around that time frame, followed by a malvertising campaign we observed in January 2024.
看起来 Atomic Stealer 是在 2023 年 12 月中下旬左右更新的,其开发人员引入了有效载荷加密以绕过检测规则。大约在那个时间段内,一些来自破解网站的样本进入了 VirusTotal,随后我们在 2024 年 1 月观察到了一场恶意广告活动。
In this blog post, we will review the latest changes with Atomic Stealer and the recent distribution with malicious ads via the Google search engine.
在这篇博文中,我们将回顾 Atomic Stealer 的最新变化以及最近通过 Google 搜索引擎分发恶意广告的情况。
December update and special promotion
12月更新和特别促销
In December, Atomic Stealer ran a promotion via a post on their Telegram channel to offer a special holiday discount to their customers:
12 月,Atomic Stealer 在其 Telegram 频道上发帖开展了促销活动,为其客户提供特别的假日折扣:
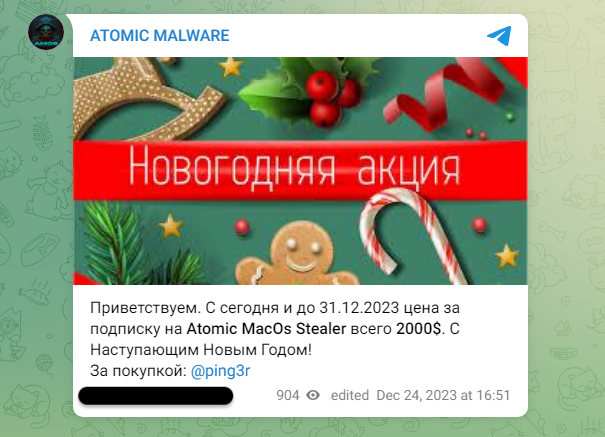
Welcome. From today until December 31, 2023, the price for a subscription to Atomic MacOs Stealer is only $2000 . Happy New Year!
欢迎。从今天到 2023 年 12 月 31 日,订阅 Atomic MacOs Stealer 的价格仅为 2000 美元。新年快乐!
While the developers did not specifically advertise this feature, it appears that around December 17 Atomic Stealer had changed some of its code to hide certain strings that were previously used for detection and identifying its command and control server.
虽然开发人员没有专门宣传此功能,但似乎在 12 月 17 日左右,Atomic Stealer 更改了其一些代码,以隐藏以前用于检测和识别其命令和控制服务器的某些字符串。
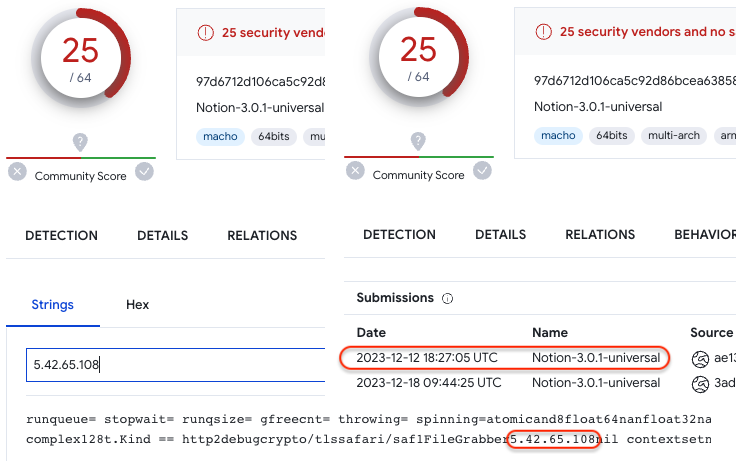
Sample with strings in clear text (Dec 12), showing for example the IP address for the malware’s C2 server:
明文字符串示例(12 月 12 日),例如显示恶意软件 C2 服务器的 IP 地址:
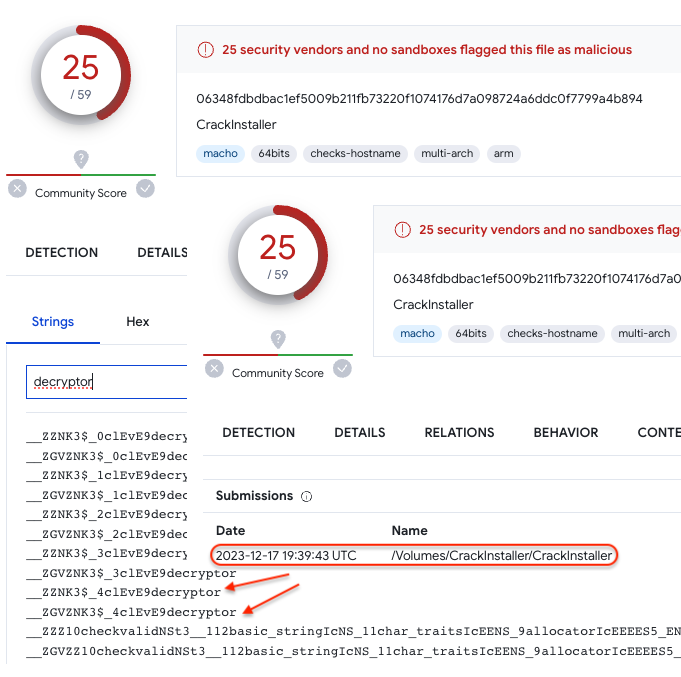
Obfuscated sample (Dec 17), using a new encryption routine that hides strings of interest:
模糊处理示例(12 月 17 日),使用隐藏相关字符串的新加密例程:
Those two samples above also represent the different distribution channels that Atomic Stealer customers are using to distribute the malware. It’s possible customers using software cracks got access to the update Atomic Stealer before those that leverage malicious ads.
上面的两个示例还代表了 Atomic Stealer 客户用于分发恶意软件的不同分发渠道。使用软件破解的客户有可能在利用恶意广告的客户之前访问更新的 Atomic Stealer。
In fact, during the holiday break, we noticed a decrease in malvertising activity, in particular for the campaigns running via Google search ads. This was somewhat expected and typically extends into early January. However, on January 8, we identified a malvertising campaign using similar tactics seen previously by threat actors distributing FakeBat. In this instance, there was also a payload destined for Mac users, Atomic Stealer in its updated version.
事实上,在假期期间,我们注意到恶意广告活动有所减少,尤其是通过 Google 搜索广告投放的广告系列。这在某种程度上是意料之中的,通常会持续到 1 月初。然而,在 1 月 8 日,我们发现了一个恶意广告活动,其策略与之前分发 FakeBat 的威胁行为者看到的策略类似。在这种情况下,还有一个针对 Mac 用户的有效载荷,即更新版本的 Atomic Stealer。
Malvertising with FakeBat – Atomic Stealer combo
使用 FakeBat 进行恶意广告 – Atomic Stealer 组合
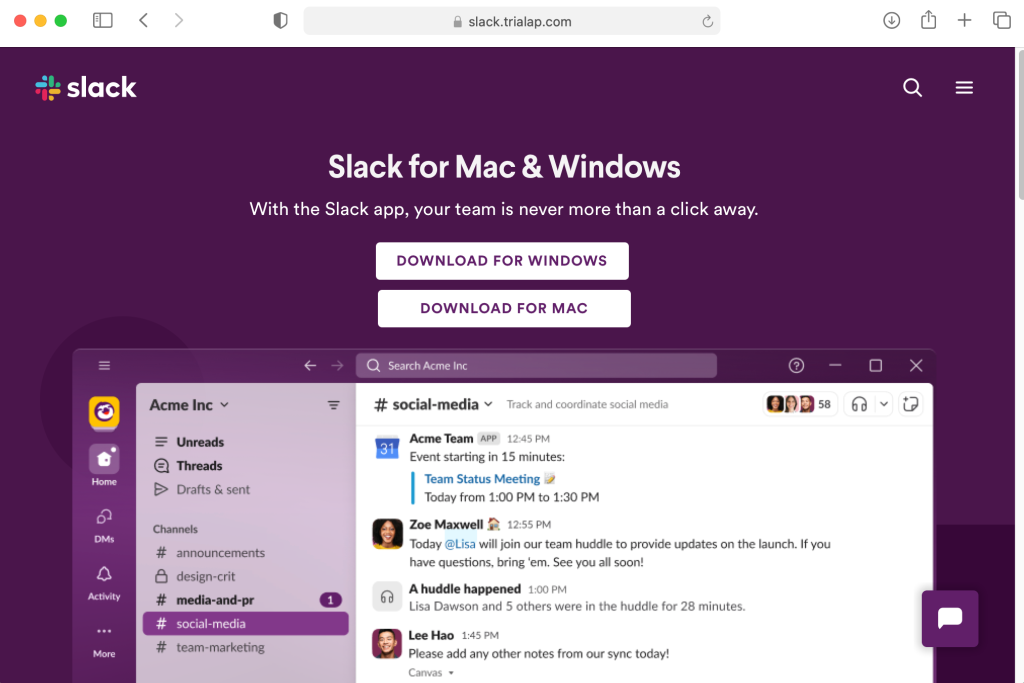
The threat actors are luring victims via a Google search ad impersonating Slack, the popular communication tool, and redirecting them to a decoy website where the app can be downloaded for both Windows and Mac:
威胁行为者通过冒充流行的通信工具 Slack 的 Google 搜索广告引诱受害者,并将他们重定向到一个诱饵网站,在该网站可以下载适用于 Windows 和 Mac 的应用程序:
The threat actors are leveraging tracking templates to filter traffic and route it through a few redirects before loading the landing page:
威胁参与者正在利用跟踪模板来过滤流量,并在加载登录页面之前通过一些重定向对其进行路由:

On that same domain, there is an open directory showing the location of the Windows payload which is an MSI installer (FakeBat), and the Mac one, Atomic Stealer (AMOS):
在同一个域上,有一个开放目录显示 Windows 有效负载的位置,该有效负载是 MSI 安装程序 (FakeBat) 和 Mac 安装程序 Atomic Stealer (AMOS):
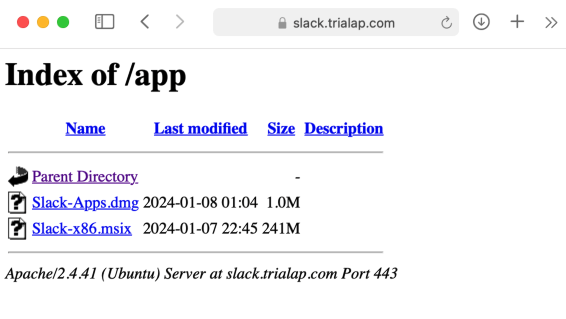
Obfuscated Atomic Stealer
混淆的原子窃取者
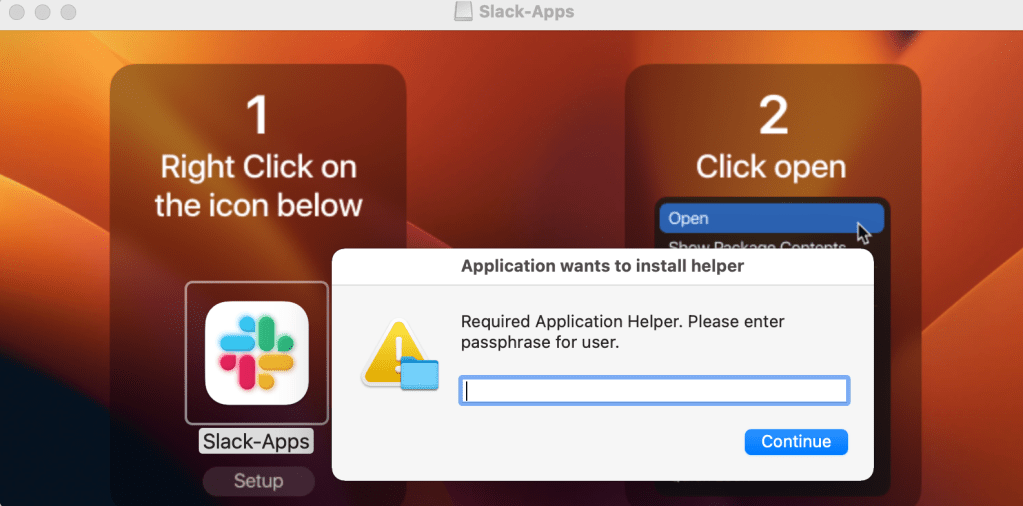
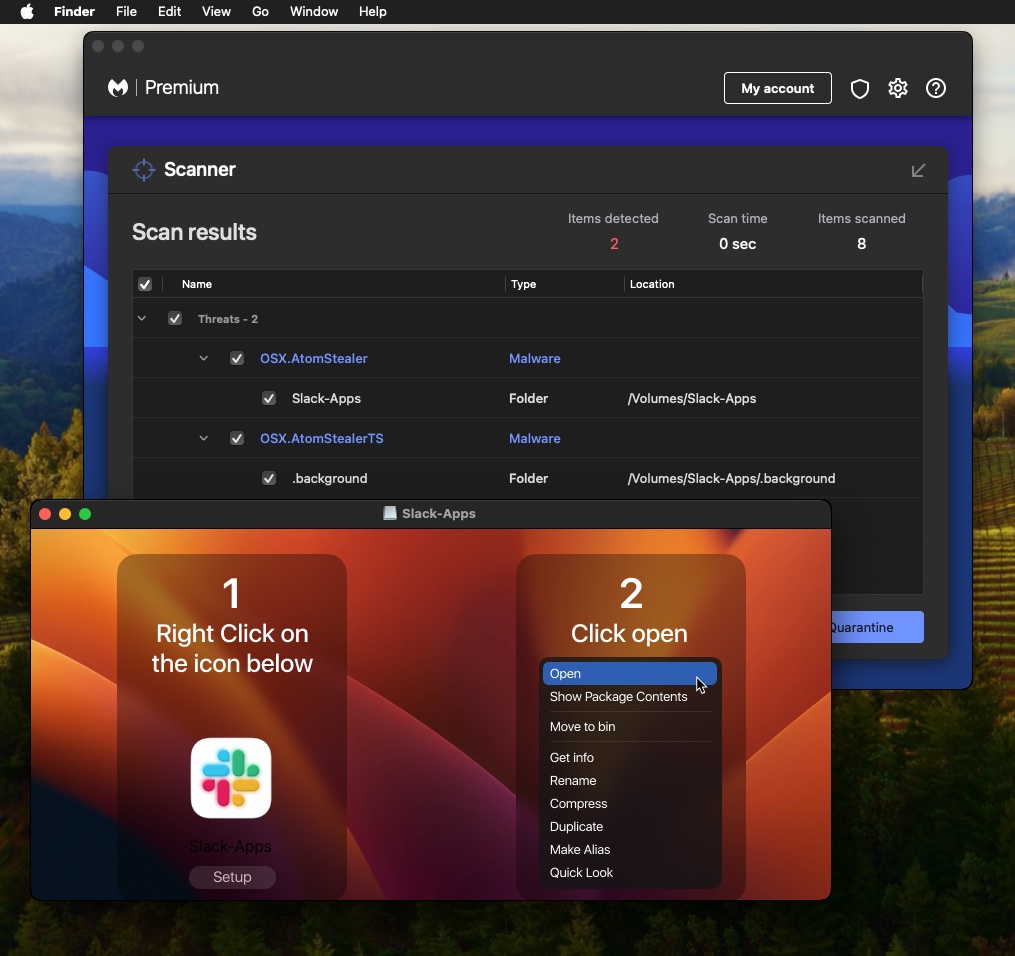
The malicious DMG file contains instructions for users to open the file as well as a dialog window asking them to enter their system password. This will allow Atomic Stealer to collect passwords and other sensitive files that are typically access-restricted.
恶意DMG文件包含用户打开文件的说明以及要求他们输入系统密码的对话窗口。这将允许 Atomic Stealer 收集密码和其他通常受访问限制的敏感文件。
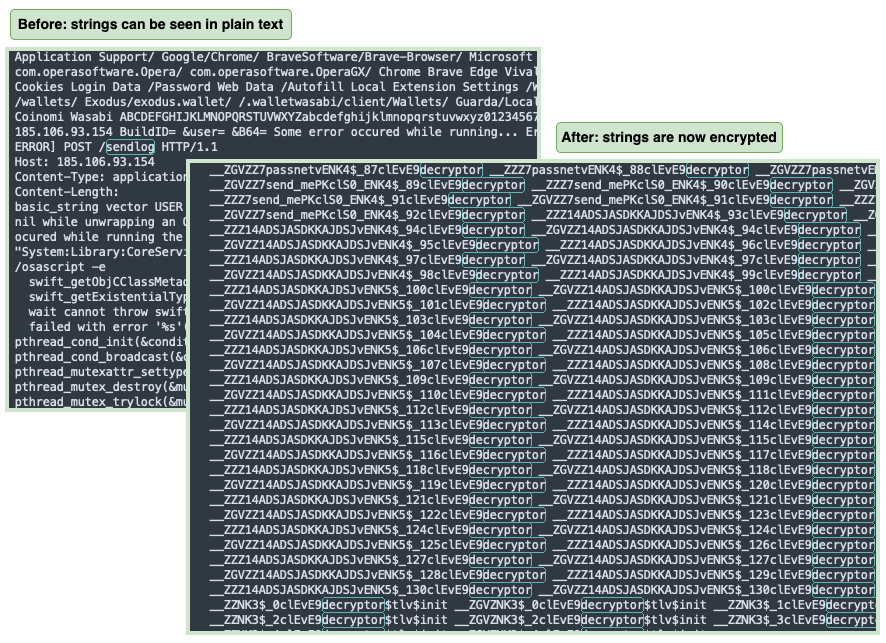
When comparing the previous Atomic Stealer samples we have, we can see that the application code has changed. Previously, we could see certain strings revealing the nature of the payload (browsers, wallets, etc.) and more importantly the command and control server that receives stolen user data. Now, these strings are no longer visible as the code is well obfuscated:
在比较我们之前拥有的 Atomic Stealer 示例时,我们可以看到应用程序代码已更改。以前,我们可以看到某些字符串揭示了有效负载(浏览器、钱包等)的性质,更重要的是,接收被盗用户数据的命令和控制服务器。现在,这些字符串不再可见,因为代码被很好地混淆了:
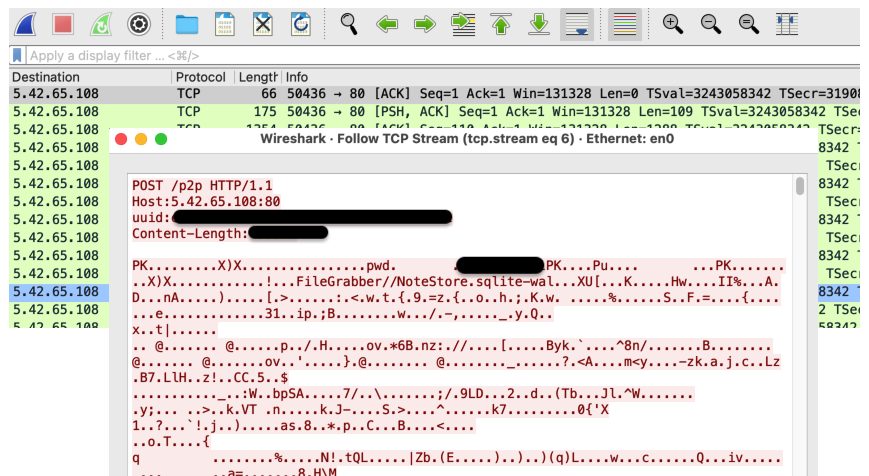
When we analyzed this sample in a sandbox we saw the data exfiltration taking place and the corresponding C2 server:
当我们在沙盒中分析此示例时,我们看到了正在发生的数据外泄和相应的 C2 服务器:
Stealing victim passwords, crypto wallets and cookies
窃取受害者密码、加密钱包和 cookie
As detailed in Objective-See’s The Mac Malware of 2023, stealers were the most popular type of malware. It’s not just passwords that are of interest to cyber criminals. Stealing browser cookies can sometimes be even better than having the victim’s password, enabling authentication into accounts via session tokens.
正如 Objective-See 的 2023 年 Mac 恶意软件中所详述的那样,窃取程序是最受欢迎的恶意软件类型。网络犯罪分子感兴趣的不仅仅是密码。窃取浏览器 cookie 有时甚至比拥有受害者的密码更好,通过会话令牌对帐户进行身份验证。
In fact, Atomic Stealer developers were working on a cookie feature they announced on Christmas Eve:
事实上,Atomic Stealer 开发人员正在开发他们在圣诞节前夕宣布的 cookie 功能:
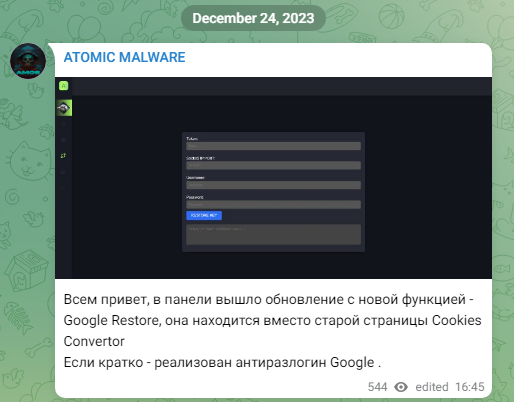
Hi everyone, the panel has released an update with a new feature – Google Restore, it is located instead of the old page Cookies Convertor. In brief – implemented anti-unlogin Google.
大家好,该小组发布了具有新功能的更新 – Google Restore,它位于旧页面Cookie Convertor的位置。简而言之 – 实现了反取消登录 Google。
As stealers continue to be a top threat for Mac users, it is important to download software from trusted locations. Malicious ads and decoy sites can be very misleading though and it only takes a single mistake (entering your password) for the malware to collect and exfiltrate your data.
由于窃取程序仍然是 Mac 用户的最大威胁,因此从受信任的位置下载软件非常重要。不过,恶意广告和诱饵网站可能非常具有误导性,恶意软件只需要一个错误(输入密码)即可收集和泄露您的数据。
We have reported the malicious ad and infrastructure to the respective parties for mitigation.
我们已向相关方报告了恶意广告和基础架构,以缓解这些措施。
To stay safe from this and other similar threats, a combination of web protection and antivirus is best suited. Malwarebytes Browser Guard and Antivirus for macOS can prevent and detect Atomic Stealer.
为了免受这种威胁和其他类似威胁的侵害,网络保护和防病毒软件的组合最适合。适用于 macOS 的 Malwarebytes 浏览器防护和防病毒软件可以防止和检测 Atomic Stealer。
Indicators of Compromise
入侵指标
Malvertising chain 恶意广告链
ivchlo[.]gotrackier[.]com red[.]seecho[.]net
Decoy site 诱饵网站
slack[.]trialap[.]com
FakeBat payload URL FakeBat 有效负载 URL
slack[.]trialap[.]com/app/Slack-x86.msix
FakeBat hash FakeBat 哈希
49f12d913ad19d4608c1596cf24e7b6fff14975418f09e2c1ad37f231943fda3
FakeBat C2 假蝙蝠 C2
ads-strong[.]online
Atomic Stealer payload URL
Atomic Stealer 有效负载 URL
slack[.]trialap[.]com/app/Slack-Apps.dmg
Atomic Stealer hash Atomic Stealer 哈希
18bc97e3f68864845c719754d2d667bb03f754f6e87428e33f9c763a8e6a704a
C2
5.42.65[.]108
