
CVE-2023-22527 is a critical vulnerability within Atlassian’s Confluence Server and Data Center. This vulnerability has the potential to permit unauthenticated attackers to inject OGNL expressions into the Confluence Instance, thereby enabling the execution of arbitrary code and system commands.
CVE-2023-22527 是 Atlassian 的 Confluence Server 和 Data Center 中的一个严重漏洞。此漏洞可能允许未经身份验证的攻击者将 OGNL 表达式注入 Confluence 实例,从而能够执行任意代码和系统命令。
Technical Details 技术细节
Initial Analysis 初步分析
The CVE description provided by Atlassian made it clear that this vulnerability was automatically rendered unexploitable in version 8.5.4 due to certain incorporated changes. However, the most recent Confluence version, 8.5.5, has also been released, completely eliminating the root cause.
Atlassian 提供的 CVE 描述明确表示,由于某些合并的更改,此漏洞在版本 8.5.4 中自动变得不可利用。但是,最新的 Confluence 版本 8.5.5 也已经发布,完全消除了根本原因。
When we compared the differences between versions 8.5.4 and 8.5.3 by patch diffing, we discovered a significant number of changes, including additions and deletions of files. This led us to spend a considerable amount of time examining various differences that appeared relevant, sometimes leading us down unexpected paths. Additionally, based on our knowledge and presumptions, there didn’t appear to be a substantial unauthenticated attack surface, especially considering the recent CVEs related to Confluence.
当我们通过补丁差异比较版本 8.5.4 和 8.5.3 之间的差异时,我们发现了大量的变化,包括文件的添加和删除。这导致我们花了相当多的时间来研究各种看似相关的差异,有时会导致我们走上意想不到的道路。此外,根据我们的知识和推测,似乎没有实质性的未经身份验证的攻击面,特别是考虑到最近与 Confluence 相关的 CVE。
A significant portion of our time was dedicated to inspecting files that had OGNL-related changes and potential vulnerabilities like dangerous sinks leading to OGNL Injection, such as findValue and translateVariables, among others.
我们的大部分时间都用于检查具有 OGNL 相关更改和潜在漏洞的文件,例如导致 OGNL 注入的危险接收器,例如 findValue 和 translateVariables 等。
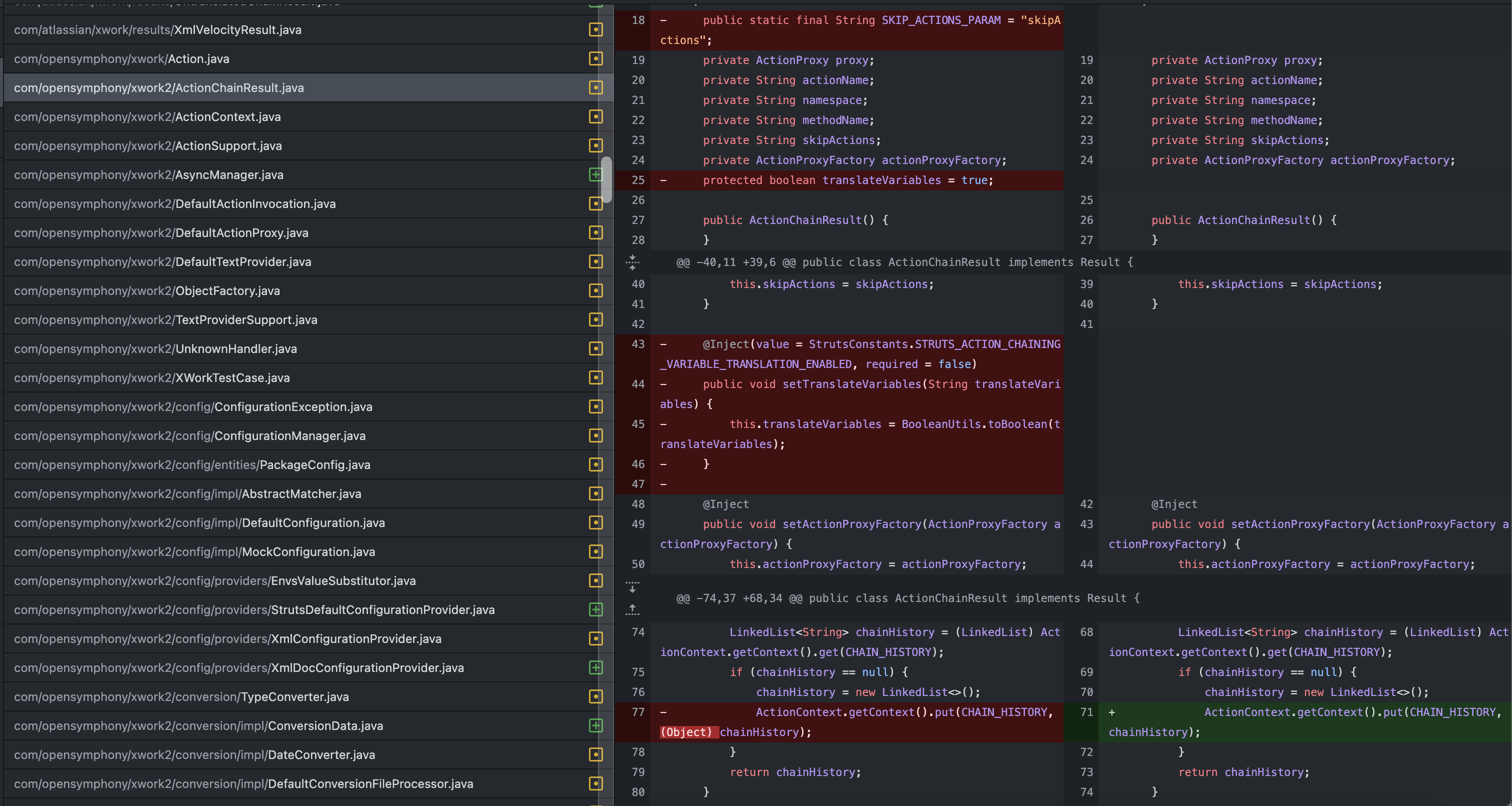
Confluence v8.5.3 和 v8.5.4 之间的补丁差异
While many of these changes appeared to be related to code refactoring, we couldn’t find anything obvious.
虽然其中许多更改似乎与代码重构有关,但我们找不到任何明显的东西。
Identifying the Unauthenticated Attack Surface
识别未经身份验证的攻击面
Drawing on our previous experience with Confluence, we were aware that the actual “views” in Confluence are rendered using Velocity template files. Interestingly, rather than accessing them solely through struts actions, they can also be accessed directly by hitting the *.vm files, and they continue to render correctly even as an unauthenticated user.
根据我们之前使用 Confluence 的经验,我们知道 Confluence 中的实际“视图”是使用 Velocity 模板文件呈现的。有趣的是,它们不是仅仅通过支柱操作来访问它们,还可以通过点击 *.vm 文件直接访问它们,即使作为未经身份验证的用户,它们也能继续正确呈现。
Upon discovering these patterns, we began searching for template files that accepted $parameters and then passed them to potentially dangerous sinks. We identified several files that directly passed the parameter values to $ognl.findValue or $stack.findValue. For instance, one such file is confluence/template/xhtml/pagelist.vm:
发现这些模式后,我们开始搜索接受 $parameters 这些模板文件,然后将它们传递给有潜在危险的接收器。我们确定了几个直接将参数值传递给 $ognl.findValue 或 $stack.findValue 的文件。例如,一个这样的文件是 confluence/template/xhtml/pagelist.vm :
Contents of confluence/template/xhtml/pagelist.vm
confluence/template/xhtml/pagelist.vm 的内容
We set up a breakpoint in the debugger at the “findValue” function to ensure that we were reaching it successfully. However, when we attempted to access /confluence/template/xhtml/pagelist.vm directly with the “pages” parameter, the breakpoint was not triggered.
我们在调试器中的“findValue”函数处设置了一个断点,以确保我们成功到达它。但是,当我们尝试使用“pages”参数直接访问 /confluence/template/xhtml/pagelist.vm 时,没有触发断点。
Later, we came to conclusion that this didn’t work by adding statements to help debug around in the pagelist.vm. We found that $parameters.pages might not be sent as String but rather an Object and later we found if we added double quotes around $parameter.pages It would have worked. The following change works perfectly and leads to OGNL injection:
后来,我们得出的结论是,通过添加语句来帮助调试 pagelist.vm .我们发现它可能不是作为字符串发送的,而是一个对象,后来我们发现如果我们在它周围 $parameter.pages 添加双引号,它 $parameters.pages 就会起作用。以下更改可以完美地工作并导致 OGNL 注射:
Next, we simply looked for any findValue calls that takes in $parameters inside double quotes. And, to our surprise we found one in confluence/template/aui/text-inline.vm.
接下来,我们只需查找任何在双引号内接受$parameters的 findValue 调用。而且,令我们惊讶的是,我们在 confluence/template/aui/text-inline.vm .
Contents of confluence/template/aui/text-inline.vm
confluence/template/aui/text-inline.vm 的内容
At this, point of time we realized we simply missed patch diffing the resources such as vm files. After doing so it was found that, this text-inline.vm file have been removed in the latest version as well which confirmed our suspicion.
在这个时间点,我们意识到我们只是错过了补丁差异资源,例如 vm 文件。这样做后,发现该文件 text-inline.vm 在最新版本中也被删除,这证实了我们的怀疑。
OGNL Expression Evaluation
OGNL表达评估
Next, we put a breakpoint on getText as well to be sure we are able to reach there and It worked.
接下来,我们还设置 getText 了一个断点,以确保我们能够到达那里并且它起作用了。
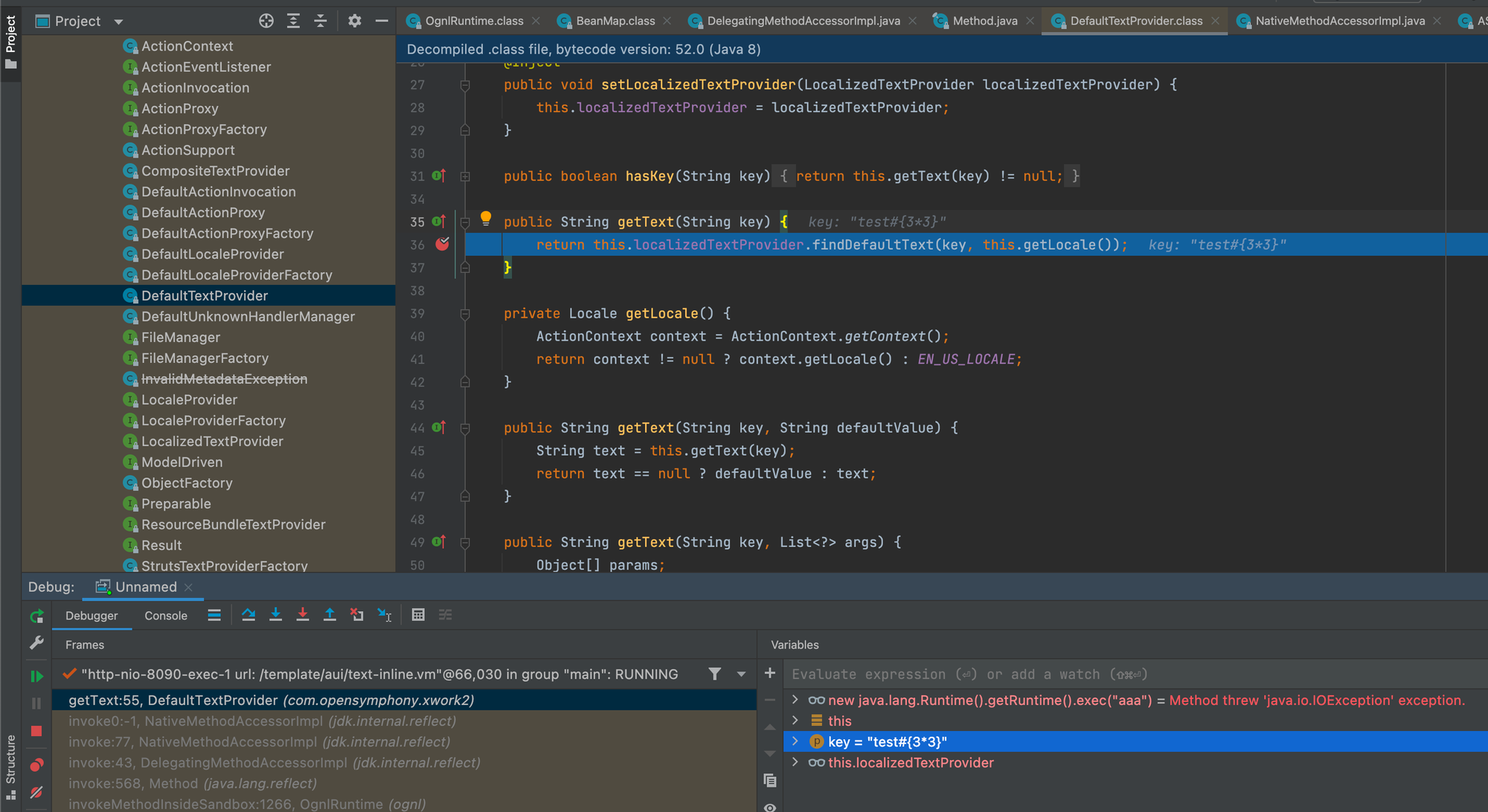
Next, we tried breaking out of the getText function call and append our OGNL expression #{3*33} but it was HTML encoded. Later, we used the previously known trick to use unicode escapes to breakout of function and append our controlled OGNL syntax and it worked.
接下来,我们尝试打破 getText 函数调用并附加我们的 OGNL 表达式 #{3*33} ,但它是 HTML 编码的。后来,我们使用了以前已知的技巧,使用 unicode 转义来突破函数并附加我们控制的 OGNL 语法,它奏效了。
HTTP request to trigger Blind OGNL expression evaluation
触发盲 OGNL 表达式求值的 HTTP 请求
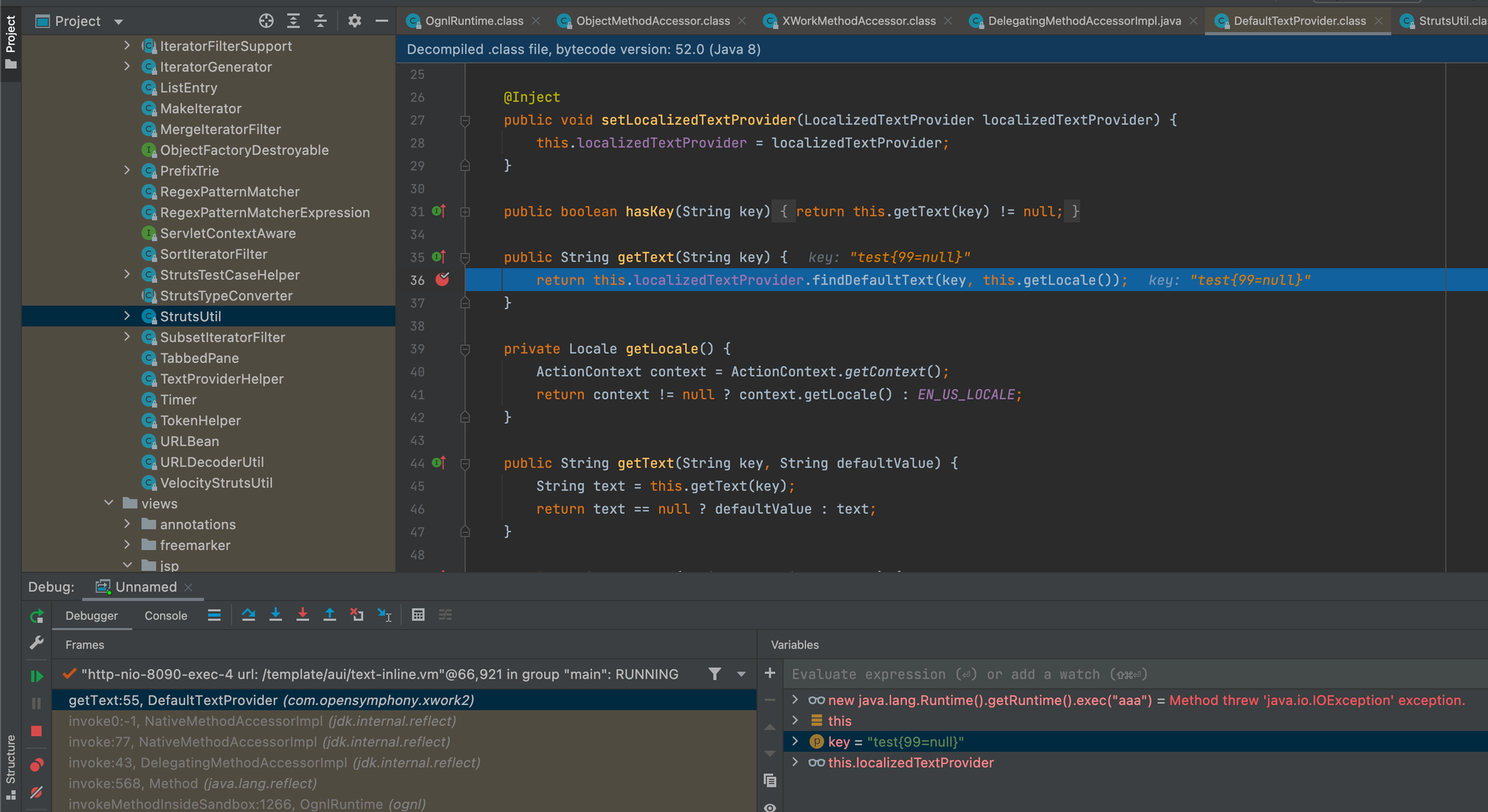
OGNL 表达式在传递给 getText 之前已计算
Now, to bypass the security restrictions setup by struts to exclude certain packages and classes to be accessed with OGNL expression.
现在,绕过 struts 设置的安全限制,以排除要使用 OGNL 表达式访问的某些包和类。
Remote Code Execution via OGNL Injection
通过OGNL注入远程执行代码
We looked at all that was available to us in the context by peeking at variables such as #attr , #application etc.
我们通过查看变量(例如 #attr 等 #application )来查看上下文中可用的所有内容。
Using the previously shared knowledge from none other than Alvaro Muñoz we found a potential way to get code execution.
利用阿尔瓦罗·穆尼奥斯(Alvaro Muñoz)之前分享的知识,我们找到了一种潜在的代码执行方法。
It was discovered that the .KEY_velocity.struts2.context key was present within the #request map. By using the expression #request['.KEY_velocity.struts2.context'].internalGet('ognl'), we were able to access the org.apache.struts2.views.jsp.ui.OgnlTool class and invoke the Ognl.findValue(String, Object) method.
发现 .KEY_velocity.struts2.context 钥匙存在于 #request 地图中。通过使用表达式 #request['.KEY_velocity.struts2.context'].internalGet('ognl') ,我们能够访问该类并调用该 org.apache.struts2.views.jsp.ui.OgnlTool Ognl.findValue(String, Object) 方法。
It’s important to note that this class belongs to the OGNL library and is not part of Struts. As a result, this “findValue” call operates outside of Struts’ sandboxed restrictions, as mentioned in the blog.
需要注意的是,此类属于 OGNL 库,不属于 Struts。因此,如博客中所述,此“findValue”调用在 Struts 的沙盒限制之外运行。
HTTP Request of failed attempt at code execution
代码执行尝试失败的 HTTP 请求
But, it didn’t work! Here’s a small twist, after debugging it was found that, if the OGNL template is longer than ~200 characters, it is blocked based on struts.ognl.expressionMaxLength setting.
但是,它没有用!这里有一个小转折,调试后发现,如果 OGNL 模板的长度超过 ~200 个字符,则会根据 struts.ognl.expressionMaxLength 设置将其阻止。ognl.OgnlException: Parsing blocked due to security reasons! [java.lang.SecurityException: This expression exceeded maximum allowed length: getText('AAAA...AAAA')]
However, modifying the payload just a little bit and utilizing #parameters map to pass argument to exec method, we could bypass this limitation and execute system commands.
但是,稍微修改有效负载并利用 #parameters map 将参数传递给 exec 方法,我们就可以绕过此限制并执行系统命令。
We’ve created a nuclei template to detect this CVE and added into nuclei-templates project – https://github.com/projectdiscovery/nuclei-templates/pull/8982
我们创建了一个 nuclei 模板来检测此 CVE 并添加到 nuclei-templates 项目中 – https://github.com/projectdiscovery/nuclei-templates/pull/8982
Nuclei template to detect CVE-2023-22527 on Atlassian Confluence instances:
用于检测 Atlassian Confluence 实例上的 CVE-2023-22527 的 Nuclei 模板:
By embracing Nuclei and participating in the open-source community or joining the ProjectDiscovery Cloud Platform, organizations can strengthen their security defenses, stay ahead of emerging threats, and create a safer digital environment. Security is a collective effort, and together we can continuously evolve and tackle the challenges posed by cyber threats.
通过拥抱 Nuclei 并参与开源社区或加入 ProjectDiscovery 云平台,组织可以加强其安全防御,领先于新出现的威胁,并创建更安全的数字环境。安全是一项集体努力,我们可以共同不断发展并应对网络威胁带来的挑战。
原文始发于Rahul Maini & Harsh Jaiswal:Atlassian Confluence – Remote Code Execution (CVE-2023-22527)
转载请注明:Atlassian Confluence – Remote Code Execution (CVE-2023-22527) | CTF导航