Microsoft Defender XDR is expanding in the full attack stage. With the new Deception capability in Microsoft Defender XDR, it is possible to detect attackers early in the kill chain and disrupt advanced attacks.
Microsoft Defender XDR正在全面扩展攻击阶段。借助 Microsoft Defender XDR 中的新欺骗功能,可以在杀伤链的早期检测攻击者并中断高级攻击。
Deception is a new feature for Microsoft Defender for Endpoint part of Defender XDR and is now in public preview. The new feature uses machine learning to autogenerate and deploy authentic decoys and lures into your environment. The real power is that no additional deployment of sensors is required and it is fully integrated into the XDR experience.
欺骗是 Microsoft Defender for Endpoint 的一项新功能,是 Defender XDR 的一部分,现已推出公共预览版。新功能使用机器学习来自动生成真实的诱饵和诱饵并将其部署到您的环境中。真正的强大之处在于不需要额外部署传感器,并且完全集成到 XDR 体验中。
| Important: Deception is currently in public preview available. 重要提示:Deception 目前提供公共预览版。 Blog information: 博客信息: Blog published: 16 January, 2024 博客发布时间:2024 年 1 月 16 日 Blog latest updated: 16 January, 2024 博客最后更新日期:2024 年 1 月 16 日 |
What is deception in Defender for Endpoint?
什么是 Defender for Endpoint 中的欺骗?
Deception is a built-in capacity in Microsoft Defender for Endpoint. Deception technologies create an artificial cyber-attack surface within your network that consists of fake credentials/ hosts and decoys that look like high-value assets. The ultimate goal is to deceive attackers and lead them into sensitive credentials/ hosts.
欺骗是 Microsoft Defender for Endpoint 中的内置功能。欺骗技术在您的网络中创建了一个人为的网络攻击面,其中包括虚假凭据/主机和看起来像高价值资产的诱饵。最终目标是欺骗攻击者并引导他们进入敏感的凭据/主机。
When the deception assets are used it will lead to detections into the Defender XDR portal. It can lead to early signs of the attack chain during the credential theft and discovery phase. Attackers commonly use LSASS and local DNS cache dump/ documents to find interesting hosts and credentials.
使用欺骗资产时,将导致检测到 Defender XDR 门户。在凭据盗窃和发现阶段,它可能会导致攻击链的早期迹象。攻击者通常使用 LSASS 和本地 DNS 缓存转储/文档来查找相关的主机和凭据。
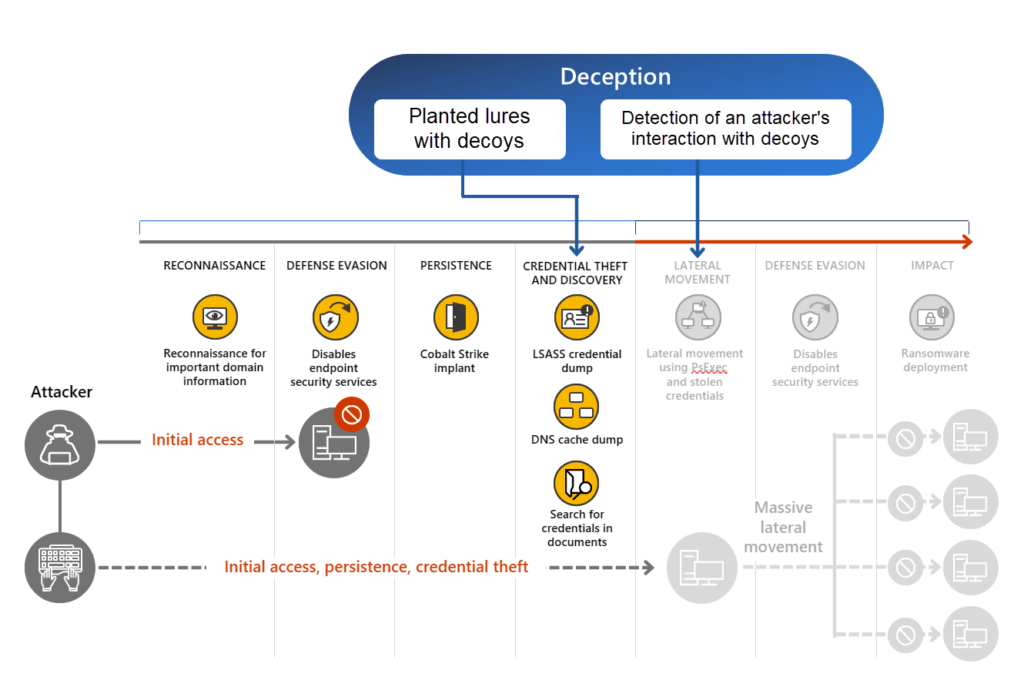
Image source: Microsoft 图片来源:Microsoft
When using deception the following is good to know before starting. In general, there are two items part of the Deception feature (Decoys and Lures).
使用欺骗时,最好在开始之前了解以下内容。一般来说,欺骗功能有两个项目(诱饵和诱饵)。
- Decoys: “fake” assets that trigger an alert when an attacker interacts with the assets, such as a user and host.
诱饵:“虚假”资产,当攻击者与资产(如用户和主机)交互时触发警报。 - Lures: are digital breadcrumbs that lead attackers to decoys and make them look more authentic, such as batch files/ file locations and more
诱饵:是将攻击者引导到诱饵并使其看起来更真实的数字面包屑,例如批处理文件/文件位置等
Prerequisites 先决条件
For the Deception capability, the following prerequisites are important. Currently, the feature is supported for Windows Endpoints only.
对于欺骗功能,以下先决条件非常重要。目前,该功能仅支持 Windows 终结点。
Defender must be the primary EDR solution since Defender for Endpoint must be able to deploy the lures:
Defender 必须是主要的 EDR 解决方案,因为 Defender for Endpoint 必须能够部署诱饵:
- Defender for Endpoint is the primary EDR solution
Defender for Endpoint 是主要的 EDR 解决方案 - Automated investigation and response is configured and enabled
配置并启用自动调查和响应 - Devices are joined or hybrid joined in Microsoft Entra ID
设备在 Microsoft Entra ID 中加入或混合加入 - PowerShell is enabled PowerShell 已启用
- Deception has been supported since Windows 10 RS5 and later
自 Windows 10 RS5 及更高版本以来,一直支持欺骗
When PowerShell is restricted it will give possible conflicts with the deployment of the Lures. When the Decoys are not deployed, check the PowerShell configuration.
当 PowerShell 受到限制时,它可能会与诱饵的部署发生冲突。如果未部署诱饵,请检查 PowerShell 配置。
More information: Manage the deception capability in Microsoft Defender XDR | Microsoft Learn
详细信息:管理 Microsoft Defender XDR 中的欺骗功能 |Microsoft 学习
How to enable deception
如何启用欺骗
The deception capability is part of Defender XDR and can be enabled via security.microsoft.com. By default, the feature is turned off. To turn the feature on, follow the steps below:
欺骗功能是 Defender XDR 的一部分,可以通过 security.microsoft.com 启用。默认情况下,该功能处于关闭状态。要启用该功能,请按照以下步骤操作:
- Select Settings > Endpoints.
选择“设置”>“终结点”。 - Under General, select Advanced features.
在“常规”下,选择“高级功能”。 - Look for Deception and toggle the switch to On.
查找欺骗并将开关切换到开。
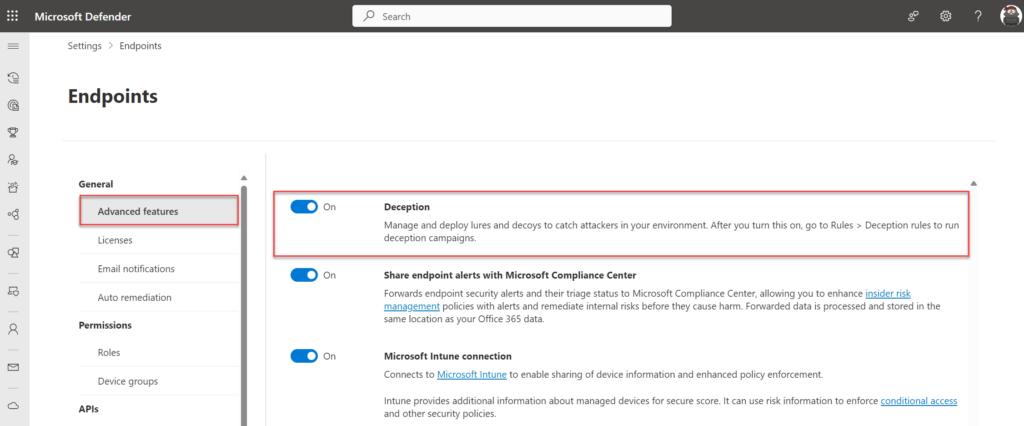
Important: When enabling the deception feature it will automatically enable a default rule. The default rule is enabled by default and deployed to all Windows client devices. When a small scoped test is required with a couple of endpoints it is recommended to disable the default rule and use a custom deception rule with a configured scope or change the scope of the default rule.
重要提示:启用欺骗功能时,它将自动启用默认规则。默认规则默认启用并部署到所有 Windows 客户端设备。当需要对几个终结点进行小型范围测试时,建议禁用默认规则,并使用具有已配置范围的自定义欺骗规则,或更改默认规则的范围。
The deception feature can be configured via Settings -> Endpoints -> Deception. The rule with the name “Default Rule” is generated by default.
欺骗功能可以通过设置 -> 端点 ->欺骗 进行配置。默认情况下会生成名为“默认规则”的规则。
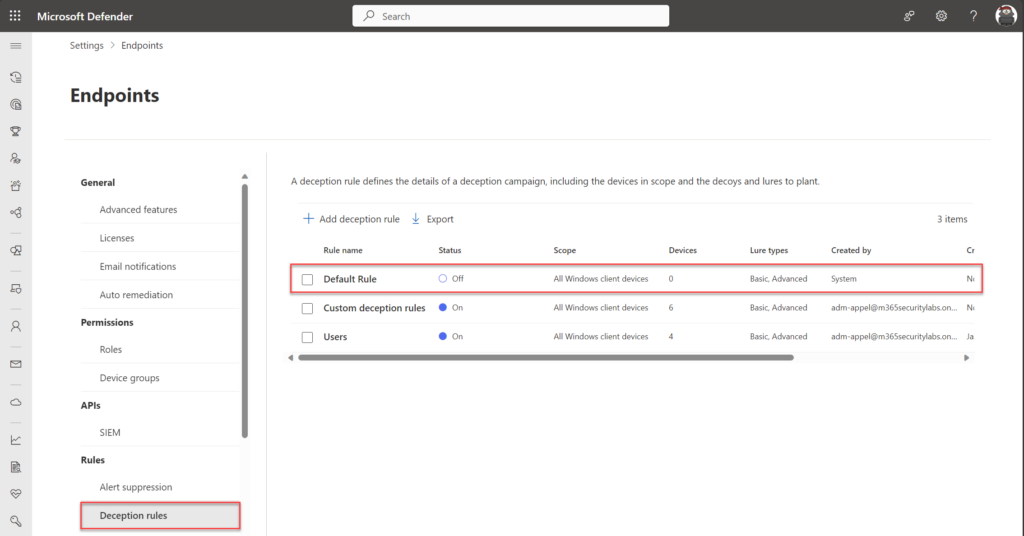
Important: Lures are only planted on Windows clients defined in the scope of a deception rule. However, attempts to use any decoy host or account on any Defender for Endpoint onboarded client raises a deception alert. It can take a couple of hours before the configuration is deployed to machines.
重要提示:诱饵仅植入欺骗规则范围内定义的 Windows 客户端上。但是,尝试在任何 Defender for Endpoint 载入的客户端上使用任何诱饵主机或帐户都会引发欺骗警报。可能需要几个小时才能将配置部署到计算机。
Create and modify deception rules
创建和修改欺骗规则
The deception feature can be configured via Settings -> Endpoints -> Deception. The rule with the name “Default Rule” is generated by default. In the configuration, it is possible to change existing rules and configure new rules.
欺骗功能可以通过设置 -> 端点 ->欺骗 进行配置。默认情况下会生成名为“默认规则”的规则。在配置中,可以更改现有规则和配置新规则。
To create a new rule select Add Deception Rule
若要创建新规则,请选择“添加欺骗规则”
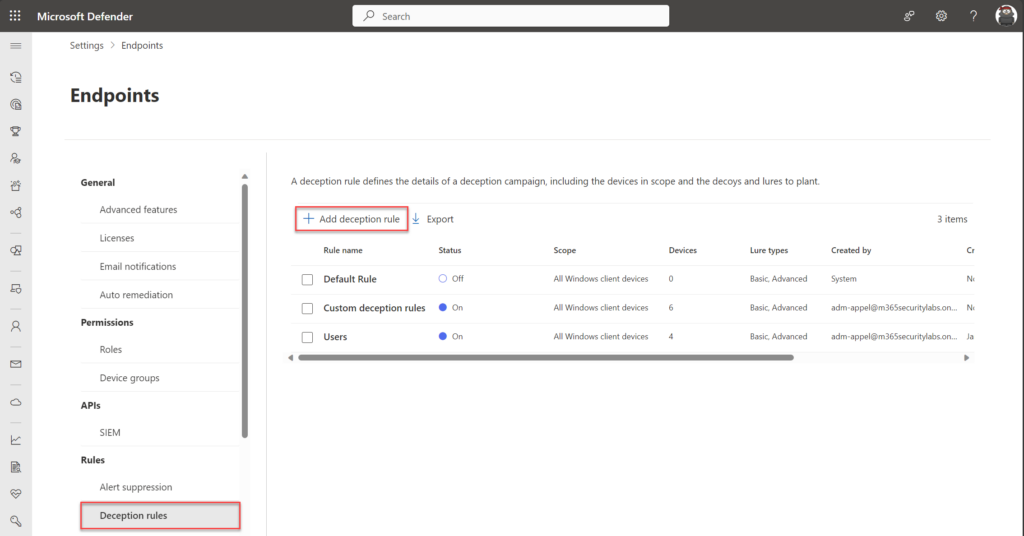
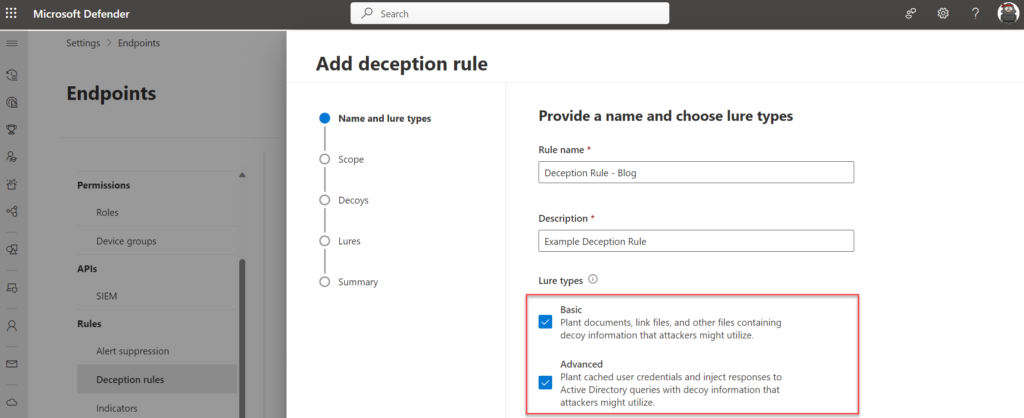
The wizard starts with the name and Lures type. There are two different types of Lures:
向导从名称和诱饵类型开始。有两种不同类型的诱饵:
Basic lures – planted documents, link files, and the like that have no or minimal interaction with the customer environment.
基本诱饵 – 植入的文档、链接文件等,与客户环境没有交互或交互最少。
Advanced lures – planted content like cached credentials and interceptions that respond or interact with the customer environment. For example, attackers might interact with decoy credentials that were injected in responses to Active Directory queries, which can be used to sign in.
高级诱饵 – 植入的内容,如缓存凭据和拦截,以响应或与客户环境交互。例如,攻击者可能会与在响应 Active Directory 查询时注入的诱饵凭据进行交互,这些凭据可用于登录。
Recommended is to configure both Basic and Advanced in the rule creation, which brings ultimate flexibility during the creation of lures.
建议在创建规则时同时配置“基本”和“高级”,这在创建诱饵时带来了极大的灵活性。
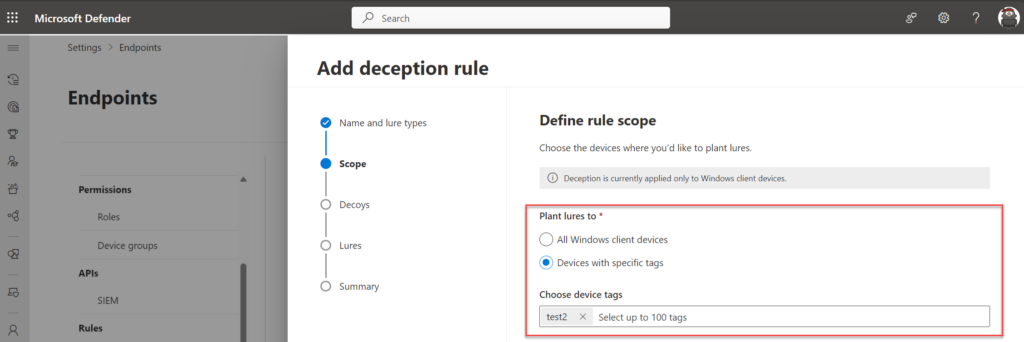
Scope 范围
In the scope wizard it is possible to scope the lures to All Windows client devices or Devices with specific tags. The tag capability works based on the Defender for Endpoint tagging mechanism, any configured tag can be selected in the wizard.
在范围向导中,可以将诱饵的范围限定为所有 Windows 客户端设备或具有特定标记的设备。标记功能基于 Defender for Endpoint 标记机制工作,可以在向导中选择任何配置的标记。
Personally; In larger production environments I would recommend starting with a selected scope based on a specific tag. With this, there is less risk across all devices.
个人;在较大的生产环境中,我建议从基于特定标记的选定范围开始。这样一来,所有设备的风险都会降低。
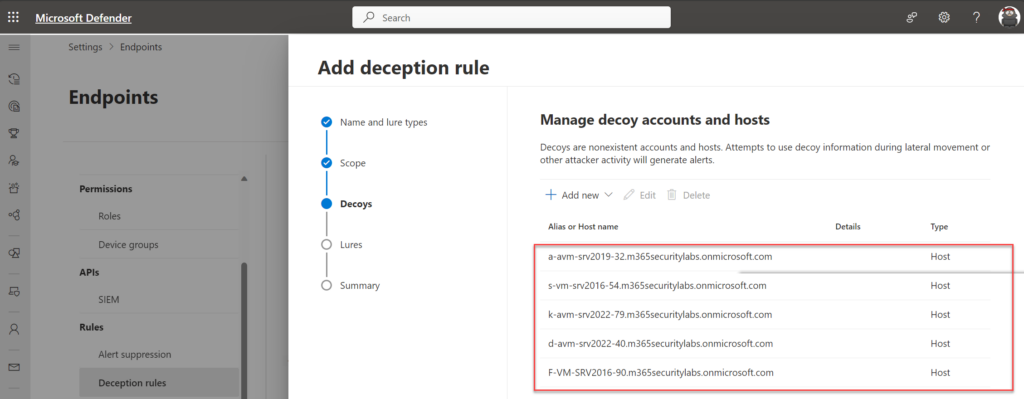
Decoys 诱饵
During the setup Defender XDR will automatically generate decoys. Decoys are nonexistent accounts and hosts.
在设置过程中,Defender XDR 将自动生成诱饵。诱饵是不存在的帐户和主机。
The generation of decoys is based on ML. Using sophisticated ML models, Defender for Endpoint automatically creates assets based on the existing onboarded machines and detected user name conventions.
诱饵的生成基于 ML。 使用复杂的 ML 模型,Defender for Endpoint 根据现有的载入计算机和检测到的用户名约定自动创建资产。
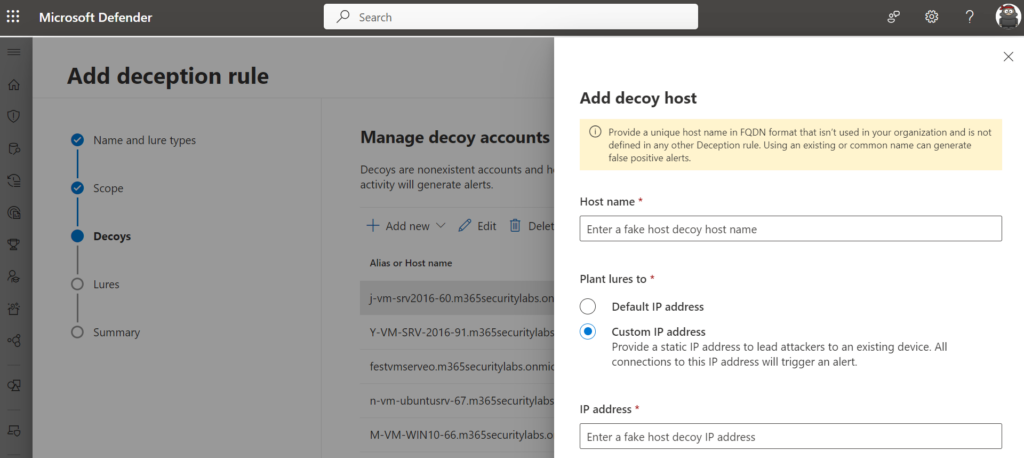
In this advice; my recommendation is to review the ML generation and create a new custom rule matching the naming convention when needed. The goal of deception is to match the company name convention and avoid too many non-company related names since too many fake accounts can be detected easily by attackers and make them suspicious. In some cases, the default ML-generated list is already sufficient with proper decoys and a good naming convention.
在这个建议中;我的建议是查看 ML 生成,并在需要时创建与命名约定匹配的新自定义规则。欺骗的目的是匹配公司名称惯例并避免过多与公司无关的名称,因为攻击者很容易检测到太多虚假帐户并使其产生怀疑。在某些情况下,默认的 ML 生成的列表已经足够了,只要有适当的诱饵和良好的命名约定。
Custom decoy (account and host) can be created via the wizard. Host decoys can be configured with an IP of a honeypot VM. With a static IP address, attackers are led to an existing “honeypot” device.
自定义诱饵(帐户和主机)可以通过向导创建。可以使用蜜罐 VM 的 IP 配置主机诱饵。使用静态 IP 地址,攻击者会被引导到现有的“蜜罐”设备。
Lures 诱惑
Lures can be configured via the following two ways:
诱饵可以通过以下两种方式进行配置:
- Use autogenerated lures 使用自动生成的诱饵
- Use custom lures only
仅使用自定义诱饵
Lures are digital breadcrumbs that lead attackers to decoys and make them look more authentic, such as documents, batch files, and more.
诱饵是数字面包屑,可引导攻击者诱饵并使其看起来更真实,例如文档、批处理文件等。
For the initial configuration, it is advisable to start with the autogenerated lures – the custom lures only feature can be used to define lures that look more authentic based on organizational criteria
对于初始配置,建议从自动生成的诱饵开始——仅自定义诱饵功能可用于根据组织标准定义看起来更真实的诱饵
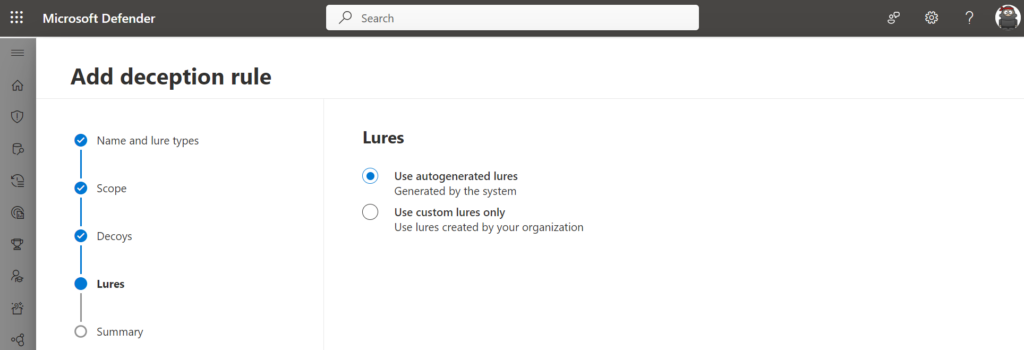
Deployment 部署
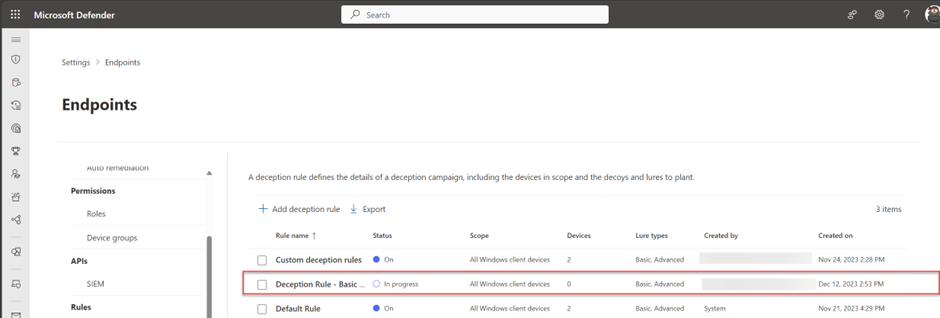
When the lures are configured, and the rule is configured/ deployed the Lures are successfully created. It will take some time before the Lures are deployed to the scoped endpoints. The status “In Progress” indicates the deployment is still in progress. (It can take some hours before the decoys are deployed across the targeted endpoints).
配置诱饵并配置/部署规则后,诱饵将成功创建。将诱饵部署到作用域内终结点需要一些时间。状态“进行中”表示部署仍在进行中。(可能需要几个小时才能在目标端点上部署诱饵)。
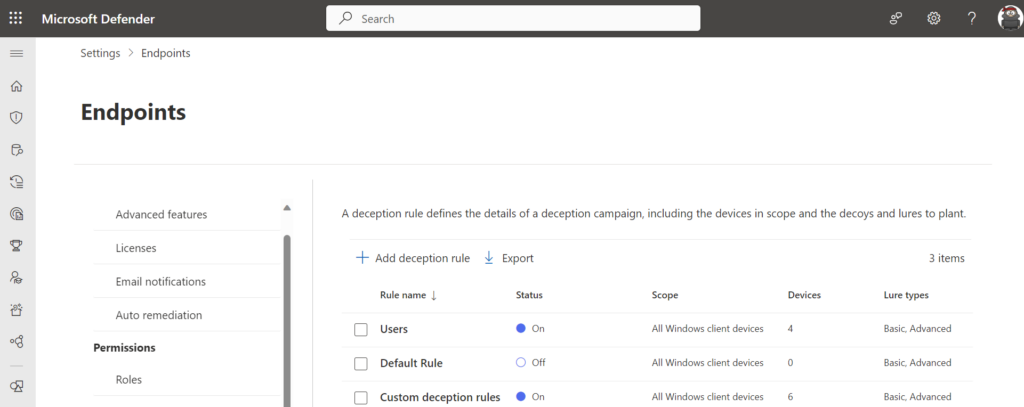
When the rule is successfully deployed it will show the status On with a count of devices. This indicates the rule is successfully enabled.
成功部署规则后,它将显示“打开”状态,并显示设备计数。这表示规则已成功启用。
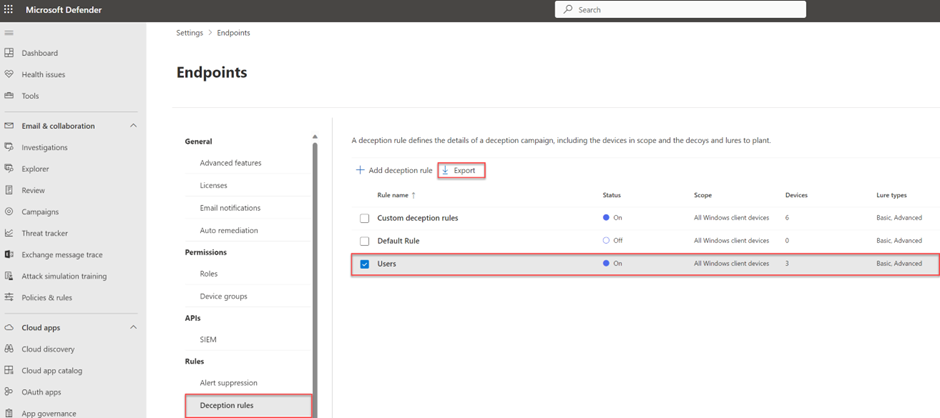
With the use of the Export to CSV button, it is possible to confirm if the lures are correctly planted on the endpoint/ devices.
通过使用“导出到 CSV”按钮,可以确认诱饵是否正确植入端点/设备上。
Part of the CSV is more information. Select the deception rule and click export to CSV. As a result, the CSV contains all the information including the deployed endpoints.
CSV 的一部分是更多信息。选择欺骗规则,然后单击导出到 CSV。因此,CSV 包含所有信息,包括已部署的终结点。
Result of the CSV file: With the deployment status and device ID it is possible to track whether the decoy is correctly enabled for which specific device. It will show the decoy/ lure type and decoy entity path.
CSV 文件的结果:通过部署状态和设备 ID,可以跟踪是否为哪个特定设备正确启用了诱饵。它将显示诱饵/诱饵类型和诱饵实体路径。
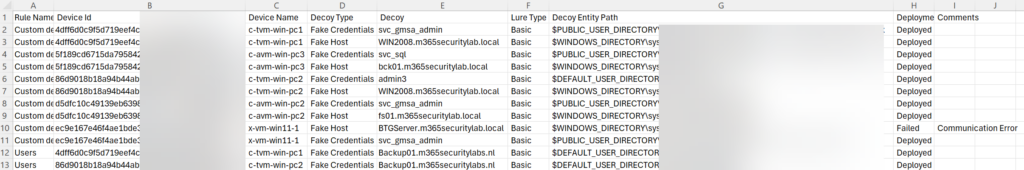
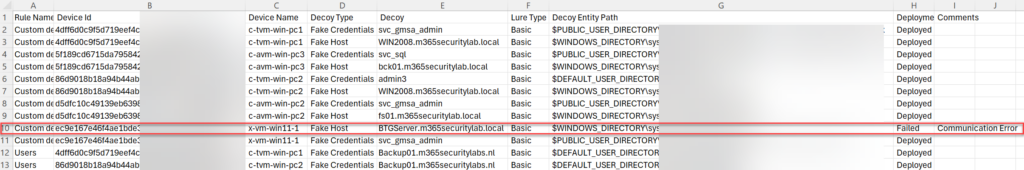
When the deployment is failed it will show the deploymentstatus Failed with additional comments.
当部署失败时,它将显示部署状态“失败”,并带有其他注释。
Where are the decoys located?
诱饵在哪里?
All decoys are planted on the scoped MDE devices and not planted in the Active Directory or Azure Active Directory. More detailed entity path locations are visible via the export CSV method as already explained in the previous step. For the fake credential type, there are various other locations where the credentials are located and planted.
所有诱饵都植入在作用域内的 MDE 设备上,而不是植入 Active Directory 或 Azure Active Directory 中。更详细的实体路径位置可通过导出 CSV 方法显示,如上一步所述。对于伪造凭据类型,还有各种其他位置可以放置和放置凭据。
Since this blog is publicly available – I will not share the actual location where the decoys are visible, and what it looks like from the end-end user’s devices. Since the real power of deception is based on visibility, and how it looks like normal/ used accounts.
由于此博客是公开的,因此我不会分享诱饵可见的实际位置,以及最终用户设备的外观。由于欺骗的真正力量是基于可见性,以及它看起来像正常/使用过的帐户。
Test and simulate 测试和模拟
Simulation of alerts based on the deception accounts is possible via various methods.
可以通过各种方法模拟基于欺骗帐户的警报。
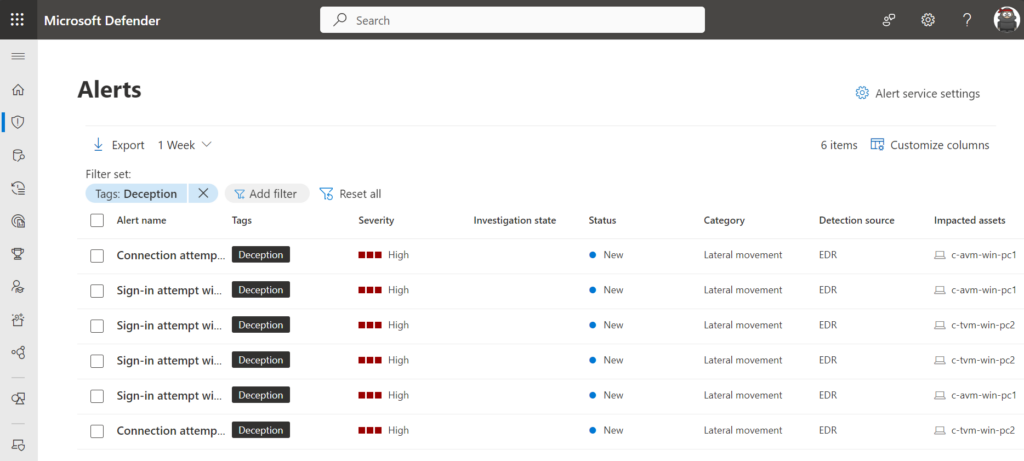
When a decoy is targeted (e.g. by Red Team or Bad Actors by lateral movement, an Incident with the tag (deception) is created in Microsoft Defender XDR.
当诱饵成为目标时(例如,由红队或不良行为者通过横向移动),将在 Microsoft Defender XDR 中创建带有标记(欺骗)的事件。
Good to know – all alerts related to the deception feature are tagged with the tag “Deception” in the Microsoft Defender XDR portal.
很高兴知道 – 与欺骗功能相关的所有警报都在 Microsoft Defender XDR 门户中标记有“欺骗”标记。
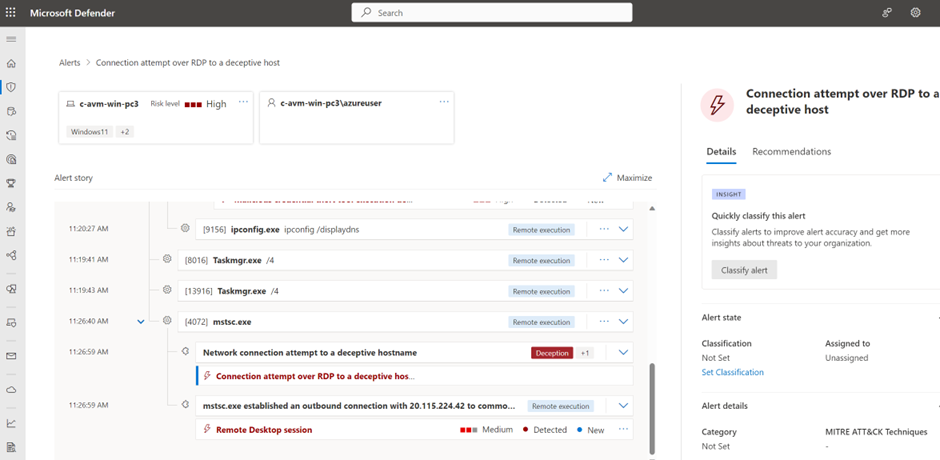
Simulate alert for host 模拟主机警报
An RDP (Remote Desktop Protocol) session to a discovered device results in an error but is enough to trigger the alert in Defender XDR. RDP to one of the hostnames; and the alert with the name: Connection attempt over RDP to a deceptive host will show in the portal.
与已发现设备的 RDP(远程桌面协议)会话会导致错误,但足以触发 Defender XDR 中的警报。RDP 到其中一个主机名;以及名称为“尝试通过 RDP 连接到欺骗性主机”的警报将显示在门户中。
Simulate alert for user 模拟用户警报
When using the deceptive user decoys during a sign-in to any MDE-covered devices in the tenant, it will lead to the following alert visible in Defender XDR: Sign-in attempt with the deceptive user account.
在登录到租户中任何 MDE 覆盖的设备期间使用欺骗性用户诱饵时,将导致 Defender XDR 中显示以下警报:使用欺骗性用户帐户登录尝试。
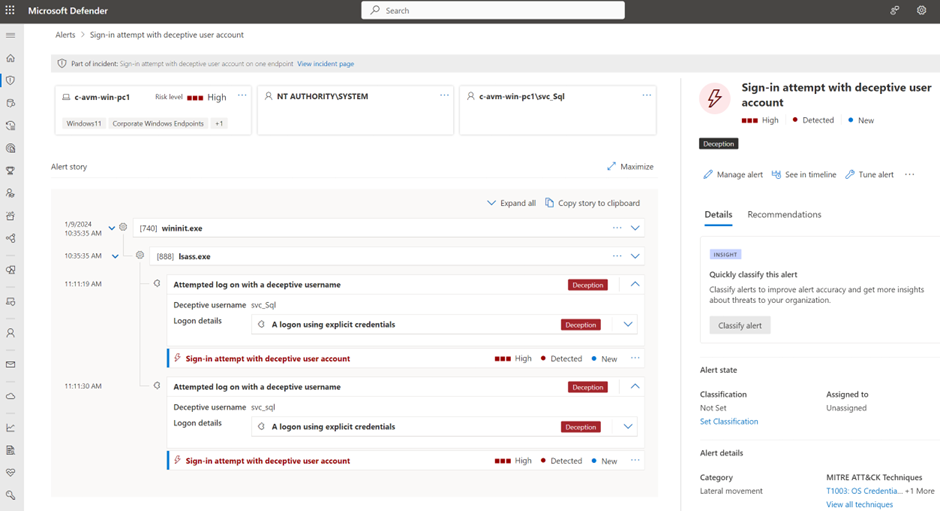
Conclusion 结论
Deception is a great new feature as part of the Defender XDR solution. It will increase the detection of attacks launched during the early stages. It is good to see the deception feature is powered by existing agents and is running without any additional sensors or separate agents installed on endpoints.
欺骗是 Defender XDR 解决方案中的一项很棒的新功能。它将增加对早期阶段发起的攻击的检测。很高兴看到欺骗功能由现有代理提供支持,并且在未在端点上安装任何其他传感器或单独代理的情况下运行。
Sources 来源
Microsoft: Manage the deception capability in Microsoft Defender XDR
Microsoft:管理 Microsoft Defender XDR 中的欺骗功能
Microsoft: Microsoft Defender for Endpoint deception | Ninjashow
Microsoft:Microsoft Defender for Endpoint 欺骗 |忍者秀
原文始发于Jeffrey, January :How to use deception in Microsoft Defender for Endpoint/ Defender XDR
转载请注明:How to use deception in Microsoft Defender for Endpoint/ Defender XDR | CTF导航